If you need to host Subversion in a Windows Server environment, it is always desirable to integrate subversion with Active Directory. For Windows Administrators it is better to use COLLABNET Subversion Edge as it comes with all-in-one installer including Apache, Subversion and a beautiful web console which simplifies tasks like managing repositories, users and SVN services using GUI.
Concept
On receiving authentication request from an SVN client, Subversion gets user information validated from Active Directory. The protocol used is LDAP, which stands for Lightweight Directory Access Protocol. Subversion acts as a LDAP Client and Active Directory is the LDAP Server.
An LDAP Client has to authenticate itself to Active Directory before sending any LDAP query. This is called LDAP Bind. LDAP Client passes a valid User DN and Password to Active Directory. Only if Bind operation is successful, LDAP client can request for additional information like list of users in an OU, User Properties like email, department etc. Bind User is also required to query for Active Directory groups and their memberships. This however also depends that whether the Bind User has required rights to that information in Active Directory. Usually, by default, “Authenticated Users” group has Read Access on every OU, users and groups. So no special permission needs to be configured on any OU. However, In a locked-down Active Directory, authenticated user ACEs are removed from the default Active Directory containers, including the Users, Systems, and OUs where User and Computer objects are stored. In such case, some permission needs to be configured.
This post only focuses on identifying required LDAP parameters from Active Directory, configuring them in COLLABNET Subversion Edge, testing and troubleshooting basic LDAP connectivity with Active Directory in non-locked-down mode. For more details on LDAP authentication protocol flow and how to prepare Active Directory in locked-down-mode for LDAP Authentication, refer post “Preparing Locked-Down Active Directory for LDAP Authentication”.
Identifying DN for LDAP Bind User and Base DN
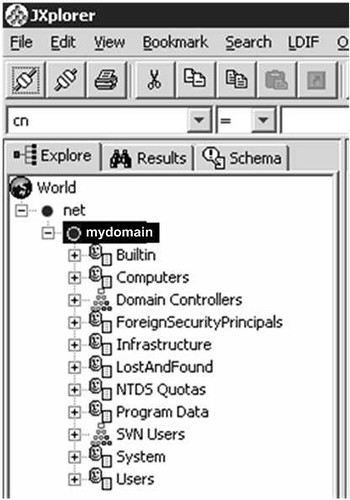
Base DN is basically the starting or entry point in Active Directory tree where operations like LDAPSearch will be carried out. Generally Base DN is the root of the domain. For example Base DN for mydomain.net will be “dc=mydomain,dc=net”. Base DN can also be of some OU. For example, for an OU “SVN Users” in mydomain.net, Base DN will be “ou=svn users,dc=mydomain,dc=net”.
Bind User DN is the DN of user that will bind to Active Directory before querying any additional information.
Sometimes it can be confusing to compile DN for a given user in Active Directory. It is always good to verify DN using some tool or another LDAP client rather than trying different combinations directly in COLLABNET Subversion Edge configuration.
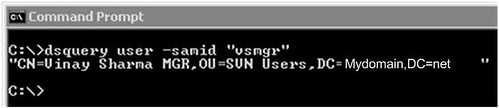
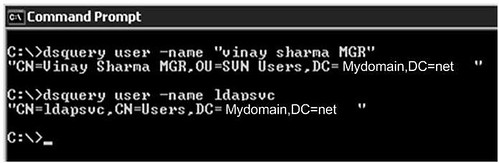
It is quick and easy to use dsquery.exe on the domain controller to get DN for a given user display name or SAM account as shown below:
Use “–samid” switch if you know the logon name. Otherwise you can also use “–name” for display name. In both cases it will output the DN of user.
Similarly you can use dsquery.exe to get DN for a given OU in Active Directory as shown below.
Testing Connectivity to Active Directory
It is better to test connectivity to active directory from server running COLLABNET Subversion before configuring LDAP authentication. This verifies that there are no firewall or permission issues in connecting to Active Directory Server i.e. Domain Controller.
Step 1 :
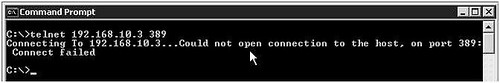
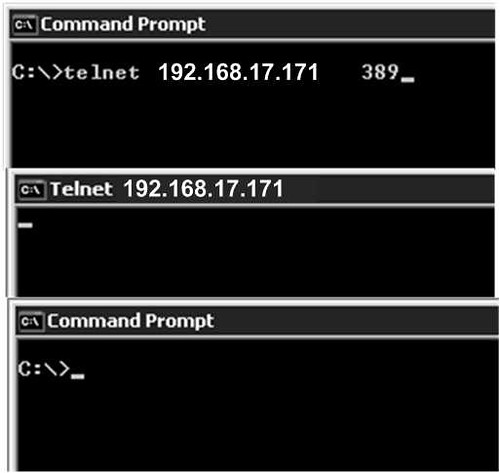
Verify that you can make a network connection to Active Directory if there are firewalls. You can simply try telnet to domain controller on port 389, which is the default LDAP port.
Unsuccessful Connection:
Telnet LDAP Server 389 Unsuccessful by dscentral.in
Successful Connection:
Step 2:
Connect to Active Directory using another LDAP client. You can use JXplorer as shown below. JXplorer is a free java based open source LDAP Browser (LDAP Client). You can even run it without installing anything on server.
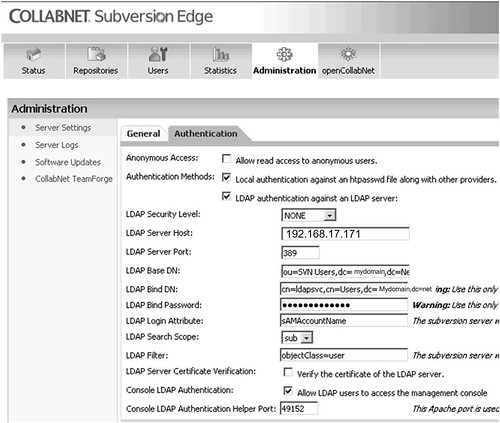
Configuring COLLABNET Subversion Edge for LDAP Authentication
This is very straightforward process if you have all required details well verified and tested.
Configure Active Directory Host address, Bind User DN, Password, Base DN and User Identifier as shown below.
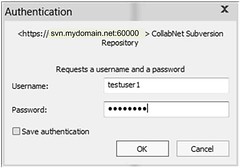
Testing LDAP Authentication
Do not use domain name in user name field.
Summary
- LDAP Client has to authenticate itself to Active Directory before asking for any information. For this we require a valid Active Directory User and Password with appropriate rights configured on Active Directory objects. This user is called Bind User.
- Use dsquery.exe to identify Bind User DN, OU DN.
- Verify LDAP Bind to Active Directory using JXplorer.
- Configure parameters in COLLABNET Subversion Edge.























 1336
1336

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








