今天直接捡重点的讲吧,不重要的部分都跳过去了
今天主要内容是SIEM的整个架构
PART II IT Threat Intelligence Using SIEM Systems
CHAPTER 5 The Anatomy of a SIEM
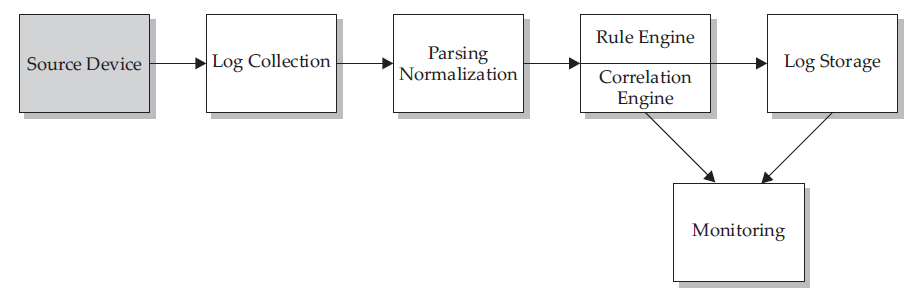
首先是整个SIEM的流程图:
Source Device:
router, switch, or some type of server logs from an application
resources:
1.Operating Systems:Linux and UNIX, AIX, Mac OS X
2.Appliances:black box systems (router or a switch)
3.Applications:
off-the-shelf applications:Domain Name System (DNS), dynamic host configuration protocol (DHCP), various types of web servers, various types of email systems, and a multitude of other types of applications
home-grown or custom-built applications:相对来说难一点,但不是不可能
Determining Needed Logs:
One thing you might want to consider is that not all logs are needed from all devices.
types of logs
types of devices
things to consider:
device’s priority
the size of the logs generated during a specific period of time
rate does this source generate logs
the network links like between the source and the SIEM
the logs in realtime or can you set up a batch process at specific times during the day
besides need more variables,and buffers -> worm outbreak / DOS….
Log Collection:
Push Log Collection
说白了就是每个device将自己产生的日志文件主动传递到SIEM的指定的server上
benifit:ease of setup and configuration at the SIEM
disadvantage:UDP failed sending、attacker inject garbage data
Pull Log Collection
相对应的,这种方式需要SIEM自己构建一个connection到源设备,然后取得log,区别的方法很简单就是看哪一端是日志流的发起者和终结者
disadvantage:关于这个方法,缺点就是非实时的,根据系统要求要实现的功能不一样
Prebuilt Log Collection:将log文件的格式重构,形成SIEM能看懂的standard的文件
Custom Log Collection:对于那些本身不支持SIEM的软件或者设备,需要自己构建一个log收集系统(own method to collect logs)
Mixed Environments:(4kinds)
- software:Cisco ASA Snort IDS
- OS:RedHat Linux Windows 2003
- database:MySQL
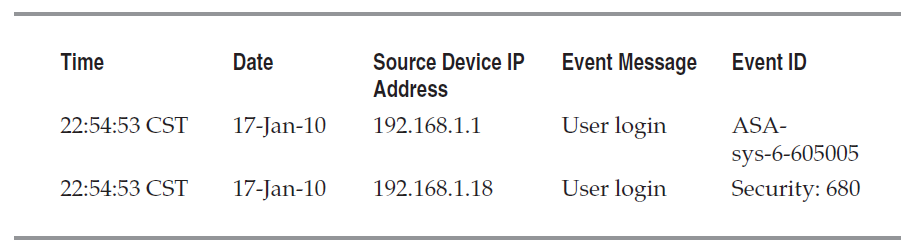
Parsing/Normalization of Logs:
一句话,类型转换many types -> single format
结果如下:
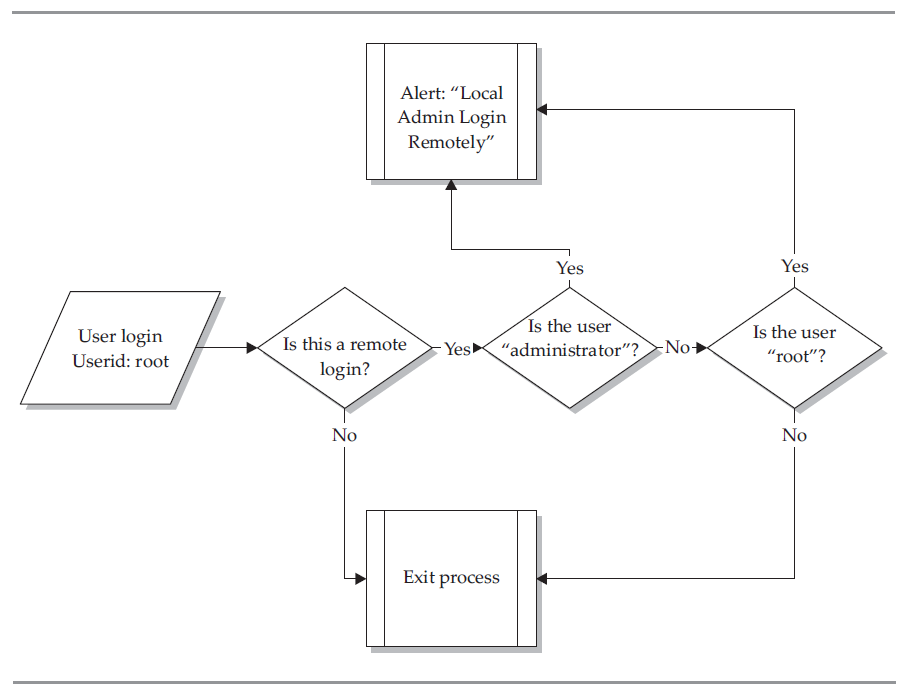
Rule Engine/Correlation Engine:
rules:类似于IDS实验当中我们在snort当中写的规则,具体判断过程如下:
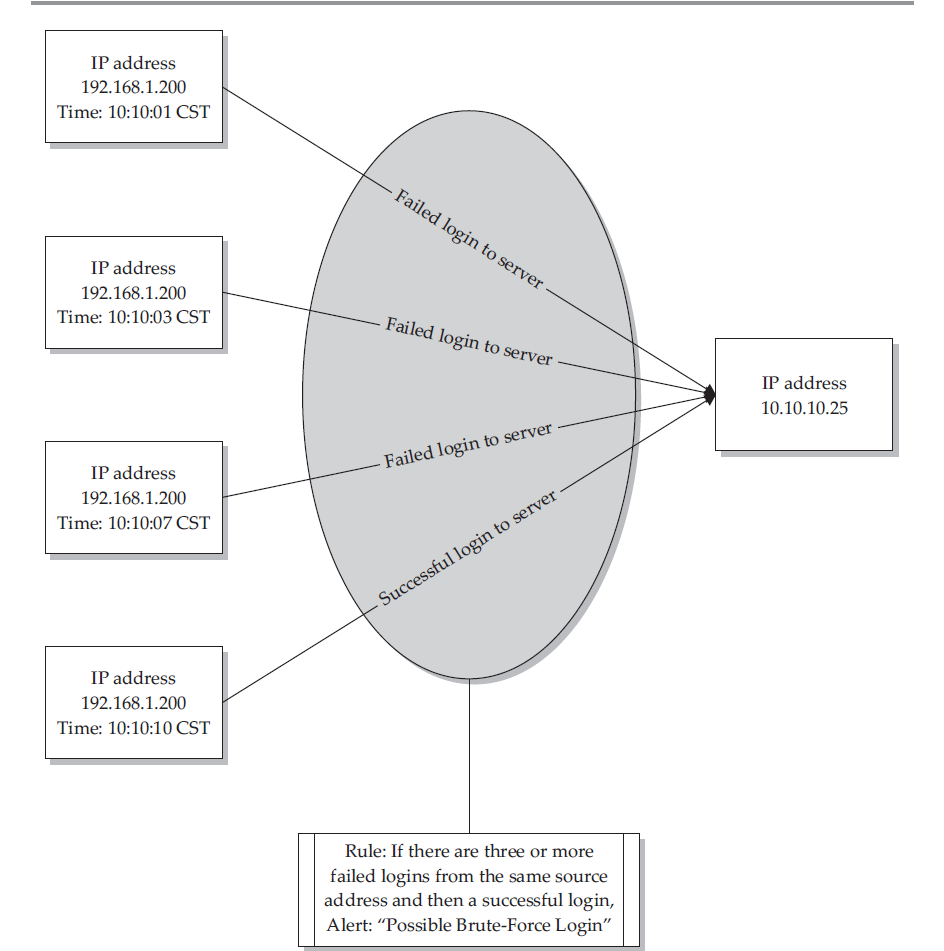
correlation:
It groups individual events, which can make up a part of a possible malicious incident, into a single event displayed on the console of an operator monitoring your environment.
example:brute-force login

after correlating:
rules:If [(failed logins >= 3) and then (Successful Login)] from the same source within 20 seconds = Possible Brute Force Compromise
Log Storage:
- Database:Oracle, MySQL, Microsoft SQL (need DBA)
- Flat Text File:slower but much easier to access
- Binary File:——
Monitoring:
one word:interface
Summary
A SIEM is composed of many parts, each doing a separate job. Remember, each of these systems can run independently of the others, but without them all running in unison, you will not have an effective SIEM. Depending on the system you are using, there may be more pieces added to that specific SIEM, but each SIEM will always have the basic underlying systems as described in this chapter. By understanding each part of the SIEM, what each piece does and how it works, you will be able to manage your SIEM effectively and troubleshoot issues as they arise.





















 1112
1112











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








