Route-based site-to-site IPSec to establish connection firstly between two sites. And the routing is also pre-defined between two sites. When there's a route available, the local private network can access remote private one.

1.Create the virtual tunnel interface
This is the first difference from policy-based.
Below is the result:

Below is the configuration after click 'new' from above page in the upper right corner.

2. IKE Phase 1
The same as policy-based.
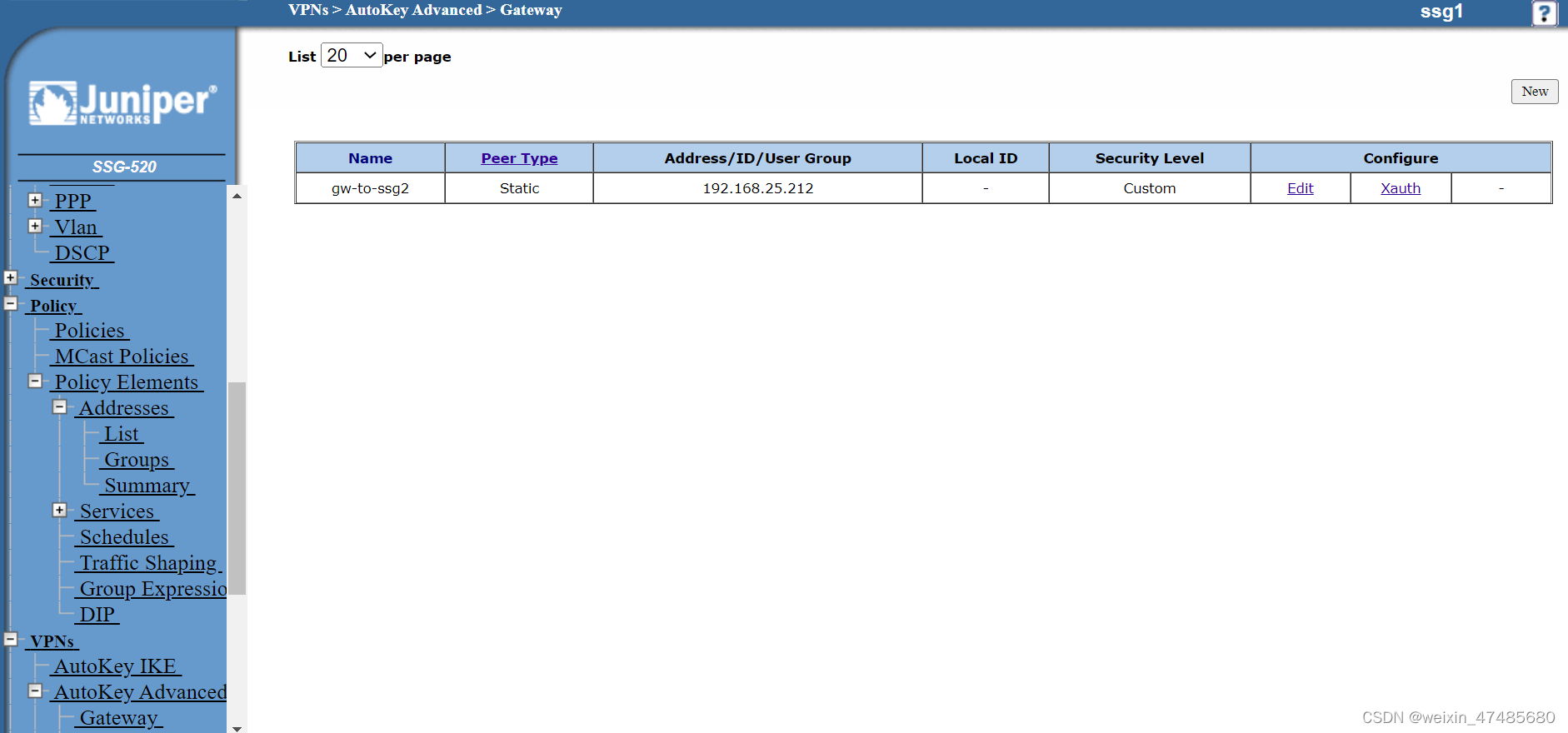


3. IKE Phase 2
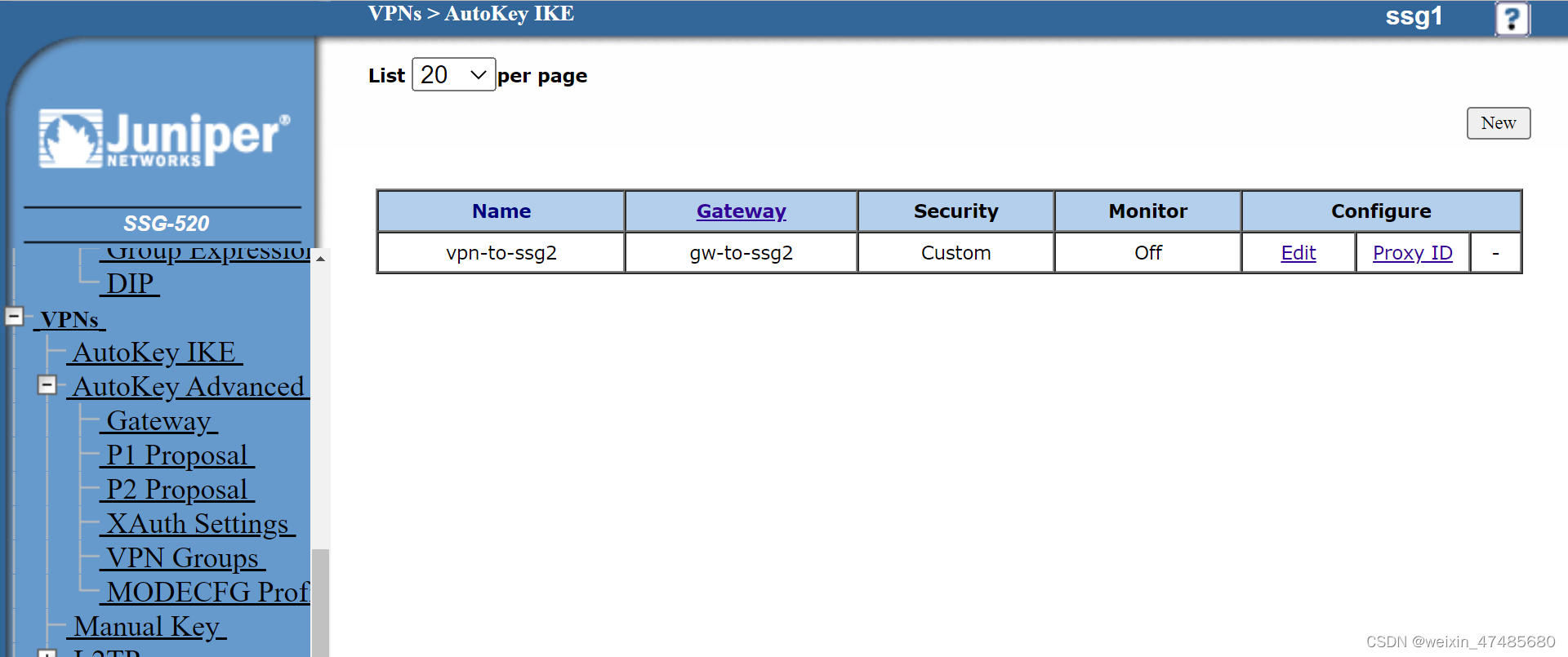

Below is the second difference from policy-based.

4. Configure routing
This is the third difference from the policy-based.
We don't need policy, so we don't need to configure address entries and policies.
The static routing is also different from the policy-based. The gate-way of route-based is the remote end of the tunnel, while the gate-way of the policy-bases is the WAN interface(public IP) of the remote end.

After about above, it shows below status: The SPI is empty. It means not yet negotiated.
ssg1-> get sa
total configured sa: 1
HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys
00000006< 192.168.25.212 500 esp:3des/sha1 00000000 expir unlim I/I -1 0
00000006> 192.168.25.212 500 esp:3des/sha1 00000000 expir unlim I/I -1 0
ssg1-> get ike cookiesIKEv1 SA -- Active: 0, Dead: 0, Total 0
IKEv2 SA -- Active: 0, Dead: 0, Total 0ssg1->
5. Test connectivity from R3 to R4.
R3-dmz#ping 10.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.2.2.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
R3-dmz#
ssg1-> get ike cookies
IKEv1 SA -- Active: 1, Dead: 0, Total 1
80522f/0003, 192.168.25.211:500->192.168.25.212:500, PRESHR/grp2/3DES/SHA, xchg(2) (gw-to-ssg1/grp-1/usr-1)
resent-tmr 26849536 lifetime 28800 lt-recv 28800 nxt_rekey 28637 cert-expire 0
initiator, err cnt 0, send dir 0, cond 0x0
nat-traversal map not available
ike heartbeat : disabled
ike heartbeat last rcv time: 0
ike heartbeat last snd time: 0
XAUTH status: 0
DPD seq local 0, peer 0
IKEv2 SA -- Active: 0, Dead: 0, Total 0ssg1-> get sa
total configured sa: 1
HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys
00000006< 192.168.25.212 500 esp:3des/sha1 823c3df9 3431 unlim A/- -1 0
00000006> 192.168.25.212 500 esp:3des/sha1 2fab33cf 3431 unlim A/- -1 0
ssg1->

6. Break down the connection and reconnect.
Before break down:
ssg1-> get sa
total configured sa: 1
HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys
00000002< 192.168.25.212 500 esp:3des/sha1 823c3df5 2203 unlim I/I -1 0
00000002> 192.168.25.212 500 esp:3des/sha1 2fab33cb 2203 unlim I/I -1 0
Go to web page bind the Virtual-Private-Network to none.
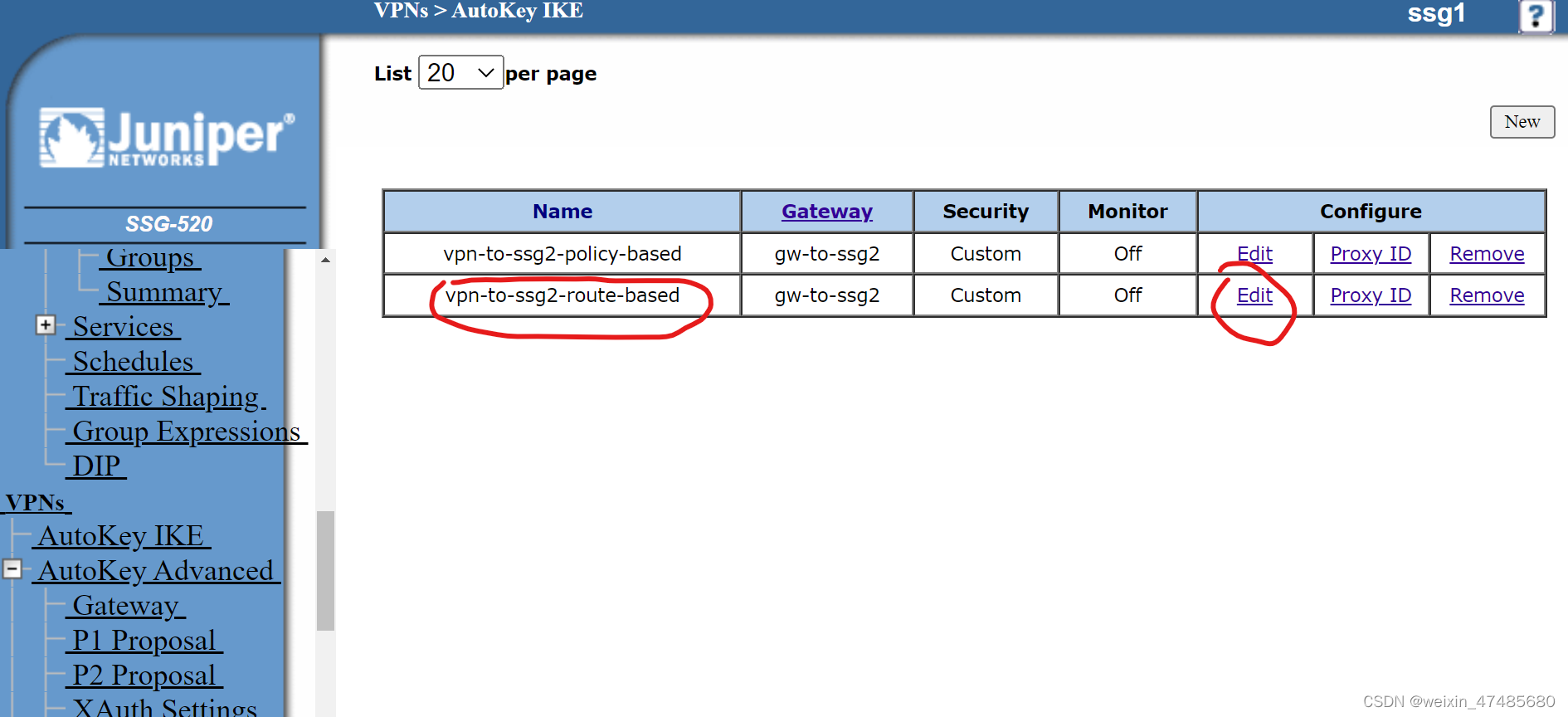


Click Return and the OK.
Check the SA again:
ssg1-> get sa
total configured sa: 0
HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys
ssg1->
Note that even unbind to the tunnel, the IKE phase 1 is not changed and always there.
Re bind to the tunnel again:

Check the SA again:
The IKE Phase 2 SA re-established with expir state due to no traffic.
The HEX ID is from 00000002 to 00000003, with expir sate.
So when re-bind to tunnel, phase 1 is always there, phase 2 needs to negotiate again to active the SA when traffic comes. If no traffic comes, it keeps expir state untill traffic comes.
ssg1-> get sa
total configured sa: 1
HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys
00000003< 192.168.25.212 500 esp:3des/sha1 00000000 expir unlim I/I -1 0
00000003> 192.168.25.212 500 esp:3des/sha1 00000000 expir unlim I/I -1 0
At the moment, let's see what happens at the remote side of the tunnel. It shows that the phase 2 SA is always there active:
ssg2-> get sa
total configured sa: 1
HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys
00000003< 192.168.25.211 500 esp:3des/sha1 2fab33cc 3346 unlim I/I -1 0
00000003> 192.168.25.211 500 esp:3des/sha1 823c3df6 3346 unlim I/I -1 0
Next, we send traffic to trigger the local Virtual-Private-Network point from expir to active.
Due to it needs phase 2 negotiate again, so the first packet of ping is timeout.
R3-dmz#ping 10.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.2.2.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 4/4/4 ms
R3-dmz#
The SA is active from expir.
ssg1-> get sa
total configured sa: 1
HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys
00000003< 192.168.25.212 500 esp:3des/sha1 823c3df8 3589 unlim A/- -1 0
00000003> 192.168.25.212 500 esp:3des/sha1 2fab33ce 3589 unlim A/- -1 0
Remote:
ssg2-> get sa
total configured sa: 1
HEX ID Gateway Port Algorithm SPI Life:sec kb Sta PID vsys
00000003< 192.168.25.211 500 esp:3des/sha1 2fab33ce 3356 unlim A/- -1 0
00000003> 192.168.25.211 500 esp:3des/sha1 823c3df8 3356 unlim A/- -1 0
From the wireshark capture, we can see only phase 2 happens when traffic comes after re-bind to the tunnel.

7. How to enable routing protocols
Firstly create OSPF instance for the virtual router.



After create the OSPF instance, the OSPF tab will show in the interface page as below:

The check the routing table, the OSPF route is there:

Check OSPF the neignbors:
ssg1-> get int tun.1 proto ospf
VR: trust-vr RouterId: 192.168.25.211
----------------------------------
Interface: tunnel.1
IpAddr: 10.1.12.1/24, OSPF: enabled, Router: enabled
Type: Point-to-Point Area: 0.0.0.0 Priority: 1 Cost: 10 Passive: No
Transit delay: 1s Retransmit interval: 5s Hello interval: 10s
Router Dead interval: 40s Authentication-Type: None
Ignore-MTU: no Reduce-flooding: no Demand-circuit: no
State: Point-to-Point
Neighbors:
RtrId: 192.168.25.212 IpAddr: 10.1.12.2 Pri: 1 State: Full
ssg1-> get int e0/0 proto ospf
VR: trust-vr RouterId: 192.168.25.211
----------------------------------
Interface: ethernet0/0
IpAddr: 10.1.1.1/24, OSPF: enabled, Router: enabled
Type: Broadcast Area: 0.0.0.0 Priority: 1 Cost: 1 Passive: No
Transit delay: 1s Retransmit interval: 5s Hello interval: 10s
Router Dead interval: 40s Authentication-Type: None
Ignore-MTU: no Reduce-flooding: no
State: Backup Designated Router DR: 10.1.1.2 BDR: 10.1.1.1(self)
Neighbors:
RtrId: 3.3.3.3 IpAddr: 10.1.1.2 Pri: 1 State: Full
ssg1->ssg1-> get route
IPv4 Dest-Routes for <untrust-vr> (0 entries)
--------------------------------------------------------------------------------------
H: Host C: Connected S: Static A: Auto-Exported
I: Imported R: RIP/RIPng P: Permanent D: Auto-Discovered
N: NHRP
iB: IBGP eB: EBGP O: OSPF/OSPFv3 E1: OSPF external type 1
E2: OSPF/OSPFv3 external type 2 trailing B: backup route
IPv4 Dest-Routes for <trust-vr> (11 entries)
--------------------------------------------------------------------------------------
ID IP-Prefix Interface Gateway P Pref Mtr Vsys
--------------------------------------------------------------------------------------
* 15 3.3.3.3/32 eth0/0 10.1.1.2 O 60 2 Root
* 21 4.4.4.4/32 tun.1 10.1.12.2 eB 40 0 Root
22 4.4.4.4/32 tun.1 10.1.12.2 O 60 12 Root
* 9 10.1.12.1/32 tun.1 0.0.0.0 H 0 0 Root
* 4 10.1.1.1/32 eth0/0 0.0.0.0 H 0 0 Root
* 5 192.168.25.0/24 eth0/1 0.0.0.0 C 0 0 Root
* 6 192.168.25.211/32 eth0/1 0.0.0.0 H 0 0 Root
* 3 10.1.1.0/24 eth0/0 0.0.0.0 C 0 0 Root
* 20 10.2.2.0/24 tun.1 10.1.12.2 eB 40 0 Root
23 10.2.2.0/24 tun.1 10.1.12.2 O 60 11 Root
* 8 10.1.12.0/24 tun.1 0.0.0.0 C 0 0 Root
ssg1->
























 7000
7000

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








