博主:[丶PURSUING](https://blog.csdn.net/weixin_44742824?spm=1011.2124.3001.5343)
在做智能家居项目的时候,因为工程量比较大需要思维导图帮忙理清楚各个函数,或者说各个功能之间的关系。XMind8就是个不错的选择。
本文为参考下篇文章,结合评论区的优秀发言整合而成,帮你避坑最快速安装。
>作者:[浩星](https://blog.csdn.net/qq_41619796)(已经取得作者转载同意)
>(免责声明:这里所有操作仅限交流学习所用,==不得用于任何商业用途==,否则后果自负!!)
# 下载地址
[XMind 8](https://www.xmind.cn/xmind8-pro/)
# 安装注意!!
(1)选择**C盘以外的盘**:方便后面破解
(2)安装路径**不能有中文**
# 破解教程
下载:[XMindCrack.jar](https://pan.baidu.com/s/11S3d0VKz4UeRl9TBfLUF-A) 提取码:mkxy
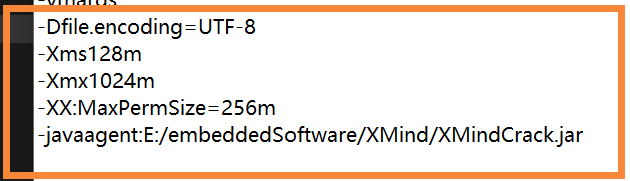
>(1)将 `XMindCrack.jar` 文件复制到安装目录:
>(2)在 `Xmind.ini` 文件尾部追加:(-javaagent:+文件路径)
例如我的:
```c
-javaagent:E:/embeddedSoftware/XMind/XMindCrack.jar
```
如图:
>(3)修改host文件
打开windows下打开路径:
```c
C:\Windows\System32\drivers\etc\
```
把host文件拖到桌面,打开追加下列两行内容:(**为什么这里要拖动出来再修改呢?因为你在那个路径下(系统文件)根本没有权限修改!!(不信你试试),百度很多修改host权限的解决办法非常麻烦,只有这一招最妙!**)
```c
127.0.0.1 xmind.net
127.0.0.1 www.xmind.net
```
如下图:

>(4)以管理员的权限运行.exe文件,打开软件。
**把电脑网络断开**
**把电脑网络断开**
**把电脑网络断开**
输入序列号:
邮箱随意:123456@qq.com
序列号:
```c
XAka34A2rVRYJ4XBIU35UZMUEEF64CMMIYZCK2FZZUQNODEKUHGJLFMSLIQMQUCUBXRENLK6NZL37JXP4PZXQFILMQ2RG5R7G4QNDO3PSOEUBOCDRYSSXZGRARV6MGA33TN2AMUBHEL4FXMWYTTJDEINJXUAV4BAYKBDCZQWVF3LWYXSDCXY546U3NBGOI3ZPAP2SO3CSQFNB7VVIY123456789012345
```
点击验证完成即可。
# 使用教程
自己去找,比如:
[6分钟b站快速上手视频](https://www.bilibili.com/video/BV1Z5411t7p5?from=search&seid=12998069872712610364)





















 2610
2610

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








