目标
aHR0cHM6Ly9zcGFjZS5iaWxpYmlsaS5jb20vNDM1Mjc1NTg=
抓包
参数w_rid加密

分析
直接搜索即可定位
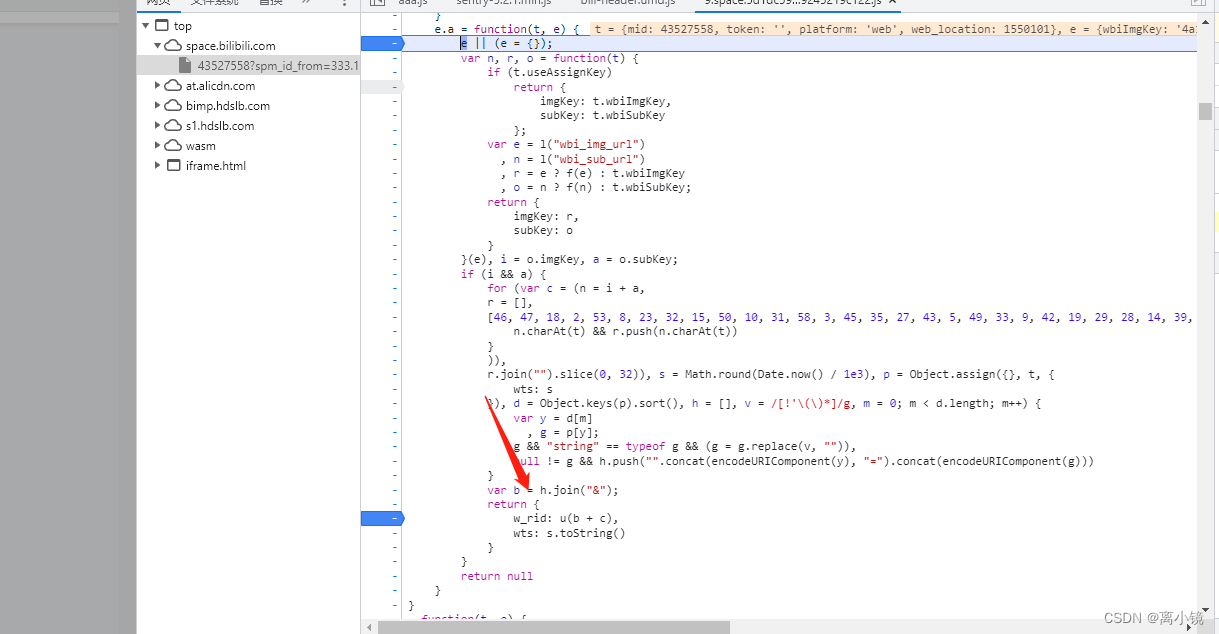
首先来看外层 函数的参数 t 和 e; t是我们的请求参数,e是一个固定值(经过测试),也可以跟栈往上找

e的跟栈,确实是写死的。

接下来分析加密函数体
e.a = function(t, e) {
e || (e = {});
var n, r, o = function(t) {
if (t.useAssignKey)
return {
imgKey: t.wbiImgKey,
subKey: t.wbiSubKey
};
var e = l("wbi_img_url")
, n = l("wbi_sub_url")
, r = e ? f(e) : t.wbiImgKey
, o = n ? f(n) : t.wbiSubKey;
return {
imgKey: r,
subKey: o
}
}(e), i = o.imgKey, a = o.subKey;
if (i && a) {
for (var c = (n = i + a,
r = [],
[46, 47, 18, 2, 53, 8, 23, 32, 15, 50, 10, 31, 58, 3, 45, 35, 27, 43, 5, 49, 33, 9, 42, 19, 29, 28, 14, 39, 12, 38, 41, 13, 37, 48, 7, 16, 24, 55, 40, 61, 26, 17, 0, 1, 60, 51, 30, 4, 22, 25, 54, 21, 56, 59, 6, 63, 57, 62, 11, 36, 20, 34, 44, 52].forEach((function(t) {
n.charAt(t) && r.push(n.charAt(t))
}
)),
r.join("").slice(0, 32)), s = Math.round(Date.now() / 1e3), p = Object.assign({}, t, {
wts: s
}), d = Object.keys(p).sort(), h = [], v = /[!'\(\)*]/g, m = 0; m < d.length; m++) {
var y = d[m]
, g = p[y];
g && "string" == typeof g && (g = g.replace(v, "")),
null != g && h.push("".concat(encodeURIComponent(y), "=").concat(encodeURIComponent(g)))
}
var b = h.join("&");
return {
w_rid: u(b + c),
wts: s.toString()
}
}
return null
}因为e是写死的,那么加密函数上面的部分逻辑就不用看了,只要分析下面代码就可以了
// i = e.wbiImgKey
// a = e.wbiSubKey
for (var c = (n = i + a,
r = [],
[46, 47, 18, 2, 53, 8, 23, 32, 15, 50, 10, 31, 58, 3, 45, 35, 27, 43, 5, 49, 33, 9, 42, 19, 29, 28, 14, 39, 12, 38, 41, 13, 37, 48, 7, 16, 24, 55, 40, 61, 26, 17, 0, 1, 60, 51, 30, 4, 22, 25, 54, 21, 56, 59, 6, 63, 57, 62, 11, 36, 20, 34, 44, 52].forEach((function(t) {
n.charAt(t) && r.push(n.charAt(t))
}
)),
r.join("").slice(0, 32)), s = Math.round(Date.now() / 1e3), p = Object.assign({}, t, {
wts: s
}), d = Object.keys(p).sort(), h = [], v = /[!'\(\)*]/g, m = 0; m < d.length; m++) {
var y = d[m]
, g = p[y];
g && "string" == typeof g && (g = g.replace(v, "")),
null != g && h.push("".concat(encodeURIComponent(y), "=").concat(encodeURIComponent(g)))
}
var b = h.join("&");
return {
w_rid: u(b + c),
wts: s.toString()
}最后的u经过测试就是个md5,如果不想还原代码直接就可以复制到本地,补上md5运行。
我这边把它还原成了python代码,代码大致的逻辑就是
1 根据指定下标取n字符串里面的元素,再拼接成新的字符串
2 生成个10位时间戳
3 参数t,多加个属性wts=当前时间戳
4 把参数t根据key排序改为key=value的形式
5 md5加密(步骤4 和 1的结果)还原
import hashlib
import time
def web_rid(param):
n = "653657f524a547ac981ded72ea172057" + "6e4909c702f846728e64f6007736a338"
r = []
c = ''.join([n[i] for i in [46, 47, 18, 2, 53, 8, 23, 32, 15, 50, 10, 31, 58, 3, 45, 35, 27, 43, 5, 49, 33, 9, 42, 19, 29, 28, 14, 39, 12, 38, 41, 13, 37, 48, 7, 16, 24, 55, 40, 61, 26, 17, 0, 1, 60, 51, 30, 4, 22, 25, 54, 21, 56, 59, 6, 63, 57, 62, 11, 36, 20, 34, 44, 52]][:32])
s = int(time.time())
param["wts"] = "1684737775"
h = []
param = "&".join([f"{i[0]}={i[1]}"for i in sorted(param.items(), key=lambda x:x[0])])
return hashlib.md5((param+c).encode(encoding='utf-8')).hexdigest(), s
print(web_rid({
"mid": 700152,
"token": "",
"platform": "web",
"web_location": 1550101
}))










 本文详细介绍了如何进行B站博主主页w_rid的逆向工程,从目标设定、网络抓包到代码分析和逻辑还原,揭示了加密参数的解密过程,其中涉及到javascript加密函数的解析,最终在Python环境中成功还原了加密逻辑。
本文详细介绍了如何进行B站博主主页w_rid的逆向工程,从目标设定、网络抓包到代码分析和逻辑还原,揭示了加密参数的解密过程,其中涉及到javascript加密函数的解析,最终在Python环境中成功还原了加密逻辑。

















 501
501

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










