破解关键:
通过定位而nop掉关键跳转,使MessageBox()弹出GOOd
首先将程序载入OD,F9开始运行,有两种登录方式

(1)输入序列号和名称和(2)单独输入序列号
先随便输入,点击check it baby,结果弹窗弹出以下内容

此时先不要点击确定按钮,回到OD暂停程序,然后查看K窗口,因为有弹窗的出现,在OD的调用函数中去寻找MessageBox函数
K:调用堆栈,可以通过它找到调用某一个函数的位置,通常会被用于查找关键代码
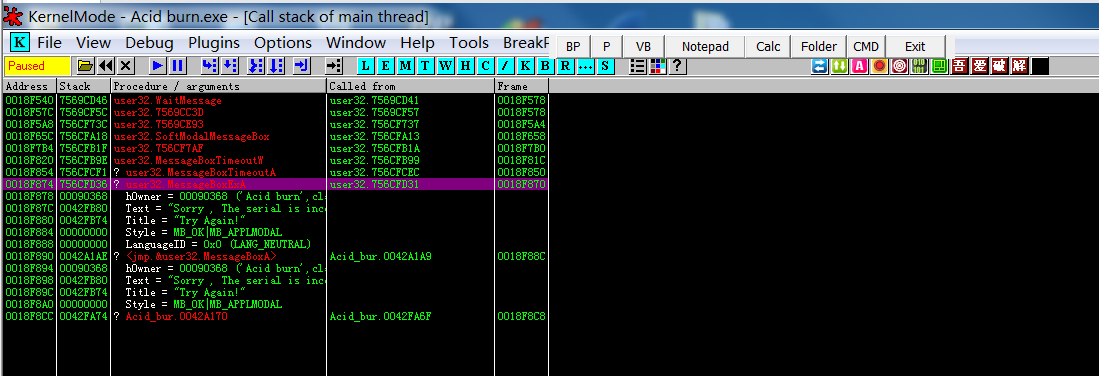

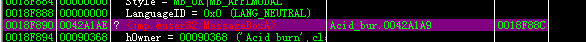
根据函数的范围
可以判断出第一个MessageBox位于系统领空,而第二个位于用户领空
所以选中第二个MessageBox右键——show call 查看相应调用
0042A170 /$ 55 push ebp
0042A171 |. 8BEC mov ebp,esp
0042A173 |. 83C4 F4 add esp,-0xC
0042A176 |. 53 push ebx
0042A177 |. 56 push esi
0042A178 |. 57 push edi
0042A179 |. 8BF9 mov edi,ecx
0042A17B |. 8BF2 mov esi,edx
0042A17D |. 8BD8 mov ebx,eax
0042A17F |. E8 7CB4FDFF call <jmp.&user32.GetActiveWindow> ; [GetActiveWindow
0042A184 |. 8945 F8 mov [local.2],eax
0042A187 |. 33C0 xor eax,eax
0042A189 |. E8 12A0FFFF call Acid_bur.004241A0
0042A18E |. 8945 F4 mov [local.3],eax
0042A191 |. 33C0 xor eax,eax
0042A193 |. 55 push ebp
0042A194 |. 68 D0A14200 push Acid_bur.0042A1D0
0042A199 |. 64:FF30 push dword ptr fs:[eax]
0042A19C |. 64:8920 mov dword ptr fs:[eax],esp
0042A19F |. 8B45 08 mov eax,[arg.1]
0042A1A2 |. 50 push eax ; /Style = MB_OK|MB_APPLMODAL
0042A1A3 |. 57 push edi ; |Title = "@"
0042A1A4 |. 56 push esi ; |Text = 00000102 ???
0042A1A5 |. 8B43 24 mov eax,dword ptr ds:[ebx+0x24] ; |
0042A1A8 |. 50 push eax ; |hOwner = NULL
0042A1A9 |. E8 FAB5FDFF call <jmp.&user32.MessageBoxA> ; \MessageBoxA
在栈帧初始部分push ebp下断点
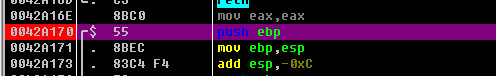
然后运行程序,继续点击check it baby,此时程序在0042A170断点处断开,查看堆栈窗口
是谁调用了MessageBox函数

点击该字符串右键——follow in disassembler
0042FA74 |. /E9 BE000000 jmp Acid_bur.0042FB37
0042FA79 |> |8D55 F0 lea edx,[local.4]
0042FA7C |. |8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA82 |. |E8 D1AFFEFF call Acid_bur.0041AA58
0042FA87 |. |8B45 F0 mov eax,[local.4]
0042FA8A |. |0FB600 movzx eax,byte ptr ds:[eax]
0042FA8D |. |F72D 50174300 imul dword ptr ds:[0x431750]
0042FA93 |. |A3 50174300 mov dword ptr ds:[0x431750],eax
0042FA98 |. |A1 50174300 mov eax,dword ptr ds:[0x431750]
0042FA9D |. |0105 50174300 add dword ptr ds:[0x431750],eax
0042FAA3 |. |8D45 FC lea eax,[local.1]
0042FAA6 |. |BA ACFB4200 mov edx,Acid_bur.0042FBAC ; CW
0042FAAB |. |E8 583CFDFF call Acid_bur.00403708
0042FAB0 |. |8D45 F8 lea eax,[local.2]
0042FAB3 |. |BA B8FB4200 mov edx,Acid_bur.0042FBB8 ; CRACKED
0042FAB8 |. |E8 4B3CFDFF call Acid_bur.00403708
0042FABD |. |FF75 FC push [local.1]
0042FAC0 |. |68 C8FB4200 push Acid_bur.0042FBC8 ; -
0042FAC5 |. |8D55 E8 lea edx,[local.6]
0042FAC8 |. |A1 50174300 mov eax,dword ptr ds:[0x431750]
0042FACD |. |E8 466CFDFF call Acid_bur.00406718
0042FAD2 |. |FF75 E8 push [local.6]
0042FAD5 |. |68 C8FB4200 push Acid_bur.0042FBC8 ; -
0042FADA |. |FF75 F8 push [local.2]
0042FADD |. |8D45 F4 lea eax,[local.3]
0042FAE0 |. |BA 05000000 mov edx,0x5
0042FAE5 |. |E8 C23EFDFF call Acid_bur.004039AC
0042FAEA |. |8D55 F0 lea edx,[local.4]
0042FAED |. |8B83 E0010000 mov eax,dword ptr ds:[ebx+0x1E0]
0042FAF3 |. |E8 60AFFEFF call Acid_bur.0041AA58
0042FAF8 |. |8B55 F0 mov edx,[local.4]
0042FAFB |. |8B45 F4 mov eax,[local.3]
0042FAFE |. |E8 F93EFDFF call Acid_bur.004039FC
0042FB03 |75 1A jnz short Acid_bur.0042FB1F
0042FB05 |. |6A 00 push 0x0
0042FB07 |. |B9 CCFB4200 mov ecx,Acid_bur.0042FBCC ; Congratz !!
0042FB0C |. |BA D8FB4200 mov edx,Acid_bur.0042FBD8 ; Good job dude =)
0042FB11 |. |A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB16 |. |8B00 mov eax,dword ptr ds:[eax] ; Acid_bur.00424090
0042FB18 |. |E8 53A6FFFF call Acid_bur.0042A170
0042FB1D |. |EB 18 jmp short Acid_bur.0042FB37
0042FB1F |> |6A 00 push 0x0
0042FB21 |. |B9 74FB4200 mov ecx,Acid_bur.0042FB74 ; Try Again!
0042FB26 |. |BA 80FB4200 mov edx,Acid_bur.0042FB80 ; Sorry , The serial is incorect !
0042FB2B |. |A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB30 |. |8B00 mov eax,dword ptr ds:[eax] ; Acid_bur.00424090
0042FB32 |. |E8 39A6FFFF call Acid_bur.0042A170
0042FB37 |> \33C0 xor eax,eax
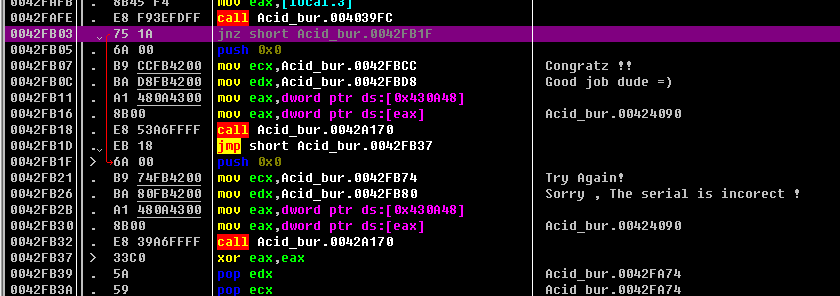

可以看到有两个关键跳转,若想要成功登录,需要将jnz给nop掉,点击jnz右键——Binary——Fill with Nops。
重新运行程序,再次点击check it baby即弹出Good

注册机算法
在跳转的上面一行call处下段点,运行程序,点击check it baby 触发断点,此时查看寄存器区域中,EDX寄存器存储着刚输入的serial

堆栈区域内容如下
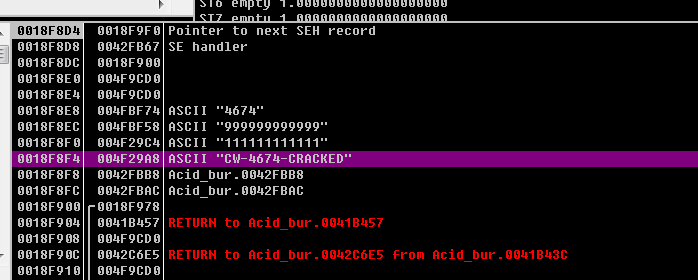
在EAX中存储着一个特殊序列,猜测可能是正确的序列号,然后将刚才设置的断点取消,在OD中重新运行程序,成功!!!!!

0042FA79 |> |8D55 F0 lea edx,[local.4]
0042FA7C |. |8B83 DC010000 mov eax,dword ptr ds:[ebx+0x1DC]
0042FA82 |. |E8 D1AFFEFF call Acid_bur.0041AA58 ;获取账户,字符串首地址存储在EBP-0x10处
0042FA87 |. |8B45 F0 mov eax,[local.4]
0042FA8A |. |0FB600 movzx eax,byte ptr ds:[eax]
0042FA8D |. |F72D 50174300 imul dword ptr ds:[0x431750]
0042FA93 |. |A3 50174300 mov dword ptr ds:[0x431750],eax
0042FA98 |. |A1 50174300 mov eax,dword ptr ds:[0x431750]
0042FA9D |. |0105 50174300 add dword ptr ds:[0x431750],eax
0042FAA3 |. |8D45 FC lea eax,[local.1]
0042FAA6 |. |BA ACFB4200 mov edx,Acid_bur.0042FBAC ; CW
0042FAAB |. |E8 583CFDFF call Acid_bur.00403708 ;将CA字符串存储在EBP-0x4处
0042FAB0 |. |8D45 F8 lea eax,[local.2]
0042FAB3 |. |BA B8FB4200 mov edx,Acid_bur.0042FBB8 ; CRACKED
0042FAB8 |. |E8 4B3CFDFF call Acid_bur.00403708 ;将CRACKED字符串存储在EBP-0x8处
0042FABD |. |FF75 FC push [local.1]
0042FAC0 |. |68 C8FB4200 push Acid_bur.0042FBC8 ; -
0042FAC5 |. |8D55 E8 lea edx,[local.6]
0042FAC8 |. |A1 50174300 mov eax,dword ptr ds:[0x431750]
0042FACD |. |E8 466CFDFF call Acid_bur.00406718 ;将0x431750存储的十六进制转换成字符串,地址存储在EBP-0x18处
0042FAD2 |. |FF75 E8 push [local.6]
0042FAD5 |. |68 C8FB4200 push Acid_bur.0042FBC8 ; -
0042FADA |. |FF75 F8 push [local.2]
0042FADD |. |8D45 F4 lea eax,[local.3]
0042FAE0 |. |BA 05000000 mov edx,0x5
0042FAE5 |. |E8 C23EFDFF call Acid_bur.004039AC ;字符串拼接。(EBP-0X4)+(EBP-0X18)+(EBP-0X8) 存储在ebp-0xC
0042FAEA |. |8D55 F0 lea edx,[local.4]
0042FAED |. |8B83 E0010000 mov eax,dword ptr ds:[ebx+0x1E0]
0042FAF3 |. |E8 60AFFEFF call Acid_bur.0041AA58 ;得到输入的密码
0042FAF8 |. |8B55 F0 mov edx,[local.4]
0042FAFB |. |8B45 F4 mov eax,[local.3]
0042FAFE |. |E8 F93EFDFF call Acid_bur.004039FC ;输入的密码与程序计算出来的KEY做比较
0042FB03 |75 1A jnz short Acid_bur.0042FB1F ;call的返回值不等于0则跳转到输出错误信息。
0042FB05 |. |6A 00 push 0x0
0042FB07 |. |B9 CCFB4200 mov ecx,Acid_bur.0042FBCC ; Congratz !!
0042FB0C |. |BA D8FB4200 mov edx,Acid_bur.0042FBD8 ; Good job dude =)
0042FB11 |. |A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB16 |. |8B00 mov eax,dword ptr ds:[eax] ; Acid_bur.00424090
0042FB18 |. |E8 53A6FFFF call Acid_bur.0042A170
0042FB1D |. |EB 18 jmp short Acid_bur.0042FB37
0042FB1F |> |6A 00 push 0x0
0042FB21 |. |B9 74FB4200 mov ecx,Acid_bur.0042FB74 ; Try Again!
0042FB26 |. |BA 80FB4200 mov edx,Acid_bur.0042FB80 ; Sorry , The serial is incorect !
0042FB2B |. |A1 480A4300 mov eax,dword ptr ds:[0x430A48]
0042FB30 |. |8B00 mov eax,dword ptr ds:[eax] ; Acid_bur.00424090
0042FB32 |. |E8 39A6FFFF call Acid_bur.0042A170
0042FB37 |> \33C0 xor eax,eax关于只有序列号的登录
关键就在于jnz上一行的call,F7 跟进后

此时各寄存器的值为
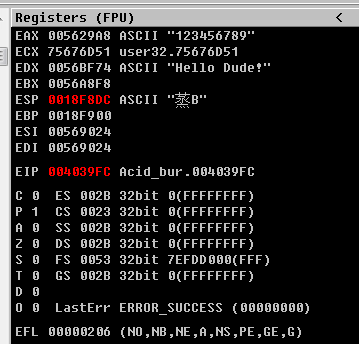
可以看到EDX寄存器中是固定的字符串Hello Dube!
而EAX中存储的值是自己手动输入的序列号,可以看到代码中有cmp eax,edx
故猜测通过序列号登录可能是固定的序列号

160个CrackMe - 001 - 『脱壳破解区』 - 吾爱破解 - LCG - LSG |安卓破解|病毒分析|www.52pojie.cn
[反汇编练习]160个CrackMe之001 - 『脱壳破解区』 - 吾爱破解 - LCG - LSG |安卓破解|病毒分析|www.52pojie.cn






















 996
996











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










