TDA4VH HS Development
HS设备类型
HS-FS
High Security - Field Securable Device type before customer keys are programmed (the state in which the device leaves TI factory). In this state, device protects the ROM code, TI keys and certain security peripherals. HS-FS devices do not enforce secure boot process.
- M3 JTAG port is closed, R5 JTAG port is open.
- DMSC Firewalls are closed, SOC Firewalls are open
- Board configuration need not be signed
- ROM Boot expects a TI signed binary (encryption is optional).
- System Firmware binary is signed by the TI Private key (TI MPK).(Refer Signing an unencrypted binary for secure boot for more details).
HS-SE
High Security – Security Enforced Device type after customer keys are programmed. HS-SE devices enforce secure boot.
- M3, R5 JTAG ports are both closed.
- DMSC, SOC Firewalls are both closed.
- Board configuration needs to be signed with active customer private key (SMPK/BMPK).
- ROM Boot expects a dual signed, encrypted system firmware binary.
- System Firmware binary is encrypted by the TI Encryption key (TI MEK), and signed by the TI Private key (TI MPK).Customer has to dual sign it with their private key (SMPK/BMPK).(Refer Signing an encrypted binary for secure boot)
HS Keywriter
Keywriter 软件补丁
Copy the OTP keywriter firmware
ti-fs-keywriter.binfile to /pdk_jacinto_08_06_00_31/packages/ti/boot/keywriter/tifs_bin/j784s4/ti-fs-keywriter.bin
Copy the TIFEK Public key
ti_fek_public.pemfile to /pdk_jacinto_08_06_00_31/packages/ti/boot/keywriter/scripts/ti_fek_public.pem
make keywriter_img_clean BOARD=j784s4_evm -j8
make keywriter_img BOARD=j784s4_evm -j8
Keywriter 硬件串口


Keywrirter OTP验证
- Configure boot mode of the board to UART boot and connect second MCU
UART.

- The terminal prints some log as shown below. You need to remove the extra CCC at the end and save as a log file.
02000000011a00006a376165700000000000000048535345000801000008010002a600000100010>02b28ecde967b79d61619f89cf299205c36d179cacb2b1c5a7f16e3169cc879602122d07ad47ae878>a46e243c6f5078c04a5452faceeccb00d0453a5a5e6420dac6cfbc5db350e9b7899b6bd036e16a454>76576ae4b9d5b8db64799c0573e816e84febd83197a80f8f1884ad190329612b94fee52b7f06f68710> 6070b357fbc30fcc0af8be03eaf7cc43c2d521427fee817fd556d5f9a37d362a39b5091752aeb
- Copy the following code and save it as a python file.python
#!/usr/bin/env python3
import binascii
import struct
import string
import sys
filename=sys.argv[1]
fp = open(filename, 'rt')
lines= fp.readlines()
fp.close()
bin_arr = [ binascii.unhexlify(x.rstrip()) for x in lines ]
bin_str = b"".join(bin_arr)
pubInfoStr='BB2B12B4B4B4B'
secInfoStr='BBHHH64B64B32B'
numBlocks = list(struct.unpack('I', bin_str[0:4]))
pubROMInfo = struct.unpack(pubInfoStr, bin_str[4:32])
if numBlocks > 1:
secROMInfo = struct.unpack(secInfoStr, bin_str[32:200])
print ('-----------------------')
print ('SoC ID Header Info:')
print ('-----------------------')
print ("NumBlocks :", numBlocks)
print ('-----------------------')
print ('SoC ID Public ROM Info:')
print ('-----------------------')
print ("SubBlockId :", pubROMInfo[0])
print ("SubBlockSize :", pubROMInfo[1])
tmpList = list(pubROMInfo[4:15])
hexList = [hex(i) for i in tmpList]
deviceName = ''.join(chr(int(c, 16)) for c in hexList[0:])
print ("DeviceName :", deviceName)
tmpList = list(pubROMInfo[16:20])
hexList = [hex(i) for i in tmpList]
deviceType = ''.join(chr(int(c, 16)) for c in hexList[0:])
print ("DeviceType :", deviceType)
dmscROMVer = list(pubROMInfo[20:24])
dmscROMVer.reverse()
print ("DMSC ROM Version :", dmscROMVer)
r5ROMVer = list(pubROMInfo[24:28])
r5ROMVer.reverse()
print ("R5 ROM Version :", r5ROMVer)
print ('-----------------------')
print ('SoC ID Secure ROM Info:')
print ('-----------------------')
print ("Sec SubBlockId :", secROMInfo[0])
print ("Sec SubBlockSize :", secROMInfo[1])
print ("Sec Prime :", secROMInfo[2])
print ("Sec Key Revision :", secROMInfo[3])
print ("Sec Key Count :", secROMInfo[4])
tmpList = list(secROMInfo[5:69])
tiMPKHash = ''.join('{:02x}'.format(x) for x in tmpList)
print ("Sec TI MPK Hash :", tiMPKHash)
tmpList = list(secROMInfo[69:133])
custMPKHash = ''.join('{:02x}'.format(x) for x in tmpList)
print ("Sec Cust MPK Hash :", custMPKHash)
tmpList = list(secROMInfo[133:167])
uID = ''.join('{:02x}'.format(x) for x in tmpList)
print ("Sec Unique ID :", uID)
- 转换log命令:python uart_boot_socid.py default_uart_hs.log
-----------------------
SoC ID Header Info:
-----------------------
('NumBlocks :', [2])
-----------------------
SoC ID Public ROM Info:
-----------------------
('SubBlockId :', 1)
('SubBlockSize :', 26)
('DeviceName :', 'j7aep\x00\x00\x00\x00\x00\x00')
('DeviceType :', 'HSSE')
('DMSC ROM Version :', [0, 1, 8, 0])
('R5 ROM Version :', [0, 1, 8, 0])
-----------------------
SoC ID Secure ROM Info:
-----------------------
('Sec SubBlockId :', 2)
('Sec SubBlockSize :', 166)
('Sec Prime :', 0)
('Sec Key Revision :', 1)
('Sec Key Count :', 1)
('Sec TI MPK Hash :', '2b28ecde967b79d61619f89cf299205c36d179cacb2b1c5a7f16e3169cc879602122d07ad47ae878a46e243c6f5078c04a5452faceeccb00d0453a5a5e6420da')
('Sec Cust MPK Hash :', 'c6cfbc5db350e9b7899b6bd036e16a45476576ae4b9d5b8db64799c0573e816e84febd83197a80f8f1884ad190329612b94fee52b7f06f687106070b357fbc30')
('Sec Unique ID :', 'fcc0af8be03eaf7cc43c2d521427fee817fd556d5f9a37d362a39b5091752aeb')
- 私钥推出公钥,然后算出刷进去的public key hash与 Sec Cust MPK Hash相同。
openssl rsa -in smpk.pem -pubout -outform DER -out k3_dev_mpk_pub.der
sha512sum k3_dev_mpk_pub.der
c6cfbc5db350e9b7899b6bd036e16a45476576ae4b9d5b8db64799c0573e816e84febd83197a80f8f1884ad190329612b94fee52b7f06f687106070b357fbc30 k3_dev_mpk_pub.der
- 将k3_dev_mek.txt内容替换为smek.key
xxd -p smek.key
30f70bc8b0db5468611f309fa9354a6223963afb63fd7c4f6b877eb88e3bb000//结果
Keywrirter Makefile
keywr_imagegen: $(SBL_BIN_FILE)
$(SBL_OBJ_COPY) $(SBL_OBJ_COPY_OPTS) -O binary $(EXE_NAME) $(SBL_BIN_PATH)
$(ECHO) \# Appending certificate to keywriter binary file.
$(CAT) $(KEYWRITER_APP_DIR)/x509cert/final_certificate.bin >> $(SBL_BIN_PATH)
ifeq ($(SOC),$(filter $(SOC), $(keywriter_SOCLIST)))
ifneq ($(OS),Windows_NT)
$(CHMOD) a+x $(SBL_CERT_GEN)
endif
$(SBL_CERT_GEN) -b $(SBL_BIN_PATH) -o $(SBL_TIIMAGE_PATH) -c R5 -l $(SBL_RUN_ADDRESS) -k $($(APP_NAME)_KEYWR_CERT_KEY) -d DEBUG -j DBG_FULL_ENABLE -m $(SBL_MCU_STARTUP_MODE)
else
$(ECHO) $(SOC) "not yet supported"
endif
$(ECHO) \# Signed Keywriter image $(SBL_TIIMAGE_PATH) created.
$(ECHO) \#
证书:
$(KEYWRITER_APP_DIR)/x509cert/final_certificate.bin
证书秘钥:
packages/ti/build/makerules/rom_degenerateKey.pem
Note:
If a random key is generated and SBL is signed with this,the ROM will copy the SBL image for authentication using memcopy.
With this key ,ROM will be directed to use DMA to load the SBL for authentication which saves boot time.
Encrypt:
( ( ((APP_NAME)_SBL_CERT_KEY) -y ENCRYPT -e $(SBL_ENCRYPT_KEY_HS) -d DEBUG -j DBG_FULL_ENABLE -m $
(SBL_MCU_STARTUP_MODE)
export SBL_ENCRYPT_KEY_HS=~/TIDummyKey/smek.txt
Keywrirter 证书生成
Keywrirter 脚本命令
执行命令
./gen_keywr_cert.sh -g
./gen_keywr_cert.sh -s keys/smpk.pem -s-wp --smek keys/smek.key --smek-wp -t ti_fek_public.pem -a keys/aes256.key --keycnt 1 --keyrev 1
参数解析
> -g #//命令
> #Generate aes256 key, bmpk, bmek, smpk, smek in keys/ folder //注释
> openssl rand 32 > keys/aes256.key #//动作
> openssl genrsa -out keys/smpk.pem 4096
> openssl genrsa -out keys/bmpk.pem 4096
> openssl rand 32 > keys/smek.key
> openssl rand 32 > keys/bmek.key
> -s
> #4096 bit(RSA private key, pem format)
> #Secondary Manufacturer Public Key to be used
> keys/smpk.pem
> smpk_info[flag]="yes"
> smpk_info[file]="keys/smpk.pem"
> -s-wp
> smpk_info[wp]="yes"
> --smek
> #256 bit (symmetric key, binary file)
> keys/smek.key
> smek_info[flag]="yes"
> smek_info[file]="keys/smek.key"
> --smek-wp
> smek_info[wp]="yes"
> -t
> #4096 bit (RSA publick key, pem format)
> #TI provided Forward Encryption Key
> ti_fek_public.pem
> tifek_info[flag]="yes"
> tifek_info[file]="ti_fek_public.pem"
> -a
> #256 bit (symmetric key)
> keys/aes256.key
> aes256key_info[flag]="yes"
> aes256key_info[file]="keys/aes256.key"
> --keycnt
> #Key Count
> 1
> parse_validate_key_cnt "1"
> --keyrev
> #Note: If Key Rev is 2, BMPKH and BMEK are used for sec boot
> 1
> parse_validate_key_rev "1"
Keywrirter 脚本结果
# Using Key Count: 0x00000001
# Using Key Rev: 0x00000001
Generating Single signed certificate!!
# encrypt aes256 key with tifek public part
# encrypt SMPK-priv signed aes256 key(hash) with tifek public part
# encrypt smpk-pub hash using aes256 key
writing RSA key
# encrypt smek (sym key) using aes256 key
3997 primary_cert.bin
3997 ../x509cert/final_certificate.bin
# SHA512 Hashes of keys are stored in verify_hash.csv for reference..
Keywrirter 脚本命令解析
0.1 openssl rand 32 > keys/aes256.key #生成256bit随机数
0.2 openssl genrsa -out keys/smpk.pem 4096 #将生成的私钥保存至filename文件,若未指定输出文件,则为标准输出。
0.3 openssl genrsa -out keys/bmpk.pem 4096
0.4 openssl rand 32 > keys/smek.key
0.5 openssl rand 32 > keys/bmek.key
0.6 smpk_info[flag]=“yes”
0.7 smpk_info[file]=“keys/smpk.pem”
0.8 smpk_info[wp]=“yes”
0.9 smek_info[flag]=“yes”
0.10 smek_info[file]=“keys/smek.key”
0.11 smek_info[wp]=“yes”
0.12 tifek_info[flag]=“yes”
0.13 tifek_info[file]=“ti_fek_public.pem”
0.14 aes256key_info[flag]=“yes”
0.15 aes256key_info[file]=“keys/aes256.key”
0.16 parse_validate_key_cnt “1”
0.17 parse_validate_key_rev “1”
# Check for presence of SM*K, BM*K (optional)
1.secondary_cert_info[flag]="no"
2.echo "Generating Single signed certificate!!"
3.mkdir -p tmpdir
4.mkdir -p configs
5.mkdir -p ../x509cert
6.openssl genrsa -out tmpdir/bmpk.pem 4096 2> /dev/null
7.bmpk_info[file]="tmpdir/bmpk.pem"
8.openssl rand 32 > tmpdir/bmek.key
9.bmek_info[file]="tmpdir/bmek.key"
# generate a random 256 bit key -- AES256 Key
10.aes256key_info[val]=$(xxd -p -c 32 "keys/aes256.key")
11.echo "" > "verify_hash.csv"
12.echo "# encrypt aes256 key with tifek public part"
# CRYPTOGRAPHIC OPERATIONS TO CALC HASH/ENC.
13.echo "# encrypt aes256 key with tifek public part"
14.encrypt "ti_fek_public.pem" "keys/aes256.key" tmpdir/enc_aes_key.enc
#encrypt(){
# encrypt命令的主要功能是使用RSA算法签名,验证身份,加密/解密数据。
# openssl rsautl -encrypt -inkey "$1" -pubin -in "$2" -out "$3"
# -encrypt:用我们的公共密钥对输入的数据进行加密。
# -inkey file:指定我们的私有密钥文件,格式必须是RSA私有密钥文件。
# -out filename:指定输出文件名,默认为标准输出。
#}
15.echo "# encrypt SMPK-priv signed aes256 key(hash) with tifek public part"
16.sign_the_hash "keys/smpk.pem" tmpdir/smpk_sign_aes256.sign "keys/aes256.key"
#sign_the_hash(){
# dgst命令的主要功能是,计算信息摘要(哈希), 给文件生成数字签名以及验证数字签名。
# openssl dgst -sha512 -sign "$1" -out "$2" "$3"
# -sign file:执行签名操作,后面指定私钥文件
# -sha512:摘要算法使用sha512
# -out filename:指定输出文件,默认标准输出
#}
17.dd if=tmpdir/smpk_sign_aes256.sign of=tmpdir/smpk_sign_aes256_1.sign bs=256 count=1 status=none
18.dd if=tmpdir/smpk_sign_aes256.sign of=tmpdir/smpk_sign_aes256_2.sign bs=256 skip=1 count=1 status=none
19.encrypt "ti_fek_public.pem" tmpdir/smpk_sign_aes256_1.sign tmpdir/enc_smpk_signed_aes_key_1.enc
20.encrypt "ti_fek_public.pem" tmpdir/smpk_sign_aes256_2.sign tmpdir/enc_smpk_signed_aes_key_2.enc
21.cat tmpdir/enc_smpk_signed_aes_key_1.enc tmpdir/enc_smpk_signed_aes_key_2.enc > tmpdir/enc_smpk_signed_aes_key.enc
22.echo "# encrypt smpk-pub hash using aes256 key"
23.gen_pub_key_x509_extension "keys/smpk.pem" tmpdir/smpkpub.der tmpdir/smpkh "SMPKH" tmpdir/smpkh.iv tmpdir/smpkh.rs tmpdir/smpkhfield tmpdir/aesenc_smpkh.enc
#priv_pem_to_pub_der(){
# openssl rsa -in "$1" -outform der -pubout -out "$2"
# 根据私钥推出公钥
#}
#calc_hash(){
# openssl dgst -sha512 -binary "$1" > "$2"
# -binary:结果使用二进制格式输出
#}
#gen_iv(){
# openssl rand -out "$1" 16
# 16:随机数长度
#}
#gen_rs(){
# openssl rand -out "$1" 32
#}
#gen_pub_key_x509_extension(){
# priv_pem_to_pub_der "$1" "$2"
# calc_hash "$2" "$3"
# echo "$4,$(xxd -p $3)" >> "${output_info[hash_csv]}"
# gen_iv "$5"
# gen_rs "$6"
# IV=$(xxd -p -c 32 "$5")
# cat "$3" "$6" > "$7"
# openssl aes-256-cbc -e -K "${aes256key_info[val]}" -iv "${IV}" -nopad -in "$7" -out "$8"
# -e:Encrypt
# -K val Raw key, in hex
# -iv val IV in hex
# -nopad Disable standard block padding
# -in infile Input file
# -out outfile Output file
#}
24.echo "# encrypt smek (sym key) using aes256 key"
25.gen_sym_key_x509_extension "SMEKH" "keys/smek.key" tmpdir/smekh tmpdir/smek.iv tmpdir/smek.rs tmpdir/smekfield tmpdir/aesenc_smek.enc
# gen_sym_key_x509_extension(){
# gen_iv "$4"
# gen_rs "$5"
# IV=$(xxd -p -c 32 "$4")
# cat "$2" "$5" > "$6"
# openssl dgst -sha512 -binary "$2" > "$3"
# echo "$1,$(xxd -p $3)" >> "${output_info[hash_csv]}"
# openssl aes-256-cbc -e -K "${aes256key_info[val]}" -iv "${IV}" -nopad -in "$6" -out "$7"
# }
26.populate_config_primary
#tmpdir/enc_aes_key.enc
#tmpdir/enc_smpk_signed_aes_key.enc
#tmpdir/aesenc_smpkh.enc
#tmpdir/smpkh.iv
#tmpdir/smpkh.rs
#tmpdir/aesenc_smek.enc
#tmpdir/smek.iv
#tmpdir/smek.rs
27.sed -i "/.*[bB][mM].[kK].*/d" "primary_cert.bin"
28.openssl req -new -x509 -key "keys/smpk.pem" \
-nodes -outform der -out "primary_cert.bin" \
-config "configs/prim_cert_config.txt" \
-sha512
#-new:说明生成证书请求文件
#-x50:说明生成自签名证书
#-key:指定已有的秘钥文件生成秘钥请求,只与生成证书请求选项-new配合。
#der:用二进制DER编码的证书
29.cat "primary_cert.bin" > "../x509cert/final_certificate.bin"
30.du -b "primary_cert.bin" "../x509cert/final_certificate.bin"
31.echo "# SHA512 Hashes of keys are stored in verify_hash.csv for reference.."
Keywrirter X509密钥关系
秘钥相互依赖关系
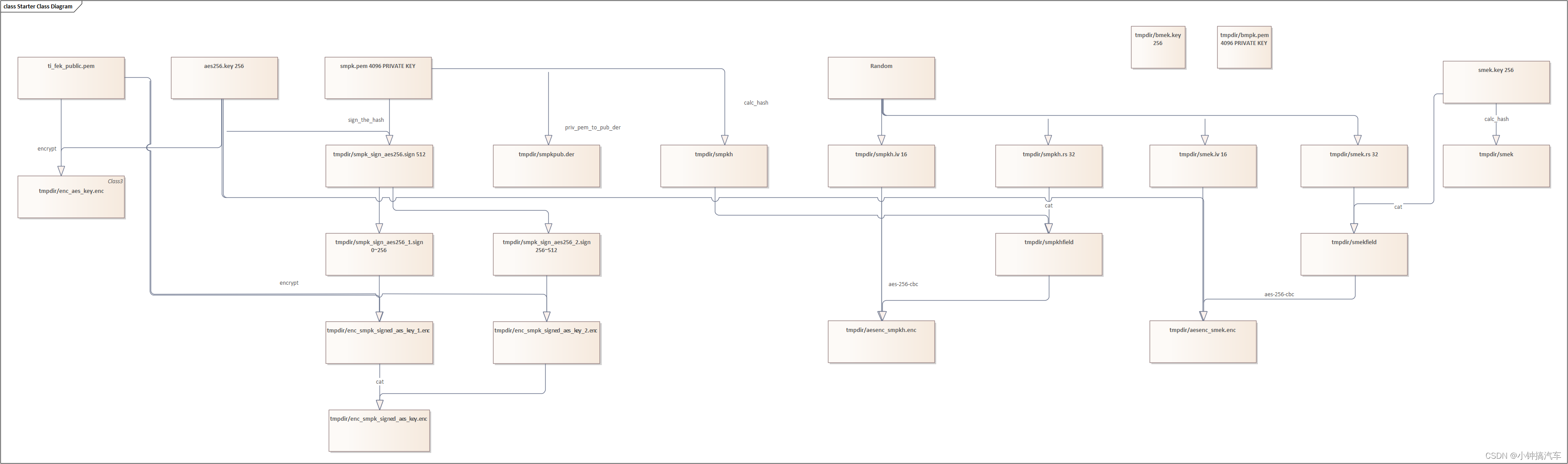 将der二进制证书转为dem格式证书命令
将der二进制证书转为dem格式证书命令
sudo openssl x509 -inform der -in primary_cert.bin -out demo.pem
查看证书内容命令
openssl x509 -in demo.pem -text
证书内容
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
60:8d:ad:b0:51:56:6a:51:93:1e:14:09:9b:b2:13:40:7a:87:a3:fd
Signature Algorithm: sha512WithRSAEncryption
Issuer: C = oR, ST = rx, L = gQE843yQV0sag, O = dqhGYAQ2Y4gFfCq0t1yABCYxex9eAxt71f, OU = a87RB35W, CN = x0FSqGTPWbGpuiV, emailAddress = kFp5uGcgWXxcfxi@vsHs9C9qQWGrBs.com
Validity
Not Before: Aug 9 02:28:06 2023 GMT
Not After : Sep 8 02:28:06 2023 GMT
Subject: C = oR, ST = rx, L = gQE843yQV0sag, O = dqhGYAQ2Y4gFfCq0t1yABCYxex9eAxt71f, OU = a87RB35W, CN = x0FSqGTPWbGpuiV, emailAddress = kFp5uGcgWXxcfxi@vsHs9C9qQWGrBs.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (4096 bit)
Modulus:
00:d1:3a:bd:15:54:7f:1b:fa:7c:ab:24:b6:33:e2:
a5:34:ba:20:99:8f:6c:94:89:5b:f1:9a:22:60:62:
23:e8:32:09:f5:5b:c4:ca:18:4a:1a:15:1b:ad:6b:
05:45:6a:77:bf:65:4d:13:f5:a7:60:9b:c2:7a:88:
d6:02:22:65:bd:49:13:d1:b1:33:f9:06:23:a8:f4:
7d:81:a8:55:08:de:a7:2a:8b:08:0f:0e:3d:a8:6a:
e6:6c:44:6d:7c:fe:e4:9c:c3:0e:fc:9e:e9:6d:d8:
0e:9f:90:04:66:2e:0e:ce:27:69:19:5a:5e:12:83:
56:c9:cd:2e:32:a7:f1:4a:b4:e0:17:17:2a:1d:55:
d9:5d:15:96:e7:7c:42:02:8c:e7:14:cc:78:4b:23:
5d:8d:cf:3b:28:19:df:14:22:6f:c1:bd:f5:85:3a:
dd:3e:00:4f:27:99:51:b5:80:d8:9c:29:60:21:05:
f5:04:d1:77:b9:02:b5:b9:44:08:9f:df:32:a1:dc:
3b:5a:aa:19:be:7d:be:0e:0a:9e:d2:c2:9e:47:0d:
32:ab:ca:d9:d4:c4:ab:13:eb:f8:3b:d3:e8:49:4c:
5f:3c:f8:94:6d:39:c8:09:af:d5:dc:27:81:b3:9f:
15:e0:64:f6:52:62:18:b2:8a:23:ac:9c:63:36:1e:
17:88:29:1f:ae:5c:bf:e7:31:b3:ad:b9:fb:14:92:
6c:f4:5f:15:e2:2d:28:68:40:4c:b1:ec:79:c9:a0:
91:44:58:72:d5:15:95:0b:a2:3b:59:58:18:d3:3c:
56:72:4e:8c:da:de:8f:7e:1b:bc:2b:cf:a2:96:ab:
53:08:39:95:20:90:9e:d0:e2:b1:36:75:e2:bc:13:
e1:38:90:bc:1d:53:11:4c:f0:ae:ea:43:e4:a2:69:
6c:9e:c7:e5:37:65:bf:55:19:87:57:36:40:7a:b1:
3c:b3:4c:1b:28:08:1d:e1:06:7e:67:32:a8:de:bc:
0c:57:da:79:f0:e8:be:09:6f:3b:95:a7:c5:60:bd:
a8:d5:9e:12:9b:71:66:ad:75:76:98:b9:96:8f:32:
de:31:74:9f:30:e5:1e:47:11:d2:04:87:e2:f9:42:
73:50:74:b2:d6:48:b9:22:ae:57:e9:d0:7f:56:ca:
f8:f6:d5:1a:c4:61:6c:25:34:ae:4d:3b:b4:a9:97:
83:51:c5:88:42:5b:5a:db:6b:7c:b6:bb:44:29:83:
76:78:3d:ff:34:a7:a2:03:6e:4d:e2:46:2d:5a:a6:
c2:6c:ab:2b:db:7c:26:89:65:48:ca:ee:9f:13:13:
94:24:e0:f6:e0:2c:c9:35:58:09:28:b4:94:75:0d:
10:63:63
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:TRUE
1.3.6.1.4.1.294.1.64:
0....... J.+C...E~..lLa...Y....CP..O....!=.E..n.]k.-.a...$..........x.D../..V....F.\.2....../.%k6.......4&xZ....F.....T'E%.j,W`..[r.#.+qq..@.
Ed..KT.+_Dd\F
.,Iu...;.......Yf......j..7(....TPCr..N.<k.....O....a.nw.4.>o..3.Y..1...n.sj.....=..P..HJ...
...m..."x...b.
z....=.Ed.`.Dr.WAc...`ZiB.l..5.X.r,-*..._..0P....'tIV...ai....&d.Z;.m.}......*{..u........v(...
...%....3*.p0..T{..|.4.yJ.b.......k.~+.
.1\@.B..!O..........._...d...3.....k.:.:...G5e....T..\..Y.p}.... ..w./p.N$..Z..:\..k...;.....mJ....(0G~..!.>........B.......
1.3.6.1.4.1.294.1.65:
0.......2.g...L7.....Q..[.'..H.q.B.F._...Z..ov.P....9.1.^TPHiy.,%e.....5-h..Of.t.g..
..O):....b..-....9.L.....8 ..O...d./<..K..#..\..L.4..U#.+.....J..V4.......}...W%...pQ.7;s.sR..g...........;A...\
.....#H............m...W.....|.|y.\.@tvK$'zl. ....!.*......5...q.;Z..]....e....~.....x.].l.Ws.oX7..+.kQ.A.....+,f,.D.b.J.d..7.t..7..a.....g.....
..T../.2Sk[.+..R..F7.I].......F.9'.(..~I.\....?.X.......k..`....*E.o17)...Z.L.Q...6.7.-
+%..]3..>.I...&y......$.6D.@]...9..L..$M5V...<..C..........._J...
...s..D+S...Ydn....N...l.s.X.....`..wv.... .Z..SoX+...5.p9!..........f......G+
..y.{..2...WB...K.W..8A..-.`F<.4.hFf..w...amdE.~.
7..G..k.W..u.K.7....`.|.....;).......U*.........c........*.%..6...-<.8.
....;!.....e,.._;e$......]m.+.oN.......W...V..M.P.p
.w..H...."M.{.........}8..".F..!+...b.......L4..VFh+P.........@.I..?...;.I..8....]t&........:..a8.5..
.G...hNtwyDd......?Oy..>..U..4J.k5.
.G...(TQ.F.7.%E.3.D.a.2[...j.].-....x.. ..'1...Ie<......3...{.>.c...X..q|@....+i.OO.B.#.t...../..&L,h&l[..........i...]a[...m...N..
?=Q..d.j.;......
1.3.6.1.4.1.294.1.67:
0...`.:,..c...h.......F...P..T]....r.u!...<....}...f..f./....2...\...;.K.
N.iul..&......[+0m...5...Om....Thk}I)/......1. s......7.0..S]..^q...l..z..\.*....`..Z..Z
1.3.6.1.4.1.294.1.68:
0..@`Y...-..1..;....E....a6K/z.%..R....m...WeT......h..W.GW.R......t...k5..?.6?.....=.. ....h+1T.+&....NN.D....KB......&..@..Z..Z
1.3.6.1.4.1.294.1.69:
0............
1.3.6.1.4.1.294.1.72:
0
..........
1.3.6.1.4.1.294.1.73:
0........................................................................................................................................................ ...............................................................
1.3.6.1.4.1.294.1.74:
0
............Z
1.3.6.1.4.1.294.1.76:
0
.............
1.3.6.1.4.1.294.1.77:
0
............Z
1.3.6.1.4.1.294.1.78:
0................
1.3.6.1.4.1.294.1.79:
0................
1.3.6.1.4.1.294.1.80:
0..................
1.3.6.1.4.1.294.1.81:
0.......
Signature Algorithm: sha512WithRSAEncryption
53:94:55:ca:48:c4:41:c9:db:74:31:56:bb:43:2d:bb:79:89:
b1:3c:e0:6e:60:a3:8c:df:57:e6:c3:75:ec:f8:c0:3c:df:17:
55:a2:fa:0b:63:2d:e9:30:dc:d9:ad:06:9c:7c:8d:2b:a8:74:
4f:54:ae:38:66:8d:ea:a3:d8:1b:cb:b1:ae:1a:79:62:55:08:
ac:8a:6d:d7:2e:2a:0d:5b:b6:06:99:2d:9a:02:d0:2d:1e:0f:
7f:cc:33:c8:a1:7b:17:74:52:3e:7b:99:50:bd:f7:24:07:72:
a2:dc:c0:95:42:26:4e:47:99:b9:d1:18:1c:da:9a:0b:51:03:
7b:3a:60:2c:3f:41:f1:01:16:53:1e:37:cf:22:e3:81:29:3b:
ee:22:cf:05:95:6c:8c:92:08:9c:5b:a4:b1:cd:78:1d:97:90:
9e:1c:b8:98:92:63:04:aa:06:b0:74:bc:97:4f:bd:4f:21:05:
b8:2c:50:d1:e2:d5:ee:ef:a6:54:9c:ab:ad:ef:1a:c0:6c:df:
27:7a:2b:39:75:3f:e5:ed:0e:f5:1a:68:fe:b2:51:97:fd:7a:
94:64:52:de:e9:c9:4d:a0:f8:85:56:0c:f8:45:f4:2b:f4:89:
34:25:e9:d8:96:36:5e:84:db:1c:49:05:01:f1:8d:43:87:09:
57:73:92:df:a9:81:8b:2e:14:4c:b4:31:17:51:fc:8e:26:d7:
10:e4:20:c0:c6:ab:6a:ff:67:8d:41:93:e2:5a:c2:36:bc:ba:
ae:50:b7:36:6c:6d:36:9d:ad:53:2f:ae:6f:7a:14:34:4d:5f:
9a:e4:31:40:d7:09:6f:80:af:29:1a:ed:d8:ba:0f:96:33:c1:
83:17:a3:27:8e:bc:52:ee:35:96:1e:5f:02:d0:d8:fe:07:0e:
1f:b5:d0:8c:c1:8e:db:8a:f0:24:94:f5:6d:e2:8c:1f:af:93:
15:0e:3e:cd:39:c9:5d:06:b2:51:31:af:47:7d:55:17:99:6f:
12:f6:f7:48:b4:e3:28:79:69:d5:6c:37:e7:1b:ec:28:56:27:
99:53:c8:ab:de:be:a0:9d:45:86:78:92:71:1f:85:37:36:4a:
c3:1b:ed:4c:30:d8:23:48:72:7c:25:af:d4:0f:30:0d:3c:36:
4e:d6:71:86:83:f5:f0:ea:d9:8a:40:98:70:41:2f:fe:ef:f6:
1e:16:b8:1e:03:af:79:0d:9c:6d:33:62:39:26:ee:53:06:55:
2c:37:d8:54:67:21:41:42:7f:79:fd:9a:da:61:38:d1:7a:de:
7e:cc:7e:9d:79:e2:20:6d:d8:30:a8:73:e9:63:50:44:d1:4c:
ab:a7:30:b6:6e:1a:7a:b2
-----BEGIN CERTIFICATE-----
MIIPmTCCDYGgAwIBAgIUYI2tsFFWalGTHhQJm7ITQHqHo/0wDQYJKoZIhvcNAQEN
BQAwgb8xCzAJBgNVBAYTAm9SMQswCQYDVQQIDAJyeDEWMBQGA1UEBwwNZ1FFODQz
eVFWMHNhZzErMCkGA1UECgwiZHFoR1lBUTJZNGdGZkNxMHQxeUFCQ1l4ZXg5ZUF4
dDcxZjERMA8GA1UECwwIYTg3UkIzNVcxGDAWBgNVBAMMD3gwRlNxR1RQV2JHcHVp
VjExMC8GCSqGSIb3DQEJARYia0ZwNXVHY2dXWHhjZnhpQHZzSHM5QzlxUVdHckJz
LmNvbTAeFw0yMzA4MDkwMjI4MDZaFw0yMzA5MDgwMjI4MDZaMIG/MQswCQYDVQQG
EwJvUjELMAkGA1UECAwCcngxFjAUBgNVBAcMDWdRRTg0M3lRVjBzYWcxKzApBgNV
BAoMImRxaEdZQVEyWTRnRmZDcTB0MXlBQkNZeGV4OWVBeHQ3MWYxETAPBgNVBAsM
CGE4N1JCMzVXMRgwFgYDVQQDDA94MEZTcUdUUFdiR3B1aVYxMTAvBgkqhkiG9w0B
CQEWImtGcDV1R2NnV1h4Y2Z4aUB2c0hzOUM5cVFXR3JCcy5jb20wggIiMA0GCSqG
SIb3DQEBAQUAA4ICDwAwggIKAoICAQDROr0VVH8b+nyrJLYz4qU0uiCZj2yUiVvx
miJgYiPoMgn1W8TKGEoaFRutawVFane/ZU0T9adgm8J6iNYCImW9SRPRsTP5BiOo
9H2BqFUI3qcqiwgPDj2oauZsRG18/uScww78nult2A6fkARmLg7OJ2kZWl4Sg1bJ
zS4yp/FKtOAXFyodVdldFZbnfEICjOcUzHhLI12NzzsoGd8UIm/BvfWFOt0+AE8n
mVG1gNicKWAhBfUE0Xe5ArW5RAif3zKh3Dtaqhm+fb4OCp7Swp5HDTKrytnUxKsT
6/g70+hJTF88+JRtOcgJr9XcJ4GznxXgZPZSYhiyiiOsnGM2HheIKR+uXL/nMbOt
ufsUkmz0XxXiLShoQEyx7HnJoJFEWHLVFZULojtZWBjTPFZyToza3o9+G7wrz6KW
q1MIOZUgkJ7Q4rE2deK8E+E4kLwdUxFM8K7qQ+SiaWyex+U3Zb9VGYdXNkB6sTyz
TBsoCB3hBn5nMqjevAxX2nnw6L4JbzuVp8VgvajVnhKbcWatdXaYuZaPMt4xdJ8w
5R5HEdIEh+L5QnNQdLLWSLkirlfp0H9Wyvj21RrEYWwlNK5NO7Spl4NRxYhCW1rb
a3y2u0Qpg3Z4Pf80p6IDbk3iRi1apsJsqyvbfCaJZUjK7p8TE5Qk4PbgLMk1WAko
tJR1DRBjYwIDAQABo4IJiTCCCYUwDAYDVR0TBAUwAwEB/zCCAhsGCSsGAQQBgiYB
QASCAgwwggIIBIICACBKzCtDHIARRX72uWxMYQSUH1kPD4WpQ1Dh0E/E98byIT0a
RcMDbglda7UtyGEF1Y8kptK7gt2P7qHOgHjQRPO0L4L/Vtqjn8ZGFVzBMq61oe7p
BS+VJWs2EtXP3Yu5LjQmeFqllxEQRsjzB83kVCdFJaRqLFdgkB5bcpYjzytxcfq7
QLQKRWT+iktUAitfRGRcRg2OLEl1Ahq3O70aupm95ftZZvHl74LjhWrvGDcoiLGJ
3VRQQ3LamU4IPGui9BQH4E8Z5t/7YQlud7c0hT5v5JYzuFn+qzGu48huCHNq0vPm
v/I9rehQD+lISpDymgof3hVtl8HYIni48NRi3w16DtiCmT3SRWTAYH9EcsdXQWPr
m+JgWmlCBGwSnTXAWOhyLC0qGcqWX6oaMFDw1KIBJ3RJVqfbmmFpx/T7tiZkrFo7
r22zfcHPsJX36ip7ppB1jAX5lrDpy8F2KIOWCQ2yh94lFcIblzMqpXAwpvdUex/p
fL00/nlKmmLy9fnkC6aqa8V+K4UN/DFcQPRC//ohT8wF47HF1vOr/pkSX8WkmmQS
G8oz2o7xDAxrrzoBOhkU+0c1Zcvbz/xUl7hcp6lZknB9sAWG3CDMFneJL3CwTiTu
4FrVnTpc55tr5t3HO6ns+5edbUr7q+XcKDBHfuHdIeI+ggCfs+4XkcVCqY+BAgIC
ADCCBBsGCSsGAQQBgiYBQQSCBAwwggQIBIIEADIeZw4Ogkw3xZgcGvlR6plb7yeR
9kigcY1C70alX43K5VqNEm9201DP+NLMOQEx815UUEhpeassJWXhFIjrkjUtaNz5
T2btdPFnwNANl9RPKTqeBZvWYo/yLY2sx/s50UwGC40Z6jggABJP2oDyZOwvPLzC
S4z5I+WZXN/QTPQ0BpxVI6crGqv4HM9Ky6pWNAS6hceYLgd9Lr2HVyUfB6ZwUYo3
O3Pec1K/w2fADsYAxRH6FqefsjtB+n/SXAoMtNnfsCNIx8cSowuYiRDMv7wCbZWi
hFfZvbbA1XyzfHnJXAxAdHZLJCd6bB8g0IiT2CHkKuejp/SXDDXE6pJxvTtavutd
lRLB/2UdDoAufoD44Ln6eANdBGyvV3OWb1g3Fe0r/2tRsUHslLv6iissZizwRAJi
HErJZKEQNxx0nwM3woRh6tKsA5hngKoBurcK2RRU16svpzJTa1vGK5ylUrH7Rjf7
SV2Dxy6NDBrzRug5J+4o49p+SbZcC8r7iD/kWN4I/IubmxtrmBxgwdnuvCpFh28x
NynAmtlaHEyMUaKlEjb1NxotDSsl//VdMwPWPhdJ9YfCJnkW28eSC78k3DZE20Bd
FYmFObXpTMWXJE01Vo7c3DwBLkMMn/Ww0PuUF5yBm19K1wylCoEC5HMa90QrU+bV
u1lkboT/E5RO/OizbIdzFViovP/A5WDGAHd2AIeukSDMWp+EU29YKxcJlDXccDkh
28SMHckcDLgIEGa8wraIFuJHKw3ktnm0e9r+MvDrtFdCwrHQS49Xzp04QYieLRtg
Rjy7NBpoRmbUl3f4n4lhbWRFr36FDTe1f0fPBWuKV+KEdbNLzzcW3YDYYO58nNMG
5b47KdGFyp/n//RVKuYZ/K25wf3av2Pe7pK5n7anxyp/JQy4Ns6W3y08GTgSChHu
ydk7Ifj41OjvZSy32V87ZSQOieCy/qpdbdUrnW9O7oqQH+UUGlf1/KNW/ddNhFAY
cA2Od4gBSO/EGrwiTYp7khOWEYv6Asu/fTjImCLcRpbLISsCv6hisL2joAQOgEw0
FBFWRmgrUPHJt866/p0cnkDdSd5/P98eGTuLSam1OO3Rj+xddCYXiLDOFecUkDra
7WE49zXM8wrZRw+vwGhOdHd5RGTPndm29ZQ/T3m6/j7XmVXmkzRKu2s1kQ2kR9rc
oChUUfBGhTcJJUWEM4REF2GMMlsEiKZqD10ILaMVjbd445AgHugnMf/kCUllPNPT
x5fV9TMFouB73j6/Y8Pqw1iE0nF8QJn6vPIrabRPT49CFSOHdJS9A6K2L66PJkws
aCZsW9vYtK2Ph5/LuYdpDq6WXWFb9++fbbYXy06Dtwo/PVGjx2Ttatk7+pUCAgQA
MIGwBgkrBgEEAYImAUMEgaIwgZ8EYKk6LK37Y52BDmjgkKT2lNmQRtqpv1D4FFRd
8hmDHHKOdSGzzIY82PuI+n3rGb1mE+Vm/S+99dmUMuif0Fz/3Bo7rUvlDU4LaXVs
qYAm6I+RxPiZWyswbdKV+jXwBN5PbQQQxZlUaGt9SSkvwoUIx767MQQgcx2ixq+5
szfFMKH8U12WDl5xFsr6bBoZepnCXLkqhgcCAWACBFqlpVowgY8GCSsGAQQBgiYB
RASBgTB/BEBgWRSX0S2coDET0ju83toERQOREZ1hNksveoYl2s5S6QjUwm3t1uNX
ZVTwzbAUibZo4edXB0dXCFJ/CRG6l5h0BBDmazWxCT/iNj/p9paSpj2nBCADh9+b
aCsxVBcrJgLG/hJOTrhEz/8J2ktCwpOk1wKMJgIBQAIEWqWlWjAaBgkrBgEEAYIm
AUUEDTALBAIAAAIFAKWlpaUwGQYJKwYBBAGCJgFIBAwwCgQBAAIFAKWlpaUwgecG
CSsGAQQBgiYBSQSB2TCB1gSBgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAABBAAAAAAAAAAAAAAAAAAAAAABCAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAQQAAAAAAAAAAAAAAAAAAAAAAIBAAIBAAIFAKWlpaUwHAYJKwYBBAGC
JgFKBA8wDQQEAAAAAQIFAKWlpVowHAYJKwYBBAGCJgFMBA8wDQQEAAAAAAIFAKWl
paUwHAYJKwYBBAGCJgFNBA8wDQQEAAAAAQIFAKWlpVowHgYJKwYBBAGCJgFOBBEw
DwQGAAAAAAAAAgUApaWlpTAeBgkrBgEEAYImAU8EETAPBAYAAAAAAAACBQClpaWl
MCAGCSsGAQQBgiYBUAQTMBEECAAAAAAAAAAAAgUApaWlpTAVBgkrBgEEAYImAVEE
CDAGBAQAAAIAMA0GCSqGSIb3DQEBDQUAA4ICAQBTlFXKSMRBydt0MVa7Qy27eYmx
POBuYKOM31fmw3Xs+MA83xdVovoLYy3pMNzZrQacfI0rqHRPVK44Zo3qo9gby7Gu
GnliVQisim3XLioNW7YGmS2aAtAtHg9/zDPIoXsXdFI+e5lQvfckB3Ki3MCVQiZO
R5m50Rgc2poLUQN7OmAsP0HxARZTHjfPIuOBKTvuIs8FlWyMkgicW6SxzXgdl5Ce
HLiYkmMEqgawdLyXT71PIQW4LFDR4tXu76ZUnKut7xrAbN8neis5dT/l7Q71Gmj+
slGX/XqUZFLe6clNoPiFVgz4RfQr9Ik0JenYljZehNscSQUB8Y1DhwlXc5LfqYGL
LhRMtDEXUfyOJtcQ5CDAxqtq/2eNQZPiWsI2vLquULc2bG02na1TL65vehQ0TV+a
5DFA1wlvgK8pGu3Yug+WM8GDF6MnjrxS7jWWHl8C0Nj+Bw4ftdCMwY7bivAklPVt
4owfr5MVDj7NOcldBrJRMa9HfVUXmW8S9vdItOMoeWnVbDfnG+woVieZU8ir3r6g
nUWGeJJxH4U3NkrDG+1MMNgjSHJ8Ja/UDzANPDZO1nGGg/Xw6tmKQJhwQS/+7/Ye
FrgeA695DZxtM2I5Ju5TBlUsN9hUZyFBQn95/ZraYTjRet5+zH6deeIgbdgwqHPp
Y1BE0UyrpzC2bhp6sg==
-----END CERTIFICATE-----
Keywrirter X509证书格式解析
版本号 V3 Version
Version: 3 (0x2)
序列号 Serial Number
Serial Number:
60:8d:ad:b0:51:56:6a:51:93:1e:14:09:9b:b2:13:40:7a:87:a3:fd
签名算法OID Signature Algorithm Identifier
Signature Algorithm: sha512WithRSAEncryption
签发者 Issuer(各项名字的集合)
Issuer: C = oR, ST = rx, L = gQE843yQV0sag, O = dqhGYAQ2Y4gFfCq0t1yABCYxex9eAxt71f, OU = a87RB35W, CN = x0FSqGTPWbGpuiV, emailAddress = kFp5uGcgWXxcfxi@vsHs9C9qQWGrBs.com
有效期 Validity
生效期 NotBefore
Not Before: Aug 9 02:28:06 2023 GMT
失效期 NotAfter
Not After : Sep 8 02:28:06 2023 GMT
申请者 Subject (各项名字的集合)
Subject: C = oR, ST = rx, L = gQE843yQV0sag, O = dqhGYAQ2Y4gFfCq0t1yABCYxex9eAxt71f, OU = a87RB35W, CN = x0FSqGTPWbGpuiV, emailAddress = kFp5uGcgWXxcfxi@vsHs9C9qQWGrBs.com
申请者公钥信息 Subject Public Key Info
算法* Algorithm
Public Key Algorithm: rsaEncryption
公钥PK Subject Public Key
Modulus:
00:d1:3a:bd:15:54:7f:1b:fa:7c🆎24:b6:33:e2:
a5:34:ba:20:99:8f:6c:94:89:5b:f1:9a:22:60:62:
23:e8:32:09:f5:5b:c4:ca:18:4a:1a:15:1b:ad:6b:
05:45:6a:77:bf:65:4d:13:f5:a7:60:9b:c2:7a:88:
d6:02:22:65:bd:49:13:d1:b1:33:f9:06:23:a8:f4:
7d:81:a8:55:08🇩🇪a7:2a:8b:08:0f:0e:3d:a8:6a:
e6:6c:44:6d:7c:fe:e4:9c:c3:0e:fc:9e:e9:6d:d8:
0e:9f:90:04:66:2e:0e:ce:27:69:19:5a:5e:12:83:
56:c9💿2e:32:a7:f1:4a:b4:e0:17:17:2a:1d:55:
d9:5d:15:96:e7:7c:42:02:8c:e7:14:cc:78:4b:23:
5d:8d:cf:3b:28:19:df:14:22:6f:c1:bd:f5:85:3a:
dd:3e:00:4f:27:99:51:b5:80:d8:9c:29:60:21:05:
f5:04:d1:77:b9:02:b5:b9:44:08:9f:df:32:a1:dc:
3b:5a:aa:19:be:7d:be:0e:0a:9e:d2:c2:9e:47:0d:
32🆎ca:d9:d4:c4🆎13:eb:f8:3b:d3:e8:49:4c:
5f:3c:f8:94:6d:39:c8:09:af:d5:dc:27:81:b3:9f:
15:e0:64:f6:52:62:18:b2:8a:23:ac:9c:63:36:1e:
17:88:29:1f:ae:5c:bf:e7:31:b3:ad:b9:fb:14:92:
6c:f4:5f:15:e2:2d:28:68:40:4c:b1:ec:79:c9:a0:
91:44:58:72:d5:15:95:0b:a2:3b:59:58:18:d3:3c:
56:72:4e:8c:da🇩🇪8f:7e:1b:bc:2b:cf:a2:96🆎
53:08:39:95:20:90:9e:d0:e2:b1:36:75:e2:bc:13:
e1:38:90:bc:1d:53:11:4c:f0:ae:ea:43:e4:a2:69:
6c:9e:c7:e5:37:65:bf:55:19:87:57:36:40:7a:b1:
3c:b3:4c:1b:28:08:1d:e1:06:7e:67:32:a8🇩🇪bc:
0c:57:da:79:f0:e8:be:09:6f:3b:95:a7:c5:60:bd:
a8:d5:9e:12:9b:71:66:ad:75:76:98:b9:96:8f:32:
de:31:74:9f:30:e5:1e:47:11:d2:04:87:e2:f9:42:
73:50:74:b2:d6:48:b9:22:ae:57:e9:d0:7f:56:ca:
f8:f6:d5:1a:c4:61:6c:25:34:ae:4d:3b:b4:a9:97:
83:51:c5:88:42:5b:5a:db:6b:7c:b6:bb:44:29:83:
76:78:3d:ff:34:a7:a2:03:6e:4d:e2:46:2d:5a:a6:
c2:6c🆎2b:db:7c:26:89:65:48:ca:ee:9f:13:13:
94:24:e0:f6:e0:2c:c9:35:58:09:28:b4:94:75:0d:
签发者唯一ID Unique ID of CA
CA:TRUE
申请者唯一ID Unique ID of Subject
扩展项 Extension
标准扩展项
1.3.6.1.4.1.294.1.64 = ASN1:SEQUENCE:enc_aes_key
1.3.6.1.4.1.294.1.65 = ASN1:SEQUENCE:enc_smpk_signed_aes_key
1.3.6.1.4.1.294.1.67 = ASN1:SEQUENCE:aesenc_smpkh
1.3.6.1.4.1.294.1.68 = ASN1:SEQUENCE:aesenc_smek
1.3.6.1.4.1.294.1.69 = ASN1:SEQUENCE:plain_mpk_options
1.3.6.1.4.1.294.1.72 = ASN1:SEQUENCE:plain_mek_options
1.3.6.1.4.1.294.1.73 = ASN1:SEQUENCE:aesenc_user_otp
1.3.6.1.4.1.294.1.74 = ASN1:SEQUENCE:plain_key_rev
1.3.6.1.4.1.294.1.76 = ASN1:SEQUENCE:plain_msv
1.3.6.1.4.1.294.1.77 = ASN1:SEQUENCE:plain_key_cnt
1.3.6.1.4.1.294.1.78 = ASN1:SEQUENCE:plain_swrev_sysfw
1.3.6.1.4.1.294.1.79 = ASN1:SEQUENCE:plain_swrev_sbl
1.3.6.1.4.1.294.1.80 = ASN1:SEQUENCE:plain_swrev_sec_brdcfg
1.3.6.1.4.1.294.1.81 = ASN1:SEQUENCE:plain_keywr_min_version
自定义扩展项
签名算法部分
签名算法OID Signature Algorithm Identifier
sha512WithRSAEncryption
签名部分
53:94:55:ca:48:c4:41:c9:db:74:31:56:bb:43:2d:bb:79:89:
b1:3c:e0:6e:60:a3:8c:df:57:e6:c3:75:ec:f8:c0:3c:df:17:
55:a2:fa:0b:63:2d:e9:30:dc:d9:ad:06:9c:7c:8d:2b:a8:74:
4f:54:ae:38:66:8d:ea:a3:d8:1b:cb:b1:ae:1a:79:62:55:08:
ac:8a:6d:d7:2e:2a:0d:5b:b6:06:99:2d:9a:02:d0:2d:1e:0f:
7f:cc:33:c8:a1:7b:17:74:52:3e:7b:99:50:bd:f7:24:07:72:
a2:dc:c0:95:42:26:4e:47:99:b9:d1:18:1c:da:9a:0b:51:03:
7b:3a:60:2c:3f:41:f1:01:16:53:1e:37:cf:22:e3:81:29:3b:
ee:22:cf:05:95:6c:8c:92:08:9c:5b:a4:b1💿78:1d:97:90:
9e:1c:b8:98:92:63:04:aa:06:b0:74:bc:97:4f:bd:4f:21:05:
b8:2c:50:d1:e2:d5:ee:ef:a6:54:9c🆎ad:ef:1a:c0:6c:df:
27:7a:2b:39:75:3f:e5:ed:0e:f5:1a:68:fe:b2:51:97:fd:7a:
94:64:52🇩🇪e9:c9:4d:a0:f8:85:56:0c:f8:45:f4:2b:f4:89:
34:25:e9:d8:96:36:5e:84:db:1c:49:05:01:f1:8d:43:87:09:
57:73:92:df:a9:81:8b:2e:14:4c:b4:31:17:51:fc:8e:26:d7:
10:e4:20:c0:c6🆎6a:ff:67:8d:41:93:e2:5a:c2:36:bc:ba:
ae:50:b7:36:6c:6d:36:9d:ad:53:2f:ae:6f:7a:14:34:4d:5f:
9a:e4:31:40:d7:09:6f:80:af:29:1a:ed:d8:ba:0f:96:33:c1:
83:17:a3:27:8e:bc:52:ee:35:96:1e:5f:02:d0:d8:fe:07:0e:
1f:b5:d0:8c:c1:8e:db:8a:f0:24:94:f5:6d:e2:8c:1f:af:93:
15:0e:3e💿39:c9:5d:06:b2:51:31:af:47:7d:55:17:99:6f:
12:f6:f7:48:b4:e3:28:79:69:d5:6c:37:e7:1b:ec:28:56:27:
99:53:c8🆎de:be:a0:9d:45:86:78:92:71:1f:85:37:36:4a:
c3:1b:ed:4c:30:d8:23:48:72:7c:25:af:d4:0f:30:0d:3c:36:
4e:d6:71:86:83:f5:f0:ea:d9:8a:40:98:70:41:2f:fe:ef:f6:
1e:16:b8:1e:03:af:79:0d:9c:6d:33:62:39:26:ee:53:06:55:
2c:37:d8:54:67:21:41:42:7f:79:fd:9a:da:61:38:d1:7a🇩🇪
7e:cc:7e:9d:79:e2:20:6d:d8:30:a8:73:e9:63:50:44:d1:4c:
ab:a7:30:b6:6e:1a:7a:b2
签名体
Keywrirter OTP Keys

BMEK:Not used.
BMPKH :Not used.
EXTENDED OTP :Not used.
KEYCNT :2 if BMPK, SMPK are used, 1 if SMPK is used, 0 if none.
KEYREV :Can have a maximum value = key count
MEK Options :These are currently not supported, and reserved for future use.
MPK Options :These are currently not supported, and reserved for future use.
MSV :Model Specific Value is a 20 bit value.
SWREV :Use of SWREV is optional.
HS 镜像签名
Keys HS

TI提供的DummyKey默认这里我们不需要使用,如果需要后续给sbl以及其他pdk镜像进行签名,可以copy客户的私钥和加密key到目录下。
# cp ${PSDKRA_PATH}/pdk/packages/ti/build/makerules/k3_dev_mpk.pem ~/TIDummyKey/smpk.pem
# cp ${PSDKRA_PATH}/pdk/packages/ti/build/makerules/k3_dev_mek.txt ~/TIDummyKey/smek.txt
SBL HS
编译SBL_HS
cd ${PDK_BUID_DIR}
make sbl_mmcsd_img_hs BOARD=${BOARD} -sj32
cd ../boot/sbl/binary/${BOARD}_hs/mmcsd/bin/
mv sbl_mmcsd_img_mcu1_0_release.tiimage tiboot3.bin
成果物路径:
ti-processor-sdk-rtos-j784s4-evm-08_06_01_03/pdk_j784s4_08_06_01_03/packages/ti/boot/sbl/binary/j784s4_evm_hs/mmcsd/bin/tiboot3.bin
签名SBL_HS

./x509CertificateGen.sh
-b /mnt/VOS8.6/VOS_TDA4VH_08_05_hs/Mcal/pdk/packages/ti/build/makerules/app #被签名镜像
-o /mnt/VOS8.6/VOS_TDA4VH_08_05_hs/Mcal/pdk/packages/ti/build/makerules/erika3app.tiimage #签名镜像成果物
-c R5 #签名内核
-l 0xA0D00000 #签名文件入口地址
-k /mnt/VOS8.6/VOS_TDA4VH_08_05_hs/Mcal/pdk/packages/ti/build/makerules/k3_dev_mpk.pem #签名私钥
-d DEBUG
-j DBG_FULL_ENABLE
-m SPLIT_MODE
签名与未签名镜像区别

签名证书内容
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
74:2b:d5:26:ef:b8:9b:b5:72:d0:d1:95:78:17:6e:29:6b:56:95:e5
Signature Algorithm: sha512WithRSAEncryption
Issuer: C = US, ST = SC, L = Dallas, O = "Texas Instruments., Inc.", OU = PBU, CN = Albert, emailAddress = Albert@ti.com
Validity
Not Before: Aug 10 03:05:06 2023 GMT
Not After : Sep 9 03:05:06 2023 GMT
Subject: C = US, ST = SC, L = Dallas, O = "Texas Instruments., Inc.", OU = PBU, CN = Albert, emailAddress = Albert@ti.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (4096 bit)
Modulus:
00:d1:3a:bd:15:54:7f:1b:fa:7c:ab:24:b6:33:e2:
a5:34:ba:20:99:8f:6c:94:89:5b:f1:9a:22:60:62:
23:e8:32:09:f5:5b:c4:ca:18:4a:1a:15:1b:ad:6b:
05:45:6a:77:bf:65:4d:13:f5:a7:60:9b:c2:7a:88:
d6:02:22:65:bd:49:13:d1:b1:33:f9:06:23:a8:f4:
7d:81:a8:55:08:de:a7:2a:8b:08:0f:0e:3d:a8:6a:
e6:6c:44:6d:7c:fe:e4:9c:c3:0e:fc:9e:e9:6d:d8:
0e:9f:90:04:66:2e:0e:ce:27:69:19:5a:5e:12:83:
56:c9:cd:2e:32:a7:f1:4a:b4:e0:17:17:2a:1d:55:
d9:5d:15:96:e7:7c:42:02:8c:e7:14:cc:78:4b:23:
5d:8d:cf:3b:28:19:df:14:22:6f:c1:bd:f5:85:3a:
dd:3e:00:4f:27:99:51:b5:80:d8:9c:29:60:21:05:
f5:04:d1:77:b9:02:b5:b9:44:08:9f:df:32:a1:dc:
3b:5a:aa:19:be:7d:be:0e:0a:9e:d2:c2:9e:47:0d:
32:ab:ca:d9:d4:c4:ab:13:eb:f8:3b:d3:e8:49:4c:
5f:3c:f8:94:6d:39:c8:09:af:d5:dc:27:81:b3:9f:
15:e0:64:f6:52:62:18:b2:8a:23:ac:9c:63:36:1e:
17:88:29:1f:ae:5c:bf:e7:31:b3:ad:b9:fb:14:92:
6c:f4:5f:15:e2:2d:28:68:40:4c:b1:ec:79:c9:a0:
91:44:58:72:d5:15:95:0b:a2:3b:59:58:18:d3:3c:
56:72:4e:8c:da:de:8f:7e:1b:bc:2b:cf:a2:96:ab:
53:08:39:95:20:90:9e:d0:e2:b1:36:75:e2:bc:13:
e1:38:90:bc:1d:53:11:4c:f0:ae:ea:43:e4:a2:69:
6c:9e:c7:e5:37:65:bf:55:19:87:57:36:40:7a:b1:
3c:b3:4c:1b:28:08:1d:e1:06:7e:67:32:a8:de:bc:
0c:57:da:79:f0:e8:be:09:6f:3b:95:a7:c5:60:bd:
a8:d5:9e:12:9b:71:66:ad:75:76:98:b9:96:8f:32:
de:31:74:9f:30:e5:1e:47:11:d2:04:87:e2:f9:42:
73:50:74:b2:d6:48:b9:22:ae:57:e9:d0:7f:56:ca:
f8:f6:d5:1a:c4:61:6c:25:34:ae:4d:3b:b4:a9:97:
83:51:c5:88:42:5b:5a:db:6b:7c:b6:bb:44:29:83:
76:78:3d:ff:34:a7:a2:03:6e:4d:e2:46:2d:5a:a6:
c2:6c:ab:2b:db:7c:26:89:65:48:ca:ee:9f:13:13:
94:24:e0:f6:e0:2c:c9:35:58:09:28:b4:94:75:0d:
10:63:63
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:TRUE
1.3.6.1.4.1.294.1.3:
0....
1.3.6.1.4.1.294.1.34:
0R..`.H.e.....@.+..H..={R...Vs.<.CQ.o.!0....&G....m.r_.`-..E>.3..bC*.....k........*x
1.3.6.1.4.1.294.1.35:
0...A......
1.3.6.1.4.1.294.1.1:
0............A......*x
1.3.6.1.4.1.294.1.2:
0M..`.H.e.....@.+..H..={R...Vs.<.CQ.o.!0....&G....m.r_.`-..E>.3..bC*.....k.....
1.3.6.1.4.1.294.1.8:
0+. .........................................
Signature Algorithm: sha512WithRSAEncryption
25:88:8e:49:4d:b0:e6:0b:96:97:68:7c:29:cf:0d:78:a7:63:
b0:18:06:19:fa:3d:fb:0d:c1:80:18:fd:4f:4f:d1:84:d8:88:
db:ee:86:9e:1e:86:d3:db:9f:e8:ce:a6:48:49:d1:ca:2b:b0:
13:c6:b5:59:50:48:22:0d:42:e1:b8:0d:e5:a5:77:1e:34:3d:
7d:e6:44:19:9d:f1:01:2f:dc:15:8b:ce:1c:b9:a1:e9:69:0f:
b6:16:72:64:39:f1:22:58:e9:70:90:45:55:1c:03:e9:cf:1d:
ad:d5:5e:f2:be:12:2e:ec:1a:d2:53:75:12:21:c1:dc:e1:05:
0e:e3:b8:0d:49:7f:ea:e5:8f:f7:af:64:26:b9:13:3b:59:49:
ee:ba:36:1a:a4:b5:49:44:b7:6a:f4:f4:aa:7a:93:b3:ba:22:
d3:1f:ec:53:a4:89:77:96:0e:ae:79:3f:0d:c2:99:34:c2:ac:
15:38:68:28:85:58:b6:89:1b:a3:3a:36:82:d8:d7:ac:a0:b4:
a3:af:54:e2:44:ef:63:96:f1:7d:5a:15:2f:40:f8:70:d0:61:
f9:c8:a5:bd:85:d9:aa:6a:c8:89:75:35:df:6f:81:dd:09:62:
5d:5d:9b:00:c9:f3:e7:a3:dd:13:47:58:a7:4c:db:9e:d0:23:
f2:91:d6:b8:dc:86:15:02:17:4f:e2:1d:ed:a6:c2:63:6b:49:
2e:b2:ee:8e:cd:aa:38:ea:e8:e4:48:a3:54:aa:5d:2d:89:2f:
fc:54:19:11:e4:e1:87:1a:29:84:25:a6:60:45:fc:a7:58:79:
73:3c:c4:9a:da:c8:0f:9b:1f:f1:0e:09:b9:5a:0f:6b:f7:61:
fa:3c:39:8c:d6:8e:38:3d:2d:4d:ec:b4:aa:ab:6f:60:0e:24:
27:5b:7e:c3:b2:e1:77:61:bd:a2:a8:51:4c:c5:31:11:03:74:
14:86:bc:40:69:c0:0b:6e:92:cb:00:a7:23:91:ae:9f:85:2c:
0b:35:5f:b3:2c:c1:e9:e7:86:32:9f:34:e8:f4:d2:af:56:50:
53:86:b5:32:1f:d5:85:cf:34:ef:26:7a:e3:f2:dd:96:67:56:
e2:32:85:21:e9:a6:2c:63:dd:d0:da:3b:a6:b9:4c:15:3b:61:
77:0d:a2:1f:53:f4:65:fd:99:2e:2a:51:06:bf:68:a0:da:eb:
95:51:43:ee:aa:b1:7f:ec:c4:74:93:e3:e3:6d:14:da:29:26:
69:04:89:99:98:6f:e4:ef:e5:d8:62:17:82:7a:18:ea:1d:af:
60:c8:75:0a:b5:3c:6b:5f:25:bb:1f:50:16:e7:56:c7:3f:16:
32:37:65:81:c9:ce:9d:a5
-----BEGIN CERTIFICATE-----
MIIHCjCCBPKgAwIBAgIUdCvVJu+4m7Vy0NGVeBduKWtWleUwDQYJKoZIhvcNAQEN
BQAwgYsxCzAJBgNVBAYTAlVTMQswCQYDVQQIDAJTQzEPMA0GA1UEBwwGRGFsbGFz
MSEwHwYDVQQKDBhUZXhhcyBJbnN0cnVtZW50cy4sIEluYy4xDDAKBgNVBAsMA1BC
VTEPMA0GA1UEAwwGQWxiZXJ0MRwwGgYJKoZIhvcNAQkBFg1BbGJlcnRAdGkuY29t
MB4XDTIzMDgxMDAzMDUwNloXDTIzMDkwOTAzMDUwNlowgYsxCzAJBgNVBAYTAlVT
MQswCQYDVQQIDAJTQzEPMA0GA1UEBwwGRGFsbGFzMSEwHwYDVQQKDBhUZXhhcyBJ
bnN0cnVtZW50cy4sIEluYy4xDDAKBgNVBAsMA1BCVTEPMA0GA1UEAwwGQWxiZXJ0
MRwwGgYJKoZIhvcNAQkBFg1BbGJlcnRAdGkuY29tMIICIjANBgkqhkiG9w0BAQEF
AAOCAg8AMIICCgKCAgEA0Tq9FVR/G/p8qyS2M+KlNLogmY9slIlb8ZoiYGIj6DIJ
9VvEyhhKGhUbrWsFRWp3v2VNE/WnYJvCeojWAiJlvUkT0bEz+QYjqPR9gahVCN6n
KosIDw49qGrmbERtfP7knMMO/J7pbdgOn5AEZi4OzidpGVpeEoNWyc0uMqfxSrTg
FxcqHVXZXRWW53xCAoznFMx4SyNdjc87KBnfFCJvwb31hTrdPgBPJ5lRtYDYnClg
IQX1BNF3uQK1uUQIn98yodw7WqoZvn2+Dgqe0sKeRw0yq8rZ1MSrE+v4O9PoSUxf
PPiUbTnICa/V3CeBs58V4GT2UmIYsoojrJxjNh4XiCkfrly/5zGzrbn7FJJs9F8V
4i0oaEBMsex5yaCRRFhy1RWVC6I7WVgY0zxWck6M2t6Pfhu8K8+ilqtTCDmVIJCe
0OKxNnXivBPhOJC8HVMRTPCu6kPkomlsnsflN2W/VRmHVzZAerE8s0wbKAgd4QZ+
ZzKo3rwMV9p58Oi+CW87lafFYL2o1Z4Sm3FmrXV2mLmWjzLeMXSfMOUeRxHSBIfi
+UJzUHSy1ki5Iq5X6dB/Vsr49tUaxGFsJTSuTTu0qZeDUcWIQlta22t8trtEKYN2
eD3/NKeiA25N4kYtWqbCbKsr23wmiWVIyu6fExOUJOD24CzJNVgJKLSUdQ0QY2MC
AwEAAaOCAWIwggFeMAwGA1UdEwQFMAMBAf8wEgYJKwYBBAGCJgEDBAUwAwIBATBh
BgkrBgEEAYImASIEVDBSBglghkgBZQMEAgMEQAQrn39IsRU9e1LZHblWc84870NR
hW/cITCFm5QQJkeFFfu8bRxyX+RgLZadRT4MM8DCYkMqkNX/yORroLQO2bECAwUq
eDAYBgkrBgEEAYImASMECzAJBARBwAEAAgEBMCMGCSsGAQQBgiYBAQQWMBQCAQEC
ARACAQIEBEHAAQACAwUqeDBcBgkrBgEEAYImAQIETzBNBglghkgBZQMEAgMEQAQr
n39IsRU9e1LZHblWc84870NRhW/cITCFm5QQJkeFFfu8bRxyX+RgLZadRT4MM8DC
YkMqkNX/yORroLQO2bEwOgYJKwYBBAGCJgEIBC0wKwQgAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAACAQQCAQACAQAwDQYJKoZIhvcNAQENBQADggIBACWI
jklNsOYLlpdofCnPDXinY7AYBhn6PfsNwYAY/U9P0YTYiNvuhp4ehtPbn+jOpkhJ
0corsBPGtVlQSCINQuG4DeWldx40PX3mRBmd8QEv3BWLzhy5oelpD7YWcmQ58SJY
6XCQRVUcA+nPHa3VXvK+Ei7sGtJTdRIhwdzhBQ7juA1Jf+rlj/evZCa5EztZSe66
NhqktUlEt2r09Kp6k7O6ItMf7FOkiXeWDq55Pw3CmTTCrBU4aCiFWLaJG6M6NoLY
16ygtKOvVOJE72OW8X1aFS9A+HDQYfnIpb2F2apqyIl1Nd9vgd0JYl1dmwDJ8+ej
3RNHWKdM257QI/KR1rjchhUCF0/iHe2mwmNrSS6y7o7Nqjjq6ORIo1SqXS2JL/xU
GRHk4YcaKYQlpmBF/KdYeXM8xJrayA+bH/EOCblaD2v3Yfo8OYzWjjg9LU3stKqr
b2AOJCdbfsOy4XdhvaKoUUzFMREDdBSGvEBpwAtukssApyORrp+FLAs1X7Mswenn
hjKfNOj00q9WUFOGtTIf1YXPNO8meuPy3ZZnVuIyhSHppixj3dDaO6a5TBU7YXcN
oh9T9GX9mS4qUQa/aKDa65VRQ+6qsX/sxHST4+NtFNopJmkEiZmYb+Tv5dhiF4J6
GOodr2DIdQq1PGtfJbsfUBbnVsc/FjI3ZYHJzp2l
-----END CERTIFICATE-----
启动SBL_HS
SBL Revision: 01.00.10.01 (Aug 11 2023 - 14:47:36)
SBL_SciClientInit start!
SBL_ReadSysfwImage!
Sciclient_getDefaultBoardCfgInfo!
Sciclient_loadFirmware!
TIFS ver: 8.6.3–1-g2249f (Chill Capybara
SCISERVER Board Configuration header population… PASSED
Sciclient_setBoardConfigHeader… PASSED
SBL_SciClientInit end!
TDA4VH_1 Build at:Aug 11 2023 14:47:36
HW_Version:B
WKUP_RESET_STAT_Reg:0x0
Initlialzing PLLs …done.
InitlialzingClocks …done.
Initlialzing DDR …done.
Initializing GTC …Begin parsing user application
Calling Sciclient_procBootRequestProcessor, ProcId 0x20…
Calling Sciclient_procBootRequestProcessor, ProcId 0x21…
Calling Sciclient_procBootRequestProcessor, ProcId 0x22…
Calling Sciclient_procBootRequestProcessor, ProcId 0x23…
Calling Sciclient_procBootRequestProcessor, ProcId 0x24…
Calling Sciclient_procBootRequestProcessor, ProcId 0x25…
Calling Sciclient_procBootRequestProcessor, ProcId 0x26…
Calling Sciclient_procBootRequestProcessor, ProcId 0x27…
Calling Sciclient_procBootRequestProcessor, ProcId 0x1…
Calling Sciclient_procBootRequestProcessor, ProcId 0x2…
Calling Sciclient_procBootRequestProcessor, ProcId 0x6…
Calling Sciclient_procBootRequestProcessor, ProcId 0x7…
Calling Sciclient_procBootRequestProcessor, ProcId 0x8…
Calling Sciclient_procBootRequestProcessor, ProcId 0x9…
Calling Sciclient_procBootRequestProcessor, ProcId 0xa…
Calling Sciclient_procBootRequestProcessor, ProcId 0xb…
Calling Sciclient_procBootRequestProcessor, ProcId 0x30…
Calling Sciclient_procBootRequestProcessor, ProcId 0x31…
Calling Sciclient_procBootRequestProcessor, ProcId 0x32…
Calling Sciclient_procBootRequestProcessor, ProcId 0x33…
Calling Sciclient_procBootRequestProcessor, ProcId 0x80…
Searching for X509 certificate …found @0x41c7fb3c, size = 1806 bytes
SBL reserved memory Found: Start = @ 0xc2000000, Size = 0x4000000
Copying 1808 bytes from app to 0xc2000002
Found seq @ 0xc200043d
image length = 342748 bytes
Copying 342752 bytes from offset 0x70c to 0xc200070e…Cert @ 0xc2000002 …Verify >Passed…done
Switching core id 8, proc_id 0x1 to split mode…
Calling Sciclient_procBootGetProcessorState, ProcId 0x1…
Sciclient_procBootSetProcessorCfg, ProcId 0x1, enabling split mode…
Calling Sciclient_procBootGetProcessorState, ProcId 0x1…
Enabling MCU TCMs after reset for core 8
Disabling HW-based memory init of MCU TCMs for core 8
Sciclient_procBootSetProcessorCfg update TCM enable/disable settings…
Copying 0x688 bytes to 0x41c82000
Copying 0x1b10 bytes to 0xa0500000
Copying 0x484c bytes to 0xa0501b10
Copying 0x2d14 bytes to 0xa0540000
Copying 0x25fb8 bytes to 0xa0542e00
Copying 0x16a38 bytes to 0xa0580000
Copying 0xa8 bytes to 0xa05a0238
Copying 0x280 bytes to 0xa05acde8
Copying 0x8 bytes to 0xa05c75b0
Copying 0xd504 bytes to 0xa05c75b8
Copying 0xb0 bytes to 0xa0d00000
Setting entry point for core 8 @0xa0d00000
Sciclient_procBootReleaseProcessor, ProcId 0x20…
Sciclient_procBootReleaseProcessor, ProcId 0x21…
Sciclient_procBootReleaseProcessor, ProcId 0x22…
Sciclient_procBootReleaseProcessor, ProcId 0x23…
Sciclient_procBootReleaseProcessor, ProcId 0x24…
Sciclient_procBootReleaseProcessor, ProcId 0x25…
Sciclient_procBootReleaseProcessor, ProcId 0x26…
Sciclient_procBootReleaseProcessor, ProcId 0x27…
Sciclient_procBootReleaseProcessor, ProcId 0x1…
Sciclient_procBootReleaseProcessor, ProcId 0x2…
Sciclient_procBootReleaseProcessor, ProcId 0x6…
Sciclient_procBootReleaseProcessor, ProcId 0x7…
Sciclient_procBootReleaseProcessor, ProcId 0x8…
Sciclient_procBootReleaseProcessor, ProcId 0x9…
Sciclient_procBootReleaseProcessor, ProcId 0xa…
Sciclient_procBootReleaseProcessor, ProcId 0xb…
Sciclient_procBootReleaseProcessor, ProcId 0x30…
Sciclient_procBootReleaseProcessor, ProcId 0x31…
Sciclient_procBootReleaseProcessor, ProcId 0x32…
Sciclient_procBootReleaseProcessor, ProcId 0x33…
Sciclient_procBootReleaseProcessor, ProcId 0x80…
Boot the core running SBL in the end
Calling Sciclient_procBootRequestProcessor, ProcId 0x1…
Sciclient_procBootSetProcessorCfg, ProcId 0x1, EntryPoint 0xa0d00000…
Sciclient_pmSetModuleClkFreq, DevId 0x15a @ 1000000000Hz…
Copying first 128 bytes from app to MCU ATCM @ 0x0 for core 8
Calling Sciclient_procBootRequestProcessor, ProcId 0x2…
Skipping Sciclient_procBootSetProcessorCfg for ProcId 0x2, EntryPoint 0xfffffffe…
Calling Sciclient_procBootRequestProcessor, ProcId 0x1…
IOEXP_I2C_init End!
MAX20089 I2C Init Succeed.
MAX20089 STAT1.OVIN was set.
MAX20089 STAT1.OVDD was set.
MAX20089 STAT2.OV1 was set.
MAX20087 I2C Init Succeed.
MAX20087 STAT1.OVIN was set.
MAX20087 STAT1.OVDD was set.
MAX20087 STAT2.OV1 was set.
MAX20087 STAT2.OV2 was set.
MAX20087 STAT2.OV3 was set.
MAX20087 STAT2.OV4 was set.
VH1_89586_RESET set low success
VH1_89586_RESET set high success
TDA4VH1 CddPower_Init End!
Boot_App HS
使用生成目录下的.signed文件,sbl库使用HS库。
make boot_app_mmcsd_linux BOARD=j784s4_evm -sj32
TIFS HS
The previous makefile and compile command will generate the GP SBL binary first, then use TI dummy key to sign and encrypt it. Also, during building the SBL_HS, it will also sign the board configuration, security configuration, RM (Resource Management) and PM (Power Management), then integrate it into SBL. So, the finally SBL can be authenticate and decrypt by HS-SE-TIDK device.
SBL依赖HS版本的boardcfg配置。
On a HS device, System Firmware relies on the efused asymmetric public key hash(PKH) to provide root of trust. Each board configuration blob must be signed by the private key corresponding to the PKH to establish authenticity. System Firmware supports two ways of signing the board configuration blobs.

编译HS版本boardcfg配置命令。
make sciclient_boardcfg_hs BOARD=j784s4_evm

这里我们需要注意只有sbl依赖sciclient_direct_hs.aer5f,app应用程序继续使用sciclient_direct.aer5f。
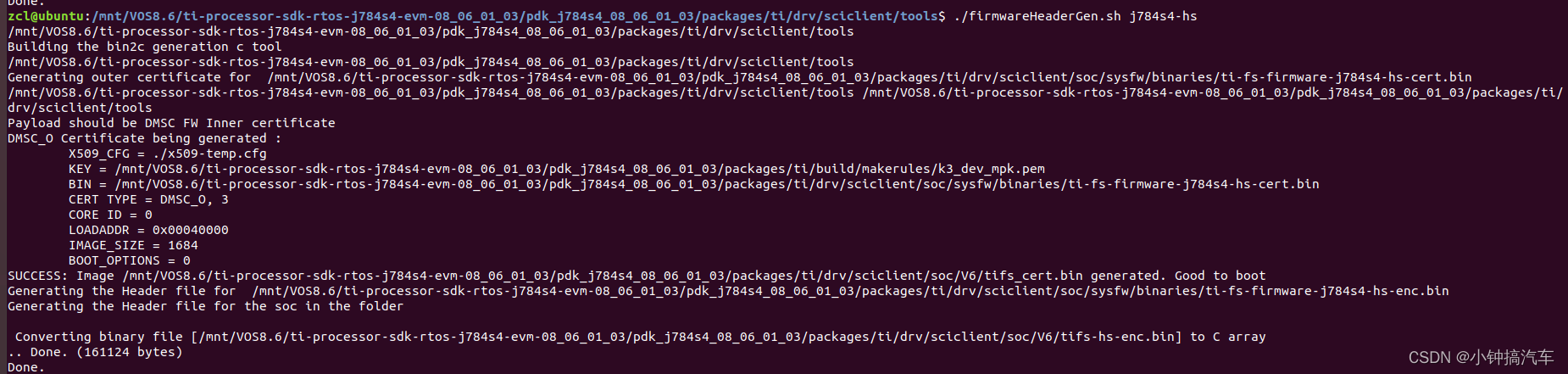
在下列目录中找到:
ti-processor-sdk-rtos-j784s4-evm-08_06_01_03/pdk_j784s4_08_06_01_03/packages/ti/drv/sciclient/tools/firmwareHeaderGen.sh
./firmwareHeaderGen.sh j784s4-hs
Lateapp1 Lateapp2 HS
$(CERT_SCRIPT) -b $(SBL_BOOTFILES_PATH)/lateapp1 -o $(SBL_BOOTFILES_PATH)/lateapp1.signed -c R5 -l 0x0 -k $(PDK_PATH)/packages/ti/build/makerules/k3_dev_mpk.pem
$(CERT_SCRIPT) -b $(SBL_BOOTFILES_PATH)/lateapp2 -o $(SBL_BOOTFILES_PATH)/lateapp2.signed -c R5 -l 0x0 -k $(PDK_PATH)/packages/ti/build/makerules/k3_dev_mpk.pem
加载成功镜像log:
BootApp_MMCBootImageLate: fp 0x 0x41c12300, fileName is 0:/lateapp1
Called SBL_MulticoreImageParse, status = 0
BootImage completed, status = 0
SBL_SlaveCoreBoot completed for Core ID#10, Entry point is 0x0
SBL_SlaveCoreBoot completed for Core ID#11, Entry point is 0x0
Loading BootImage
BootApp_MMCBootImageLate: fp 0x 0x41c12300, fileName is 0:/lateapp2
Called SBL_MulticoreImageParse, status = 0
BootImage completed, status = 0
SBL_SlaveCoreBoot completed for Core ID#14, Entry point is 0x0
SBL_SlaveCoreBoot completed for Core ID#15, Entry point is 0x0
SBL_SlaveCoreBoot completed for Core ID#18, Entry point is 0xab200000
SBL_SlaveCoreBoot completed for Core ID#19, Entry point is 0xae600000
SBL_SlaveCoreBoot completed for Core ID#20, Entry point is 0xb1a00000
SBL_SlaveCoreBoot completed for Core ID#21, Entry point is 0xb4e00000
Loading BootImage
A72 HS
TI 介绍A核启动的时候,还是对ATF DTB还有Kernel进行签名,文件系统不需要签名。
The difference is the ATF (Arm Trusted Firmware) image, DTB (Device Tree Binary) image, and Linux kernel
image should be signed and encrypted if running Linux in A72 core, and the file system does not need to be
signed. Also, only ATF and IFS (Image FileSystem) images need to be signed, if implementing the QNX in A72
core.
对linux文件进行签名:
echo "crate signed atf_optee.appimage"
$PDK_INSTALL_PATH/ti/build/makerules/x509CertificateGen.sh -b $ROOT_DIR/output/atf_optee.appimage -o $ROOT_DIR/output/atf_optee.appimage.signed -c R5 -l 0x0 -k $PDK_INSTALL_PATH/ti/build/makerules/k3_dev_mpk.pem
echo "crate signed tidtb_linux.appimage"
$PDK_INSTALL_PATH/ti/build/makerules/x509CertificateGen.sh -b $ROOT_DIR/output/tidtb_linux.appimage -o $ROOT_DIR/output/tidtb_linux.appimage.signed -c R5 -l 0x0 -k $PDK_INSTALL_PATH/ti/build/makerules/k3_dev_mpk.pem
echo "tikernelimage_linux.appimage"
$PDK_INSTALL_PATH/ti/build/makerules/x509CertificateGen.sh -b $ROOT_DIR/output/tikernelimage_linux.appimage -o $ROOT_DIR/output/tikernelimage_linux.appimage.signed -c R5 -l 0x0 -k $PDK_INSTALL_PATH/ti/build/makerules/k3_dev_mpk.pem
HS签名与验签过程
生成数字签名
1 利用RSA算法生成公钥、私钥。私钥由密钥持有者自主保存,公钥可对外发布。
2 准备好待签名的文档。
3 利用哈希算法(HASH),生成待签名文档的摘要。(文档摘要)
4 利用签名者的私钥,加密文档摘要。
5 将签名者的公钥、数字签名、文档,传递给验签者。

验证数字签名

1 验签者获得签名者发过来的数字签名、公钥、文档。
2 验签者利用签名者的公钥解密数字签名,得到解密后的文档摘要。
3 验签者利用哈希算法生成文档的摘要
4 比对解密后的文档摘要与利用哈希算法生成的摘要。
5 若两个摘要完全一致,则验签成功;否者验签失败
TDA4验签签名
TDA4的验签与签名与上述相同,多的是使用OTP提前将公钥的HASH存在OPT,传输的镜像的公钥HASH值必须与OTP内部的公钥HASH值相同才能验签。

























 15万+
15万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








