2.17_1 ezRsa
from Crypto.Util.number import *
from secret import flag
m = bytes_to_long(flag)
e = 2
p = getPrime(512)
c = pow(m, e, p)
print(f"p = {p}")
print(f"c = {c}")
'''
p = 7709388356791362098686964537734555579863438117190798798028727762878684782880904322549856912344789781854618283939002621383390230228555920884200579836394161
c = 5573755468949553624452023926839820294500672937008992680281196534187840615851844091682946567434189657243627735469507175898662317628420037437385814152733456
'''
爆破
import libnum
import gmpy2
n = 7709388356791362098686964537734555579863438117190798798028727762878684782880904322549856912344789781854618283939002621383390230228555920884200579836394161
c = 5573755468949553624452023926839820294500672937008992680281196534187840615851844091682946567434189657243627735469507175898662317628420037437385814152733456
e=2
def exp(n, e, c):
k = 0
while 1:
m1 = k * n + c
m, t = gmpy2.iroot(m1, e)
if t:
print(m)
print(k)
print(libnum.n2s(int(m)))
break
k += 1
exp(n, e, c)
2916733710303623644856178494701210213708717656316720675449471304876254438460979581
1103503305
b'begin{quadr4ticresidue_i5_s0_3asy}'
二次剩余
import gmpy2
from Crypto.Util.number import *
import sympy
p = 7709388356791362098686964537734555579863438117190798798028727762878684782880904322549856912344789781854618283939002621383390230228555920884200579836394161
a = 5573755468949553624452023926839820294500672937008992680281196534187840615851844091682946567434189657243627735469507175898662317628420037437385814152733456
e = 2
k = 0
P = p - 1
if p % 4 == 3:
print(pow(a,(p + 1)//4,p))
else:
while P % 2 == 0:
P //= 2
k += 1
q = 2
while q:
l = pow(q,(p-1)//2,p)
if l == p - 1:
break
q = sympy.nextprime(q)
b = pow(q,P,p)
x = [0 for i in range(k)]
re_a = gmpy2.invert(a,p)
x[k-1] = pow(a,(P+1)//2,p)
for i in range(1,k):
m = re_a * pow(x[k-i],2)
n = pow(2,(k-i-1))
if pow(m,n,p) == p-1:
j0 = 1
x[k-i-1] = x[k-i]*pow(b,j0*(2**(i-1))) % p
else:
j1 = 0
x[k-i-1] = x[k-i] % p
print(long_to_bytes(x[0]))
2.17_2 fake_n
from Crypto.Util.number import *
from secret import flag
def fakeN_list():
puzzle_list = []
for i in range(15):
r = getPrime(32)
puzzle_list.append(r)
p = getPrime(32)
q = getPrime(32)
com = p*q
puzzle_list.append(com)
return puzzle_list
def encrypt(m,e,fake_n_list):
fake_n = 1
for i in range(len(fake_n_list)):
fake_n *= fake_n_list[i]
really_n = 1
for i in range(len(fake_n_list)-1):
really_n *= fake_n_list[i]
c = pow(m,e,really_n)
print("c =",c)
print("fake_n =",fake_n)
if __name__ == '__main__':
m = bytes_to_long(flag)
e = 65537
fake_n_list = fakeN_list()
encrypt(m,e,fake_n_list)
'''
c = 6451324417011540096371899193595274967584961629958072589442231753539333785715373417620914700292158431998640787575661170945478654203892533418902
fake_n = 178981104694777551556050210788105224912858808489844293395656882292972328450647023459180992923023126555636398409062602947287270007964052060975137318172446309766581
'''
先将fake_n进行yafu分解

再对C19进行分解
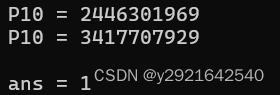
然后得到fake_n的17个因数
k = [2215221821,2290486867,2333428577,2361589081,2446301969,2507934301,2590663067,3107210929,3278987191,3389689241 ,3417707929,3429664037,3716624207,3859354699 ,3965529989 ,4098704749,4267348123]
from Crypto.Util.number import *
import gmpy2
fake_n = 178981104694777551556050210788105224912858808489844293395656882292972328450647023459180992923023126555636398409062602947287270007964052060975137318172446309766581
k = [2215221821,2290486867,2333428577,2361589081,2446301969,2507934301,2590663067,3107210929,3278987191,3389689241 ,3417707929,3429664037,3716624207,3859354699 ,3965529989 ,4098704749,4267348123]
e = 65537
c = 6451324417011540096371899193595274967584961629958072589442231753539333785715373417620914700292158431998640787575661170945478654203892533418902
for i in range(17):
for j in range(17):
if i != j:
com = k[i] * k[j]
phi = 1
really_n = fake_n // com
for a in range(17):
if a == i or a == j:
continue
phi *= k[a] - 1
d = gmpy2.invert(e, phi)
m = pow(c, d, really_n)
print(long_to_bytes(m))
b'begin{y0u_f1nd_th3_re4l_n}'







 文章讲述了如何使用Python解决一个基于RSA加密的谜题,涉及公钥加密、二次剩余理论、因数分解等技术。解密过程包括利用伪随机数生成的prime列表和计算私钥d。
文章讲述了如何使用Python解决一个基于RSA加密的谜题,涉及公钥加密、二次剩余理论、因数分解等技术。解密过程包括利用伪随机数生成的prime列表和计算私钥d。
















 831
831

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








