linux内核编译
想学习一下kasan的相关配置,但kasan是内核中的相关配置,开启得编译内核,本文使用虚拟机与wsl两种方式来编译内核启动kasan。
虚拟机编译自己的内核
在虚拟机里编译内核参考ubuntu内核编译与Kasan初探
查看当前的内核
uname -a
查看可支持的内核
sudo apt-cache search linux-source
选择可支持的内核版本安装,这里选择4.15
sudo apt-get install linux-source-4.15.0
安装完成后会在/usr/src中看到相应的内核源码,打开并解压
cd /usr/src
sudo tar -axvf linux-source-4.15.0.tar.bz2
可以看到解压后的源码内容
修改设置
sudo make menuconfig
报错缺少menuconfig
安装库
sudo apt-get install libncurses5-dev
再次运行
sudo make menuconfig
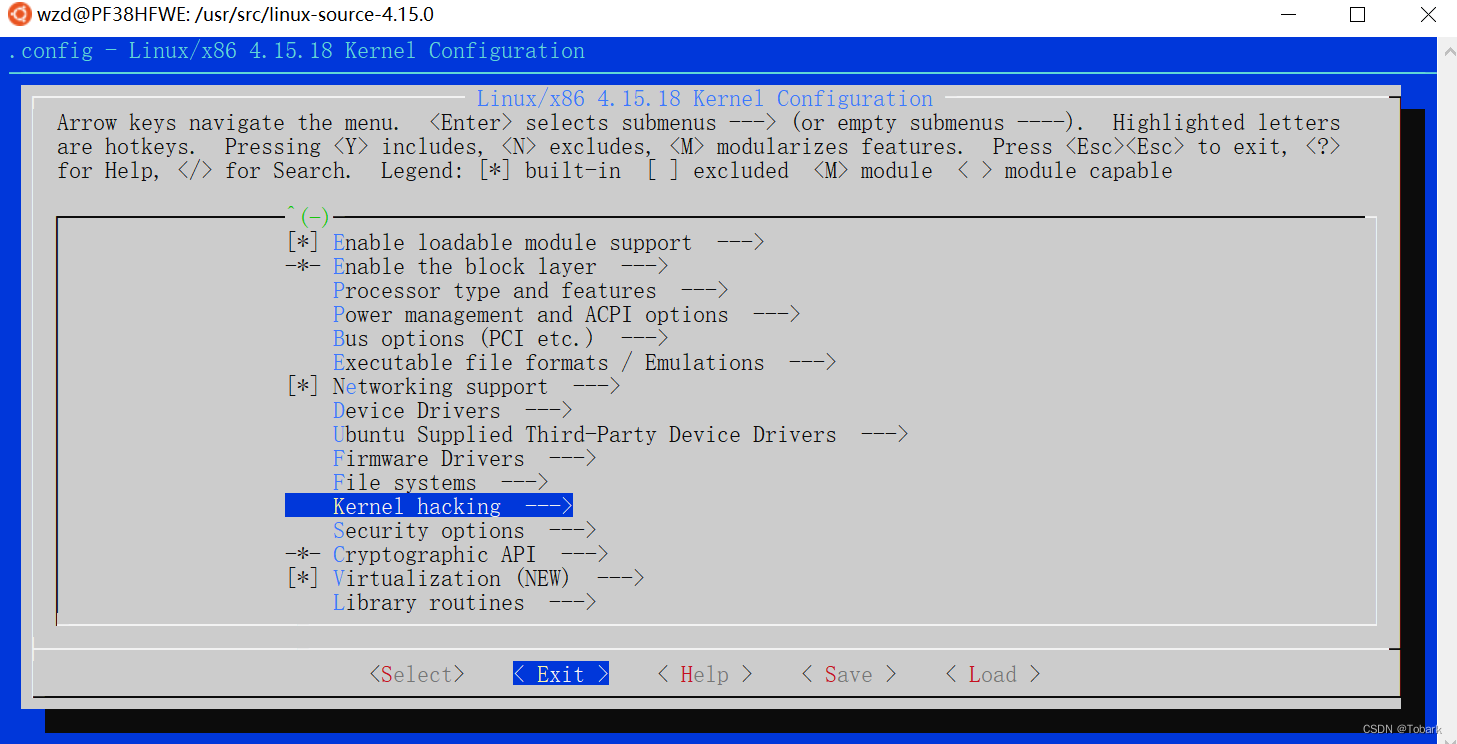
在kernel hacking/memory debugging,点击H,查看依赖
编译内核
cd linux-source-4.15.0/
make -j 2 clean #先清除临时文件
make -j 2 bzImage #先编译内核,生成bzImage文件
sudo make -j 2 modules #再编译模块,要权限(大量时间)
编译后的文件位于kernel中
编译完内核后,没有将其放入到相关的系统路径中,模块需要安装,内核也需要移动。运行modules_install,将模块安装到lib/modules
sudo make modules_install
安装之后在/lib/modules下回生成一个新目录
移动内核
sudo cp /usr/src/linux-source-4.10.0/arch/x86/boot/bzImage /boot/vmlinuz-4.10.17
sudo cp /usr/src/linux-source-4.10.0/.config /boot/config-4.10.17
#给新内核文件添加 X 权限
sudo chmod a+x /boot/vmlinuz-4.10.17
sudo cp /usr/src/linux-source-4.10.0/System.map /boot/System.map-4.10.17
sudo gzip -c /usr/src/linux-source-4.10.0/Module.symvers > /boot/symvers-4.10.17(这个要最高权限)
##sudo passwd设置密码(第一次时)
##su
##获取最高权限
建立对应的initial Ram Disk
首先安装dracut,安装完之后建立对应disk
sudo apt install dracut
sudo dracut -v /boot/initramfs-4.10.17.img 4.10.17
编辑开机选项
grub-mkconfig -o /boot/grub/grub.cfg
在虚拟机上编译内核后重启会出现一个错误:
VBoxClient (seamless): failed to start. Stage: Setting guest IRQ filter mas Error: VERR_INTERNAL_ERROR
解决该错误参考
sudo apt-get install gcc make perl
cd /media/$USER/VBox_GAs_5.2.22
sudo ./VBoxLinuxAdditions.run
sudo reboot
以上是在虚拟机上编译的结果,但不巧的是我使用的最多是是WSL
WSL编译自己的内核
参考如何让WSL2使用自己编译的内核
编译内核使用的均为相同的内核源码,但与使用虚拟机不同,WSL中微软进行了一些配置,熟悉内核配置的人都知道内核相关配置位于kenel目录下的.config中,因此我们需要在内核官网上下载相应的.config文件:
尽量使用WSL2,查询自己的WSL:
wsl -l -v
使用一下命令可以转换版本
wsl --set-version ubuntu 2
WSL运行效率高,编译内核迅速,可以利用windows上的资源,方便的使用windows上的软件来查看文件
去官网或者镜像站下载内核源码
与在虚拟机上编译不同,WSL需要对配置文件进行配置:
使用微软的配置文件,项目的链接在/Microsoft/config-wsl
在要执行编译的工作区目录创建配置文件,可以删除之前的配置文件
rm .config
touch .config
这里是使用WSL来学习kasan,修改.config,在其中加入(这里并不是一个好的操作,推荐将wsl的.config复制进来后根据虚拟机中的方法使用make menuconfig来进行修改)
CONFIG_SLUB_DEBUG=y
CONFIG_KASAN=y
保存后编译,-j8代表内核的线程,
make -j8
加入后会在编译开始出现几个新的配置,代表加入成功:
出现以下报错:
CHK include/config/kernel.release
CHK include/generated/uapi/linux/version.h
DESCEND objtool
CHK include/generated/utsrelease.h
CHK scripts/mod/devicetable-offsets.h
CHK include/generated/bounds.h
CHK include/generated/timeconst.h
CHK include/generated/asm-offsets.h
CALL scripts/checksyscalls.sh
CHK include/generated/compile.h
CC [M] ubuntu/xr-usb-serial/xr_usb_serial_common.o
CHK kernel/config_data.h
CC [M] ubuntu/vbox/vboxguest/common/log/log.o
ubuntu/xr-usb-serial/xr_usb_serial_common.c: In function ‘xr_usb_serial_ctrl_irq’:
ubuntu/xr-usb-serial/xr_usb_serial_common.c:301:21: warning: unused variable ‘tty’ [-Wunused-variable]
struct tty_struct *tty;
^~~
ubuntu/xr-usb-serial/xr_usb_serial_common.c: In function ‘xr_usb_serial_process_read_urb’:
ubuntu/xr-usb-serial/xr_usb_serial_common.c:433:24: warning: unused variable ‘tty’ [-Wunused-variable]
struct tty_struct *tty;
^~~
ubuntu/xr-usb-serial/xr_usb_serial_common.c: In function ‘xr_usb_serial_softint’:
ubuntu/xr-usb-serial/xr_usb_serial_common.c:508:24: warning: unused variable ‘tty’ [-Wunused-variable]
struct tty_struct *tty;
^~~
ubuntu/xr-usb-serial/xr_usb_serial_common.c: In function ‘xr_usb_serial_tty_ioctl’:
ubuntu/xr-usb-serial/xr_usb_serial_common.c:918:17: warning: this ‘if’ clause does not guard... [-Wmisleading-indentation]
if (get_user(val, (int __user *)(arg + 2 * sizeof(int))))
^~
ubuntu/xr-usb-serial/xr_usb_serial_common.c:921:4: note: ...this statement, but the latter is misleadingly indented as if it were guarded by the ‘if’
if (channel == -1)
^~
CC [M] ubuntu/vbox/vboxguest/common/log/logrelellipsis.o
CC [M] ubuntu/vbox/vboxguest/common/log/logcom.o
CC [M] ubuntu/vbox/vboxguest/common/log/logformat.o
CC [M] ubuntu/vbox/vboxguest/common/misc/RTAssertMsg1Weak.o
CC [M] ubuntu/vbox/vboxguest/common/misc/RTAssertMsg2.o
CC [M] ubuntu/vbox/vboxguest/common/misc/RTAssertMsg2Add.o
CC [M] ubuntu/vbox/vboxguest/common/misc/RTAssertMsg2AddWeak.o
CC [M] ubuntu/vbox/vboxguest/common/misc/RTAssertMsg2AddWeakV.o
CC [M] ubuntu/vbox/vboxguest/common/misc/RTAssertMsg2Weak.o
In file included from ./include/linux/bitmap.h:9:0,
from ./include/linux/cpumask.h:12,
from ./arch/x86/include/asm/cpumask.h:5,
from ./arch/x86/include/asm/msr.h:11,
from ./arch/x86/include/asm/processor.h:21,
from ./arch/x86/include/asm/cpufeature.h:5,
from ./arch/x86/include/asm/thread_info.h:53,
from ./include/linux/thread_info.h:39,
from ./arch/x86/include/asm/preempt.h:7,
from ./include/linux/preempt.h:81,
from ./include/linux/spinlock.h:51,
from ./include/linux/seqlock.h:36,
from ./include/linux/time.h:6,
from ./include/linux/stat.h:19,
from ./include/linux/module.h:10,
from ./ubuntu/vbox/vboxguest/include/internal/iprt.h:56,
from ubuntu/vbox/vboxguest/common/log/log.c:32:
In function ‘memcpy’,
inlined from ‘rtLogStPNCpyPad’ at ubuntu/vbox/vboxguest/common/log/log.c:3587:9,
inlined from ‘rtLogOutputPrefixed’ at ubuntu/vbox/vboxguest/common/log/log.c:3819:25:
./include/linux/string.h:374:4: error: call to ‘__read_overflow2’ declared with attribute error: detected read beyond size of object passed as 2nd parameter
__read_overflow2();
^~~~~~~~~~~~~~~~~~
readelf: Warning: [31]: Info field (30) should index a relocatable section.
scripts/Makefile.build:333: recipe for target 'ubuntu/vbox/vboxguest/common/log/log.o' failed
make[3]: *** [ubuntu/vbox/vboxguest/common/log/log.o] Error 1
make[3]: *** Waiting for unfinished jobs....
scripts/Makefile.build:607: recipe for target 'ubuntu/vbox/vboxguest' failed
make[2]: *** [ubuntu/vbox/vboxguest] Error 2
scripts/Makefile.build:607: recipe for target 'ubuntu/vbox' failed
make[1]: *** [ubuntu/vbox] Error 2
make[1]: *** Waiting for unfinished jobs....
readelf: Warning: [31]: Info field (30) should index a relocatable section.
Makefile:1087: recipe for target 'ubuntu' failed
make: *** [ubuntu] Error 2
出现该问题是因为GCC版本不对,要更新到和微软提供的配置文件一样的版本,GCC版本更新参考
注:WSL使用过程中遇到的一些问题,可以直接在微软的github上提交相应的issue,基本上都有很快的回答和解决,这里要注意,我们虽然使用的是WSL2,但是在微软的issue上在WSL上提交即可。
将编译产生的文件
/usr/src/linux-source-4.15.0/arch/x86/boot/bzImage
复制替换C:\WINDOWS\System32\lxss\tools 的kernel,注意将kernel备份
重启wsl
wsl --shutdown
uname -r #检查内核版本
编译内核成功
编译后的镜像文件比编译前的大一倍左右

测试kasan
在源码lib中包含了test_kasan的测试文件test_kasan.c
makefile:
obj-m += test_kasan.o
all:
make -C /lib/modules/4.15.0/build M=$(PWD) modules
clean:
make -C /lib/modules/4.15.0/build M=$(PWD) clean
~
编译生成test_kasan.ko文件
安装ko文件
insmod test_kasan.ko
报错
insmod test_kasan.ko
insmod: ERROR: could not insert module test_kasan.ko: Operation not permitted
打印系统信息
dmesg
打印以下信息
kmalloc_oob_krealloc_more+0x6c/0xd8 [test_kasan]
[14513.029878] kmalloc_tests_init+0x2b/0xd2b [test_kasan]
[14513.029882] do_one_initcall+0x7d/0x240
[14513.029885] do_init_module+0x22a/0x790
[14513.029888] load_module+0x5336/0x8230
[14513.029891] SyS_finit_module+0x202/0x260
[14513.029894] do_syscall_64+0x22b/0x600
[14513.029898] entry_SYSCALL_64_after_hwframe+0x41/0xa6
[14513.029901] Freed by task 0:
[14513.029901] (stack is not available)
[14513.029903] The buggy address belongs to the object at ffff88829179ea88
which belongs to the cache kmalloc-32 of size 32
[14513.029904] The buggy address is located 19 bytes inside of
32-byte region [ffff88829179ea88, ffff88829179eaa8)
[14513.029905] The buggy address belongs to the page:
[14513.029906] page:ffffea000a45e780 count:1 mapcount:0 mapping:0000000000000000 index:0xffff88829179f388 compound_mapcount: 0
[14513.029912] flags: 0x4000000000008100(slab|head)
[14513.029915] raw: 4000000000008100 0000000000000000 ffff88829179f388 000000010015000f
[14513.029920] raw: ffff888187c03c50 ffff888187c03c50 ffff888187c0c640 0000000000000000
[14513.029924] page dumped because: kasan: bad access detected
[14513.029927] Memory state around the buggy address:
[14513.029928] ffff88829179e980: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[14513.029929] ffff88829179ea00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[14513.029930] >ffff88829179ea80: fc 00 00 03 fc fc fc fc fc fc fc fc fc fc fc fc
[14513.029931] ^
[14513.029932] ffff88829179eb00: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[14513.029933] ffff88829179eb80: fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc fc
[14513.029934] ==================================================================
[14513.029937] kasan test: kmalloc_oob_krealloc_less out-of-bounds after krealloc less
[14513.029946] ==================================================================
[14513.029949] BUG: KASAN: slab-out-of-bounds in kmalloc_oob_krealloc_less+0xc1/0xd0 [test_kasan]
[14513.029950] Write of size 1 at addr ffff88829179f397 by task insmod/11566
[14513.029952] CPU: 1 PID: 11566 Comm: insmod Tainted: PF B O 4.15.18-wzd-kasan_debug-WSL2 #5
[14513.029956] Call Trace:
[14513.029959] dump_stack+0xe3/0x13e
[14513.029963] ? switchdev_obj_size.isra.1.part.2+0x7/0x7
[14513.029967] ? kmalloc_oob_krealloc_less+0xc1/0xd0 [test_kasan]
[14513.029972] ? printk+0x94/0xb0
[14513.029976] ? SyS_gethostname.cold+0x11/0x11
[14513.029980] ? SyS_gethostname.cold+0x11/0x11
[14513.030003] ? kmalloc_oob_krealloc_less+0xc1/0xd0 [test_kasan]
[14513.030010] print_address_description+0x6a/0x270
[14513.030017] ? kmalloc_oob_krealloc_less+0xc1/0xd0 [test_kasan]
[14513.030026] kasan_report+0x240/0x350
[14513.030032] kmalloc_oob_krealloc_less+0xc1/0xd0 [test_kasan]
[14513.030037] ? copy_user_test+0x1c9/0x1c9 [test_kasan]
[14513.030042] kmalloc_tests_init+0x30/0xd2b [test_kasan]
[14513.030046] do_one_initcall+0x7d/0x240
[14513.030049] ? initcall_blacklisted+0x180/0x180
[14513.030054] ? kasan_unpoison_shadow+0x30/0x40
[14513.030058] ? __asan_register_globals+0x6e/0x80
[14513.030062] do_init_module+0x22a/0x790
[14513.030066] ? SyS_delete_module+0x640/0x640
[14513.030069] ? load_module+0x5329/0x8230
[14513.030073] load_module+0x5336/0x8230
[14513.030079] ? module_frob_arch_sections+0x20/0x20
[14513.030083] ? vfs_read+0x24e/0x2e0
[14513.030087] ? kernel_read+0x90/0x130
[14513.030090] ? kernel_read_file+0x3fb/0x670
[14513.030095] ? kernel_read_file_from_fd+0x74/0xb0
[14513.030099] SyS_finit_module+0x202/0x260
[14513.030103] ? SyS_init_module+0x320/0x320
[14513.030107] ? SyS_newfstat+0x75/0xb0
[14513.030111] ? filp_close+0x1d0/0x1d0
[14513.030115] ? SyS_init_module+0x320/0x320
[14513.030118] do_syscall_64+0x22b/0x600
[14513.030122] ? __switch_to_asm+0x31/0x60
[14513.030125] ? __switch_to_asm+0x25/0x60
[14513.030128] ? __switch_to_asm+0x31/0x60
[14513.030132] ? syscall_return_slowpath+0x2d0/0x2d0
[14513.030136] ? do_page_fault+0x87/0x310
[14513.030140] ? __do_page_fault+0x9f0/0x9f0
[14513.030143] ? prepare_exit_to_usermode+0x200/0x200
[14513.030147] ? syscall_trace_enter+0xc10/0xc10
[14513.030151] ? __put_user_4+0x1c/0x30
[14513.030155] entry_SYSCALL_64_after_hwframe+0x41/0xa6
[14513.030159] RIP: 0033:0x7f319220c539
[14513.030161] RSP: 002b:00007fffddb8d7e8 EFLAGS: 00000246 ORIG_RAX: 0000000000000139
[14513.030166] RAX: ffffffffffffffda RBX: 00005634a5a9f480 RCX: 00007f319220c539
[14513.030169] RDX: 0000000000000000 RSI: 00005634a398acee RDI: 0000000000000003
[14513.030173] RBP: 00005634a398acee R08: 0000000000000000 R09: 00007f31924df000
[14513.030177] R10: 0000000000000003 R11: 0000000000000246 R12: 0000000000000000
[14513.030180] R13: 00005634a5a9f450 R14: 0000000000000000 R15: 0000000000000000





















 2391
2391











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








