Learning how to utilize an incident plan to prepare an organization to respond to cyber-attacks including phishing, ransomware, and wire fraud attempts is crucial for any organization.
学习如何利用事件计划来使组织做好准备以应对网络攻击,包括网络钓鱼,勒索软件和有线欺诈企图对于任何组织都至关重要。
The internet has become an increasingly dangerous place, and we hear stories day to day for cybersecurity breaches happening seemingly to everyone. Most people don’t understand, though is that when the security incident happens you have to be fast to respond since every second does matter. A compromised computer can infect the others in an organization in a matter of seconds if not found and stopped at the right time. Ransomware can cause immense damage if it gets to the correct computer, and it may be catastrophic for the entire organization. Phishing also it’s really scary since they can use the accounts that are compromised to gain privileged access, which in some cases can give the attackers full access.
互联网已经变得越来越危险,我们每天都在听到有关每个人似乎都在发生网络安全漏洞的故事。 大多数人不了解,尽管当安全事件发生时,您必须快速做出响应,因为每一秒都很重要。 如果找不到并在适当的时间停止运行,受感染的计算机可能会在几秒钟内感染组织中的其他计算机。 如果勒索软件安装到正确的计算机上,则可能造成巨大破坏,并且可能对整个组织造成灾难性的影响。 网络钓鱼真的很可怕,因为他们可以使用被盗用的帐户来获得特权访问,在某些情况下,这可以使攻击者具有完全访问权限。
Even if you are a new company with a small group of people working, you should have a security incident protocol in place. It should take off immediately after an alarm goes off and should follow the necessary procedures to stop the attacks. This could be crucial to the prosperity of your company and would save headaches in the future.
即使您是一小群工作的新公司,也应该有一个安全事件协议。 警报响起后应立即起飞,并应按照必要的程序停止攻击。 这对于您公司的繁荣至关重要,并且可以避免将来的麻烦。
What is considered a cybersecurity incident?
什么被视为网络安全事件?
There are many types of information security breaches that could be classified as cybersecurity incidents. They are from severe cybersecurity attacks on critical national infrastructure and major organized cybercrime, through hacktivism and basic malware attacks, to internal misuse of systems and software malfunction. However, there is no way to definitively help organizations decide what is and what isn’t a security incident, breach, or attack.
有许多类型的信息安全漏洞可以归类为网络安全事件。 它们包括从对国家关键基础设施和主要有组织的网络犯罪的严重网络安全攻击(通过黑客行为和基本的恶意软件攻击)到内部滥用系统和软件故障。 但是,没有办法最终帮助组织确定什么是安全事件,破坏或攻击。
The original government definition of cybersecurity incidents as being state-sponsored attacks on critical national infrastructure or defense capabilities is still valid. However, the industry which is fuelled by the media has adopted the term. Now the term cybersecurity incident is often used to describe traditional information security incidents.
政府最初将网络安全事件定义为国家资助的关键国家基础设施或防御能力的攻击仍然有效。 但是,在媒体的推动下,该行业采用了该术语。 现在,术语“网络安全事件”通常用于描述传统的信息安全事件。
The below graph will help you understand better, which are considered traditional information security incidents and which are cybersecurity attacks.
下图将帮助您更好地理解哪些是传统的信息安全事件,哪些是网络安全攻击。
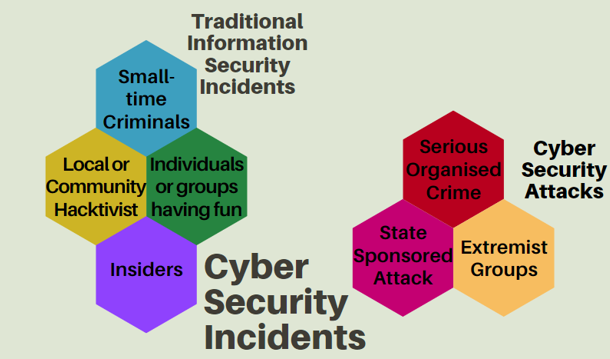
What is Incident Response?
什么是事件响应?
Incident Response or short IR is a detailed plan for managing security incidents, violations, and cyber threats. A clear incident response plan allows you to effectively recognize, reduce the damage, and decrease the cost of a cyberattack while finding and fixing the cause to prevent attacks from happening in the future.
事件响应或短路 IR是用于管理安全事件,违规和网络威胁的详细计划。 清晰的事件响应计划可让您有效地识别,减少破坏并降低网络攻击的成本,同时查找并修复原因以防止将来发生攻击。
When faced with a cybersecurity incident security teams are often in a chaotic environment and this hinders their ability to take the right measure at the right time. This is bad for the business since one second could mean millions of dollars worth of information stolen. That’s why we plan incident responses so that the security team does know what the most important tasks are and not get bullied around by the attackers. Having an incident response plan checklist will tremendously help. Having an IR Policy in place will help your team get the best support from the organization so that they can do their work most efficiently.
当面对网络安全事件时,安全团队通常处于混乱的环境中,这阻碍了他们在正确的时间采取正确的措施的能力。 这对企业不利,因为一秒钟可能意味着价值数百万美元的信息被盗。 这就是为什么我们计划事件响应,以便安全团队确实知道最重要的任务是什么,并且不会被攻击者欺负。 制定事件响应计划清单将极大地帮助您。 制定IR策略将帮助您的团队从组织中获得最佳支持,从而使他们可以最高效地完成工作。
Main challenges with a cybersecurity incident response.
网络安全事件响应的主要挑战。
In today’s commercial world, governments and large organizations often overlook the importance of being able to respond fast to cybersecurity incidents. They assign more resources when the cyberattack is happening and after the danger has passed, they go back to thinking that won’t happen again and they pull back. This happens a lot more then you can imagine and even to bigger companies with huge reputations. Top management in organizations does not believe that they are at risk of these cybersecurity incidents, or in some cases, they aren’t aware of the negative impact that could cause to the company.
在当今的商业世界中,政府和大型组织常常忽略了能够快速响应网络安全事件的重要性。 他们会在网络攻击发生时分配更多的资源,并且在危险过去之后,他们会重新考虑这种情况不会再发生,而是撤回。 这种情况发生得比您想像的要多得多,甚至发生在声誉卓著的大型公司中。 组织中的高层管理人员不认为自己有遭受这些网络安全事件的风险,或者在某些情况下,他们不知道可能对公司造成的负面影响。
Research shows what the most common difficulties organizations face in responding to a cybersecurity incident in a quick, efficient, and logical manner are in:
研究表明,组织以快速,高效和合乎逻辑的方式应对网络安全事件时面临的最常见困难是:
1. Identifying a suspected cybersecurity incident.
1.确定可疑的网络安全事件。
2. Establishing the objective of any investigation and clean-up operation.
2.确定任何调查和清理操作的目标。
3. Analyzing all available information related to the potential cybersecurity incident.
3.分析与潜在网络安全事件相关的所有可用信息。
4. Determining what has actually happened.
4.确定实际发生了什么。
5. Identifying what systems, networks, and information have been compromised.
5.确定哪些系统,网络和信息受到了破坏。
6. Determining what information has been disclosed to unauthorized parties, stolen, deleted, or corrupted.
6.确定哪些信息已泄露给未授权方,被盗,删除或损坏。
7. Finding out who did it and why.
7.找出是谁做的,为什么。
8. Working out how it happened.
8.弄清楚它是怎么发生的。
9. Determining the potential business impact of the cybersecurity incident.
9.确定网络安全事件的潜在业务影响。
10. Conducting sufficient investigation to identify the perpetrator.
10.进行充分的调查,以确定肇事者。
Preparing for a cybersecurity incident.
为网络安全事件做准备。
When dealing with a cybersecurity incident, one of the most important actions is to be properly prepared. This will help you to recover your systems more quickly, minimize the impact of the attack, instill confidence in your customers, and even save you money in the long term.
处理网络安全事件时,最重要的操作之一就是要做好适当的准备。 这将帮助您更快地恢复系统,最大程度地减少攻击的影响,建立对客户的信心,甚至从长远来看可以节省金钱。
- Conduct an assessment of critical information
- 对关键信息进行评估
Basically you need to define which information does your company considers critical and also other assets. Then you need to determine what kind of cybersecurity threats can affect these critical assets and raise awareness to the employees.
基本上,您需要定义公司认为哪些信息是关键信息以及其他资产。 然后,您需要确定哪种网络安全威胁会影响这些关键资产并提高员工的意识。
- Do a cybersecurity threat analysis
- 做网络安全威胁分析
You need to understand the level of threat to your organization from different types of cybersecurity incidents. To do this, you should first have produced a definition of what a cybersecurity incident means to your organization and created a set of examples of the types of threats associated with these incidents, such as phishing, ransomware, and hacking.
您需要了解不同类型的网络安全事件对组织的威胁级别。 为此,您首先应该确定网络安全事件对组织的意义,并创建一组与这些事件相关的威胁类型的示例,例如网络钓鱼,勒索软件和黑客攻击。
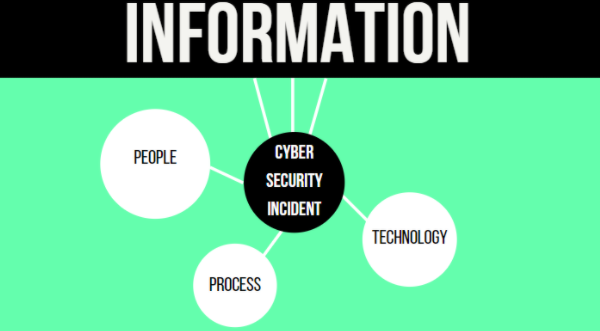
- Consider the implications of people, technology, processes, and information
- 考虑人员,技术,流程和信息的含义
It’s difficult identifying the culprit, and as we saw from the research conducted, this was the main challenge that companies faced when responding to cybersecurity incidents. However, in the earlier stages, nothing is left out of the investigation.
很难找出罪魁祸首,正如我们从进行的研究中所看到的那样,这是公司在应对网络安全事件时面临的主要挑战。 但是,在早期阶段,什么都没有排除在调查之外。
Responding to a cybersecurity incident.
响应网络安全事件。
When dealing with cybersecurity incidents the security team usually should have a detailed plan with tasks that they should complete in order to handle the situation in the best way. This plan should already be in place and can’t be implemented in times of crisis. While the organizations most typically think that an incident is a one-time thing a lot of the times for the most sophisticated incidents they have been going for months or even years. To provide you with a broader understanding of a typical live situation, the four following steps have been developed.
在处理网络安全事件时,安全团队通常应该制定详细计划,并制定任务,以便以最佳方式处理这种情况。 该计划应该已经到位,在危机时期不能实施。 尽管组织通常通常认为事件是一次复杂的事件,但对于大多数复杂的事件而言,它们已经持续了几个月甚至几年的时间。 为了使您对典型的现场情况有更广泛的了解,已制定了以下四个步骤。
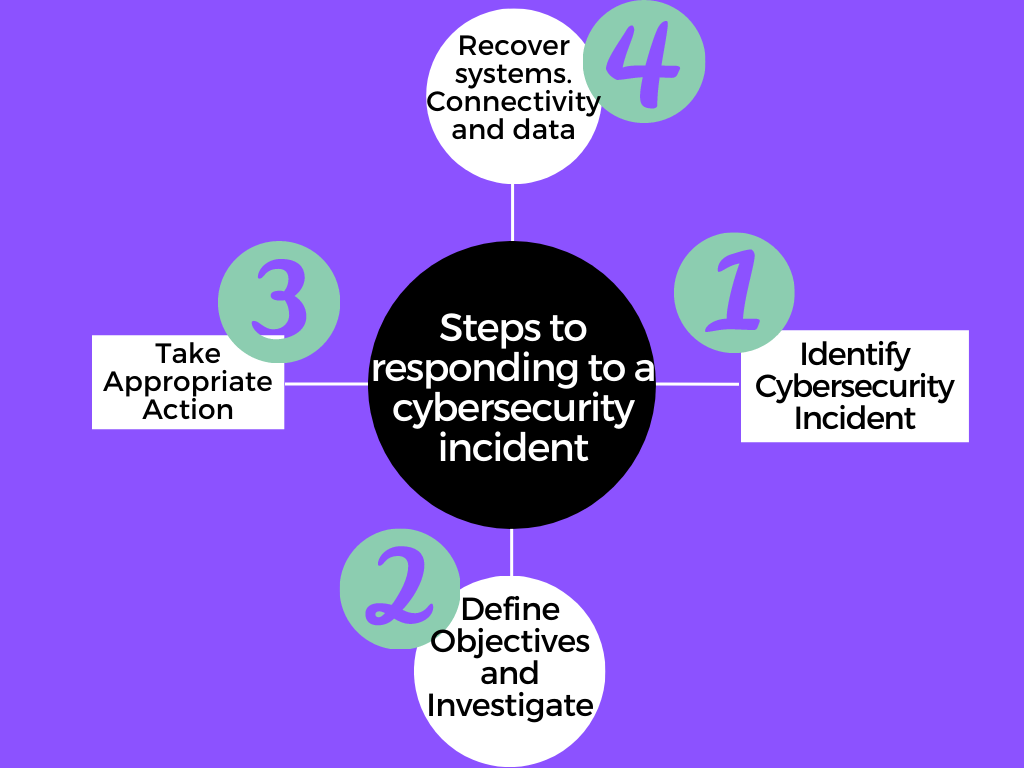
- Identify the cybersecurity incident
- 识别网络安全事件
For most organizations, identifying the cybersecurity incident was the most challenging thing to figure out. The incident response team is responsible for the process to accurately detect and figure out possible cybersecurity incidents while determining whether an incident has occurred and, if so, the type, extent, and the magnitude of the problem. They need to detect cybersecurity incidents and analyze them at a high level while in real-time so it’s not an easy thing to do but also crucial. Sometimes there are no hints that something is going on but the experts still must be able to figure it out.
对于大多数组织而言,要确定网络安全事件是最具挑战性的事情。 事件响应团队负责在确定事件是否已发生以及问题的类型,程度和严重性的同时,准确地检测并找出可能的网络安全事件的过程。 他们需要检测网络安全事件并实时进行高级别分析,因此这不是一件容易的事,而是至关重要的。 有时没有迹象表明正在发生某些事情,但是专家仍然必须能够弄清楚。
- Define objective and investigate the situation
-确定目标并调查情况
Once a cybersecurity incident has been recognized, the next step is to define what the objectives are for the response team. They have to investigate the situation in a serious manner. The response team should be able to understand clearly what the most valuable information they have to protect first is and whether any critical assets have been compromised. Sometimes it can be very useful to have access to cyber threat intelligence, to be able to research into the attackers to determine their capabilities, motives, and likely actions that they will take.
一旦发现网络安全事件,下一步就是定义响应团队的目标。 他们必须认真调查情况。 响应团队应该能够清楚地了解他们首先要保护的最有价值的信息是什么,以及是否有任何关键资产被盗用。 有时,访问网络威胁情报可能非常有用,能够对攻击者进行调查以确定他们的能力,动机和将要采取的行动。
- Taking appropriate action when responding to attackers
- 应对攻击者时采取适当的措施
One of the first and most important actions to be taken after the initial investigation is to contain the damage being done by the cybersecurity incident. For example, by stopping it from spreading to other networks and devices both within your organization and beyond. Containment usually includes a number of concurrent actions aimed at decreasing the immediate impact of the cybersecurity incident, primarily by exterminating the perpetrator’s access to the systems. The objective of containment is not always to get back to business as usual, but to make sufficient efforts to return to function as a normal business while continuing to analyze the incident and plan long term remediation.
进行初步调查后,首先要采取的最重要的措施之一就是遏制网络安全事件造成的损害。 例如,通过阻止它传播到组织内外的其他网络和设备。 遏制通常包括一系列旨在减少网络安全事件的直接影响的并发行动,主要是通过消除犯罪者对系统的访问来实现。 遏制的目的并不总是恢复正常,而是要做出充分的努力以恢复正常业务,同时继续分析事件并计划长期补救措施。
- Recover systems, connectivity, and data
- 恢复系统,连接性和数据
The last step in responding to a cybersecurity incident is to restore systems to normal operations as soon as possible. The teams have to confirm that the systems are functioning normally, and remediate vulnerabilities to prevent similar incidents from occurring again in the future. It’s important to validate the systems as soon as possible, and sometimes internal penetration testing needs to be done so that you know for sure that you are well protected.
应对网络安全事件的最后一步是使系统尽快恢复正常运行。 团队必须确认系统正常运行,并补救漏洞以防止将来再次发生类似事件。 尽快验证系统非常重要,有时还需要进行内部渗透测试,以确保您受到良好保护。
翻译自: https://levelup.gitconnected.com/how-to-utilize-an-incident-response-ir-plan-f631c47bbcc7





















 3846
3846

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








