虽然是和上一篇一起看的,以防混淆我还是分开来写吧
另:大佬们不给事情做真的让我很心痛啊/(ㄒoㄒ)/~~
今天主要讲的是第三部分,SIEM的工具
PART III SIEM Tools
CHAPTER 8 AlienVault OSSIM Implementation
OSSIM:Open Source Security Information Management
The concept of OSSIM is simple—don’t reinvent the wheel
some open source tools:
- Snort:the premier open source IDS available today
- OpenVAS:a General Public Licensed (GPL) version of Nessus, a popular open source vulnerability scanning tool,provide vulnerability scans of network assets and add that valuable information to the OSSIM database
- Ntop:a popular open source network traffic–monitoring tool
- Nagios:a popular open source network device–monitoring software tool
- PADS:The Passive Asset Detection System (PADS) is a unique tool(sniffer)
- P0f:passive operating system fingerprinting (discovery of operating system type and version)
- OCS-NG:This tool provides an automated way to keep track of what you have and provides the security analyst with that information as needed.
- OSSEC:an open source host-based intrusion detection system (HIDS)(protect OSSIM itself)
- OSVDB:database
- NFSen/NFDump:an important artifact of network traffic and is extremely valuable in the correlation process
- Inprotect:a web-based interface for Nessus, OpenVAS, and NMAP
Functionality:
Detect:pattern based (signature) and anomaly based(事实上就是特征检测和异常检测,后者可以有效的识别新的攻击模式,而前者不行)
Monitor:
Network Monitoring:
- Network usage information
- Service activity information
- Real-time session monitoring
Availability Monitoring:DoS attackers
Customized System Monitoring:自定义
Scan:OpenVAS
Inventory:点清楚我们到底有些什么,才能知道我们会失去什么
Collect:与前面一致
Risk Assessment:A measure of the potential Impact of a Threat on Assets given the Probability that it will occur.
- Asset value (how much does it cost if compromised?)
- Threat represented by the event (how much damage can be done to the asset?)
- The probability that the event will occur (or get past mitigating factors)
Correlate: The most important aspect of any SIEM tool is the correlation engine.
false positives (false alarms) and false negatives(where intrusions go unnoticed)这个概念我们下一章再聊
- Logical Correlation: rules
- Inventory Correlation: 不太可能出现的情况
- Cross Correlation:a cross-check between IDS data and vulnerability data
Respond、Manage、Report、Measure
Design:
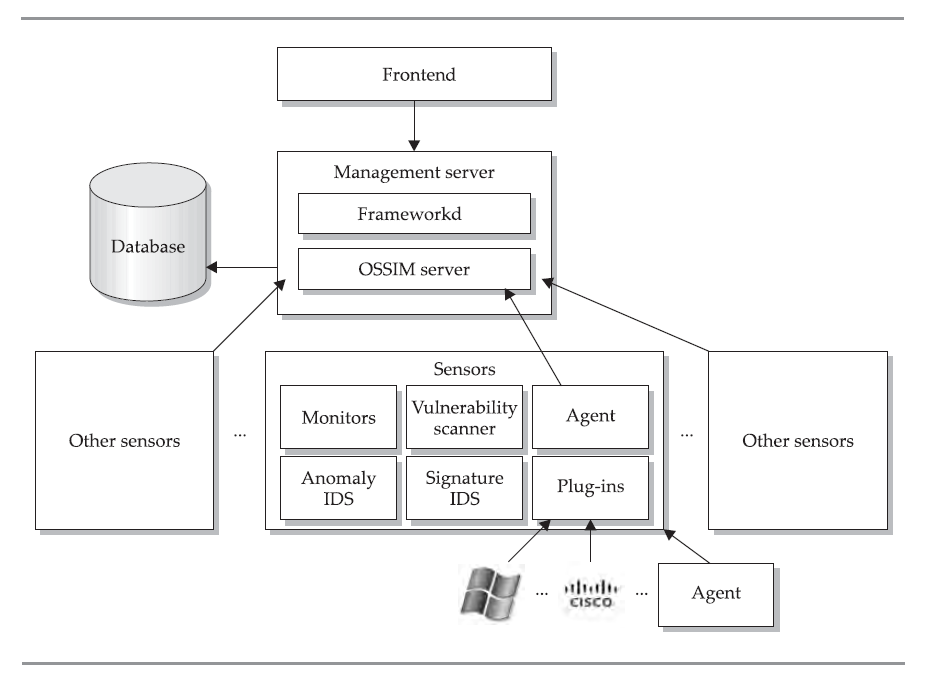
Architecture:这就是实际上的SIEM的整个架构
Sensor:
- Serve as a security detector by performing pattern-based or anomaly intrusion detection
- Serve as a network vulnerability scanner
- Perform network monitoring
Management Server:
- Frameworkd, which serves as a daemon that controls other components
- OSSIM server, which processes the events received from sensors
Database:需购买专业版- -
Frontend:interface
这一章后面的内容就是关于如何安装与使用(下一章),有需要的朋友可以详细阅读Security Information and Event Management (SIEM) Implementation






















 1112
1112











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








