先辈们的学习链接:
概率论网址收集:https://blog.csdn.net/qq_53631388/article/details/125352583
概率论积分表:http://t.csdnimg.cn/fV2q1
数电资料:http://t.csdnimg.cn/dexze (已经不可用了…)
大二下物联整体指南:http://t.csdnimg.cn/p7zSu
国院生涯规划问题:https://blog.csdn.net/qq_53631388/article/details/138234604?spm=1001.2014.3001.5502
产品开发:搜索csdn“围巾师傅”的博客
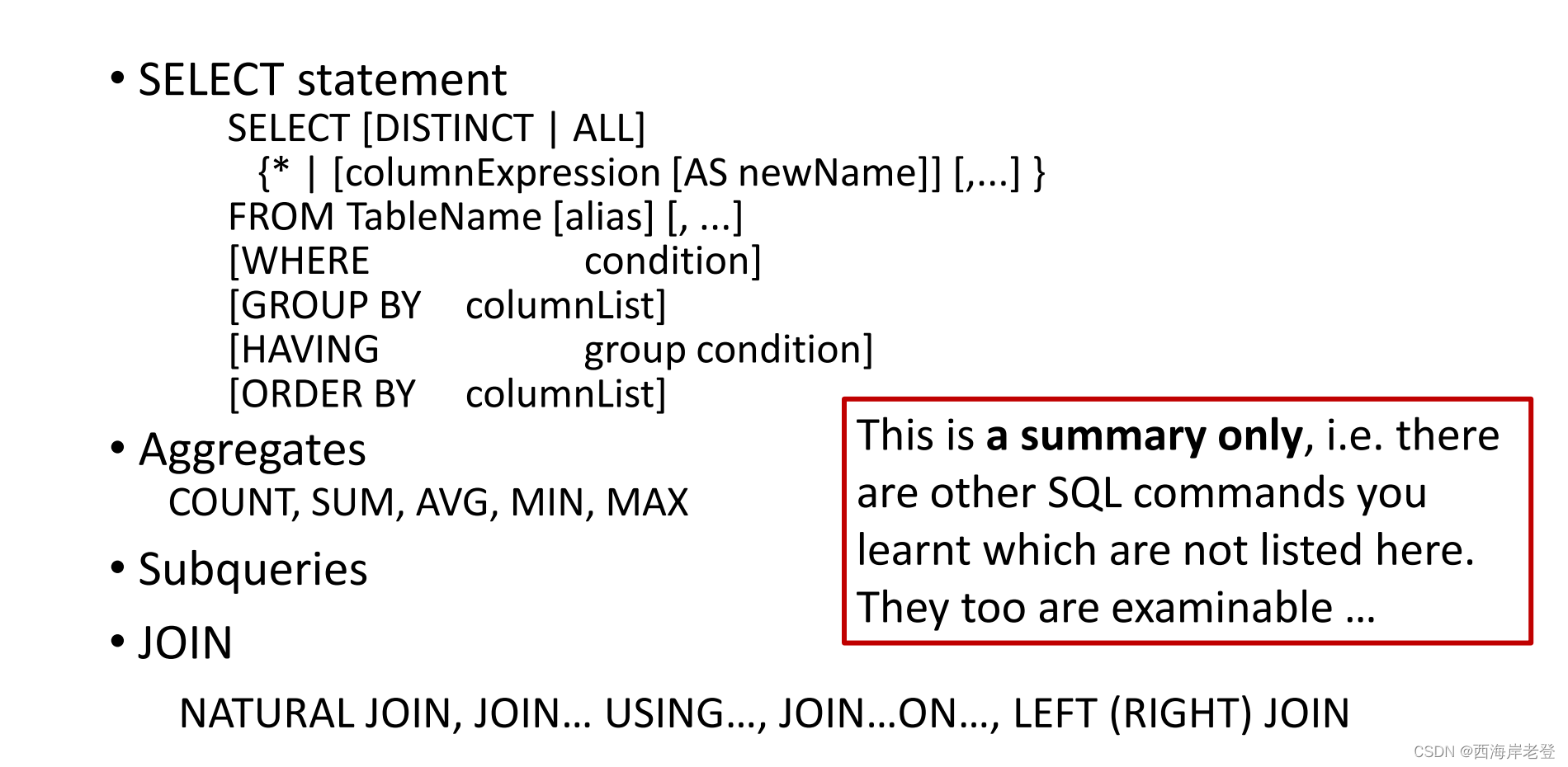
这里写目录标题
- 数据库
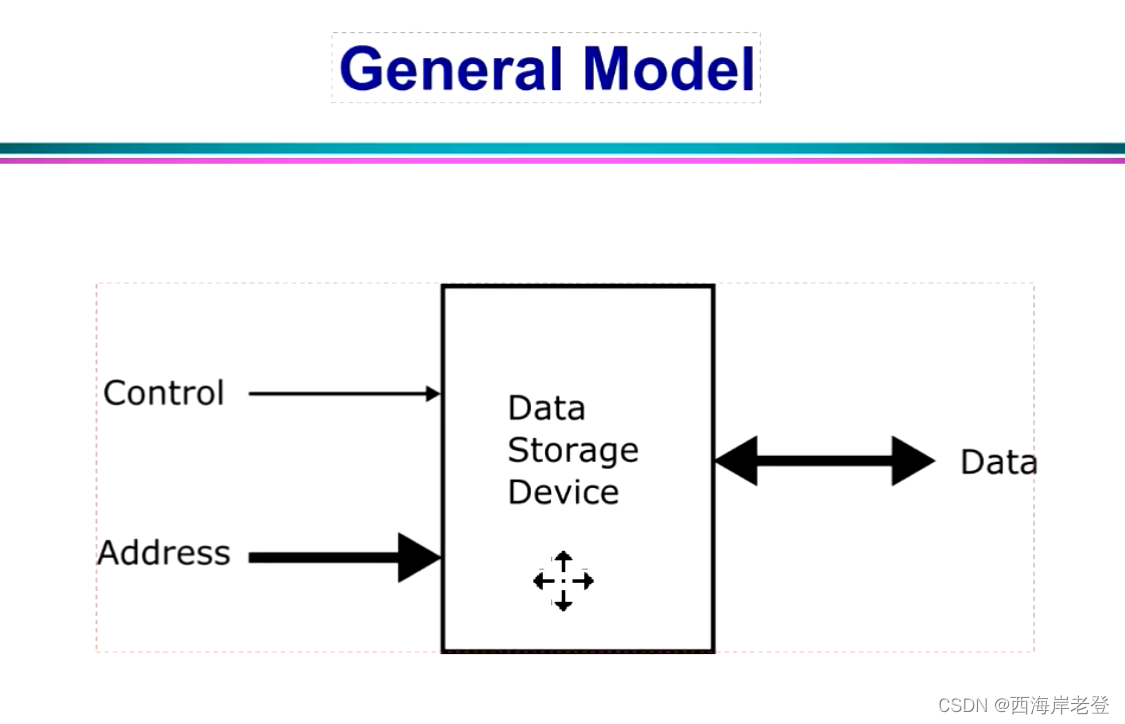
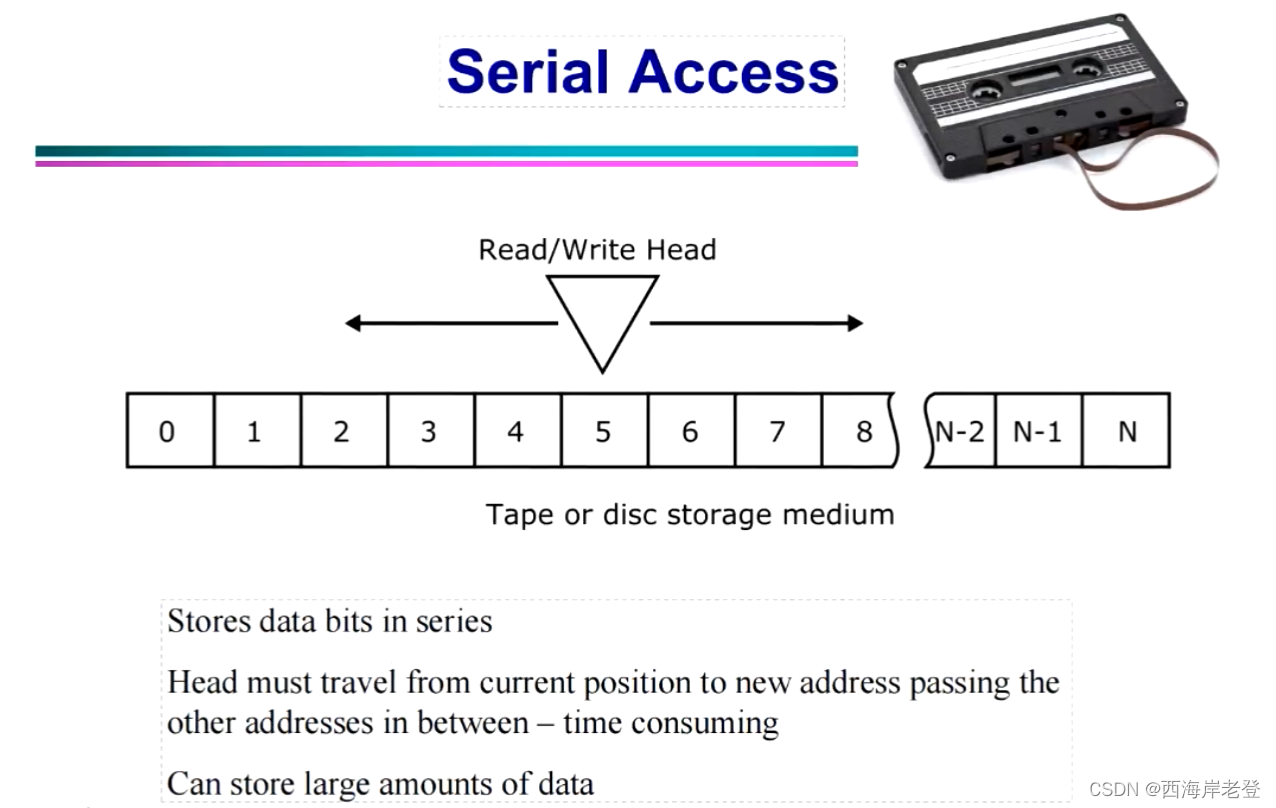
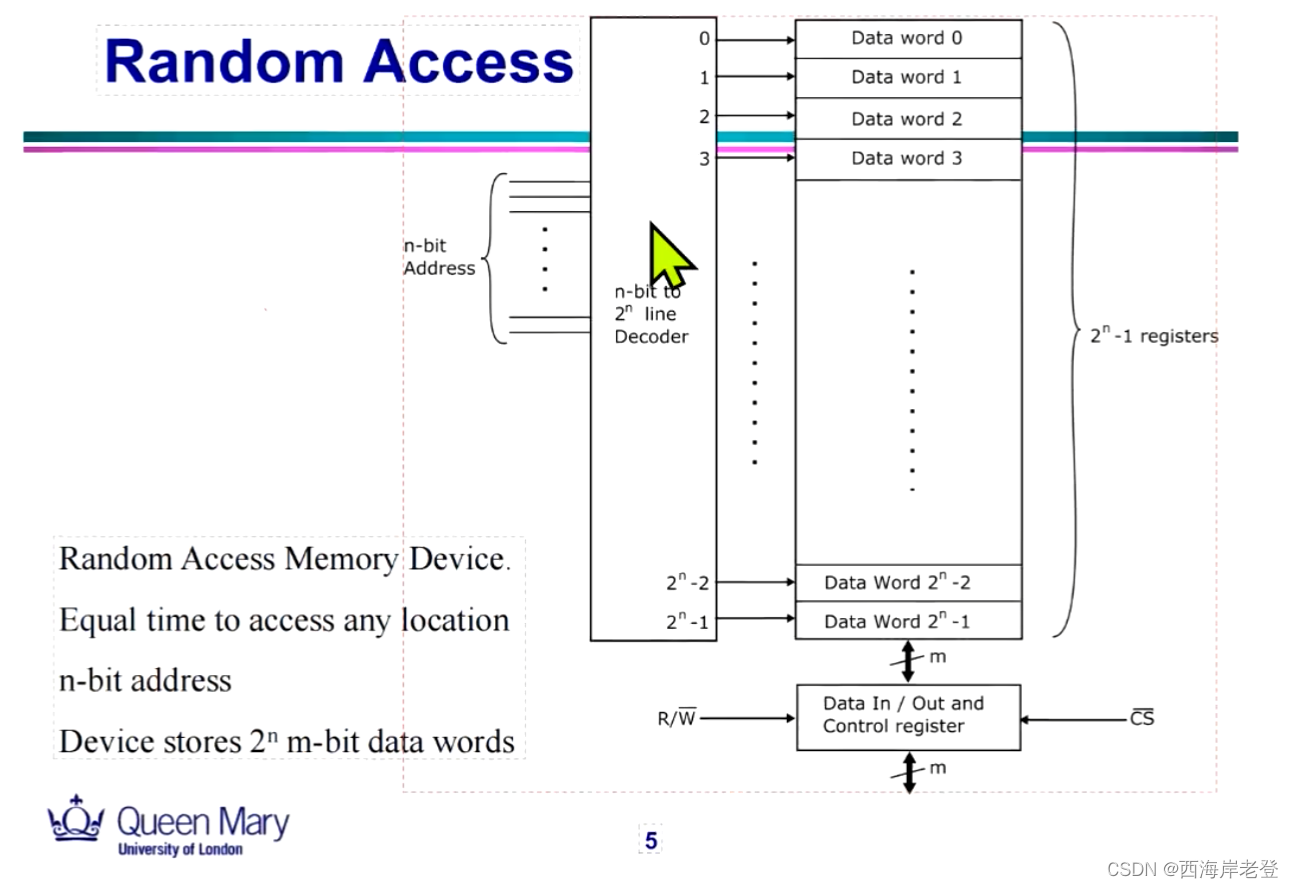
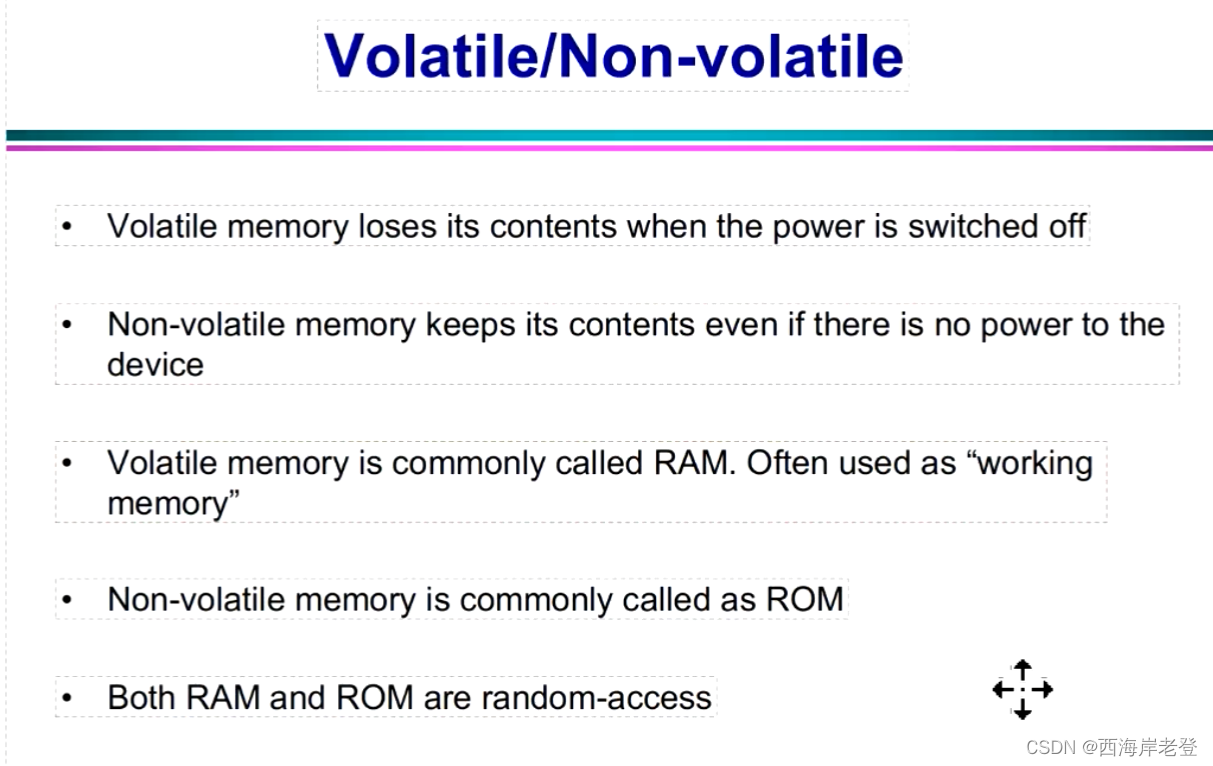
- Data
- Database
- DBMS
- Data Model
- Relation
- Attribute
- Tuple
- Cardinality
- Degree
- Domain
- Candidate (Primary) Key
- Foreign Key
- Multiplicity
- Purpose of Normalization
- • Large databases are used by many people
- • If we don’t allow for concurrency then transactions are run sequentially
- Distributed Database
- Distributed DBMS
- Deference between distributed process and distributed DBMS
- explain what a view is in database and how it can provide security to the database.
- explain 4 principles in data ethics
- 数电
- java
- 产开 大头
- 概率论
数据库
基于revision ppt的地毯式复习:
Data
Facts and analysis collected together for reference and analysis.
Database
A shared collection of logically related data (and a description of this data) designed to meet the information need of an organization.
DBMS
A software system that enables users to define, create, maintain, and control access to the database.
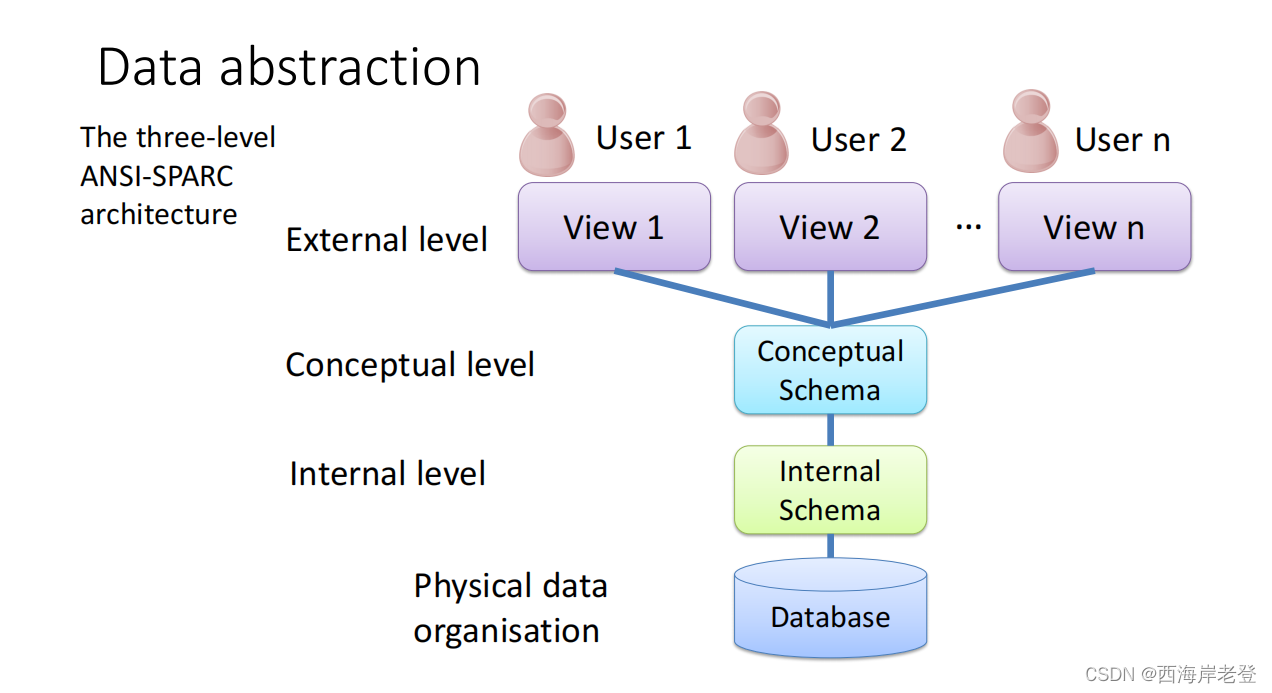
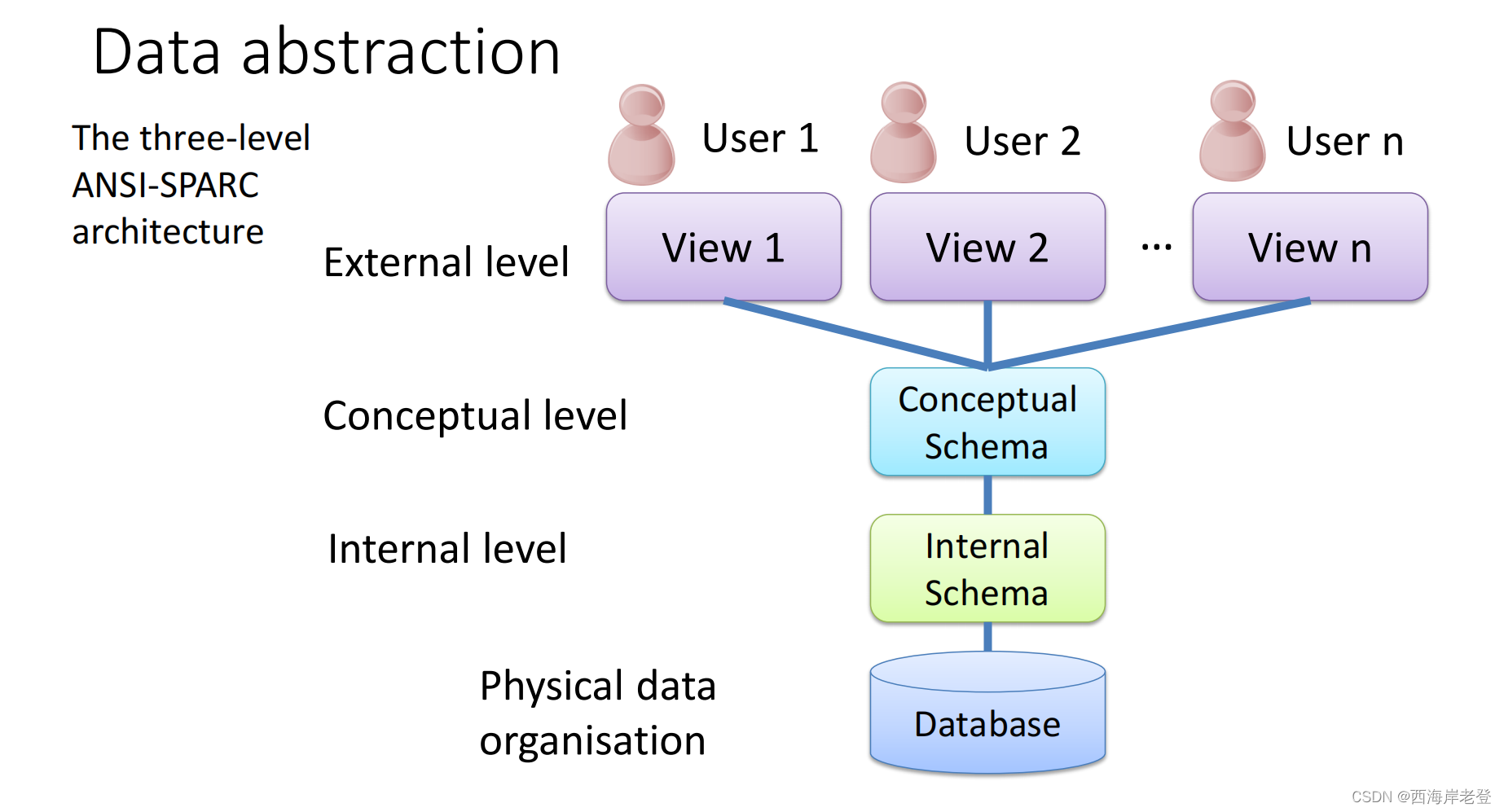
Data Model
A data model is a graphical description of the components of database.

Relation
A relation is a two-dimensional table arranged in columns and rows.
Attribute
An attribute is a named column of data.
Tuple
A tuple is a row of relation.
Cardinality
The number of tuples in a relation.
Degree
The number of attributes in a relation.
Domain
A set of allowable values for one or more attributes.
Candidate (Primary) Key
Selected to identify tuples uniquely within relation.
Foreign Key
Foreign key is an attribute or a set of attributes, within one relation that matches candidate(primary) key of another relation.

Multiplicity
number (or range) of possible occurrences of an entity type that may relate to a single occurrence of an associated entity type through a particular relationship

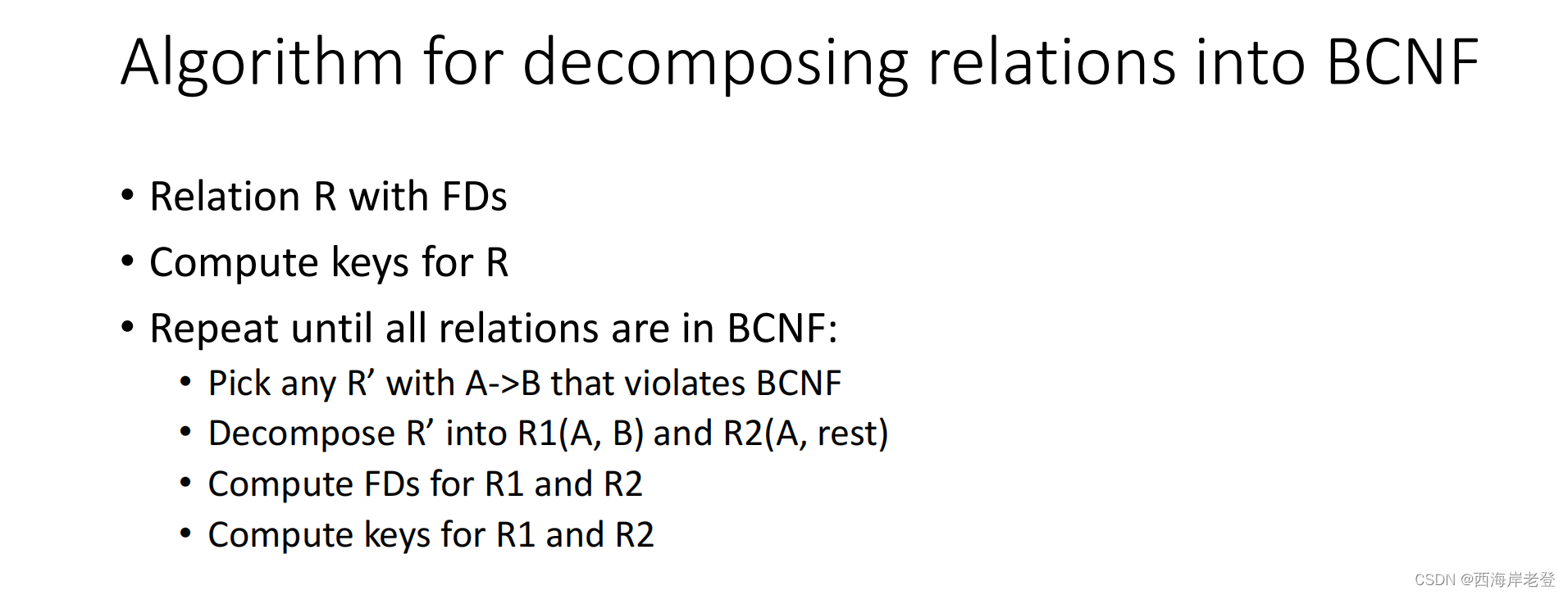
Purpose of Normalization
Normalization is a technique for producing a suitable set of relations that support the data requirements of an enterprise.
What is a suitable set of relations
• the minimal number of attributes necessary
to support the data requirements of the
enterprise;
• attributes with a close logical relationship are
found in the same relation;
• minimal redundancy with each attribute
represented only once with the important
exception of attributes that form all or part of
foreign keys.
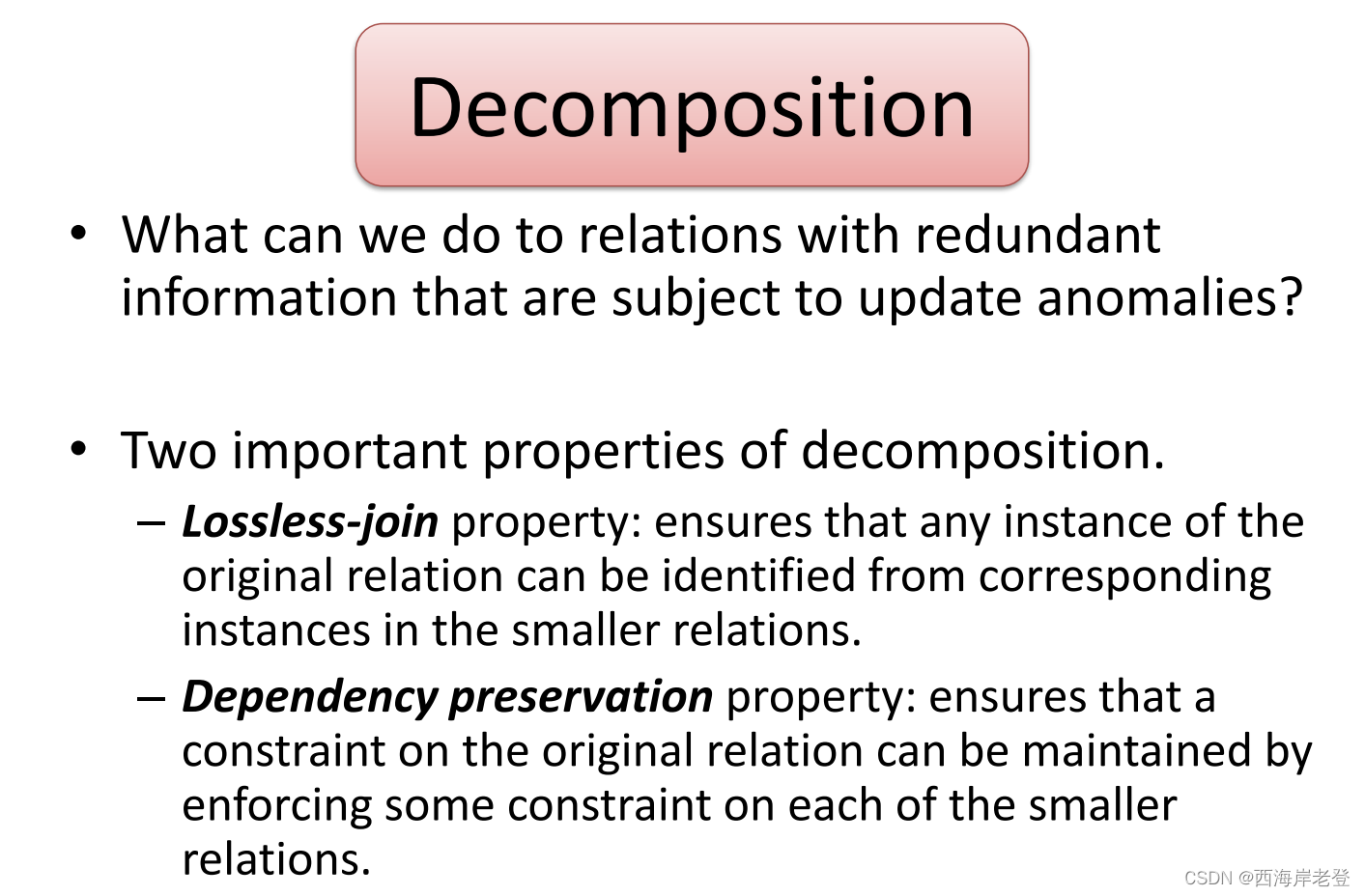
Data Redundancy and Update Anomalies
• Relations that contain redundant information
may have problems called update anomalies:
Include:
Insertion Anomalies, Deletion Anomalies, Modification Anomalies
无损连接和依赖保护

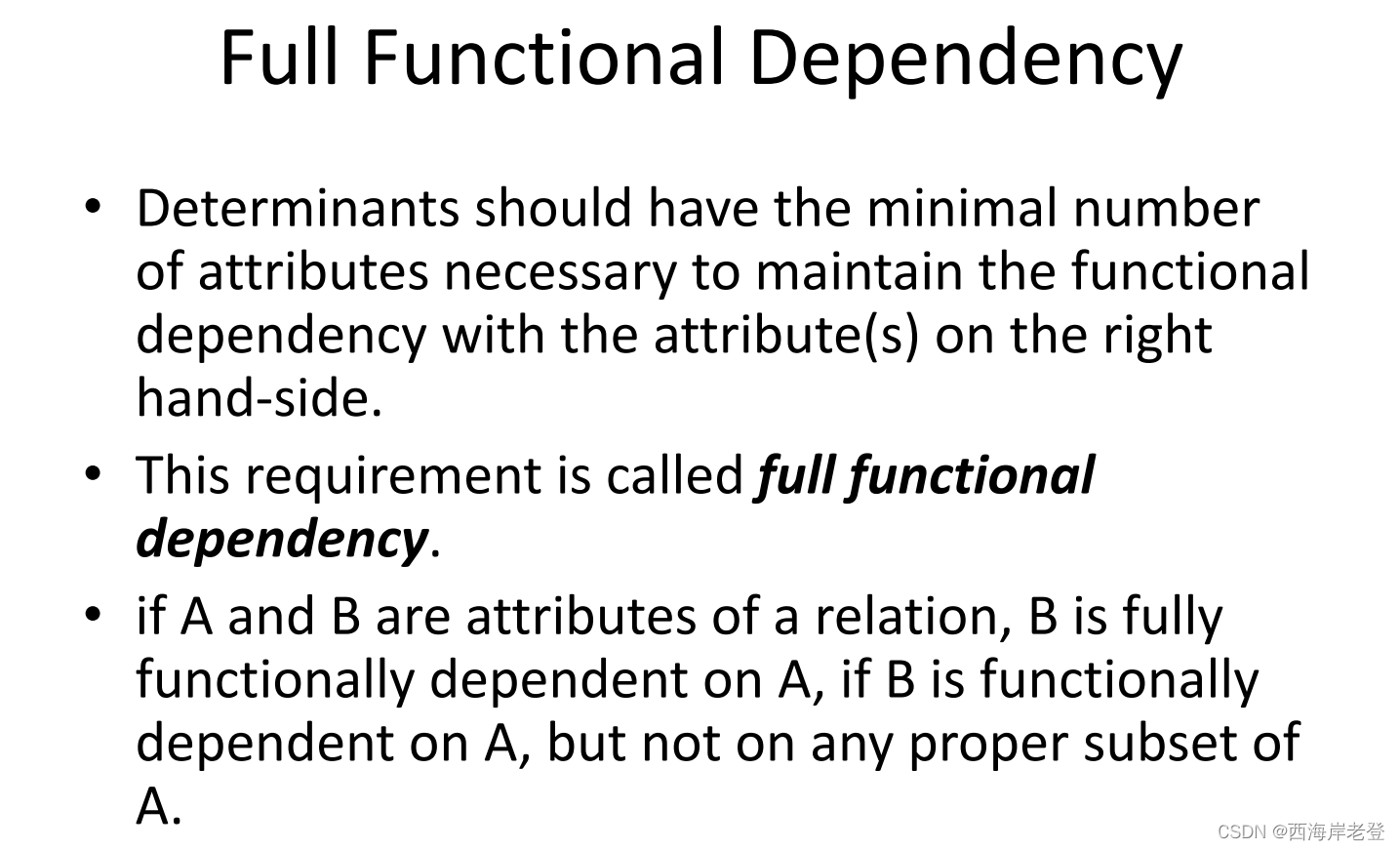
Functional dependency describes relationship
between attributes.
Functional dependency is a property of the meaning or
semantics of the attributes in a relation.
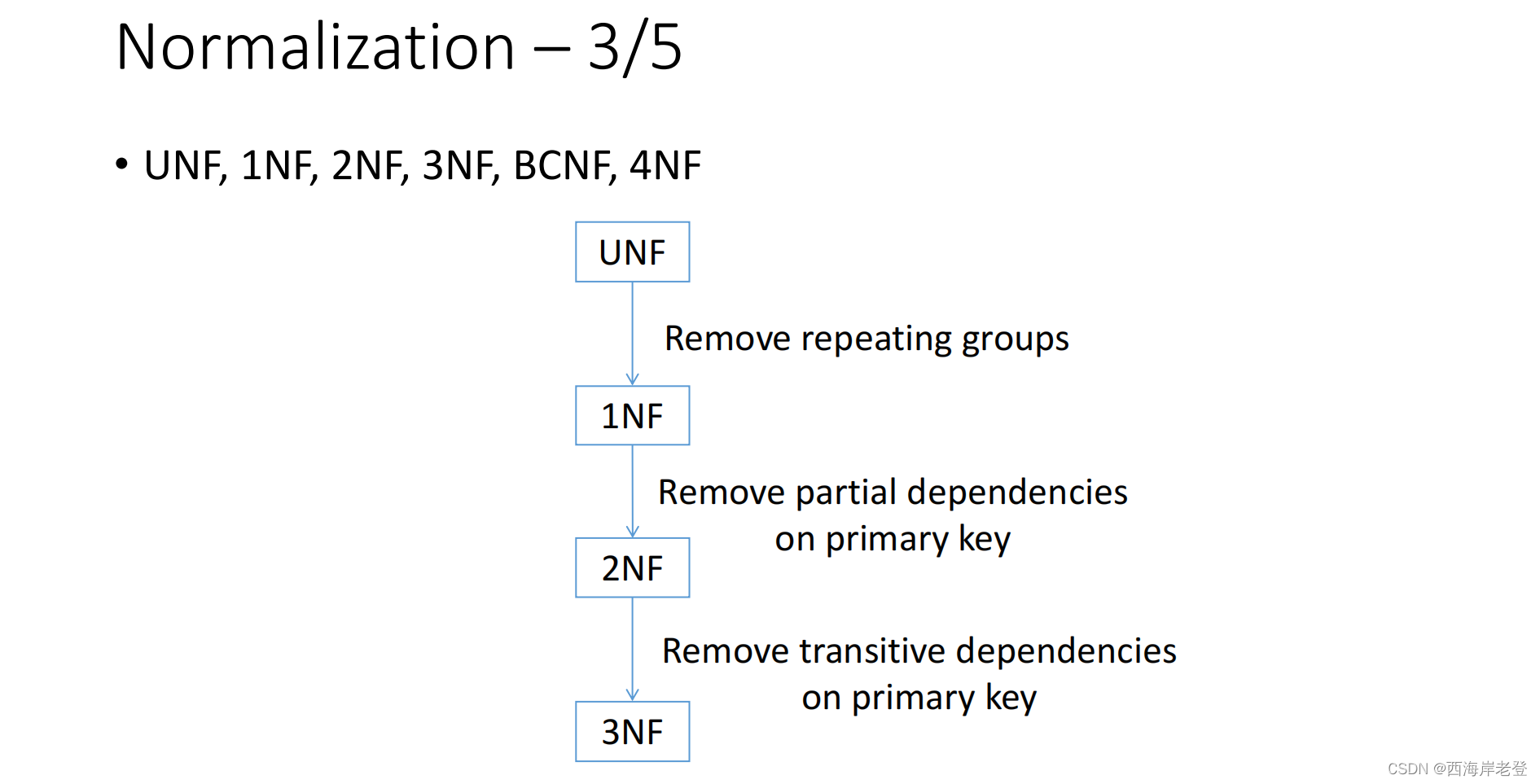
与之相对应的是:Partial Functional Dependency


网址(数据库三范式和BC范式的总结):https://blog.csdn.net/weixin_43954951/article/details/125494783

这里有点不太理解,会考吗??


回答Purpose从以下几个方面
• Large databases are used by many people
• Many transactions to be run on the database
• It is desirable to let them run at the same time as each
other
• Need to preserve isolation
• If we don’t allow for concurrency then transactions are run sequentially
• Have a queue of transactions
• Long transactions (e.g. backups) will make others wait
for long periods




Distribution Transparency
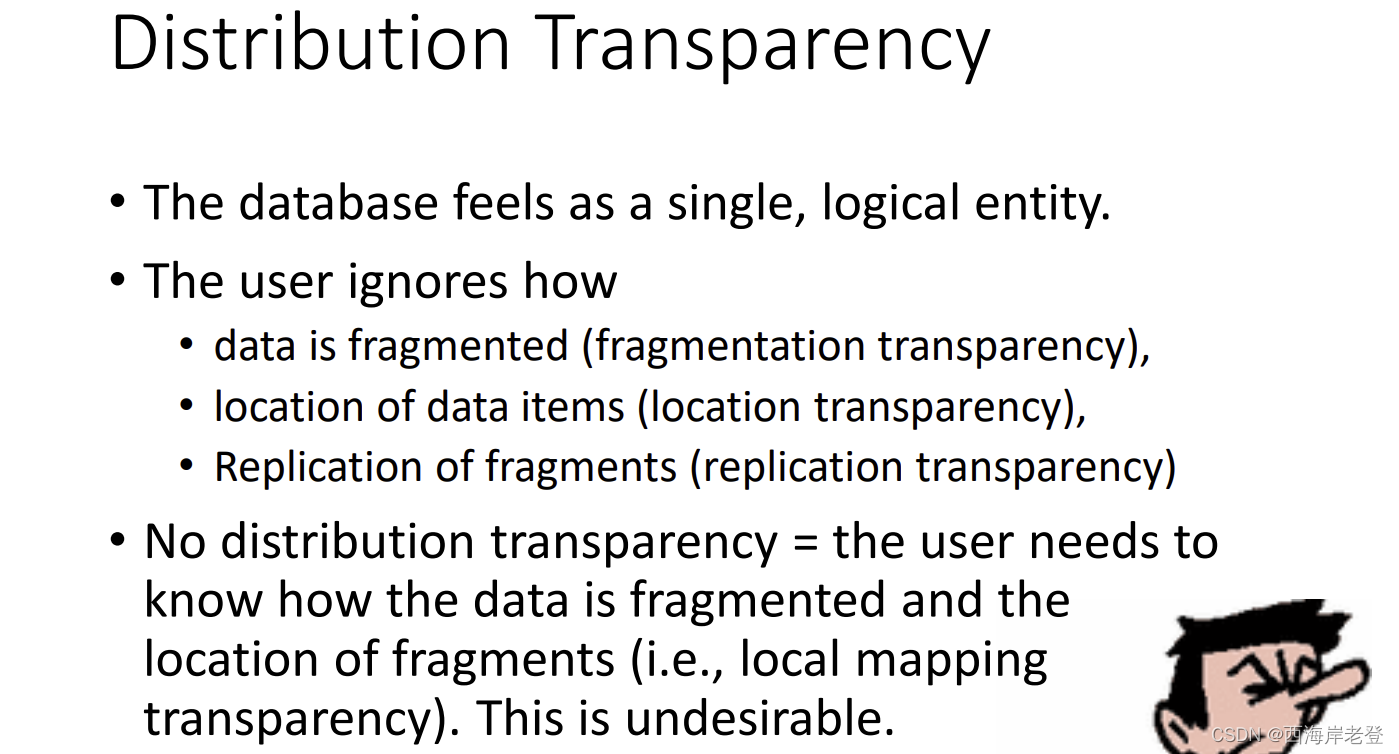
Transaction Transparency
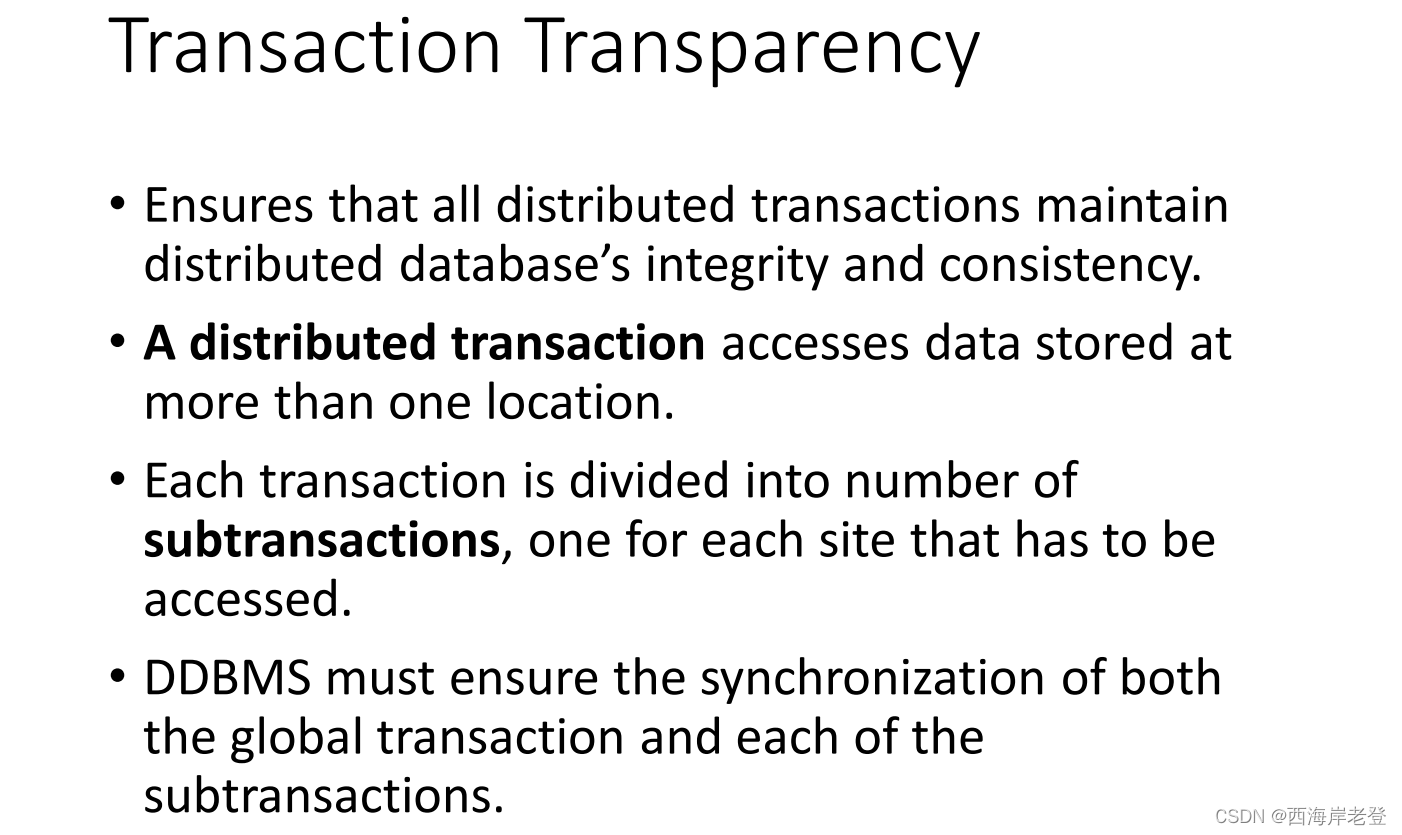
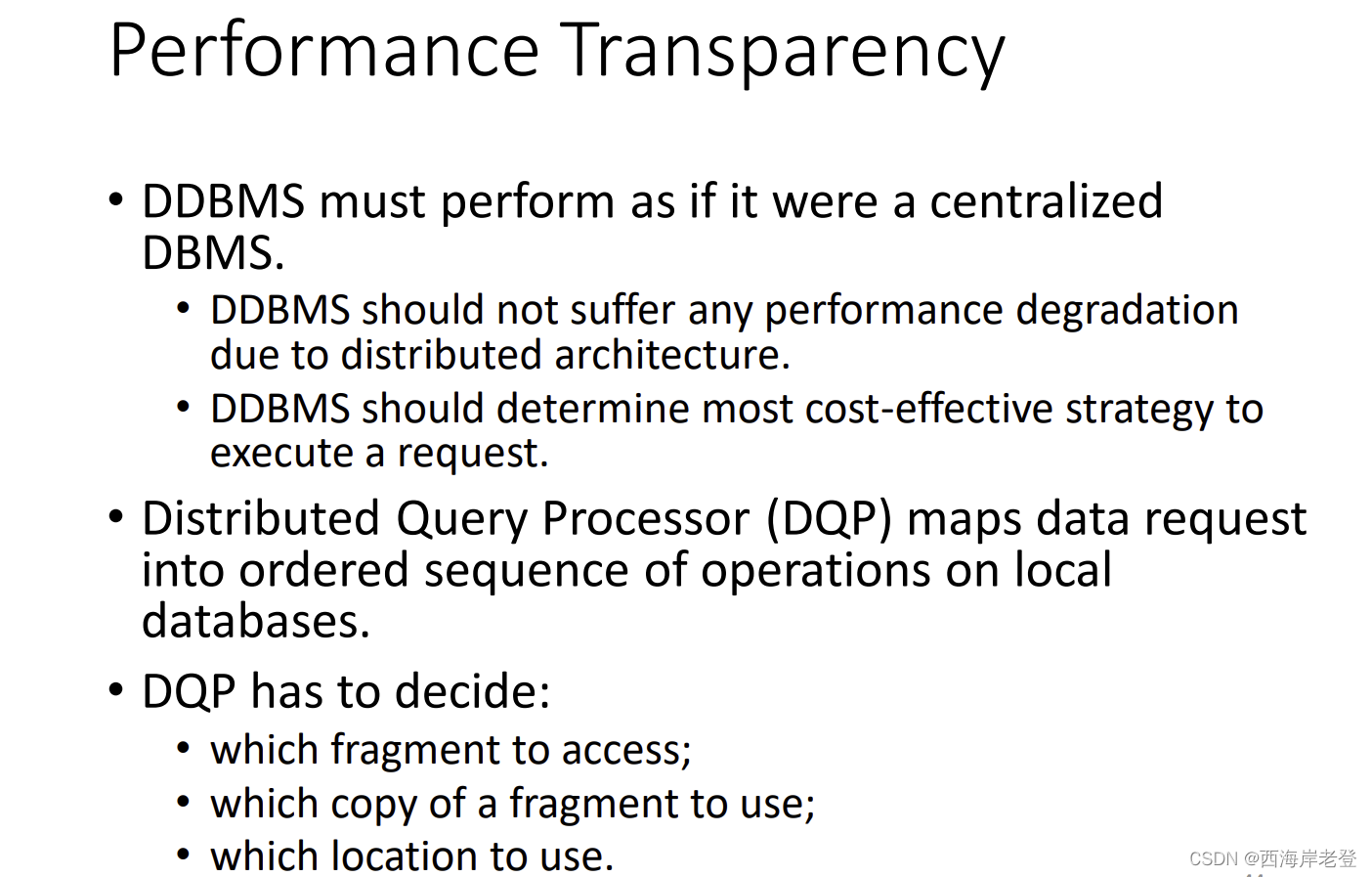
Performance Transparency
Advantages of DDBMSs
• Reflects organizational structure
• Improved shareability and local autonomy
• Improved availability
• Improved reliability
• Improved performance
• Economics
• Modular growth
Disadvantages of DDBMSs
• Complexity
• Cost
• Security
• Integrity control more difficult
• Lack of standards
• Lack of experience
• Database design more complex
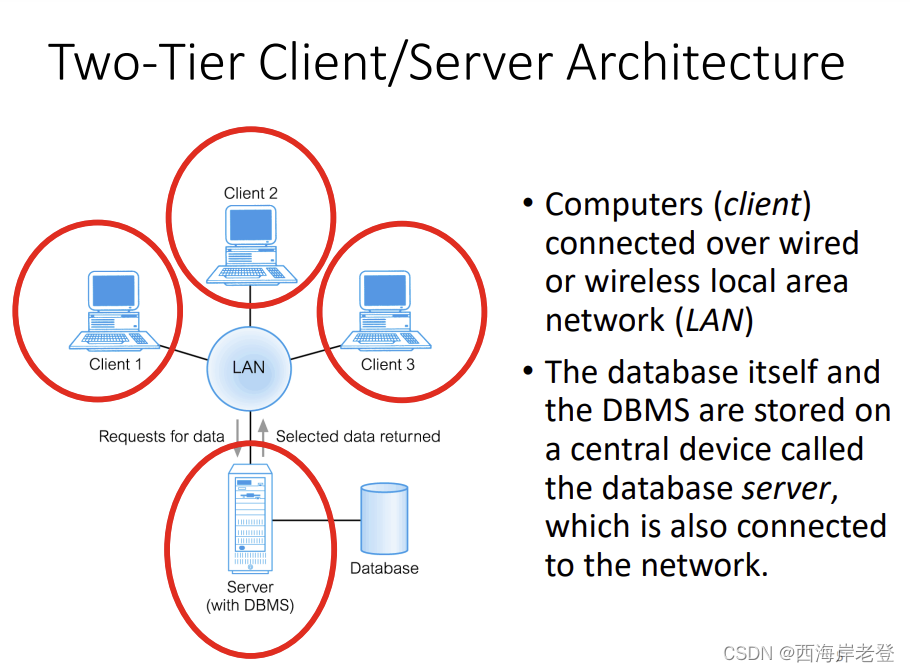
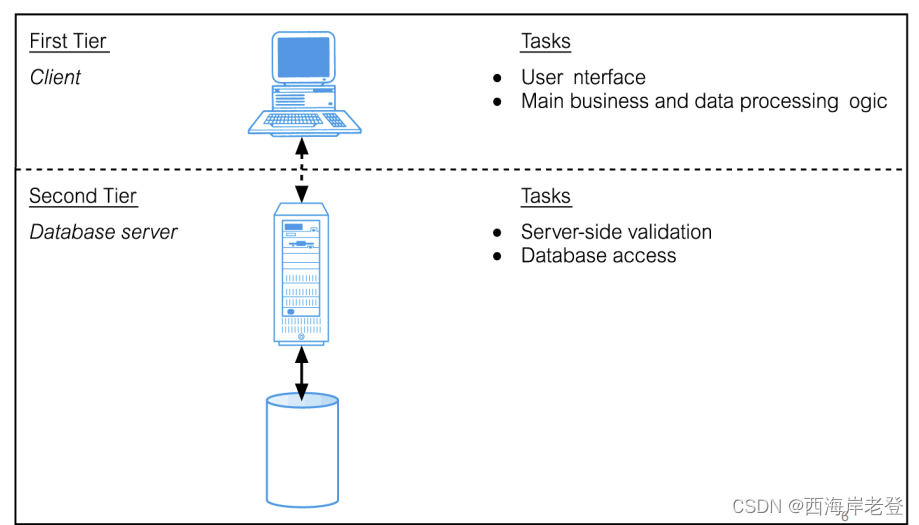
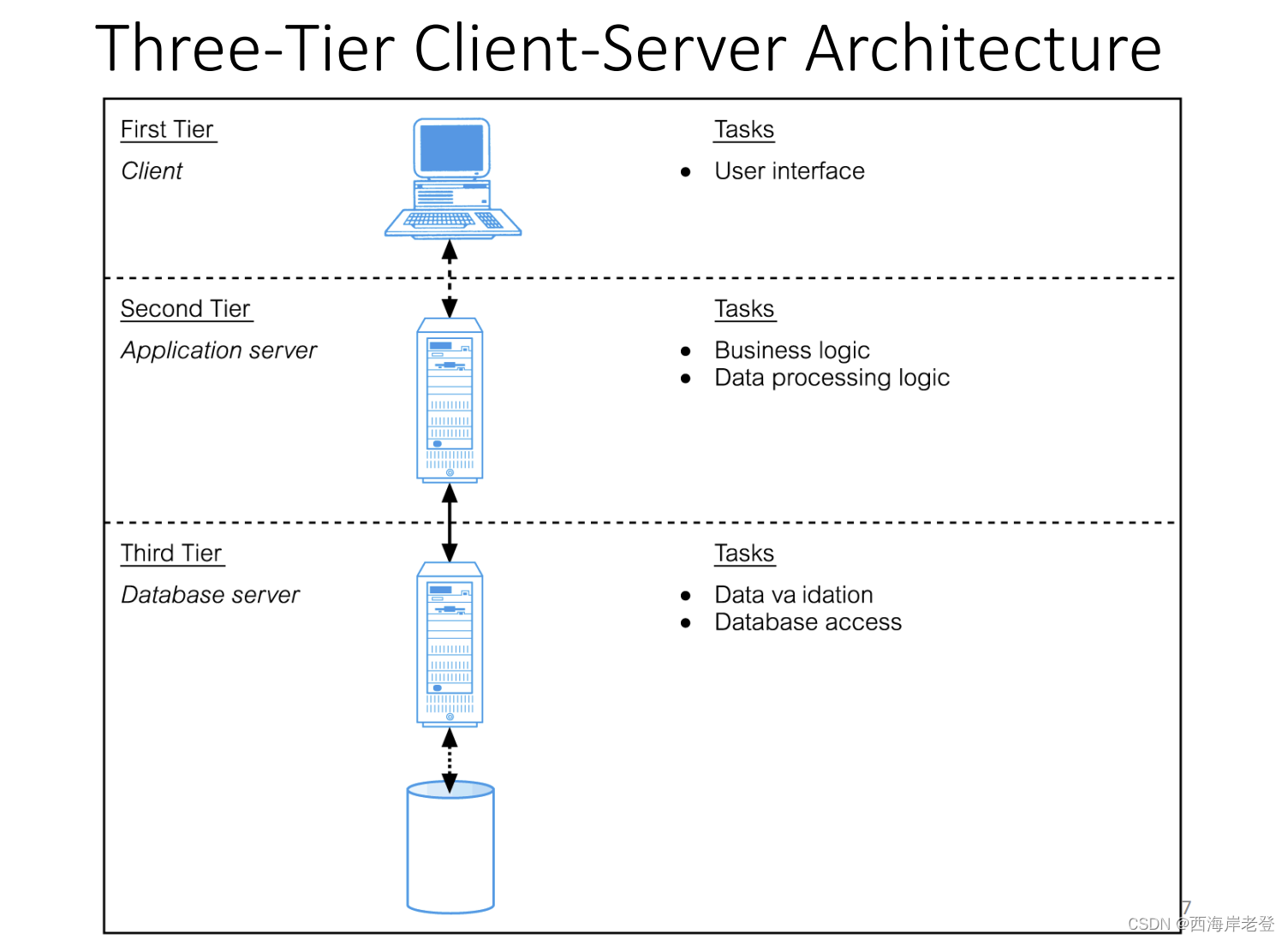
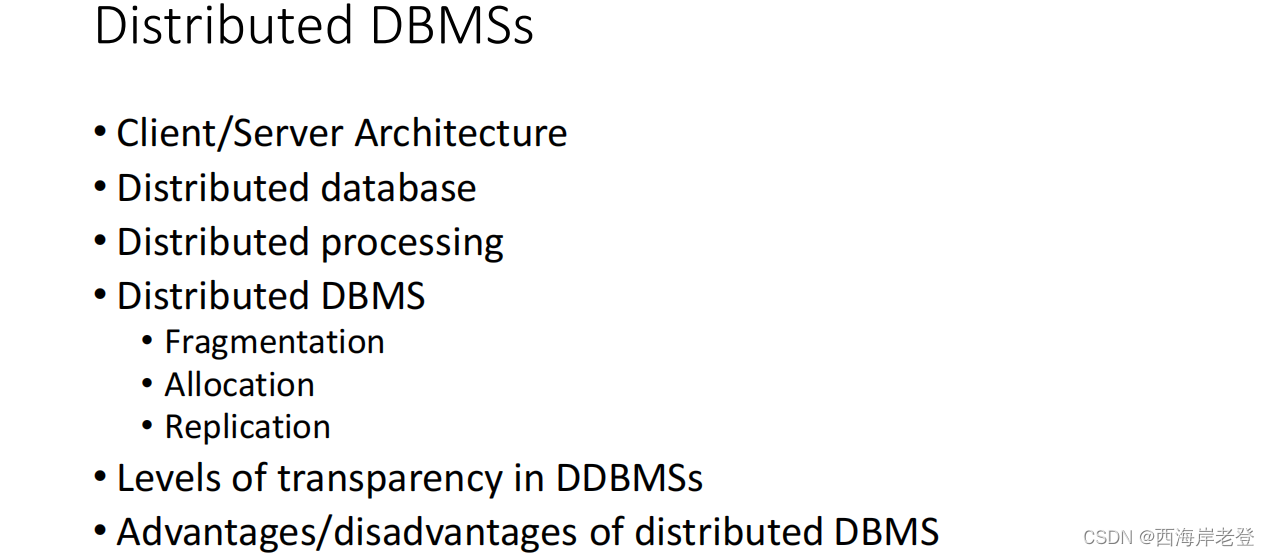
Distributed Database
A logically interrelated collection of shared data (and a
description of this data), physically spread over a computer
network.
Distributed DBMS
Software system that permits the management of the
distributed database and makes the distribution
transparent to users.
Deference between distributed process and distributed DBMS
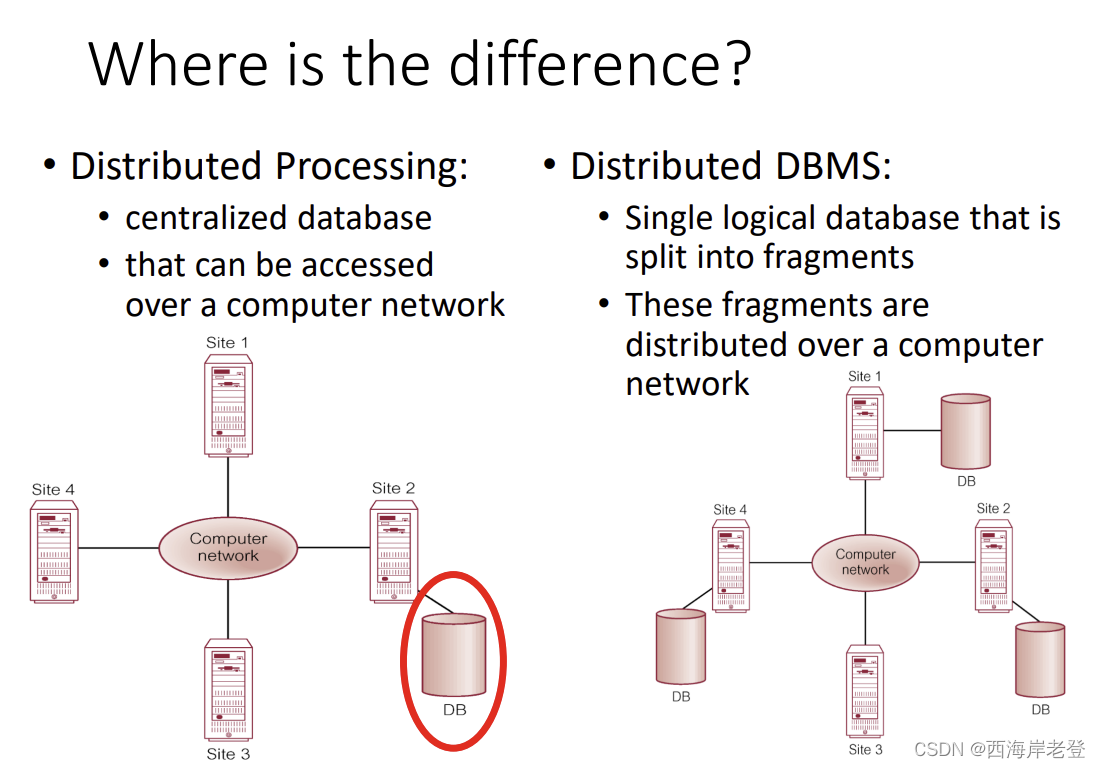

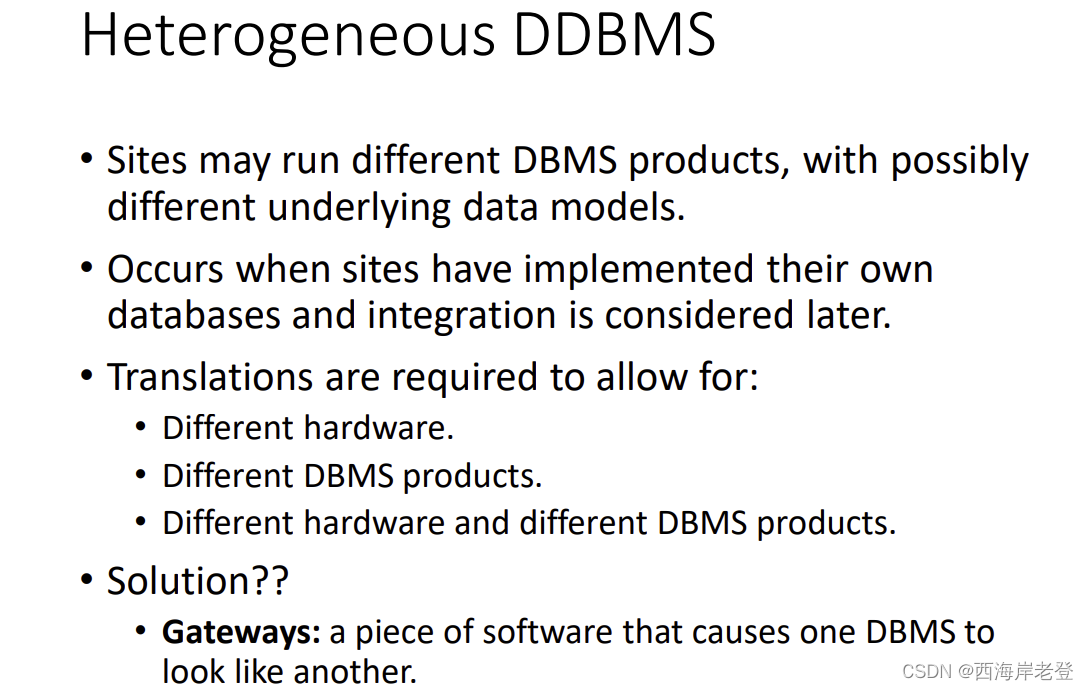
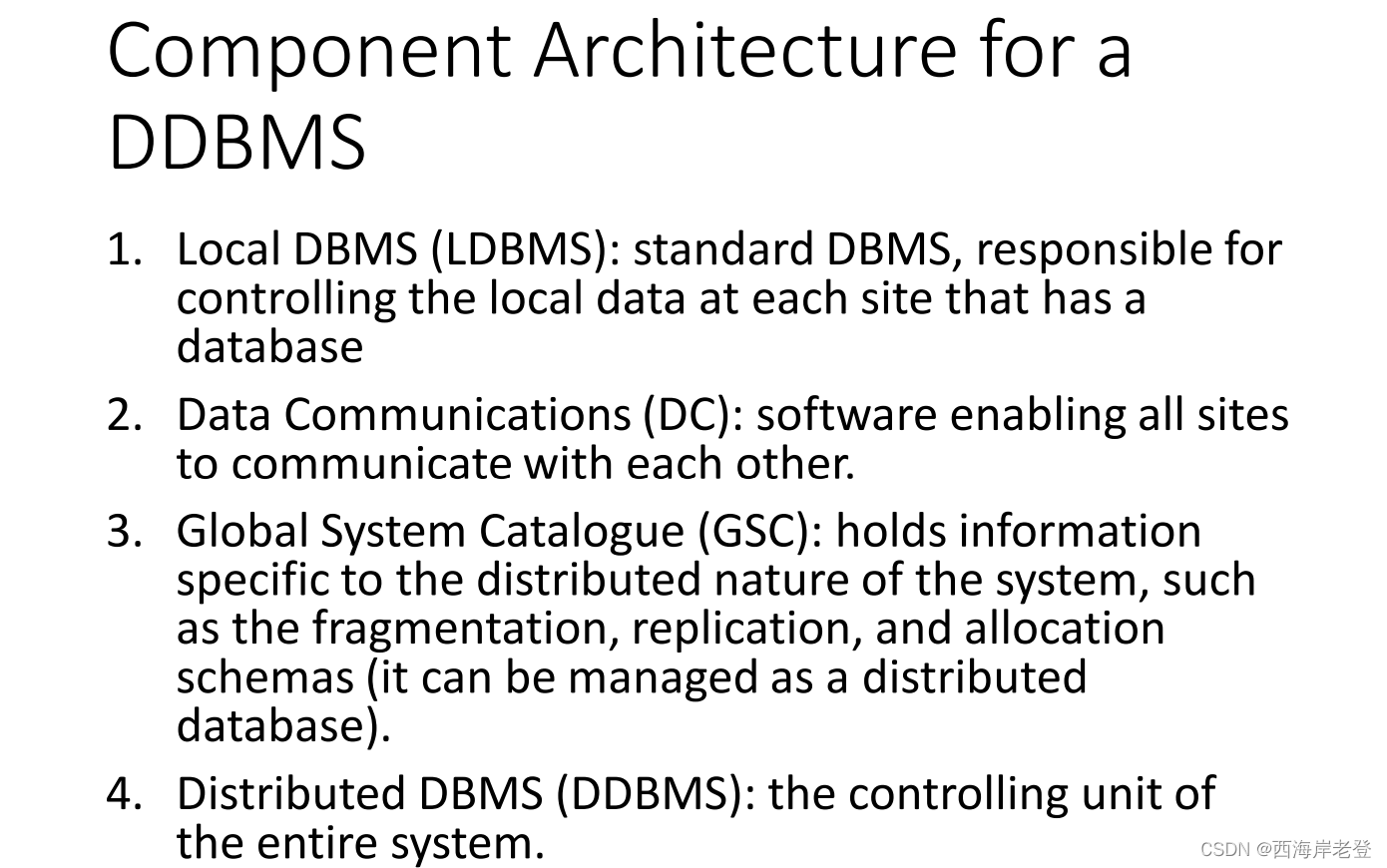
这一块有点没懂,应该不考??
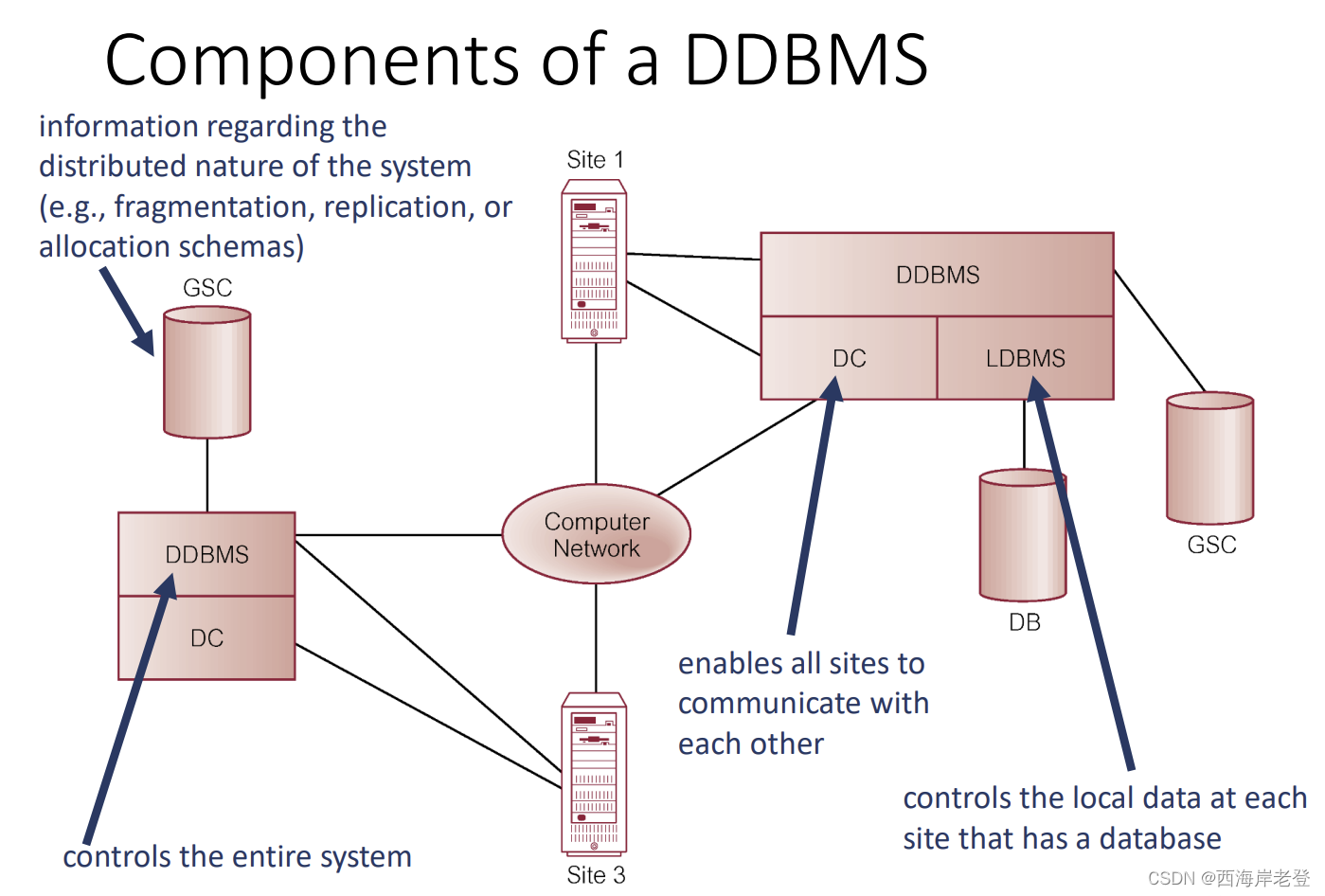

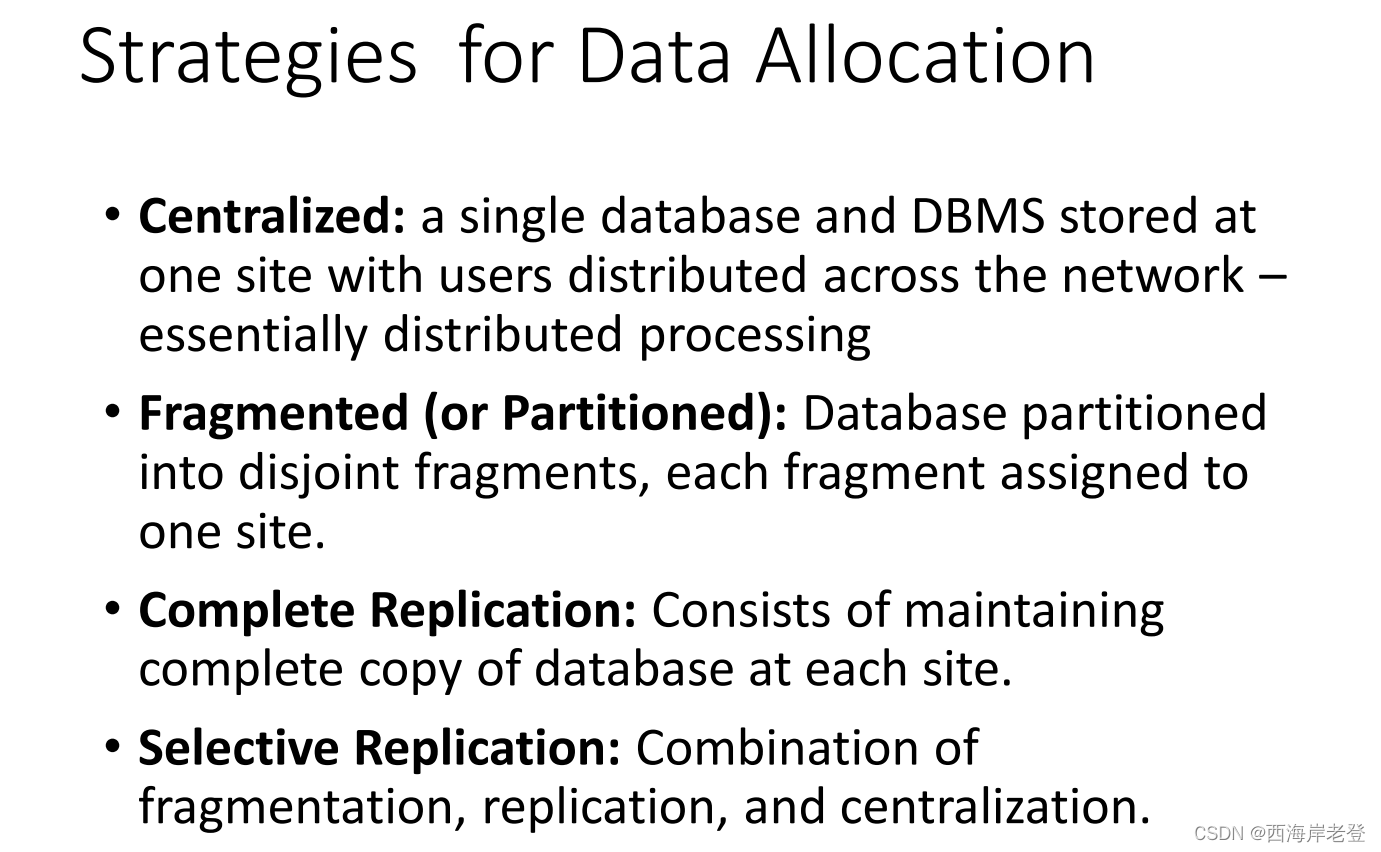



背诵第四周内容要点
会做nf的证明题??
tutorial 1
tutorial 2
六种database security measures:
Database Security measures
• Authorization
• Access controls
• Views
• Backup and recovery
• Integrity
• Encryption
explain what a view is in database and how it can provide security to the database.
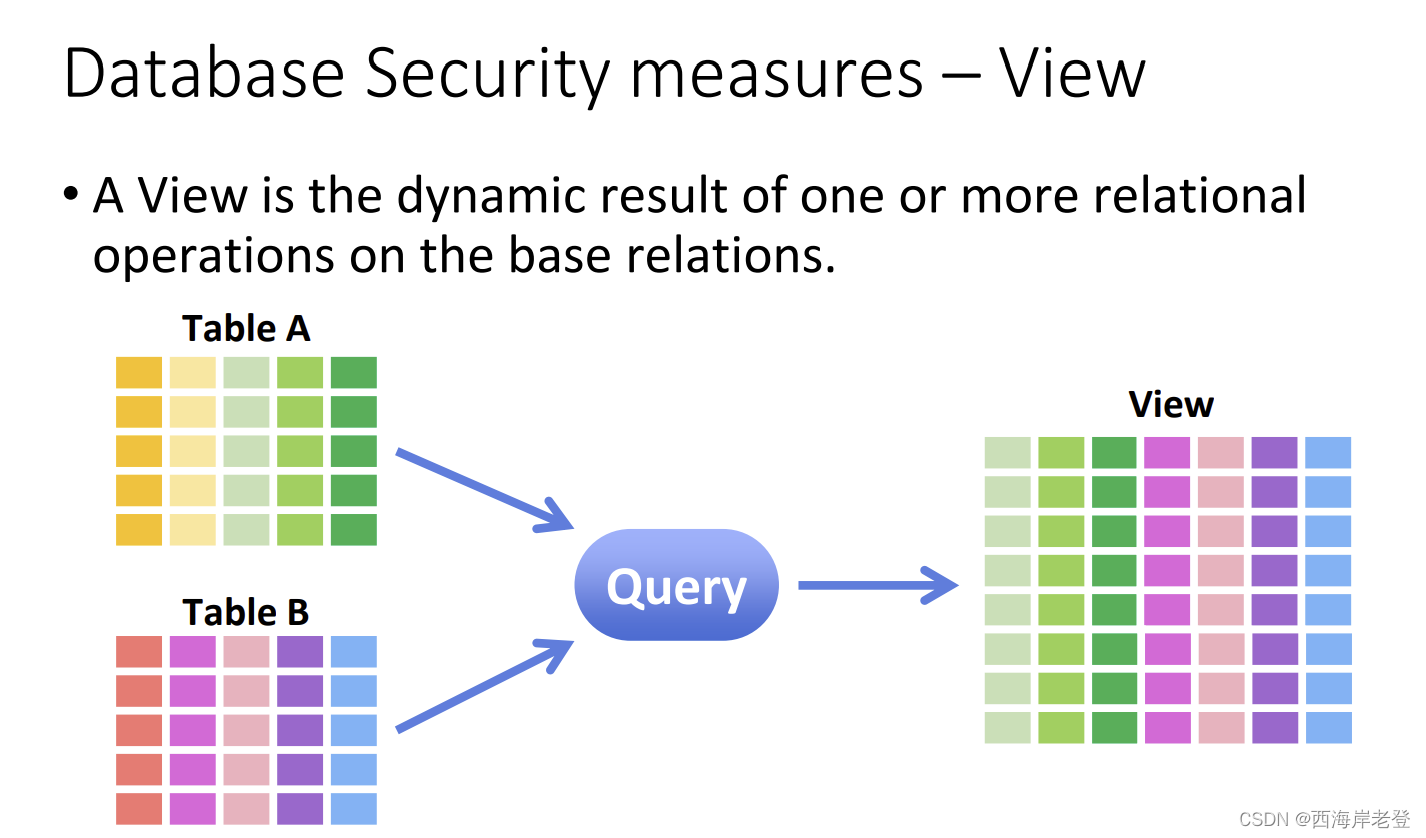

explain 4 principles in data ethics
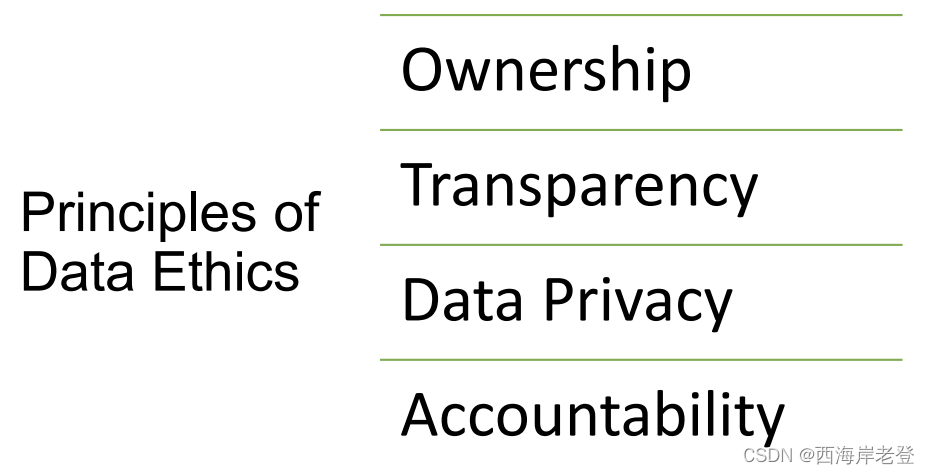
| The first principle of data ethics is that an individual has ownership over their personal information.• An individual should be able to make meaningful choices about personal data.• Consent should be obtained before you collect someone’s personal data. | Transparency refers to clear communication of what data will be gathered, whether (and how) it will be stored, how the data may be used, and who it might be shared with.• While terms and conditions or policies documents can be long, and almost require legal expertise, users should understand how the company will use their information |
| Data privacy is about ensuring data subjects’ privacy. • Personally identifiable information (PII) refers to any information linked to a person’s identity, including: • Full name, date of birth, address, phone number, credit card information, bank account number, passport number, etc • To protect individuals’ privacy, database security mechanisms are essential, so personal data doesn’t end up in the wrong hands. | Accountability refers to an organization taking responsibility fo what happens to an individual’s data after collecting it. • From data leaks to sales to a third party, companies need to accept accountability for the damage their processes can cause users. |
NoSQL Key features:
• Flexible schema
• Quicker/cheaper to set up
• Massive scalability
• Relaxed consistency --> higher
performance & availability
Database architectures
• Distributed database, Distributed DBMS
• Functions and architecture for a DDBMS
• Distributed database design: fragmentation, allocation
and replication
• Fragmentation techniques
• Levels of transparency in DDBMS
• Distribution transparency
• Transaction transparency
• Performance transparency
• Advantages and disadvantages of distributed databases
可见性 原子性 丢失
1.Lost Update Problem: Successfully completed update is overridden byanother user.
2.Uncommitted Dependency Problem/Dirty Read Problem:Occurs when one transaction can see intermediateresults of another transaction before it hascommitted.
3.Inconsistent Analysis Problem:Occurs when a transaction reads several values from the database but a second transaction updates some of them during the execution of thefirst.
数电
EPI:只被一个圈圈起来的1。每个卡诺图,如果是MSP,则一定包含EPI
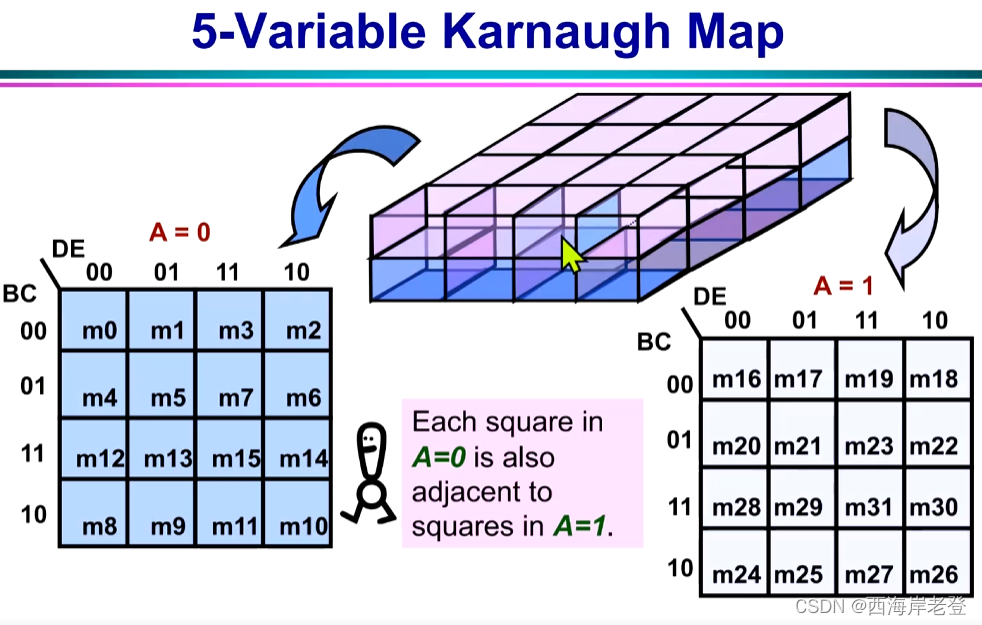
卡诺图的其他运用:
五变量卡诺图

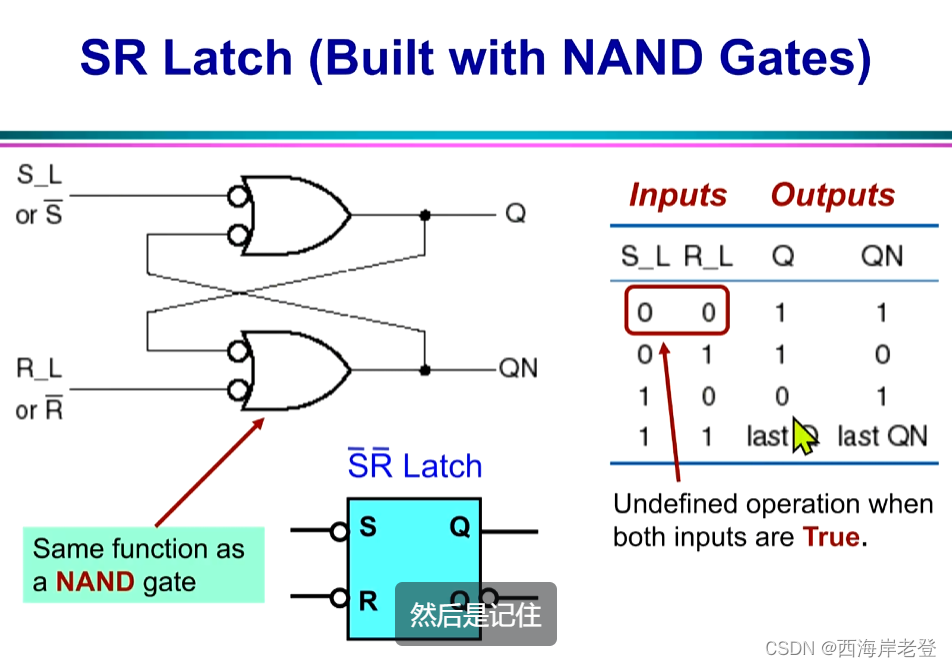
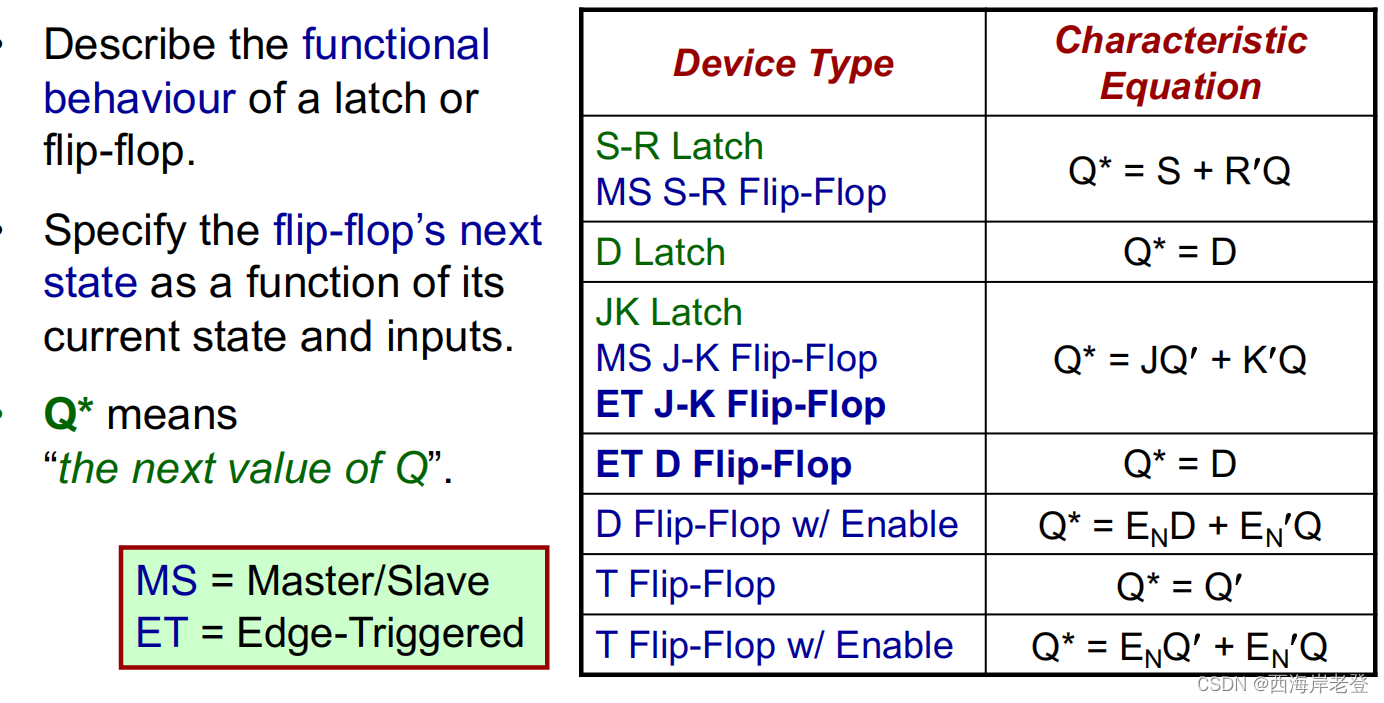
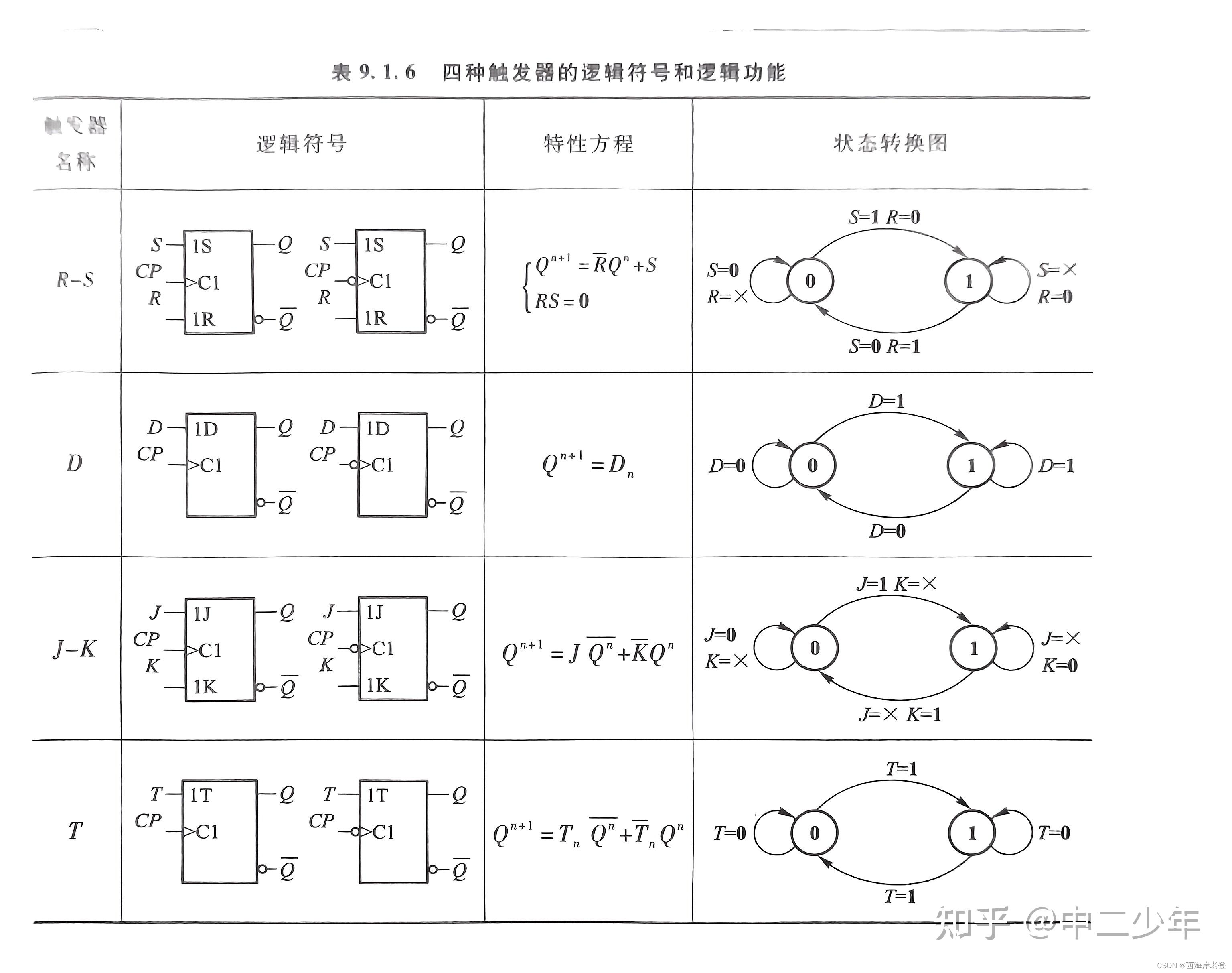
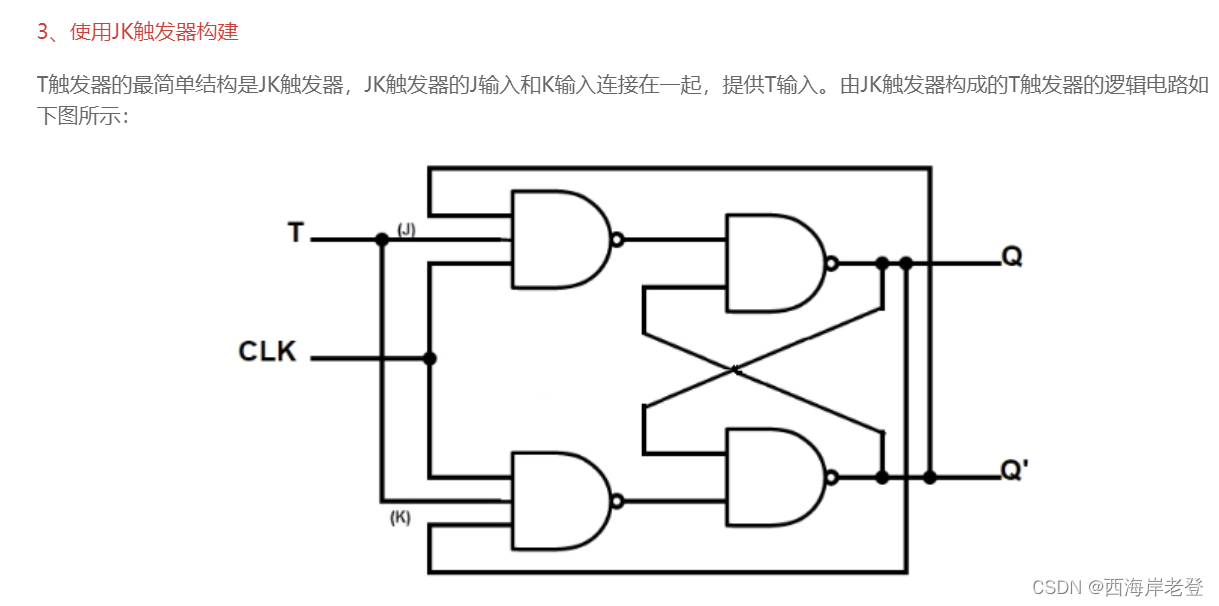
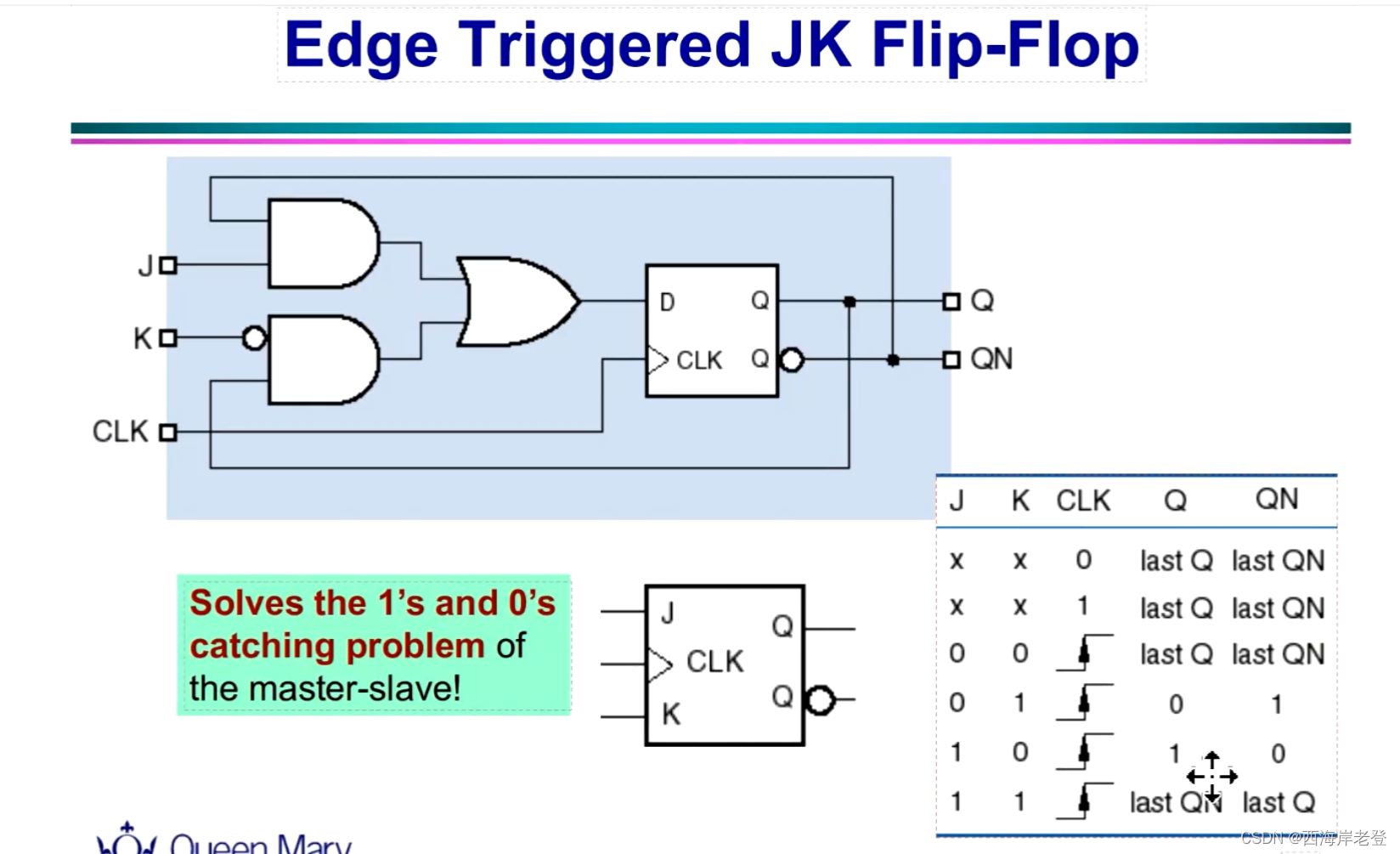
关于T触发器是怎么搭建起来的:https://www.mrchip.cn/newsDetail/897
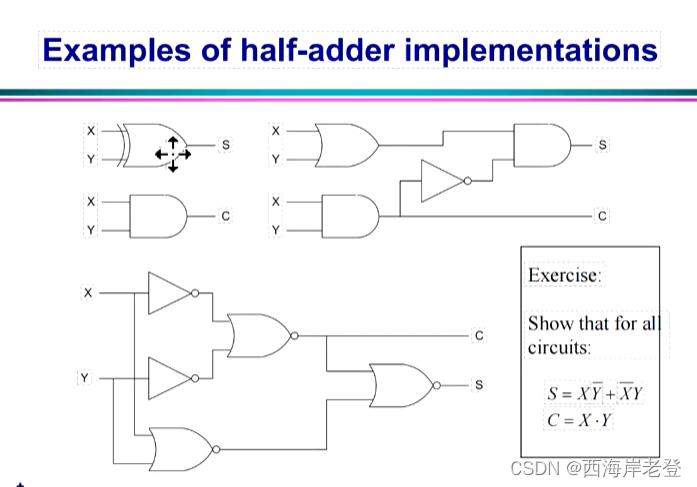
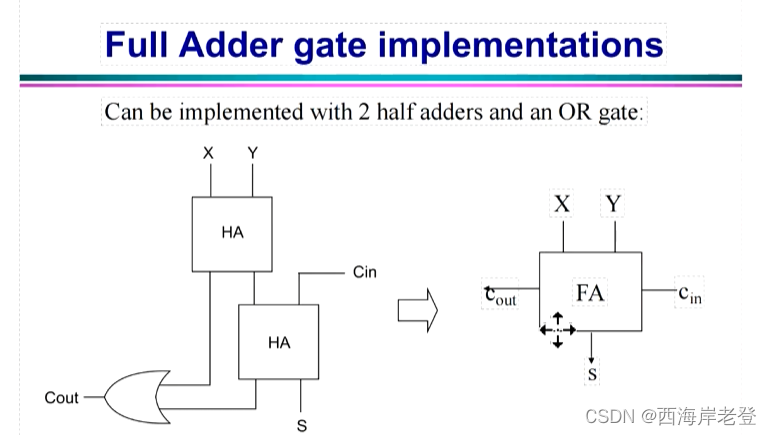
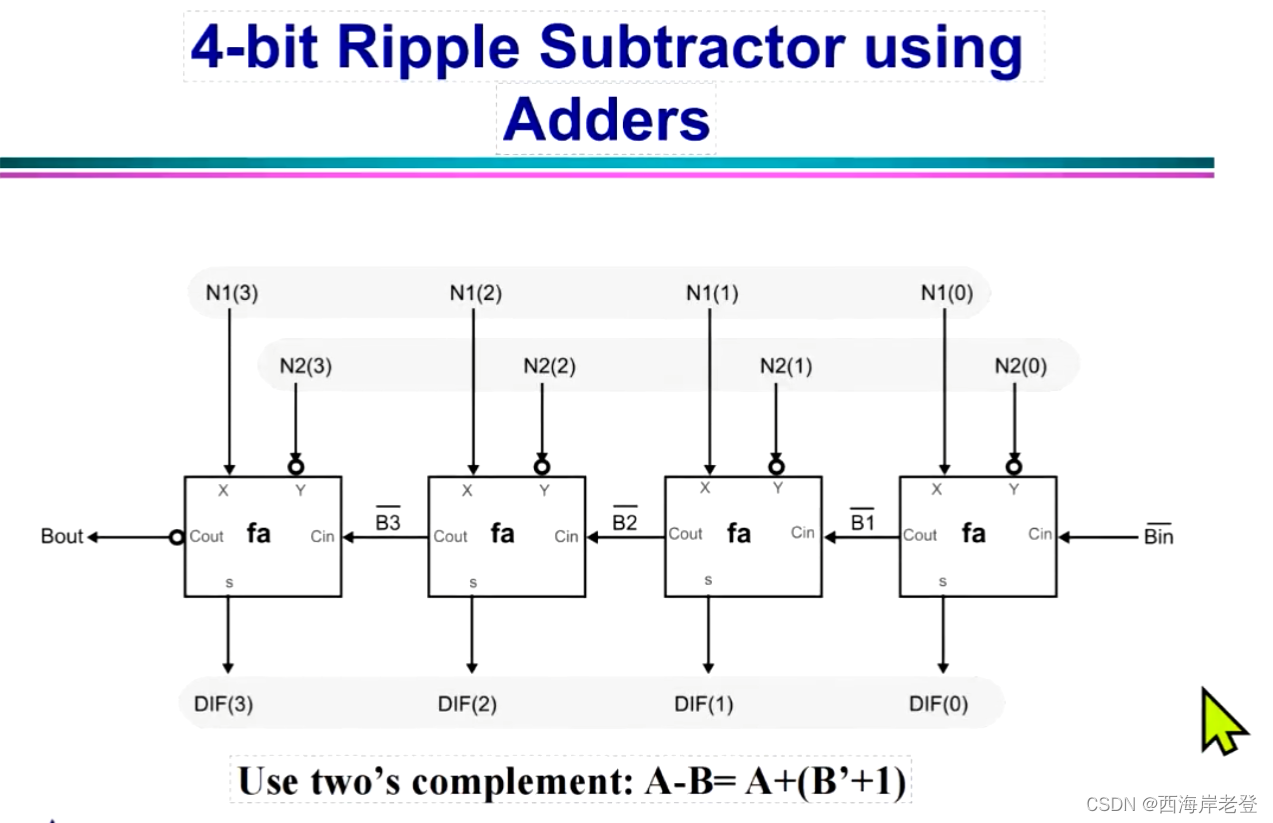
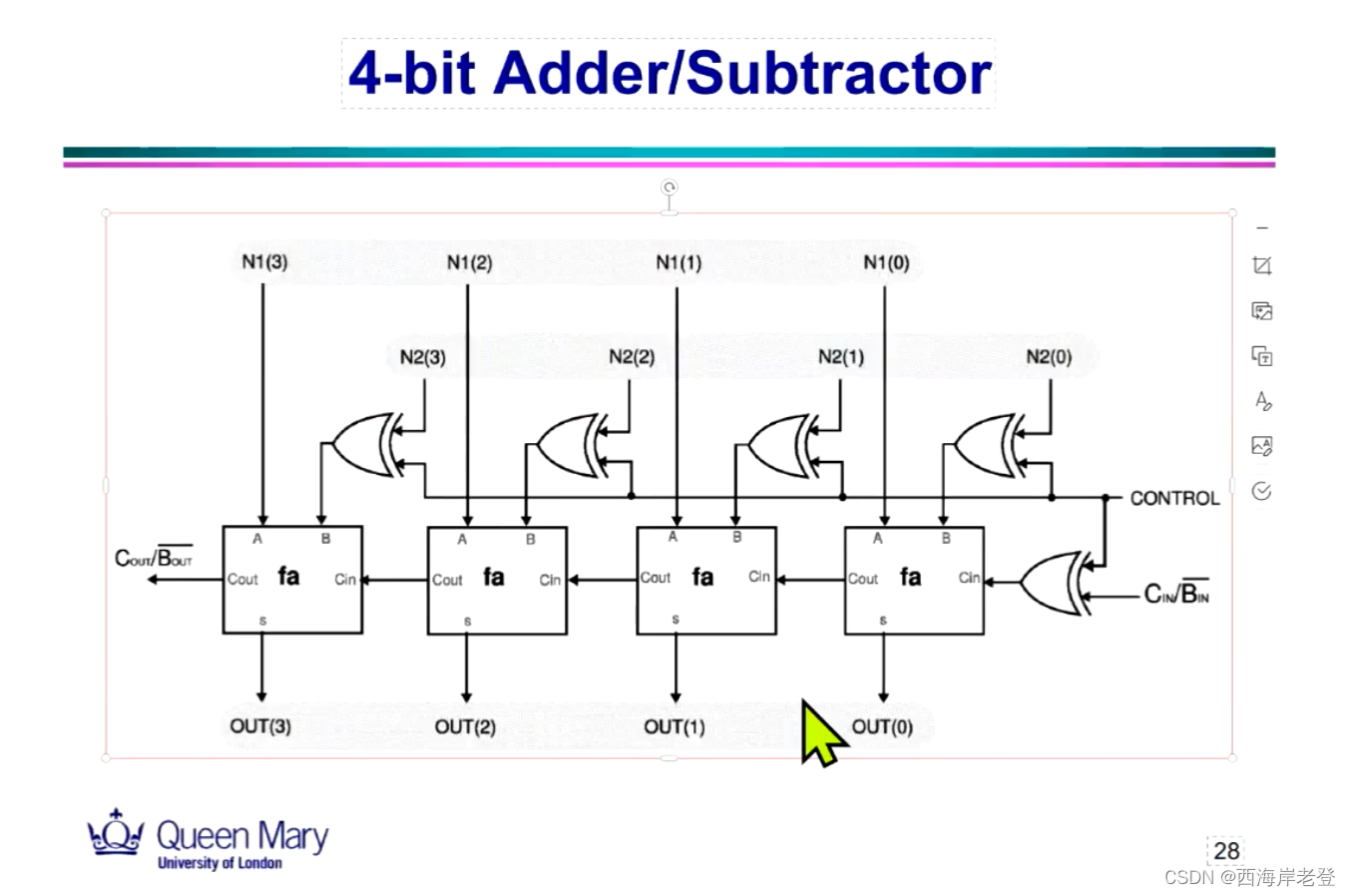
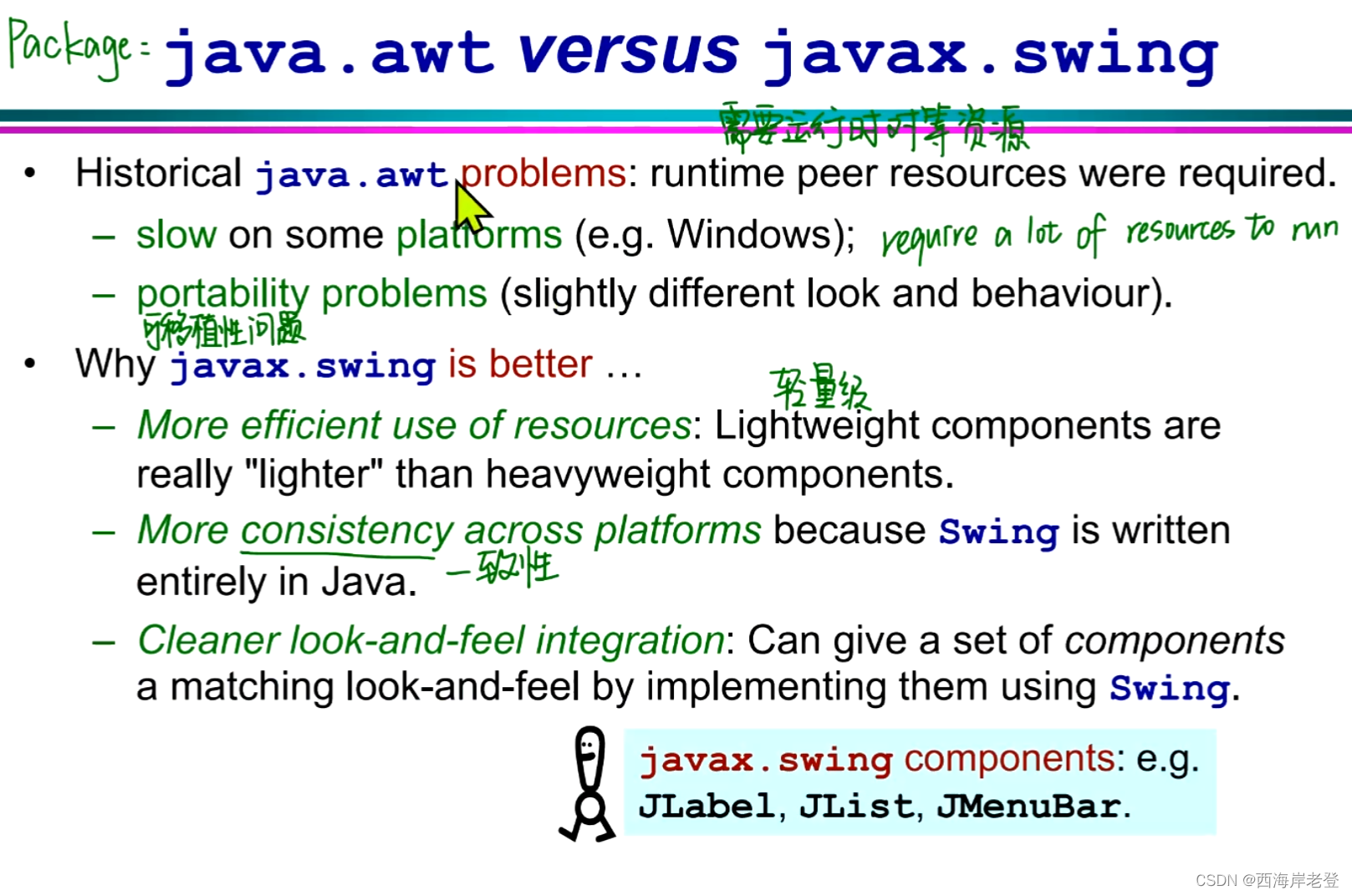
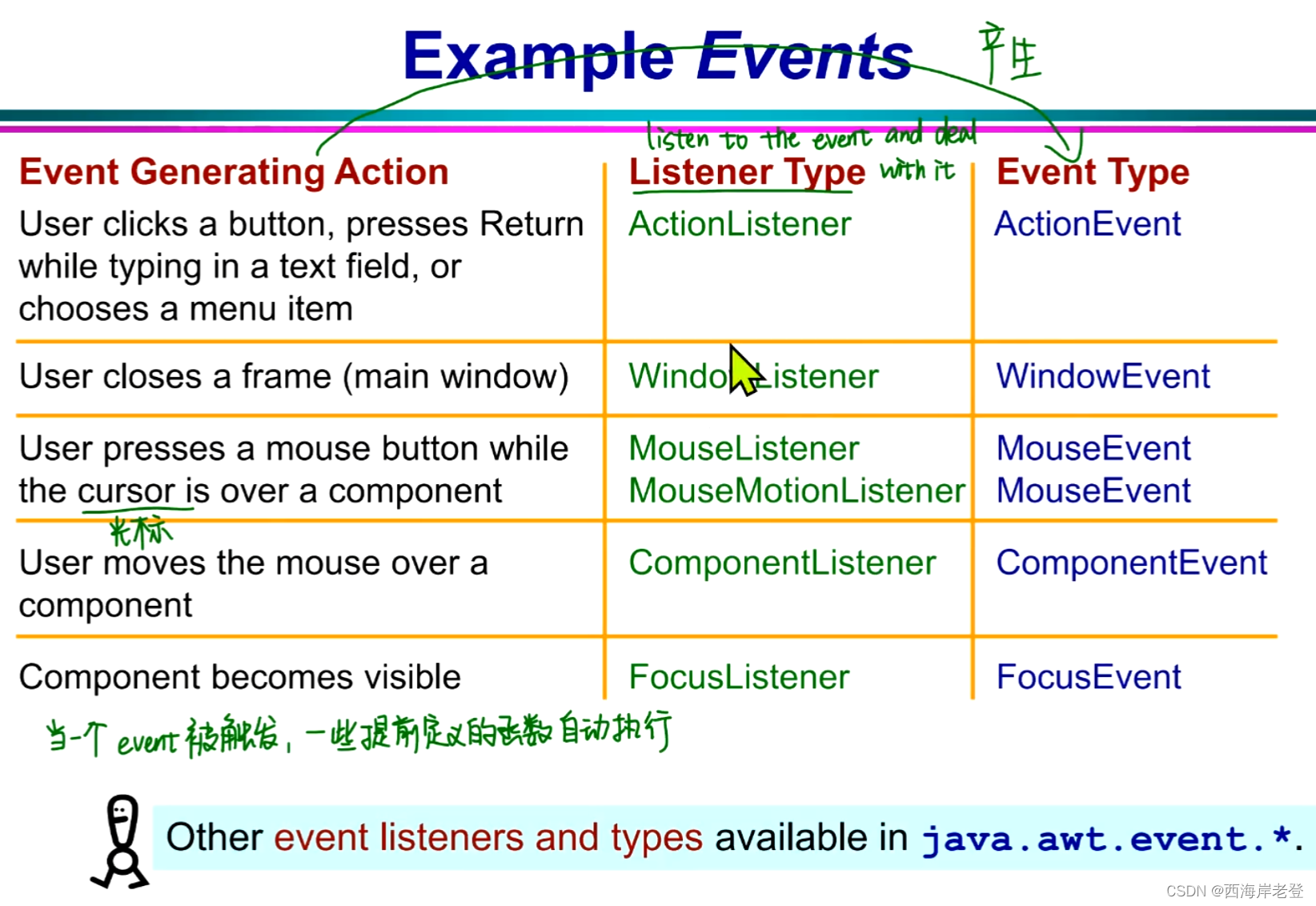
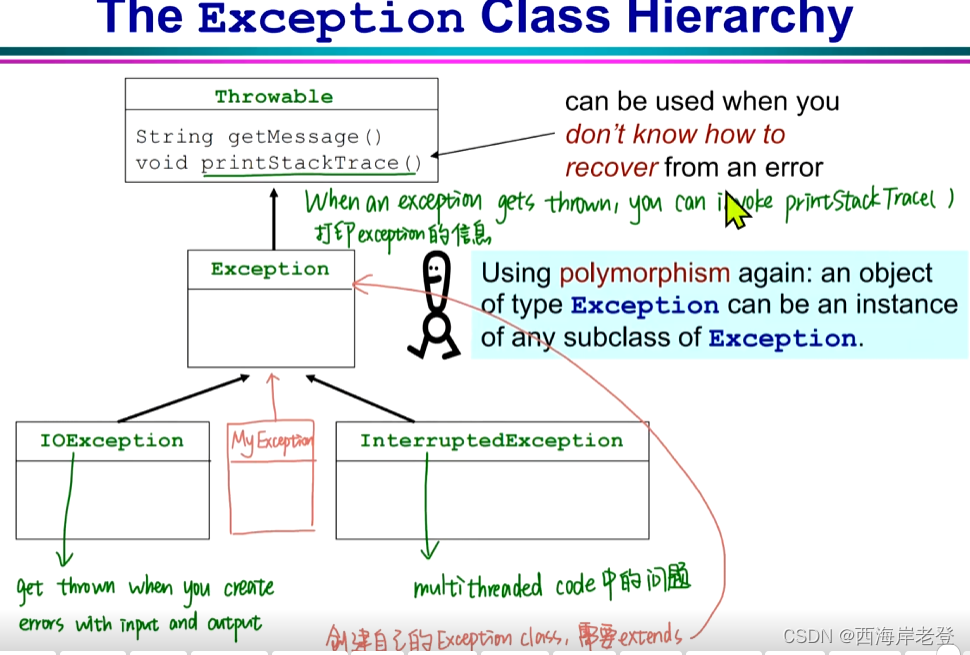
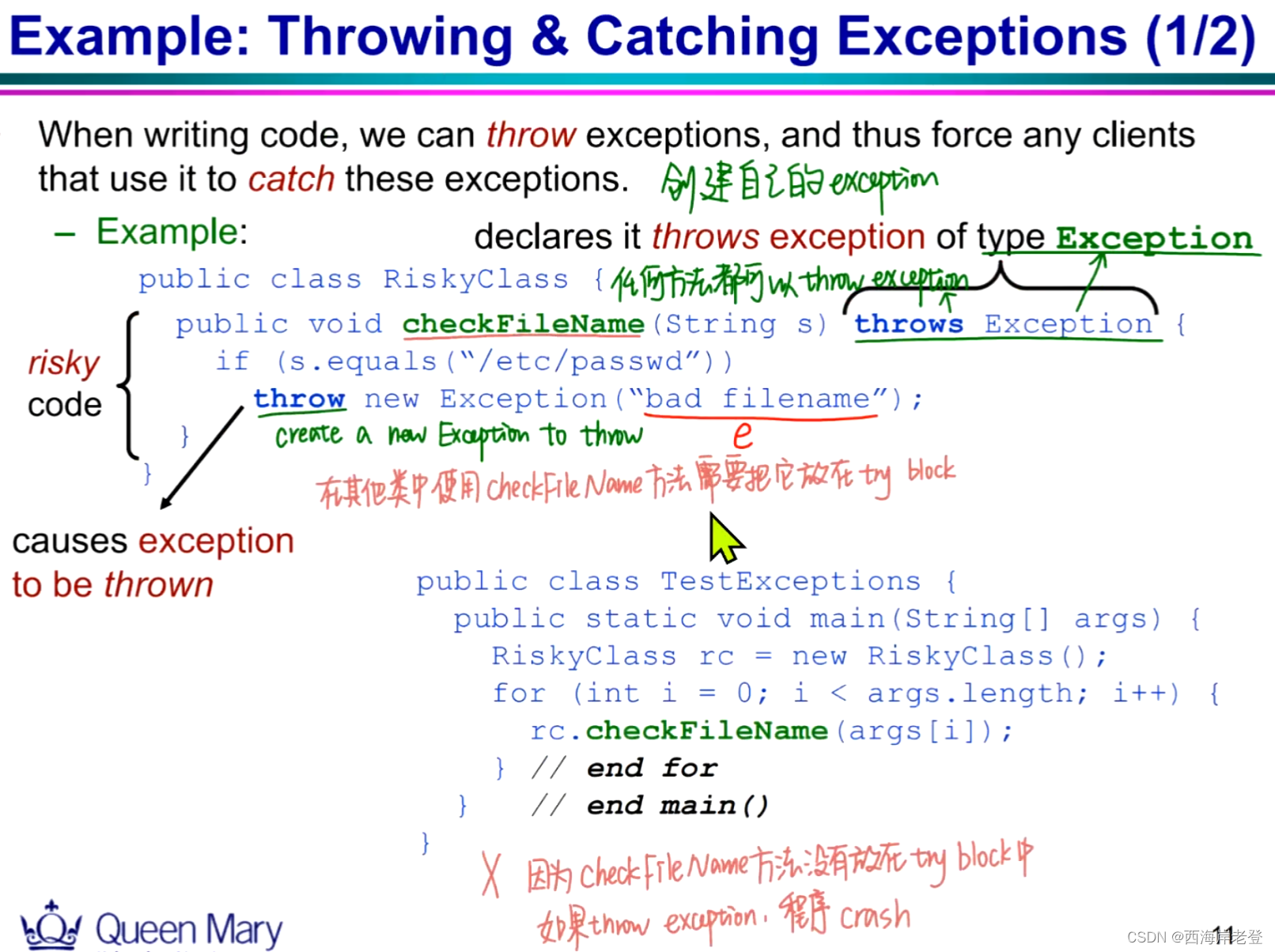
java
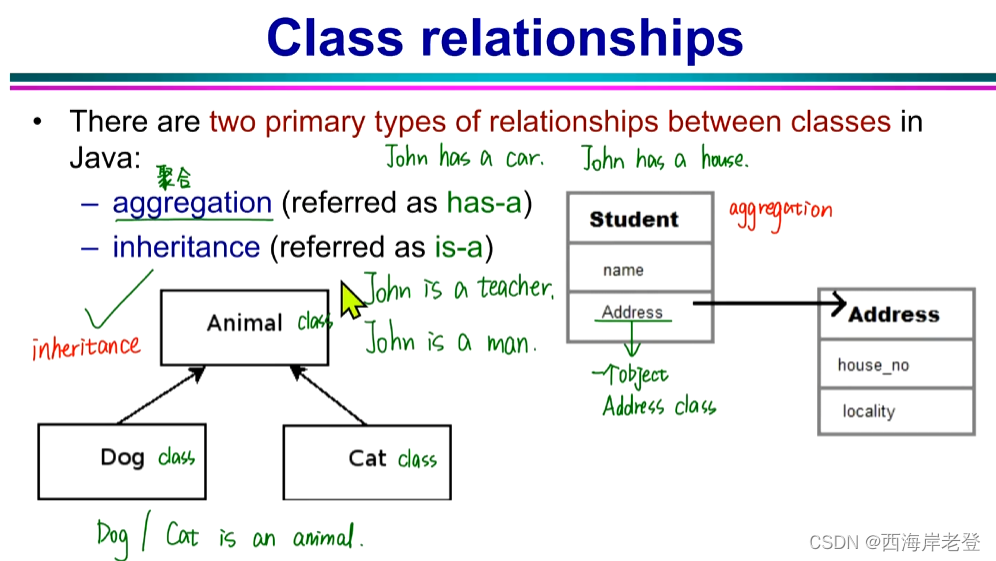
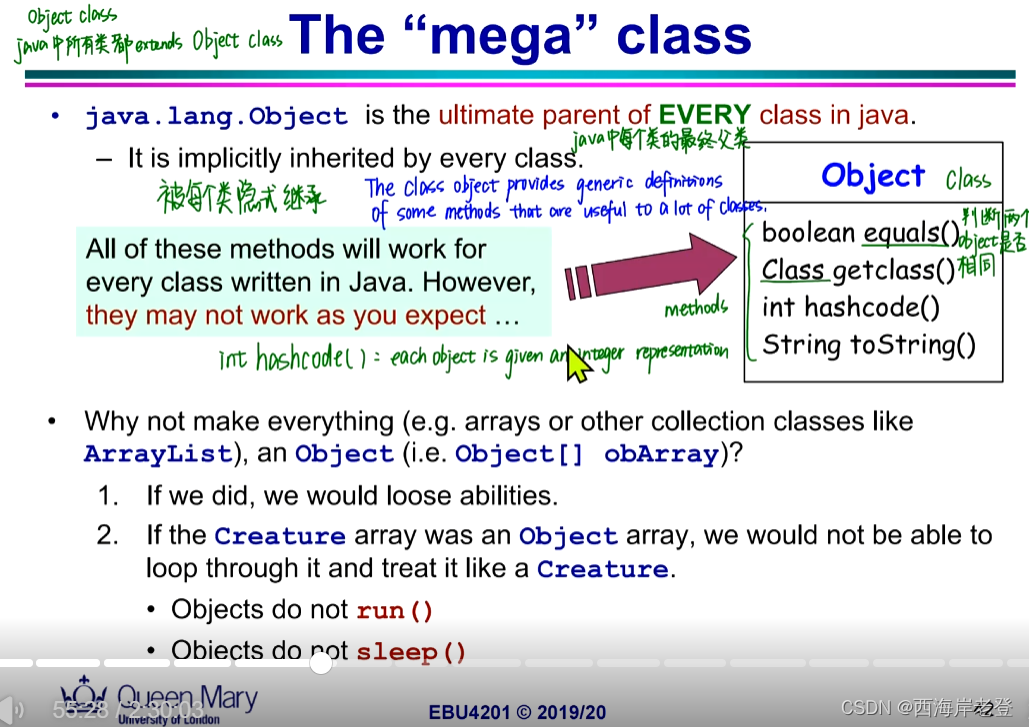
这一页ppt下方的问题貌似值得探讨
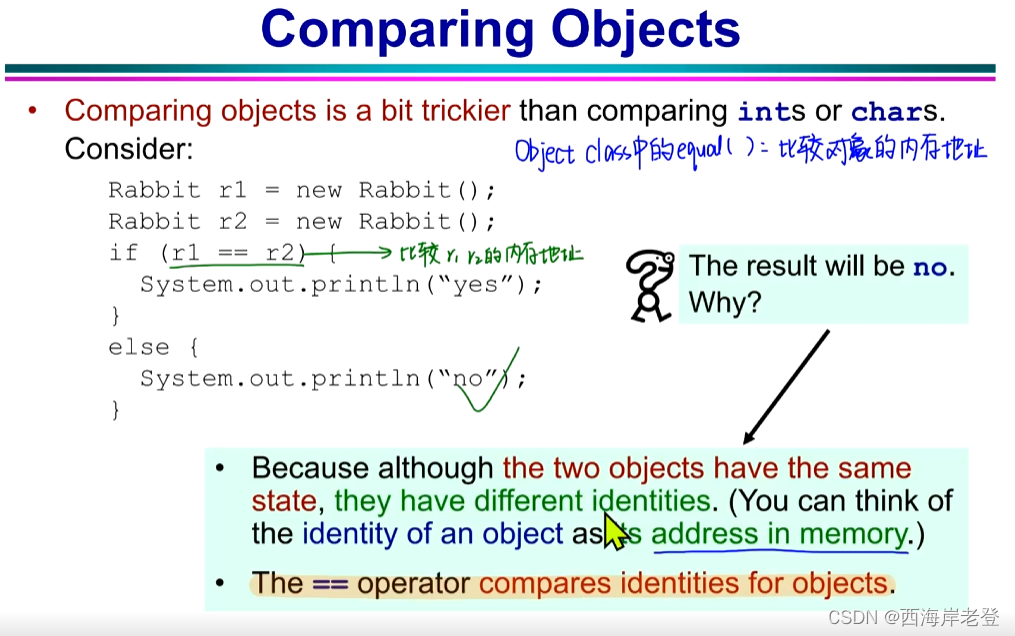
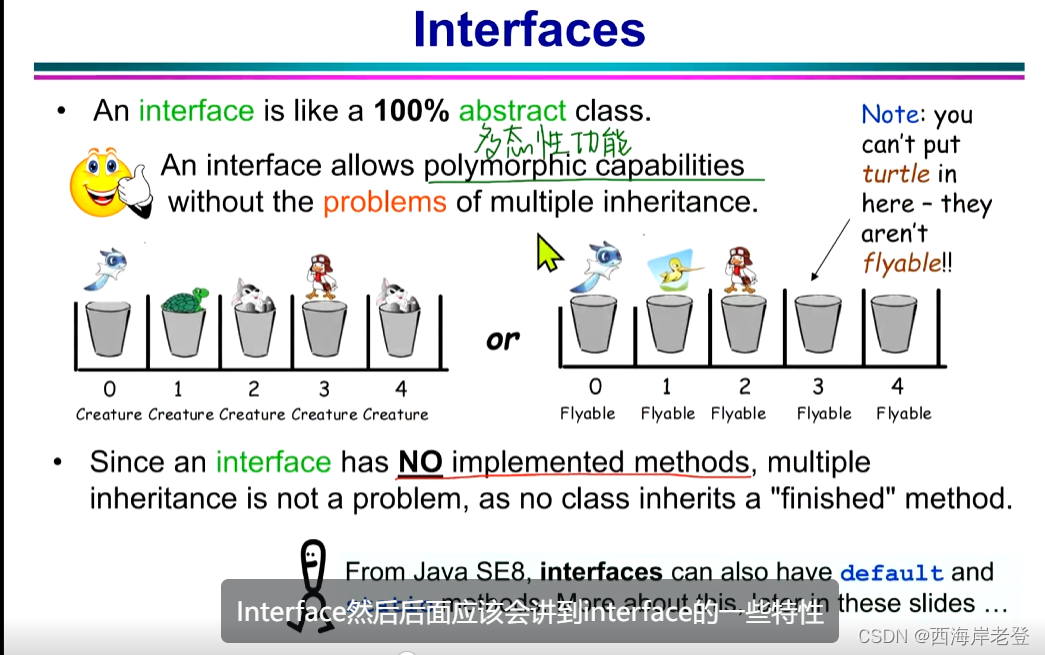


构造器的隐式调用
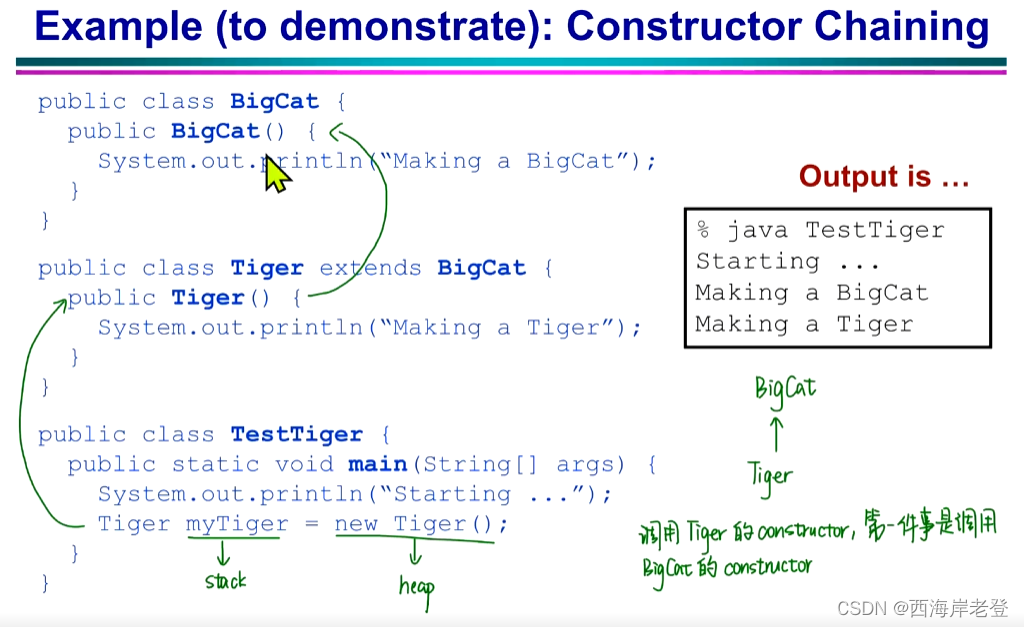
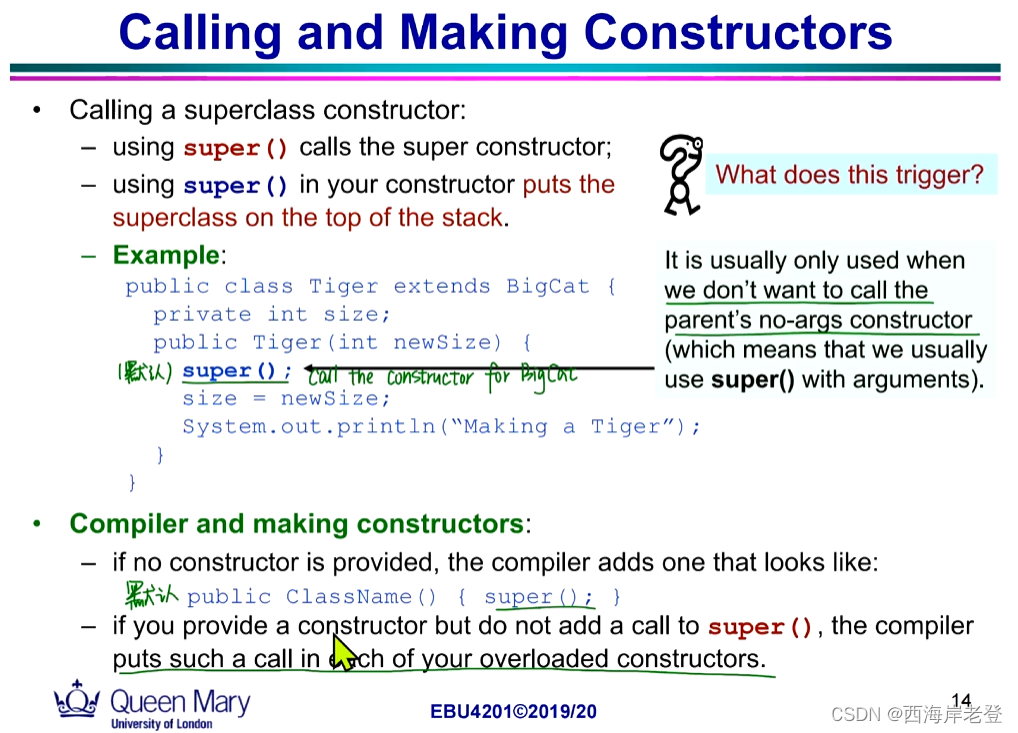
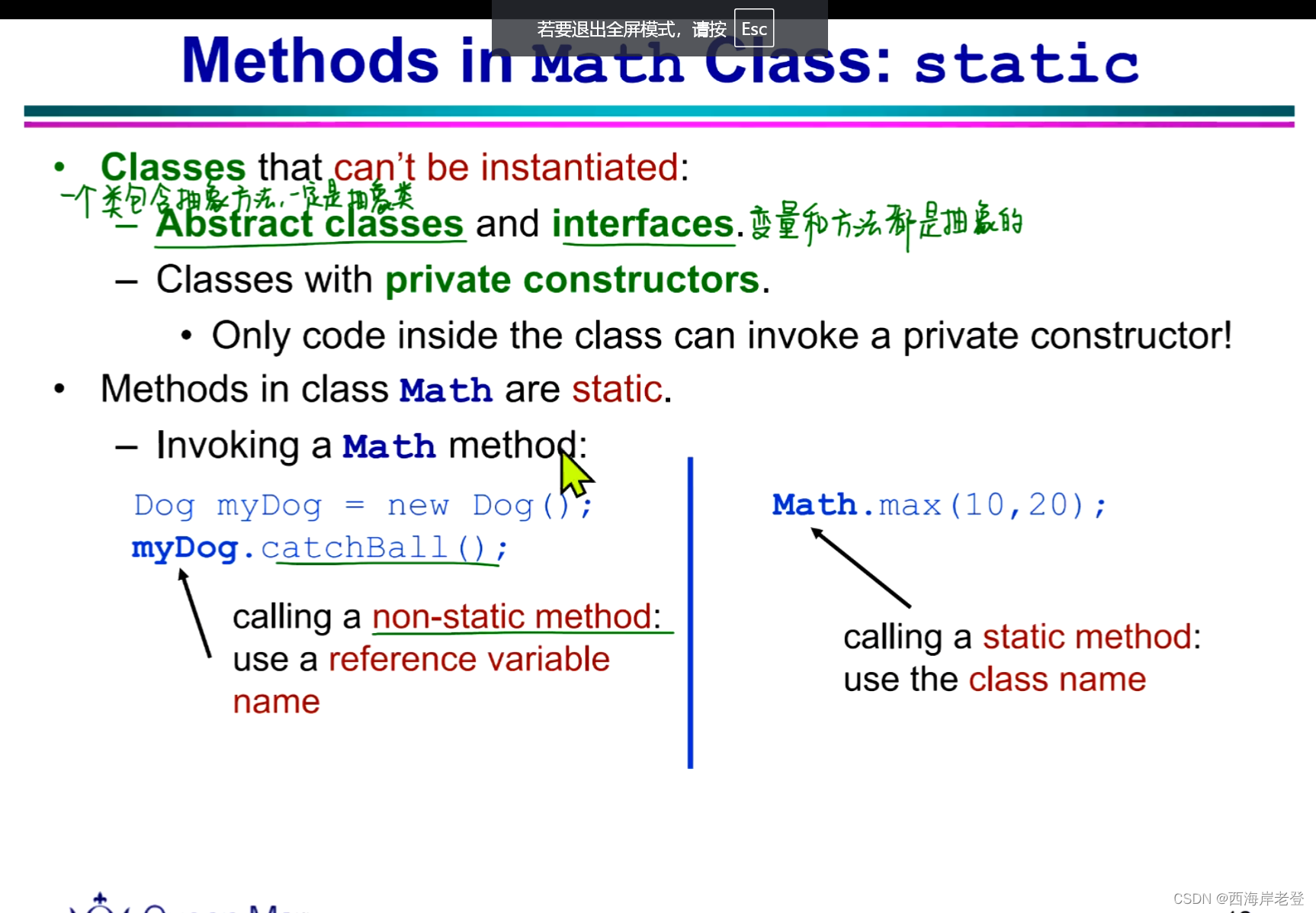
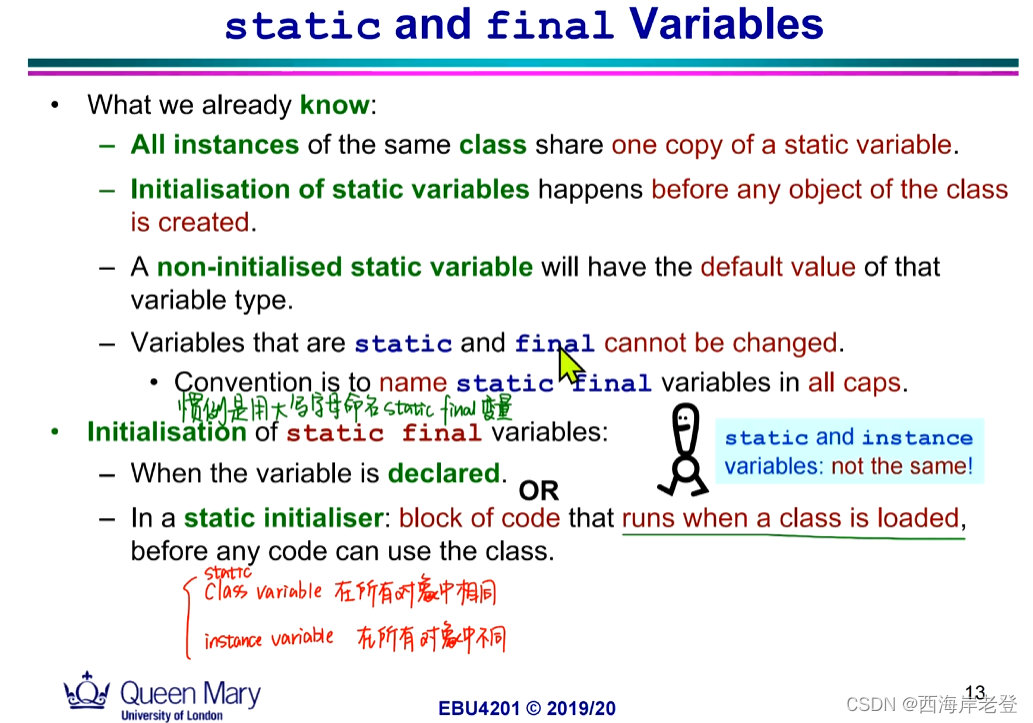
构造器是私有化的类不能被实例(Initialized)
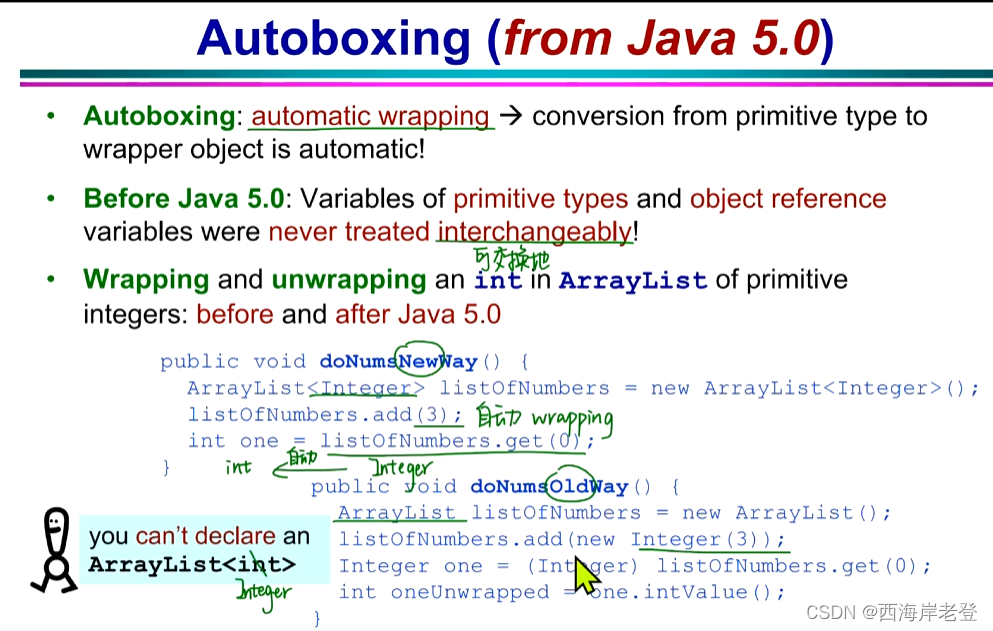
wrapper class转化:
int i=10;
Integer iWrapper = new Integer(i);
int returnValue = iWrapper.intValue();


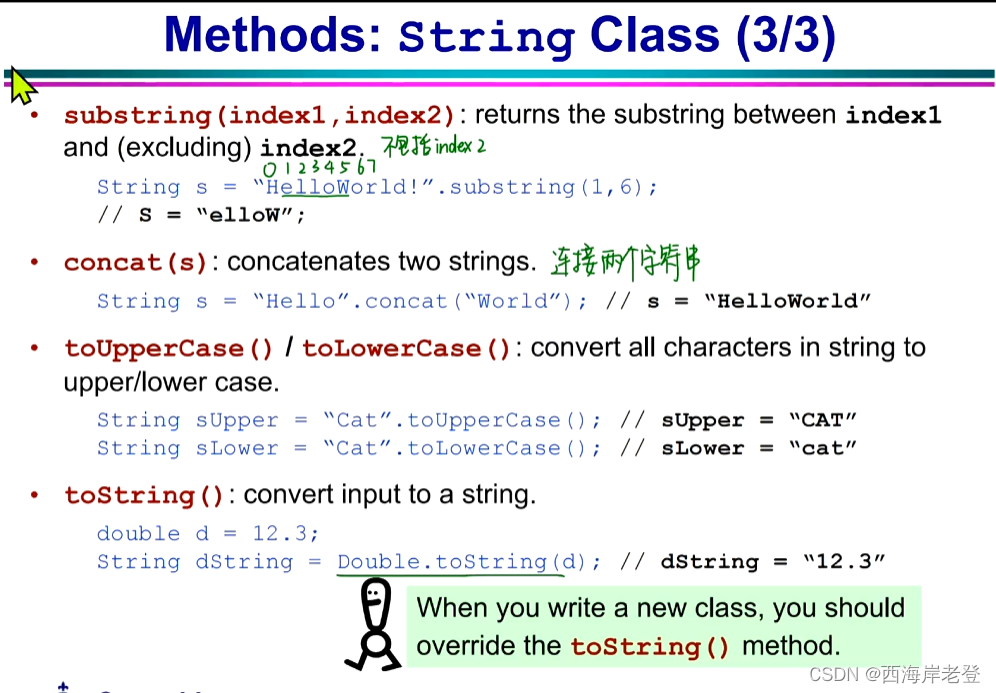
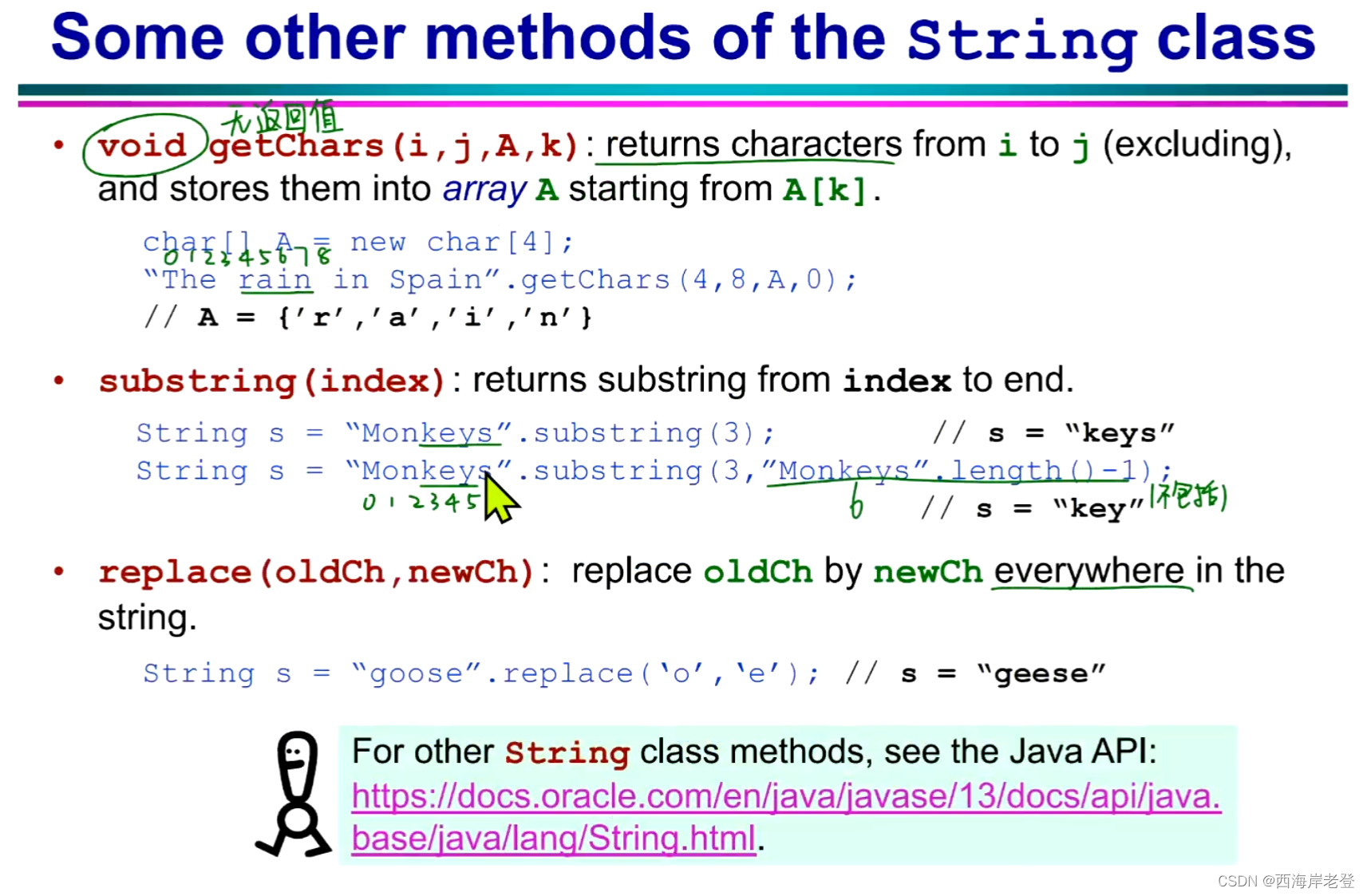
String() 方法



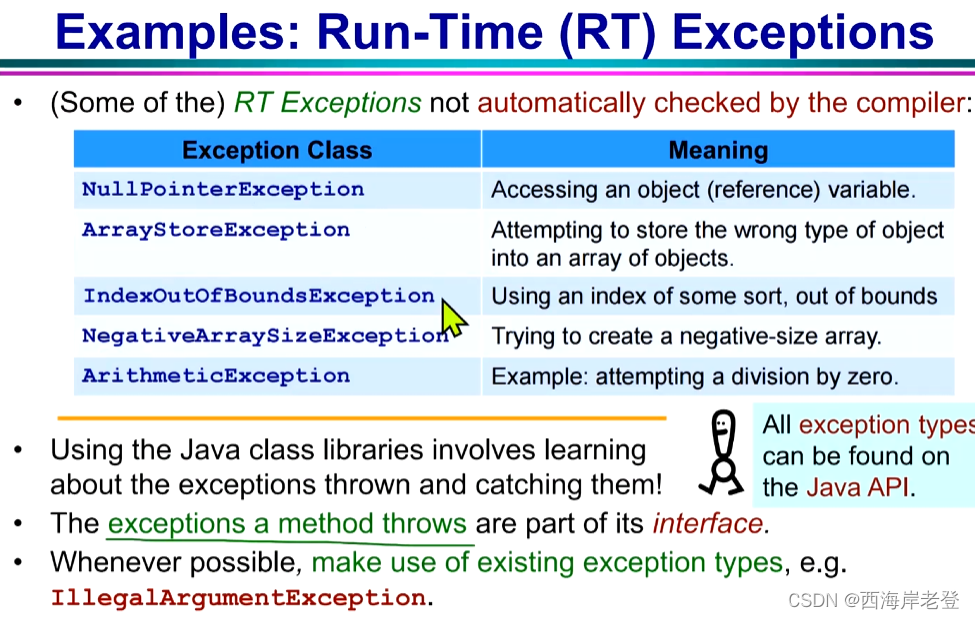
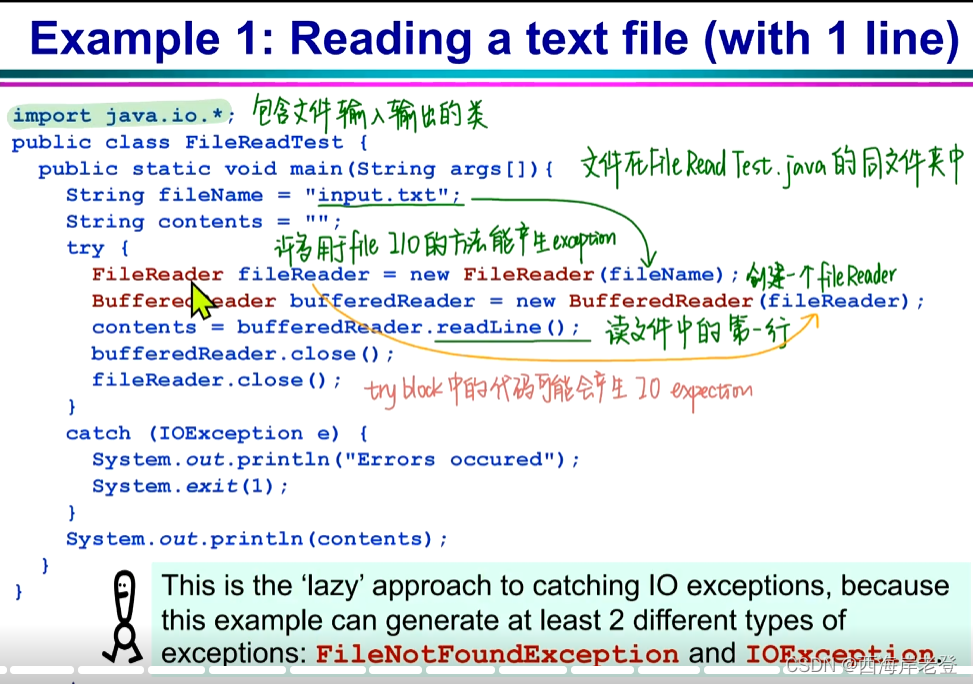
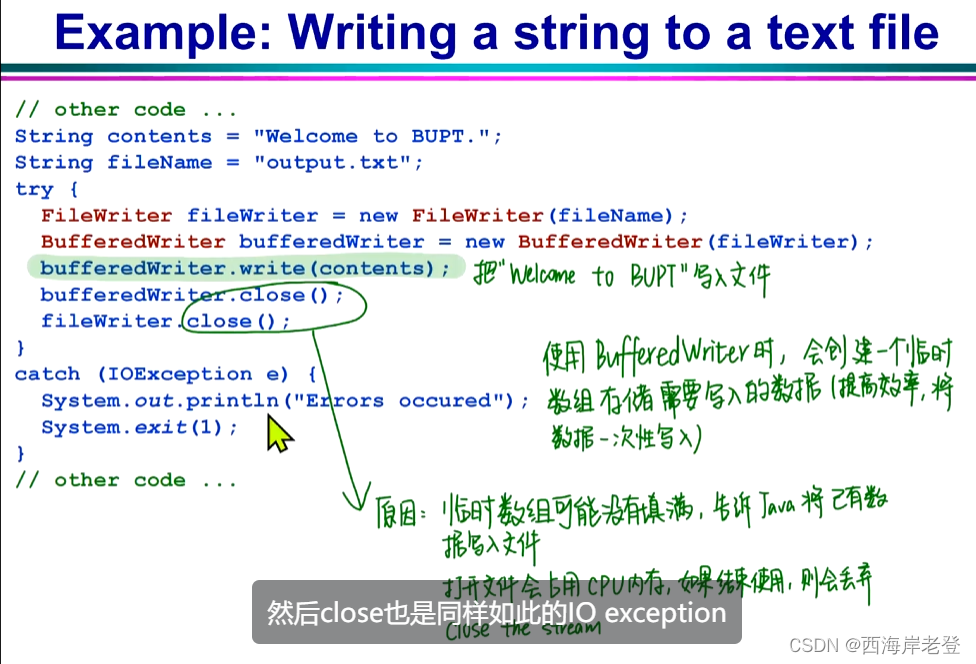
File Input/Output:
File (Buffered)FileReader (Buffered)FileWriter
JDK JRE JVM之间的区别联联系:http://t.csdnimg.cn/NPiEX
ArrayList()对象的.size() .add() .contains()返回boolean .indexOf()不存在返回-1 .remove() .isEmpty()
data type convertion
产开 大头
考试内容:黄线标出来的部分

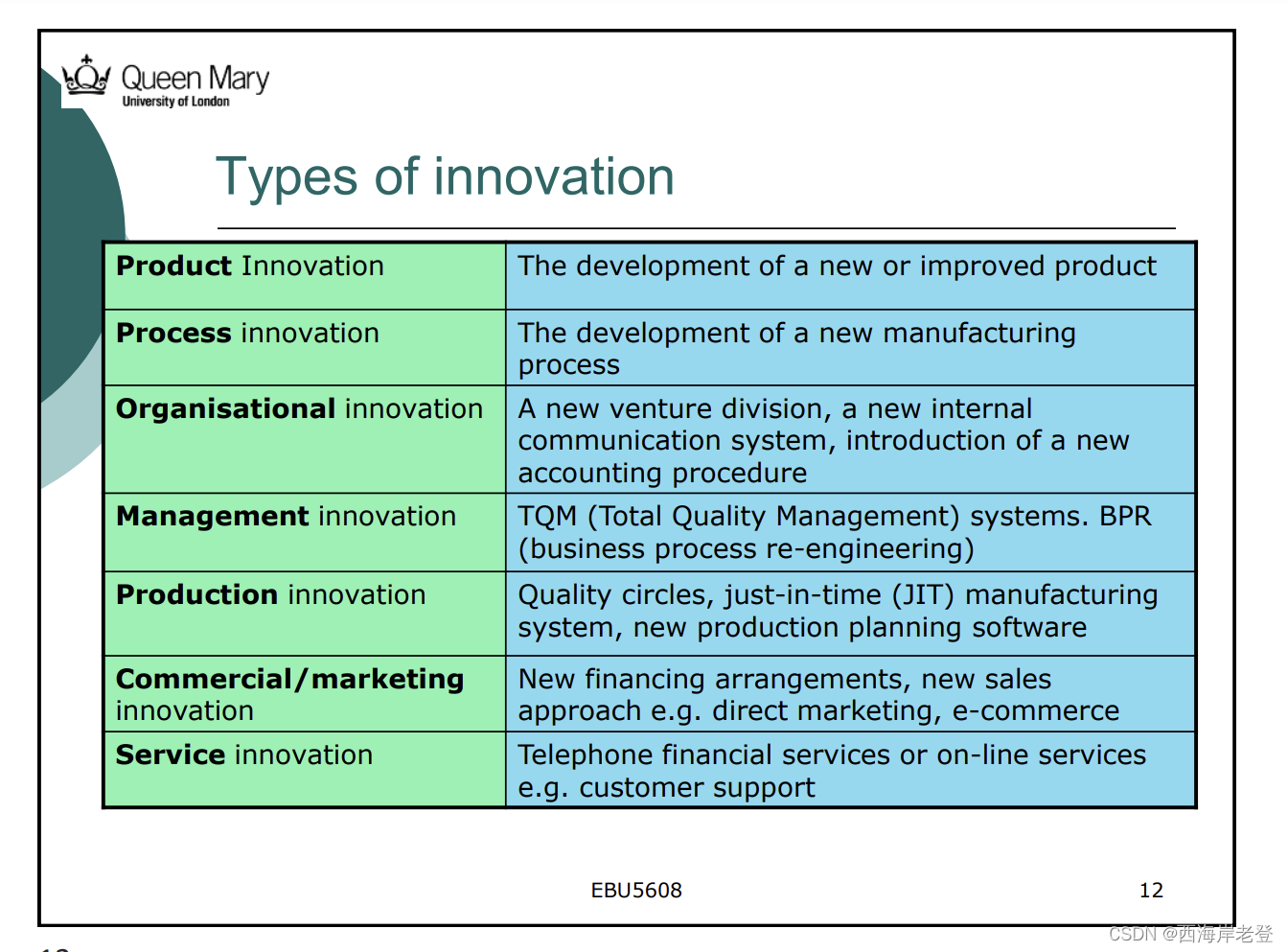
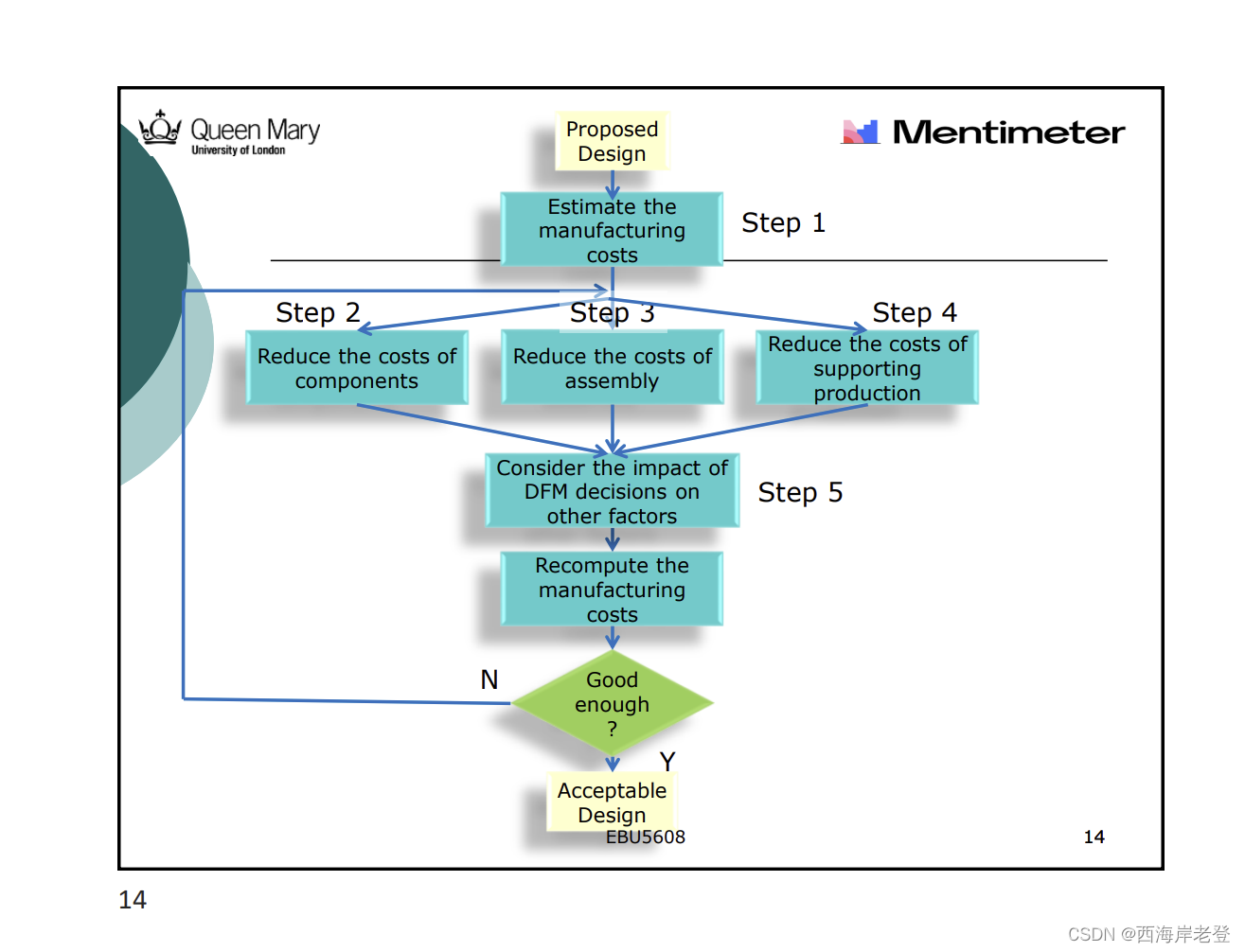
DFM 5 steps
7Ps法则:
Product Place Price Promotion Physical_Evidence People Processes
[What Are the 7Ps of the Marketing Mix?]:https://www.youtube.com/watch?v=OF4w862D0s4
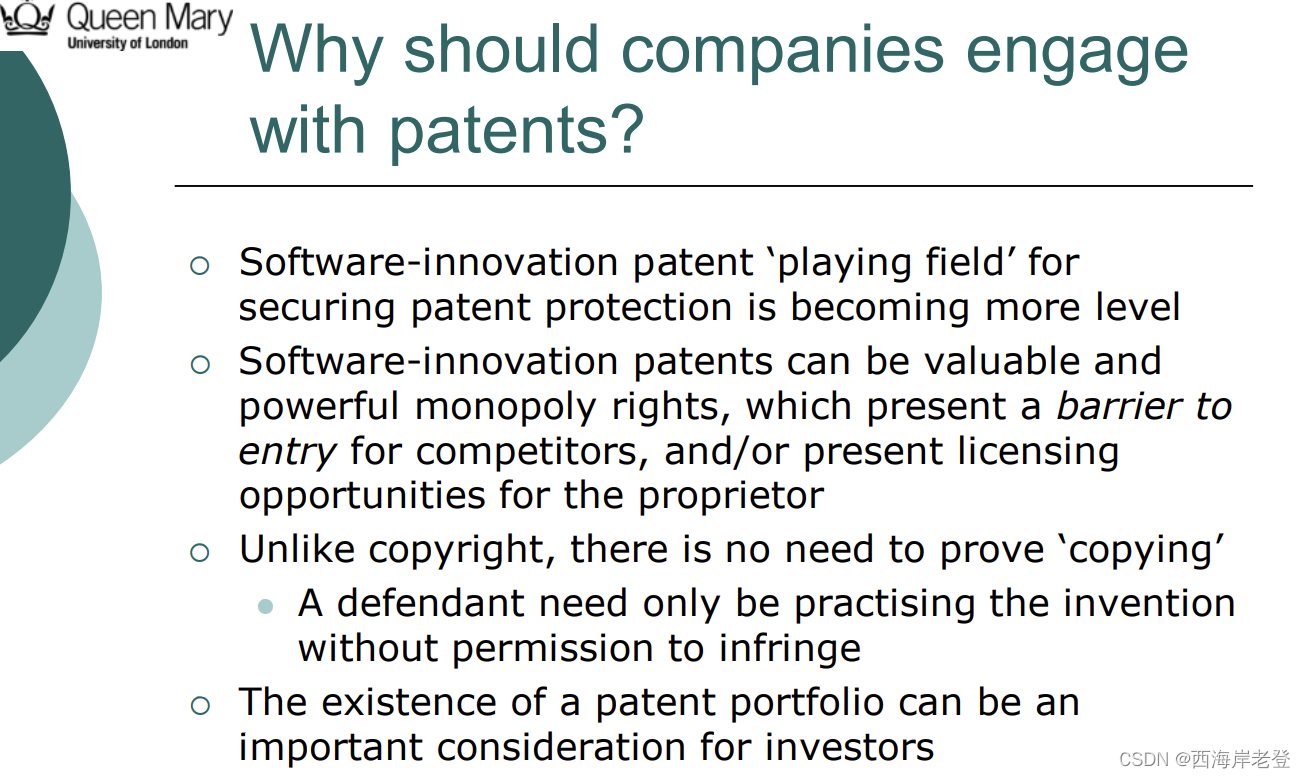
知识产权:必考
IP strategy



9题 两个半小时 150min 16.6min一题
prototyping: terms, 3 phases, uses
Intellectual Property: define, copyright protection range, patent, benefits and limitations of using patents
Exam Questions 2022-23
QUESTION 1
a) Discuss in detail FIVE (5) sources of to identify new product opportunities.
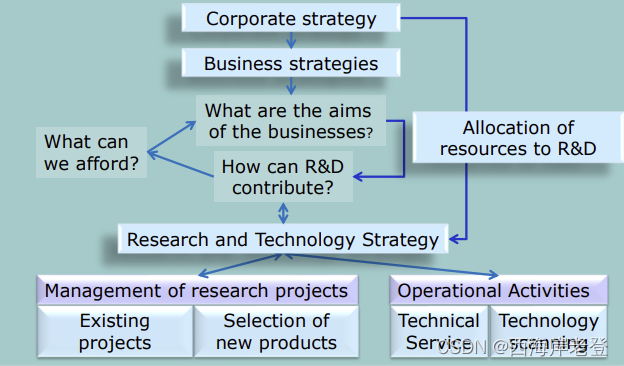
b) Describe the Strategic Decision-making process in relation to the allocation of funds for R&D using a diagram.
关键词:Strategic Decision-making process、allocation of funds for
R&D
QUESTION 2
a) Define Phase 2 of the Product Development Process – System-level Design. Describe the TWO (2) different modes of system-level design. Use suitable examples to demonstrate your understanding.
b) Product architecture determines the arrangement of functional elements of a product. Identify and discuss FIVE (5) implications of product architecture in the context of a product development process.
这两题我没关注,今年不考
QUESTION 3
a) A digital music service provider (Spotify) is promoting and hosting a live-streamed concert by TNT on a global games console platform (Sony PlayStation) during the interval of an eSports tournament being held and promoted by a leading games publisher (Electronic Arts) working alongside a famous brand (Gucci). The brand is providing digital as well as physical merchandise to fans – they can purchase original non-fungible tokens (NFTs), exchange them for a VIP personalised experience or physical fashion items.
Consider all the different commercial entities and their assets appearing in this scenario. ||Outline a possible intellectual property (IP) strategy for protecting these assets. ||Identify the different assets and appropriate intellectual property rights attached to them.
关键词:commercial entities、assets、intellectual property strategy、intellectual property rights
参考答案:
Intellectual property rights (IPRs) allow people to own their creativity and innovation in the same way that they can own physical property.
· Music, songs, electronic art – are protected by copyright designates legal ownership
of a musical composition or sound recording. This ownership includes exclusive rights to
redistribute and reproduce the work, as well as licensing rights that enable the copyright
holder to earn royalties.
· Games console platform – the underlying software protected by copyright as an
original literary work or by patent if it qualifies for protection as a software-implemented
invention.
· NFT token stands for “non-fungible token” – NFTs are essentially digitalised assets,
which represent underlying works such as art, memes, gifs, music or graphical
representation of physical items such as shoes and clothes. A question arises whether an
·NFT could be protectable as a work per se (e.g., independently from the underlying
work). Notwithstanding the fact that originality threshold is relatively low in most
jurisdictions, the act of minting may not be qualifying for copyright to subsist.
· Physical fashion items – in the fashion world, copyright protects graphic designs,
artistic works, literary works and works of artistic craftsmanship. This means that
protection can be given to fabrics, surface patterns and any graphic elements shown on
a garment, whether a shape, badge, or wording.
· Branding or logos – any sings attached to the goods or services associated with the
company can be protected as trademarks.
b) Xiu Li is using her Oculus VR (virtual reality) headset to attend the live-streamed concert by TNT. Even though she received multiple notifications to update the firmware on her headset, she has not installed any of the critical software patches. Hackers have successfully used this weak point and gained access to her network credentials, acquiring the same account privileges as her. This gave them access to her personal and biometric data.
Identify and discuss in detail the following cybersecurity concepts: vulnerability, threat, risk, and safeguard. Use suitable examples from the scenario above to demonstrate your understanding.
概率论
概率论中其实把所有的知识点都基本了解难度不大,如果你已经基本了解了,那么需要多做一些题,因为往往是关键的一些易错题容易让你丢分。
由于今年杨建奎老师没有讲到第八章,第六章应该也没怎么讲,第八章只是在最后给了个录制视频。应该会出题,但是会出的比较简单。前面可能会出难题了。
杨老师出的考试大纲:


其中需要重点关注
1
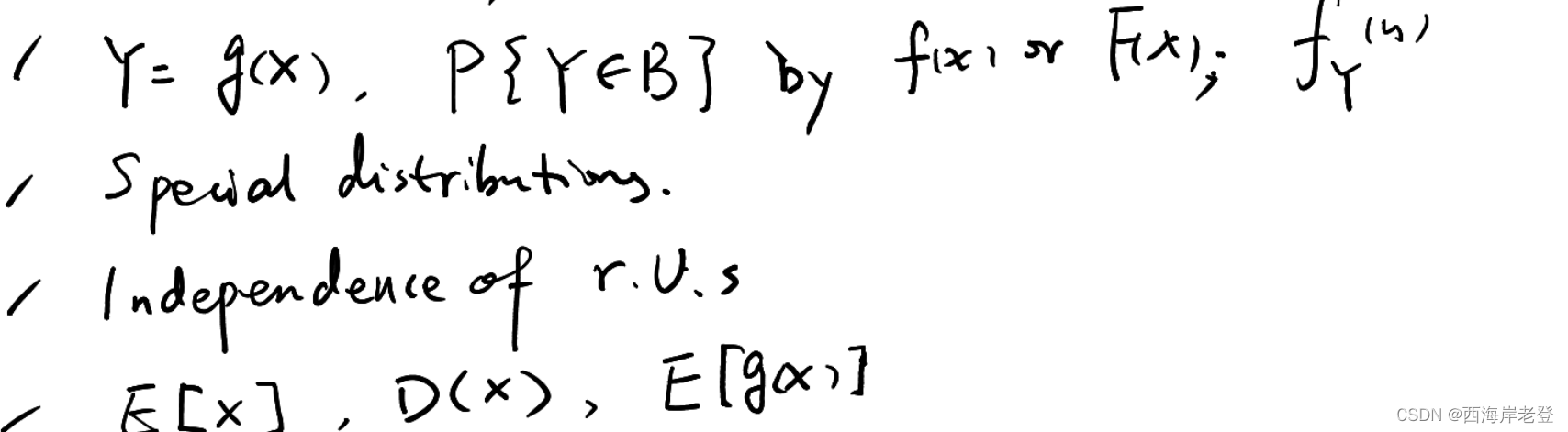
2
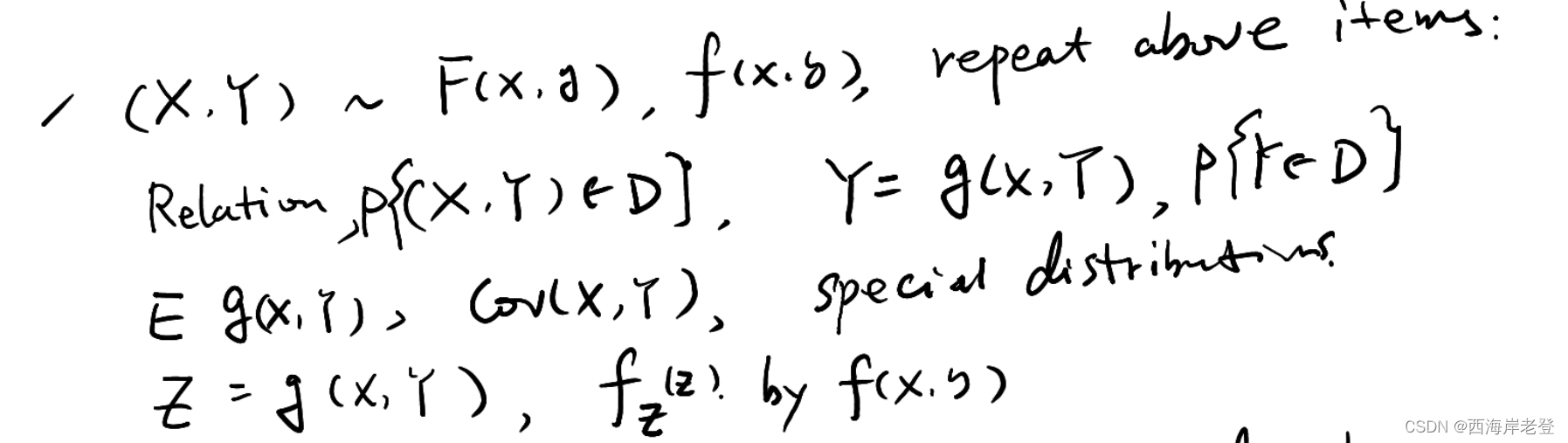
3
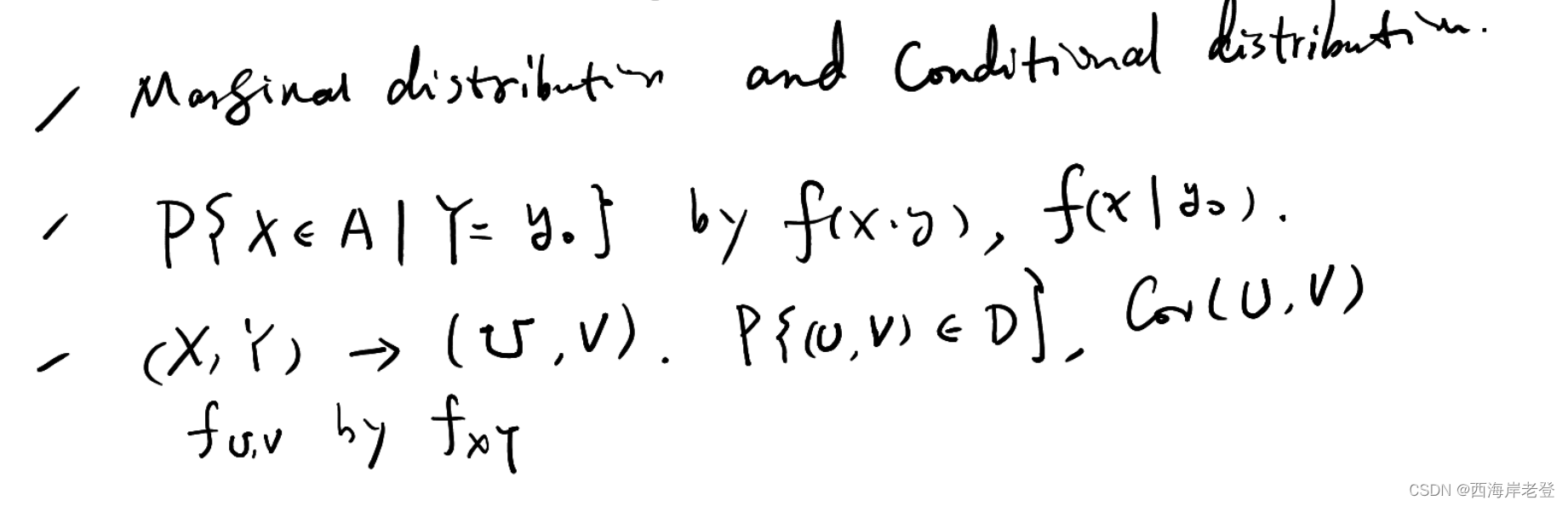
概率论部分到此结束,之后是随机过程
4、

limit distribution?我们考不考各态历经性?
记住马尔可夫转移概率矩阵每一行行和都是1. 包括它的平方,三次方,n次方同样如此。(防止计算出错的二级结论)
5、
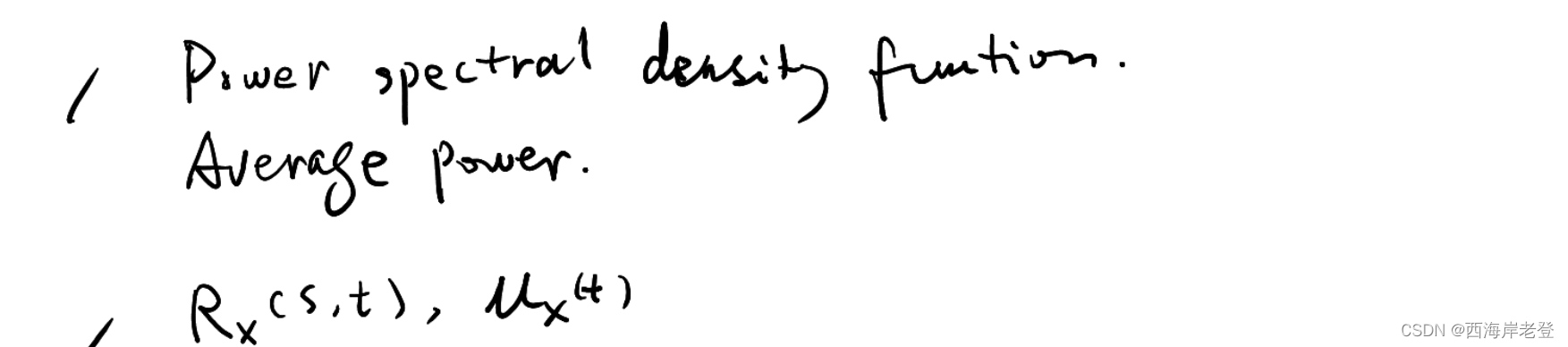
6、
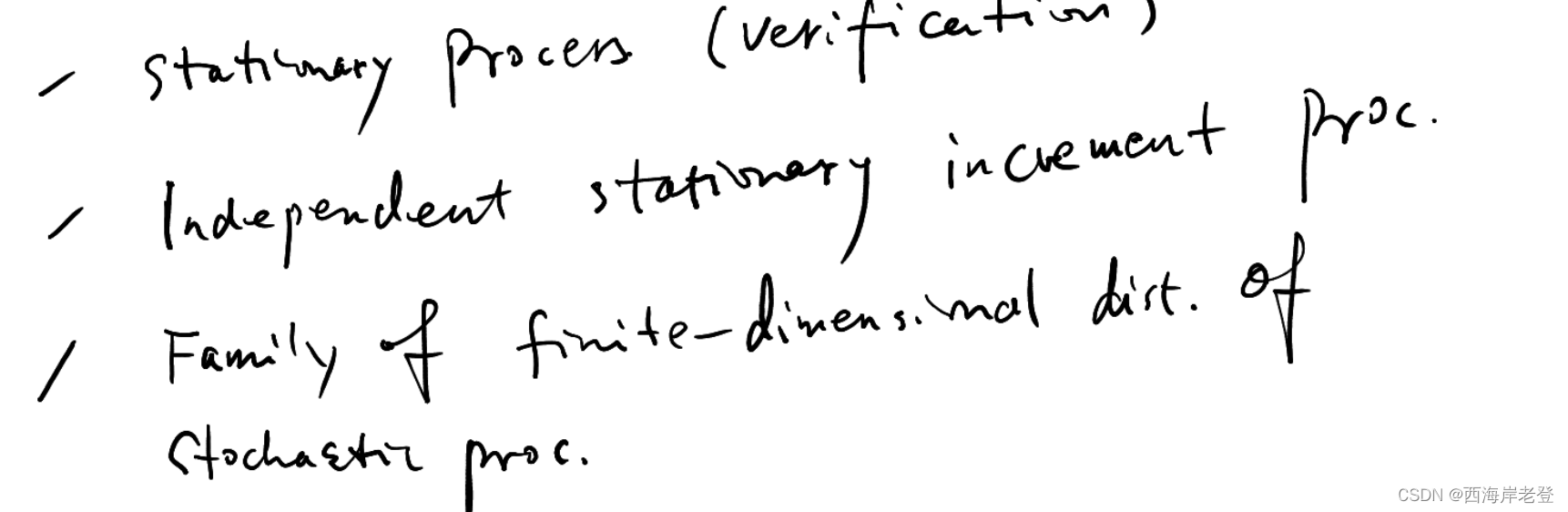
高斯过程不怎么考:可能考也就考验证一个过程是一个高斯过程
维纳过程就是一个特殊的高斯过程??证明
维纳是不是一个宽平稳过程?





















 9314
9314

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








