ipsec ***: lan-to-lan ***(站点到站点)
最基本的ipsec ***,当我需要对敏感数据在传输的过程中进行加密,以保证数据的,保密性,不可篡改,源认证!而对加密,对称加密比公钥加密具有更高的效率,可以用硬件支持,但是密钥的分发是一个问题,所以用公钥和对称密钥结合的办法去解决,但是怎么保证公钥的安全性,一般用的是D-H算法!但是ipsec lan-to-lan也有它的限制,当有多个子公司或者子公司的地址是通过拨号获得的,那么就不能实现,所以在实现lan-to-lan ***的时候 双方的 公网地址必须是静态的!
所以ipsec 配置的过程分为主要的两个步骤;
(1)ike 的配置,主要协商密钥加密策略(2)ipsec的加密算法的协商
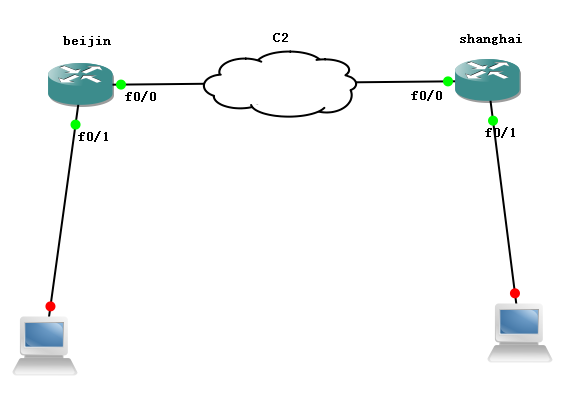
北京总公司:
R1>
R1>EN
R1#
R1#config t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config-if)#int f0/0
R1(config-if)#no shu
*Mar 1 00:02:34.987: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Mar 1 00:02:35.987: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
R1(config-if)#ip address 210.45.165.1 255.255.255.0
R1(config-if)#int f0/1
R1(config-if)#no shu
R1(config-if)#ip address 172.16.
*Mar 1 00:02:55.235: %LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to up
*Mar 1 00:02:56.235: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to up
R1(config-if)#ip address 172.16.1.1 255.255.255.0
R1(config-if)#exit
R1(config)#ip route 0.0.0.0 0.0.0.0 f0/0
R1(config)#crypto isakmp policy 10(第一阶段,定义ike的策略)R1(config-isakmp)#group 2(D-H算法,在思科路由器上有
1 2 5 )
R1(config-isakmp)#hash md5(哈希 用md5)
R1(config-isakmp)#authentication pre-share(预共享密钥)
R1(config-isakmp)#encryption 3des(加密 用3des ,注意此处的加密和下面的转换级的加密 ,加密的对象不一样)
R1(config-isakmp)#exit
R1(config)#crypto isakmp key 0 gaoshan address 210.45.165.2 (定义预共享密钥为gaoshan,对象的ip地址)
R1(config)#crypto ipsec transform-set ipsec esp-des esp-sha-hmac(转换级的名字是ipsec 加密数据的策略,两端必须一
致)
R1(config)#$ 101 permit ip 172.16.1.0 255.255.255.0 192.168.1.0 255.255.255.0(定义感兴趣流,说明哪些流量被加密
,一般是通信点的ip地址)
R1(config)#crypto map smap 1 ipsec-isakmp(定义map 的映射)
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R1(config-crypto-map)#set transform-set ipsec(调用上面的 ipsec)
R1(config-crypto-map)#set peer 210.45.165.2(对等体的ip地址)
R1(config-crypto-map)#match address 101(调用 控制访问列表)
R1(config-crypto-map)#exit
R1(config)#int f0/0
R1(config-if)#crypto map smap(把map 用在端口上,用来对特定的数据来撞击map,而触发加密)
R1(config-if)#
*Mar 1 00:05:55.371: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
上海子公司:
R1>
R1>EN
R1#
R1#config t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config-if)#int f0/0
R1(config-if)#no shu
*Mar 1 00:02:34.987: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Mar 1 00:02:35.987: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
R1(config-if)#ip address 210.45.165.2 255.255.255.0
R1(config-if)#int f0/1
R1(config-if)#no shu
*Mar 1 00:02:55.235: %LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to up
*Mar 1 00:02:56.235: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to up
R1(config-if)#ip address 192.168.1.1 255.255.255.0
R1(config-if)#exit
R1(config)#ip route 0.0.0.0 0.0.0.0 f0/0
R1(config)#crypto isakmp policy 10(第一阶段,定义ike的策略)R1(config-isakmp)#group 2(D-H算法,在思科路由器上有
1 2 5 )
R1(config-isakmp)#hash md5(哈希 用md5)
R1(config-isakmp)#authentication pre-share(预共享密钥)
R1(config-isakmp)#encryption 3des(加密 用3des ,注意此处的加密和下面的转换级的加密 ,加密的对象不一样)
R1(config-isakmp)#exit
R1(config)#crypto isakmp key 0 gaoshan address 210.45.165.1 (定义预共享密钥为gaoshan,对象的ip地址)
R1(config)#crypto ipsec transform-set ipsec esp-des esp-sha-hmac(转换级的名字是ipsec 加密数据的策略,两端必须一
致)
R1(config)#$ 101 permit ip 192.168.1.0 255.255.255.0 172.16.1.0 255.255.255.0(定义感兴趣流,说明哪些流量被加密
,一般是通信点的ip地址)
R1(config)#crypto map smap 1 ipsec-isakmp(定义map 的映射)
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R1(config-crypto-map)#set transform-set ipsec(调用上面的 ipsec)
R1(config-crypto-map)#set peer 210.45.165.1(对等体的ip地址)
R1(config-crypto-map)#match address 101(调用 控制访问列表)
R1(config-crypto-map)#exit
R1(config)#int f0/0
R1(config-if)#crypto map smap(把map 用在端口上,用来对特定的数据来撞击map,而触发加密)
R1(config-if)#
*Mar 1 00:05:55.371: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
测试,从北京pinig 上海:
R2#ping 172.16.1.1 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
..!!!
Success rate is 60 percent (3/5), round-trip min/avg/max = 80/97/112 ms
查看isakmp sa
R2#sh crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
210.45.165.1 210.45.165.2 QM_IDLE 1001 0 ACTIVE
查看 ipsec sa
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (172.16.1.1/255.255.255.255/0/0)
current_peer 210.45.165.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
测试nat 对ipsec 的影响
R2(config)#int f0/0
R2(config-if)#ip nat outside
*Mar 1 00:25:04.215: %LINEPROTO-5-UPDOWN: Line protocol on Interface NVI0, changed state to up
R2(config-if)#int f0/1
R2(config-if)#ip nat inside
R2(config-if)#exit
R2(config)#access-list 1 permit 192.168.1.1 172.16.1.1
R2(config)#ip nat inside
R2(config)#ip nat inside source list 1 interface f0/0 overload
再次测试R2#ping 172.16.1.1 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
.
*Mar 1 00:27:49.571: %CRYPTO-4-RECVD_PKT_NOT_IPSEC: Rec'd packet not an IPSEC paket.
(ip) vrf/dest_addr= /192.168.1.1, src_addr= 172.16.1.1, prot= 1....
Success rate is 0 percent (0/5)
所以ipsec是无法穿越nat 的,因为nat的优先级比ipsec高,我们把要ipsec 封装的流量取出!
R2#config t
Enter configuration commands, one per line. End with CNTL/Z.
R2(config)#no access-list 1
R2(config)#access-list 1 deny 192.168.1.1 172.16.1.1
R2(config)#access-list 1 permit any
R2(config)#end
R2#config t
*Mar 1 00:31:03.451: %SYS-5-CONFIG_I: Configured from console by console
再次测试:
R2#ping 172.16.1.1 source 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 180/216/248 ms
R2#sh crypto ipsec sa
local ident (addr/mask/prot/port): (192.168.1.1/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (172.16.1.1/255.255.255.255/0/0)
current_peer 210.45.165.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
现在就可以加密了,当要去访问北京,就加密!访问其他的就可以通过nat转换出去!这个就是隧道分离技术!
现在分析包查询和包的封装结构:
首先 原始的ip包 :sip 192.168.1.1 dip 172.16.1.1
查询路由表,发现是从f0/0端口出去,送到f0/0,发现有map,并且定义的感兴趣流量也符合!就撞击map,触发esp的封装!封装后的ip数据包结构
sip 210.45.165.1 dip 210.45.165.2 esp sip 192.168.1.1 dip 172.16.1.1
最后从物理口送出!
转载于:https://blog.51cto.com/011010/511684





















 289
289











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








