通过名称去找
// MyGETPRCOADDRESS.cpp : 此文件包含 "main" 函数。程序执行将在此处开始并结束。
//
#include <iostream>
#include<Windows.h>
/*WINBASEAPI //导出不需要使用,那么我们注释掉*/
FARPROC
WINAPI
MyGetProcAddress(
_In_ HMODULE hModule,
_In_ LPCSTR lpProcName
)
{
PIMAGE_DOS_HEADER pIMAGE_DOS_HEADER = (PIMAGE_DOS_HEADER)hModule;
PIMAGE_NT_HEADERS pIMAGE_NT_HEADERS = (PIMAGE_NT_HEADERS)(pIMAGE_DOS_HEADER->e_lfanew + (DWORD)hModule); //NT头
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORYRVA = (PIMAGE_EXPORT_DIRECTORY)(pIMAGE_NT_HEADERS->OptionalHeader.DataDirectory[0].VirtualAddress); //导出表项,获得RVA RVA并不是真正的导出表项需要转VA,转VA需要加上image_base(也就是加载地址)
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORY = (PIMAGE_EXPORT_DIRECTORY)((DWORD)pIMAGE_EXPORT_DIRECTORYRVA + (DWORD)hModule); //这个才是真正的VA,真正的导出表项,因为RVA在内存中是没有的
DWORD ModuleName = pIMAGE_EXPORT_DIRECTORY->Name + (DWORD)hModule;
printf("%s", ModuleName);
return NULL;
}
int main()
{
std::cout << "Hello World!\n";
HMODULE Hmodule = GetModuleHandleA("ntdll.dll"); //为了防止同名函数,所以先要获得哪个模块 那么Hmodule相当于模块基址
//void *p = GetProcAddress(Hmodule, "RtlDispatchAPC");
//void *p2 = GetProcAddress(Hmodule, (LPCSTR)1);
void* p1 = MyGetProcAddress(Hmodule, "RtlDispatchAPC");
printf("%s", p1);
}
// 运行程序: Ctrl + F5 或调试 >“开始执行(不调试)”菜单
// 调试程序: F5 或调试 >“开始调试”菜单
// 入门使用技巧:
// 1. 使用解决方案资源管理器窗口添加/管理文件
// 2. 使用团队资源管理器窗口连接到源代码管理
// 3. 使用输出窗口查看生成输出和其他消息
// 4. 使用错误列表窗口查看错误
// 5. 转到“项目”>“添加新项”以创建新的代码文件,或转到“项目”>“添加现有项”以将现有代码文件添加到项目
// 6. 将来,若要再次打开此项目,请转到“文件”>“打开”>“项目”并选择 .sln 文件

可以看到找成功了
接下来获取名称表格
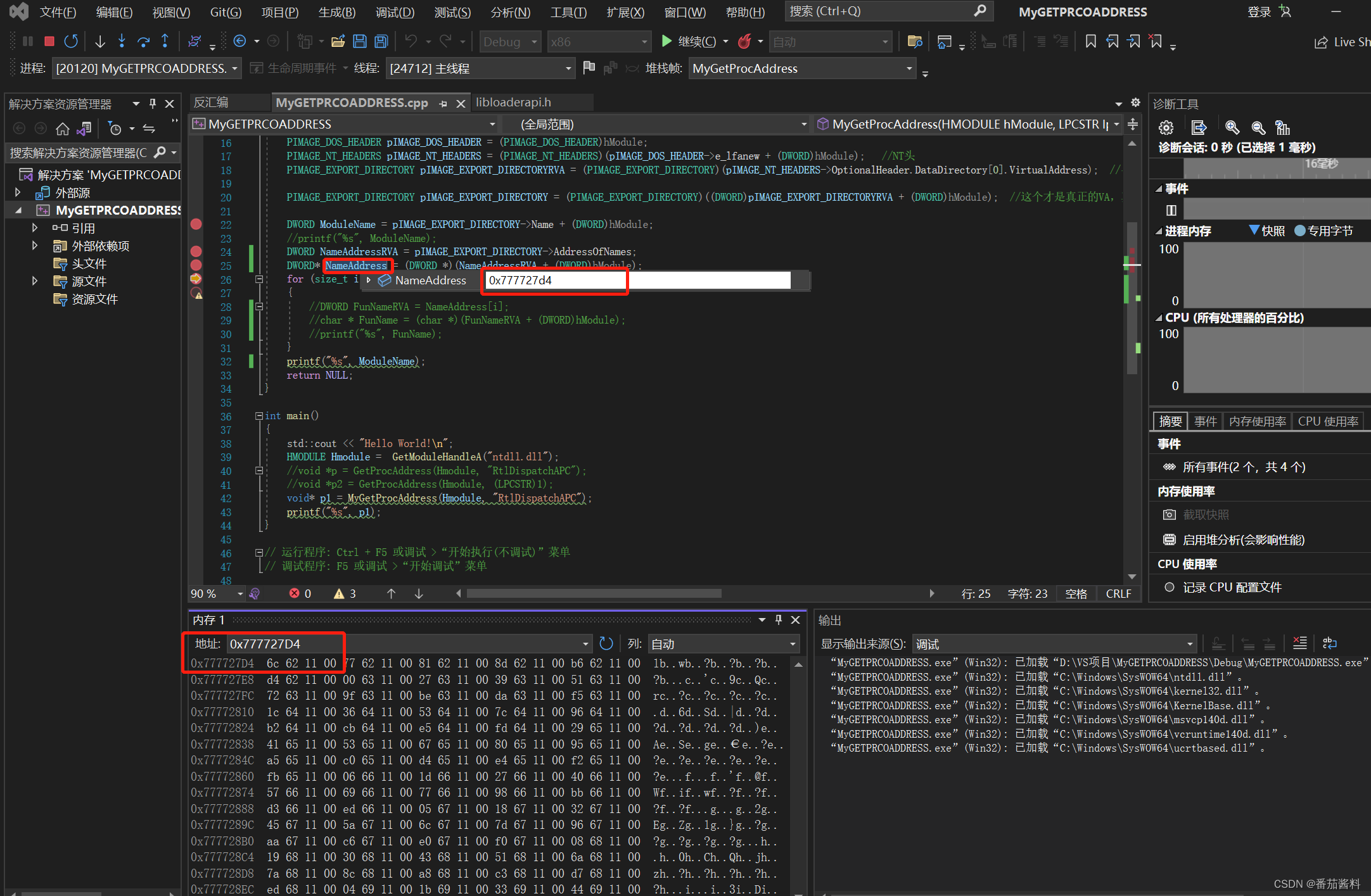
可以看到0x777727D4就是函数的地址,那么函数地址第一个就是0x0011626c,因为DWORD是4字节
但是还需要加基址hModule(0x77660000),那么就是0x0011626c+0x77660000,也就是如下

可以看到成功定位到了函数,那么可以正确获取到名称表格
然后我们写循环
for (size_t i = 0; i < pIMAGE_EXPORT_DIRECTORY->NumberOfNames; i++)
{
DWORD FunNameRVA = NameAddress[i];
char * FunName = (char *)(FunNameRVA + (DWORD)hModule);
printf("%s\n", FunName);
}


#include <iostream>
#include<Windows.h>
/*WINBASEAPI //导出不需要使用,那么我们注释掉*/
FARPROC
WINAPI
MyGetProcAddress(
_In_ HMODULE hModule,
_In_ LPCSTR lpProcName
)
{
PIMAGE_DOS_HEADER pIMAGE_DOS_HEADER = (PIMAGE_DOS_HEADER)hModule;
PIMAGE_NT_HEADERS pIMAGE_NT_HEADERS = (PIMAGE_NT_HEADERS)(pIMAGE_DOS_HEADER->e_lfanew + (DWORD)hModule); //NT头
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORYRVA = (PIMAGE_EXPORT_DIRECTORY)(pIMAGE_NT_HEADERS->OptionalHeader.DataDirectory[0].VirtualAddress); //导出表项,获得RVA RVA并不是真正的导出表项需要转VA,转VA需要加上image_base(也就是加载地址)
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORY = (PIMAGE_EXPORT_DIRECTORY)((DWORD)pIMAGE_EXPORT_DIRECTORYRVA + (DWORD)hModule); //这个才是真正的VA,真正的导出表项,因为RVA在内存中是没有的
DWORD ModuleName = pIMAGE_EXPORT_DIRECTORY->Name + (DWORD)hModule;
//printf("%s", ModuleName);
DWORD NameAddressRVA = pIMAGE_EXPORT_DIRECTORY->AddressOfNames;
DWORD* NameAddress = (DWORD *)(NameAddressRVA + (DWORD)hModule);
for (size_t i = 0; i < pIMAGE_EXPORT_DIRECTORY->NumberOfNames; i++)
{
DWORD FunNameRVA = NameAddress[i];
char * FunName = (char *)(FunNameRVA + (DWORD)hModule);
printf("%s\n", FunName);
}
printf("%s\n", ModuleName);
return NULL;
}
int main()
{
std::cout << "Hello World!\n";
HMODULE Hmodule = GetModuleHandleA("ntdll.dll");
//void *p = GetProcAddress(Hmodule, "RtlDispatchAPC");
//void *p2 = GetProcAddress(Hmodule, (LPCSTR)1);
void* p1 = MyGetProcAddress(Hmodule, "RtlDispatchAPC");
printf("%s", p1);
}
但是这样写看着有点不舒服,那么我们写一个RVA转AV的函数,让整体代码看起来舒服点
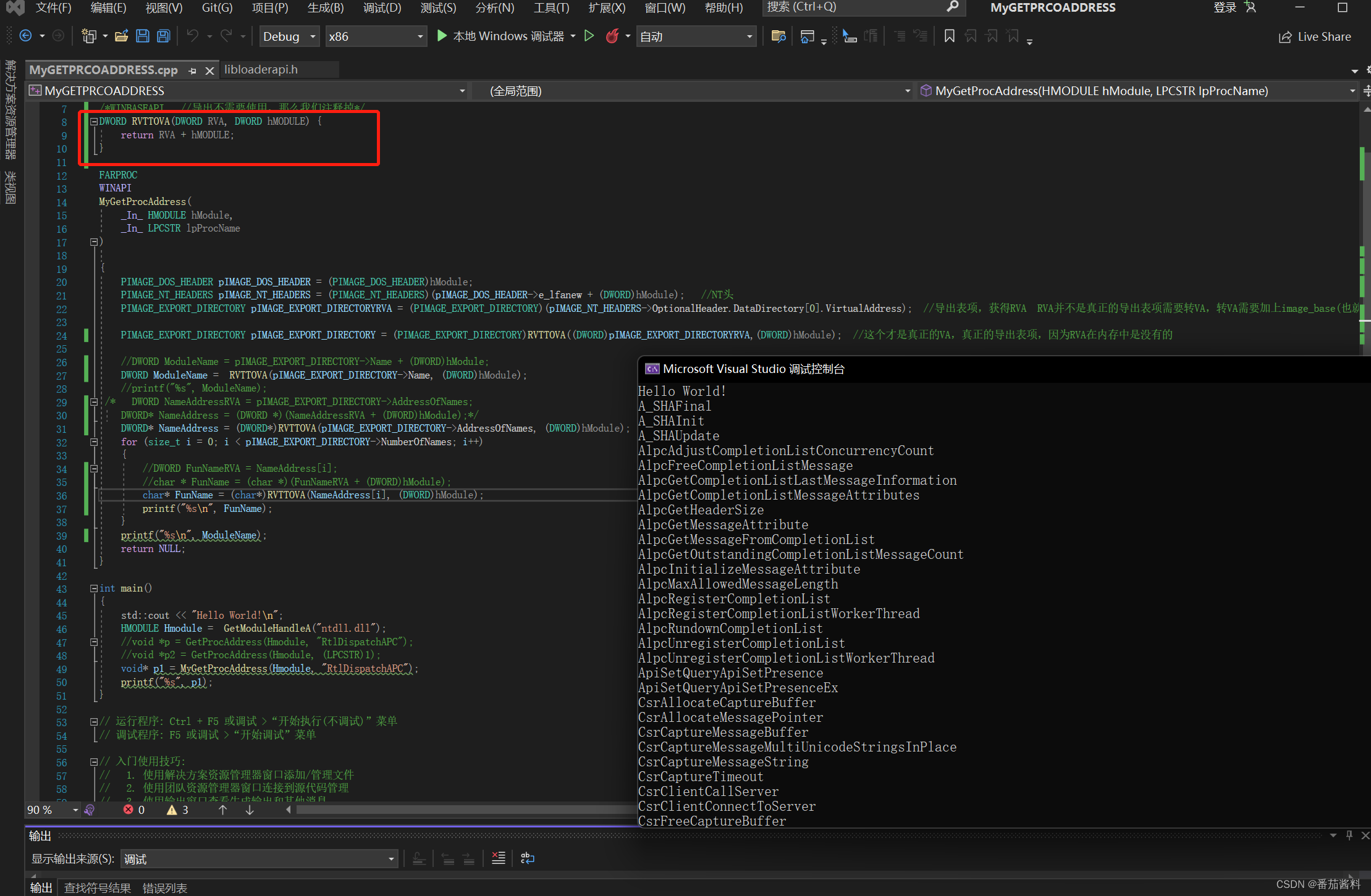
可以看到再次运行可以成功输出相同的结果
#include <iostream>
#include<Windows.h>
/*WINBASEAPI //导出不需要使用,那么我们注释掉*/
DWORD RVTTOVA(DWORD RVA, DWORD hMODULE) {
return RVA + hMODULE;
}
FARPROC
WINAPI
MyGetProcAddress(
_In_ HMODULE hModule,
_In_ LPCSTR lpProcName
)
{
PIMAGE_DOS_HEADER pIMAGE_DOS_HEADER = (PIMAGE_DOS_HEADER)hModule;
PIMAGE_NT_HEADERS pIMAGE_NT_HEADERS = (PIMAGE_NT_HEADERS)(pIMAGE_DOS_HEADER->e_lfanew + (DWORD)hModule); //NT头
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORYRVA = (PIMAGE_EXPORT_DIRECTORY)(pIMAGE_NT_HEADERS->OptionalHeader.DataDirectory[0].VirtualAddress); //导出表项,获得RVA RVA并不是真正的导出表项需要转VA,转VA需要加上image_base(也就是加载地址)
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORY = (PIMAGE_EXPORT_DIRECTORY)RVTTOVA((DWORD)pIMAGE_EXPORT_DIRECTORYRVA,(DWORD)hModule); //这个才是真正的VA,真正的导出表项,因为RVA在内存中是没有的
//DWORD ModuleName = pIMAGE_EXPORT_DIRECTORY->Name + (DWORD)hModule;
DWORD ModuleName = RVTTOVA(pIMAGE_EXPORT_DIRECTORY->Name, (DWORD)hModule);
//printf("%s", ModuleName);
/* DWORD NameAddressRVA = pIMAGE_EXPORT_DIRECTORY->AddressOfNames;
DWORD* NameAddress = (DWORD *)(NameAddressRVA + (DWORD)hModule);*/
DWORD* NameAddress = (DWORD*)RVTTOVA(pIMAGE_EXPORT_DIRECTORY->AddressOfNames, (DWORD)hModule);
for (size_t i = 0; i < pIMAGE_EXPORT_DIRECTORY->NumberOfNames; i++)
{
//DWORD FunNameRVA = NameAddress[i];
//char * FunName = (char *)(FunNameRVA + (DWORD)hModule);
char* FunName = (char*)RVTTOVA(NameAddress[i], (DWORD)hModule);
printf("%s\n", FunName);
}
printf("%s\n", ModuleName);
return NULL;
}
int main()
{
std::cout << "Hello World!\n";
HMODULE Hmodule = GetModuleHandleA("ntdll.dll");
//void *p = GetProcAddress(Hmodule, "RtlDispatchAPC");
//void *p2 = GetProcAddress(Hmodule, (LPCSTR)1);
void* p1 = MyGetProcAddress(Hmodule, "RtlDispatchAPC");
printf("%x", p1);
}
最后输出的0这里有问题,是因为需要我们改成printf打印p而不是p1,要进行对比
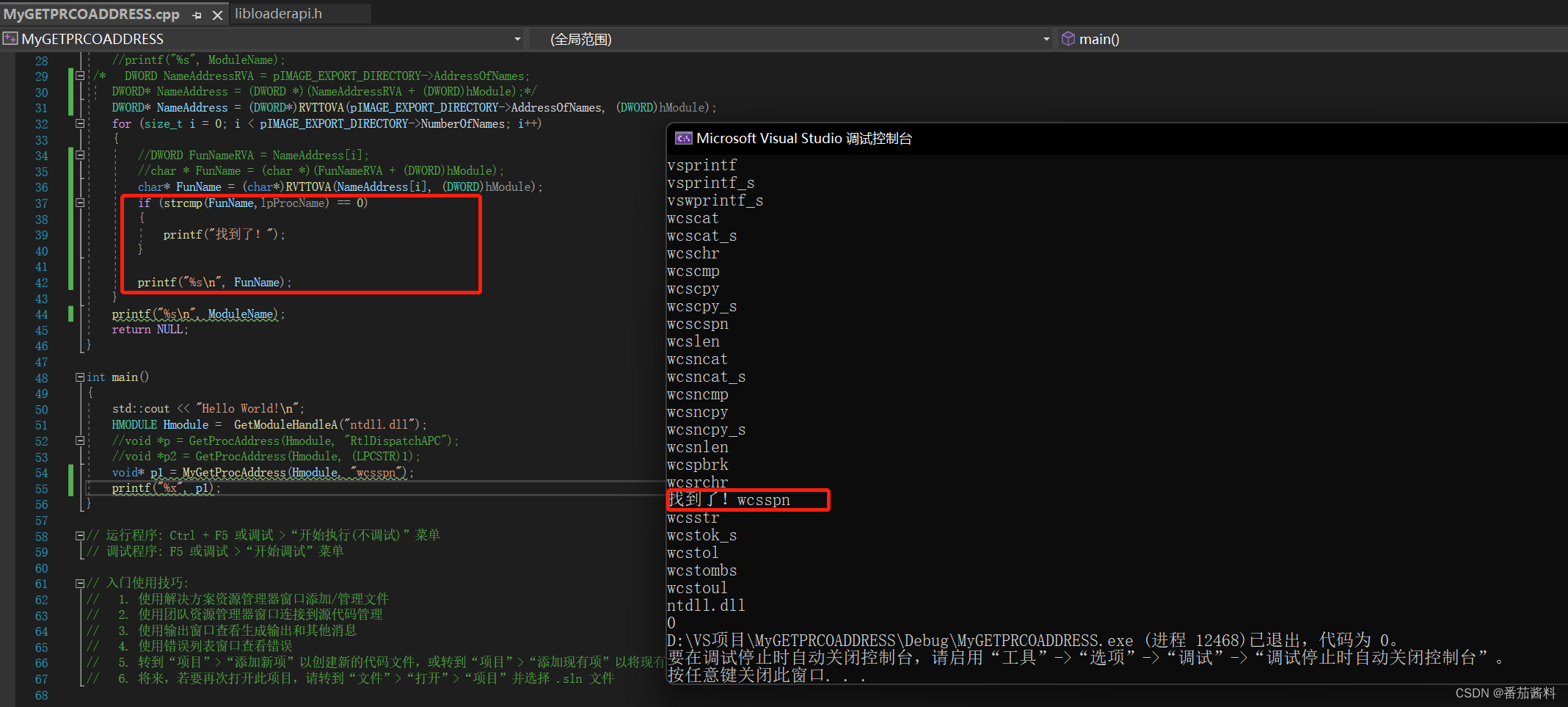
注意之前的自定义函数名写错了,应该是RVATOVA,因为是RVA转VA,之前写的没注意到

然后我们写导出函数名称序号表
//导出函数名称序号表
DWORD* NameOrdinalAddress = (DWORD*)RVATOVA(pIMAGE_EXPORT_DIRECTORY->AddressOfNameOrdinals, (DWORD)hModule);

可以看到显示出了序号,发现是二字节而不是四字节,那么我们就不能用DWORD了要用二字节的WORD
那么我们打印序号,接下来写导出函数地址表,都写在一块了
//导出函数名称序号表
WORD* NameOrdinalAddress = (WORD*)RVATOVA(pIMAGE_EXPORT_DIRECTORY->AddressOfNameOrdinals, (DWORD)hModule);
//导出函数地址表
DWORD* AddressFun = (DWORD*)RVATOVA(pIMAGE_EXPORT_DIRECTORY->AddressOfFunctions, (DWORD)hModule);
for (size_t i = 0; i < pIMAGE_EXPORT_DIRECTORY->NumberOfNames; i++)
{
//DWORD FunNameRVA = NameAddress[i];
//char * FunName = (char *)(FunNameRVA + (DWORD)hModule);
char* FunName = (char*)RVATOVA(NameAddress[i], (DWORD)hModule);
if (strcmp(FunName,lpProcName) == 0)
{
printf("%d\n",NameOrdinalAddress[i] + pIMAGE_EXPORT_DIRECTORY->Base);
printf("%x\n", RVATOVA(AddressFun[NameOrdinalAddress[i]],(DWORD)hModule));
printf("找到了!");
}
//printf("%s\n", FunName);
}
printf("%s\n", ModuleName);
return NULL;
}
试试wcsspn函数

试试RtlDispatchAPC函数

可以看到对比序号都一样,说明没有序号找错
总结
那么这里来总结下,总共四步骤
1.导出表
2.导出函数名称表
3.导出函数名称序号表
4.导出函数地址表
完整代码:
#include <iostream>
#include<Windows.h>
/*WINBASEAPI //导出不需要使用,那么我们注释掉*/
DWORD RVATOVA(DWORD RVA, DWORD hMODULE) {
return RVA + hMODULE;
}
FARPROC
WINAPI
MyGetProcAddress(
_In_ HMODULE hModule,
_In_ LPCSTR lpProcName
)
{
PIMAGE_DOS_HEADER pIMAGE_DOS_HEADER = (PIMAGE_DOS_HEADER)hModule;
PIMAGE_NT_HEADERS pIMAGE_NT_HEADERS = (PIMAGE_NT_HEADERS)(pIMAGE_DOS_HEADER->e_lfanew + (DWORD)hModule); //NT头
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORYRVA = (PIMAGE_EXPORT_DIRECTORY)(pIMAGE_NT_HEADERS->OptionalHeader.DataDirectory[0].VirtualAddress); //导出表项,获得RVA RVA并不是真正的导出表项需要转VA,转VA需要加上image_base(也就是加载地址)
//导出表
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORY = (PIMAGE_EXPORT_DIRECTORY)RVATOVA((DWORD)pIMAGE_EXPORT_DIRECTORYRVA,(DWORD)hModule); //这个才是真正的VA,真正的导出表项,因为RVA在内存中是没有的
//DWORD ModuleName = pIMAGE_EXPORT_DIRECTORY->Name + (DWORD)hModule;
DWORD ModuleName = RVATOVA(pIMAGE_EXPORT_DIRECTORY->Name, (DWORD)hModule);
//printf("%s", ModuleName);
/* DWORD NameAddressRVA = pIMAGE_EXPORT_DIRECTORY->AddressOfNames;
DWORD* NameAddress = (DWORD *)(NameAddressRVA + (DWORD)hModule);*/
//导出函数名称表
DWORD* NameAddress = (DWORD*)RVATOVA(pIMAGE_EXPORT_DIRECTORY->AddressOfNames, (DWORD)hModule);
//导出函数名称序号表
WORD* NameOrdinalAddress = (WORD*)RVATOVA(pIMAGE_EXPORT_DIRECTORY->AddressOfNameOrdinals, (DWORD)hModule);
//导出函数地址表
DWORD* AddressFun = (DWORD*)RVATOVA(pIMAGE_EXPORT_DIRECTORY->AddressOfFunctions, (DWORD)hModule);
for (size_t i = 0; i < pIMAGE_EXPORT_DIRECTORY->NumberOfNames; i++)
{
//DWORD FunNameRVA = NameAddress[i];
//char * FunName = (char *)(FunNameRVA + (DWORD)hModule);
char* FunName = (char*)RVATOVA(NameAddress[i], (DWORD)hModule);
if (strcmp(FunName,lpProcName) == 0)
{
printf("%d\n",NameOrdinalAddress[i] + pIMAGE_EXPORT_DIRECTORY->Base);
printf("%x\n", RVATOVA(AddressFun[NameOrdinalAddress[i]],(DWORD)hModule));
printf("找到了!");
}
//printf("%s\n", FunName);
}
printf("%s\n", ModuleName);
return NULL;
}
int main()
{
std::cout << "Hello World!\n";
HMODULE Hmodule = GetModuleHandleA("ntdll.dll");
void *p = GetProcAddress(Hmodule, "RtlDispatchAPC");
//void *p2 = GetProcAddress(Hmodule, (LPCSTR)1);
void* p1 = MyGetProcAddress(Hmodule, "RtlDispatchAPC");
printf("%x", p);
}
通过序号去找
以刚才的例子,这里通过刚才得到的8去获取名称
反汇编代码看1是比较是否大于FFFF,如果大于就跳到字符串,小于就跳到序号
比如8,就需要8-base才是获得的
可以看到自定义的序号查找也找到了
#include <iostream>
#include<Windows.h>
/*WINBASEAPI //导出不需要使用,那么我们注释掉*/
DWORD RVATOVA(DWORD RVA, DWORD hMODULE) {
return RVA + hMODULE;
}
//FARPROC
//WINAPI
//MyGetProcAddress(
// _In_ HMODULE hModule,
// _In_ LPCSTR lpProcName
//)
FARPROC
WINAPI
MyOrdinalGetProcAddress(
_In_ HMODULE hModule,
_In_ LPCSTR lpProcName
)
{
PIMAGE_DOS_HEADER pIMAGE_DOS_HEADER = (PIMAGE_DOS_HEADER)hModule;
PIMAGE_NT_HEADERS pIMAGE_NT_HEADERS = (PIMAGE_NT_HEADERS)(pIMAGE_DOS_HEADER->e_lfanew + (DWORD)hModule); //NT头
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORYRVA = (PIMAGE_EXPORT_DIRECTORY)(pIMAGE_NT_HEADERS->OptionalHeader.DataDirectory[0].VirtualAddress); //导出表项,获得RVA RVA并不是真正的导出表项需要转VA,转VA需要加上image_base(也就是加载地址)
//导出表
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORY = (PIMAGE_EXPORT_DIRECTORY)RVATOVA((DWORD)pIMAGE_EXPORT_DIRECTORYRVA,(DWORD)hModule); //这个才是真正的VA,真正的导出表项,因为RVA在内存中是没有的
//导出函数地址表
DWORD* AddressFun = (DWORD*)RVATOVA(pIMAGE_EXPORT_DIRECTORY->AddressOfFunctions, (DWORD)hModule);
DWORD dwBase = pIMAGE_EXPORT_DIRECTORY->Base;
DWORD funAddress = RVATOVA( AddressFun[(DWORD)lpProcName - dwBase],(DWORD)hModule);
printf("%x\n", funAddress);
return NULL;
}
int main()
{
std::cout << "Hello World!\n";
HMODULE Hmodule = GetModuleHandleA("ntdll.dll");
void *p = GetProcAddress(Hmodule, "RtlDispatchAPC");
void *p2 = GetProcAddress(Hmodule, (LPCSTR)8);
void* p1 = MyOrdinalGetProcAddress(Hmodule, (LPCSTR)8);
printf("%x", p1);
printf("%x", p2);
}
以上是找到了该函数,那么我们通过strcmp函数来获得该函数
#include <iostream>
#include<Windows.h>
/*WINBASEAPI //导出不需要使用,那么我们注释掉*/
//FARPROC
//WINAPI
DWORD MyGetProcAddress(
_In_ HMODULE hModule,
_In_ LPCSTR lpProcName
)
{
PIMAGE_DOS_HEADER pIMAGE_DOS_HEADER = (PIMAGE_DOS_HEADER)hModule;
PIMAGE_NT_HEADERS pIMAGE_NT_HEADERS = (PIMAGE_NT_HEADERS)(pIMAGE_DOS_HEADER->e_lfanew + (DWORD)hModule); //NT头
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORYRVA = (PIMAGE_EXPORT_DIRECTORY)(pIMAGE_NT_HEADERS->OptionalHeader.DataDirectory[0].VirtualAddress); //导出表项,获得RVA RVA并不是真正的导出表项需要转VA,转VA需要加上image_base(也就是加载地址)
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORY = (PIMAGE_EXPORT_DIRECTORY)((DWORD)pIMAGE_EXPORT_DIRECTORYRVA + (DWORD)hModule); //这个才是真正的VA,真正的导出表项,因为RVA在内存中是没有的
DWORD ModuleName = pIMAGE_EXPORT_DIRECTORY->Name + (DWORD)hModule;
//可以看到底下地址都需要写成指针形式
DWORD *pAddressOfFunction = (DWORD*)(pIMAGE_EXPORT_DIRECTORY->AddressOfFunctions + (DWORD)hModule);
//printf("%s", ModuleName);
DWORD *NameAddress = (DWORD*)(pIMAGE_EXPORT_DIRECTORY->AddressOfNames + (DWORD)hModule);
WORD* pAddressOfNameOrdinals = (WORD*)(pIMAGE_EXPORT_DIRECTORY->AddressOfNameOrdinals + (DWORD)hModule);
for (size_t i = 0; i < pIMAGE_EXPORT_DIRECTORY->NumberOfNames; i++)
{
DWORD FunNameRVA = NameAddress[i];
char* FunName = (char*)(FunNameRVA + (DWORD)hModule);
if (strcmp(lpProcName, FunName) == 0)
{
return (pAddressOfFunction[pAddressOfNameOrdinals[i]] + (DWORD)hModule);
}
printf("%s\n", FunName);
}
printf("%s\n", ModuleName);
return NULL;
}
int main()
{
std::cout << "Hello World!\n";
HMODULE Hmodule = GetModuleHandleA("ntdll.dll");
//void *p = GetProcAddress(Hmodule, "RtlDispatchAPC");
//void *p2 = GetProcAddress(Hmodule, (LPCSTR)1);
DWORD p1 = MyGetProcAddress(Hmodule, "RtlDispatchAPC");
printf("%s", p1);
}

可以看到成功获得函数
这里我们要获得的是Kernel32.dll里的CreateFileA函数

#include <iostream>
#include<Windows.h>
/*WINBASEAPI //导出不需要使用,那么我们注释掉*/
//FARPROC
//WINAPI
DWORD MyGetProcAddress(
_In_ HMODULE hModule,
_In_ LPCSTR lpProcName
)
{
PIMAGE_DOS_HEADER pIMAGE_DOS_HEADER = (PIMAGE_DOS_HEADER)hModule;
PIMAGE_NT_HEADERS pIMAGE_NT_HEADERS = (PIMAGE_NT_HEADERS)(pIMAGE_DOS_HEADER->e_lfanew + (DWORD)hModule); //NT头
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORYRVA = (PIMAGE_EXPORT_DIRECTORY)(pIMAGE_NT_HEADERS->OptionalHeader.DataDirectory[0].VirtualAddress); //导出表项,获得RVA RVA并不是真正的导出表项需要转VA,转VA需要加上image_base(也就是加载地址)
PIMAGE_EXPORT_DIRECTORY pIMAGE_EXPORT_DIRECTORY = (PIMAGE_EXPORT_DIRECTORY)((DWORD)pIMAGE_EXPORT_DIRECTORYRVA + (DWORD)hModule); //这个才是真正的VA,真正的导出表项,因为RVA在内存中是没有的
DWORD ModuleName = pIMAGE_EXPORT_DIRECTORY->Name + (DWORD)hModule;
//可以看到底下地址都需要写成指针形式
DWORD *pAddressOfFunction = (DWORD*)(pIMAGE_EXPORT_DIRECTORY->AddressOfFunctions + (DWORD)hModule);
//printf("%s", ModuleName);
DWORD *NameAddress = (DWORD*)(pIMAGE_EXPORT_DIRECTORY->AddressOfNames + (DWORD)hModule);
WORD* pAddressOfNameOrdinals = (WORD*)(pIMAGE_EXPORT_DIRECTORY->AddressOfNameOrdinals + (DWORD)hModule);
for (size_t i = 0; i < pIMAGE_EXPORT_DIRECTORY->NumberOfNames; i++)
{
DWORD FunNameRVA = NameAddress[i];
char* FunName = (char*)(FunNameRVA + (DWORD)hModule);
if (strcmp(lpProcName, FunName) == 0)
{
return (pAddressOfFunction[pAddressOfNameOrdinals[i]] + (DWORD)hModule);
}
printf("%s\n", FunName);
}
printf("%s\n", ModuleName);
return NULL;
}
int main()
{
std::cout << "Hello World!\n";
HMODULE Hmodule = GetModuleHandleA("Kernel32.dll");
//void *p = GetProcAddress(Hmodule, "RtlDispatchAPC");
//void *p2 = GetProcAddress(Hmodule, (LPCSTR)1);
DWORD p1 = MyGetProcAddress(Hmodule, "CreateFileA");
printf("%s", p1);
}
这里获得的是地址,之后调用需要转换成函数形式
























 1468
1468

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








