数据数据泄露泄露
The IBM Security “Cost of a Data breach” survey is out [here], and it analyses the ever-increasing costs involved in data breaches. It involves a survey of 524 companies who have recently had a data breach (between August 2019 and April 2020) and covers over 17 countries, and 17 different sectors.
IBM Security“数据泄露成本”调查已在[ 此处 ]进行,它分析了数据泄露所涉及的不断增加的成本。 它涉及对524家最近发生数据泄露事件(2019年8月至2020年4月)的公司的调查,涵盖了17个国家和17个不同领域。
As previous research has shown, the industries which bare the most costs are healthcare ($7.13 billion) and energy ($6.9 billion). These two are often seen as soft targets, and which have high amounts of sensitive personally identifiable information (PII):
正如先前的研究表明,成本最高的行业是医疗保健 (71.3亿美元)和能源 (69亿美元)。 这两个通常被视为软目标,并且具有大量敏感的个人身份信息(PII):

The highest cost per record relates to consumer PII and is $150 per record breached. When it comes to the motivates for threat actors, it is still the human failing for the love of money that keeps them focused on their targets, but there is a significant percentage associated with hacktivist and nation-states:
每条记录的最高成本与消费者PII有关, 每条记录被破坏的成本为150美元 。 当谈到威胁行为者的动机时,仍然是人类对金钱的热爱使他们无法专注于目标,但与黑客主义者和民族国家相关的比例却很大:

For the things that can save costs related to data breaches, the best investment is within Incident Response (IR) testing, business continuity planning and implementation, having an IR team, having an AI platform, extensive encryption, security analytics, and red team testing:
为了节省与数据泄露相关的成本,最好的投资是在事件响应(IR)测试,业务连续性计划和实施,拥有IR团队,拥有AI平台,广泛的加密,安全分析和红色团队测试的范围内:

But the things that increase costs are cloud migration, a shortage of security skills and complex security systems. When it comes to pointing blame on who is responsible for a data breach, the CISO/CSO comes out in front, and for taking technical responsibility the CIO/CTO role is the one that is most pin-pointed:
但是增加成本的是云迁移,安全技能不足和复杂的安全系统。 当要归咎于谁应对数据泄露负责时,CISO / CSO排在首位,对于承担技术责任,CIO / CTO的角色是最明确的:
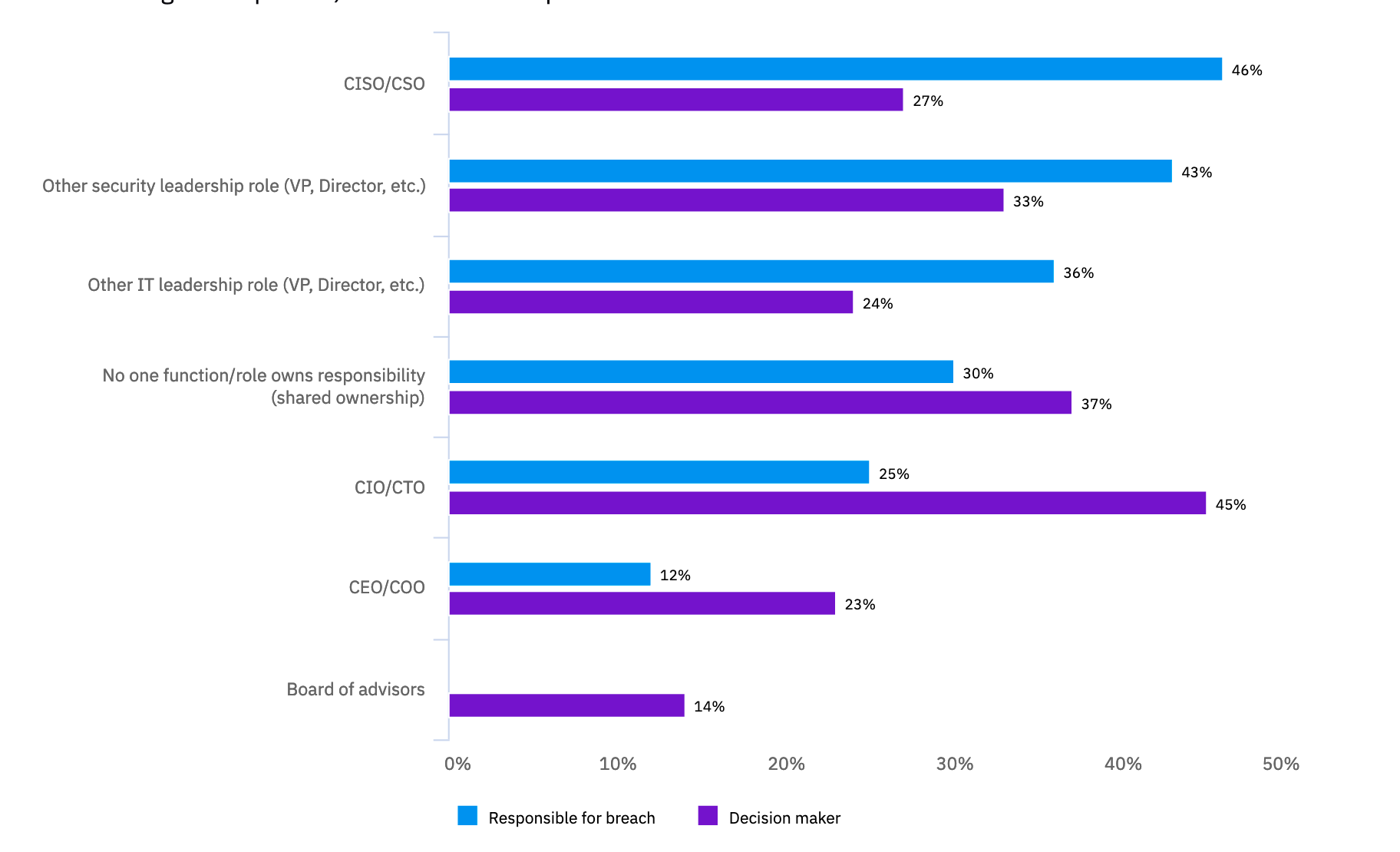
It is interesting that the board of advisors seem to bare very little responsibility for a breach, but have some influence in decision making.
有趣的是,顾问委员会对违约行为几乎没有承担任何责任,但对决策有一定影响。
So, with all this investment in security, is the time to detect a data breach and containing it reducing? Well, not from those survey, as the average time to detect a breach is a massive 207 days, and 73 days to contain it:
因此,在安全性方面进行了所有这些投资之后,检测数据泄露并对其进行遏制的时间是否减少了? 好吧,不是来自那些调查,因为发现违规的平均时间是207天 ,而遏制它的时间是73天 :

The average costs savings when a breach is contained within 200 days is estimated at $1 million. One particular target for threat actors are compromised credentials and cloud misconfiguration, and which account for nearly one-fifth of all malicious breaches. The average estimated saving for those with automated security controls is $3.8 million, and $2 million for those with Incident Response (IR) teams.
在200天之内遏制一次违规,平均节省的费用估计为100万美元。 威胁参与者的一个特定目标是凭据遭到破坏和云配置错误 ,它们占所有恶意破坏的近五分之一。 具有自动安全控制功能的人员平均节省380万美元,具有事件响应(IR)团队的人员平均节省200万美元。
So, in a COVID-19 era, is the time rising or falling to detect and/or contain a data breach? Well, the vast majority of companies in the survey say that there’s an increased time spent on this:
因此,在COVID-19时代,检测和/或遏制数据泄露的时间在增加还是减少? 好吧,接受调查的绝大多数公司都表示,在此方面花费的时间越来越多:

And that the costs of dealing with a breach have increased:
而且处理违规的成本增加了:

结论 (Conclusions)
The true cost of a data breach is much more than just containing it. In the case of Travelex, it can push the company over the edge, and inflict significant damage to a brand. It can also affect other things such as staff morale and result in a loss of key staff (or even difficulties in recruiting staff).
数据泄露的真正代价远不只是遏制它。 就Travelex而言,它可以使公司脱颖而出,并严重损害品牌。 它还可能会影响其他因素,例如员工士气,并导致关键员工的流失(甚至招募人员有困难)。
While the figures in the IBM report can be disputed for whether they are actually real costs, there’s some good pointers to the areas that companies perhaps need to invest in. For small companies in IR, red teaming, encryption and security training, it provides a bit of evidence for investments from boards.
尽管IBM报告中的数字实际上是否为实际成本尚有争议,但对于公司可能需要投资的领域还是有一些很好的指点。对于IR,红队,加密和安全培训方面的小型公司,它提供了一个董事会投资的一些证据。
翻译自: https://medium.com/asecuritysite-when-bob-met-alice/the-cost-of-data-breaches-d81d401f8b35
数据数据泄露泄露





















 326
326











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








