十、NAT穿越
部署IPSec VPN网络时,如果发起者位于一个私网内部,远端位于公网侧,而它希望与
远端响应者直接建立一条IPSec隧道。为保证存在NAT设备的IPSec隧道能够正常建立,
这就涉及到IPSec的NAT穿越问题

由于AH对数据进行的完整性检查会对包括IP地址在内的整个IP包进行Hash运算,而地址转换会改变IP地址,从而破坏AH的Hash值。因此使用AH的IPSec隧道无法穿越NAT设备。
ESP对数据进行的完整性检查不包括外部的IP头,若只进行地址转换时,ESP可以正常工作。但ESP是三层协议,无法设置端口,所以执行允许端口转换的NAT时ESP也存在问题。NAT穿越采用了增加UDP头封装ESP报文的方法解决这个问题。
传输模式下,NAT穿越在原报文的IP头和ESP头间增加一个标准的UDP报头;
隧道模式下,NAT穿越在新IP头和ESP头间增加一个标准的UDP报头。
这样,当ESP报文穿越NAT设备时,NAT设备对该报文的外层IP头和增加的UDP报头进行地址和端口号转换;转换后的报文到达IPSec隧道对端后,与普通IPSec处理方式相同。
NAT设备上的NAT会话表项有一定的存活时间,如果IPSec隧道建立后长时间没有报文进行NAT穿越,NAT设备会删除该NAT会话表项,这将导致在NAT设备外网侧的对等体无法继续传输数据。为防止NAT表项老化,NAT设备内网侧的IKESA会以一定的时间间隔向对端发送NAT Keepalive报文,以维持NAT会话的存活。
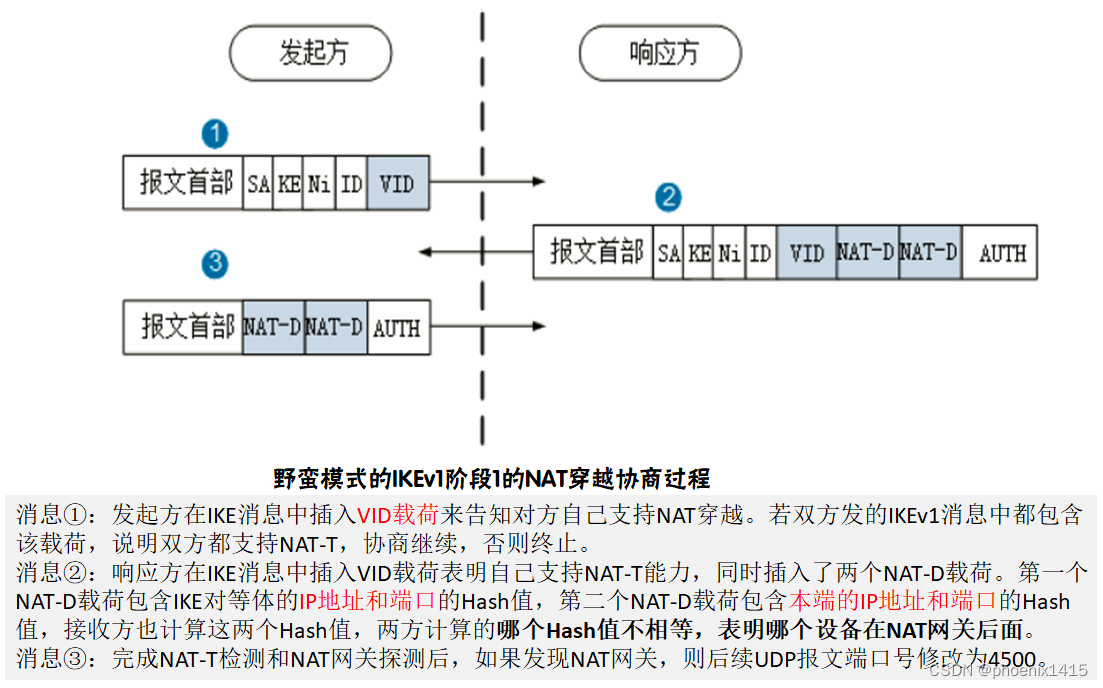
1、ikev1的NAT穿越-----阶段一必须使用野蛮模式
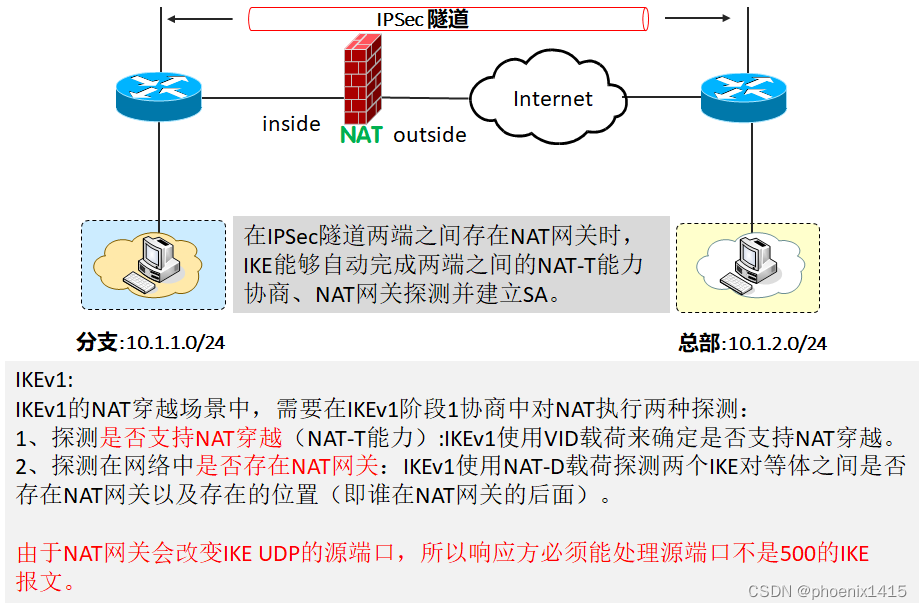
 2、ikev2的NAT穿越
2、ikev2的NAT穿越
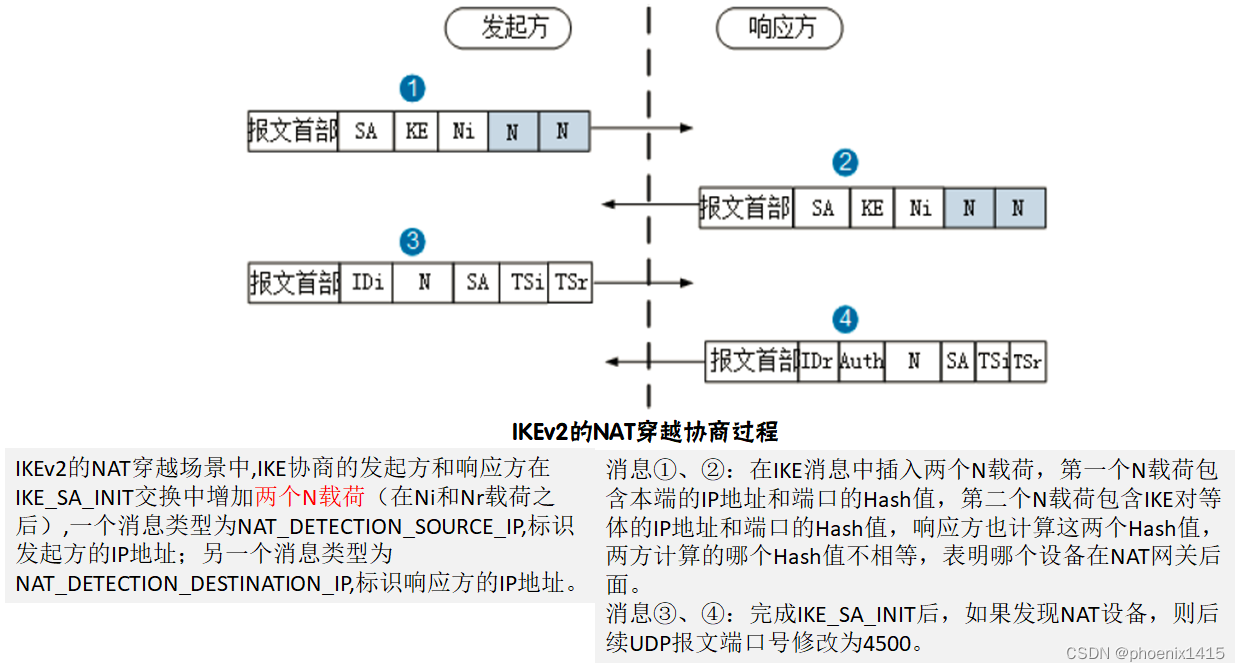
3、验证
A、无NAT,ikev1,查看NAT-T能力协商

ike peer ra v1
exchange-mode aggressive
pre-shared-key simple 123
ike-proposal 5
nat traversal
remote-address 2.1.1.1
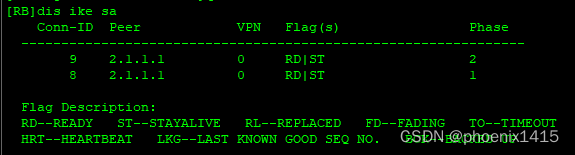
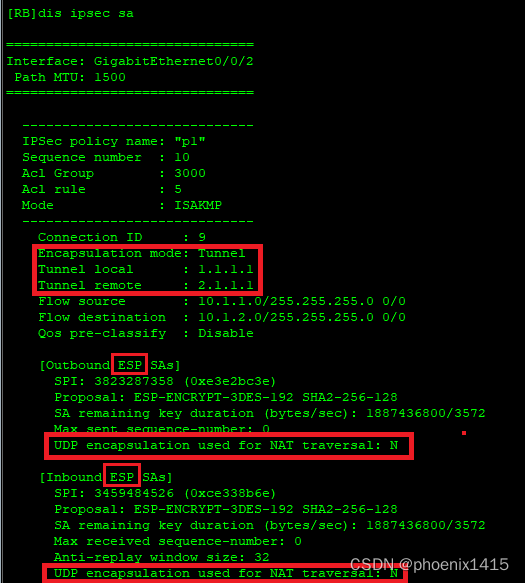
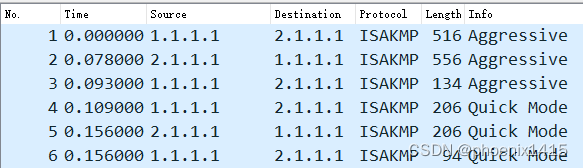
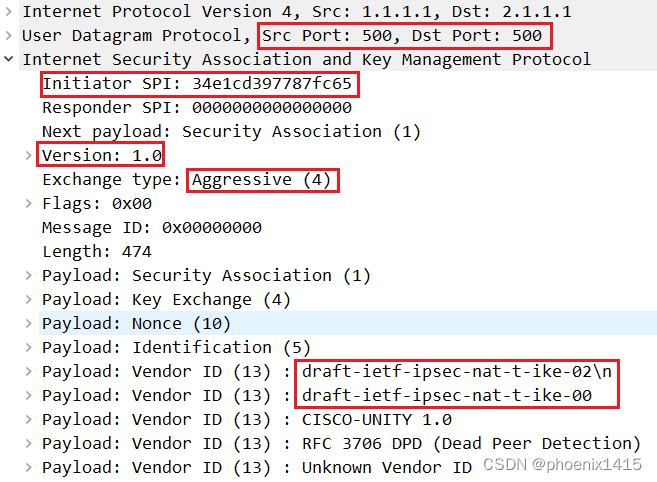
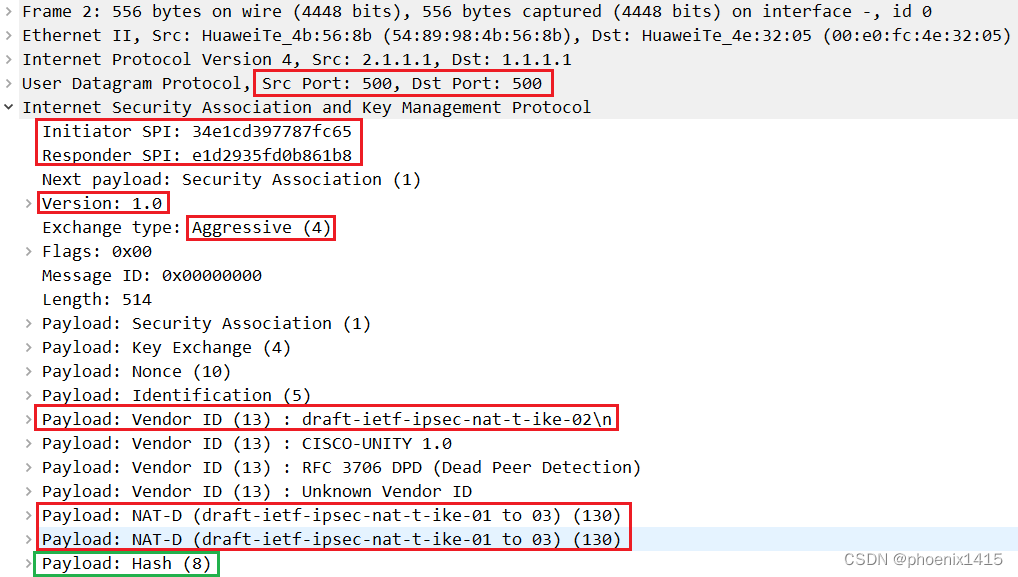
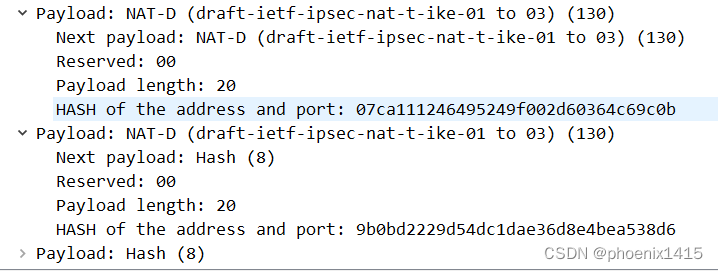
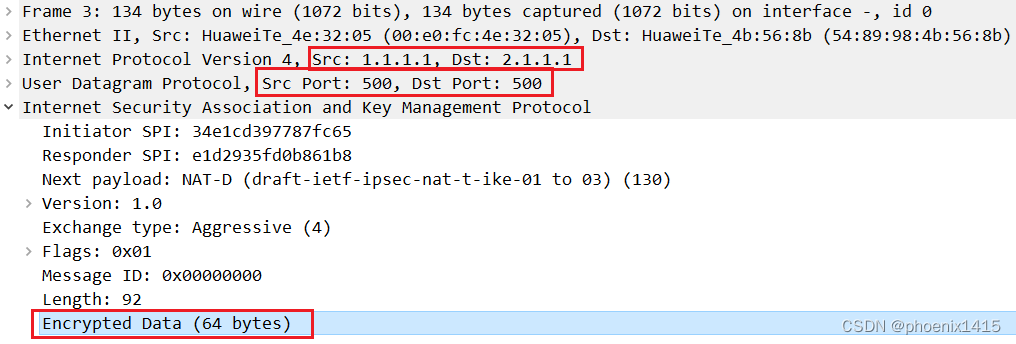 对等体之间还是用udp500进行isakmp消息的交互--------中间没有NAT设备。
对等体之间还是用udp500进行isakmp消息的交互--------中间没有NAT设备。
B、有NAT,ikev1,查看NAT-T能力协商
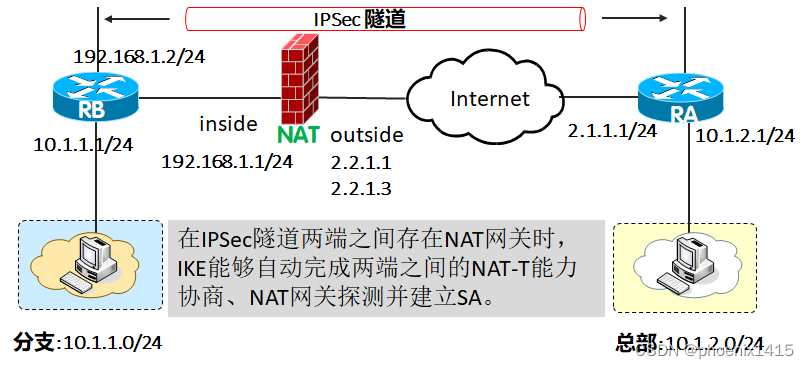
NAT:
acl 2000
rule 5 permit source 192.168.1.0 0.0.0.255
interface GigabitEthernet0/0/2
ip address 2.2.1.1 255.255.255.0
nat outbound 2000
nat static global 2.2.1.3 inside 192.168.1.2
#
ike local-name RB
ike peer ra v1
exchange-mode aggressive
pre-shared-key simple 123
ike-proposal 5
local-id-type name
remote-name RA
nat traversal
remote-address 2.1.1.1
#
ipsec policy p1 10 isakmp
security acl 3000
ike-peer ra
proposal pro1
#
ike local-name RA
ike peer rb v1
exchange-mode aggressive
pre-shared-key simple 123
ike-proposal 5
local-id-type name
remote-name RB
nat traversal
///RA使用模板,在此不需要指定remote-address
#
ipsec policy-template tmp1 10
ike-peer rb
proposal pro1
#
ipsec policy p1 10 isakmp template tmp1
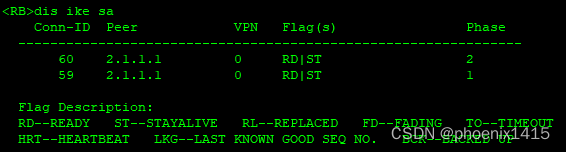
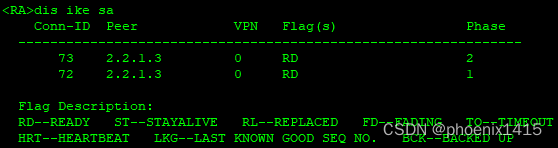
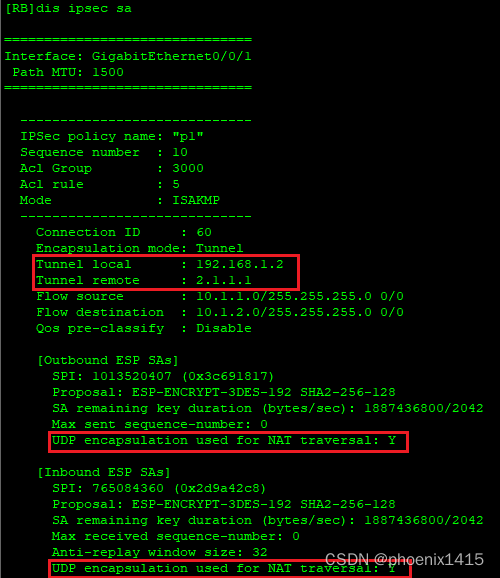
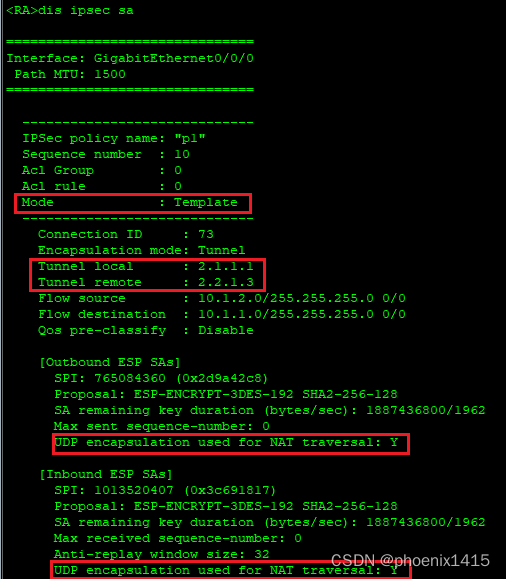
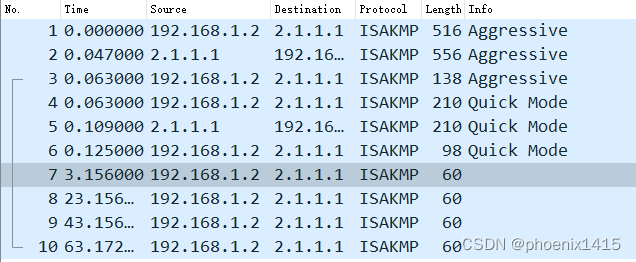
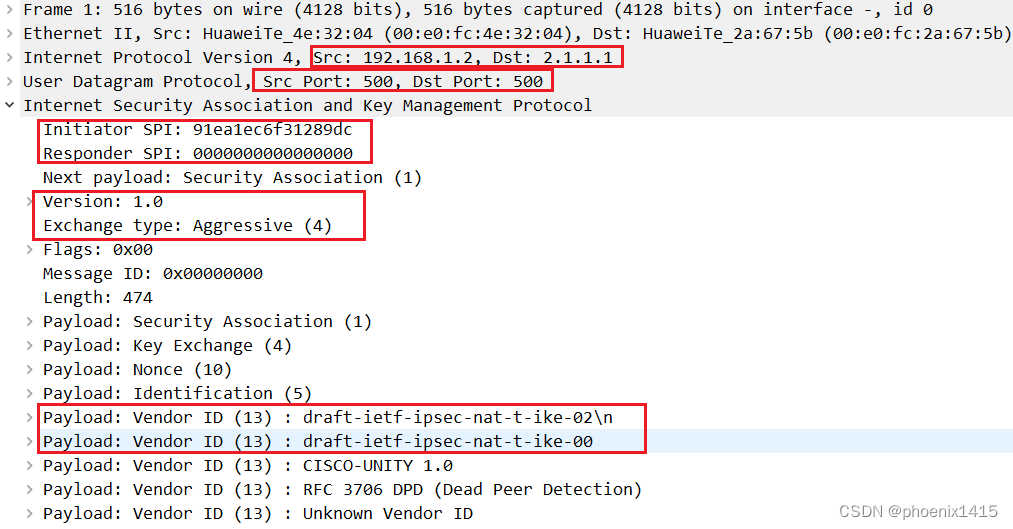
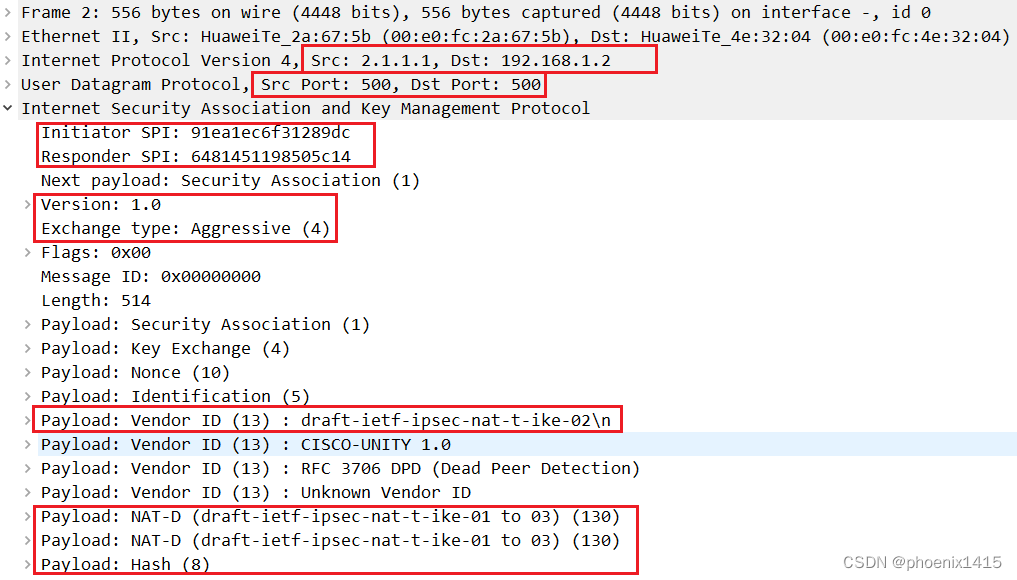

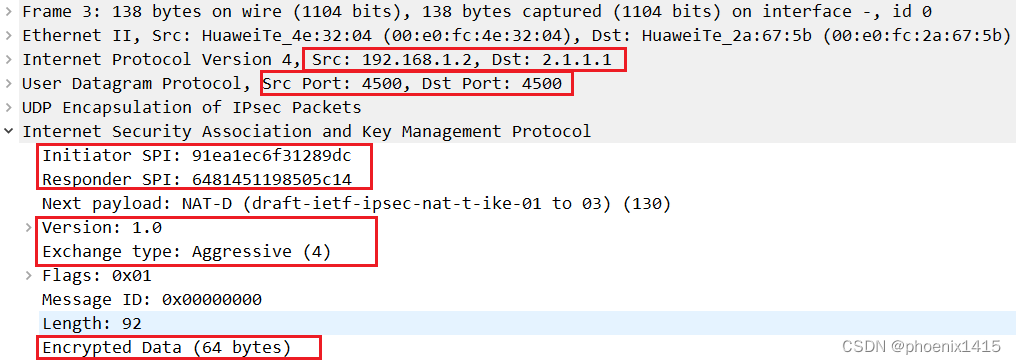
发现存在NAT设备后,端口号有500变成4500了
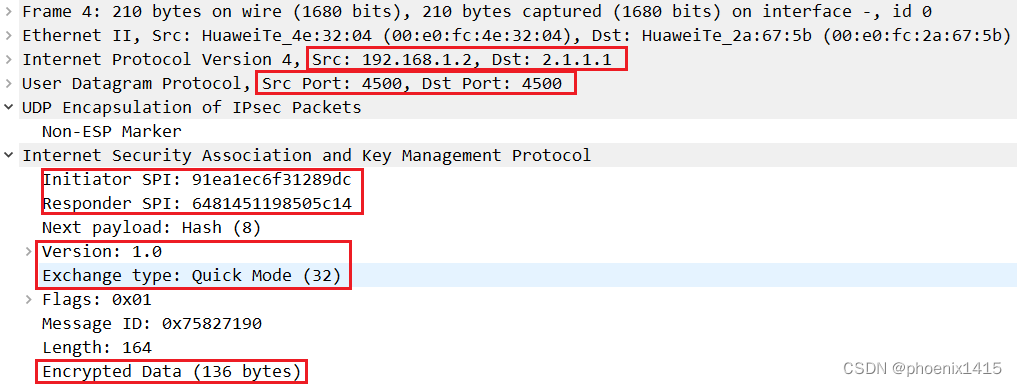
第二阶段快速模式的三条消息类似,不再赘述。
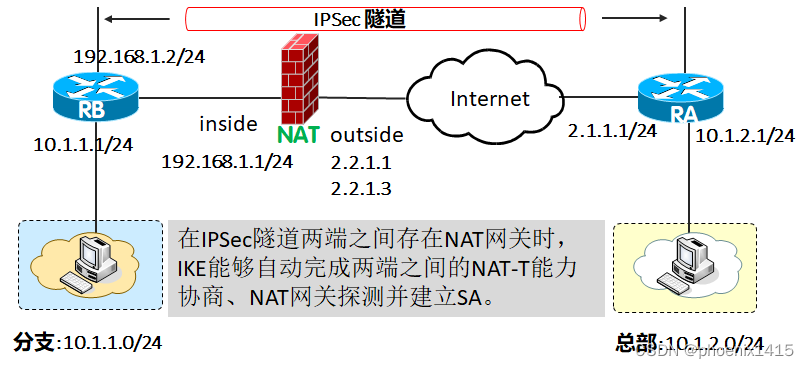
C、有NAT,ikev2,查看NAT-T能力协商
ike local-name RB
ike peer ra v2
pre-shared-key simple 123
ike-proposal 5
local-id-type name
remote-name RA
nat traversal
remote-address 2.1.1.1
#
ipsec policy p1 10 isakmp
security acl 3000
ike-peer ra
proposal pro1
#
ike local-name RA
ike peer rb v2
pre-shared-key simple 123
ike-proposal 5
local-id-type name
remote-name RB
nat traversal
#
ipsec policy-template tmp1 10
ike-peer rb
proposal pro1
#
ipsec policy p1 10 isakmp template tmp1

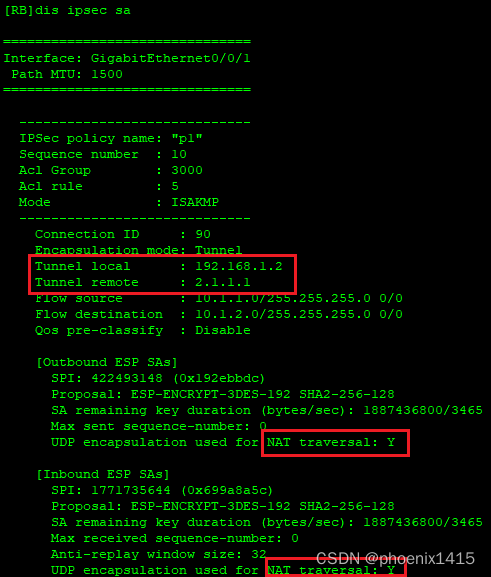
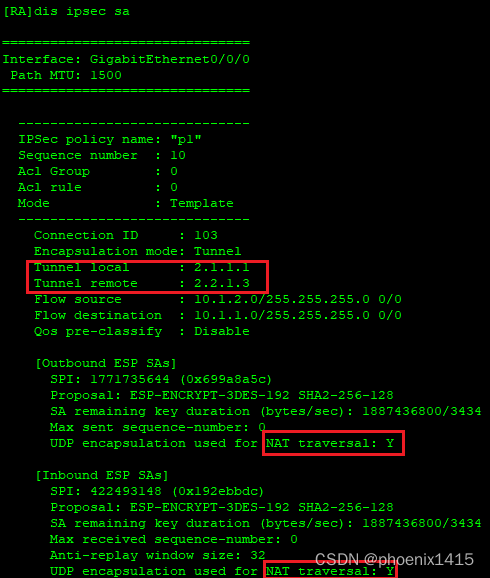
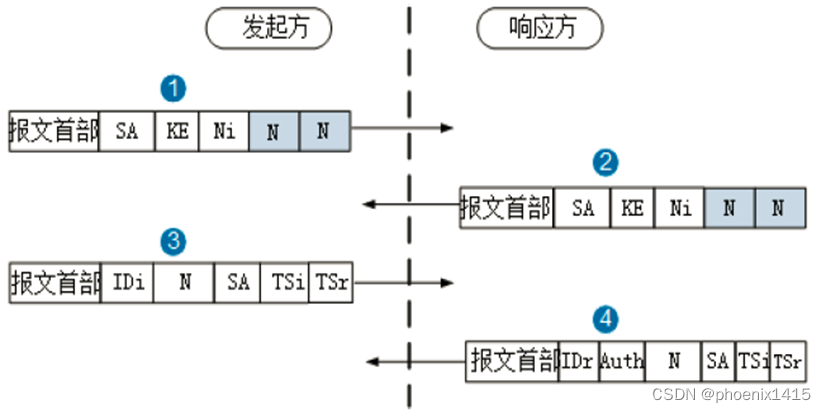
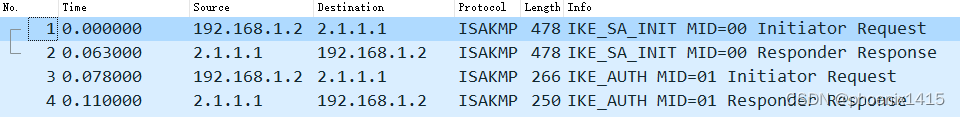
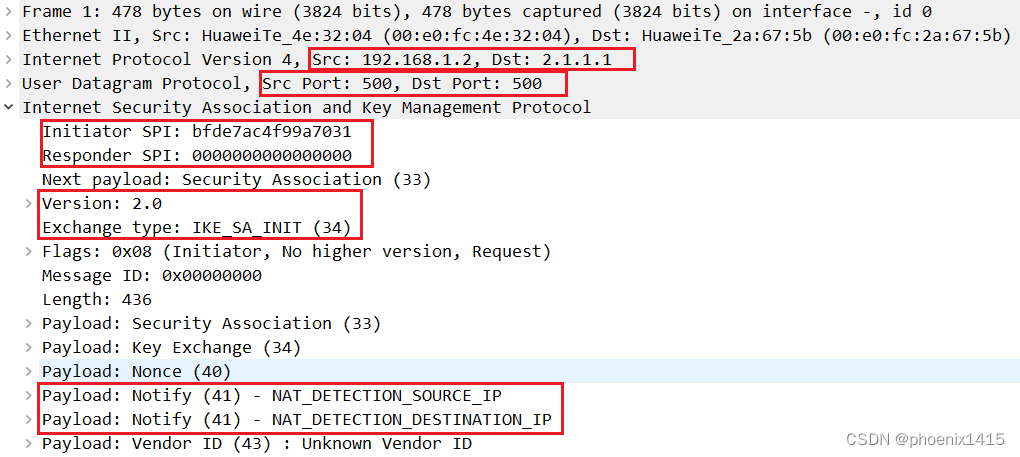
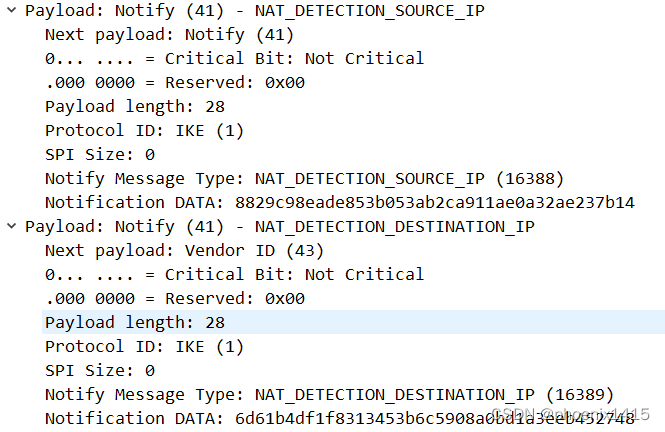
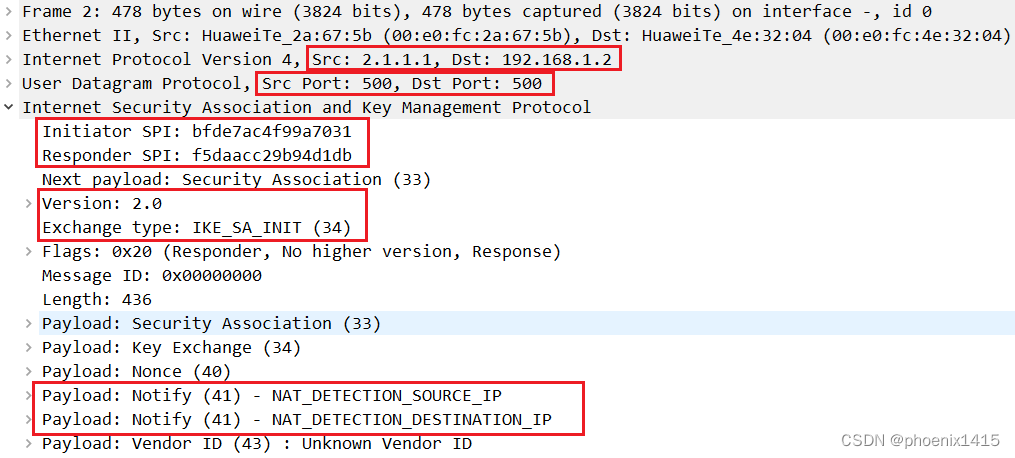

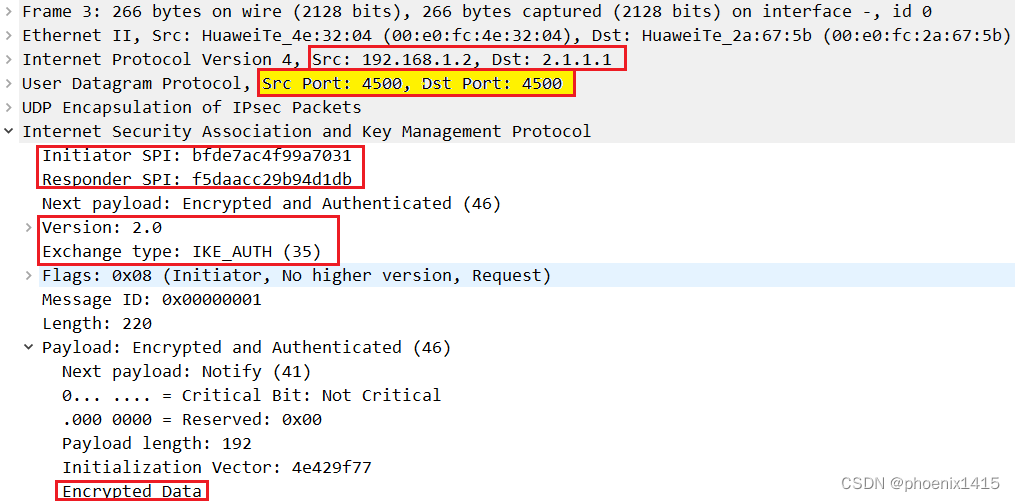
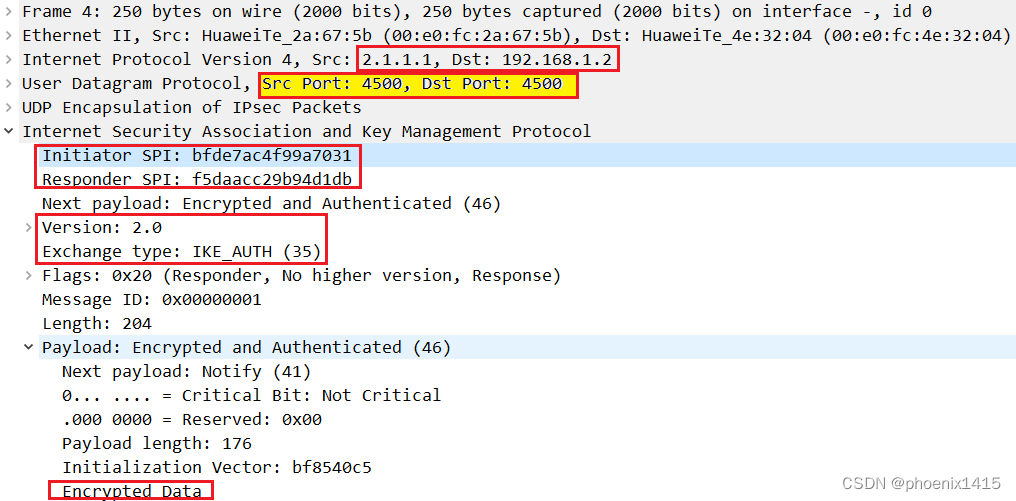
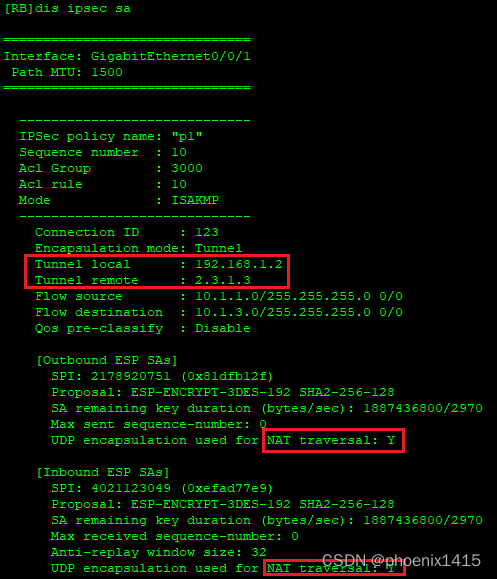
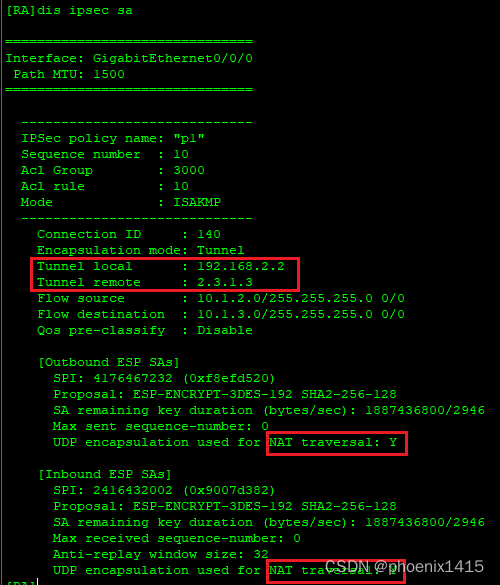
D、发起者和响应者都在NAT内部,ikev2,查看NAT-T能力协商
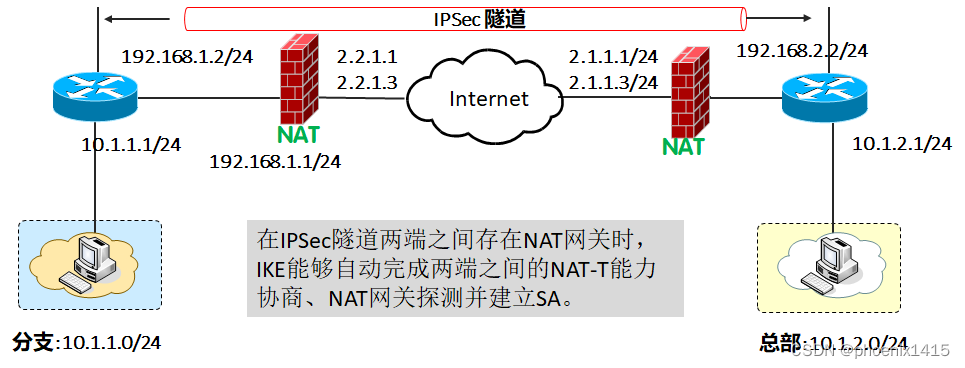
NAT1:
nat static global 2.2.1.3 inside 192.168.1.2 netmask 255.255.255.255
NAT2:
nat static global 2.1.1.3 inside 192.168.2.2 netmask 255.255.255.255
#
ike local-name RB
ike peer ra v2
pre-shared-key simple 123
ike-proposal 5
local-id-type name
remote-name RA
nat traversal
remote-address 2.1.1.3
#
ipsec policy p1 10 isakmp
security acl 3000
ike-peer ra
proposal pro1
#
ike local-name RA
ike peer rb v2
pre-shared-key simple 123
ike-proposal 5
local-id-type name
remote-name RB
nat traversal
remote-address 2.2.1.3
#
ipsec policy p1 10 isakmp
security acl 3000
ike-peer ra
proposal pro1
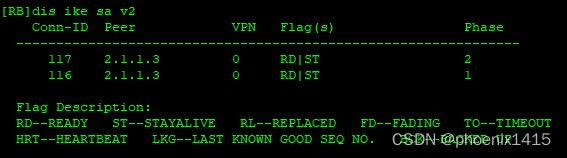
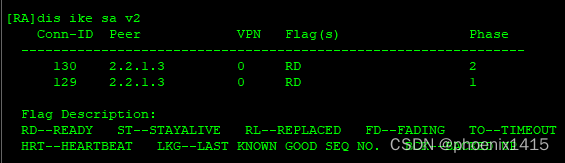
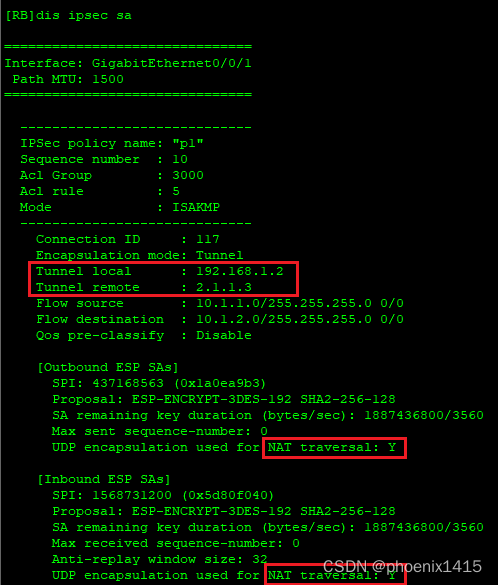
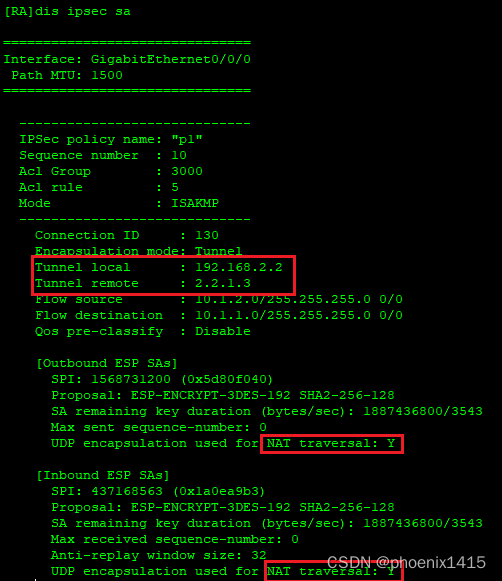
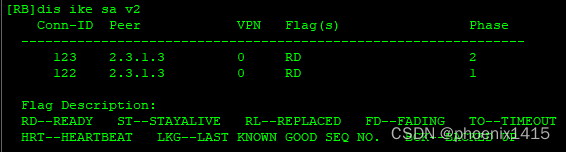
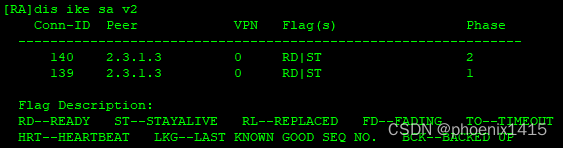
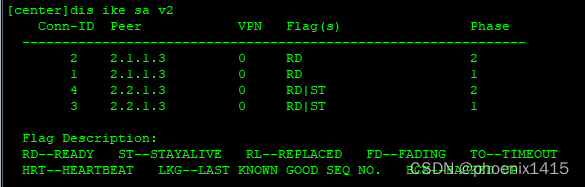
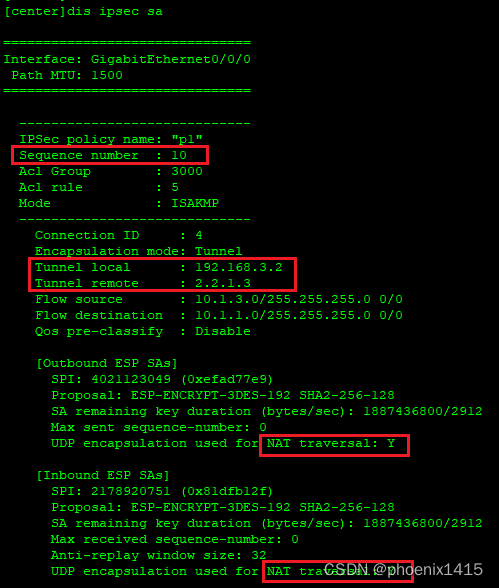
E、点到多点,ikev2,查看NAT-T能力协商
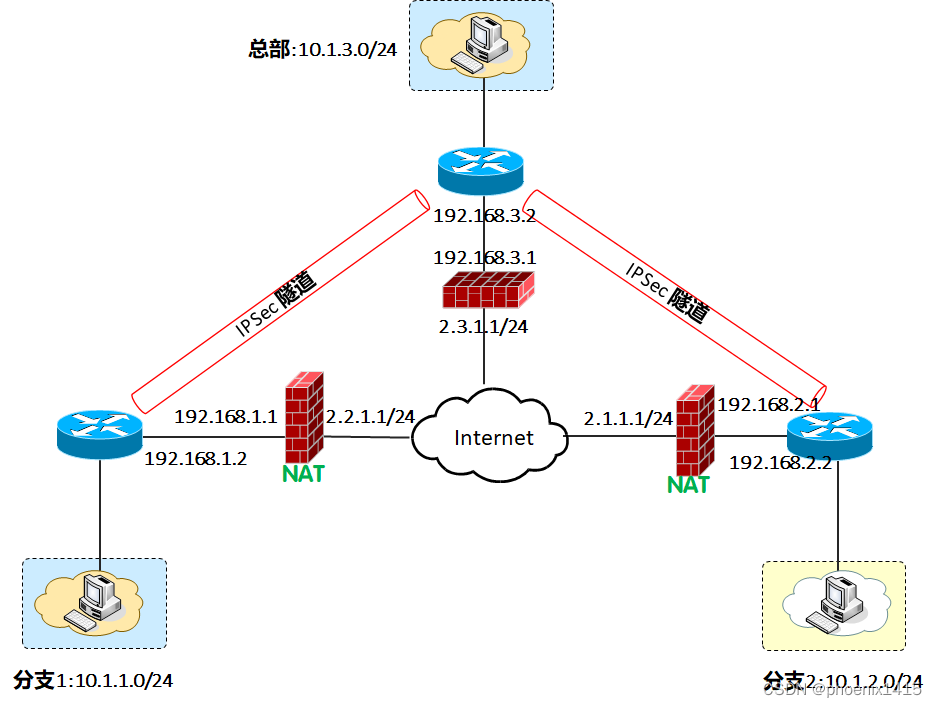
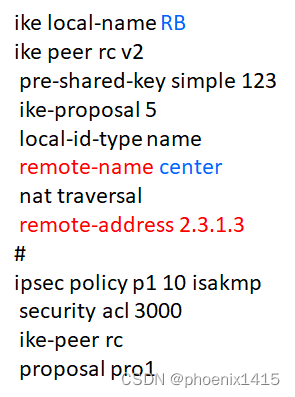
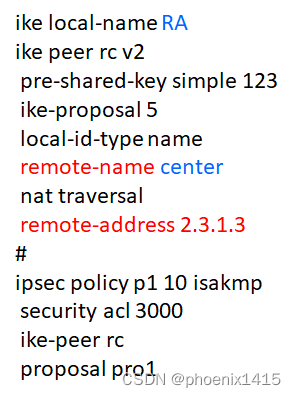
ike local-name center
#
ike peer ra v2
pre-shared-key simple 123
ike-proposal 5
local-id-type name
remote-name RA
nat traversal
remote-address 2.1.1.3
#
ike peer rb v2
pre-shared-key simple 123
ike-proposal 5
local-id-type name
remote-name RB
nat traversal
remote-address 2.2.1.3
#
ipsec policy p1 10 isakmp
security acl 3000
ike-peer ra
proposal pro1
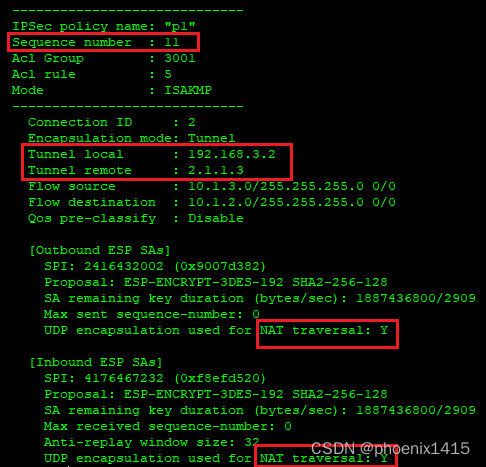
ipsec policy p1 11 isakmp
security acl 3001
ike-peer rb
proposal pro1
十一、ike debugging信息
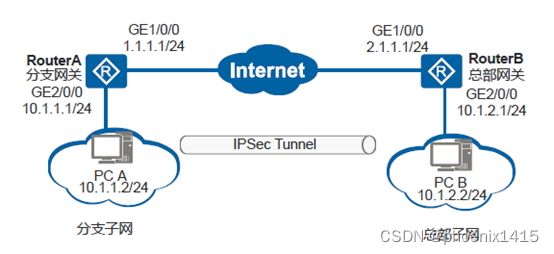
ikev1-主模式
ike peer RB v1
pre-shared-key simple 123
ike-proposal 5
remote-address 2.1.1.1
ike peer RA v1
pre-shared-key simple 123
ike-proposal 5
remote-address 1.1.1.1
发起方:
<RA>debugging ike packet
[RA]int g1/0/0
[RA-GigabitEthernet1/0/0]ipsec policy p1
阶段一:主模式
//发起方:发送封装有IKE安全提议的SA载荷给响应方进行安全提议协商。
17:4541 IKE Packet Contents sent to 2.1.1.1 for message type Send_SA : fe93c458
1b9a1369 00000000 00000000 01100200 00000000 0000007c 0d000038 00000001 00000001
0000002c 01010001 00000024 00010000 80010005 80020001 80030001 8004000e 800b000
1 000c0004 00015180 0d000014 afcad713 68a1f1c9 6b8696fc 77570100 00000014 485541
57 45492d49 4b457631 44534350
//发起方:接收到响应方发送的确认SA载荷。
17:4368 IKE Packet Contents received from 2.1.1.1 for message type Recv_SA : fe9
3c458 1b9a1369 5786584d 9ca9e1d9 01100200 00000000 0000007c 0d000038 00000001 00
000001 0000002c 01010001 00000024 00010000 80010005 80020001 80030001 8004000e 8
00b0001 000c0004 00015180 0d000014 afcad713 68a1f1c9 6b8696fc 77570100 00000014
48554157 45492d49 4b457631 44534350
//发起方:发送封装有密钥生成信息的KE_NONCE载荷给响应方,用来交换DH公开值和临时随机数。
17:4541 IKE Packet Contents sent to 2.1.1.1 for message type Send_KE_NONCE : fe9
3c458 1b9a1369 5786584d 9ca9e1d9 04100200 00000000 00000134 0a000104 00000000 00
000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0
0000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000
0 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000000
00 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000
000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000
0002 00000014 6e236d65 162cbd89 965ca3ac 42010926
//发起方:接收到响应方发送的KE_NONCE载荷。
17:4368 IKE Packet Contents received from 2.1.1.1 for message type Recv_KE_NONCE
: fe93c458 1b9a1369 5786584d 9ca9e1d9 04100200 00000000 00000134 0a000104 00000
000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000
0000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000
00000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00
000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0
0000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000
0 00000002 00000014 98a063f2 492b932a 88228773 d5ab39bc
//发起方:发送封装有身份ID和验证数据Hash信息的ID_AUTH载荷给响应方。
17:4541 IKE Packet Contents sent to 2.1.1.1 for message type Send_ID_AUTH : fe93
c458 1b9a1369 5786584d 9ca9e1d9 05100200 00000000 0000003c 0800000c 01000000 010
10101 00000014 de9b1b76 8481da2b b3cd50c3 4731b3a1
//发起方:接收到响应方发送的ID_AUTH载荷。
17:4368 IKE Packet Contents received from 2.1.1.1 for message type Recv_ID_AUTH
: fe93c458 1b9a1369 5786584d 9ca9e1d9 05100201 00000000 0000003c 0800000c 010000
00 02010101 00000014 71aa1f80 4f6c2433 5ab1a577 33b831f9
阶段二:快速模式
//发起方:发送封装有IPSec安全提议、身份和验证数据的HASH_SA_NONCE载荷给响应方。
17:4541 IKE Packet Contents sent to 2.1.1.1 for message type Send_HASH_SA_NONCE
: fe93c458 1b9a1369 5786584d 9ca9e1d9 08102000 362d58e3 000000d8 01000014 c26b6a
d1 56570f44 35d754da 30e1ca51 0a000074 00000001 00000001 02000034 01020401 3f89f
da1 00000028 01030000 80010001 00020004 00000e10 80010002 00020004 001c2000 8004
0001 80050002 00000034 01030401 426e62d8 00000028 01030000 80010001 00020004 000
00e10 80010002 00020004 001c2000 80040001 80050002 05000014 134561d2 b67d83b3 68
16971a c25e6c8c 05000010 04000000 0a010100 ffffff00 00000010 04000000 0a010200 f
fffff00
//发起方:接收到响应方发送的HASH_SA_NONCE载荷。
17:4368 IKE Packet Contents received from 2.1.1.1 for message type Recv_HASH_SA_
NONCE : fe93c458 1b9a1369 5786584d 9ca9e1d9 08102001 362d58e3 000000d8 01000014
048f96d1 086f2247 2428562e 058ae914 0a000074 00000001 00000001 02000034 01020401
5dbefc0c 00000028 01030000 80010001 00020004 00000e10 80010002 00020004 001c200
0 80040001 80050002 00000034 01030401 db9d811b 00000028 01030000 80010001 000200
04 00000e10 80010002 00020004 001c2000 80040001 80050002 05000014 05a5e854 a7bb7
748 2979675b 3beaa8d8 05000010 04000000 0a010100 ffffff00 00000010 04000000 0a01
0200 ffffff00 00000000
//发起方:发送封装有验证数据的HASH载荷给响应方。
17:4541 IKE Packet Contents sent to 2.1.1.1 for message type Send_HASH : fe93c45
8 1b9a1369 5786584d 9ca9e1d9 08102000 362d58e3 00000030 00000014 3816aa45 d37b24
25 9adff1f7 8615293f
<RA>undo deb all
Info: All possible debugging has been turned off
响应方:
阶段一:主模式
<RB>debugging ike pa
//响应方:接收到发起方发送的SA载荷
17:4368 IKE Packet Contents received from 1.1.1.1 for message type Recv_SA : 6c3
bb652 c996ee22 00000000 00000000 01100200 00000000 0000007c 0d000038 00000001 00
000001 0000002c 01010001 00000024 00010000 80010005 80020001 80030001 8004000e 8
00b0001 000c0004 00015180 0d000014 afcad713 68a1f1c9 6b8696fc 77570100 00000014
48554157 45492d49 4b457631 44534350
//响应方:查找最先匹配的IKE安全提议,发送一个SA载荷,表明接受协商的IKE安全提议。
17:4541 IKE Packet Contents sent to 1.1.1.1 for message type Send_SA : 6c3bb652
c996ee22 8baab549 3795d7c2 01100200 00000000 0000007c 0d000038 00000001 00000001
0000002c 01010001 00000024 00010000 80010005 80020001 80030001 8004000e 800b000
1 000c0004 00015180 0d000014 afcad713 68a1f1c9 6b8696fc 77570100 00000014 485541
57 45492d49 4b457631 44534350
//响应方:接收到发起方发送的KE_NONCE载荷。
17:4368 IKE Packet Contents received from 1.1.1.1 for message type Recv_KE_NONCE
: 6c3bb652 c996ee22 8baab549 3795d7c2 04100200 00000000 00000134 0a000104 00000
000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000
0000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000
00000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00
000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0
0000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000
0 00000002 00000014 8ef8f7fd 509aa71f b5ca59b3 94e0b118
//响应方:发送封装有密钥生成信息的KE_NONCE载荷给发起方,用来交换DH公开值和临时随机数。
17:4541 IKE Packet Contents sent to 1.1.1.1 for message type Send_KE_NONCE : 6c3
bb652 c996ee22 8baab549 3795d7c2 04100200 00000000 00000134 0a000104 00000000 00
000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0
0000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000
0 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000000
00 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000
000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000
0002 00000014 00a0549e 4d0b575b 2dfea57f 4fc6a8cb
//响应方:接收到发起方发送的ID_AUTH载荷。
17:4368 IKE Packet Contents received from 1.1.1.1 for message type Recv_ID_AUTH
: 6c3bb652 c996ee22 8baab549 3795d7c2 05100201 00000000 0000003c 0800000c 010000
00 01010101 00000014 85401aca 615c0f4e faa9e0e2 d221c1d7
//响应方:发送封装有身份ID和验证数据Hash信息的ID_AUTH载荷给发起方。
17:4541 IKE Packet Contents sent to 1.1.1.1 for message type Send_ID_AUTH : 6c3b
b652 c996ee22 8baab549 3795d7c2 05100200 00000000 0000003c 0800000c 01000000 020
10101 00000014 93d0493e 9c606c0f f52bf4a5 fb87aaa4
阶段二:快速模式
//响应方:接收到发起方发送的HASH_SA_NONCE载荷
17:4368 IKE Packet Contents received from 1.1.1.1 for message type Recv_HASH_SA_
NONCE : 6c3bb652 c996ee22 8baab549 3795d7c2 08102001 283d8403 000000d8 01000014
e7e1cd41 5f1cd19a 5dcb106c 30423d2d 0a000074 00000001 00000001 02000034 01020401
730a5852 00000028 01030000 80010001 00020004 00000e10 80010002 00020004 001c200
0 80040001 80050002 00000034 01030401 081e09ad 00000028 01030000 80010001 000200
04 00000e10 80010002 00020004 001c2000 80040001 80050002 05000014 b90dc106 8f130
2cd f275df78 def1cea6 05000010 04000000 0a010100 ffffff00 00000010 04000000 0a01
0200 ffffff00 00000000
//响应方:查找最先匹配的IPSec安全提议,发送封装有IPSec安全提议、身份信息和验证数据的HASH_SA_NONCE载荷给发起方。
17:4541 IKE Packet Contents sent to 1.1.1.1 for message type Send_HASH_SA_NONCE
: 6c3bb652 c996ee22 8baab549 3795d7c2 08102000 283d8403 000000d8 01000014 802808
05 b0010953 a04481c8 a3cd587f 0a000074 00000001 00000001 02000034 01020401 3eca2
389 00000028 01030000 80010001 00020004 00000e10 80010002 00020004 001c2000 8004
0001 80050002 00000034 01030401 5669bbd9 00000028 01030000 80010001 00020004 000
00e10 80010002 00020004 001c2000 80040001 80050002 05000014 4dcca0e8 da96ef12 7d
48540e 988ff945 05000010 04000000 0a010100 ffffff00 00000010 04000000 0a010200 f
fffff00
//响应方:接收到发起方发送的HASH载荷。
17:4368 IKE Packet Contents received from 1.1.1.1 for message type Recv_HASH : 6
c3bb652 c996ee22 8baab549 3795d7c2 08102001 283d8403 00000030 00000014 53e91c1e
82a0c23f 09aab56f 0c7397f5 00000000
ikev1-野蛮模式
ike peer RB v1
exchange-mode aggressive
pre-shared-key simple 123
ike-proposal 5
remote-address 2.1.1.1
ike peer RA v1
exchange-mode aggressive
pre-shared-key simple 123
ike-proposal 5
remote-address 1.1.1.1
发起方:
阶段一:野蛮模式
//发起方:发送封装有IKE安全提议、密钥生成信息和身份信息的SA_KE_NONCE_ID_VID载荷给响应方。
IKE Packet Contents sent to 2.1.1.1 for message type Send_SA_KE_NONCE_ID_VID : c
8b156d0 64fa6faa 00000000 00000000 01100400 00000000 000001b4 04000038 00000001
00000001 0000002c 01010001 00000024 00010000 80010005 80020001 80030001 8004000e
800b0001 000c0004 00015180 0a000104 00000000 00000000 00000000 00000000 0000000
0 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000000
00 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000
000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000
0000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000
00000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00
000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0
0000000 00000000 00000000 00000000 00000000 000000
//发起方:接收到响应方发送的SA_KE_NONCE_ID_VID_NATD_AUTH载荷。
IKE Packet Contents received from 2.1.1.1 for message type Recv_SA_KE_NONCE_ID_V
ID_NATD_AUTH : c8b156d0 64fa6faa a09c5057 0dbd0398 01100400 00000000 000001c8 04
000038 00000001 00000001 0000002c 01010001 00000024 00010000 80010005 80020001 8
0030001 8004000e 800b0001 000c0004 00015180 0a000104 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000
0 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000000
00 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000
000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000
0000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000
00000 00000000 00000000 00000000 00000000 00000000
//发起方:发送封装有验证数据的NATD_AUTH载荷给响应方。
17:4541 IKE Packet Contents sent to 2.1.1.1 for message type Send_NATD_AUTH : c8
b156d0 64fa6faa a09c5057 0dbd0398 08100400 00000000 00000030 00000014 23b8f887 a
97f0aec aff83601 2054c5a1
阶段二:快速模式
//发起方:发送封装有IPSec安全提议、身份和验证数据的HASH_SA_NONCE载荷给响应方。
17:4541 IKE Packet Contents sent to 2.1.1.1 for message type Send_HASH_SA_NONCE
: c8b156d0 64fa6faa a09c5057 0dbd0398 08102000 108afd46 000000d8 01000014 a1f0b8
8b 5047ba5b d6824abb b6ca6749 0a000074 00000001 00000001 02000034 01020401 43003
6ad 00000028 01030000 80010001 00020004 00000e10 80010002 00020004 001c2000 8004
0001 80050002 00000034 01030401 83767ea7 00000028 01030000 80010001 00020004 000
00e10 80010002 00020004 001c2000 80040001 80050002 05000014 43f2e401 df089534 89
51939e da527549 05000010 04000000 0a010100 ffffff00 00000010 04000000 0a010200 f
fffff00
//发起方:接收到响应方发送的HASH_SA_NONCE载荷。
17:4368 IKE Packet Contents received from 2.1.1.1 for message type Recv_HASH_SA_
NONCE : c8b156d0 64fa6faa a09c5057 0dbd0398 08102001 108afd46 000000d8 01000014
2ca0d6a4 e03fabb8 dbda131a 35425074 0a000074 00000001 00000001 02000034 01020401
a676eb1e 00000028 01030000 80010001 00020004 00000e10 80010002 00020004 001c200
0 80040001 80050002 00000034 01030401 6d3f5013 00000028 01030000 80010001 000200
04 00000e10 80010002 00020004 001c2000 80040001 80050002 05000014 909c0b8f e6112
d6e 0e42a00e be4ccb9b 05000010 04000000 0a010100 ffffff00 00000010 04000000 0a01
0200 ffffff00 00000000
//发起方:发送封装有验证数据的HASH载荷给响应方。
17:4541 IKE Packet Contents sent to 2.1.1.1 for message type Send_HASH : c8b156d
0 64fa6faa a09c5057 0dbd0398 08102000 108afd46 00000030 00000014 eefa7d52 371f20
73 283ed8d3 e656d588
<RA>undo debugging all
Info: All possible debugging has been turned off
响应方:
阶段一:野蛮模式
//响应方:接收到发起方发送的SA_KE_NONCE_ID_VID载荷,
IKE Packet Contents received from 1.1.1.1 for message type Recv_SA_KE_NONCE_ID_V
ID : c8b156d0 64fa6faa 00000000 00000000 01100400 00000000 000001b4 04000038 000
00001 00000001 0000002c 01010001 00000024 00010000 80010005 80020001 80030001 80
04000e 800b0001 000c0004 00015180 0a000104 00000000 00000000 00000000 00000000 0
0000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000000
0 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000000
00 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000
000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000
0000 00000000 00000000 00000000 00000000 00000000
//响应方:查找最先匹配的IKE安全提议,发送封装有IKE安全提议、密钥生成信息、身份信息和验证数据的SA_KE_NONCE_ID_VID_NATD_AUTH载荷给发起方。
IKE Packet Contents sent to 1.1.1.1 for message type Send_SA_KE_NONCE_ID_VID_NAT
D_AUTH : c8b156d0 64fa6faa a09c5057 0dbd0398 01100400 00000000 000001c8 04000038
00000001 00000001 0000002c 01010001 00000024 00010000 80010005 80020001 8003000
1 8004000e 800b0001 000c0004 00015180 0a000104 00000000 00000000 00000000 000000
00 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000
000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0000
0000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 000
00000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00
000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 0
0000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
00000000 00000000 00000000 00000000 00000000 00000
//响应方:接收到发起方发送的NATD_AUTH载荷。
17:4368 IKE Packet Contents received from 1.1.1.1 for message type Responder_rec
v_NATD_AUTH : c8b156d0 64fa6faa a09c5057 0dbd0398 08100401 00000000 00000030 000
00014 23b8f887 a97f0aec aff83601 2054c5a1 00000000
阶段二:快速模式
//响应方:接收到发起方发送的HASH_SA_NONCE载荷,
17:4368 IKE Packet Contents received from 1.1.1.1 for message type Recv_HASH_SA_
NONCE : c8b156d0 64fa6faa a09c5057 0dbd0398 08102001 108afd46 000000d8 01000014
a1f0b88b 5047ba5b d6824abb b6ca6749 0a000074 00000001 00000001 02000034 01020401
430036ad 00000028 01030000 80010001 00020004 00000e10 80010002 00020004 001c200
0 80040001 80050002 00000034 01030401 83767ea7 00000028 01030000 80010001 000200
04 00000e10 80010002 00020004 001c2000 80040001 80050002 05000014 43f2e401 df089
534 8951939e da527549 05000010 04000000 0a010100 ffffff00 00000010 04000000 0a01
0200 ffffff00 00000000
//响应方:查找最先匹配的IPSec安全提议,发送封装有IPSec安全提议、身份信息和验证数据的HASH_SA_NONCE载荷给发起方。
17:4541 IKE Packet Contents sent to 1.1.1.1 for message type Send_HASH_SA_NONCE
: c8b156d0 64fa6faa a09c5057 0dbd0398 08102000 108afd46 000000d8 01000014 2ca0d6
a4 e03fabb8 dbda131a 35425074 0a000074 00000001 00000001 02000034 01020401 a676e
b1e 00000028 01030000 80010001 00020004 00000e10 80010002 00020004 001c2000 8004
0001 80050002 00000034 01030401 6d3f5013 00000028 01030000 80010001 00020004 000
00e10 80010002 00020004 001c2000 80040001 80050002 05000014 909c0b8f e6112d6e 0e
42a00e be4ccb9b 05000010 04000000 0a010100 ffffff00 00000010 04000000 0a010200 f
fffff00
//响应方:接收到发起方发送的HASH载荷。
17:4368 IKE Packet Contents received from 1.1.1.1 for message type Recv_HASH : c
8b156d0 64fa6faa a09c5057 0dbd0398 08102001 108afd46 00000030 00000014 eefa7d52
371f2073 283ed8d3 e656d588 00000000
<RB>undo debugging all
Info: All possible debugging has been turned off
ikev2
ike peer RB v2
pre-shared-key simple 123
ike-proposal 5
remote-address 2.1.1.1
ike peer RA v2
pre-shared-key simple 123
ike-proposal 5
remote-address 1.1.1.1
发起方:
//发起方:发送封装有IKE安全提议、密钥生成信息和验证数据的SA_INIT载荷给响应方。
42:6403 IKEv2 Exch Type: SA_INIT
42:6313 Sent Msg: SA | KE | NONCE | V_ID |
//发起方:接收到响应方发送的SA_INITE载荷。
42:6362 IKEv2 Exch Type: SA_INIT
42:6265 Recv Msg: SA | KE | NONCE | V_ID |
//发起方:发送封装有IPSec安全提议、身份信息和验证数据的IKE_AUTH载荷给响应方。
42:6403 IKEv2 Exch Type: IKE_AUTH
42:6313 Sent Msg: NOTIFY | NOTIFY | NOTIFY | ID_I | ID_R | AUTH | SA | TS_I | TS_R |
发起方:接收到响应方发送的IKE_AUTH载荷。
42:6362 IKEv2 Exch Type: IKE_AUTH
42:6265 Recv Msg: NOTIFY | NOTIFY | ID_R | AUTH | SA | TS_I | TS_R |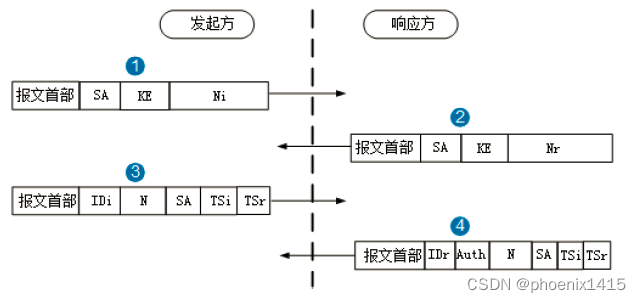
响应方:
//响应方:接收到发起方发送的SA INIT载荷
42:6362 IKEv2 Exch Type: SA_INIT
42:6265 Recv Msg: SA | KE | NONCE | V_ID |
//响应方:查找最先匹配的IKE安全提议,发送封装有IKE安全提议、身份信息和验证数据的SA_INIT载荷给发起方。
42:6403 IKEv2 Exch Type: SA_INIT
42:6313 Sent Msg: SA | KE | NONCE | V_ID |
//响应方:接收到发起方发送的IKE_AUTH
42:6362 IKEv2 Exch Type: IKE_AUTH
42:6265 Recv Msg: NOTIFY | NOTIFY | NOTIFY | ID_I | ID_R | AUTH | SA | TS_I | TS_R |
//响应方:查找最先匹配的IPSec安全提议,发送封装有IPSec安全提议、身份信息和验证数据的IKE_AUTH载荷给发起方。
42:6403 IKEv2 Exch Type: IKE_AUTH
42:6313 Sent Msg: NOTIFY | NOTIFY | ID_R | AUTH | SA | TS_I | TS_R |






















 8537
8537











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








