1.简要介绍
2024年5月28日,国家密码管理局官方网站发布《关于对通过商用密码检测机构(商用密码应用安全性评估业务)资质申请材料审查的机构名单进行公示的通知》,按照《商用密码管理条例》、《商用密码检测机构管理办法》有关规定,国家密码管理局组织对新一批商用密码检测机构(商用密码应用安全性评估业务)资质申请材料进行了审查,现将通过材料审查的19家机构名单予以公示。公示期间,任何机构及个人均可通过申请机构所在地省、自治区、直辖市密码管理部门向我局实名提出书面意见。至此,共有174家密评机构通过商用密码检测机构资质申请材料审查,覆盖32个省、直辖市、自治区、新疆生产建设兵团。如下图:


2.能力验证
2.1IPSec协议
在描述这一块内容的时候,首先我们得熟悉GB/T 36968-2018《信息安全技术 IPSec VPN技术规范》,以便于我们能够更好的理解接下里要讲解的内容。
IPSec协议是我们网络和通信层面现场测评过程当中经常遇到的协议,IPSec协议实际上是一套协议集合,而不是一个单独的协议。它为网络层上的通信数据提供一整套的安全体系结构,包括互联网密钥交换(Internet Key Exchange, IKE)协议、认证头(Authentication Header, AH)协议、封装安全载荷(Encapsulating Security Payload, ESP)协议和用于网络身份鉴别及加密的一些算法等。从工作流程上看,IPSec协议可分为两个环节:IKE是第一个环节,完成通信双方的身份鉴别、确定通信时使用的IPSec安全策略和密钥;第二个环节是使用数据报文封装协议和IKE中协定的IPSec安全策略和密钥,实现对通信数据的安全传输。
AH和ESP协议可以工作在传输模式或隧道模式下。传输模式一般用于端到端的应用场景,只有IP载荷部分被保护,对IP头不做改动;隧道模式对整个IP数据报文提供加密和认证功能,并在此基础上添加新的IP头,一般用于创建虚拟专用网(Virtual Private Networks, VPN)隧道链路。
接下来我们先从IPSec的IKE协议说起,ISAKMP的工作模式分为两个阶段:第一阶段是主模式,通信双方建立一个ISAKMP SA,并实现双方的身份鉴别和密钥交换,得到工作密钥,该工作密钥用于保护第二阶段的协商过程;第二阶段是快速模式,使用已建立的ISAKMP SA提供保护,实现通信双方IPSec SA的协商,确定通信双方IPSec安全策略和会话密钥。其中,IPSec安全策略定义了哪些服务以何种形式提供给IP数据报文,如数据加密服务以SM4的CBC模式实现。
2.2主模式
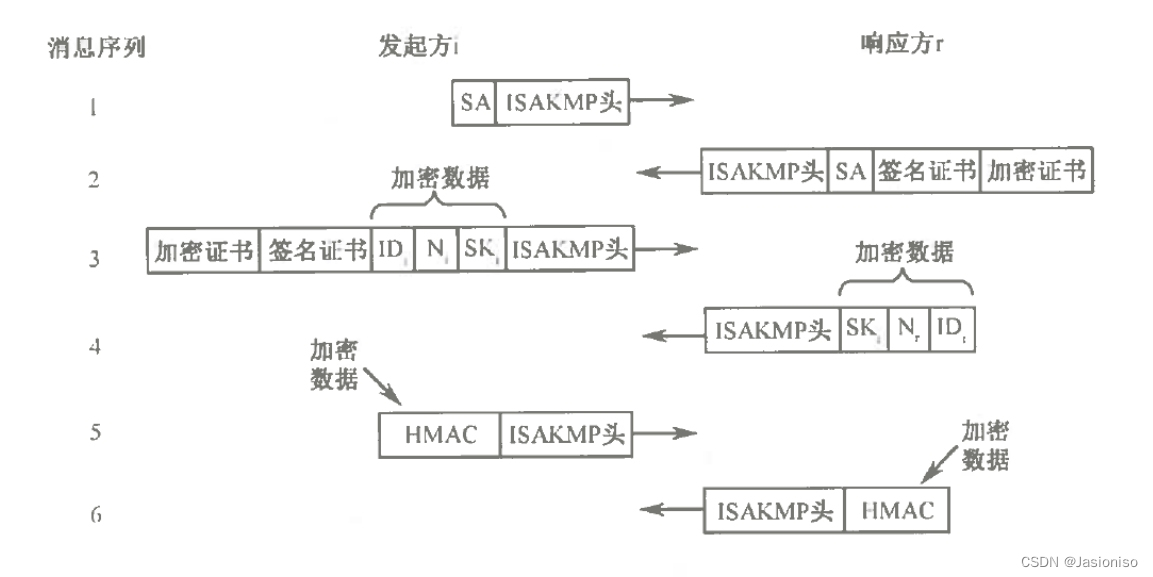
(1)第一阶段:主模式。主模式是一个身份保护的交换,其交换过程由6个消息组成。双方身份的鉴别采用数字证书的方式实现。如下图所示:
然后我们接下来来看一下数据流量包,对照着36968这个标准,可以看到ISAKMP消息头的有关信息,如下图:

然后我们接着往下看,下面是SA安全联盟,和下一个载荷,其中下一个载荷的ID为13,对照标准可以看到是厂商ID,如下图所示:


然后我们来看一下SA的通用载荷,如下图:

然后我们来看一下解释域和情形,如下图:


然后接下来往下分析是建议载荷(下一级载荷)和变换载荷(下下一级),如下图:



然后我们接着往下看第二个消息,如下图:

公钥:0405bffaeec406c8f3f580a6e39c528476c0df2b61065d4a74f476af0fb66890f896acc4b21d8b036d13f17bd4d38234908bedb77f8e3eae870654fc6fa8048d0c
接下来来看一下密钥的用途:(签名/内容确定)

然后我们来看第三个消息,如下图:

2.2.1私钥
我们先用事先给好的PEM格式文件,解析出相应方的私钥,如图所示:
-----BEGIN PRIVATE KEY-----
MIGHAgEAMBMGByqGSM49AgEGCCqBHM9VAYItBG0wawIBAQQgLrRk3CWTe+WZOFSf
TMYwbOocLs3MSRpOO0/AvSmvH5mhRANCAAR9vqVFQ0WBcr07aI5QnC31RYas4AtY
7JQUmflKUKWMZ11vmtr/CJ6BN6djQ6zS81yjCopcz4G3zc5SZqAWueNk
-----END PRIVATE KEY-----

IPSec数据包
响应方私钥:
2eb464dc25937be59938549f4cc6306cea1c2ecdcc491a4e3b4fc0bd29af1f99
这个就是私钥,那如何确定这个的真实性,我们来点成一个G点生成公钥,然后与加密证书里面的公钥进行对比,可以发现是是一致的!
047dbea54543458172bd3b688e509c2df54586ace00b58ec941499f94a50a58c675d6f9adaff089e8137a76343acd2f35ca30a8a5ccf81b7cdce5266a016b9e364

2.2.2加密SKi
然后来看一下SKi,如下图:
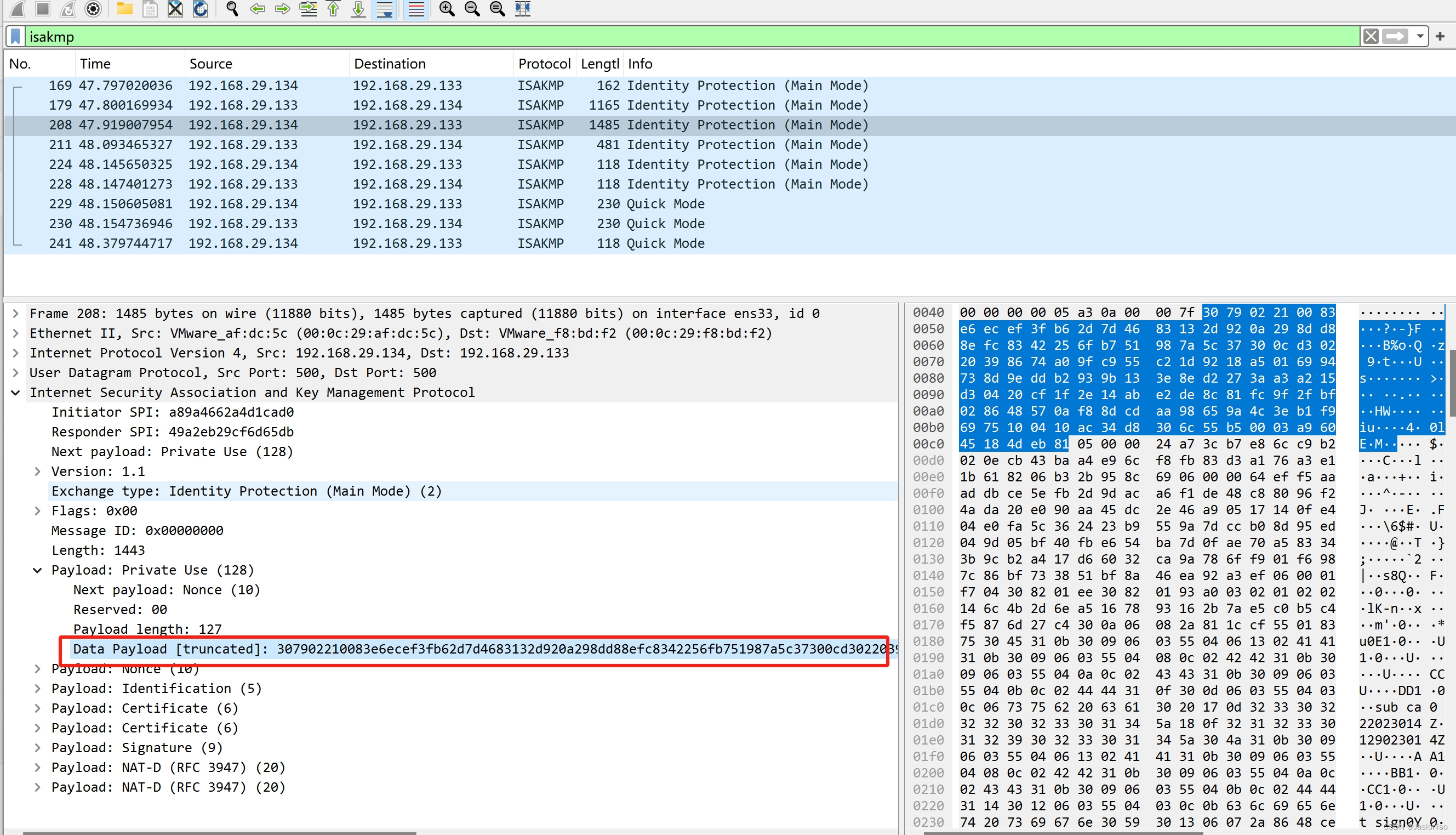
然后用私钥进行解密,如下图:
加密的SKi:
3079
022100
83e6ecef3fb62d7d4683132d920a298dd88efc8342256fb751987a5c37300cd3 :C1一个点
0220
398674a09fc955c21d9218a5016994738d9eddb2939b133e8ed2273aa3a215d3 :C3
0420
cf1f2e14abe2de8c81fc9f2fbf028648570af88dcdaa98659a4c3eb1f9697510
0410
ac34d8306c55b50003a96045184deb81 :C2
83e6ecef3fb62d7d4683132d920a298dd88efc8342256fb751987a5c37300cd3398674a09fc955c21d9218a5016994738d9eddb2939b133e8ed2273aa3a215d3cf1f2e14abe2de8c81fc9f2fbf028648570af88dcdaa98659a4c3eb1f9697510ac34d8306c55b50003a96045184deb81
E6B74813213BFE4759C20225ADE2678E

2.2.3解密NI
然后用响应方的私钥解密加密的SKi(去掉格式),得到SKi明文:
E6B74813213BFE4759C20225ADE2678E
NI密文:
a73cb7e86cc9b2020ecb43baa4e96cf8fb83d3a176a3e11b618206b32b958c69
用SKi明文做密钥,解密NI密文得到NI明文(SM4-CBC ):
IV:00000000000000000000000000000000
NI明文:
450BE90D637A4C714D129D13E15642370000000000000000000000000000000F


2.2.4解密IDi
IDi密文:
eff5aaad
dbce5efb2d9daca6f1de48c88096f24ada20e090aa45dc2e46a90517140fe404e0fa5c362423b9559a7dccb08d95ed049d05bf40fbe654ba7d0fae70a583343b9cb2a417d66032ca9a786ff901f6987c86bf733851bf8a46ea92a3ef
密钥不变:E6B74813213BFE4759C20225ADE2678E
用上一个密文分组的最后一个分组作为IV值:fb83d3a176a3e11b618206b32b958c69
IDi明文:
09000000304A310B3009060355040613024141310B3009060355040813024242310B3009060355040A13024343310B3009060355040B13024444311430120603550403130B636C69656E74207369676E0000000000000000000000000000000F

 2.2.5验签
2.2.5验签
然后接下来进行验签操作,如图所示:
SKi||Ni||IDi||Cert_enc
E6B74813213BFE4759C20225ADE2678E
450BE90D637A4C714D129D13E1564237
09000000304A310B3009060355040613024141310B3009060355040813024242310B3009060355040A13024343310B3009060355040B13024444311430120603550403130B636C69656E74207369676E
05
308201ed30820192a00302010202145b2ebfa257b547c1b04ebce83ad65e6c595addaa300a06082a811ccf550183753045310b3009060355040613024141310b300906035504080c024242310b3009060355040a0c024343310b3009060355040b0c024444310f300d06035504030c067375622063613020170d3233303232323032333031345a180f32313233303132393032333031345a3049310b3009060355040613024141310b300906035504080c024242310b3009060355040a0c024343310b3009060355040b0c0244443113301106035504030c0a636c69656e7420656e633059301306072a8648ce3d020106082a811ccf5501822d034200042920dde9348041de867e49a5caa1936d3241f9b79cb5dcc5c6d59b31f8d88467b05b38505b101f7dbf242bcba73daf394cf0879d3f0e8ec08739f1db00fa770ca35a305830090603551d1304023000300b0603551d0f040403020338301d0603551d0e041604147cf13c4f768f4733a2ffe2e259346b90cfb474a8301f0603551d23041830168014ac61eb22806259083e96c8d17fce745c02af3c99300a06082a811ccf550183750349003046022100e2131845079c82d4a4b09b4990b21bc4e281899b83b226c9916d5c5fee12139f022100e7d3e711561a7a0be92392ed9f94f63ca2aa899d9039611f4472488bf14565ea
拼接完之后(签名消息):
E6B74813213BFE4759C20225ADE2678E450BE90D637A4C714D129D13E156423709000000304A310B3009060355040613024141310B3009060355040813024242310B3009060355040A13024343310B3009060355040B13024444311430120603550403130B636C69656E74207369676E05308201ed30820192a00302010202145b2ebfa257b547c1b04ebce83ad65e6c595addaa300a06082a811ccf550183753045310b3009060355040613024141310b300906035504080c024242310b3009060355040a0c024343310b3009060355040b0c024444310f300d06035504030c067375622063613020170d3233303232323032333031345a180f32313233303132393032333031345a3049310b3009060355040613024141310b300906035504080c024242310b3009060355040a0c024343310b3009060355040b0c0244443113301106035504030c0a636c69656e7420656e633059301306072a8648ce3d020106082a811ccf5501822d034200042920dde9348041de867e49a5caa1936d3241f9b79cb5dcc5c6d59b31f8d88467b05b38505b101f7dbf242bcba73daf394cf0879d3f0e8ec08739f1db00fa770ca35a305830090603551d1304023000300b0603551d0f040403020338301d0603551d0e041604147cf13c4f768f4733a2ffe2e259346b90cfb474a8301f0603551d23041830168014ac61eb22806259083e96c8d17fce745c02af3c99300a06082a811ccf550183750349003046022100e2131845079c82d4a4b09b4990b21bc4e281899b83b226c9916d5c5fee12139f022100e7d3e711561a7a0be92392ed9f94f63ca2aa899d9039611f4472488bf14565ea

签名值:
3045
022100
8fd24caa07d506eb6b88ebd5852839e127e875738747a8d2c356150e4b95c6f2
0220
14a9f5aea118004276fbd8437b0f6e5db84d138b058236f7d6656f3dedefd740
8fd24caa07d506eb6b88ebd5852839e127e875738747a8d2c356150e4b95c6f214a9f5aea118004276fbd8437b0f6e5db84d138b058236f7d6656f3dedefd740

公钥:
04
2d617e74d5586dde23d2490fbd468e30f11d012d50a8f392cd1849b10b167e9a0661f7e3a2a00ee7ec4718ed937b4ab2c50aa0d341d15e4095743b3850af6d3c

验签:


2.2.6Right数据包
同样的数据我们拿来Right数据包来解密第四个数据包,具体的流程细节和上面一样,这里就不过多描述了,直接看图。
Right私钥:
-----BEGIN PRIVATE KEY-----
MIGHAgEAMBMGByqGSM49AgEGCCqBHM9VAYItBG0wawIBAQQguz0M4/6qUhgHAxuG
WI2NPtNciIwmYAN4AUDoBEka1tehRANCAAQpIN3pNIBB3oZ+SaXKoZNtMkH5t5y1
3MXG1Zsx+NiEZ7BbOFBbEB99vyQry6c9rzlM8IedPw6OwIc58dsA+ncM
-----END PRIVATE KEY-----
bb3d0ce3feaa521807031b86588d8d3ed35c888c266003780140e804491ad6d7
---------------------------------------------------------------------------
3079022100
e2fee5b1439937014b7ad1a585f4a62910787a7c885884c1370cd9fb8dadd12c
0220
1c2f5ab9ba02bc9d9c21cf18afaa6b64f0b0a733bd730508d6567f9faac722aa
0420
00376aa46646d90577b5ab0170f97043356acef83504b8a4b9ae159a0e834fc3
0410
01734e922fa8c88ad6814c59264e9f21
解密得到:
93754381265FEBCF025A6C0D53ABF6D3


Nr密文:
a469aa4b7374d33262e76b20ed2f65e6
ccbd5799630f7f8e68320b2f121e0a26
Nr明文:(用解密得到的SKr明文做密钥,使用SM4-CBC模式进行解密)
098664CD2C46BFBC8C5F5DCB856E6481
0000000000000000000000000000000F

IDr密文:
07
1d
406e
e84d676c2837ba45490b650b27f664aa7a732aef599c69d06b25fd9be2e7f4f11d5306aa2ced370b6958a6b4a9c91b3ddb2fb6f61673d897fdf12f73796643992e7cc9d996cac9ddaa571b2ec85a68150fad375d6e94b62c28dfcd8d
拼接完以后:
071d406ee84d676c2837ba45490b650b27f664aa7a732aef599c69d06b25fd9be2e7f4f11d5306aa2ced370b6958a6b4a9c91b3ddb2fb6f61673d897fdf12f73796643992e7cc9d996cac9ddaa571b2ec85a68150fad375d6e94b62c28dfcd8d
解密IDr明文:
09000000304A310B3009060355040613024141310B3009060355040813024242310B3009060355040A13024343310B3009060355040B13024444311430120603550403130B736572766572207369676E
0000000000000000000000000000000F

------------------------------------------------------------------------
SKr||Nr||IDr||Cert_enc_r
93754381265FEBCF025A6C0D53ABF6D3
098664CD2C46BFBC8C5F5DCB856E6481
09000000304A310B3009060355040613024141310B3009060355040813024242310B3009060355040A13024343310B3009060355040B13024444311430120603550403130B736572766572207369676E
加密证书(在第二个数据包里面找加密证书):
05
308201eb30820192a003020102021468d892e963aca045620e799d6fc31d937433e57c300a06082a811ccf550183753045310b3009060355040613024141310b300906035504080c024242310b3009060355040a0c024343310b3009060355040b0c024444310f300d06035504030c067375622063613020170d3233303232323032333031345a180f32313233303132393032333031345a3049310b3009060355040613024141310b300906035504080c024242310b3009060355040a0c024343310b3009060355040b0c0244443113301106035504030c0a73657276657220656e633059301306072a8648ce3d020106082a811ccf5501822d034200047dbea54543458172bd3b688e509c2df54586ace00b58ec941499f94a50a58c675d6f9adaff089e8137a76343acd2f35ca30a8a5ccf81b7cdce5266a016b9e364a35a305830090603551d1304023000300b0603551d0f040403020338301d0603551d0e0416041467a5add59476e05a9c5e56b8860ff13b28eeec54301f0603551d23041830168014ac61eb22806259083e96c8d17fce745c02af3c99300a06082a811ccf550183750347003044022047593579c4adec8db7df98c4aae1661c1139a5ef1293f22a3aa412d09becd6e602206e57301d177946956fd39cb5ac603902cd17c7517ed8941ecc985ea7db6958c8
拼接(消息):
93754381265FEBCF025A6C0D53ABF6D3098664CD2C46BFBC8C5F5DCB856E648109000000304A310B3009060355040613024141310B3009060355040813024242310B3009060355040A13024343310B3009060355040B13024444311430120603550403130B736572766572207369676E05308201eb30820192a003020102021468d892e963aca045620e799d6fc31d937433e57c300a06082a811ccf550183753045310b3009060355040613024141310b300906035504080c024242310b3009060355040a0c024343310b3009060355040b0c024444310f300d06035504030c067375622063613020170d3233303232323032333031345a180f32313233303132393032333031345a3049310b3009060355040613024141310b300906035504080c024242310b3009060355040a0c024343310b3009060355040b0c0244443113301106035504030c0a73657276657220656e633059301306072a8648ce3d020106082a811ccf5501822d034200047dbea54543458172bd3b688e509c2df54586ace00b58ec941499f94a50a58c675d6f9adaff089e8137a76343acd2f35ca30a8a5ccf81b7cdce5266a016b9e364a35a305830090603551d1304023000300b0603551d0f040403020338301d0603551d0e0416041467a5add59476e05a9c5e56b8860ff13b28eeec54301f0603551d23041830168014ac61eb22806259083e96c8d17fce745c02af3c99300a06082a811ccf550183750347003044022047593579c4adec8db7df98c4aae1661c1139a5ef1293f22a3aa412d09becd6e602206e57301d177946956fd39cb5ac603902cd17c7517ed8941ecc985ea7db6958c8
响应方签名公钥:
04
05bffaeec406c8f3f580a6e39c528476c0df2b61065d4a74f476af0fb66890f8
96acc4b21d8b036d13f17bd4d38234908bedb77f8e3eae870654fc6fa8048d0c
签名值:
3046022100
c8ac036fbce28ff4e7f5366c704e405b23753b8ca95a4319b8657ea1fb46534e
022100
f14eeb8858614a62409af9aa1037e2b4b42b155e931b359cd792189ca90e09d4
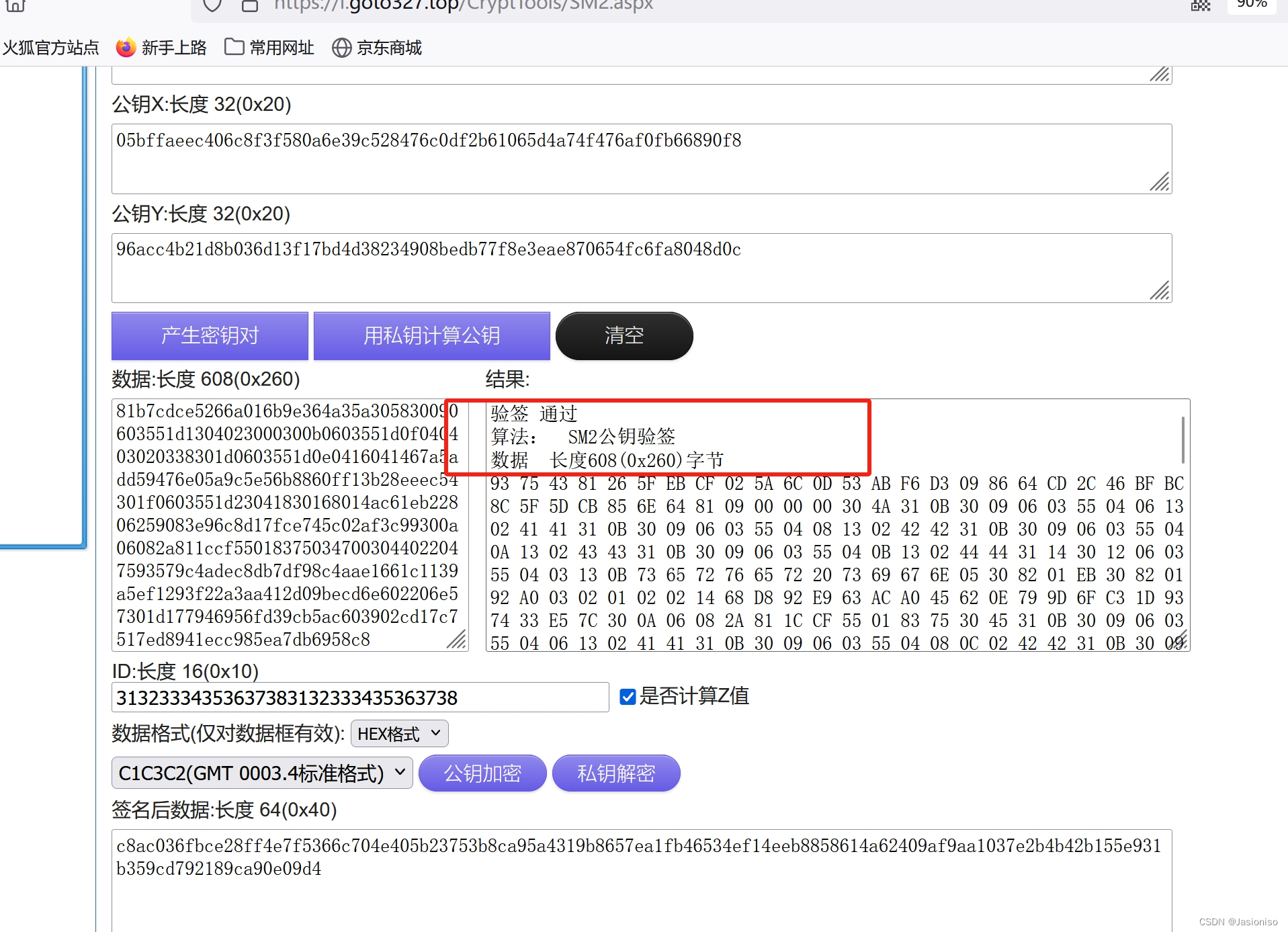

2.2.7HASH(Ni||Nr)
HASH(Ni||Nr):
450BE90D637A4C714D129D13E1564237
098664CD2C46BFBC8C5F5DCB856E6481
450BE90D637A4C714D129D13E1564237098664CD2C46BFBC8C5F5DCB856E6481
拼接做SM3哈希:
83FDDF2B5DC8BD853C343EE68F780CFAF2E37FDDE3998DA2C76A4B368816E972


接下来我们来求SKEYID、SKEYID_d、SKEYID_a、SKEYID_e
CKY-I||CKY-R :a89a4662a4d1cad049a2eb29cf6d65db
将HASH(Ni||Nr)作为密钥输入,对CKY-I||CKY-R进行哈希
SKEYID :AF75DB413C0BABF64D866F08B53432CE027C59A975A30B284B31236C0689113E

SKEYID_d: D07385874BD72FA3EC6D42714E643A94DE6644D24F2F50239892F8EF478293E7

SKEYID_a: 51B531818C073C1B72CA8E9A883E6B19755604445ABEDF57DF176D575F4320FE

SKEYID_e:F60661271D29C5093894DACDACF5378C13AEEA3D52B2BE0CE06AD87EDBC9F7D1
密钥:F60661271D29C5093894DACDACF5378C
13AEEA3D52B2BE0CE06AD87EDBC9F7D1

2.2.8消息5和消息6

HASHi
IV=HASH(SKi||SKr):
E6B74813213BFE4759C20225ADE2678E
93754381265FEBCF025A6C0D53ABF6D3
E6B74813213BFE4759C20225ADE2678E93754381265FEBCF025A6C0D53ABF6D3
HASH的结果:
DE788AA1E41303BAF97136E86F82F2FC05FD904DF03879C49C1E1A9A868B0E1A
IV值:DE788AA1E41303BAF97136E86F82F2FC
05FD904DF03879C49C1E1A9A868B0E1A

然后我们来解密第5个数据包,如下图:
密文:c60c2e7689fa1519256ec690bbfb7d6380a52de3d51ce8fb1ac5923a84ceac86b958be5fa74277fc91b3bfd3d1cbf7e0
密钥:F60661271D29C5093894DACDACF5378C
IV值:DE788AA1E41303BAF97136E86F82F2FC

解密:
000000245855A82383911ACACE237A72D2C6427AA18D552FC4D80D13288104A7F9DA2F3C000000000000000000000000
00(下一个载荷)
00(保留的)
0024(长度)
5855A82383911ACACE237A72D2C6427AA18D552FC4D80D13288104A7F9DA2F3C (HASH值)
000000000000000000000000 (填充)
接下来我们来验证一下HASH值:
我们把CKY-I||CKY-R拿下来,再拼接上SAi_b||IDi_b,其中

求HASHi
CKY-I||CKY-R :a89a4662a4d1cad049a2eb29cf6d65db
SAi_b||IDi_b:
SAi_b:
0d000034
0000000100000001000000280001000100000020010100008001007f800200148003000a80140002800b0001800c3de0
IDi_b:
09000000304A310B3009060355040613024141310B3009060355040813024242310B3009060355040A13024343310B3009060355040B13024444311430120603550403130B636C69656E74207369676E
CKY-I||CKY-R||SAi||IDi 然后拼接(消息):
a89a4662a4d1cad049a2eb29cf6d65db0000000100000001000000280001000100000020010100008001007f800200148003000a80140002800b0001800c3de009000000304A310B3009060355040613024141310B3009060355040813024242310B3009060355040A13024343310B3009060355040B13024444311430120603550403130B636C69656E74207369676E
密钥SKEYID:
AF75DB413C0BABF64D866F08B53432CE027C59A975A30B284B31236C0689113E
5855A82383911ACACE237A72D2C6427AA18D552FC4D80D13288104A7F9DA2F3C (HASH值)

在这里可以发现解出来的东西是一样的!
2.3快速模式

第二阶段
hash(上一阶段最后一个分组密文||MSGID)
dd55ad19832211a7909550c3472615c55feddb949b5ee01f9cfe6d9e228e3a1d
d92048953a172891b194012f8db5f7b0 (消息6的最后一个分组)
MSGID:cc2d2221
d92048953a172891b194012f8db5f7b0cc2d2221
hash:
56E6DFC945499AE8ACA47A6CA9CF2ADA
005AC24E502D2AD621591EFD5D57BDBE

第一个包的密文:
0480348d01d6635a2c2a912fbdb677f0e718ca239c1758319069d74efc0601c4bdb814f8d5575add1acc7075723263a65270547f464345b292753cd5c759fde4c94048f5ced4b161679c75a3cb0fec2d80c292df8b6a567b916cb0cdb57d30097f841630cfb8081cc8b65b0be54dcd45acef18456a1dbb1b764b4a4164b4ffab0b364556de52ec116c1014112986fd82359b204f92800504072e2994af771b88
第一个包解密:
IV值:56E6DFC945499AE8ACA47A6CA9CF2ADA
密钥:F60661271D29C5093894DACDACF5378C
010000240C52ABF2BEE8337F08694EE22B97E4571EF491EF5C88EDA04A5F4C3FC82C03D90A00003C00000001000000010000003000030401C515ECD500000024017F000080050014800400018001000180021734800100020002000400086470050000144FDBBCE1785046B21F1EB00AFBEC31C40500001004000000AC101D00FFFFFF000000001004000000AC101C00FFFFFF00000000000000000000000000
分解:
01 下一个载荷:SA
00
0024
0C52ABF2BEE8337F08694EE22B97E4571EF491EF5C88EDA04A5F4C3FC82C03D9
SA载荷Nounce
0A
00
003C
00000001 解释域
00000001 情形
子载荷:建议载荷
00 下一个载荷:无
00
0030
00
03 协议类型ESP
04 SPI长度
01 变换数
C515ECD5 变长的SPI
变换载荷
00
00
0024
01 变换号
7F 变换ID:SM4
0000
80050014 SM3-HMAC鉴别
80040001 隧道封装
80010001 生存类型:秒
80021734 生存期:5940秒=99分钟
800100020002000400086470
nounce包
05 下一载荷:ID
00
0014
4FDBBCE1785046B21F1EB00AFBEC31C4
IDi包
05
00
0010
04000000AC101D00FFFFFF00
IDr包
00
00
0010
04000000AC101C00FFFFFF00
000000000000000000000000 填充
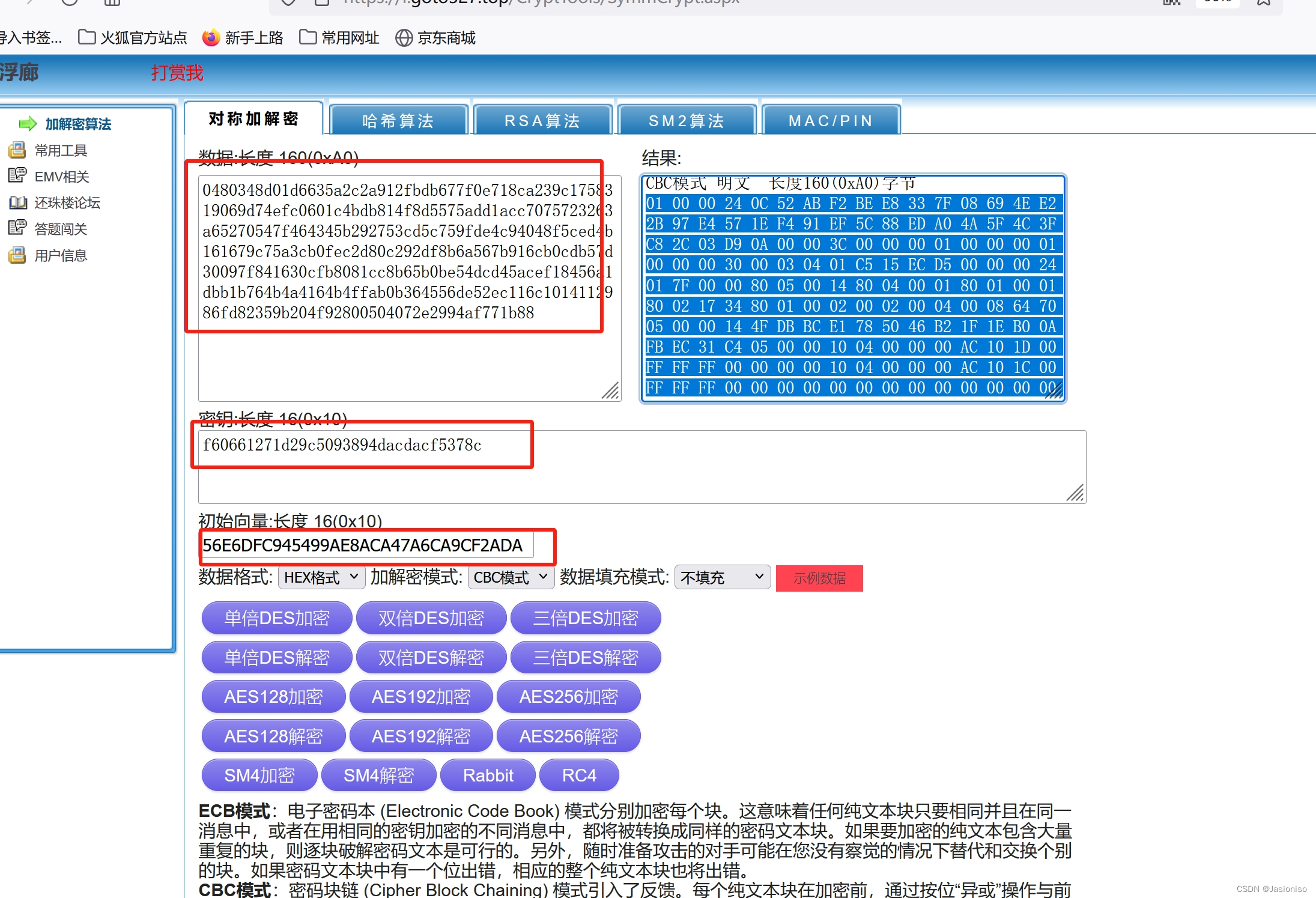
同理,解析出第二个和第三个包,这里不再描述。
第二个包密文
49813dfd83a4c3c3bf2950290904fc4237c90e5e45e4991a60336a91ee6848de0ca5964fbb5af6f0aa607ebcc8188e9774a8ac79f1f93b1a72140625c3588eea7e1e4b137783c948e9bd7a060f8d36821b5198c7e3eb41a5ad4e3f30acf978f80930e47a79e3ddae43fb9d1463c6dbcb45ad9d37ead1eb54fbcf39058a9e9c39f7a9c43c6c1aecc5a1a58522abd59609
20f20261bf78e32847d2f84e7f4cbdb2
第二个包解密
01000024d90aad574e561b98e0fd9136cc217e7e4c8300cf8c3829aa2c650e8de73e7c210a00003c00000001000000010000003000030401c713ad0600000024017f00008005001480040001800100018002173480010002000200040008647005000014106bcaa925dc5b6d994efc88369d60590500001004000000ac101d00ffffff000000001004000000ac101c00ffffff00000000000000000000000000
第三个包解密
00
00
0024
c6125d6cc79a13a4fa8f0806e7fed72ec4280f5a64b5a0a67789bd8e698036c9
000000000000000000000000填充

























 6229
6229

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










