实验拓扑:

实验思路:
1、R5为ISP,其上只能配置IP地址;
2、R4作为企业边界路由器,出口公网地址需要通过PPP协议获取,并进行chap认证;
3、整个OSPF环境IP基于172.16.0.0/16划分;
4、所有设备均可访问R5的环回;
5、减少LSA的更新量,加快收敛,保证更新安全;
6、全网可达;
实验步骤:
一:划分网段
area0: 172.16.0.0/19
172.16.0.0/24
172.16.1.0/24 ---MA
172.16.2.0/24 ---R4环回
172.16.3.0/24 ---R5环回
172.16.4.0/24 ---R6环回
172.16.5.0/24 ---R7环回
172.16.6.0/24 ---隧道
area1: 172.16.32.0/19
172.16.32.0/24
172.16.33.0/24 ---MA
172.16.34.0/24 ---R1环回
172.16.35.0/24 ---R2环回
172.16.36.0/24 ---R3环回
area2: 172.16.64.0/19
172.16.64.0/24
172.16.65.0/24 ---MA
172.16.65.0/30
172.16.65.4/30
172.16.66.0/24 ---R11环回
area3: 172.16.96.0/19
172.16.96.0/24
172.16.97.0/24 ---MA
172.16.97.0/30
172.16.97.4/30
172.16.98.0/24 ---R8环回
area4: 172.16.128.0/19
172.16.128.0/24
172.16.129/24 ---MA
172.16.129.0/30
172.16.130.0/24 ---R9环回
172.16.131.0/24 ---R10环回
rip:172.16.160.0/19
L0: 172.16.160.0/24
L1: 172.16.161.0/24
二:配置IP地址
R1: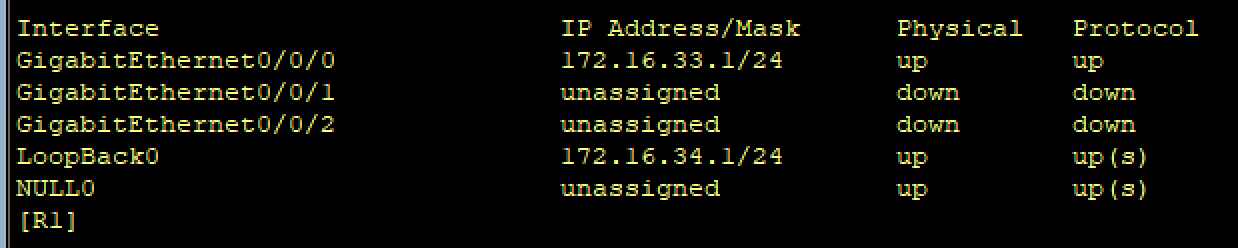
R2:

R3:

R4:

R5:

R6:

R7:

R8:

R9:

R10:

R11:

R12:

三:配置OSPF,搞通公私网
area1:
[R1]:
ospf 1 router-id 1.1.1.1
a 1
net 172.16.33.0 0.0.0.255
net 172.16.34.0 0.0.0.255
[R2]:
ospf router-id 2.2.2.2
a 1
net 172.16.33.0 0.0.0.255
net 172.16.35.0 0.0.0.255[R3]:
ospf router-id 3.3.3.3
a 1
net 172.16.33.0 0.0.0.255
net 172.16.36.0 0.0.0.255
# 查看邻居关系,刚做完这个配置时只有1.1.1.1 和 2.2.2.2 的邻居关系,小清寒当时忘记截图了
area0:
[R5]:
ospf 1 router-id 5.5.5.5
a 0
net 172.16.3.0 0.0.0.255[R6]:
ospf 1 router-id 6.6.6.6
a 0
net 172.16.4.0 0.0.0.255
[R7]:
ospf 1 router-id 7.7.7.7
a 0
net 172.16.5.0 0.0.0.255
area2:
[R6]:
ospf 1
a 2
net 172.16.65.0 0.0.0.3
[R11]:
ospf 1 router-id 11.11.11.11
a 2
net 172.16.65.0 0.0.0.3
net 172.16.66.0 0.0.0.255
[R12]:域内接口g0/0/0使用ospf协议,域外区域使用RIP协议
ospf 1 router-id 12.12.12.12
a 2
net 172.16.65.6 0.0.0.0
q
q
rip 1
v 2
undo summary
net 172.16.0.0
ospf 1
import-route rip
q
area3:
[R7]:
ospf 1
a 3
net 172.16.97.1 0.0.0.0
[R8]:
ospf 1 router-id 8.8.8.8
a 3
net 172.16.97.2 0.0.0.0
net 172.16.97.5 0.0.0.0
net 172.16.98.0 0.0.0.255
[R9]:
ospf 1 router-id 9.9.9.9
a 3
net 172.16.97.6 0.0.0.0
area4:
[R9]:
ospf 2 router-id 9.9.9.9
a 4
net 172.16.129.1 0.0.0.0
net 172.16.130.0 0.0.0.255
ospf 1
import-route ospf 2
q
ospf 2
import-route ospf 1
[R10]:
ospf 2 router-id 10.10.10.10
a 4
net 172.16.129.2 0.0.0.0
net 172.16.131.0 0.0.0.255
内外网的出入路由器配置四条缺省:
[R3]:ip route-static 0.0.0.0 0 12.0.0.1
[R5]:ip route-static 0.0.0.0 0 23.0.0.1
[R6]:ip route-static 0.0.0.0 0 34.0.0.1
[R7]:ip route-static 0.0.0.0 0 45.0.0.1
四:创建MGRE VPN 隧道
R3:
undo int Tunnel 0/0/0
undo ip add 172.16.6.3 24
undo tunnel-protocol gre p2mp
undo source GigabitEthernet 0/0/1
undo nhrp network-id 100
undo nhrp entry multicast dynamic
R5:
int Tunnel 0/0/0
ip add 172.16.6.5 24
tunnel-protocol gre p2mp
source GigabitEthernet 0/0/0
nhrp network-id 100
nhrp entry 172.16.6.3 12.0.0.2 register
R6:
int Tunnel 0/0/0
ip add 172.16.6.6 24
tunnel-protocol gre p2mp
source GigabitEthernet 0/0/2
nhrp network-id 100
nhrp entry 172.16.6.3 12.0.0.2 register
R7:
int Tunnel 0/0/0
ip add 172.16.6.7 24
tunnel-protocol gre p2mp
source GigabitEthernet 0/0/0
nhrp network-id 100
nhrp entry 172.16.6.3 12.0.0.2 register
对隧道网段进行宣告【R3 R5 R6 R7】:
net 172.16.6.0 0.0.0.255
查看路由器的建邻关系:
R3这个才现在这张截图:

测试全网通:



五:NAT配置
[R5]:
acl 2000
rule permit source 172.16.0.0 0.0.255.255
q
int g 4/0/0
nat outbound 2000[R7]:
acl 2000
rule permit source 172.16.0.0 0.0.255.255
q
int g 0/0/0
nat outbound 2000
[R3]:acl 2000
rule permit source 172.16.0.0 0.0.255.255
q
int g 0/0/1
nat outbound 2000
[R6]:acl 2000
rule permit source 172.16.0.0 0.0.255.255
q
int g 0/0/2
nat outbound 2000
六:减少LSA的更新
①:路由汇总:
R3:
[R3]ospf 1
[R3-ospf-1]a 1
[R3-ospf-1-area-0.0.0.1]abr-summary 172.16.32.0 255.255.224.0
R6:
[R6]ospf 1
[R6-ospf-1]a 2
[R6-ospf-1-area-0.0.0.2]abr-summary 172.16.64.0 255.255.224.0
R7:
[R7]ospf 1
[R7-ospf-1]a 3
[R7-ospf-1-area-0.0.0.3]abr-summary 172.16.96.0 255.255.224.0
②:特殊区域:
totally stub区域:
area 1 :
R1:
[R1]ospf 1
[R1-ospf-1]a 1
[R1-ospf-1-area-0.0.0.1]stub no-summary
R2:
[R2]ospf 1
[R2-ospf-1]a 1
[R2-ospf-1-area-0.0.0.1]stub no-summary
R3:
[R3]ospf 1
[R3-ospf-1]a 1
[R3-ospf-1-area-0.0.0.1]stub no-summary
totally NSSA区域
area 2:
R6:
[R6]ospf 1
[R6-ospf-1]a 2
[R6-ospf-1-area-0.0.0.2]nssa no-summary
R11:
[R11]ospf 1
[R11-ospf-1]a 2
[R11-ospf-1-area-0.0.0.2]nssa no-summary
R12:
[R12]ospf 1
[R12-ospf-1]a 2
[R12-ospf-1-area-0.0.0.2]nssa no-summary
area 3:
R7:
[R7]ospf 1
[R7-ospf-1]a 3
[R7-ospf-1-area-0.0.0.3]nssa no-summary
R8:
[R8]ospf 1
[R8-ospf-1]a 3
[R8-ospf-1-area-0.0.0.3]nssa no-summary
R9:
[R9]ospf 1
[R9-ospf-1]a 3
[R9-ospf-1-area-0.0.0.3]nssa no-summary

测试私网pingR4的环回:
R1:

R12:

R10:

原因是因为各个区域都依靠缺省路由去访问公网,那么R10就没有可以去学习到的详细路由条目,从而导致访问不了R4的环回,解决方法:
[R9-ospf-2]default-route-advertise

七:缩短计时器
ospf timer hello 5 #所有路由器对应的接口
八:认证
[r1-ospf-1-area-0.0.0.1]authentication-mode md5 1 cipher 123
[r2-ospf-1-area-0.0.0.1]authentication-mode md5 1 cipher 123
[r3-ospf-1-area-0.0.0.1]authentication-mode md5 1 cipher 123
[r3-ospf-1-area-0.0.0.0]authentication-mode md5 1 cipher 123
[r4-ospf-1-area-0.0.0.0]authentication-mode md5 1 cipher 123
[r6-ospf-1-area-0.0.0.0]authentication-mode md5 1 cipher 123
[r7-ospf-1-area-0.0.0.0]authentication-mode md5 1 cipher 123
[r6-ospf-1-area-0.0.0.2]authentication-mode md5 1 cipher 123
[r11-ospf-1-area-0.0.0.2]authentication-mode md5 1 cipher 123
[r12-ospf-1-area-0.0.0.2]authentication-mode md5 1 cipher 123
[r7-ospf-1-area-0.0.0.3]authentication-mode md5 md5 1 cipher 123
[r8-ospf-1-area-0.0.0.3]authentication-mode md5 md5 1 cipher 123
[r9-ospf-1-area-0.0.0.3]authentication-mode md5 md5 1 cipher 123
[r9-ospf-2-area-0.0.0.4]authentication-mode md5 1 cipher 123
[r10-ospf-1-area-0.0.0.4]authentication-mode md5 1 cipher 123
九:测试
R1pingR4的环回:

R1pingR12的环回:

查看优化后的链路数据库:
































 1148
1148

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










