你真的是大学生吗
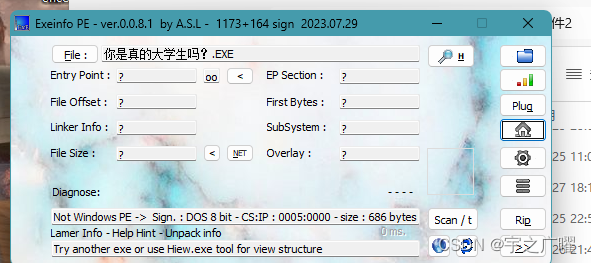
MSDOS 程序,需要读汇编

enc=[ 0x76, 0x0E, 0x77, 0x14, 0x60, 0x06, 0x7D, 0x04, 0x6B, 0x1E,
0x41, 0x2A, 0x44, 0x2B, 0x5C, 0x03, 0x3B, 0x0B, 0x33, 0x05]
print(len(enc))
flag=[0x00]*20
for i in range(19):
flag[i]=enc[i]^enc[i+1]
# sub si,1 mov al,[si]
# xor [si],al
flag[19]=enc[19]^flag[0] #这个没看出来
print(''.join([chr(i) for i in flag]))
# xyctf{you_know_8086}
ez_enc
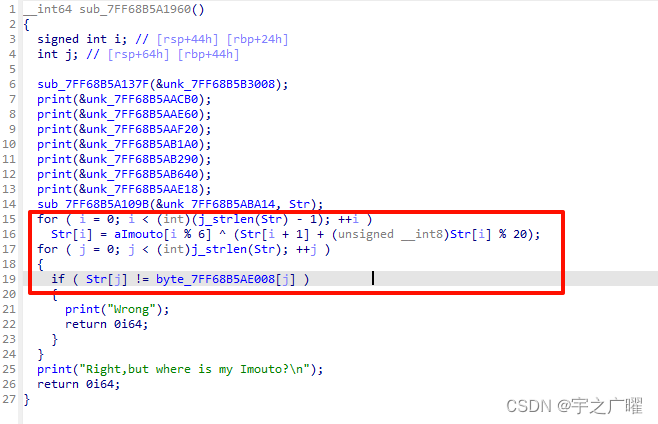
en,确实不好逆,直接爆破。 还不太会,看大佬wp,还可以用z3来爆。
from z3 import *
s=Solver()
flags=[BitVec('flag[%d]' % i ,8)for i in range(34)]
flag_decls=flags[:]
for i in range(34):
s.add(flags[i]<127)
s.add(flags[i]>=32)
enc=[ 0x27, 0x24, 0x17, 0x0B, 0x50, 0x03, 0xC8, 0x0C, 0x1F, 0x17,
0x36, 0x55, 0xCB, 0x2D, 0xE9, 0x32, 0x0E, 0x11, 0x26, 0x02,
0x0C, 0x07, 0xFC, 0x27, 0x3D, 0x2D, 0xED, 0x35, 0x59, 0xEB,
0x3C, 0x3E, 0xE4, 0x7D]
str='IMouto'
for i in range(34-1):
flags[i]=ord(str[i%6])^(flags[i+1]+flags[i]%20)&0xff
for i in range(34):
s.add(flags[i]==enc[i])
if s.check()==sat:
m=s.model()
print(m)
print(''.join(chr(m[flag_decls[i]].as_long()) for i in range(34)))
# flag[33] = 125]
# >lag{!_r3ea11y_w4nt_@_cu7e_s1$ter}又get到z3的新用法。
Findme
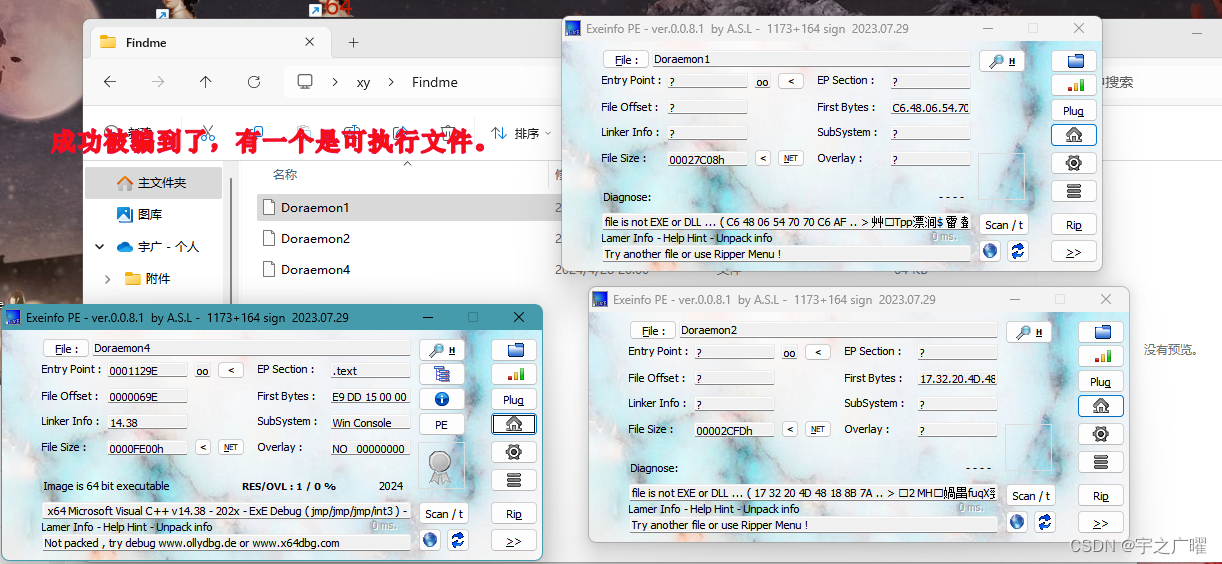
Doraemon应该是关键字符,没有main函数,该字符所在位置应该就是关键函数
__int64 sub_140016010()
{
size_t v0; // rax
int v2; // eax
FILE *Stream; // 输入文件流
FILE *v4; // 输出文件流
int v5; // 用于循环计数
int v6; // 用于生成随机数种子
int v7; // 用于加密过程
int v8; // 用于加密过程
unsigned __int8 v9; // 输入文件字节
unsigned __int8 v10; // 加密后的字节
int i; // 用于循环计数
// 调用另一个函数,可能是初始化一些数据
sub_1400113AC(&unk_1400230A2);
j_create512(); // 生成512个数
// 初始化变量
v5 = 0;
v7 = 0;
v8 = 0;
// 清空数组
j_memset(FileName, 0, 0x100ui64);
j_memset(byte_14001D7A0, 0, 0x100ui64);
// 获取当前目录路径
GetCurrentDirectoryA(0x100u, FileName);
v0 = j_strlen(FileName);
j_memcpy(byte_14001D7A0, FileName, v0);
// 拼接文件路径
j_strcat(FileName, "\\Doraemon3"); // 输入文件路径
j_strcat(byte_14001D7A0, "\\Doraemon1"); // 输出文件路径
// 打开输入文件
Stream = fopen(FileName, "rb");
if ( Stream )
{
// 打开输出文件
v4 = fopen(byte_14001D7A0, "wb");
while ( !feof(Stream) ) // 读取输入文件直到结束
{
v7 = (v7 + 1) % 512;
v8 = (byte_14001D960[v7] + v8) % 512;
byte_14001D201 = byte_14001D960[v7];
byte_14001D960[v7] = byte_14001D960[v8];
byte_14001D960[v8] = byte_14001D201;
// 获取输入文件的字节并进行加密
v10 = byte_14001D960[(unsigned __int8)((byte_14001D960[v8] + byte_14001D960[v7]) % 512)];
v9 = v10 ^ fgetc(Stream);
// 将加密后的字节写入输出文件
fputc(v9, v4);
// 生成随机数种子,产生 0 到 3 之间的随机数,写入输出文件
srand(byte_14001D960[v5 % 512]);
v6 = rand() % 4;
for ( i = 0; i < v6; ++i )
{
v2 = rand();
fputc(v2 % 256, v4);
}
++v5;
}
print("end");
fclose(Stream);
fclose(v4);
system("pause");
return 0i64;
}
else
{
print("No Such File\n");
return 0i64;
}
}
从输入文件中读取数据,对数据进行加密处理,然后将加密后的数据写入输出文件中。在加密过程中,使用了一个伪随机数生成算法,并将加密结果存储在 byte_14001D960 数组中。
Doraemon3是我们输入的文件,下面运算只有简单异或和伪随机数保护
嗯,一眼流密码,魔改rc4 (还不行)
fputc(ch1,FileIO): 相当于解密出一个字节的数据
先运行到creat512后面,得到数据:
__int64 sub_140011900()
{
char *v0; // rdi
__int64 i; // rcx
char v3[32]; // [rsp+0h] [rbp-20h] BYREF
char v4; // [rsp+20h] [rbp+0h] BYREF
unsigned int v5; // [rsp+24h] [rbp+4h]
char v6; // [rsp+44h] [rbp+24h]
char v7[532]; // [rsp+70h] [rbp+50h] BYREF
unsigned int j; // [rsp+284h] [rbp+264h]
int v9; // [rsp+2A4h] [rbp+284h]
int v10; // [rsp+2C4h] [rbp+2A4h]
v0 = &v4;
for ( i = 178i64; i; --i )
{
*(_DWORD *)v0 = -858993460;
v0 += 4;
}
sub_1400113AC((__int64)&unk_1400230A2); // 调用另一个函数,参数是 unk_1400230A2 的地址
v5 = j_strlen(Str); // 计算字符串 Str 的长度,保存在 v5 中
memset(v7, 0, 0x200ui64); // 将 v7 数组清零
print("start\n"); // 打印 "start\n" 字符串
// 循环,给 v7 和 byte_14001D960 数组赋值
for ( j = 0; j < 0x200; ++j )
{
v6 = j; // 将 j 赋值给 v6
byte_14001D960[j] = -(char)j; // 将 byte_14001D960[j] 赋值为 j 的补码
v7[j] = Str[j % v5]; // 将 Str 中的字符赋值给 v7[j]
}
v9 = 0;
v10 = 0;
// 循环,进行加密操作
while ( v9 < 512 )
{
v10 = ((unsigned __int8)v7[v9] + byte_14001D960[v9] + v10) % 512; // 计算下一个位置
byte_14001D201 = byte_14001D960[v9]; // 保存 byte_14001D960[v9] 的值
byte_14001D960[v9] = byte_14001D960[v10]; // 将 byte_14001D960[v10] 的值赋值给 byte_14001D960[v9]
byte_14001D960[v10] = byte_14001D201; // 将保存的值赋值给 byte_14001D960[v10]
++v9;
}
return sub_140011343(v3, &unk_14001AC80); // 调用另一个函数 sub_140011343,参数是 v3 和 unk_14001AC80 的地址
}
unsigned char ida_chars[] =
{
0xF3, 0x75, 0xC9, 0xB4, 0x2A, 0x3A, 0x9A, 0x90, 0xBE, 0x43,
0x65, 0x33, 0x39, 0xD3, 0xF0, 0x46, 0xA5, 0x32, 0xCE, 0x4B,
0x8A, 0x6C, 0x60, 0xC7, 0x70, 0x55, 0xEF, 0x96, 0xB2, 0x08,
0xC7, 0x68, 0x53, 0x6E, 0xD9, 0x0D, 0xD4, 0x69, 0xCD, 0x87,
0x45, 0x01, 0xE9, 0x93, 0x7B, 0x21, 0x65, 0xDE, 0x8E, 0x24,
0x26, 0xA6, 0xC8, 0x94, 0x7E, 0xFD, 0x4F, 0xFD, 0xAD, 0x2B,
0x51, 0x28, 0x0A, 0x5C, 0xA1, 0x0E, 0x11, 0x45, 0x25, 0x6D,
0x6B, 0x9F, 0x75, 0x5D, 0x3E, 0x20, 0xFA, 0xDC, 0x07, 0xA3,
0x77, 0xC6, 0x8C, 0xEC, 0x8B, 0x3C, 0xCE, 0x2D, 0x18, 0xE3,
0xBA, 0xBD, 0xBC, 0xCA, 0xB7, 0xB4, 0x03, 0x5B, 0xF0, 0x4D,
0x4C, 0xF2, 0x3B, 0x34, 0x42, 0xB3, 0x39, 0x91, 0x67, 0x23,
0x16, 0xEA, 0x88, 0x05, 0x08, 0x19, 0xDA, 0xDF, 0xD0, 0xF5,
0x09, 0x23, 0x59, 0x6D, 0x62, 0x13, 0x85, 0xBD, 0x3D, 0x7E,
0x92, 0xE4, 0x82, 0x06, 0xBB, 0x7B, 0x6A, 0x47, 0xD9, 0xF6,
0x1E, 0x09, 0x58, 0x1A, 0xD8, 0xFE, 0x29, 0x8C, 0xBF, 0x54,
0xAF, 0xAE, 0xA2, 0x8F, 0xD6, 0xE7, 0xBB, 0x24, 0x97, 0x7A,
0xD7, 0x7F, 0xCB, 0x40, 0x3F, 0x49, 0x00, 0xDC, 0xE0, 0x5E,
0xC9, 0xE0, 0x95, 0x4E, 0xC4, 0x90, 0xEB, 0x74, 0x6B, 0xA0,
0x9D, 0xCD, 0xDE, 0xA2, 0x87, 0x1A, 0xD1, 0x12, 0xC8, 0x1B,
0x80, 0xE2, 0x4A, 0x10, 0x60, 0x79, 0x37, 0x29, 0x25, 0xBA,
0xAE, 0x04, 0x1B, 0xDB, 0xD5, 0x48, 0xFE, 0x51, 0x05, 0x83,
0x15, 0x64, 0xC4, 0x76, 0x34, 0xB5, 0xF2, 0xC5, 0x78, 0x6F,
0xC6, 0x10, 0x5F, 0x53, 0x81, 0xFB, 0x8D, 0x40, 0xE6, 0x71,
0xA8, 0x57, 0xB7, 0x99, 0x20, 0x98, 0x56, 0xF4, 0xD8, 0x70,
0xB9, 0xF8, 0xE4, 0xB5, 0x7A, 0xAA, 0xFA, 0x3C, 0x73, 0x77,
0xE8, 0xF9, 0x12, 0x83, 0x2A, 0xB1, 0xC1, 0x9F, 0xF5, 0x5E,
0xF1, 0xF6, 0xD7, 0x89, 0x30, 0x63, 0xF4, 0x68, 0xA9, 0x0B,
0x36, 0x85, 0xF8, 0xB3, 0x95, 0x64, 0x79, 0x56, 0x97, 0x19,
0x5F, 0xA8, 0x6C, 0x4C, 0x52, 0x69, 0xB6, 0x5A, 0x54, 0x63,
0x58, 0x16, 0x86, 0x46, 0xBE, 0x31, 0x1D, 0xCF, 0x42, 0x31,
0x59, 0xEE, 0xEA, 0x0F, 0x28, 0x57, 0x3B, 0x7F, 0xD0, 0xB9,
0x8D, 0xED, 0x44, 0x30, 0xA7, 0xC1, 0x5B, 0x04, 0x33, 0xAC,
0x02, 0x73, 0xDB, 0xFF, 0x01, 0x3D, 0xB1, 0x36, 0x9C, 0xA0,
0x4D, 0x9C, 0x3E, 0x72, 0xF1, 0x1F, 0x88, 0xE5, 0xAD, 0x00,
0x49, 0x0E, 0x3A, 0xE6, 0xD2, 0xE1, 0xE9, 0x44, 0x27, 0x52,
0x99, 0xEC, 0xBC, 0x47, 0xCC, 0xA6, 0x9E, 0xD2, 0x7C, 0xFB,
0x72, 0xDA, 0xA7, 0x9A, 0x86, 0x55, 0x8A, 0x76, 0x9B, 0xF3,
0x7C, 0x8F, 0x14, 0x7D, 0xC5, 0x94, 0x17, 0x8B, 0xAB, 0x15,
0xBF, 0x2E, 0xDD, 0x2C, 0xB0, 0x62, 0x89, 0x71, 0x92, 0x21,
0x9D, 0x0C, 0xEF, 0x9E, 0xD1, 0x2B, 0x06, 0xF7, 0x4F, 0xC3,
0xCF, 0xFF, 0x6E, 0xE5, 0xEB, 0x96, 0xF9, 0xDF, 0xCA, 0x07,
0xD4, 0xA3, 0x84, 0xE3, 0x1F, 0x66, 0x1D, 0x18, 0x35, 0x41,
0x2F, 0x02, 0x66, 0x2E, 0x6F, 0x61, 0xD5, 0x3F, 0x7D, 0x78,
0x1C, 0x32, 0xAB, 0xA4, 0x67, 0xC2, 0xC0, 0x1C, 0x11, 0xE2,
0x2C, 0x38, 0x8E, 0xB2, 0x48, 0xE1, 0x0A, 0x22, 0xD3, 0x41,
0xD6, 0x91, 0x0D, 0x03, 0xFC, 0xFC, 0x38, 0xAC, 0xA9, 0x98,
0xAA, 0x14, 0xCB, 0xCC, 0x4B, 0x81, 0x2D, 0x5C, 0xB8, 0x0F,
0x1E, 0xAF, 0x93, 0xB6, 0x50, 0x50, 0xE7, 0x35, 0x4A, 0xC2,
0xA5, 0x37, 0x43, 0x9B, 0x22, 0x80, 0xC3, 0xDD, 0xED, 0x5A,
0x5D, 0x0C, 0x0B, 0x6A, 0x27, 0x2F, 0x74, 0xEE, 0xF7, 0x26,
0x82, 0x84, 0xB8, 0xE8, 0x61, 0xA4, 0xB0, 0xC0, 0x13, 0x4E,
0xA1, 0x17
};复制了一下别人的脚本:
import ctypes
import os#加载 C 库
if os.name == 'nt': # 如果是 Windows 系统
libc = ctypes.CDLL('msvcrt.dll')
else: # 如果是其他系统
libc = ctypes.CDLL('libc.so.6')
#声明 srand 和 rand 函数的签名
libc.srand.argtypes = [ctypes.c_uint]
libc.rand.restype = ctypes.c_int
#定义 Python 封装函数
def set_seed(seed):
libc.srand(seed)
def generate_random():
return libc.rand()
print(os.getcwd()) #来输出当前工作目录
import os
print("当前工作目录:", os.getcwd())
data = [0xF3, 0x75, 0xC9, 0xB4, 0x2A, 0x3A, 0x9A, 0x90, 0xBE, 0x43, 0x65,0x33,0x39, 0xD3, 0xF0, 0x46, 0xA5, 0x32, 0xCE, 0x4B, 0x8A, 0x6C, 0x60, 0xC7,0x70, 0x55,0xEF, 0x96, 0xB2, 0x08, 0xC7, 0x68, 0x53, 0x6E, 0xD9, 0x0D, 0xD4, 0x69,0xCD, 0x87,0x45, 0x01, 0xE9, 0x93, 0x7B, 0x21, 0x65, 0xDE, 0x8E, 0x24, 0x26, 0xA6,0xC8, 0x94,0x7E, 0xFD, 0x4F, 0xFD, 0xAD, 0x2B, 0x51, 0x28, 0x0A, 0x5C, 0xA1, 0x0E,0x11, 0x45,0x25, 0x6D, 0x6B, 0x9F, 0x75, 0x5D, 0x3E, 0x20, 0xFA, 0xDC, 0x07, 0xA3,0x77, 0xC6,0x8C, 0xEC, 0x8B, 0x3C, 0xCE, 0x2D, 0x18, 0xE3, 0xBA, 0xBD, 0xBC, 0xCA,0xB7, 0xB4,0x03, 0x5B, 0xF0, 0x4D, 0x4C, 0xF2, 0x3B, 0x34, 0x42, 0xB3, 0x39, 0x91,0x67, 0x23,0x16, 0xEA, 0x88, 0x05, 0x08, 0x19, 0xDA, 0xDF, 0xD0, 0xF5, 0x09, 0x23,0x59, 0x6D,0x62, 0x13, 0x85, 0xBD, 0x3D, 0x7E, 0x92, 0xE4, 0x82, 0x06, 0xBB, 0x7B,0x6A, 0x47,0xD9, 0xF6, 0x1E, 0x09, 0x58, 0x1A, 0xD8, 0xFE, 0x29, 0x8C, 0xBF, 0x54,0xAF, 0xAE,0xA2, 0x8F, 0xD6, 0xE7, 0xBB, 0x24, 0x97, 0x7A, 0xD7, 0x7F, 0xCB, 0x40,0x3F, 0x49,
0x00, 0xDC, 0xE0, 0x5E, 0xC9, 0xE0, 0x95, 0x4E, 0xC4, 0x90, 0xEB, 0x74,0x6B, 0xA0,0x9D, 0xCD, 0xDE, 0xA2, 0x87, 0x1A, 0xD1, 0x12, 0xC8, 0x1B, 0x80, 0xE2,0x4A, 0x10,0x60, 0x79, 0x37, 0x29, 0x25, 0xBA, 0xAE, 0x04, 0x1B, 0xDB, 0xD5, 0x48,0xFE, 0x51,0x05, 0x83, 0x15, 0x64, 0xC4, 0x76, 0x34, 0xB5, 0xF2, 0xC5, 0x78, 0x6F,0xC6, 0x10,0x5F, 0x53, 0x81, 0xFB, 0x8D, 0x40, 0xE6, 0x71, 0xA8, 0x57, 0xB7, 0x99,0x20, 0x98,0x56, 0xF4, 0xD8, 0x70, 0xB9, 0xF8, 0xE4, 0xB5, 0x7A, 0xAA, 0xFA, 0x3C,0x73, 0x77,0xE8, 0xF9, 0x12, 0x83, 0x2A, 0xB1, 0xC1, 0x9F, 0xF5, 0x5E, 0xF1, 0xF6,0xD7, 0x89,0x30, 0x63, 0xF4, 0x68, 0xA9, 0x0B, 0x36, 0x85, 0xF8, 0xB3, 0x95, 0x64,0x79, 0x56,0x97, 0x19, 0x5F, 0xA8, 0x6C, 0x4C, 0x52, 0x69, 0xB6, 0x5A, 0x54, 0x63,0x58, 0x16,0x86, 0x46, 0xBE, 0x31, 0x1D, 0xCF, 0x42, 0x31, 0x59, 0xEE, 0xEA, 0x0F,0x28, 0x57,0x3B, 0x7F, 0xD0, 0xB9, 0x8D, 0xED, 0x44, 0x30, 0xA7, 0xC1, 0x5B, 0x04,0x33, 0xAC,0x02, 0x73, 0xDB, 0xFF, 0x01, 0x3D, 0xB1, 0x36, 0x9C, 0xA0, 0x4D, 0x9C,0x3E, 0x72,0xF1, 0x1F, 0x88, 0xE5, 0xAD, 0x00, 0x49, 0x0E, 0x3A, 0xE6, 0xD2, 0xE1,0xE9, 0x44,0x27, 0x52, 0x99, 0xEC, 0xBC, 0x47, 0xCC, 0xA6, 0x9E, 0xD2, 0x7C, 0xFB,0x72, 0xDA,0xA7, 0x9A, 0x86, 0x55, 0x8A, 0x76, 0x9B, 0xF3, 0x7C, 0x8F, 0x14, 0x7D,0xC5, 0x94,0x17, 0x8B, 0xAB, 0x15, 0xBF, 0x2E, 0xDD, 0x2C, 0xB0, 0x62, 0x89, 0x71,0x92, 0x21,0x9D, 0x0C, 0xEF, 0x9E, 0xD1, 0x2B, 0x06, 0xF7, 0x4F, 0xC3, 0xCF, 0xFF,0x6E, 0xE5,0xEB, 0x96, 0xF9, 0xDF, 0xCA, 0x07, 0xD4, 0xA3, 0x84, 0xE3, 0x1F, 0x66,0x1D, 0x18,0x35, 0x41, 0x2F, 0x02, 0x66, 0x2E, 0x6F, 0x61, 0xD5, 0x3F, 0x7D, 0x78,0x1C, 0x32,0xAB, 0xA4, 0x67, 0xC2, 0xC0, 0x1C, 0x11, 0xE2, 0x2C, 0x38, 0x8E, 0xB2,0x48, 0xE1,0x0A, 0x22, 0xD3, 0x41, 0xD6, 0x91, 0x0D, 0x03, 0xFC, 0xFC, 0x38, 0xAC,0xA9, 0x98,0xAA, 0x14, 0xCB, 0xCC, 0x4B, 0x81, 0x2D, 0x5C, 0xB8, 0x0F, 0x1E, 0xAF,0x93, 0xB6,0x50, 0x50, 0xE7, 0x35, 0x4A, 0xC2, 0xA5, 0x37, 0x43, 0x9B, 0x22, 0x80,0xC3, 0xDD,0xED, 0x5A, 0x5D, 0x0C, 0x0B, 0x6A, 0x27, 0x2F, 0x74, 0xEE, 0xF7, 0x26,0x82, 0x84,0xB8, 0xE8, 0x61, 0xA4, 0xB0, 0xC0, 0x13, 0x4E, 0xA1, 0x17]
Doraemon1 = []
#打开文件并读取字节
with open("Doraemon1", "rb") as file:
#读取文件字节并赋值给temp
Doraemon1 = list(file.read())
outfile = []
idx = 0
idx_1 = 0
idx_2 = 0
Doraemon1idx = 0
while Doraemon1idx<len(Doraemon1) :
idx_1 = (idx_1 + 1) % 512
idx_2 = (data[idx_1] + idx_2) % 512
temp = data[idx_1]
data[idx_1] = data[idx_2]
data[idx_2] = temp
data_ch = data[((data[idx_2] + data[idx_1]) % 512) & 0xff]
Stream = data_ch ^ Doraemon1[Doraemon1idx]
Doraemon1idx += 1
outfile.append(Stream.to_bytes(1, 'big'))
set_seed(data[idx % 512])
randnum = generate_random() % 4
for i in range(randnum):
Doraemon1idx += 1
idx += 1
print(outfile)#打开文件进行写入
with open("output_file.exe", "wb") as file:
#逐字节写入文件
for byte in outfile:
file.write(byte) #将每个字节转换为字节数组并写入文件
 真的有耶。
真的有耶。

还有个大佬说:
Doraemon4 会初始化一个 512 字节的 BOX,然后用 BOX 加密 Doraemon3 得到 Doraemon1。由于 BOX 初始状态已知,正向顺序重新跑一次即可。复制反编译代码到新的 C 源文件,fputc 和 fgetc 互换,直接跑得到 Doraemon3。
#include <stdio.h>
#include <string.h>
const char *Str = "Find_Doraemon";
unsigned char BOX[512];
void init_box()
{
char *v0; // rdi
__int64 i; // rcx
char v3[32]; // [rsp+0h] [rbp-20h] BYREF
char v4; // [rsp+20h] [rbp+0h] BYREF
unsigned int v5; // [rsp+24h] [rbp+4h]
char v6; // [rsp+44h] [rbp+24h]
char v7[532]; // [rsp+70h] [rbp+50h] BYREF
unsigned int j; // [rsp+284h] [rbp+264h]
int v9; // [rsp+2A4h] [rbp+284h]
int v10; // [rsp+2C4h] [rbp+2A4h]
v5 = strlen(Str);
memset(v7, 0, 0x200);
for (j = 0; j < 0x200; ++j)
{
v6 = j;
BOX[j] = -(char)j;
v7[j] = Str[j % v5];
}
v9 = 0;
v10 = 0;
while (v9 < 512)
{
v10 = ((unsigned __int8)v7[v9] + BOX[v9] + v10) % 512;
unsigned char tmp = BOX[v9];
BOX[v9] = BOX[v10];
BOX[v10] = tmp;
++v9;
}
}
int main()
{
size_t v3; // rax
int v5; // eax
FILE *fout; // [rsp+28h] [rbp+8h]
FILE *fin; // [rsp+48h] [rbp+28h]
int v8; // [rsp+64h] [rbp+44h]
int v9; // [rsp+84h] [rbp+64h]
int v10; // [rsp+A4h] [rbp+84h]
int v11; // [rsp+C4h] [rbp+A4h]
unsigned __int8 v12; // [rsp+104h] [rbp+E4h]
unsigned __int8 v13; // [rsp+144h] [rbp+124h]
int i; // [rsp+164h] [rbp+144h]
init_box();
v8 = 0;
v10 = 0;
v11 = 0;
fout = fopen("Doraemon3", "wb");
fin = fopen("Doraemon1", "rb");
while (!feof(fin))
{
v10 = (v10 + 1) % 512;
v11 = (BOX[v10] + v11) % 512;
unsigned char tmp = BOX[v10];
BOX[v10] = BOX[v11];
BOX[v11] = tmp;
v13 = BOX[(unsigned __int8)((BOX[v11] + BOX[v10]) % 512)];
v12 = v13 ^ fgetc(fin);
fputc(v12, fout);
srand(BOX[v8 % 512]);
v9 = rand() % 4;
for (i = 0; i < v9; ++i)
{
v5 = rand();
fgetc(fin);
}
++v8;
}
fclose(fout);
fclose(fin);
return 0;
}还是比较懵的,需要多看看。





















 775
775











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








