最近才注意到bro更名为zeek了,官网上有说明,貌似是因为bro有不太好的含义。
bro官网上提供了一个探测ftp暴力破解进行登录的例子。该例子中把所有突破阈值的可疑主机记录了下来(这些主机多次尝试登录某个ftp服务器,很不幸,它们登录失败了很多次,被改脚本记录为可疑的主机并通过NOTICE框架写到了notice.log中)。
下面是我尝试用bro写的一个简单的例子,有对logging,sumstats,notice框架的简单使用。
potential_ftp_attackers中存放那些曾经尝试登录ftp且失败了的主机ip。ftp_quests中存放成功登录ftp服务器的主机的ip。potential_attacks_info中存放那些可疑的攻击者以及它们尝试登录失败的次数。在脚本的最后对每个可疑的攻击者作检查,看看是否有成功登录了的。
另,在vscode中可以找到bro的插件,虽然只是语法高亮(基本没人用这个东西呀)。
新的调研内容:要求获取突破成功(那些可疑主机)的用户名和密码,并将之保存至日志。
新创建一个日志流,写一个名为ftp-request-info.log的日志文件。这里是所有的ftp请求的用户名和密码的记录。想要知道突破成功的主机的用户名和密码,就在此日志文件的基础上筛选。
##! FTP brute-forcing detector, triggering when too many rejected usernames or
##! failed passwords have occurred from a single address.
@load base/protocols/ftp
@load base/frameworks/sumstats
@load base/utils/time
module FTP;
global potential_ftp_attackers : set[string];
global ftp_quests : set[string];
global potential_attacks_info : table[string] of count;
export {
redef enum Notice::Type += {
## Indicates a host bruteforcing FTP logins by watching for too
## many rejected usernames or failed passwords.
Bruteforcing
};
# Create an ID for our new stream. By convention, this is
# called "MY_LOG".
redef enum Log::ID += { MY_LOG,
REQUEST_LOG };
# Define the record type that will contain the data to log.
type Info: record {
ts: time &log;
id: conn_id &log;
};
type request_info: record{
ts: time &log;
ftp_requester_ip: addr &log;
command: string &log;
username: string &log;
password: string &log;
};
# Optionally, we can add a new field to the connection record so that
# the data we are logging (our "Info" record) will be easily
# accessible in a variety of event handlers.
redef record connection += {
# By convention, the name of this new field is the lowercase name
# of the module.
ftp: Info &optional;
};
## How many rejected usernames or passwords are required before being
## considered to be bruteforcing.
const bruteforce_threshold: double = 20 &redef;
## The time period in which the threshold needs to be crossed before
## being reset.
const bruteforce_measurement_interval = 15mins &redef;
}
event bro_init(){
print "ready to use SumStats";
local r1: SumStats::Reducer = [$stream="ftp.failed_auth", $apply=set(SumStats::UNIQUE), $unique_max=double_to_count(bruteforce_threshold+2)];
local r2: SumStats::Reducer = [$stream="ftp.success_auth", $apply=set(SumStats::SUM)];
local r3: SumStats::Reducer = [$stream="ftp.failed_auth_sum", $apply=set(SumStats::SUM)];
SumStats::create([$name = "ftp.success_auth",
$epoch = 1min,
$reducers = set(r2),
$epoch_result(ts: time, key: SumStats::Key, result: SumStats::Result) =
{
print key;
print result;
print fmt("Number of successful ftp login(s) from %s within one minute: %.0f", key$host, result["ftp.success_auth"]$sum);
}]);
SumStats::create([$name = "ftp.failed_auth_sum",
$epoch = bruteforce_measurement_interval,
$reducers = set(r3),
$epoch_result(ts: time, key: SumStats::Key, result: SumStats::Result) =
{
print fmt("Number of unsuccessful ftp logins(s) from %s within 15 minutes: %.0f", key$host, result["ftp.failed_auth_sum"]$sum);
}]);
SumStats::create([$name = "ftp-detect-bruteforcing",
$epoch = bruteforce_measurement_interval,
$reducers = set(r1),
$threshold_val(key: SumStats::Key, result: SumStats::Result) =
{
return result["ftp.failed_auth"]$num+0.0;
},
$threshold = bruteforce_threshold,
$threshold_crossed(key: SumStats::Key, result: SumStats::Result) =
{
local r = result["ftp.failed_auth"];
local dur = duration_to_mins_secs(r$end-r$begin);
local plural = r$unique>1 ? "s" : "";
local message = fmt("%s had %d failed logins on %d FTP server%s in %s", key$host, r$num, r$unique, plural, dur);
print message;
NOTICE([$note = FTP::Bruteforcing,
$src = key$host,
$msg = message,
$identifier = cat(key$host)]);
},
$epoch_result(ts: time, key: SumStats::Key, result: SumStats::Result) = {
for (e in result["ftp.failed_auth"]$unique_vals){
print fmt("attacker wants to login %s via FTP", e$str);
}
# here is an output example below
# ts: 1499171520.032659
# key: [str=<uninitialized>, host=172.16.0.1]
# result: {
# [ftp.failed_auth] = [begin=1499170763.708863, end=1499171519.331044, num=2441, average=<uninitialized>, hll_unique=0, card=<uninitialized>, hll_error_margin=<uninitialized>, hll_confidence=<uninitialized>, last_elements=<uninitialized>, max=<uninitialized>, min=<uninitialized>, samples=[], sample_elements=0, num_samples=0, variance=<uninitialized>, prev_avg=<uninitialized>, var_s=0.0, std_dev=0.0, sum=0.0, topk=<uninitialized>, unique=1, unique_max=22, unique_vals={
# [num=<uninitialized>, dbl=<uninitialized>, str=192.168.10.50]
# }]
# }
}
]);
}
# This event is handled at a priority higher than zero so that if
# users modify this stream in another script, they can do so at the
# default priority of zero.
event bro_init() &priority=5{
# Create the stream. This adds a default filter automatically.
Log::create_stream(FTP::MY_LOG, [$columns=Info, $path="ftp"]);
Log::create_stream(FTP::REQUEST_LOG, [$columns=request_info, $path="ftp-request-info"]);
# Add a new filter to the FTP::MY_LOG stream that logs only
# timestamp and originator address.
local filter: Log::Filter = [$name="orig-only", $path="origs",
$include=set("ts", "id.orig_h")];
Log::add_filter(FTP::MY_LOG, filter);
# We can get a log file called origs.log using this filter
}
# Here I want to collect username and password sent by requesters.
event ftp_request(c :connection, command: string, arg: string){
print "a ftp request occurred! ";
if(command == "USER"){
local rec1: FTP::request_info = [$ts = network_time(),
$ftp_requester_ip = c$id$orig_h,$command = command,
$username = arg, $password = ""];
Log::write(FTP::REQUEST_LOG, rec1);
} else if(command == "PASS"){
local rec2: FTP::request_info = [$ts = network_time(),
$ftp_requester_ip = c$id$orig_h, $command = command,
$username = "", $password = arg];
Log::write(FTP::REQUEST_LOG, rec2);
}
}
event ftp_reply(c: connection, code: count, msg: string, cont_resp: bool){
# logging
local rec: FTP::Info = [$ts = network_time(), $id = c$id];
# Store a copy of the data in the connection record so other
# event handlers can access it.
# c$ftp = rec;
Log::write(FTP::MY_LOG, rec);
local cmd = c$ftp$cmdarg$cmd;
if (code == 331 || code == 332){
print "request for a user name or password!";
}
if (code == 200){
# print c;
local test = fmt("%s", c$id$orig_h);
if(test !in ftp_quests){
add ftp_quests[test];
} else {
# this host has once established a ftp connection
# maybe it is an attacker
print "depulicate ftp connection (obviously the previous ftp connection has broken down)";
}
print fmt("a successful ftp login from %s!", c$id$orig_h);
SumStats::observe("ftp.success_auth", SumStats::Key($host=c$id$orig_h),
SumStats::Observation($num=1));
}
if ( cmd == "USER" || cmd == "PASS" ){
if ( FTP::parse_ftp_reply_code(code)$x == 5 ){
# local test1 = fmt("%s", c$id$resp_h);
local test2 = fmt("%s", c$id$orig_h);
# if(test1 !in potential_ftp_attackers){
# add potential_ftp_attackers[test1];
# potential_attacks_info[test1] = 1;
# } else {
# potential_attacks_info[test1] += 1;
# }
if(test2 !in potential_ftp_attackers){
add potential_ftp_attackers[test2];
potential_attacks_info[test2] = 1;
} else {
potential_attacks_info[test2] += 1;
}
SumStats::observe("ftp.failed_auth", [$host=c$id$orig_h], [$str=cat(c$id$resp_h)]);
SumStats::observe("ftp.failed_auth_sum", SumStats::Key($host=c$id$orig_h),
SumStats::Observation($num=1));
}
}
}
event bro_done(){
print "finishing";
print "here are(is) potential ftp attacker(s): ";
print potential_ftp_attackers;
print "here are hosts which established ftp connections successfully";
print ftp_quests;
print "here are poential attackers cooresponding to their attempt times";
print potential_attacks_info;
print "start checking...";
for(e in potential_ftp_attackers){
print fmt("check %s", e);
if(e in ftp_quests){
print fmt("It seems that %s is an attacker and it succeeded to login via ftp(input wrong password %d times).", e, potential_attacks_info[e]);
} else {
print fmt("%s failed to login via ftp", e);
}
}
print "end checking...";
}运行的结果,拿得是bro官网提供的pcap文件:
here are poential attackers cooresponding to their attempt times
{
[120.221.194.180] = 16,
[56.199.108.57] = 5,
[106.20.55.102] = 1,
[131.243.3.49] = 11,
[121.58.136.76] = 12,
[98.37.80.166] = 1,
[54.231.35.101] = 2,
[133.128.74.175] = 5,
[33.96.133.127] = 1,
[79.71.74.165] = 7,
[10.84.255.93] = 1,
[10.194.47.41] = 12,
[185.90.84.96] = 3,
[176.224.179.191] = 1,
[30.159.200.190] = 1,
[42.113.44.231] = 1,
[131.243.1.83] = 123,
[195.96.20.122] = 2,
[184.217.39.68] = 2,
[224.20.132.30] = 2,
[187.18.15.111] = 1,
[178.148.238.232] = 2,
[196.233.219.147] = 1,
[172.130.217.52] = 1,
[198.158.17.190] = 1,
[135.160.181.10] = 3,
[96.159.45.4] = 1,
[94.7.2.86] = 1,
[246.124.22.82] = 1,
[30.146.52.247] = 2,
[241.34.155.201] = 9,
[68.98.238.60] = 1,
[5.181.121.178] = 2,
[234.147.130.114] = 9,
[210.13.53.158] = 1,
[110.102.141.8] = 3,
[74.12.78.121] = 1,
[65.105.203.243] = 1,
[218.65.255.185] = 3,
[188.179.92.114] = 10,
[230.126.59.23] = 2,
[179.192.184.110] = 4,
[138.151.189.128] = 18,
[136.145.76.48] = 1,
[191.63.112.154] = 1,
[206.135.167.184] = 1,
[253.87.26.29] = 1,
[116.70.243.164] = 1,
[142.195.176.72] = 1,
[202.239.81.189] = 1,
[4.18.95.135] = 1,
[32.175.23.146] = 1,
[222.38.6.47] = 1,
[232.82.19.92] = 2,
[99.201.191.152] = 4,
[250.180.225.181] = 2,
[222.162.33.207] = 123,
[205.199.2.103] = 16,
[198.184.76.139] = 3,
[248.186.1.156] = 8,
[147.67.156.179] = 11,
[204.189.164.75] = 1,
[183.173.223.0] = 1,
[135.118.232.105] = 1,
[121.119.209.34] = 1,
[213.102.101.225] = 1,
[59.235.58.155] = 1,
[248.170.78.217] = 2,
[107.143.150.55] = 1,
[234.129.51.135] = 2,
[131.243.1.10] = 279,
[229.226.233.186] = 1,
[20.89.52.195] = 21,
[210.125.39.24] = 4,
[136.64.44.127] = 8,
[66.15.143.67] = 4,
[138.142.53.216] = 1,
[44.76.136.98] = 24,
[25.141.7.128] = 4,
[216.181.212.62] = 1,
[254.105.15.81] = 1,
[163.35.234.74] = 1,
[29.135.233.80] = 1,
[146.134.112.83] = 3,
[42.176.40.48] = 1,
[51.165.231.205] = 2,
[131.102.149.29] = 1,
[234.60.65.4] = 3,
[150.206.239.185] = 1,
[219.199.171.180] = 7,
[13.155.12.221] = 35,
[135.205.98.18] = 1,
[25.188.155.59] = 1,
[132.79.26.176] = 2,
[11.117.225.64] = 1,
[45.9.79.41] = 1,
[44.85.238.2] = 2,
[49.131.41.26] = 2,
[90.50.23.40] = 1,
[253.9.198.39] = 2,
[218.51.165.238] = 1,
[131.192.25.203] = 1,
[208.167.163.43] = 3,
[197.109.165.121] = 2,
[223.252.32.126] = 5,
[70.212.208.175] = 3,
[44.120.49.173] = 1,
[118.14.158.208] = 2,
[194.123.168.69] = 3,
[213.82.145.63] = 2,
[165.166.76.61] = 1,
[95.38.206.165] = 7,
[206.212.29.97] = 1,
[49.241.172.178] = 3,
[228.136.177.100] = 1,
[60.31.90.94] = 3,
[128.224.254.154] = 5,
[149.179.123.67] = 1,
[133.88.74.25] = 5,
[198.111.78.1] = 2,
[120.86.184.155] = 5,
[123.103.74.35] = 1,
[95.237.72.221] = 1,
[150.250.38.223] = 10,
[176.152.171.164] = 3,
[132.34.219.22] = 1,
[176.97.142.45] = 1,
[157.3.95.196] = 1,
[127.127.179.120] = 1,
[157.94.151.3] = 5,
[48.191.139.130] = 5,
[2.246.14.185] = 3,
[78.101.5.64] = 5,
[198.82.60.50] = 4,
[8.138.220.65] = 1,
[145.82.149.241] = 1,
[249.4.134.221] = 1
}
start checking...
check 120.221.194.180
It seems that 120.221.194.180 is an attacker and it succeeded to login via ftp(input wrong password 16 times).
check 56.199.108.57
It seems that 56.199.108.57 is an attacker and it succeeded to login via ftp(input wrong password 5 times).
check 106.20.55.102
It seems that 106.20.55.102 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 131.243.3.49
131.243.3.49 failed to login via ftp
check 121.58.136.76
121.58.136.76 failed to login via ftp
check 98.37.80.166
98.37.80.166 failed to login via ftp
check 54.231.35.101
It seems that 54.231.35.101 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 133.128.74.175
It seems that 133.128.74.175 is an attacker and it succeeded to login via ftp(input wrong password 5 times).
check 33.96.133.127
It seems that 33.96.133.127 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 79.71.74.165
79.71.74.165 failed to login via ftp
check 10.84.255.93
10.84.255.93 failed to login via ftp
check 10.194.47.41
10.194.47.41 failed to login via ftp
check 185.90.84.96
185.90.84.96 failed to login via ftp
check 176.224.179.191
It seems that 176.224.179.191 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 30.159.200.190
30.159.200.190 failed to login via ftp
check 42.113.44.231
42.113.44.231 failed to login via ftp
check 131.243.1.83
131.243.1.83 failed to login via ftp
check 195.96.20.122
195.96.20.122 failed to login via ftp
check 184.217.39.68
It seems that 184.217.39.68 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 224.20.132.30
It seems that 224.20.132.30 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 187.18.15.111
It seems that 187.18.15.111 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 178.148.238.232
178.148.238.232 failed to login via ftp
check 196.233.219.147
It seems that 196.233.219.147 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 172.130.217.52
It seems that 172.130.217.52 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 198.158.17.190
It seems that 198.158.17.190 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 135.160.181.10
It seems that 135.160.181.10 is an attacker and it succeeded to login via ftp(input wrong password 3 times).
check 96.159.45.4
It seems that 96.159.45.4 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 94.7.2.86
94.7.2.86 failed to login via ftp
check 246.124.22.82
246.124.22.82 failed to login via ftp
check 30.146.52.247
It seems that 30.146.52.247 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 241.34.155.201
It seems that 241.34.155.201 is an attacker and it succeeded to login via ftp(input wrong password 9 times).
check 68.98.238.60
68.98.238.60 failed to login via ftp
check 5.181.121.178
It seems that 5.181.121.178 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 234.147.130.114
234.147.130.114 failed to login via ftp
check 210.13.53.158
210.13.53.158 failed to login via ftp
check 110.102.141.8
110.102.141.8 failed to login via ftp
check 74.12.78.121
It seems that 74.12.78.121 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 65.105.203.243
65.105.203.243 failed to login via ftp
check 218.65.255.185
It seems that 218.65.255.185 is an attacker and it succeeded to login via ftp(input wrong password 3 times).
check 188.179.92.114
It seems that 188.179.92.114 is an attacker and it succeeded to login via ftp(input wrong password 10 times).
check 230.126.59.23
It seems that 230.126.59.23 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 179.192.184.110
It seems that 179.192.184.110 is an attacker and it succeeded to login via ftp(input wrong password 4 times).
check 138.151.189.128
It seems that 138.151.189.128 is an attacker and it succeeded to login via ftp(input wrong password 18 times).
check 136.145.76.48
136.145.76.48 failed to login via ftp
check 191.63.112.154
191.63.112.154 failed to login via ftp
check 206.135.167.184
It seems that 206.135.167.184 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 253.87.26.29
It seems that 253.87.26.29 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 116.70.243.164
It seems that 116.70.243.164 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 142.195.176.72
142.195.176.72 failed to login via ftp
check 202.239.81.189
202.239.81.189 failed to login via ftp
check 4.18.95.135
4.18.95.135 failed to login via ftp
check 32.175.23.146
32.175.23.146 failed to login via ftp
check 222.38.6.47
222.38.6.47 failed to login via ftp
check 232.82.19.92
It seems that 232.82.19.92 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 99.201.191.152
It seems that 99.201.191.152 is an attacker and it succeeded to login via ftp(input wrong password 4 times).
check 250.180.225.181
It seems that 250.180.225.181 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 222.162.33.207
It seems that 222.162.33.207 is an attacker and it succeeded to login via ftp(input wrong password 123 times).
check 205.199.2.103
It seems that 205.199.2.103 is an attacker and it succeeded to login via ftp(input wrong password 16 times).
check 198.184.76.139
It seems that 198.184.76.139 is an attacker and it succeeded to login via ftp(input wrong password 3 times).
check 248.186.1.156
It seems that 248.186.1.156 is an attacker and it succeeded to login via ftp(input wrong password 8 times).
check 147.67.156.179
It seems that 147.67.156.179 is an attacker and it succeeded to login via ftp(input wrong password 11 times).
check 204.189.164.75
It seems that 204.189.164.75 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 183.173.223.0
It seems that 183.173.223.0 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 121.119.209.34
It seems that 121.119.209.34 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 135.118.232.105
135.118.232.105 failed to login via ftp
check 213.102.101.225
It seems that 213.102.101.225 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 59.235.58.155
It seems that 59.235.58.155 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 248.170.78.217
It seems that 248.170.78.217 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 107.143.150.55
It seems that 107.143.150.55 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 234.129.51.135
It seems that 234.129.51.135 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 229.226.233.186
It seems that 229.226.233.186 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 131.243.1.10
131.243.1.10 failed to login via ftp
check 20.89.52.195
It seems that 20.89.52.195 is an attacker and it succeeded to login via ftp(input wrong password 21 times).
check 210.125.39.24
210.125.39.24 failed to login via ftp
check 136.64.44.127
It seems that 136.64.44.127 is an attacker and it succeeded to login via ftp(input wrong password 8 times).
check 66.15.143.67
It seems that 66.15.143.67 is an attacker and it succeeded to login via ftp(input wrong password 4 times).
check 138.142.53.216
It seems that 138.142.53.216 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 44.76.136.98
44.76.136.98 failed to login via ftp
check 25.141.7.128
25.141.7.128 failed to login via ftp
check 216.181.212.62
216.181.212.62 failed to login via ftp
check 254.105.15.81
254.105.15.81 failed to login via ftp
check 163.35.234.74
163.35.234.74 failed to login via ftp
check 29.135.233.80
29.135.233.80 failed to login via ftp
check 146.134.112.83
146.134.112.83 failed to login via ftp
check 42.176.40.48
42.176.40.48 failed to login via ftp
check 51.165.231.205
51.165.231.205 failed to login via ftp
check 131.102.149.29
It seems that 131.102.149.29 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 234.60.65.4
234.60.65.4 failed to login via ftp
check 150.206.239.185
It seems that 150.206.239.185 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 219.199.171.180
It seems that 219.199.171.180 is an attacker and it succeeded to login via ftp(input wrong password 7 times).
check 13.155.12.221
It seems that 13.155.12.221 is an attacker and it succeeded to login via ftp(input wrong password 35 times).
check 135.205.98.18
It seems that 135.205.98.18 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 25.188.155.59
It seems that 25.188.155.59 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 132.79.26.176
It seems that 132.79.26.176 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 11.117.225.64
It seems that 11.117.225.64 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 45.9.79.41
It seems that 45.9.79.41 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 44.85.238.2
44.85.238.2 failed to login via ftp
check 49.131.41.26
It seems that 49.131.41.26 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 90.50.23.40
It seems that 90.50.23.40 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 253.9.198.39
It seems that 253.9.198.39 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 218.51.165.238
218.51.165.238 failed to login via ftp
check 131.192.25.203
131.192.25.203 failed to login via ftp
check 208.167.163.43
208.167.163.43 failed to login via ftp
check 197.109.165.121
It seems that 197.109.165.121 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 223.252.32.126
It seems that 223.252.32.126 is an attacker and it succeeded to login via ftp(input wrong password 5 times).
check 44.120.49.173
It seems that 44.120.49.173 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 70.212.208.175
It seems that 70.212.208.175 is an attacker and it succeeded to login via ftp(input wrong password 3 times).
check 118.14.158.208
It seems that 118.14.158.208 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 194.123.168.69
It seems that 194.123.168.69 is an attacker and it succeeded to login via ftp(input wrong password 3 times).
check 213.82.145.63
It seems that 213.82.145.63 is an attacker and it succeeded to login via ftp(input wrong password 2 times).
check 165.166.76.61
165.166.76.61 failed to login via ftp
check 95.38.206.165
It seems that 95.38.206.165 is an attacker and it succeeded to login via ftp(input wrong password 7 times).
check 206.212.29.97
206.212.29.97 failed to login via ftp
check 49.241.172.178
49.241.172.178 failed to login via ftp
check 228.136.177.100
228.136.177.100 failed to login via ftp
check 60.31.90.94
60.31.90.94 failed to login via ftp
check 149.179.123.67
It seems that 149.179.123.67 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 128.224.254.154
128.224.254.154 failed to login via ftp
check 133.88.74.25
It seems that 133.88.74.25 is an attacker and it succeeded to login via ftp(input wrong password 5 times).
check 198.111.78.1
198.111.78.1 failed to login via ftp
check 120.86.184.155
It seems that 120.86.184.155 is an attacker and it succeeded to login via ftp(input wrong password 5 times).
check 123.103.74.35
It seems that 123.103.74.35 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 95.237.72.221
95.237.72.221 failed to login via ftp
check 176.152.171.164
176.152.171.164 failed to login via ftp
check 150.250.38.223
It seems that 150.250.38.223 is an attacker and it succeeded to login via ftp(input wrong password 10 times).
check 132.34.219.22
It seems that 132.34.219.22 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 176.97.142.45
176.97.142.45 failed to login via ftp
check 157.3.95.196
It seems that 157.3.95.196 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 127.127.179.120
It seems that 127.127.179.120 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 157.94.151.3
It seems that 157.94.151.3 is an attacker and it succeeded to login via ftp(input wrong password 5 times).
check 48.191.139.130
It seems that 48.191.139.130 is an attacker and it succeeded to login via ftp(input wrong password 5 times).
check 2.246.14.185
It seems that 2.246.14.185 is an attacker and it succeeded to login via ftp(input wrong password 3 times).
check 78.101.5.64
It seems that 78.101.5.64 is an attacker and it succeeded to login via ftp(input wrong password 5 times).
check 198.82.60.50
It seems that 198.82.60.50 is an attacker and it succeeded to login via ftp(input wrong password 4 times).
check 8.138.220.65
It seems that 8.138.220.65 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
check 145.82.149.241
145.82.149.241 failed to login via ftp
check 249.4.134.221
It seems that 249.4.134.221 is an attacker and it succeeded to login via ftp(input wrong password 1 times).
end checking...可以看到可疑的ip以及它们尝试登录ftp且失败的次数,并且列出了有可疑行为且成功登录了的主机(由于输出太多,上面只列出了最后的结果)。
另外,这里用logging框架生成了两个日志文件,分别是origs.log和ftp.log。其中ftp.log是在添加日志流之后自动生成的。
# Create an ID for our new stream. By convention, this is
# called "MY_LOG".
redef enum Log::ID += { MY_LOG };
# Define the record type that will contain the data to log.
type Info: record {
ts: time &log;
id: conn_id &log;
};
# Optionally, we can add a new field to the connection record so that
# the data we are logging (our "Info" record) will be easily
# accessible in a variety of event handlers.
redef record connection += {
# By convention, the name of this new field is the lowercase name
# of the module.
ftp: Info &optional;
}; # logging
local rec: FTP::Info = [$ts = network_time(), $id = c$id];
# Store a copy of the data in the connection record so other
# event handlers can access it.
# c$ftp = rec;
Log::write(FTP::MY_LOG, rec); 每个日志流至少对应一个日志文件,这部分就对应ftp.log文件了。下面是ftp.log的部分内容:

因为这里的id本身又是record类型的,它包含orig_h,orig_p,resp_h,resp_p四个成员。这四个成员分别是,源主机ip,源主机端口,目的主机ip,目的主机端口。所以,ftp.log实际上记录了五个字段。
在默认的情况下,每个日志流只对应一个日志文件,但可以通过添加过滤器的方法,为某一个日志流添加多个日志文件。
# This event is handled at a priority higher than zero so that if
# users modify this stream in another script, they can do so at the
# default priority of zero.
event bro_init() &priority=5{
# Create the stream. This adds a default filter automatically.
Log::create_stream(FTP::MY_LOG, [$columns=Info, $path="ftp"]);
# Add a mew filter to the FTP::MY_LOG stream that logs only
# timestamp and originator address.
local filter: Log::Filter = [$name="orig-only", $path="origs",
$include=set("ts", "id.orig_h")];
Log::add_filter(FTP::MY_LOG, filter);
# We can get a log file called origs.log using this filter
}这个过滤器会创建origs.log文件,origs.log的内容如下:

因为取了id的orig_h成员,所以最后origs.log中就只有这两个字段。
下面是notice.log的内容:
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path notice
#open 2018-12-12-16-51-49
#fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p fuid file_mime_type file_desc proto note msg sub src dst p n peer_descr actions suppress_for dropped remote_location.country_code remote_location.region remote_location.city remote_location.latitude remote_location.longitude
#types time string addr port addr port string string string enum enum string string addr addr port count string set[enum] interval bool string string string double double
1042214045.140824 - - - - - - - - - FTP::Bruteforcing 222.162.33.207 had 20 failed logins on 1 FTP server in 1m10s - 222.162.33.207 - - - - Notice::ACTION_LOG 3600.000000 F - - - - -
1042511846.764683 - - - - - - - - - FTP::Bruteforcing 13.155.12.221 had 20 failed logins on 1 FTP server in 0m4s - 13.155.12.221 - - - - Notice::ACTION_LOG 3600.000000 F - - - - -
1042736636.176201 - - - - - - - - - FTP::Bruteforcing 20.89.52.195 had 20 failed logins on 1 FTP server in 1m51s - 20.89.52.195 - - - - Notice::ACTION_LOG 3600.000000 F - - - - -
#close 2018-12-12-16-53-37 
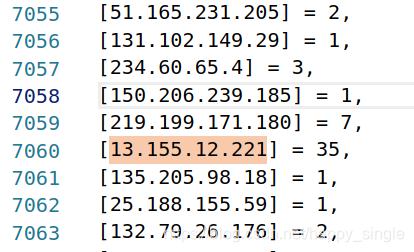

可以看到notice.log中所提及的三个ip的ftp登录失败次数。
check 20.89.52.195
It seems that 20.89.52.195 is an attacker and it succeeded to login via ftp(input wrong password 21 times).
check 13.155.12.221
It seems that 13.155.12.221 is an attacker and it succeeded to login via ftp(input wrong password 35 times).
check 222.162.33.207
It seems that 222.162.33.207 is an attacker and it succeeded to login via ftp(input wrong password 123 times).并且它们最终都暴力破解成功了(成功登上了ftp服务器)。
查看记录用户名和密码(筛选之前的,即所有发出ftp请求并发送用户名和密码的主机,都记录下来,筛选是后话了)

可惜,用户名全是anonymous(匿名),密码全是<password>。看来bro没有直接提供报文中破解之后的密码。

























 1563
1563

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










