1、清除闪存中配置文件
write erase
2、显示nat信息
show xlate
3、默认情况下pix的直连接口可以ping通的。但对于穿越pix的icmp的流量需要通过ACL来控制。
4、允许(inside)ping(outside)的配置
access-list outside extended permit icmp any any
access-group outside in interface outside
5、允许(inside)ping(dmz)的配置
access-list 100 permit icmp any any #允许DMZ区域的主机的ICMP协议的报文能够访问出去
access-group 100 in interface dmz #将策略应用在dmz接口上
static (inside,dmz) 192.168.100.2 192.168.100.2 #192.168.100.2 为内部需要和DMZ通讯的主机,这条保证内部访问dmz主机时不被nat转换
6、外网访问DMZ区域的web服务器,配置防火墙的反向NAT。
static (inside,outside) tcp interface www 10.1.1.2 www
//将DMZ区域的web发布到公网上//
access-list 100 permit tcp any host 202.101.1.1 eq 80 /// 允许外网访问dmz的80 端口///
access-group 100 in interface outside
7、(DMZ)访问(inside)内主机的23端口
access-list 100 permit ip host 192.168.120.3 host 192.168.100.2
access-group 100 in interface dmz
8、映射内部的主机到公网,例如把192.168.100.2 的23 端口映射为202.100.100.10 的23端口
static (inside,outside) tcp 202.100.100.10 telnet 192.168.100.2 telnet netmask 255.255.255.255
access-list 101 extended permit tcp any any eq telnet
access-group 101 in interface outside
9、映射DMZ主机到公网,例如把192.168.120.3 的23端口映射为202.100.100.11 的23端口
static (dmz,outside) tcp 202.100.100.11 telnet 192.168.120.3 telnet netmask 255.255.255.255
access-list 101 extended permit tcp any any eq telnet
access-group 101 in interface outside
-------------------------基本配置------------------
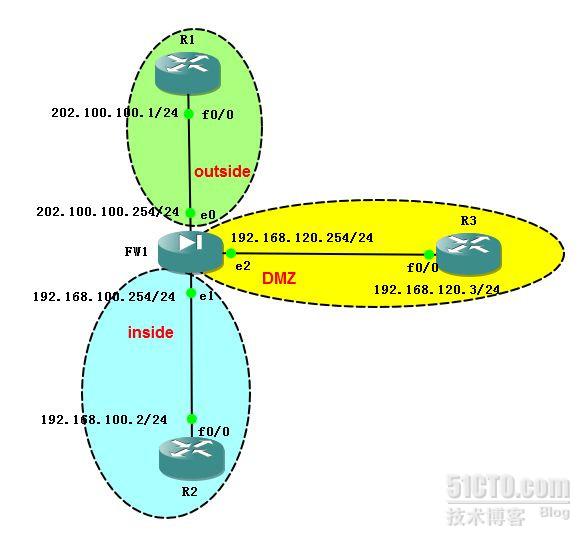
interface Ethernet0
nameif outside
security-level 0
ip address 202.100.100.254 255.255.255.0
!
interface Ethernet1
nameif inside
security-level 100
ip address 192.168.100.254 255.255.255.0
!
interface Ethernet2
nameif dmz
security-level 50
ip address 192.168.120.254 255.255.255.0
access-list 100 extended permit icmp any any
access-list 100 extended permit ip host 192.168.120.3 host 192.168.100.2
!
global (outside) 1 interface
nat (inside) 1 0.0.0.0 0.0.0.0
!
static (inside,dmz) 192.168.100.2 192.168.100.2 netmask 255.255.255.255
access-group 100 in interface dmz
转载于:https://blog.51cto.com/haolun/991607





















 296
296











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








