摘要
文章首先从双层优化的角度统一表示了超参数优化、多任务和元学习等复杂学习和视觉问题,建立了一个基于最佳响应的单层重构和一个统一的算法框架,来制定一个基于梯度的双层优化方法,最后讨论了该框架的潜力和未来研究方向。
BLO思想
用其KKT条件替换LL子问题等式,并最小化原始变量x和y及其乘数。
由此产生的问题称为平衡约束数学程序(MPEC)。该问题的求解方法有两种:。第一种方法,即非线性规划方法将互补约束重写为非线性不等式,然后允许利用强大的数值非线性规划解算器;另一种方法,即组合方法处理析取约束的组合性质。
使用MPEC方法处理BLO问题会导致两个问题:首先,理论上,如果LL子问题存在多个乘数,则MPEC将不等同于原始BLO;其次,在求解BLO问题时,引入的辅助乘子变量会限制数值效率。
双层优化
双层优化(BLO)包含两层优化任务,其中一层嵌套在另一层中作为约束。内部(或嵌套)和外部优化任务通常分别称为低级(LL)和高级(UL))子问题。
LL子问题表示为以下参数优化任务。
min
y
∈
Y
f
(
x
,
y
)
,
(
p
a
r
a
m
e
t
e
r
i
z
e
d
b
y
x
)
\min\limits_{y\in Y}f(x,y),(parameterized by x)
y∈Yminf(x,y),(parameterizedbyx)
标准BLO问题可以正式表示为如下公式。
min
x
∈
X
F
(
x
,
y
)
,
s
.
t
.
y
∈
S
(
x
)
\min\limits_{x\in \mathcal{X}}F(x,y),s.t. y\in \mathcal{S}(x)
x∈XminF(x,y),s.t.y∈S(x)
将UL和LL子问题分别称为“领导者”和“追随者”。“领导者”首先选择决策x,然后“追随者”观察x,以响应决策y。
因此,追随者可能取决于领导者的决定。同样,领导者必须满足取决于追随者决策的约束。
值得注意的是,如图1,对于UL决策变量x的每个(或某些)固定值,LL子问题可能有多个解。当LL子问题的解不是唯一的时,领导者很难预测跟随者将选择S(x)中的哪一点。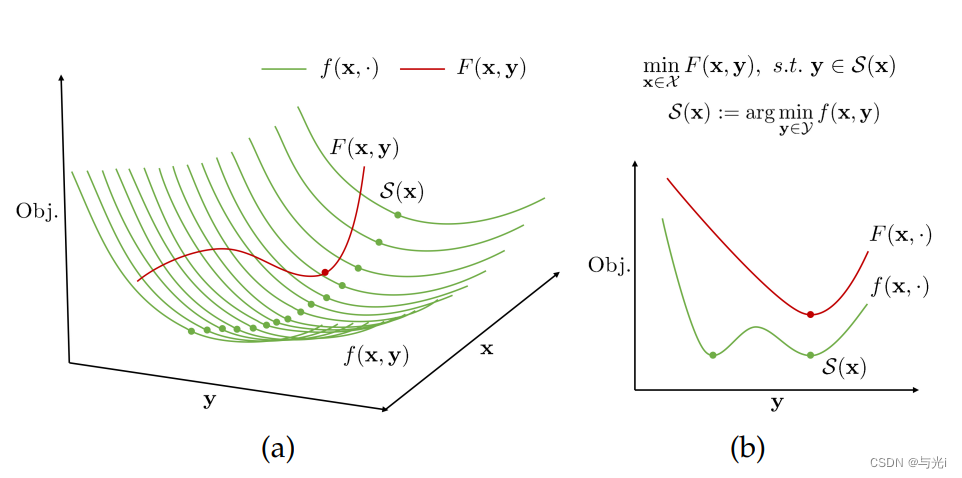
图1 BLO问题
BLOS解决实际问题
超参数优化
超参数优化 (Hyper parameter Optimization,HO)是指识别无法单独使用训练数据学习的最优超参数集的问题,是BLO在学习和视野领域最直接的应用。
具体而言,UL目标
F
(
x
,
y
;
D
v
a
l
)
F(x,y;Dval)
F(x,y;Dval)旨在最大限度地减少与超参数(例如权重衰减)相关的验证集损失,而LL目标
F
(
x
,
y
;
D
t
r
)
F(x,y;Dtr)
F(x,y;Dtr)需要通过最大限度地减少与模型参数(例如权重和偏差)相关的训练损失来输出学习算法。如图2所示,完整数据集D分为训练和验证数据集(即
D
t
r
∪
D
v
a
l
Dtr∪ Dval
Dtr∪Dval)并说明了如何从BLO的角度对HO任务进行建模。受这种嵌套优化的启发,大多数HO应用程序可以表示为以双层结构为特征的BLO问题。UL子问题涉及超参数x的优化,LL子问题(w.r.t.权重参数y)旨在通过最小化训练损失找到学习算法
g
y
(
⋅
)
g_y(·)
gy(⋅)。
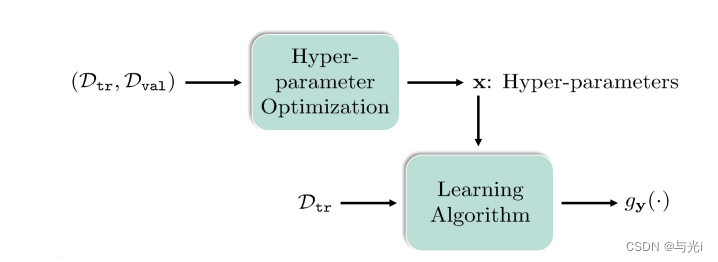
图2
多任务和元学习
元学习Meta Learning,含义为学会学习,即learn to learn。Meta Learning希望使得模型获取一种“学会学习”的能力,使其可以在获取已有“知识”的基础上快速学习新的任务。
根据元参数和网络参数之间的依赖关系,当前基于元学习的方法可以大致分为两组,即元特征学习和元初始化学习。
元初始化学习旨在通过网络初始化来研究多个任务的元信息。从BLO的角度来看,实际上是分别通过LL和UL子问题来表示网络参数及其初始化(基于多任务信息)。
元特征学习方法首先将网络体系结构分离为元特征提取部分和任务特定部分。然后制定分层学习过程。因此,在这些任务中,可以使用UL和LL子问题分别对元特征部分和任务特定部分进行建模。
神经架构搜索
神经架构搜索(NAS)旨在自动化选择最佳神经网络架构的过程。
现在常用的方法是基于梯度的可微NAS方法。给定适当的搜索空间,基于梯度的可差分NAS方法有助于为不同的视觉和学习任务推导出最佳的体系结构。从BLO的角度来看,UL目标w.r.t.架构权重(如块/单元)可以用x参数化,LL目标w.r.t.模型权重可以用y参数化。因此,整个搜索过程实际上可以表述为BLO范式,其中,UL目标由基于验证数据集Dval的F (x,y; Dval)定义,LL目标由基于训练数据集Dtr的f (x,y;Dtr)给出。
对抗性学习
对抗性学习(AL)目前被认为是最重要的学习任务之一。它已应用于多种应用领域,即图像生成、对抗性攻击和人脸验证。
大多数AL方法可以将无监督学习问题描述为两个对手之间的双层博弈:从分布中采样的生成器和将样本分类为真或假的鉴别器。在BLO范式下,参与者和评论家分别对应于UL和L变量。
主流的BLO模型
如图3,可以将现有方法分为两大类,即 w/ 和 w/o LLS 假设。 在使用 LLS 假设求解 BLO 时,这些方法可以进一步分为两类:EGBR 和 IGBR。 对于 EGBR,它们可以通过不同的自动微分 (AD) 技术来求解(如虚线矩形所示)。 最近的研究还提出了两种算法来解决没有 LLS 假设的 BLO,实际上引入了双层梯度聚合或基于值函数的内点法来计算间接梯度。
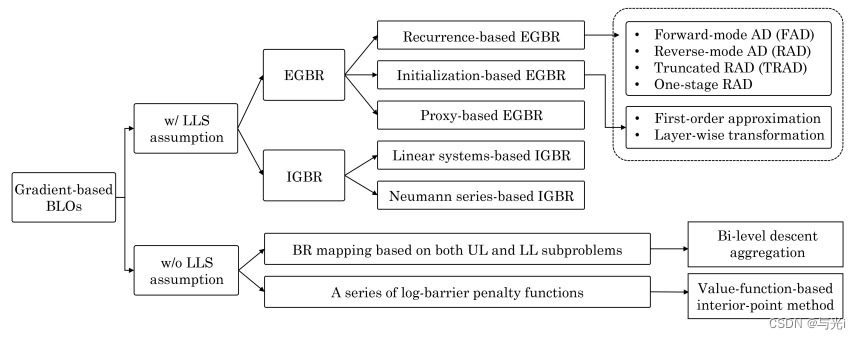
图3
现有主流基于梯度的BLO方法的优化过程如图4所示。
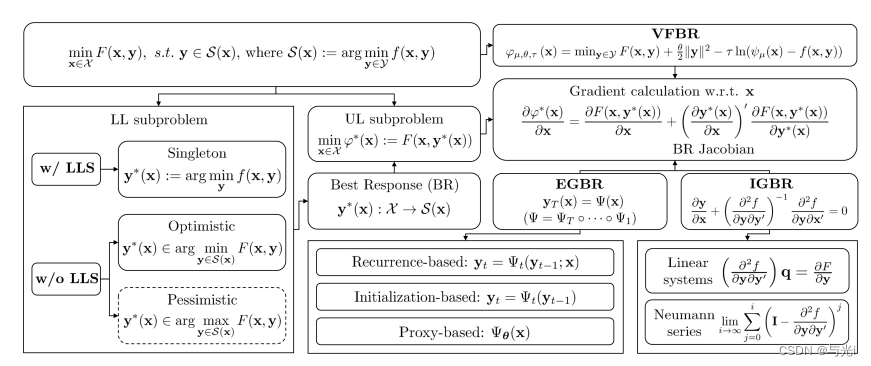
图4





















 2万+
2万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








