光盘 机密
背景(Background)
Google Cloud provides encryption and/or integrity of data in transit and at rest by default. We also employ other techniques like sandboxing to help protect our infrastructure and customer data. This virtualization security model allows us to offer a secure multi-tenant architecture where VMs can run isolated and protected from each other.
谷歌云默认提供加密和/或传输中的数据的完整性和休息。 我们还采用沙盒技术等其他技术来帮助保护我们的基础架构和客户数据。 这种虚拟化安全模型使我们能够提供安全的多租户架构,使VM可以隔离运行并彼此保护。
In this security model, the hypervisor is part of the Trusted Computing Base since it creates, manages and isolates these VMs. Hence, it is critical to the security of the system. If the hypervisor itself is compromised all the VMs can become vulnerable.
在此安全模型中,管理程序是可信计算库的一部分,因为它创建,管理和隔离了这些虚拟机。 因此,对于系统的安全性至关重要。 如果虚拟机管理程序本身遭到破坏,则所有VM都可能变得脆弱。
We put a lot of effort to harden and keep our infrastructure secure, including KVM, the hypervisor Google uses. We proactively research and test for vulnerabilities, contributing our changes back to the community, and have processes to provide code integrity and provenance assurance.
我们付出了很多努力来加强和保持基础架构的安全,包括Google使用的虚拟机管理程序KVM 。 我们会主动研究和测试漏洞,将所做的更改反馈给社区,并制定流程来提供代码完整性和源保证。
Still, some markets can benefit from protecting their VMs from bugs in the hypervisor or the cloud provider, especially those on regulated industries or managing highly sensitive data. Confidential Computing comes to solve this.
尽管如此,某些市场仍可以从虚拟机管理程序或云提供商中保护其VM免受错误中受益,尤其是那些受管制行业或管理高度敏感数据的缺陷。 机密计算可以解决这个问题。
提升安全性 (Security to the next level)
The Confidential Computing Consortium, that Google is member of, aims to address the security of data in use. Even when data is encrypted in transit or at rest it must be decrypted for processing in memory. If another process were able to read that memory it would compromise the security of the system. Of course one such process is the hypervisor. In theory, other processes running at lower privilege level could also get access to that memory if they exploit a bug in the hypervisor.
Google隶属于机密计算联盟,旨在解决使用中数据的安全性。 即使在传输途中或静止时对数据进行加密,也必须将其解密以在内存中进行处理。 如果另一个进程能够读取该内存,则将损害系统的安全性。 当然,管理程序就是这样一种过程。 从理论上讲,如果其他进程利用虚拟机管理程序中的错误,则以较低特权级别运行的其他进程也可以访问该内存。
Non-volatile memory technology aggravates this situation. These memory chips can be physically removed and their data read like a hard drive. Other types of attacks like DRAM interface snooping are also possible. Arguably, these are quite complicated in a cloud environment.
非易失性存储技术加剧了这种情况。 这些内存芯片可以物理卸下,并且像硬盘一样读取数据。 其他类型的攻击,例如DRAM接口侦听也是可能的。 可以说,这些在云环境中非常复杂。
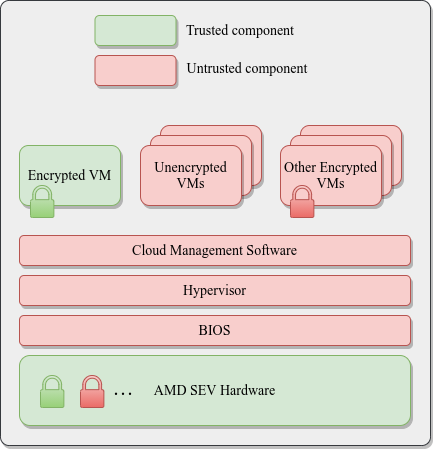
To address this type of security risks and give more confidence and control to users, Google now offers Confidential VMs. These are GCE VMs running on hosts using the AMD Secure Encrypted Virtualization (SEV) technology. This technology provides memory encryption of VMs, using a key that is known only to the processor and not the hypervisor. Not even Google has access to it.
为了解决这种类型的安全风险并为用户提供更多的信心和控制权,Google现在提供了机密VM 。 这些是使用AMD安全加密虚拟化(SEV)技术在主机上运行的GCE VM。 该技术使用仅处理器而非管理程序知道的密钥来提供VM的内存加密。 甚至Google都无法访问它。
This way, when a new VM is created a random key is also created, and its memory is automatically encrypted so that its contents can only be read by the VM itself. Other processes including the hypervisor could only access the data in its encrypted form. Security is rooted in the hardware itself.
这样,在创建新的VM时,还会创建一个随机密钥,并且其内存会自动加密,因此其内容只能由VM自己读取。 包括管理程序在内的其他进程只能访问其加密形式的数据。 安全性植根于硬件本身。
There are other solutions for confidential computing used by other cloud providers based on Intel SGX technology. This technology allows to partition regions of memory into enclaves, which are areas of execution with hardware-assisted encryption and integrity protections to prevent access from other processes outside the enclave itself, including those running at higher privilege levels.
还有其他基于英特尔SGX技术的云提供商使用的机密计算解决方案。 该技术允许的内存分区区域并入飞地,这是与硬件辅助加密和完整性保护的执行区域,以防止其他进程飞地本身,包括那些在更高的权限级别运行的外部访问。
Intel includes SGX instruction set extensions on some modern CPUs that allow code developers to create and manage these enclaves. However, this means that users should modify their applications to take advantage of this technology, and use it appropriately. This is a serious drawback, although Intel and Microsoft have developed SDKs and frameworks to make this work easier for developers.
英特尔在某些现代CPU上包括了SGX指令集扩展,这些扩展使代码开发人员可以创建和管理这些区域。 但是,这意味着用户应修改其应用程序以利用此技术,并适当地使用它。 这是一个严重的缺点,尽管英特尔和微软已经开发了SDK和框架,以使开发人员更容易进行此工作。
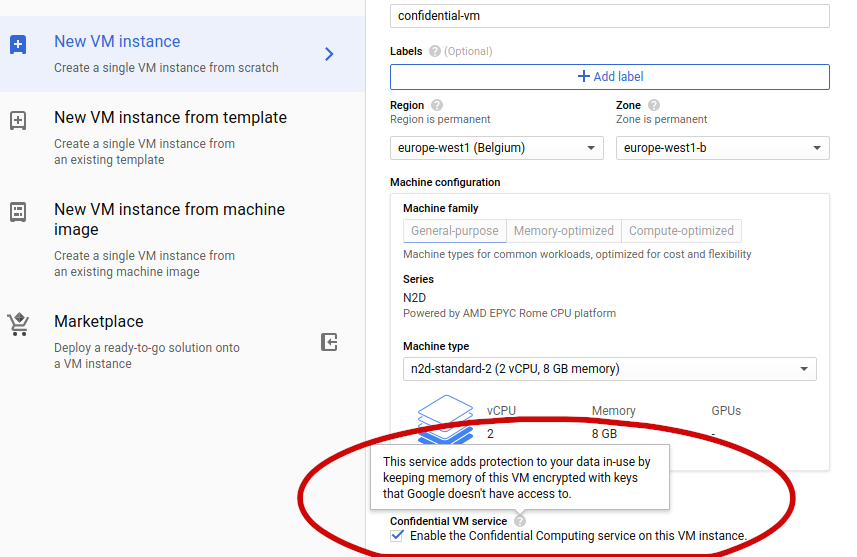
AMD SEV technology is a superior solution since it allows confidential computing without requiring any application software changes. The changes to support it should be made on the lower levels of the stack, in the guest operating system and hypervisor. Google takes care of that for you, so your application can be migrated as is. Users only need to enable it when creating a new VM.
AMD SEV技术是一种出色的解决方案,因为它可以进行机密计算,而无需更改任何应用程序软件。 支持它的更改应在客户操作系统和虚拟机管理程序的堆栈的较低级别上进行。 Google会帮您解决这个问题,因此您的应用程序可以按原样迁移。 用户仅需要在创建新VM时启用它。
魔术如何发生 (How the magic happens)
AMD SEV builds upon AMD-V virtualization features. AMD-V supports running multiple VMs under the control of a hypervisor. When the hypervisor runs guest VM code, it executes a VMRUN instruction with the virtual machine control block as argument which describes the VM. SEV encryption capabilities can then be enabled by setting a control bit.
AMD SEV建立在AMD-V虚拟化功能的基础上。 AMD-V支持在管理程序的控制下运行多个VM。 系统管理程序运行来宾VM代码时,它将执行VMRUN指令,并以虚拟机控制块作为参数来描述VM。 然后可以通过将控制位设置来启用SEV加密功能。
Each SEV-enabled VM is associated with a unique memory encryption key. Key management is not handled by the CPU but a separate Secure Processor and firmware, so encryption keys are not visible to the main CPU or the hypervisor. The firmware provides an interface to help the hypervisor perform common tasks such as launching, running, snapshotting, and migrating a VM.
每个启用了SEV的VM都与唯一的内存加密密钥关联。 密钥管理不是由CPU处理,而是由单独的安全处理器和固件处理,因此加密密钥对主CPU或管理程序不可见。 固件提供了一个界面,可帮助管理程序执行常见任务,例如启动,运行,快照和迁移VM。
The generated keys are loaded to memory controllers. Each controller includes an AES-128 engine that encrypts data when it is written to DRAM and decrypts it when read. Once SEV encryption is enabled, the guest OS can decide which pages of memory will be private (encrypted) or shared by setting the C-bit (enCrypted bit) in the corresponding guest page table entry (PTE). Typically, the guest will map all memory pages as private except e.g. those to be shared with the hypervisor for I/O.
生成的密钥将加载到内存控制器。 每个控制器都包括一个AES-128引擎,该引擎在将数据写入DRAM时对其进行加密,并在读取时对其进行解密。 一旦SEV加密启用,来宾操作系统可以决定哪些内存页面将是私有(加密),或通过设置C-位在相应的客人页表项(PTE)(ENçrypted位)共享。 通常,guest虚拟机会将所有内存页面映射为私有页面,除了那些要与虚拟机管理程序共享的I / O页面。
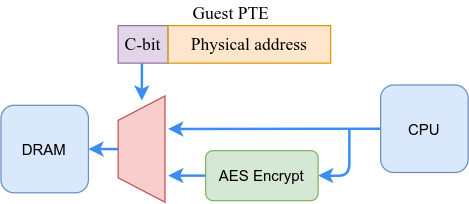
Not only data is encrypted when SEV is enabled. Guest instruction pages and page tables themselves are always treated as private, so other processes such as the hypervisor can’t inject or modify guest code successfully. While in theory the hypervisor can modify these pages, doing so would cause junk data to be executed (and very likely a fault).
启用SEV时,不仅数据被加密。 来宾指令页面和页表本身始终被视为私有,因此其他进程(例如管理程序)无法成功注入或修改来宾代码。 虽然理论上虚拟机管理程序可以修改这些页面,但这样做会导致执行垃圾数据(很可能是错误)。
AMD SEV offers more features than described here. I have described the basics but there are more technologies being developed to protect virtual environments against more complex threat models.
AMD SEV提供的功能比此处描述的更多。 我已经描述了基础知识,但是正在开发更多的技术来保护虚拟环境免受更复杂的威胁模型的侵害。
结论 (Conclusion)
Confidential Computing enables new cloud scenarios where customers can run highly sensitive workloads minimizing their risk to hypervisor bugs or insider access, and the need for trust in the cloud provider. Along with encryption of data in transit and at rest, encrypting data in use is the third pillar to the end-to-end encryption story. This is really a game changing technology that raises the security bar, and now Google offers it to you with a click of a button. Isn’t it cool?
机密计算实现了新的云方案,在这些方案中,客户可以运行高度敏感的工作负载,从而最大程度地降低了对虚拟机管理程序错误或内部访问的风险以及对云提供商的信任度。 除了对传输中的数据和静态数据进行加密之外,对使用中的数据进行加密是端到端加密故事的第三大Struts。 这确实是一项改变游戏规则的技术,它提高了安全性,现在Google只需单击一下按钮即可为您提供安全性。 是不是很酷?
PS: Thanks to Jose Carlos Cerezo for the inspiration to write about this.
PS:感谢Jose Carlos Cerezo的灵感来撰写此内容。
翻译自: https://medium.com/@juliodiez/confidential-computing-is-cool-1d715cf47683
光盘 机密





















 398
398











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








