1 拓扑
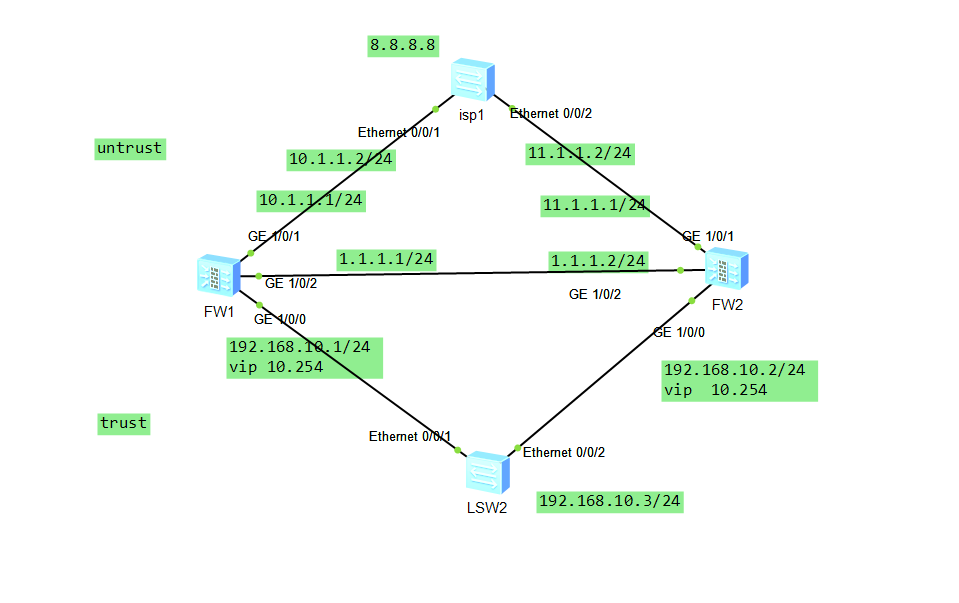
2分析
fw1 和fw2 作为主备 fw1 hrp为主,fw2 hrp 为备
用vgmp 和hrp 联动
isp 用8.8.8.8
lsw2 直接模拟pc 192.168.10.3 上外网8.8.8.8
3配置
1 fw1 上配置
HRP_M[fw1] display current-configuration
2023-02-26 10:32:11.090
!Software Version V500R005C10SPC300
#
sysname fw1
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
hrp enable
hrp interface GigabitEthernet1/0/2 remote 1.1.1.2
hrp timer hello 500
hrp standby config enable
hrp preempt delay 5
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/1
#
update schedule location-sdb weekly Sun 03:24
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 23:41
update schedule av-sdb daily 23:41
update schedule sa-sdb daily 23:41
update schedule cnc daily 23:41
update schedule file-reputation daily 23:41
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%]xm9*o$.rLah^u%S0+*L>s7=0%yN#(}x911;9p"p`go,s7@>@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%^qL'0Y^jhUC*~(=/Ua=%rLDa_G%rHt!;SHg-(71&QenPLDdr@%@%
level 15
manager-user admin
password cipher @%@%edE1=4'1$N`z^B~]nKgWrW#k,8CzS=dY52=_Wg"OGDr'W#nr@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.10.1 255.255.255.0
vrrp vrid 1 virtual-ip 192.168.10.254 active
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.1.1.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 1.1.1.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/2
#
ip route-static 0.0.0.0 0.0.0.0 10.1.1.2
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name hrp
source-zone dmz
source-zone local
destination-zone dmz
destination-zone local
source-address 1.1.1.0 mask 255.255.255.0
destination-address 1.1.1.0 mask 255.255.255.0
action permit
rule name vrrp
source-zone local
source-zone trust
destination-zone local
destination-zone trust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name shangwang
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
rule name wai
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action source-nat easy-ip
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return
2 fw2
#
HRP_S<fw2>display current-configuration
2023-02-26 10:33:24.290
!Software Version V500R005C10SPC300
#
sysname fw2
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
hrp enable
hrp standby-device
hrp interface GigabitEthernet1/0/2 remote 1.1.1.1
hrp timer hello 500
hrp standby config enable
hrp preempt delay 5
hrp track interface GigabitEthernet1/0/0
hrp track interface GigabitEthernet1/0/1
#
update schedule location-sdb weekly Sun 23:06
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 04:46
update schedule av-sdb daily 04:46
update schedule sa-sdb daily 04:46
update schedule cnc daily 04:46
update schedule file-reputation daily 04:46
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%r7XGANP;)Qe=ZMJV5-.6Vf|HbnAR<`bU(V|Mpc)FSzXYf|KV@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%\Rl{.M)s_9Lam):=KvC.$FtC!bm&+|K}X5LLXHPF",JPFtF$@%@%
level 15
manager-user admin
password cipher @%@%Pw)KEC^aV/sZAH4k@BcJ]LcduBenS\arPU.^O2@m4X3,Lcg]@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 192.168.10.2 255.255.255.0
vrrp vrid 1 virtual-ip 192.168.10.254 standby
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 11.1.1.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 1.1.1.2 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/3
undo shutdown
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/2
#
ip route-static 0.0.0.0 0.0.0.0 11.1.1.2
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name hrp
source-zone dmz
source-zone local
destination-zone dmz
destination-zone local
source-address 1.1.1.0 mask 255.255.255.0
destination-address 1.1.1.0 mask 255.255.255.0
action permit
rule name vrrp
source-zone local
source-zone trust
destination-zone local
destination-zone trust
source-address 192.168.10.0 mask 255.255.255.0
destination-address 192.168.10.0 mask 255.255.255.0
action permit
rule name shangwang
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
rule name wai
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action source-nat easy-ip
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
return
4 细节讲解
首先配置防火墙的接口安全域
配置hrp 先保重hrp 主备正常因为下面的配置策略可以正常同步
注意防火墙的上下接口 左右一定要对称这是个细节
nat 的时候一定是先放策略,后放nat 安全策略
验证
5总结
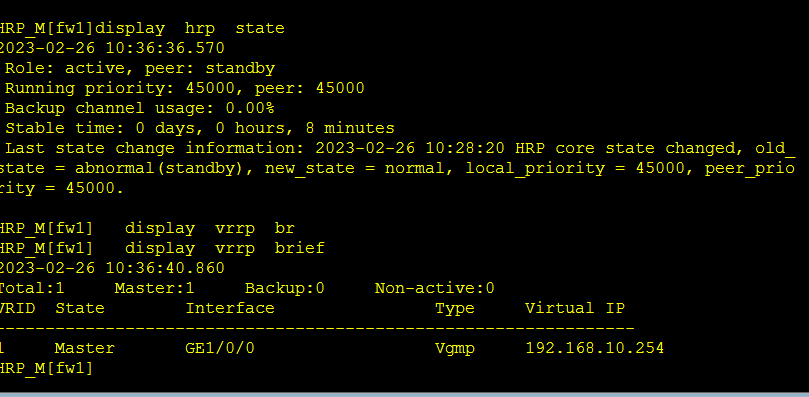
尤其是hrp 的配置
要进行上行链路侦测
查看相关信息
HRP_M<fw2>display firewall session table
2023-02-26 10:39:58.330
Current Total Sessions : 4
icmp VPN: public --> public 192.168.10.3:54443[11.1.1.1:2049] --> 8.8.8.8:204
8
udp VPN: public --> public 1.1.1.1:16384 --> 1.1.1.2:18514
udp VPN: public --> public 1.1.1.1:49152 --> 1.1.1.2:18514
udp VPN: public --> public 1.1.1.2:49152 --> 1.1.1.1:18514
HRP_M<fw2>display vrrp br
HRP_M<fw2>display vrrp brief
2023-02-26 10:40:20.850
Total:1 Master:1 Backup:0 Non-active:0
VRID State Interface Type Virtual IP
----------------------------------------------------------------
1 Master GE1/0/0 Vgmp 192.168.10.254
HRP_M<fw2>
HRP_M<fw2>
HRP_M<fw2>dis
HRP_M<fw2>display hr
HRP_M<fw2>display hrp sta
HRP_M<fw2>display hrp stat
HRP_M<fw2>display hrp state
2023-02-26 10:40:23.920
Role: active, peer: standby (should be "standby-active")
Running priority: 45000, peer: 44998
Backup channel usage: 0.00%
Stable time: 0 days, 0 hours, 0 minutes
Last state change information: 2023-02-26 10:39:35 HRP core state changed, old_
state = normal, new_state = abnormal(active), local_priority = 45000, peer_prior
ity = 44998.





















 4781
4781











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








