文章目录
堆溢出
向堆中写入的字节数超过本身可使用的字节数(可使用的字节数不一定等于申请的字节数,是因为堆管理器会对用户所申请的字节数进行调整,这也导致可利用的字节数都不小于用户申请的字节数),所以可能覆盖到相邻高地址的下一个堆块
前提:
- 能向堆上写入数据
- 写入的数据没有控制好
策略:
- 覆盖与其相邻的高地址chunk的内容
- 再利用堆中的机制来实现任意地址写入或控制堆块内容,进而控制程序的执行流
基本过程
寻找堆分配函数
malloc函数
calloc函数
会清空data内容
calloc(0x20);
//等同于
ptr=malloc(0x20);
memset(ptr,0,0x20);
realloc函数
realloc(chunkdata段地址,size)
-
size大于chunkdata段地址对应的chunk的size时
chunkdata段地址对应的chunk与topchunk相邻,直接扩展该chunk到新size大小
chunkdata段地址对应的chunk与topchunk不相邻,相当于free(chunkdata段地址),malloc(size)
-
size小于chunkdata段地址对应的chunk的size时
相差容得下一个最小chunk(不同位数最小chunk大小不同),则不变
相差容得下一个最小chunk,则切割chunk两部分,free掉chunkdata段地址对应的chunk的size-size的部分
-
size等于0,相当于free(ptr)
-
size等于chunkdata段地址对应的chunk的size时
寻找危险函数
输入
gets,直接读取一行,忽略 ‘\x00’
scanf
vscanf
输出
printf
sprintf
字符串
strlen,字符串长度,遇到 ‘\x00’ 停止
strcpy,字符串复制,遇到 ‘\x00’ 停止
strcat,字符串拼接,遇到 ‘\x00’ 停止
bcopy
具体分配
malloc接受数值会经过下列转化:
(((req) + SIZE_SZ + MALLOC_ALIGN_MASK < MINSIZE) ? MINSIZE: ((req) + SIZE_SZ + MALLOC_ALIGN_MASK) & ! MALLOC_ALIGN_MASK
一个三目运算符 a?b :c
reg为malloc传入的参数,SIZE_SZ和操作系统位数有关 32位为4,64位为8位。MALLOC_ALIGN_MASK也与操作系统位数有关,32位为7,64位为15.最后的值为size大小(不包括标志位)(除了malloc参数小于8和16,size大小一律为0x10和0x20)
first-fit 演示(Demonstrating glibc malloc’s first-fit behavior.)
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
int main()
{
fprintf(stderr, "This file doesn't demonstrate an attack, but shows the nature of glibc's allocator.\n");
fprintf(stderr, "glibc uses a first-fit algorithm to select a free chunk.\n");
fprintf(stderr, "If a chunk is free and large enough, malloc will select this chunk.\n");
fprintf(stderr, "This can be exploited in a use-after-free situation.\n");
fprintf(stderr, "Allocating 2 buffers. They can be large, don't have to be fastbin.\n");
char* a = malloc(0x512);
char* b = malloc(0x256);
char* c;
fprintf(stderr, "1st malloc(0x512): %p\n", a);
fprintf(stderr, "2nd malloc(0x256): %p\n", b);
fprintf(stderr, "we could continue mallocing here...\n");
fprintf(stderr, "now let's put a string at a that we can read later \"this is A!\"\n");
strcpy(a, "this is A!");
fprintf(stderr, "first allocation %p points to %s\n", a, a);
fprintf(stderr, "Freeing the first one...\n");
free(a);
fprintf(stderr, "We don't need to free anything again. As long as we allocate smaller than 0x512, it will end up at %p\n", a);
fprintf(stderr, "So, let's allocate 0x500 bytes\n");
c = malloc(0x500);
fprintf(stderr, "3rd malloc(0x500): %p\n", c);
fprintf(stderr, "And put a different string here, \"this is C!\"\n");
strcpy(c, "this is C!");
fprintf(stderr, "3rd allocation %p points to %s\n", c, c);
fprintf(stderr, "first allocation %p points to %s\n", a, a);
fprintf(stderr, "If we reuse the first allocation, it now holds the data from the third allocation.\n");
}
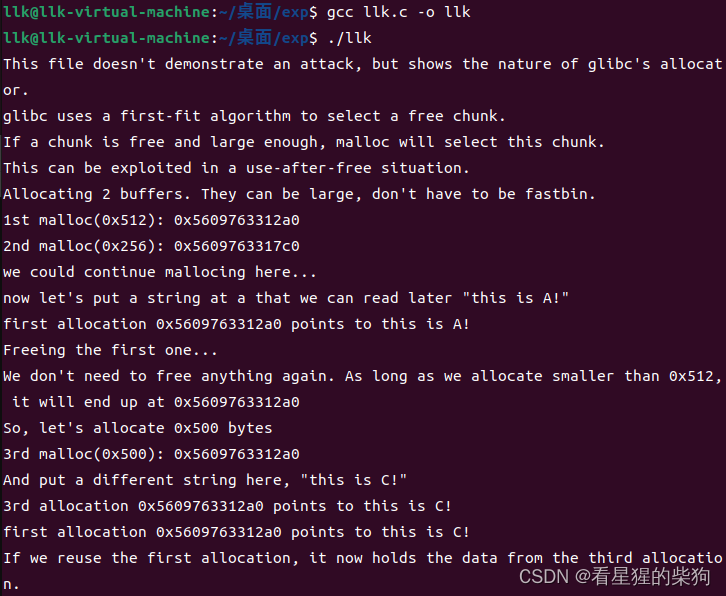
结果
发现第一次malloc free后的堆指针和第三次malloc后的堆指针相同。
释放掉一个内存后,这个内存的指针依旧是有效的,若不慎在后续代码中再次引用了已释放的内存块,可能导致不能预知的错误。这个缺陷被叫做 Use-after-free(UaF)
tcache演示(Demonstrating glibc’s tcache index calculation)
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <malloc.h>
struct malloc_chunk {
size_t mchunk_prev_size; /* Size of previous chunk (if free). */
size_t mchunk_size; /* Size in bytes, including overhead. */
struct malloc_chunk* fd; /* double links -- used only if free. */
struct malloc_chunk* bk;
/* Only used for large blocks: pointer to next larger size. */
struct malloc_chunk* fd_nextsize; /* double links -- used only if free. */
struct malloc_chunk* bk_nextsize;
};
/* The corresponding word size. */
#define SIZE_SZ (sizeof (size_t))//32位还是64位
#define MALLOC_ALIGNMENT (2 * SIZE_SZ < __alignof__ (long double) \
? __alignof__ (long double) : 2 * SIZE_SZ) /为8字节还是16字节
/* The corresponding bit mask value. */
#define MALLOC_ALIGN_MASK (MALLOC_ALIGNMENT - 1)
/* The smallest possible chunk */
#define MIN_CHUNK_SIZE (offsetof(struct malloc_chunk, fd_nextsize)) //最小的chunk的size的大小
/* The smallest size we can malloc is an aligned minimal chunk */
#define MINSIZE \
(unsigned long)(((MIN_CHUNK_SIZE+MALLOC_ALIGN_MASK) & ~MALLOC_ALIGN_MASK))
#define request2size(req) \
(((req) + SIZE_SZ + MALLOC_ALIGN_MASK < MINSIZE) ? \
MINSIZE : \
((req) + SIZE_SZ + MALLOC_ALIGN_MASK) & ~MALLOC_ALIGN_MASK)
/* When "x" is from chunksize(). */
# define csize2tidx(x) (((x) - MINSIZE + MALLOC_ALIGNMENT - 1) / MALLOC_ALIGNMENT)//求在tcache bin中的索引
/* When "x" is a user-provided size. */
# define usize2tidx(x) csize2tidx (request2size (x))
int main()
{
unsigned long long req;
unsigned long long tidx;
fprintf(stderr, "This file doesn't demonstrate an attack, but calculates the tcache idx for a given chunk size.\n");
fprintf(stderr, "The basic formula is as follows:\n");
fprintf(stderr, "\tIDX = (CHUNKSIZE - MINSIZE + MALLOC_ALIGNMENT - 1) / MALLOC_ALIGNMENT\n");
fprintf(stderr, "\tOn a 64 bit system the current values are:\n");
fprintf(stderr, "\t\tMINSIZE: 0x%lx\n", MINSIZE);
fprintf(stderr, "\t\tMALLOC_ALIGNMENT: 0x%lx\n", MALLOC_ALIGNMENT);
fprintf(stderr, "\tSo we get the following equation:\n");
fprintf(stderr, "\tIDX = (CHUNKSIZE - 0x%lx) / 0x%lx\n\n", MINSIZE-MALLOC_ALIGNMENT+1, MALLOC_ALIGNMENT);
fprintf(stderr, "BUT be AWARE that CHUNKSIZE is not the x in malloc(x)\n");
fprintf(stderr, "It is calculated as follows:\n");
fprintf(stderr, "\tIF x + SIZE_SZ + MALLOC_ALIGN_MASK < MINSIZE(0x%lx) CHUNKSIZE = MINSIZE (0x%lx)\n", MINSIZE, MINSIZE);
fprintf(stderr, "\tELSE: CHUNKSIZE = (x + SIZE_SZ + MALLOC_ALIGN_MASK) & ~MALLOC_ALIGN_MASK) \n");
fprintf(stderr, "\t=> CHUNKSIZE = (x + 0x%lx + 0x%lx) & ~0x%lx\n\n\n", SIZE_SZ, MALLOC_ALIGN_MASK, MALLOC_ALIGN_MASK);
while(1) {
fprintf(stderr, "[CTRL-C to exit] Please enter a size x (malloc(x)) in hex (e.g. 0x10): ");
scanf("%llx", &req);
tidx = usize2tidx(req);
if (tidx > 63) {
fprintf(stderr, "\nWARNING: NOT IN TCACHE RANGE!\n");
}
fprintf(stderr, "\nTCache Idx: %llu\n", tidx);
}
return 0;
}
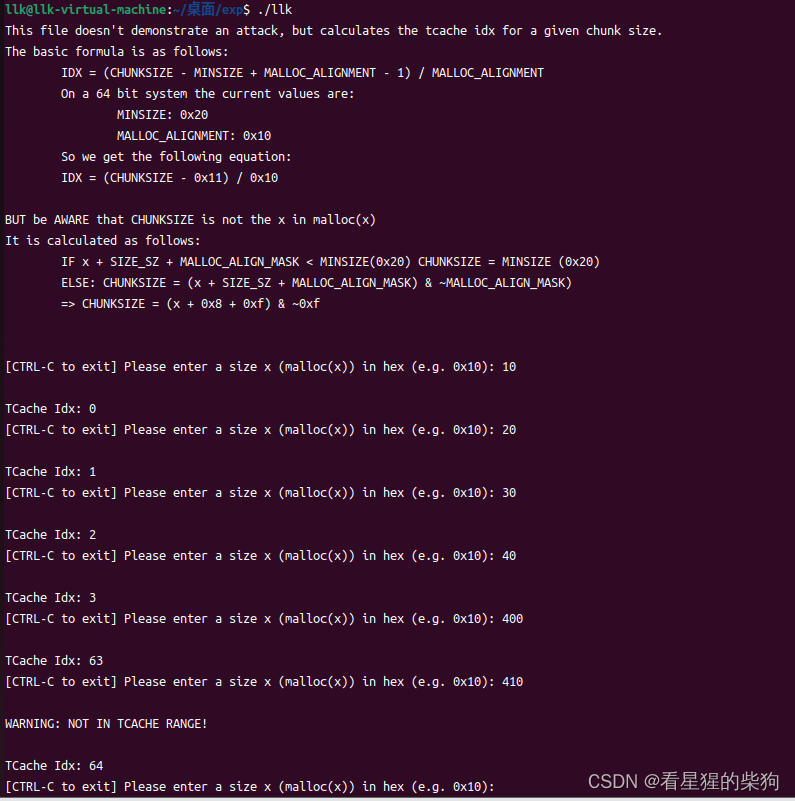
结果
可以发现以0x10递增,总共64个0x10























 1014
1014











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










