07-20210305在WIN10下通过USB口给华为海思Hi3516DV300刷机(鸿蒙系统)
2021/3/5 17:26
https://blog.csdn.net/cocoron/article/details/105194160
【海思篇】【Hi3516DV300】三、使用USB烧写映像
https://blog.csdn.net/qq_30722795/article/details/113501321
IPC Hi3518EV300开发板——移植Linux 0.串口快速烧录教程
开发板:【HarmonyOS HiSpark AI Camera】
串口/SSH工具:Xshell-7(Build 0056)
USB转串口驱动:CH340请自行安装
USB刷机用的驱动程序:Zadig 2.5 (4.9 MB) (Updated 2020.03.28)
https://zadig.akeo.ie/
https://github.com/pbatard/libwdi/releases/download/b730/zadig-2.5.exe
烧录工具:Hi3516-HiTool.zip。HiTool版本:5.2.7
烧录方式:通过USB线刷机。
需要2条TYPE-C接口的USB线。
第一条:和黄色网口同侧的灰色TYPE-C接口的USB线。这条USB线是供电线,我直接接Coolpad充电器了!
接到电脑上应该也是可以的!^_
第二条:接在网口背面的白色TYPE-C接口的USB线。
请严重注意,这条USB线必须接,并且必须接到你的WINDOWS电脑上!!!!


1、Zadig 2.5的安装(STEP-BY-STEP):(只需要安装一次!)
通过XShell7在Hi3516DV300启动到uboot的时候按回车键,然后输入:usb device。

点击右下角的USB设备图标,可以看到:弹出HiUSBBurn。(只是告诉你确认,不是让你真弹出这个设备!)


Options→List All Devices→


Options→List All Devices→HiUSBBurn
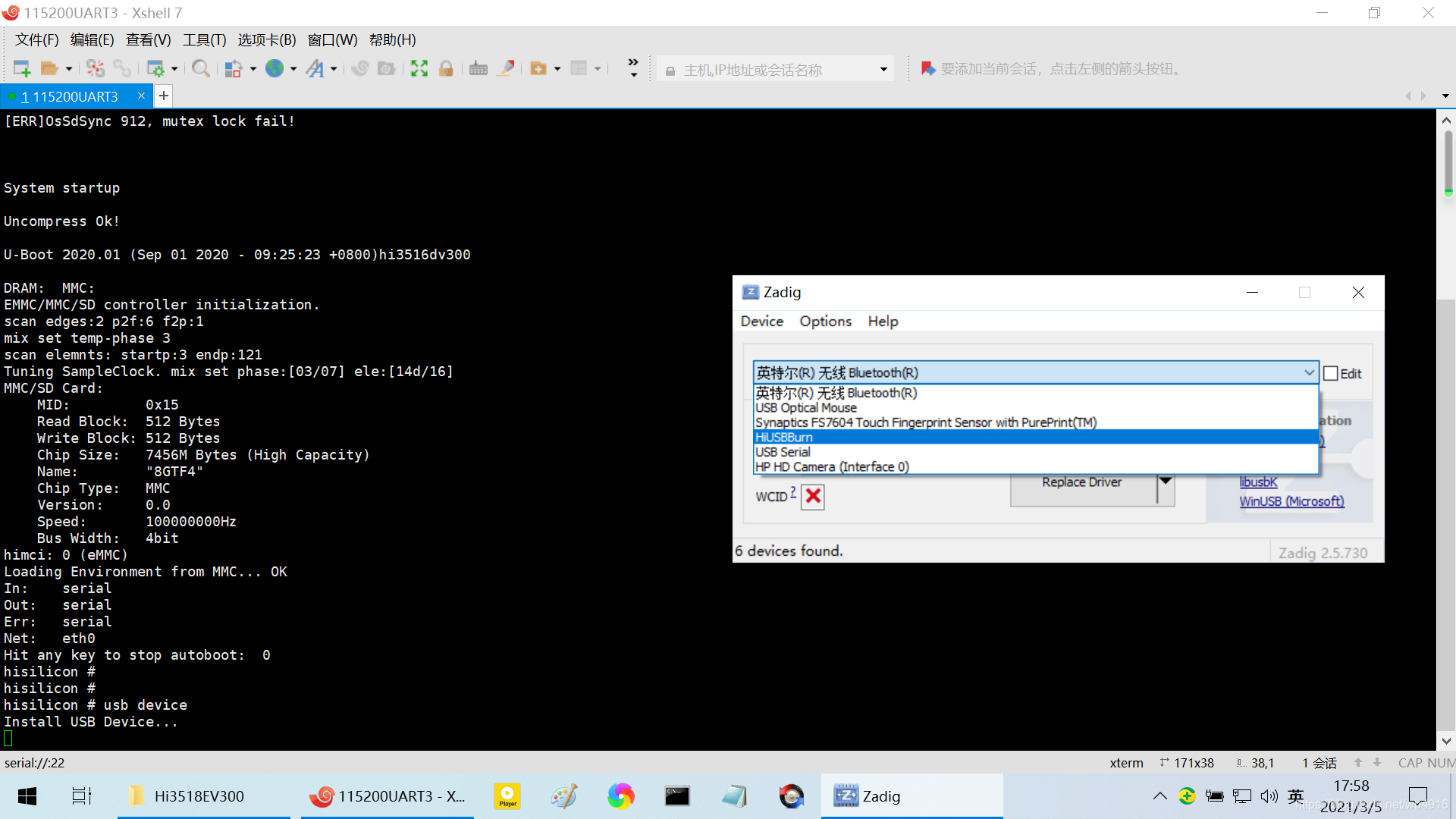
点击:Install Driver


不用管360杀毒/安全卫士的警告了,直接选择:允许程序所有操作!

点击Install Driver

The driver was installed successfully


3、通过USB线刷机:
HiTool配置:
PC与板端配置:
传输方式:USB口
本地PC配置:(不需要配置)
板端配置:(不需要配置)
点击:烧写!


出现刷机界面之后(大概5秒钟,你默念1到5即可^_),还需要重新拔(等大概5秒钟)插USB一次。
(请严重注意,是开发板背面的那条线!^_)



4、
由于没有擦除全器件,刷机之后你会发现:
根目录的你建立的文件没有了!
/userdata下的文件和目录还在!^_
[BEGIN] 2021/3/5 17:14:50
OHOS #
OHOS #
OHOS #
OHOS # pwd
/
OHOS #
OHOS #
OHOS # ls
Directory /:
drwxr-xr-x 0 u:0 g:0 dev
dr-xr-xr-x 0 u:0 g:0 proc
drwxrwxrwx 0 u:0 g:0 sdcard
drwxrwxrwx 0 u:0 g:0 storage
drwxrwxrwx 0 u:0 g:0 userdata
drwxrwxrwx 0 u:0 g:0 bin
drwxrwxrwx 0 u:0 g:0 etc
drwxrwxrwx 0 u:0 g:0 lib
drwxrwxrwx 0 u:0 g:0 system
drwxrwxrwx 0 u:0 g:0 usr
drwxrwxrwx 0 u:0 g:0 vendor
OHOS #
OHOS #
OHOS # mkdir 03051714
OHOS #
OHOS # ls
Directory /:
drwxr-xr-x 0 u:2 g:2 03051714
drwxr-xr-x 0 u:0 g:0 dev
dr-xr-xr-x 0 u:0 g:0 proc
drwxrwxrwx 0 u:0 g:0 sdcard
drwxrwxrwx 0 u:0 g:0 storage
drwxrwxrwx 0 u:0 g:0 userdata
drwxrwxrwx 0 u:0 g:0 bin
drwxrwxrwx 0 u:0 g:0 etc
drwxrwxrwx 0 u:0 g:0 lib
drwxrwxrwx 0 u:0 g:0 system
drwxrwxrwx 0 u:0 g:0 usr
drwxrwxrwx 0 u:0 g:0 vendor
OHOS #
OHOS #
OHOS # touch 03051715
touch error: Permission denied
OHOS # sudo touch 03051715
sudo:command not found
OHOS #
OHOS #
OHOS # who
who:command not found
OHOS #
OHOS # whoami
whoami:command not found
OHOS #
OHOS #
OHOS # help
*******************shell commands:*************************
arp cat cat_logmpp cd chgrp chmod chown cp
cpup date dhclient dmesg dns format free help
hi3881 hwi ifconfig ipdebug kill log ls lsfd
memcheck mkdir mount netstat oom partinfo partition ping
ping6 pmm pwd readreg reset rm rmdir sem
stack statfs su swtmr sync systeminfo task telnet
tftp touch umount uname v2p virstatfs vmm watch
writeproc
OHOS #
OHOS #
OHOS # touch 55555555
touch error: Permission denied
OHOS #
OHOS #
OHOS # ps
ps:command not found
OHOS #
OHOS #
OHOS # pwd
/
OHOS #
OHOS # ls
Directory /:
drwxr-xr-x 0 u:2 g:2 03051714
drwxr-xr-x 0 u:0 g:0 dev
dr-xr-xr-x 0 u:0 g:0 proc
drwxrwxrwx 0 u:0 g:0 sdcard
drwxrwxrwx 0 u:0 g:0 storage
drwxrwxrwx 0 u:0 g:0 userdata
drwxrwxrwx 0 u:0 g:0 bin
drwxrwxrwx 0 u:0 g:0 etc
drwxrwxrwx 0 u:0 g:0 lib
drwxrwxrwx 0 u:0 g:0 system
drwxrwxrwx 0 u:0 g:0 usr
drwxrwxrwx 0 u:0 g:0 vendor
OHOS #
OHOS #
OHOS # mkdir 88888888
OHOS #
OHOS #
OHOS # ls
Directory /:
drwxr-xr-x 0 u:2 g:2 03051714
drwxr-xr-x 0 u:2 g:2 88888888
drwxr-xr-x 0 u:0 g:0 dev
dr-xr-xr-x 0 u:0 g:0 proc
drwxrwxrwx 0 u:0 g:0 sdcard
drwxrwxrwx 0 u:0 g:0 storage
drwxrwxrwx 0 u:0 g:0 userdata
drwxrwxrwx 0 u:0 g:0 bin
drwxrwxrwx 0 u:0 g:0 etc
drwxrwxrwx 0 u:0 g:0 lib
drwxrwxrwx 0 u:0 g:0 system
drwxrwxrwx 0 u:0 g:0 usr
drwxrwxrwx 0 u:0 g:0 vendor
OHOS #
OHOS #
OHOS # cd userdata
OHOS #
OHOS #
OHOS # ls
Directory /userdata:
drwxrwxrwx 0 u:0 g:0 12345678
OHOS #
OHOS #
OHOS # touch 03051716
OHOS #
OHOS # ls
Directory /userdata:
drwxrwxrwx 0 u:0 g:0 12345678
-rwxrwxrwx 0 u:0 g:0 03051716
OHOS #
OHOS #
OHOS # touch loveu99
OHOS #
OHOS # ls
Directory /userdata:
drwxrwxrwx 0 u:0 g:0 12345678
-rwxrwxrwx 0 u:0 g:0 03051716
-rwxrwxrwx 0 u:0 g:0 loveu99
OHOS #
OHOS #
OHOS # cd ..
OHOS #
OHOS #
OHOS # ls
Directory /:
drwxr-xr-x 0 u:2 g:2 03051714
drwxr-xr-x 0 u:2 g:2 88888888
drwxr-xr-x 0 u:0 g:0 dev
dr-xr-xr-x 0 u:0 g:0 proc
drwxrwxrwx 0 u:0 g:0 sdcard
drwxrwxrwx 0 u:0 g:0 storage
drwxrwxrwx 0 u:0 g:0 userdata
drwxrwxrwx 0 u:0 g:0 bin
drwxrwxrwx 0 u:0 g:0 etc
drwxrwxrwx 0 u:0 g:0 lib
drwxrwxrwx 0 u:0 g:0 system
drwxrwxrwx 0 u:0 g:0 usr
drwxrwxrwx 0 u:0 g:0 vendor
OHOS #
OHOS #
OHOS # pwd
/
OHOS #
OHOS #
OHOS # mkdir loveyou99
OHOS #
OHOS # ls
Directory /:
drwxr-xr-x 0 u:2 g:2 03051714
drwxr-xr-x 0 u:2 g:2 88888888
drwxr-xr-x 0 u:0 g:0 dev
drwxr-xr-x 0 u:2 g:2 loveyou99
dr-xr-xr-x 0 u:0 g:0 proc
drwxrwxrwx 0 u:0 g:0 sdcard
drwxrwxrwx 0 u:0 g:0 storage
drwxrwxrwx 0 u:0 g:0 userdata
drwxrwxrwx 0 u:0 g:0 bin
drwxrwxrwx 0 u:0 g:0 etc
drwxrwxrwx 0 u:0 g:0 lib
drwxrwxrwx 0 u:0 g:0 system
drwxrwxrwx 0 u:0 g:0 usr
drwxrwxrwx 0 u:0 g:0 vendor
OHOS #
OHOS #
OHOS # reset
[ERR]OsSdSync 912, mutex lock fail!
System startup
Uncompress Ok!
U-Boot 2020.01 (Sep 01 2020 - 09:25:23 +0800)hi3516dv300
DRAM: MMC:
EMMC/MMC/SD controller initialization.
scan edges:2 p2f:6 f2p:1
mix set temp-phase 3
scan elemnts: startp:3 endp:121
Tuning SampleClock. mix set phase:[03/07] ele:[14d/16]
MMC/SD Card:
MID: 0x15
Read Block: 512 Bytes
Write Block: 512 Bytes
Chip Size: 7456M Bytes (High Capacity)
Name: "8GTF4"
Chip Type: MMC
Version: 0.0
Speed: 100000000Hz
Bus Width: 4bit
himci: 0 (eMMC)
Loading Environment from MMC... OK
In: serial
Out: serial
Err: serial
Net: eth0
Hit any key to stop autoboot: 0
hisilicon #
hisilicon #
hisilicon # usb device
Install USB Device...
MMC write: dev # 0, block # 2048, count 10112 ... 10112 blocks written: OK
37.74 MB/s
MMC write: dev # 0, block # 20480, count 28686 ... 28686 blocks written: OK
37.31 MB/s
MMC write: dev # 0, block # 51200, count 102400 ... 102400 blocks written: OK
37.22 MB/s
resetting ...
System startup
Uncompress Ok!
U-Boot 2020.01 (Sep 01 2020 - 09:25:23 +0800)hi3516dv300
DRAM: MMC:
EMMC/MMC/SD controller initialization.
scan edges:2 p2f:6 f2p:1
mix set temp-phase 3
scan elemnts: startp:3 endp:121
Tuning SampleClock. mix set phase:[03/07] ele:[14d/16]
MMC/SD Card:
MID: 0x15
Read Block: 512 Bytes
Write Block: 512 Bytes
Chip Size: 7456M Bytes (High Capacity)
Name: "8GTF4"
Chip Type: MMC
Version: 0.0
Speed: 100000000Hz
Bus Width: 4bit
himci: 0 (eMMC)
Loading Environment from MMC... OK
In: serial
Out: serial
Err: serial
Net: eth0
Hit any key to stop autoboot: 0
MMC read: dev # 0, block # 2048, count 18432 ... 18432 blocks read: OK
45.22 MB/s
## Starting application at 0x80000000 ...
******************Welcome******************
Processor : Cortex-A7 * 2
Run Mode : SMP
GIC Rev : GICv2
build time : Feb 26 2021 15:41:49
Kernel : Huawei LiteOS 2.0.0.35/debug
*******************************************
main core booting up...
[ERR][HDF:E/hcs_blob_if]CheckHcsBlobLength: the blobLength: 13128, byteAlign: 1, totalSize: -13108
releasing 1 secondary cores
cpu 0 entering scheduler
random dev init ...
cpu 1 entering scheduler
proc fs init ...
Mount procfs finished.
MMC dev init ...[ERR]No console dev used.
[ERR]No console dev used.
mem dev init ...
spi nor flash init ...
spinor_get_dev_id(56): Spi(cs0) have no device.
Cs[0] have no device!!!
spinor_get_dev_id(56): Spi(cs1) have no device.
Cs[1] have no device!!!
hifmc100_attach(130): Error:spinor scan fail!
net init ...
tcpip_init start
tcpip_init end
Ethernet start.hisi_eth: User did not set phy mode, use default=rmii
disk_init : register /dev/mmcblk0 ok!
hisi_eth: User did not set phy addr, auto scan...
No OTP data, festa PHY use default ATE parameters!
festa PHY wait autotrim done timeout!
Detected phy addr 1, phyid: 0x1cc816
spinor_get_dev_id(56): Spi(cs0) have no device.
Cs[0] have no device!!!
spinor_get_dev_id(56): Spi(cs1) have no device.
Cs[1] have no device!!!
hifmc100_attach(130): Error:spinor scan fail!
Link is Up - 100Mbps/Full
************************************************************
usb init ...
******** usb_init in **********
usb v3.05 2019-11-20 10:40
xhci_init (xhci0): 64 bytes context size, 32-bit DMA
usb_bus_attach (usbus0): 5.0Gbps Super Speed USB v3.0
spinor_get_dev_id(56): Spi(cs0) have no device.
Cs[0] have no device!!!
spinor_get_dev_id(56): Spi(cs1) have no device.
Cs[1] have no device!!!
hifmc100_attach(130): Error:spinor scan fail!
******** usb_init ok**********
Date:Feb 26 2021.
Time:15:42:43.
ugen0.1: <vendor 0x0000> at usbus0
OsMountRootfs start ...
device_set_usb_desc (uhub0): <vendor 0x0000 XHCI root HUB, class 9/0, rev 3.00/1.00, addr 1> on usbus0
disk_init : register /dev/mmcblk0 ok!
DiskAddPart : register /dev/mmcblk0p0 ok!
DiskAddPart : register /dev/mmcblk0p1 ok!
DiskAddPart : register /dev/mmcblk0p2 ok!
OsMountRootfs end ...
g_mmz_start=0x88000000, g_mmz_size=0x180
mmz param= anonymous,0,0x88000000,384M
<6>Hisilicon Media Memory Zone Manager
Load hifb.ko OK!
[VERSION]:Hi3881V100R001C00SPC020 2020-07-16 23:15:00
oam_main_init SUCCESSFULLY!
wal_customize_init SUCCESSFULLY!
oal_main_init SUCCESSFULLY
frw_main_init SUCCESSFULLY!
hi_wifi_plat_init SUCCESSFULLY
sdio probe:pull up power on gpio
hcc_hmac_init SUCCESSFULLY
uhub_attach (uhub0): 1 port with 1 removable, self powered
plat_firmware_init SUCCESSFULLY
Device is Ready!
wlan_pm_open SUCCESSFULLY!!
hmac_main_init SUCCESSULLY
get rates from device
wal_main_init SUCCESSFULLY
hi_wifi_host_init SUCCESSFULLY
Hi3881 DRV insmod SUCCESSFULLY!
[ERR][HDF:E/HDF_LOG_TAG]HdfWifiDriverInit:init chip 0 success!
sdk init end
cat log shell end
[Init] ****/****/****/****/OpenHarmony/****/****/3/OpenHarmony 1.0/debug
[Init] DoMount, failed for vfat /dev/mmcblk0 /sdcard rw,umask=000, err -1.
[ERR]Failed to find block driver /dev/mmcblk1
[Init] DoMount, failed for vfat /dev/mmcblk1 /sdcard rw,umask=000, err -1.
[Init] start service shell succeed, pid 3.
OHOS # [Init] start service apphilogcat succeed, pid 4.
[Init] start service foundation succeed, pid 5.
01-01 00:00:10.500 5 29 I 01800/Samgr: Initialize Registry!
01-01 00:00:10.515 5 29 I 00000/(null): Init pms service success
01-01 00:00:10.525 5 29 I 00000/(null): Init ipcAuth feature success
01-01 00:00:10.530 5 29 I 00000/(null): Init pms inner feature success
01-01 00:00:10.530 5 29 I 00000/(null): Init pms lite feature success
01-01 00:00:10.553 5 29 I 01300/abilityms: AbilityManagerService::Init(43): ams start result is successfully
01-01 00:00:10.554 5 29 I 01300/abilityms: AbilityMgrFeature::Init(70): ams feature init success
01-01 00:00:10.554 5 29 I 01300/abilityms: AbilityInnerFeature::Init(60): ams inner feature init success
01-01 00:00:10.584 5 29 D 00000/(null): BundleMS start success
01-01 00:00:10.584 5 29 D 00000/(null): BundleMS inner feature start success
01-01 00:00:10.584 5 29 D 00000/(null): BundleMS feature start success
01-01 00:00:10.616 5 29 D 00000/(null): [DMSLITE][Init:86][dms service start success]
01-01 00:00:10.619 5 29 I 01800/Samgr: Bootstrap core services(count:5).
01-01 00:00:10.626 5 29 I 01800/Samgr: Init service:samgr TaskPool:0x2000f8e0
[UnRegisteDeathCallback : 960]Wrong cbId:4294967295.
01-01 00:00:10.626 5 29 I 01800/Samgr: Init service:permissionms TaskPool:0x2000f930
[UnRegisteDeathCallback : 960]01-01 00:00:10.626 5 29 I 01800/Samgr: Init service:abilityms TaskPool:0x2000f950
Wrong cbId:4294967295.
[UnRegisteDeathCallback : 960]Wrong cbId:4294967295.
01-01 00:00:10.666 5 36 D 01800/Samgr: RegisterRemoteFeatures<bundlems, BmsInnerFeature> ret:0
01-01 00:00:10.666 5 36 D 01800/Samgr: RegisterIdentity <abilityms, AmsFeature> pid<5> <36, 1>
01-01 00:00:10.666 5 36 D 01800/Samgr: RegisterRemoteFeatures<abilityms, AmsFeature> ret:0
01-01 00:00:10.666 5 36 D 01800/Samgr: RegisterIdentity <abilityms, AmsInnerFeature> pid<5> <36, 2>
01-01 00:00:10.666 5 36 D 01800/Samgr: RegisterRemoteFeatures<abilityms, AmsInnerFeature> ret:0
01-01 00:00:10.666 5 36 D 01800/Samgr: RegisterIdentity <bundlems, BmsFeature> pid<5> <36, 3>
01-01 00:00:10.666 5 36 D 01800/Samgr: RegisterRemoteFeatures<bundlems, BmsFeature> ret:0
[DISCOVERY] InitLocalDeviceInfo ok
01-01 00:00:10.666 5 36 D 01800/Samgr: RegisterIdentity <permissionms, PmsFeature> pid<5> <36, 4>
01-01 00:00:10.666 5 36 D 01800/Samgr: RegisterRemoteFeatures<permissionms, PmsFeature> ret:0[DISCOVERY] CoapReadHandle coin select begin
[AUTH] StartBus StartListener fail
[DISCOVERY] InitService BusManager(1) fail
[DISCOVERY] InitService ok
[DISCOVERY] PublishCallback publishId=1, result=0
01-01 00:00:10.666 5 36 I 01800/Samgr: Register endpoint<ipc receive> and iunknown finished! remain<0> iunknown!
01-01 00:00:10.768 5 34 D 00000/(null): [DMSLITE][RegisterTcpCallback:85][Register failed, errCode = -1]
01-01 00:00:10.768 5 34 I 00000/(null): [DMSLITE][OnPublishSuccess:115][dms service publish success]
01-01 00:00:10.768 5 34 I 01800/Samgr: Init service dtbschedsrv <time: 153ms> success!
01-01 00:00:10.768 5 34 I 01800/Samgr: Initialized all core system services!
01-01 00:00:10.768 5 34 I 01800/Samgr: Goto next boot step failed! errno:-9
[Init] start service bundle_daemon succeed, pid 6.
01-01 00:00:11.233 6 39 E 01100/bundle_deamon: BundleDaemon::Init(52): register default feature api success[UnRegisteDeathCallback : 960]Wrong cbId:4294967295.
[UnRegisteDeathCallback : 960]Wrong cbId:4294967295.
01-01 00:00:11.233 6 39 I 01800/Samgr: Init service:bundle_daemon TaskPool:0x236bfc10
01-01 00:00:11.233 6 40 I 01800/Samgr: Initialize Registry!
01-01 00:00:11.234 5 30 I 01800/Samgr: Register Endpoint<6, 41, 0>
01-01 00:00:11.234 5 30 D 01800/Samgr: Register Feature<bundle_daemon, (null)> pid<6>, id<41, 0> ret:0
01-01 00:00:11.235 6 41 D 01800/Samgr: RegisterRemoteFeatures<bundle_daemon, (null)> ret:0
01-01 00:00:11.235 6 41 I 01800/Samgr: Register endpoint<ipc client> and iunknown finished! remain<0> iunknown!
01-01 00:00:11.235 5 30 D 01800/Samgr: Register Feature<bundle_daemon, (null)> pid<6>, id<41, 0> ret:0
01-01 00:00:11.235 6 40 I 01800/Samgr: Register server sa<bundle_daemon, (null)> id<4294967295, 0> retry:1 ret:0!
01-01 00:00:11.235 6 40 I 01800/Samgr: Init service bundle_daemon <time: 2ms> success!
01-01 00:00:11.235 6 40 I 01800/Samgr: Initialized all core system services!
01-01 00:00:11.235 6 40 I 01800/Samgr: Goto next boot step failed! errno:-9
01-01 00:00:11.333 5 33 I 01800/Samgr: Create proxy[0x1fe11890]<bundle_daemon, (null), 41, 0>
01-01 00:00:11.333 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 8
01-01 00:00:11.356 5 33 I 00000/(null): current mode is 0!
[ERR]Unsupported API sysconf
01-01 00:00:11.377 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:140] :sign head: size: 8409, blockNum:0x2
01-01 00:00:11.393 5 33 E 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:168] :find block type: 20000002
write file switch /storage/data/log/hilog1.txt
01-01 00:00:11.393 5 33 E 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:168] :find block type: 20000000
01-01 00:00:11.396 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:189] :type: 536870912, len: 3409, offset: 4968 signoffset: 43408
01-01 00:00:11.404 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:220] :buf begin
01-01 00:00:11.482 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:909] :load root ca success
01-01 00:00:11.490 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:613] :ParseSignedData 0
01-01 00:00:11.490 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1300] :Parse pkcs#7 signed data success
01-01 00:00:11.490 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:793] :To filter one signer's cert
01-01 00:00:11.493 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:797] :Found signer's low level cert
01-01 00:00:11.493 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1083] :pkcs7 parse message sucess
01-01 00:00:11.493 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1098] :get cert Type : 2
01-01 00:00:11.493 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1022] :signer : 1
01-01 00:00:11.822 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:996] :Verify signers cert chain root cert success
01-01 00:00:11.822 5 33 D 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1035] :Verify : 0
01-01 00:00:11.847 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify_hap.c:53] :alg: 6 wholelen: 22
01-01 00:00:11.848 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:189] :type: 536870914, len: 4944, offset: 24 signoffset: 43408
01-01 00:00:11.859 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:220] :buf begin
write file switch /storage/data/log/hilog2.txt
01-01 00:00:11.859 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify_hap.c:143] :signBuf 30 4944
01-01 00:00:11.860 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify_hap.c:332] :finish
01-01 00:00:11.860 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1026] :VerifyRawHash success
01-01 00:00:11.860 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:862] :get signer signature len : 70
01-01 00:00:11.860 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:291] :signer context hash equal with attr hash
01-01 00:00:11.937 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:892] :Verify signer signature success
01-01 00:00:11.953 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:545] :Parse signed data certs success
01-01 00:00:11.953 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:613] :ParseSignedData 0
01-01 00:00:11.953 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1300] :Parse pkcs#7 signed data success
01-01 00:00:11.953 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:793] :To filter one signer's cert
01-01 00:00:11.953 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:797] :Found signer's low level cert
01-01 00:00:11.953 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:489] :pkcs7 parse message sucess
01-01 00:00:11.953 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1022] :signer : 1
[Init] start service appspawn succeed, pid 7.
01-01 00:00:12.236 7 43 I 00000/(null): [appspawn] get service name appspawn.
[UnRegisteDeathCallback : 960]Wrong cbId:4294967295.
[UnRegisteDeathCallback : 960]Wrong cbId:4294967295.
01-01 00:00:12.236 7 44 I 01800/Samgr: Initialize Registry!
01-01 00:00:12.237 7 43 I 00000/(null): [appspawn] HOS_SystemInit is called!
01-01 00:00:12.237 7 44 I 00000/(null): [appspawn] get service name appspawn.
01-01 00:00:12.237 7 44 I 01800/Samgr: Init service appspawn <time: 1ms> success!
write file switch /storage/data/log/hilog1.txt
01-01 00:00:12.237 7 44 I 01800/Samgr: Initialized all core system services!
01-01 00:00:12.237 7 44 I 00000/(null): [appspawn] get service name appspawn.
01-01 00:00:12.237 7 44 I 01800/Samgr: Goto next boot step failed! errno:-9
01-01 00:00:12.237 7 43 I 00000/(null): [appspawn] main, entering wait.
01-01 00:00:12.237 5 30 I 01800/Samgr: Register Endpoint<7, 45, 0>
01-01 00:00:12.238 5 30 D 01800/Samgr: Register Feature<appspawn, (null)> pid<7>, id<45, 0> ret:0
01-01 00:00:12.238 7 45 D 01800/Samgr: RegisterRemoteFeatures<appspawn, (null)> ret:0
01-01 00:00:12.238 7 45 I 01800/Samgr: Register endpoint<ipc client> and iunknown finished! remain<0> iunknown!
01-01 00:00:12.274 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:996] :Verify signers cert chain root cert success
01-01 00:00:12.274 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:979] :find crl
01-01 00:00:12.274 5 33 D 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1035] :Verify : 0
01-01 00:00:12.274 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:495] :Verify certs success
01-01 00:00:12.275 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:381] :profile source name : huawei system apps
01-01 00:00:12.275 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:862] :get signer signature len : 70
01-01 00:00:12.275 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:291] :signer context hash equal with attr hash
01-01 00:00:12.353 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:993] :verify prof get content success
01-01 00:00:12.354 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:596] :GetEcPk *len 65
01-01 00:00:12.354 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:827] :cert consistent
01-01 00:00:12.354 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:895] :check app sign cert ret : 0
write file switch /storage/data/log/hilog2.txt
01-01 00:00:12.359 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1189] :file len: 52470
01-01 00:00:12.359 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1217] :free verify rst data
01-01 00:00:12.366 5 33 I 00000/(null): create ZipFile instance
01-01 00:00:12.366 5 33 I 00000/(null): open: /system/internal/setting.hap
01-01 00:00:12.384 5 33 I 00000/(null): parse 8 central entries from /system/internal/setting.hap
01-01 00:00:12.384 5 33 I 00000/(null): extract file config.json
01-01 00:00:12.384 5 33 I 00000/(null): get entry by name: config.json
01-01 00:00:12.384 5 33 D 00000/(null): get entry successed
01-01 00:00:12.479 6 40 I 00000/(null): create ZipFile instance
01-01 00:00:12.479 6 40 I 00000/(null): open: /system/internal/setting.hap
01-01 00:00:12.499 6 40 I 00000/(null): parse 8 central entries from /system/internal/setting.hap
01-01 00:00:12.506 6 40 I 00000/(null): extract file config.json
01-01 00:00:12.506 6 40 I 00000/(null): get entry by name: config.json
01-01 00:00:12.512 6 40 I 00000/(null): seek to entry start 0x000001f3
01-01 00:00:12.564 6 40 D 00000/(null): get entry successed
01-01 00:00:12.571 6 40 D 00000/(null): get entry successed
01-01 00:00:12.573 6 40 I 00000/(null): unzip with inflated success
01-01 00:00:12.578 6 40 D 00000/(null): get entry successed
01-01 00:00:12.579 6 40 I 00000/(null): unzip with inflated success
01-01 00:00:12.583 6 40 D 00000/(null): get entry successed
01-01 00:00:12.593 6 40 I 00000/(null): extract file res/assets/resources/rawfile/wpa_supplicant.conf
01-01 00:00:12.603 6 40 I 00000/(null): get entry by name: res/drawable/setting.png
01-01 00:00:12.604 6 40 I 00000/(null): unzip with inflated
01-01 00:00:12.604 6 40 I 00000/(null): seek to entry start 0x00007e2d
01-01 00:00:12.605 6 40 I 00000/(null): unzip with inflated success
01-01 00:00:12.608 6 40 I 00000/(null): close: /system/internal/setting.hap
01-01 00:00:12.622 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 1
01-01 00:00:12.625 5 32 D 01300/abilityms: AbilityMgrHandler::TerminateApp(233): start
write file switch /storage/data/log/hilog1.txt
01-01 00:00:12.626 5 32 D 01300/abilityms: AppTerminateTask::Execute(29): start
01-01 00:00:12.628 5 32 I 01300/abilityms: AppManager::TerminateAppProcess(66): app record is not find
01-01 00:00:12.686 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 4
01-01 00:00:12.737 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:613] :ParseSignedData 0
01-01 00:00:12.737 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1300] :Parse pkcs#7 signed data success
01-01 00:00:12.737 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:793] :To filter one signer's cert
01-01 00:00:12.737 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:797] :Found signer's low level cert
01-01 00:00:12.737 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1083] :pkcs7 parse message sucess
01-01 00:00:12.737 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1098] :get cert Type : 2
01-01 00:00:12.737 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1022] :signer : 1
01-01 00:00:13.045 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:996] :Verify signers cert chain root cert success
01-01 00:00:13.045 5 33 D 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1035] :Verify : 0
01-01 00:00:13.058 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:189] :type: 536870914, len: 5284, offset: 24 signoffset: 31362
01-01 00:00:13.076 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:220] :buf begin
01-01 00:00:13.076 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify_hap.c:143] :signBuf 30 5284
01-01 00:00:13.077 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify_hap.c:332] :finish
01-01 00:00:13.077 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1026] :VerifyRawHash success
write file switch /storage/data/log/hilog2.txt
01-01 00:00:13.077 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:862] :get signer signature len : 71
01-01 00:00:13.077 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:291] :signer context hash equal with attr hash
01-01 00:00:13.154 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:892] :Verify signer signature success
01-01 00:00:13.165 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:545] :Parse signed data certs success
01-01 00:00:13.166 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:613] :ParseSignedData 0
01-01 00:00:13.166 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1300] :Parse pkcs#7 signed data success
01-01 00:00:13.166 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:793] :To filter one signer's cert
01-01 00:00:13.166 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:797] :Found signer's low level cert
01-01 00:00:13.166 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:489] :pkcs7 parse message sucess
01-01 00:00:13.166 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1022] :signer : 1
[Init] start service media_server succeed, pid 8.
01-01 00:00:13.495 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:996] :Verify signers cert chain root cert success
01-01 00:00:13.496 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:979] :find crl
01-01 00:00:13.496 5 33 D 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1035] :Verify : 0
01-01 00:00:13.496 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:495] :Verify certs success
Media server initialize succeed.
01-01 00:00:13.496 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:381] :profile source name : huawei system apps
01-01 00:00:13.577 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:827] :cert consistent
write file switch /storage/data/log/hilog1.txt
01-01 00:00:13.583 5 33 I 00000/(null): create ZipFile instance
01-01 00:00:13.583 5 33 I 00000/(null): open: /system/internal/launcher.hap
01-01 00:00:13.591 5 33 I 00000/(null): parse 4 central entries from /system/internal/launcher.hap
01-01 00:00:13.591 5 33 D 00000/(null): get entry successed
01-01 00:00:13.598 5 33 I 00000/(null): close: /system/internal/launcher.hap
01-01 00:00:13.611 6 40 I 00000/(null): create ZipFile instance
01-01 00:00:13.611 6 40 I 00000/(null): open: /system/internal/launcher.hap
01-01 00:00:13.619 6 40 I 00000/(null): parse 4 central entries from /system/internal/launcher.hap
01-01 00:00:13.637 6 40 I 00000/(null): extract file config.json
01-01 00:00:13.637 6 40 D 00000/(null): get entry successed
01-01 00:00:13.649 6 40 I 00000/(null): get entry by name: liblauncher.so
01-01 00:00:13.668 6 40 I 00000/(null): unzip with inflated success
01-01 00:00:13.692 6 40 I 00000/(null): get entry by name: res/drawable/weather.png
01-01 00:00:13.695 6 40 I 00000/(null): unzip with inflated
01-01 00:00:13.695 6 40 I 00000/(null): seek to entry start 0x0000740a
01-01 00:00:13.698 6 40 I 00000/(null): close: /system/internal/launcher.hap
01-01 00:00:13.699 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 1
01-01 00:00:13.699 5 32 D 01300/abilityms: AbilityMgrHandler::TerminateApp(233): start
01-01 00:00:13.699 5 32 D 01300/abilityms: AppTerminateTask::Execute(29): start
01-01 00:00:13.699 5 32 I 01300/abilityms: AppManager::TerminateAppProcess(66): app record is not find
01-01 00:00:13.699 5 32 E 01300/abilityms: AbilityMissionStack::RemoveMissionRecord(68): missionRecord is null
01-01 00:00:13.699 5 32 E 01300/abilityms: AbilityStackManager::GetTopPageAbility(69): topMissionStack is nullptr
01-01 00:00:13.705 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 3
01-01 00:00:13.717 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 4
01-01 00:00:13.726 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 4
write file switch /storage/data/log/hilog2.txt
01-01 00:00:13.731 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 1
01-01 00:00:13.740 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 1
01-01 00:00:13.760 5 33 I 00000/(null): current mode is 0!
01-01 00:00:13.768 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:613] :ParseSignedData 0
01-01 00:00:13.769 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1300] :Parse pkcs#7 signed data success
01-01 00:00:13.769 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:793] :To filter one signer's cert
01-01 00:00:13.769 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:797] :Found signer's low level cert
01-01 00:00:13.769 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1083] :pkcs7 parse message sucess
01-01 00:00:13.769 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1098] :get cert Type : 2
01-01 00:00:13.769 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1022] :signer : 1
01-01 00:00:14.077 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:996] :Verify signers cert chain root cert success
01-01 00:00:14.077 5 33 D 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1035] :Verify : 0
01-01 00:00:14.091 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify_hap.c:72] :content: 22, 0
01-01 00:00:14.091 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:189] :type: 536870914, len: 4940, offset: 24 signoffset: 46421
01-01 00:00:14.107 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:220] :buf begin
01-01 00:00:14.107 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify_hap.c:143] :signBuf 30 4940
01-01 00:00:14.108 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify_hap.c:332] :finish
write file switch /storage/data/log/hilog1.txt
01-01 00:00:14.108 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1026] :VerifyRawHash success
01-01 00:00:14.108 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:862] :get signer signature len : 71
01-01 00:00:14.108 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:291] :signer context hash equal with attr hash
01-01 00:00:14.186 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:892] :Verify signer signature success
01-01 00:00:14.201 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:545] :Parse signed data certs success
01-01 00:00:14.201 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:613] :ParseSignedData 0
01-01 00:00:14.201 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1300] :Parse pkcs#7 signed data success
01-01 00:00:14.201 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:793] :To filter one signer's cert
01-01 00:00:14.201 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:797] :Found signer's low level cert
01-01 00:00:14.201 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:489] :pkcs7 parse message sucess
01-01 00:00:14.201 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1022] :signer : 1
[Init] start service wms_server succeed, pid 9.
[DISPLAY I/] LayerInitialize: layer initialize success
01-01 00:00:14.534 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:996] :Verify signers cert chain root cert success
01-01 00:00:14.534 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:979] :find crl
01-01 00:00:14.534 5 33 D 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:1035] :Verify : 0
01-01 00:00:14.534 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:495] :Verify certs success
01-01 00:00:14.534 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:381] :profile source name : huawei system apps
write file switch /storage/data/log/hilog2.txt
01-01 00:00:14.534 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/mbedtls_pkcs7.c:862] :get signer signature len : 71
01-01 00:00:14.534 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:291] :signer context hash equal with attr hash
01-01 00:00:14.615 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:993] :verify prof get content success
01-01 00:00:14.615 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:827] :cert consistent
01-01 00:00:14.615 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:850] :dev cert consistent
01-01 00:00:14.615 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:895] :check app sign cert ret : 0
01-01 00:00:14.615 5 33 I 00000/(null): [../../base/security/frameworks/app_verify/src/app_verify.c:1007] :verfiy app source success
01-01 00:00:14.633 5 33 I 00000/(null): parse 14 central entries from /system/internal/camera.hap
01-01 00:00:14.633 5 33 I 00000/(null): extract file config.json
01-01 00:00:14.633 5 33 I 00000/(null): get entry by name: config.json
01-01 00:00:14.633 5 33 D 00000/(null): get entry successed
01-01 00:00:14.636 5 33 I 00000/(null): close: /system/internal/camera.hap
01-01 00:00:14.650 6 40 I 00000/(null): open: /system/internal/camera.hap
01-01 00:00:14.679 6 40 I 00000/(null): seek to entry start 0x0000002d
01-01 00:00:14.681 6 40 I 00000/(null): unzip with inflated success
01-01 00:00:14.708 6 40 I 00000/(null): seek to entry start 0x00004f31
01-01 00:00:14.720 6 40 I 00000/(null): unzip with inflated success
01-01 00:00:14.729 6 40 D 00000/(null): get entry successed
01-01 00:00:14.735 6 40 D 00000/(null): get entry successed
01-01 00:00:14.738 6 40 D 00000/(null): get entry successed
01-01 00:00:14.740 6 40 I 00000/(null): unzip with inflated success
01-01 00:00:14.756 6 40 I 00000/(null): get entry by name: res/image/camera/ic_camera_record_shutter.png
01-01 00:00:14.761 6 40 I 00000/(null): get entry by name: res/image/camera/ic_camera_record_stop.png
write file switch /storage/data/log/hilog1.txt
01-01 00:00:14.769 6 40 I 00000/(null): seek to entry start 0x00009f4e
01-01 00:00:14.792 6 40 I 00000/(null): get entry by name: res/image/camera/ic_timer.png
01-01 00:00:14.792 6 40 D 00000/(null): get entry successed
01-01 00:00:14.793 6 40 I 00000/(null): unzip with inflated
01-01 00:00:14.793 6 40 I 00000/(null): seek to entry start 0x0000b253
01-01 00:00:14.796 6 40 I 00000/(null): unzip with inflated success
01-01 00:00:14.802 6 40 I 00000/(null): close: /system/internal/camera.hap
01-01 00:00:14.803 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 1
01-01 00:00:14.803 5 32 D 01300/abilityms: AbilityMgrHandler::TerminateApp(233): start
01-01 00:00:14.803 5 32 D 01300/abilityms: AppTerminateTask::Execute(29): start
01-01 00:00:14.803 5 32 I 01300/abilityms: AppManager::TerminateAppProcess(66): app record is not find
01-01 00:00:14.803 5 32 E 01300/abilityms: AbilityMissionStack::RemoveMissionRecord(68): missionRecord is null
01-01 00:00:14.803 5 32 E 01300/abilityms: AbilityStackManager::GetTopPageAbility(69): topMissionStack is nullptr
01-01 00:00:14.812 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 3
01-01 00:00:14.823 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 4
01-01 00:00:14.830 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 2
01-01 00:00:14.841 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 4
01-01 00:00:14.849 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 1
01-01 00:00:14.855 6 40 I 01100/bundle_deamon: BundleDaemon::Invoke(102): bundle_daemon invoke start 1
01-01 00:00:14.869 5 32 D 01300/abilityms: AbilityMgrHandler::OnServiceInited(122): start
01-01 00:00:14.869 5 32 I 01300/abilityms: WMSClient::WaitUntilWmsReady(35): wait for window manager service start
[Init] main, entering wait.
[DISPLAY I/] HdmiStart: start hdmi success
[DISPLAY E/] CheckHdmiConnect: HI_MPI_HDMI_GetSinkCapability failure, ret = 0xa0288005!
[DISPLAY I/] LcdIntfInit: hdmi disconnected
[DISPLAY I/] StartVoLayer: start vo layer success
[DISPLAY I/] PrintLayerInfo: layerInfo:
[DISPLAY I/] PrintLayerInfo: type = 0
[DISPLAY I/] PrintLayerInfo: width = 960
[DISPLAY I/] PrintLayerInfo: height = 480
[DISPLAY I/] PrintLayerInfo: bpp = 16
[DISPLAY I/] PrintLayerInfo: pixFormat = 9
[DISPLAY I/] OpenGraphicLayer: open graphic layer success, layerId = 0!
[DISPLAY I/] GfxInitialize: gfx initialize success
[UnRegisteDeathCallback : 960]Wrong cbId:4294967295.
[UnRegisteDeathCallback : 960]Wrong cbId:4294967295.
01-01 00:00:17.352 9 48 I 01800/Samgr: Bootstrap core services(count:1).
GetInputInterface: enter
01-01 00:00:17.354 9 50 I 01800/Samgr: Initialized all core system services!
GetInputInterface: exit succ
OpenInputDevice: open dev1 succ
RegisterReportCallback: create monitor thread succ, index = 1
RegisterReportCallback: device1 register callback succ, callbackNum = 1
OpenInputDevice: dev2 does not exist
01-01 00:00:17.355 5 32 D 01300/abilityms: AbilityStackManager::GeneratePageAbility(35): launcher jumps to default or default jumps to launcher
write file switch /storage/data/log/hilog2.txt
01-01 00:00:17.355 5 32 D 01300/abilityms: AbilityMissionRecord::AbilityMissionRecord(29): Constuctor
01-01 00:00:17.370 5 32 D 01300/abilityms: PageAbilityRecord::PageAbilityRecord(42): Constructor
01-01 00:00:17.370 5 32 D 01300/abilityms: AbilityStartTask::Execute(73): topAbility is nullptr or not active
01-01 00:00:17.379 5 32 D 01300/abilityms: AppSpawnClient::SpawnProcess(68): start
01-01 00:00:17.379 5 32 I 01800/Samgr: Create proxy[0x1fe11dd0]<appspawn, (null), 45, 0>
01-01 00:00:17.380 7 44 I 00000/(null): [appspawn] msg<com.huawei.launcher,,73014444033,101,101>
01-01 00:00:17.386 7 44 I 00000/(null): [appspawn] invoke, reply pid 10.
01-01 00:00:17.386 5 32 D 01300/abilityms: AppManager::StartAppProcess(42): start app name:com.huawei.launcher, token: 73014444033
01-01 00:00:17.867 10 54 I 00000/(null): AbilityThread::ThreadMain enter
01-01 00:00:17.871 10 54 I 01800/Samgr: Initialize Registry!
01-01 00:00:17.873 5 30 D 01800/Samgr: Find Feature<abilityms, AmsFeature> id<36, 1> ret:0
01-01 00:00:17.873 10 54 I 01800/Samgr: Create remote sa proxy[0x22929e40]<abilityms, AmsFeature> id<36,1>!
01-01 00:00:17.873 10 54 I 00000/(null): AbilityThread::ThreadMain start loop
01-01 00:00:17.873 5 32 I 01300/abilityms: AbilityMgrFeature::Invoke(84): ams invoke called
01-01 00:00:17.886 5 32 D 01300/abilityms: AbilityAttachTask::Execute(33): start
01-01 00:00:17.886 5 32 D 01300/abilityms: AbilityThreadClient::Initialize(62): token(73014444033) bundleName(com.huawei.launcher) success
01-01 00:00:17.886 5 32 I 00000/(null): Perm file not exists[pkgName: com.huawei.launcher]
[DISPLAY I/] GfxInitialize: gfx initialize success
01-01 00:00:17.897 10 54 I 00000/(null): Start app init
01-01 00:00:17.912 10 54 I 00000/(null): RegisterAbility MainAbility
01-01 00:00:17.912 10 54 I 00000/(null): RegisterAbilitySlice MainAbilitySlice
01-01 00:00:17.916 10 54 I 00000/(null): Set env ret: 0, App init end
01-01 00:00:17.920 10 54 I 00000/(null): perform transact ability state to [3]
01-01 00:00:17.920 10 54 I 00000/(null): Create ability success [MainAbility]
01-01 00:00:17.920 10 54 I 00000/(null): Hal and UI init
write file switch /storage/data/log/hilog1.txt
01-01 00:00:17.968 10 54 I 01800/Samgr: Bootstrap core services(count:0).
01-01 00:00:17.968 10 54 I 01800/Samgr: Initialized all core system services!
01-01 00:00:17.968 10 54 I 01800/Samgr: Goto next boot step failed! errno:-9
01-01 00:00:17.969 5 30 D 01800/Samgr: Judge Auth<WMS, (null)> ret:0
01-01 00:00:17.969 5 30 D 01800/Samgr: Find Feature<WMS, (null)> id<49, 0> ret:0
01-01 00:00:17.969 10 54 I 01800/Samgr: Create remote sa proxy[0x2293ad50]<WMS, (null)> id<49,0>!
01-01 00:00:18.441 10 54 I 00000/(null): Create UITaskPost thread
01-01 00:00:18.441 10 54 I 00000/(null): Ability Init
01-01 00:00:18.441 10 56 I 00000/(null): start UITaskPost loop
01-01 00:00:18.446 10 54 I 00000/(null): Ability OnStart
01-01 00:00:18.446 10 54 I 00000/(null): AbilitySlice Init
01-01 00:00:18.446 10 54 I 00000/(null): AbilitySlice OnStart
01-01 00:00:18.524 10 54 I 00000/(null): [GetFeatureApi S:permissionms F:PmsFeature]: BEGIN
01-01 00:00:18.524 10 54 I 00000/(null): [QueryInterface CLIENT_PROXY_VER S:permissionms, F:PmsFeature]: is 0x22439da0
01-01 00:00:18.529 5 31 I 00000/(null): Enter ID_CHECK, [callerPid: 10][callerUid: 101]
01-01 00:00:18.529 10 54 I 00000/(null): [Release api S:permissionms, F:PmsFeature]: is 0x22439da0 ref:1
[DISPLAY I/] GrallocInitialize: gralloc initialize success
01-01 00:00:18.530 5 30 D 01800/Samgr: Judge Auth<bundlems, BmsFeature> ret:0
01-01 00:00:18.530 5 30 D 01800/Samgr: Find Feature<bundlems, BmsFeature> id<36, 3> ret:0
01-01 00:00:18.530 10 54 I 01800/Samgr: Create remote sa proxy[0x22439e40]<bundlems, BmsFeature> id<36,3>!
01-01 00:00:18.530 10 54 I 00000/(null): [GetFeatureApi S:permissionms F:PmsFeature]: BEGIN
01-01 00:00:18.530 10 54 I 00000/(null): [QueryInterface CLIENT_PROXY_VER S:permissionms, F:PmsFeature]: is 0x22439da0
01-01 00:00:18.530 5 31 I 00000/(null): Enter ID_CHECK, [callerPid: 10][callerUid: 101]
01-01 00:00:18.530 10 54 I 00000/(null): [Release api S:permissionms, F:PmsFeature]: is 0x22439da0 ref:1
[DISPLAY I/] GrallocInitialize: gralloc initialize success
01-01 00:00:19.156 10 54 I 00000/(null): Ability OnActive
01-01 00:00:19.156 10 54 I 00000/(null): AbilitySlice OnActive
01-01 00:00:19.156 10 54 I 00000/(null): perform transact ability state done [3]
write file switch /storage/data/log/hilog2.txt
01-01 00:00:19.157 5 32 I 01300/abilityms: AbilityMgrFeature::Invoke(84): ams invoke called
01-01 00:00:19.157 5 32 D 01300/abilityms: AbilityMgrHandler::AbilityTransaction(219): start
01-01 00:00:19.157 5 32 D 01300/abilityms: AbilityWorker::AbilityTransaction(85): ability token(73014444032), state(3)
01-01 00:00:19.157 5 32 D 01300/abilityms: AbilityActivateTask::Execute(26): start
OHOS #
OHOS #
OHOS #
OHOS #
OHOS #
OHOS #
OHOS # pwd
/
OHOS #
OHOS #
OHOS #
OHOS # ls
Directory /:
drwxr-xr-x 0 u:0 g:0 dev
dr-xr-xr-x 0 u:0 g:0 proc
drwxrwxrwx 0 u:0 g:0 sdcard
drwxrwxrwx 0 u:0 g:0 storage
drwxrwxrwx 0 u:0 g:0 userdata
drwxrwxrwx 0 u:0 g:0 bin
drwxrwxrwx 0 u:0 g:0 etc
drwxrwxrwx 0 u:0 g:0 lib
drwxrwxrwx 0 u:0 g:0 system
drwxrwxrwx 0 u:0 g:0 usr
drwxrwxrwx 0 u:0 g:0 vendor
OHOS #
OHOS #
OHOS # cd userdata
OHOS #
OHOS #
OHOS # ls
Directory /userdata:
drwxrwxrwx 0 u:0 g:0 12345678
-rwxrwxrwx 0 u:0 g:0 03051716
-rwxrwxrwx 0 u:0 g:0 loveu99
OHOS #
OHOS #
[END] 2021/3/5 17:25:00
5、HiTool的刷机LOG:
Platform Version: 5.2.7
HiBurn Version: 5.2.0
HiSilicon Technologies Co., Ltd. All rights reserved. (C) 2011-2019
Platform Version: 5.2.7
HiBurn Version: 5.2.0
HiSilicon Technologies Co., Ltd. All rights reserved. (C) 2011-2019
# ---- 36%
# ---- 100%
Boot download completed!
start download process.
Boot started successfully!
Send command: getinfo ddrfree
[EOT](OK)
Send command: mw.b 0x81000000 0xFF 0x4f0000
[EOT](OK)
Send command: Downloading File : OHOS_Image.bin
[Download File by usb]
file = Z:\hi3516dv300\out\ipcamera_hi3516dv300\OHOS_Image.bin
address = 0x81000000
fileLength = 5177028 B
##
done
Send command: mmc write 0x0 0x81000000 0x800 0x2780
MMC write: dev # 0, block # 2048, count 10112 ... 10112 blocks written: OK
37.74 MB/s
[EOT](OK)
Partition OHOS_Image burned successfully!
Send command: mw.b 0x81000000 0xFF 0xe01c00
[EOT](OK)
Send command: Downloading File : rootfs.img
[Download File by usb]
file = Z:\hi3516dv300\out\ipcamera_hi3516dv300\rootfs.img
address = 0x81000000
fileLength = 14687232 B
####
done
Send command: mmc write 0x0 0x81000000 0x5000 0x700e
MMC write: dev # 0, block # 20480, count 28686 ... 28686 blocks written: OK
37.31 MB/s
[EOT](OK)
Partition rootfs burned successfully!
Send command: mw.b 0x81000000 0xFF 0x3200000
[EOT](OK)
Send command: Downloading File : userfs.img
[Download File by usb]
file = Z:\hi3516dv300\out\ipcamera_hi3516dv300\userfs.img
address = 0x81000000
fileLength = 52428800 B
#############
done
Send command: mmc write 0x0 0x81000000 0xc800 0x19000
MMC write: dev # 0, block # 51200, count 102400 ... 102400 blocks written: OK
37.22 MB/s
[EOT](OK)
Partition userfs burned successfully!
Partition burnt completed!
Send command: reset
reset success!
USB channels were closed successfully.

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








