msp432 读一个端口值
截至2020年2月10日的最新消息 (The latest scoop as of February 10, 2020)
The Huntress team recently learned that a person allegedly tied to the w0zniak account has been arrested in Atlanta. We received this information shortly after we released our blog and here are a few key updates:
女猎手团队最近获悉,据称与w0zniak帐户有关的一个人已在亚特兰大被捕 。 我们在发布博客后不久就收到了此信息,以下是一些重要更新:
Insider Threat: w0zniak was a disgruntled ex-employee of the MSP Based on the criminal complaint affidavit, w0zniak is likely the Torum handle belonging to Marquavious Britt, who worked for our victim MSP until he was “terminated for failure to complete tasks assigned to him”.
内部威胁:w0zniak是MSP的一名不满员工,根据刑事诉状 ,w0zniak可能是Marrumvious Britt的Torum把手,他曾为我们的受害者MSP工作,直到他“因未能完成指派给他的任务而被解雇” ”。

What’s especially interesting is the Vultr account sold by w0zniak belonged to Marquavious Britt and included the last four of Britt’s SSN in the password. Additionally, the Coinbase account that received payment for the MSP access was registered to Britt’s name, SSN, address, and date of birth. Sounds like:
尤其有趣的是w0zniak出售的Vultr帐户属于Marquavious Britt,并且密码中包括Britt的SSN的后四个。 此外,已收到用于MSP访问的付款的Coinbase帐户已注册为Britt的姓名,SSN,地址和出生日期。 听起来好像:
- w0zniak didn’t have the greatest online OPSEC w0zniak没有最好的在线OPSEC
- MSPs need to closely audit admin accounts after employees depart 员工离职后,MSP需要紧密审核管理员帐户

Some Dark Web hackers are not super thrilled with our effort
一些Dark Web黑客对我们的努力并不感到兴奋
Since our story was published, we’ve seen hackers warn each other about who they talk to and what they see. They are on high alert, knowing their shady deeds are being watched:
自从我们的故事发表以来,我们已经看到黑客相互警告他们所交谈的对象和所见内容。 他们处于高度戒备状态,知道他们的幕后行为正受到关注:
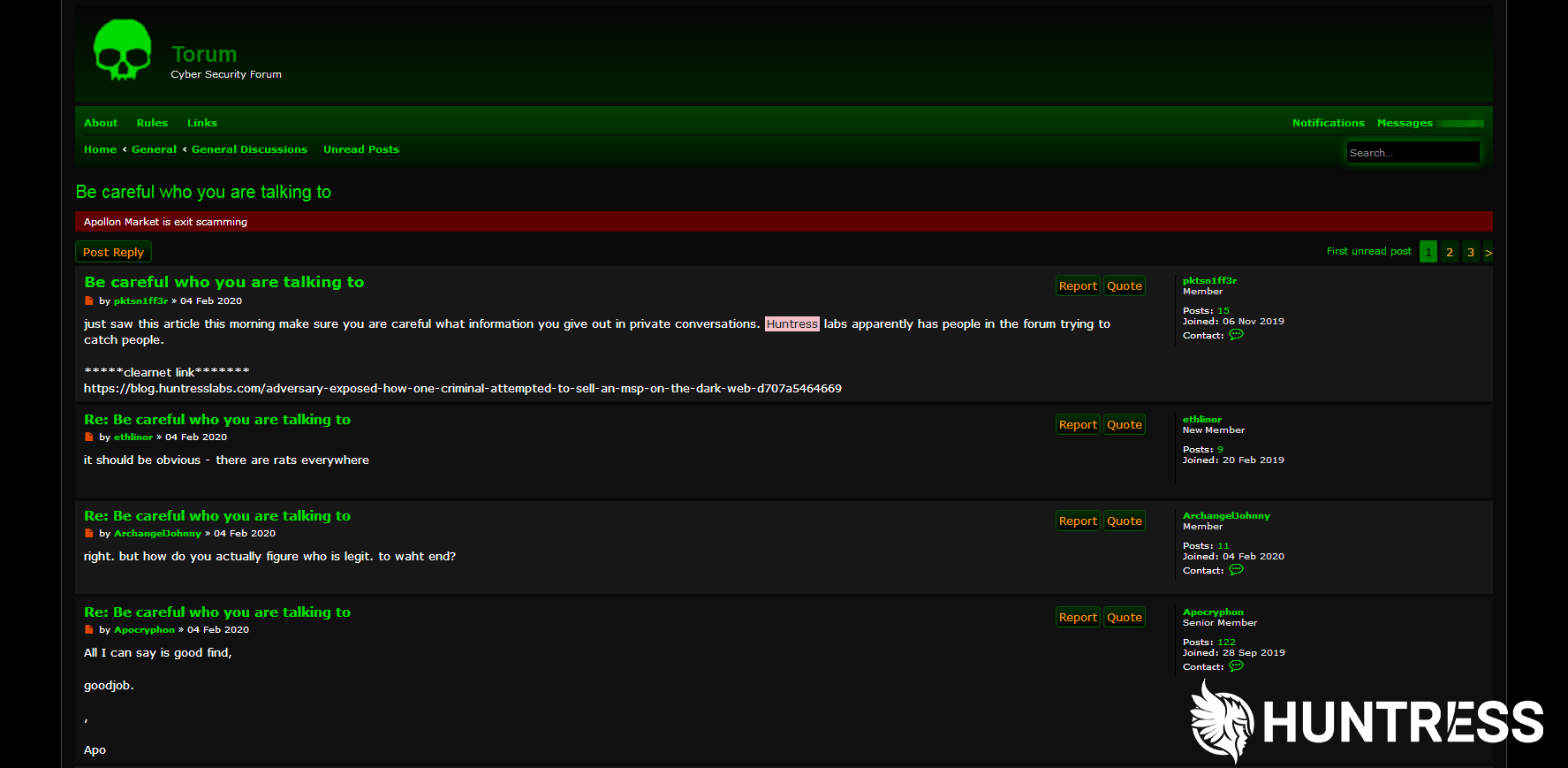

Security will always be a cat and mouse game, but that game doesn’t have to be checkers. Playing chess probably starts with an offensive approach to defense.
安全永远是猫和老鼠的游戏,但该游戏不必是跳棋。 下棋可能始于采取防御性的进攻方式。
If Britt is responsible, w0zniak is a man
如果布里特负责,w0zniak是一个男人
While we wrote this blog, we definitely had fun imagining our hacker as a woman. It was an interesting thought exercise that challenged us to remove our preconceived notions. However, not everyone agreed with our decision:
当我们撰写此博客时,将黑客想象成一个女人绝对很有趣。 这是一次有趣的思想练习,挑战了我们删除我们先入为主的观念。 但是,并非所有人都同意我们的决定:
At the end of the day, we are just relieved to see one more criminal is receiving their day in court. MSPs are increasingly vulnerable to hackers on the Dark Web. This blog was just another example of our commitment to protecting MSPs to keep them safe.
归根结底,看到另一名罪犯在法庭上受审,我们感到宽慰。 MSP越来越容易受到Dark Web上的黑客的攻击。 该博客只是我们致力于保护MSP以确保其安全的另一个示例。
2020年2月4日以来的原始帖子 (Original Post from February 4, 2020)
Think about all the things you can buy and do on the dark web.
Most of what you see on the dark web stems from the fact that it is powered by anonymity. While there is certainly an argument for freedom of expression that drives part of the dark web, most of what we see and hear are nefarious activities of hacktivists and a growing organized cybercrime underworld. But we often hear about the events after their criminal activity has already run its course.
您在暗网中看到的大部分内容都是由匿名支持的。 尽管肯定有言论自由的论点驱动了黑暗网络的一部分,但我们所看到和听到的大多数都是黑客主义者的邪恶活动和日益增长的有组织网络犯罪黑社会。 但是,我们经常听到有关其犯罪活动已经发生的事件。
In a rare encounter, we found ourselves directly interacting with one of these cybercriminals. Read on to see how our very own Kyle Hanslovan, Chris Bisnett, and John Ferrell took a deep dive into the dark web with a first-hand encounter with an attacker.
在一次罕见的相遇中,我们发现自己直接与其中一位网络犯罪分子互动。 请继续阅读以了解我们自己的凯尔·汉斯洛万 ( Kyle Hanslovan) , 克里斯 ·比斯奈特 ( Chris Bisnett )和约翰·费雷尔 ( John Ferrell )如何与攻击者进行第一手接触,从而深入研究了暗网。
当日销售 (The Sale of the Day)
Back in October, Datto identified a threat actor through their routine dark web monitoring practices. This cyber criminal, known by her Torum handle as “w0zniak”, was seen selling access to an MSP’s VPS control panel on the dark web for $600 BTC:
早在10月, Datto就通过常规的暗网监视实践确定了威胁因素。 这位网络犯罪分子被Torum称为“ w0zniak”,被发现以600美元的BTC的价格出售其在深色网上访问MSP的VPS控制面板的权限:

“I’m selling access to a MSP. They’re located in the U.S. , eastern side…… I’m asking for $600 BTC. If you’re interested message me here or on wikr… i’m also on jabber. […] I can provide photos if requested.”
“我正在出售对MSP的访问权限。 他们位于美国东部……我要的是600美元的比特币。 如果您有兴趣在这里或在wikr上给我发消息,我也在jabber上。 […]如果需要,我可以提供照片。”
We’re looking at a businesswoman at work. She’s laying out her terms — establishing price, contact information, and evidence to build trust. But what type of businesswoman is she? What are her motivations? Is it all about just a quick payout, or is there more to her plans?
我们在找一个上班的女商人。 她正在布置自己的条款-建立价格,联系信息和建立信任的证据。 但是她是什么类型的女商人? 她的动机是什么? 仅仅是快速付款,还是她的计划还有更多?
Of course, the primary goal was to identify and help our victimized member of our community. But as crazy curious cyber defenders, our secondary goal was to get a better understanding of who we were dealing with so we could “know our attacker”. It’s not every day where we have the opportunity to talk directly to a cyber criminal. This was our chance to learn more about her motivations and tactics.
当然,主要目标是确定并帮助我们社区中受害的成员。 但是,作为疯狂的好奇网络防御者,我们的次要目标是更好地了解我们与谁打交道,以便我们“ 了解我们的攻击者 ”。 并非每天都有机会直接与网络罪犯交谈。 这是我们有机会了解她的动机和策略的机会。
背景 (Background)
Let’s rewind for a second just to see how we got to this point.
让我们倒转一秒钟,只是看看我们如何达到这一点。
We’ve always believed in the power of collaboration, and we certainly are not alone. Back in July 2019, our very own VP of ThreatOps, John Ferrell, and the CISO of Datto, Ryan Weeks, got together to brainstorm ways to better secure our communities. This conversation quickly expanded to both our Huntress ThreatOps team and Datto’s security team, resulting in the creation of a Slack channel to facilitate collaboration. Evolving into the very first grassroots MSP-ISAC, we had established an avenue for vendors in the MSP community to share what we’ve seen and collaborate together.
我们一直相信协作的力量,我们当然并不孤单。 早在2019年7月,我们自己的ThreatOps副总裁John Ferrell和Datto的CISO Ryan Weeks聚在一起,共同探讨如何更好地保护我们的社区。 此对话Swift扩展到我们的Huntress ThreatOps团队和Datto的安全团队,从而创建了一个Slack渠道来促进协作。 演变为第一个草根MSP-ISAC,我们为MSP社区中的供应商建立了共享我们所见和共同协作的渠道。
What all of our community members have learned through combined decades in security is that intel sharing is one of the best and most effective ways for all of us to stay ahead of the attackers.
我们所有社区成员通过数十年的安全经验共同了解到,情报共享是我们所有人领先于攻击者的最佳,最有效的方法之一。
This story is a perfect example of a team effort. And the biggest takeaway is working together allows us to not just find and resolve threats, but to identify new behavior patterns and methods of cyber criminals. In the end, this makes us all better at protecting ourselves and each other against a potentially new type of adversary.
这个故事是团队合作的完美典范。 最大的收获是,通过共同努力,我们不仅可以发现和解决威胁,还可以识别网络犯罪分子的新行为模式和方法。 最后,这使我们所有人都能够更好地保护自己和彼此免受潜在新型对手的攻击。
侦察 (Reconnaissance)
Okay, enough with the high fives; let’s get back to the story.
好吧,击掌就足够了; 让我们回到这个故事。
Datto, one of the founding members of the MSP-ISAC, came across the Torum post shared above and showed it to the rest of the MSP-ISAC. Given our background in cyber operations at the NSA, seeing this perked up our ears motivating us to go all in to thwart this attacker.
Mat -ISAC的创始成员之一Datto碰到了上面分享的Torum帖子,并向MSP-ISAC的其他成员展示了该帖子。 鉴于我们在NSA从事网络运营的背景,看到这种声音使我们耳目一新,促使我们全力以赴来阻止此攻击者。
We started doing some snooping, watched subsequent posts, and it became evident that our adversary is a person who is looking for ways to grow and develop her business. This next post makes it clear that she’s mastered how to compromise IT departments and managed service providers, but wants to build a team to help with encryption.
我们开始做一些侦探,观察随后的帖子,很明显,我们的对手是一个正在寻找发展和发展业务的人。 下一篇文章清楚地表明,她已经掌握了如何折衷IT部门和受管服务提供商的方法,但是她想组建一个团队来帮助进行加密。
In fact, she turned down someone who offered to work with her because she wanted someone that is willing to work on a longer term strategy. This is a person who is all about the ring on their finger, not just a one-time fling.
实际上,她拒绝了一个愿意与她一起工作的人,因为她想要一个愿意长期工作的人。 这是一个人,他们的手指全靠指环,而不仅仅是一次挥拳。

“Thanks for the offer but I’m looking more for a partner or partners who want to work long time and make money.”
“感谢这项提议,但我正在寻找一个或多个想要长期工作并赚钱的合作伙伴。”
吸引我们的对手 (Engaging Our Adversary)
We knew it was imperative that we sound credible in order to get the attacker to talk. So we zipped up our black hoodies and threw ourselves into a tactical negotiation.
我们知道,为了让攻击者说话,我们必须信誉可靠。 因此,我们拉上了黑色帽衫的拉链,投入了战术谈判。

Our bogus offer:
我们的虚假报价:
- Proof of access with all the info upfront — We absolutely had no intention of paying, but was it still possible to extract clues that would lead us back to either our victim MSP or one of their clients without handing over a single dime? 预先提供所有信息的访问证明-我们绝对不打算付费,但是是否仍有可能提取线索,将我们带回受害者MSP或他们的客户之一,而无需交一分钱?
Down to $500 BTC, but we wanted to learn how to get access — not just get access by itself. Remember, our secondary goal is to actually understand more about our adversary.
最低价格为500美元BTC,但我们想学习如何获得访问权-不仅仅是自己获得访问权。 请记住,我们的次要目标是真正了解我们的对手。
- And lastly, the payment terms of the deal. 最后是交易的付款条件。

Success!! She responded! And more importantly, we’re drawing her in to give us some important details.
成功!! 她回应了! 更重要的是,我们正在吸引她,向我们提供一些重要的细节。
“I was able to get in via phishing the credentials. User accounts, customer list, and compromised accounts I can show via screenshots…. MSP is a great target because of the plethora of clients.”
“我能够通过仿冒凭据进入。 我可以通过屏幕快照显示用户帐户,客户列表和被盗帐户...。 由于客户过多,因此MSP是一个不错的目标。”
私人对话 (Private Conversations)
It worked! We were DM’ing with her on Wickr, pretending to flush out the business arrangement. Our intention was to craft our responses convincingly so that she’d give us enough details to eventually identify the targeted MSP as soon as possible so they could start remediation.
有效! 我们在Wickr上与她DM在一起 ,假装冲销业务安排。 我们的目的是令人信服地制定我们的回应,以便她为我们提供足够的详细信息,以便最终尽快确定目标MSP,以便他们可以开始进行补救。
She sent us a screenshot of what she had compromised. Wickr would have notified w0zniak if we took an “in-app” screenshot, so we resorted to the next best thing — a picture of our phone. 😉
她向我们发送了自己遭到破坏的屏幕截图。 如果我们拍摄了“应用程序内”屏幕截图,Wickr会通知 w0zniak,因此我们求助于次要的事情–手机图片。 😉

Another parlor trick? There is evidence that indicate many cyber criminals or sellers on the dark web won’t even sell their goods to US buyers. So to keep up with the facade, we said we’d “transfer EUR to BTC” to make it sound as though we were based out of the country. 😎
另一个客厅把戏? 有证据表明,许多网络犯罪分子或黑网上的卖家甚至都不会将其商品出售给美国买家。 因此,为了跟上外观,我们说过要“将EUR转移到BTC”,使声音听起来好像我们是在国外。 😎
寻找和帮助我们的朋友 (Finding and Helping Our Friends)
We took a closer look at these screenshots and the first thing we saw were the names and IP addresses of servers being managed by this MSP.
我们仔细查看了这些屏幕截图,我们首先看到的是此MSP管理的服务器的名称和IP地址。

We started ‘dig’ging through DNS records and looking at WHOIS information to help us find domain registrations, AS numbers — anything that would help us trace back to the MSP or even one of their customers. Commonalities in all of this information started to emerge, giving us confidence that we had found the MSP we were looking for.
我们开始通过DNS记录进行“ 挖掘 ”,并查看WHOIS信息,以帮助我们查找域注册,AS编号-可以帮助我们追溯到MSP甚至是其客户之一的任何内容。 所有这些信息的共性开始出现,使我们对找到所需的MSP充满信心。
With the name of the victim MSP in hand, it was now time to get a hold of them. An email or phone call seemed like an obvious next step, but this turned out to be a much harder challenge than we had anticipated.
有了受害者MSP的名字,现在该握住他们了。 电子邮件或电话似乎是显而易见的下一步,但是事实证明,这比我们预期的要困难得多。
We imagined how this call would go down:
我们想象了这个呼叫将如何下降:

成功的伙伴关系 (A Successful Partnership)
So we sat there, heads in our hands, trying to figure out what we should do. We urgently needed to get a hold of this MSP. Eventually, FQDNs and registrars from our mountain of research started staring back at us until we finally realized — some hostnames actually contained names strongly hinting that our MSP was, in fact, a ConnectWise customer.
所以我们坐在那里,双手合十,试图弄清楚我们应该做什么。 我们迫切需要掌握此MSP。 最终,来自我们大量研究的FQDN和注册服务商开始回头盯着我们,直到我们最终意识到-一些主机名实际上包含的名称强烈暗示着我们的MSP实际上是ConnectWise客户。
Using our ISAC community, we reached out for extra help. Through our community, we contacted John Ford, former CISO of ConnectWise, who helped us confirm that the MSP was indeed a ConnectWise partner. John used his business relationships to contact this MSP, passing along all the details of what we found so they could expel the hacker, protect their clients, and harden their internal network.
使用我们的ISAC社区,我们寻求了更多帮助。 通过我们的社区,我们联系了ConnectWise的前CISO John Ford ,他帮助我们确认了MSP确实是ConnectWise的合作伙伴。 John利用他的业务关系与该MSP联系,传递了我们发现的所有详细信息,以便他们驱逐黑客,保护其客户并加强其内部网络。
We couldn’t have been happier about the outcome. Reflecting on this story, it perfectly highlights how close collaboration and threat intel sharing, even between competitive vendors, can be used to go head-to-head against hackers. Putting our egos aside and succeeding at a common goal is something we can all be extremely proud of.
我们对结果再开心不过了。 回顾这个故事,它完美地凸显了如何利用紧密的协作和威胁情报共享,即使是在竞争性供应商之间,也可以用来与黑客并肩作战。 将我们的自我抛弃并在一个共同的目标上取得成功是我们所有人都可以感到自豪的。
黑客的来信 (A Message From Our Hacker)
The reality is, this story is already becoming part of a new normal. Since these events have happened, our attacker, w0zniak, has already struck again:
现实情况是,这个故事已经成为新常态的一部分。 由于发生了这些事件,我们的攻击者w0zniak已经再次袭击:

The truth is this follow-up message is not a surprise after seeing the original events. Attackers will continue discovering new victims, new markets, and new ways to succeed in their dirty business.
事实是,在看到原始事件后,此后续消息不足为奇。 攻击者将继续发现新的受害者,新的市场以及成功开展肮脏生意的新方法。
What we need to take away from this is confirmation of the essential defenses that we absolutely need to put in place in order to protect our networks and our users. We’ve heard the same story from vendors, security magazines, certification providers, etc: apply multi-factor authentication, do not expose RDP externally, watch out for phishing, the list goes on. But now, we are hearing it directly from our attacker.
我们需要摆脱的是对我们绝对需要采取的基本防御措施的确认,以保护我们的网络和用户。 我们从供应商,安全杂志,认证提供商等处听到了同样的故事:应用多因素身份验证,不向外部公开RDP,当心网上诱骗,清单还在继续。 但是现在,我们正在直接从攻击者那里听到它。
I’ll provide you with the username and password for the admin accounts. The passwords and username for client account is provided … You’ll access most of these clients through RDP.
我将为您提供管理员帐户的用户名和密码。 提供了客户帐户的密码和用户名…您将通过RDP访问这些客户中的大多数。
There is no better confirmation supporting these defenses than from the source.
没有比从源头上更好的证实支持这些防御的证据。
分享是关怀 (Sharing is Caring)
While we do our best to avoid them, we each have our own unique encounters with these attackers. And because we’re always seeing new attacker behavior, sharing these encounters is exceedingly important. It helps us stay together as a community to corroborate events, warn others of what we’ve seen, and enrich everyone.
尽管我们尽力避免它们,但我们每个人与这些攻击者都有自己独特的遭遇。 而且由于我们总是看到新的攻击者行为,因此分享这些遭遇非常重要。 它可以帮助我们作为一个社区团结在一起,以确认事件,警告其他人我们所见的事物并丰富每个人。
As always, we will stand by our commitment to sharing what we see and find ways to improve our community. And as long as hackers keep hacking, we will always keep hunting.
与往常一样,我们将恪守承诺,分享我们的见解并找到改善社区的方法。 只要骇客继续骇客,我们就会永远追捕。
编者注 (Editorial Note)
Huntress purposefully personified this hacker as a business-savvy woman of (offensive) cybersecurity. The truth is, we actually don’t know the identity or gender of the attacker. We personified this hacker as a woman for the sheer fact that there’s not enough representation of women in the cybersecurity industry and that there are equally capable cyber criminals out there that are women.
Huntress故意将这位黑客形象化为(攻击性)网络安全的精明业务女人。 事实是,我们实际上不知道攻击者的身份或性别。 我们纯粹是因为在网络安全行业中没有足够的女性代表,而且那里有同样能力强大的网络罪犯是女性,因此将这个黑客假扮成女性。
msp432 读一个端口值





















 8426
8426

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








