目录
一、IPSEC静态VPN概述
工作原理:
IPSec(Internet Protocol Security)是一种用于保护IP通信的安全协议,它通过加密和认证机制来确保数据在公共网络(如互联网)中传输时的机密性、完整性和真实性。IPSec VPN(Virtual Private Network)是基于IPSec协议构建的虚拟专用网络,能够在公共网络上建立安全的通信隧道。
主要目的:
实现不同站点的私网地址在通过公网时进行加密再传输,确保了安全性和完整性。
二、配置
1.配置思路
A站点:(B站点同理)
①首先完成基本的数据连通性(PC1---R1,PC2--R2,R1---R1)
在R3上配置默认路由指向R1,在R1配置回程路由指向R3,配置默认路由指向R5
②在出口路由器R1上配置感兴趣流量(匹配PC1的私网流量,定义需要进入隧道的流量)
③接着创建安全提议(封装模式、封装协议、加密算法、验证算法)
④再创建安全策略(调用ACL、调用安全提议、创建隧道外层封装源、目、定义安全联盟SPI、定义AH验证钥匙)
⑤最后调用安全策略(在出接口上)
拓扑图:
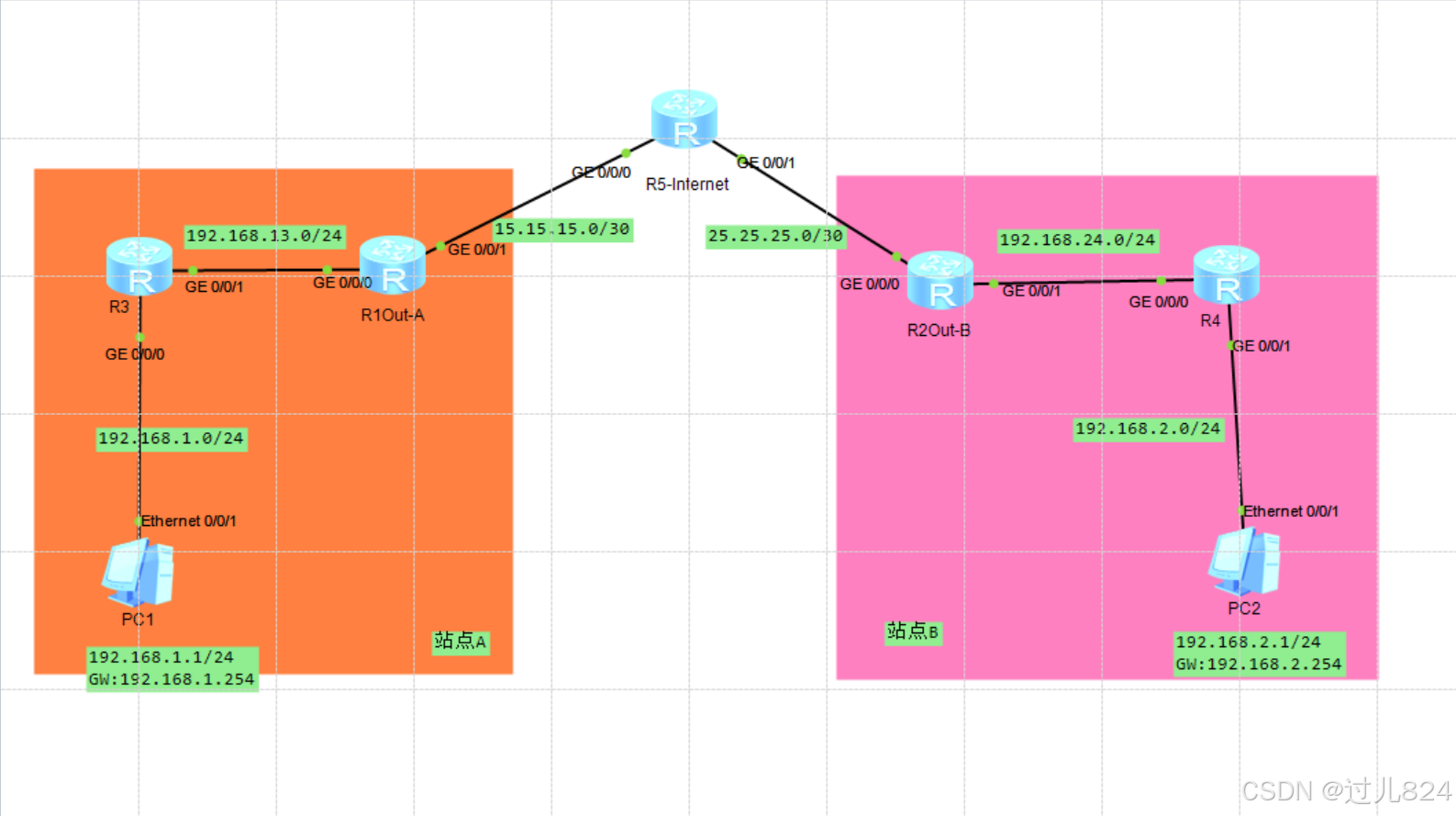
2.具体配置
①完成基本的数据连通性
R3:
[R3]ip route-static 0.0.0.0 0.0.0.0 192.168.13.1
R1:
[R1]ip route-static 0.0.0.0 0.0.0.0 15.15.15.5
[R1]ip route-static 192.168.1.0 255.255.255.0 192.168.13.3
R2:
[R2]ip route-static 0.0.0.0 0.0.0.0 25.25.25.5
[R2]ip route-static 192.168.2.0 255.255.255.0 192.168.24.4
R4:
[R4]ip route-static 0.0.0.0 0.0.0.0 192.168.24.2测试:
PC1-R1

R1-R2

②在出口路由器配置ACL
R1:
[R1-acl-adv-3000]acl 3000
[R1-acl-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
R2:
[R2]acl 3000
[R2-acl-adv-3000]rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255③创建安全提议
这边我用的是AH-ESP封装协议
R1:
[R1]ipsec proposal AB
[R1-ipsec-proposal-AB]encapsulation-mode tunnel
[R1-ipsec-proposal-AB]transform ah-esp
[R1-ipsec-proposal-AB]ah authentication-algorithm md5
[R1-ipsec-proposal-AB]esp authentication-algorithm md5
[R1-ipsec-proposal-AB]esp encryption-algorithm aes-128
R2:
[R2]ipsec proposal AB
[R2-ipsec-proposal-AB]encapsulation-mode tunnel
[R2-ipsec-proposal-AB]transform ah-esp
[R2-ipsec-proposal-AB]ah authentication-algorithm md5
[R2-ipsec-proposal-AB]esp authentication-algorithm md5
[R2-ipsec-proposal-AB]esp encryption-algorithm aes-128查看配置:

④创建安全策略
对端设备outbound和inbound的SPI数字需要相反(即A的outbound=B的ibound)
R1:
[R1]ipsec policy p1 10 manual
[R1-ipsec-policy-manual-p1-10] security acl 3000
[R1-ipsec-policy-manual-p1-10] proposal AB
[R1-ipsec-policy-manual-p1-10] tunnel local 15.15.15.1
[R1-ipsec-policy-manual-p1-10] tunnel remote 25.25.25.2
定义ESP安全联盟SPI
[R1-ipsec-policy-manual-p1-10] sa spi inbound esp 654321
[R1-ipsec-policy-manual-p1-10] sa spi outbound esp 123456
定义ESP验证密钥
[R1-ipsec-policy-manual-p1-10] sa string-key inbound esp simple 654321
[R1-ipsec-policy-manual-p1-10] sa string-key outbound esp simple 123456
定义AH安全联盟SPI
[R1-ipsec-policy-manual-p1-10] sa spi inbound ah 123456
[R1-ipsec-policy-manual-p1-10] sa spi outbound ah 654321
定义AH验证密钥
[R1-ipsec-policy-manual-p1-10] sa string-key inbound ah simple 654321
[R1-ipsec-policy-manual-p1-10] sa string-key outbound ah simple 123456
R2:
[R2]ipsec policy p1 10 manual
[R2-ipsec-policy-manual-p1-10] security acl 3000
[R2-ipsec-policy-manual-p1-10] proposal AB
[R2-ipsec-policy-manual-p1-10] tunnel local 25.25.25.2
[R2-ipsec-policy-manual-p1-10] tunnel remote 15.15.15.1
定义安全联盟SPI
[R2-ipsec-policy-manual-p1-10] sa spi inbound esp 123456
[R2-ipsec-policy-manual-p1-10] sa spi outbound esp 654321
定义ESP验证密钥
[R2-ipsec-policy-manual-p1-10] sa string-key inbound esp simple 123456
[R2-ipsec-policy-manual-p1-10] sa string-key outbound esp simple 654321
定义AH安全联盟SPI
[R2-ipsec-policy-manual-p1-10] sa spi inbound ah 654321
[R2-ipsec-policy-manual-p1-10] sa string-key inbound ah simple 123456
定义AH验证密钥
[R2-ipsec-policy-manual-p1-10] sa spi outbound ah 123456
[R2-ipsec-policy-manual-p1-10] sa string-key outbound ah simple 654321⑤出接口调用安全策略
R1:
[R1]int g0/0/1
[R1-GigabitEthernet0/0/1]ipsec policy p1
R2:
[R2]int g0/0/0
[R2-GigabitEthernet0/0/0]ipsec policy p1
最后成功实现数据在公网中的封装与加密

如果出现以下报错:
说明你的安全策略或者安全提议配置错误或左右不对等
三、wireshark抓包分析
(在R5连接R1的接口上抓包)

封装的格式为:




























 1346
1346

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








