高手进阶区(2)
题目5:说我作弊需要证据
题目来源: ISCC-2017
题目描述:X老师怀疑一些调皮的学生在一次自动化计算机测试中作弊,他使用抓包工具捕获到了Alice和Bob的通信流量。狡猾的Alice和Bob同学好像使用某些加密方式隐藏通信内容,使得X老师无法破解它,也许你有办法帮助X老师。X老师知道Alice的RSA密钥为(n, e) = (0x53a121a11e36d7a84dde3f5d73cf, 0x10001) (192.168.0.13)?,Bob的RSA密钥为(n, e) =(0x99122e61dc7bede74711185598c7, 0x10001) (192.168.0.37)
题目附件:一个pcapng文件
解题:
用wireshark打开这个文件并观察抓包情况,选择追踪TCP流,可以看到内容如下:

用base64解码该内容并用二者的RSA私钥解密,对于这种不是很大的数的私钥直接破解就可以。
import gmpy2
import base64
import regex
from Crypto.PublicKey import RSA
class RSAPerson(object):
def __init__(self, e, p, q):
self.n = p * q
self.e = e
self.p = p
self.q = q
self.d = int(gmpy2.invert(e, (p-1)*(q-1)))
self.key = RSA.construct((int(self.n), int(self.e), self.d))
def sign(self, message):
return self.key.sign(message, '')
def verify(self, message, signature):
return self.key.publickey().verify(message, [signature])
def encrypt(self, message):
return self.key.publickey().encrypt(message)
def decrypt(self, message):
return self.key.decrypt(message)
alice = RSAPerson(
0x10001,
38456719616722997,
44106885765559411
)
bob = RSAPerson(
0x10001,
49662237675630289,
62515288803124247
)
packets = []
f= open("decode.txt","wb+")
with open('test.txt') as lines:
for line in lines:
decoded = base64.b64decode(line).decode()
content=regex.findall(r'= (.*?);',decoded,regex.S)
seq = int(content[0],10)#以十进制形式
data = int(content[1][2:-1],16)#-1表示倒数第一个
signature = int (content[2][2:-1],16)
data = bob.decrypt(data)
if alice.verify(data, signature):
data =chr(data)
packets .append((
seq,
data,
signature
)
)
print (''.join([packet[1] for packet in sorted(packets)]))
f.close()
————————————————————————————————————题目6:x_xor_md5
难度系数:
题目来源: RCTF-2015
题目描述:key 不存在
题目附件:
一堆乱码————i5A瀠x]H勍fyU0ILV襰pEê吚>Ssx*K閣&^s开厹oT,sX奻H[劙€?s\R L?7 藦jSx L?7 藦jSx L?7 藦jSx L?7 壵Ⅻ
解题:
题目提示了用异或和MD5,我们可以看到最后几行是比较相似的,可以尝试用最后几行与进行异或操作。
首先,我们用Winhex打开这个文件,显示的文件内容如下:

使用第六行与其他几行分别异或,得到的结果转化为字符为:
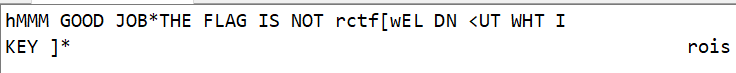
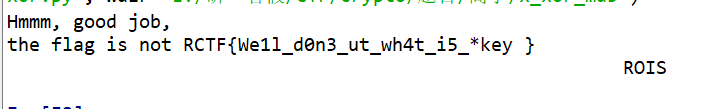
括号中的文字还存在问题,查看十六进制数字我们可以发现,有许多的位置为00,可以大胆猜测这些位置是空格,但是空格对应的是0x20,于是我们可将这些字符与0x20异或。
异或后的结果为:
————————————————————————————————————
题目7:cr2-many-time-secrets
题目来源: alexctf-2017
题目描述:暂无
题目附件:
0529242a631234122d2b36697f13272c207f2021283a6b0c7908
2f28202a302029142c653f3c7f2a2636273e3f2d653e25217908
322921780c3a235b3c2c3f207f372e21733a3a2b37263b313012
2f6c363b2b312b1e64651b6537222e37377f2020242b6b2c2d5d
283f652c2b31661426292b653a292c372a2f20212a316b283c09
29232178373c270f682c216532263b2d3632353c2c3c2a293504
613c37373531285b3c2a72273a67212a277f373a243c20203d5d
243a202a633d205b3c2d3765342236653a2c7423202f3f652a18
2239373d6f740a1e3c651f207f2c212a247f3d2e65262430791c
263e203d63232f0f20653f207f332065262c3168313722367918
2f2f372133202f142665212637222220733e383f2426386b
解题:
这道题使用的是一次一密加密,可以使用Crib dragging attack来破解。
可以使用https://github.com/SpiderLabs/cribdrag中的脚本来破译。

可以参照链接https://www.jianshu.com/p/a00157b981b5中的教程进行破译,最终结果为ALEXCTF{HERE_GOES_THE_KEY}
————————————————————————————————————
题目8:Easy_Crypto
题目来源: 高校网络信息安全运维挑战赛
题目描述:小明在密码学课上新学了一种加密算法,你能帮他看看么
题目附件:
加密方式
get buf unsign s[256]
get buf t[256]
we have key:hello world
we have flag:???
for i:0 to 256
set s[i]:ifor i:0 to 256
set t[i]:key[(i)mod(key.lenth)]for i:0 to 256
set j:(j+s[i]+t[i])mod(256)
swap:s[i],s[j]for m:0 to 37
set i:(i + 1)mod(256)
set j:(j + S[i])mod(256)
swap:s[i],s[j]
set x:(s[i] + (s[j]mod(256))mod(256))
set flag[m]:flag[m]^s[x]fprint flagx to file
密文
暑?H撵V="*細昿#9v;?)+T 嘵7#>y媨?x
解题:
这道题给出的是伪代码,从伪代码中可以看出,这是一个RC4加密,于是使用RC4解密即可。
f = open('enc.txt','r',encoding='ISO-8859-1')
c = f.read()
t = []
key = 'hello world'
ch = ''
j = 0 #初始化
s = list(range(256)) #创建有序列表
for i in range(256):
j = (j + s[i] + ord(key[i % len(key)])) % 256
s[i],s[j] = s[j],s[i]
i = 0 #初始化
j = 0 #初始化
for r in c:
i = (i + 1) % 256
j = (j + s[i]) % 256
s[i], s[j] = s[j], s[i]
x = (s[i] + (s[j] % 256)) % 256
ch += chr(ord(r) ^ s[x])
print(ch)
结果为:EIS{55a0a84f86a6ad40006f014619577ad3}
————————————————————————————————————题目9:OldDriver
难度系数:
题目来源: XCTF 4th-WHCTF-2017
题目描述:有个年轻人得到了一份密文,身为老司机的你能帮他看看么?
题目附件:
[{“c”: 7366067574741171461722065133242916080495505913663250330082747465383676893970411476550748394841437418105312353971095003424322679616940371123028982189502042, “e”: 10, “n”: 25162507052339714421839688873734596177751124036723831003300959761137811490715205742941738406548150240861779301784133652165908227917415483137585388986274803},
{“c”: 21962825323300469151795920289886886562790942771546858500842179806566435767103803978885148772139305484319688249368999503784441507383476095946258011317951461, “e”: 10, “n”: 23976859589904419798320812097681858652325473791891232710431997202897819580634937070900625213218095330766877190212418023297341732808839488308551126409983193},
{“c”: 6569689420274066957835983390583585286570087619048110141187700584193792695235405077811544355169290382357149374107076406086154103351897890793598997687053983, “e”: 10, “n”: 18503782836858540043974558035601654610948915505645219820150251062305120148745545906567548650191832090823482852604346478335353784501076761922605361848703623},
{“c”: 4508246168044513518452493882713536390636741541551805821790338973797615971271867248584379813114125478195284692695928668946553625483179633266057122967547052, “e”: 10, “n”: 23383087478545512218713157932934746110721706819077423418060220083657713428503582801909807142802647367994289775015595100541168367083097506193809451365010723},
{“c”: 22966105670291282335588843018244161552764486373117942865966904076191122337435542553276743938817686729554714315494818922753880198945897222422137268427611672, “e”: 10, “n”: 31775649089861428671057909076144152870796722528112580479442073365053916012507273433028451755436987054722496057749731758475958301164082755003195632005308493},
{“c”: 17963313063405045742968136916219838352135561785389534381262979264585397896844470879023686508540355160998533122970239261072020689217153126649390825646712087, “e”: 10, “n”: 22246342022943432820696190444155665289928378653841172632283227888174495402248633061010615572642126584591103750338919213945646074833823905521643025879053949},
{“c”: 1652417534709029450380570653973705320986117679597563873022683140800507482560482948310131540948227797045505390333146191586749269249548168247316404074014639, “e”: 10, “n”: 25395461142670631268156106136028325744393358436617528677967249347353524924655001151849544022201772500033280822372661344352607434738696051779095736547813043},
{“c”: 15585771734488351039456631394040497759568679429510619219766191780807675361741859290490732451112648776648126779759368428205194684721516497026290981786239352, “e”: 10, “n”: 32056508892744184901289413287728039891303832311548608141088227876326753674154124775132776928481935378184756756785107540781632570295330486738268173167809047},
{“c”: 8965123421637694050044216844523379163347478029124815032832813225050732558524239660648746284884140746788823681886010577342254841014594570067467905682359797, “e”: 10, “n”: 52849766269541827474228189428820648574162539595985395992261649809907435742263020551050064268890333392877173572811691599841253150460219986817964461970736553},
{“c”: 13560945756543023008529388108446940847137853038437095244573035888531288577370829065666320069397898394848484847030321018915638381833935580958342719988978247, “e”: 10, “n”: 30415984800307578932946399987559088968355638354344823359397204419191241802721772499486615661699080998502439901585573950889047918537906687840725005496238621}]
解题:这种给出一个较小的10、明文相同的RSA加密可以使用低加密指数的方法解密
from functools import reduce
import gmpy2
import json, binascii
#求e的逆元
def modinv(a, m):
return int(gmpy2.invert(gmpy2.mpz(a), gmpy2.mpz(m)))
#中国剩余定理
def chinese_remainder(n, a):
sum = 0
#mod的最小公倍数
prod = reduce(lambda a, b: a * b, n) #lambda:匿名函数,参数为a,b;;reduce:会进行累积
for n_i, a_i in zip(n, a):
#求N/ni
p = prod // n_i
#求出一个特解
sum += a_i * modinv(p, n_i) * p
return int(sum % prod)
nset = []
cset = []
with open("enc.txt") as f:
now = f.read().strip('\n')#去掉'\n'
now = eval(now)#计算now所表示的表达式:将字符串转换为字典
for item in now:
nset.append(item['n'])
cset.append(item['c'])
#求出m^e
m = chinese_remainder(nset, cset)
m = int(gmpy2.iroot(gmpy2.mpz(m),10)[0])
print(m)
#print(hex(gmpy2.mpz(m))[2:])
print (binascii.unhexlify(hex(m)[2:]))#返回16进制的二进制表达形式
————————————————————————————————————
题目10:safer-than-rot13
题目来源: tinyctf-2014
题目描述:暂无
题目附件:
XMVZGC RGC AMG RVMG HGFGMQYCD VT VWM BYNO, NSVWDS NSGO RAO XG UWFN AF
HACDGMVWF. AIRVFN AII AMG JVRRVC-XVMC, FYRBIG TVIZ ESV SAH CGQGM XGGC
RVMG NSAC A RYIG TMVR NSG SVWFG ESGMG NSGO EGMG XVMC WCNYI NSG HAO
FVRG IVMH JARG MVWCH NV NAZG NSGR VTT NV EAM. OVWM TIAD YF “CV NSYF
YF CVN JMOBNV RO HGAM”, YC IVEGMJAFG, EYNS WCHGMFJVMGF YCFNGAH VT
FBAJGF, FWMMVWCHGH XO NSG WFWAI “TIAD” NAD ACH JWMIO XMAJGF. GCUVO.
解题:
这道题可以看到是由标点和字符组成的,可以猜想是由一种字母置换算法实现的,于是我们可以通过在线的字母置换来找出可能的结果,例如网站https://quipqiup.com/
结果为flag{no_this_is_not_crypto_my_dear}
————————————————————————————————————
题目11:sleeping-guard
:题目来源: csaw-ctf-2016-quals
题目描述:只有真正的hacker才能看到这张图片
题目场景:
给出了一堆乱码,另外攻防世界上给出的条件不足,应该还有一个python代码
import base64
from twisted.internet import reactor, protocol
import os
PORT = 9013
import struct
def get_bytes_from_file(filename):
return open(filename, "rb").read()
KEY = "[CENSORED]"
def length_encryption_key():
return len(KEY)
def get_magic_png():
image = get_bytes_from_file("./sleeping.png")
encoded_string = base64.b64encode(image)
key_len = length_encryption_key()
print 'Sending magic....'
if key_len != 12:
return ''
return encoded_string
class MyServer(protocol.Protocol):
def connectionMade(self):
resp = get_magic_png()
self.transport.write(resp)
class MyServerFactory(protocol.Factory):
protocol = MyServer
factory = MyServerFactory()
reactor.listenTCP(PORT, factory)
reactor.run()
有事来不及写了,参考一下网站吧嘻嘻嘻嘻嘻https://blog.csdn.net/zz_Caleb/article/details/89365805






















 2799
2799











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








